Security Monitoring and Analysis Service
Antiy provides the most efficient and professional security monitoring service in the industry. It realizes real-time monitoring through specialized security equipment, such as PTA, PTD and IEP, and provides the monitoring data by measuring regularly the potential risks existing in the systems, such as Web, malicious domain names and emails. With its help, customers can master the security states of their own systems in real time and measure the improvements. It can free up the security operation and maintenance personnel of the user units from the tedious daily security maintenance work, and reduce the manpower and energy input for security operation and maintenance, which reduces the management costs.
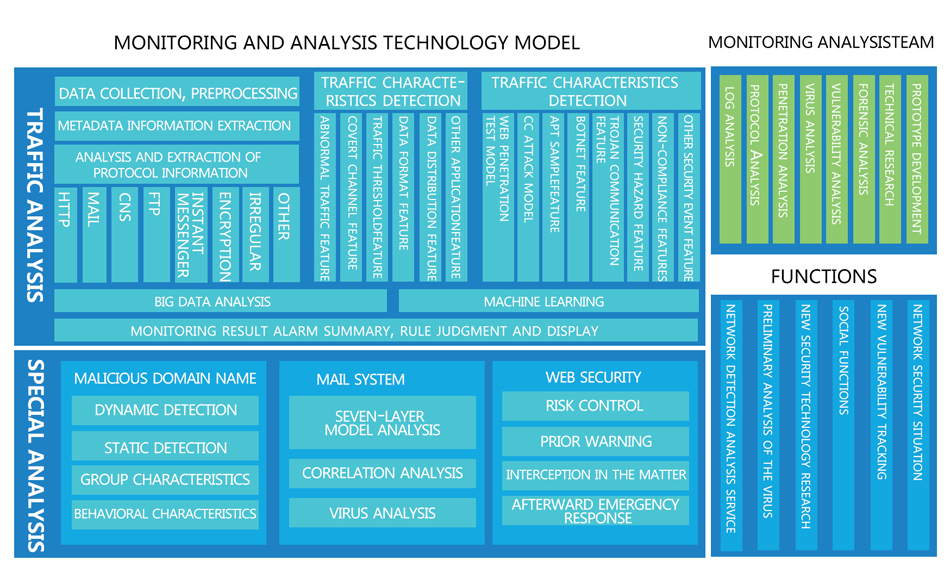
The monitoring and analysis firstly extracts and stores the information required for security events through the collection of traffic data and metadata information, and then detects abnormal traffic, such as hidden channels, traffic thresholds, data formats, data distribution and etc.. Then, various types of attack behaviors of security events are modeled and extracted. Finally, the monitoring results are aggregated, studied, and displayed through big data analysis and machine learning techniques. For key systems, it can carry out in-depth analysis through specific analysis technologies, such as DNS, email systems, and Web systems.
The security monitoring service includes the following aspects:
1.Real-time monitoring
The monitoring service is aiming at achieving 365*24 hours of real-time monitoring and backtracking capabilities. Note: According to the storage space and traffic conditions, the original data stream backtracking is generally within 48 hours, and the log backtracking is generally within 30 days.
2.Comprehensive monitoring of borders
This service plan guarantees the deployment of monitoring equipment at all border outlets of the network, and the processing capacity exceeds the upper limit of the communication bandwidth to ensure that there are no missing or dead corners in the boundary monitoring.
3.Comprehensive monitoring of attack behaviors
Monitoring network attack behaviors include: SQL injection, XSS injection, code execution, CSRF attack, cross-directory access, logic error attack, file inclusion attack, uploading vulnerability attack, scanning attack, brute force attack, 0-day attack and other common ones.
4.Comprehensive monitoring of major security incidents
Major security incidents include: high-risk security incidents, such as APT attacks, botnets, Trojan control, worm viruses, information breaching, and CC attacks, which seriously endanger and affect the core security of the government affairs’ network.
5.Comprehensive monitoring of security risks
In addition to attacks and controlled events, security risks are monitored based on traffic analysis, such as non-demanded encryption, weak passwords, software bugs, and sensitive information disclosure.
6.Comprehensive protection of the core network
For the core network, it carries out comprehensive protection from the external attack behaviors, and blocks the common attack behaviors to a certain extent to ensure the normal operation of the network. At the same time, according to the monitoring and analysis situation, it constantly optimizes the configuration to achieve more effective defense and blocking.
7.Provide disposal suggestions and cooperation
For the discovered high-risk security incidents and security risks, our security experts will provide relevant disposal suggestions based on experience and information; if the customers have self-determination capabilities and operating conditions, we can assist them in handling various security incidents
