Antiy Endpoint Defense System (IEP)

Introduction
Multi-environment threat identification, multi-dimensional indicator correlation
Antiy IEP is a set of professional endpoint security products. IEP integrates Antiy’s own R&D and internationally leading anti-virus engine. While providing powerful virus detection capabilities, it also provides the following functions, such as active defense, ransomware protection, vulnerability detection and repairing, security baseline, unknown threat protection, threat tracking and deleting, visual management, statistical reports and etc.. It can help users in the face of new threats to network security, build a terminal security and effective protection system to ensure the security of terminal assets, data and business.
Features
1.Threat detection engine designed by patented technology
The built-in anti-virus engine of IEP is independently developed by Antiy and has complete independent intellectual property rights. Antiy is one of the earliest independent anti-virus engine manufacturers in China. It has been working on anti-virus research for 17 years and is in the first level in the world.
2. Private cloud killing, dual control of “black” and “white” files
IEP adopts a private cloud killing architecture that can adapt to the user’s network environment and establish a dedicated knowledge base for the user’s business situation to ensure user privacy. Antiy IEP utilizes Black and white dual control detection mechanism, thus it can identify and control executable files in system: identifying exactly safe (white) and malicious (black) executable files, and for grey (unknown) files, users can determine the running of unknown files in terms of security control levels of different hosts.
3. Multidimensional anti-ransomware
IEP adopts a multi-dimensional protection mechanism of host boundary protection, active defense, and document protection to perform ransomware protection, and can effectively prevent the blackmailing of ransomware without updating the virus database.
4. Terminal Asset Visibility Management
Based on the user’s network topology and organizational relationship, IEP can generate a 3D visual management interface for the entire network terminal, which can display information such as terminal asset information, security status, and threat posture of the entire network. It also supports management personnel to perform related operations.
5. All-terminal scene adaptation
IEP is ideally suited to various types of user terminals, including office terminals, server terminals, virtualized terminals, special-purpose equipment terminals (such as financial terminals or industrial control equipment, etc.) and mobile terminals, and provides a full-scene terminal security solution.
IEP has a good adaptability to the localization system and hardware. It supports 32/64-bit domestically-acquired operating systems such as NeoKylin, NATIONAL FUNDAMENTAL SOFTWARE OF CHINA, and Kylin. It also supports localized hardware such as Loongson and Feiteng.
Customer Value
1. Easy management and reduced costs
Cross-platform integration and centralized management reduces implementation, management, and maintenance costs. Only one management center can realize the multi-platform viruses such as PC terminal, server, virtual cloud terminal, dedicated terminal, and mobile terminal, such as unified virus detection and killing, uniform vulnerability recovery, unified virus database update, and APT traceability.
2. Improved capacity and established system
Strong virus killing and multiple protection functions, enhance terminal protection capabilities, and build an effective protection system. The leading localization engine helps to accurately identify and quickly handle security threats, avoid false killings, and protect functions such as vulnerability repair, anti-ransomware, and unknown threat protection, and build a secure and effective protection system for terminals.
Intuitive runtime screenshots and intermediate file feedback
Intercepting the key state of screen status diagram, at the same time, extracting and storing files downloaded and released during operation, providing accurate and vivid picture and document basis with high values.
3. Full awareness and fast response
It can carry out real-time awareness of the status of the entire network terminal, improving the speed of response to security incidents, and effectively clearing security threats in a timely manner. It can perform real-time awareness of terminal asset information and terminal security posture of the entire network in all domains. When a security event occurs, rapid response can be achieved through traceability of the entire network, fixed-point killing, and other means.
Typical Scene
IEP supports Internet, isolation network, virtualization and other application scenarios and can be applied to various network environments in the industries such as enterprises, education, finance, energy, government affairs, military industry, and public security.
IEP can meet the deployment requirements in different application scenarios. The supported deployment modes include single management center deployment, multi-level management center deployment, and virtual hierarchy deployment mode. In different application scenarios, IEP supports the unified management of physical terminals and virtualized terminals by the management center.
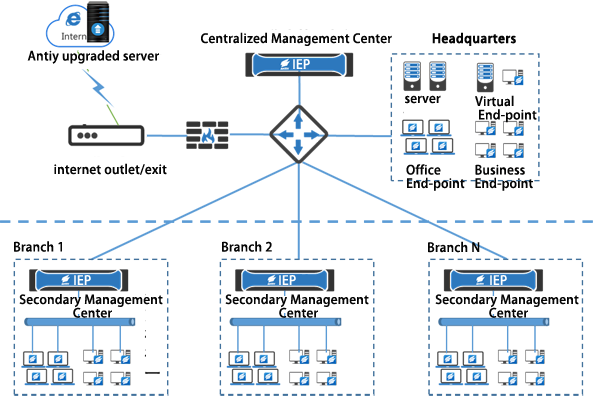
Hierarchical Management Center Deployment Diagram
The above figure shows a typical hierarchical deployment diagram. A centralized management center is deployed at the headquarters and a secondary management center is deployed at the branch offices. Each management center manages terminals in the region, and the secondary management center reports terminal security data to the primary management center and obtains security data from the primary management center.
