Antiy Persistent Threat Analysis System (PTA-mobile)

Introduction
Multi-environment threat identification, multi-dimensional indicator correlation
With the rapid increase in the number of applications on smart mobile terminal devices, the number of malicious applications has also increased. With the deepening of the complexity of mobile applications, and the continuous improvement of professional requirements for security supervision and risk auditing of mobile applications, efficient and accurate analysis and authentication of mobile applications has become an urgent need for a large number of users. In this context, Antiy Persistent Threat Analysis System (PTA-mobile) came into being.
The PTA (mobile) system was independently developed by Antiy, aiming to perform fine-grained, scene-based dynamic behavior analysis on applications under the Android platform, to maximize the performance and recording of the behavior of the tested application. Through dynamic behavior analysis technology, it can effectively solve the technical difficulties encountered in static analysis such as confusion and reinforcement; at the same time, it can effectively monitor and record the actual behavior of mobile applications, providing the most direct aid for determination of behavioral intentions and corresponding forensic work.
Function & Value
PTA (mobile) can provide professional assistance for various users:
1. Mobile application security supervision analysis and auditing engineers can use PTA (mobile) to automate the in-depth behavior analysis of the Android platform application and provide strong support for security supervision and auditing.
2. The security functional departments and scientific research institutions can use PTA (mobile) to perform malicious determinations on Android applications and to collect and trace the clues of malicious applications.
3. Security analysts, operators, security departments, application developers, and other security professionals can use PTA (mobile) to perform in-depth analysis of Android applications.
4. PTA (mobile) can cooperate with other products such as a secure terminal protection system, a network virus monitoring system, and an Android application static analysis system to realize comprehensive security defense.
Advantages
Great behavior monitoring
Fine-grained monitoring and application of various dynamic behaviors, and in-depth detection of application runtime, such as power lifting, encryption and decryption, interface calls and other complex behaviors, generating detailed and easy-to-read log records.
Comprehensive network monitoring capabilities
Real-time network monitoring and network data analysis capture key network activities and record operational data, making it easier and faster to trace online threat behaviors.
Intuitive runtime screenshots and intermediate file feedback
Intercepting the key state of screen status diagram, at the same time, extracting and storing files downloaded and released during operation, providing accurate and vivid picture and document basis with high values.
Original scenario analysis
The in-depth scenario analysis of various original attack scenarios, such as CC, blackmail, privacy disclosure, and power escalation has exposed the malicious application intent.
Static analysis plug-in integration support
The malicious application static analysis module participates in the entire process, and provides a strong support for the analysis and determination of malicious applications using a sophisticated static threat knowledge base.
Complete operating environment simulation capabilities
Investigate environmental factors for targeted simulations when applications running and restore the runtime environment to maximize application activity trigger rates.
Product Form
-Server:
The server configuration is deployed as an independent mobile application in-depth analysis system with high-volume processing capabilities.
-Mobile:
The portable form is equipped with real mobile equipment as a culture carrier, as a rapid analysis system.
Applied Scenario
1.Android applied depth behavior analysis
For customers: safety regulators and security industry practitioners.
PTA (mobile) is a professional Android application dynamic analysis system, using sandbox technology, through dynamic breeding, to maximize the behavior of the measured application intentions.
PTA (mobile) can record more than 200 detailed dynamic behaviors under the 26 categories of actions including call, text message, network, database, address book, and media operation when the application is running, combined with the network data captured at runtime, and the application of intermediate files. The system creates original scene-based behavior information to generate in-depth dynamic analysis reports, providing professional support for in-depth dynamic analysis.
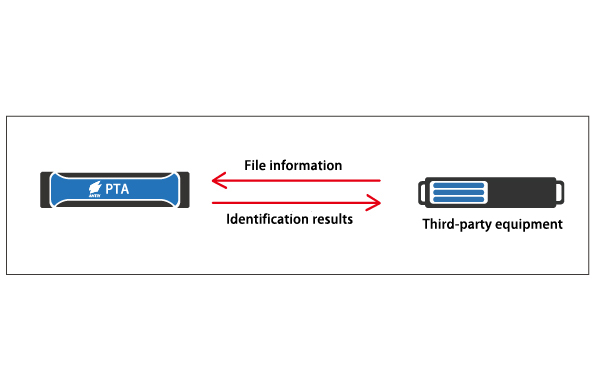
2.Android applied network communication feature association traceability
For customers: safety regulators, security vendors, government and corporate customers.
When PTA (mobile) analyzes the Android application, it will monitor and record the URL, IP, SMS, email, and FTP data in the running process, and combine the unique scene detection to capture the run-time data. Classified under different scene tags. While mass-detecting Android apps’ intentions of behavior, users can gradually form a CC control domain intelligence system on the Internet to facilitate the traceability of mobile network attacks.
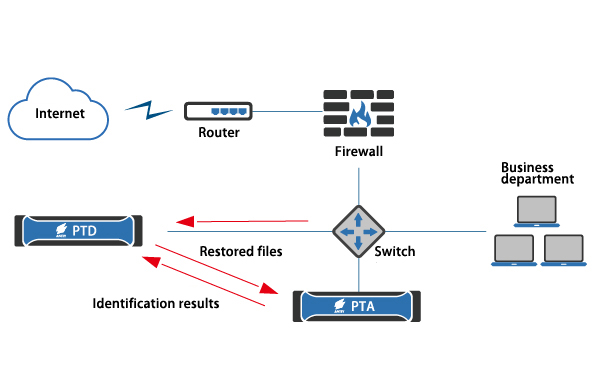
3.Analysis of traffic monitoring equipment linkage
For customers: safety regulators, government and corporate customers.
By bypassing the network mirroring data, PTD can monitor the virus epidemic in the mobile network environment in real time, malicious code file transfer in the mobile network, malicious software network behavior, and user’s access to malicious addresses.
Through linkage, PTA (mobile) can perform in-depth analysis of malicious files captured by PTD, helping users establish a complete and efficient network security protection system.
PTA (mobile) provides an open collaborative service interface so that it can be linked with products such as the Antiy Persistent Threat Detection System.