Persistent Threat Analysis System (PTA)

Introduction
Multi-environment threat identification, multi-dimensional indicator correlation
Persistent Threat Analysis System (PTA for short) is an in-depth threat identification device independently developed by Antiy Labs that can perform in-depth security analysis on objects such as format documents and executable files, effectively detecting various types of known and unknown threats. PTA is a professional anti-APT product designed for organizations such as governments, enterprises, who require deep identification and analysis capabilities. With AVL SDK built-in, combined with massive virus database and whitelist database, PTA can realize high-accuracy detection to known threats and mark the whitelist objects. Relying on Antiy’s 17 years of professional antivirus experience and several years’ of APT incident analysis, PTA has stronger detection and analysis capabilities for advanced threats, and is significantly superior to ordinary sandbox products that rely only on dynamic monitoring or open source systems in terms of detection accuracy, detection capability and detection speed.
Features
1. Isolate network files for check
When external files needed to be copied to internal network, they can be put into PTA for identification for security concerns.
2. Advanced threat incident tracing
When a new APT incident occurs, users can query whether the APT incident’s signatures exist in the current PTA data to verify the security of the network.
Combined with Persistent Threat Analysis System (PTA for short), it can improve users’ capability to discover unknown vulnerabilities, unknown malicious programs, as well as C&C commands and channels of remote Trojans.
3. Analysis and determination of malicious code samples
After the discovered virus samples are put into PTA, the analysis report output can provide powerful analysis support data for the security analysis team.
4. Email attachment security check
PTA can check the mail contents and attachments received and sent by the mail server. The mail server administrator can formulate a flexible management and control strategy on the server side based on its identification results, to contain the spread of malicious behaviors from the source of the mail.
Advantages
Comprehensive threat behavior revealing, intelligence output supports effective defense
1. Fast and efficient large-volume file analysis capabilities
With AVL SDK built-in, combined with massive virus database and whitelist database, adopting a combination of dynamic and static malicious code detection technology and intelligent decision-making mechanism, PTA can quickly and efficiently analyze large batches of files. Supported file sources include: bulk uploading tool in PTA Web interface, self-owned secure devices and third-party security products.
2. Dynamic and static identification combination, multi-vectors extraction, effectively revealing malicious programs and 0day attacks
PTA adopts a dynamic and static combination identification method. With its unique intelligent learning function, PTA can perform in-depth security analysis on documents such as format documents, executable files and URLs, effectively detecting known threats and unknown threats. Meanwhile, PTA has a rich variety of vectors extraction capabilities. In the initial analysis phase when the file has not been put into the sandbox, PTA can complete the extraction of a variety of vectors only through static analysis; can accurately find the format document overflows, 0day vulnerabilities and other attacks through dynamic in-depth analysis.
3. Provides a variety of operating system and application software combinations to support the construction of user-specific detection capabilities
In addition to Windows and Linux systems and common application software, PTA is the first dynamic analysis product that supports China-developed Kylin operating system environmental sandbox and office software WPS. PTA can combine specific operating system and software based on user requirements to build an analysis environment that is more in line with the user’s actual scenarios, giving the user unique threat detection capabilities, more effectively defend targeted attacks.
Application Scenarios
1. Link with other Antiy products to form a complete security solution identification result
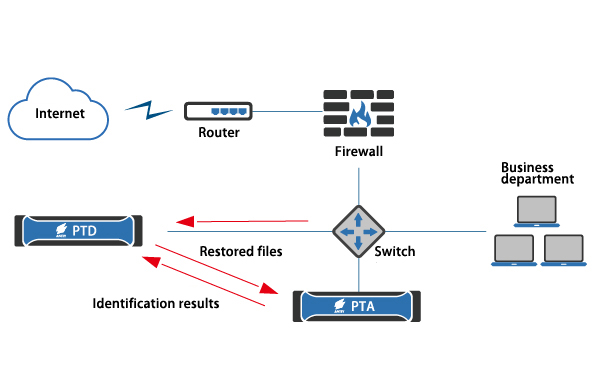
PTA and PTD Linkage Diagram
PTD can restore network traffic to files, and determine the security of the files. Combined with PTA’s in-depth identification capability, PTD can accurately demonstrate the network security situation and provide administrators with an understanding of the network security situation, helping them make security warnings and take security measures.
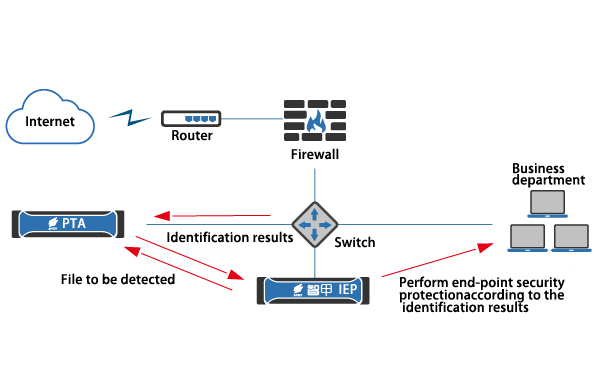
PTA and IEP Linkage Diagram
Intelligent Endpoint Protection (IEP for short) can provide security protection for all endpoints (hosts, PCs, etc.) in the network. In combination with the PTA’s in-depth identification capability, IEP can discover threats more quickly and accurately and dispose them according to the configuration.
2. Standalone deployment
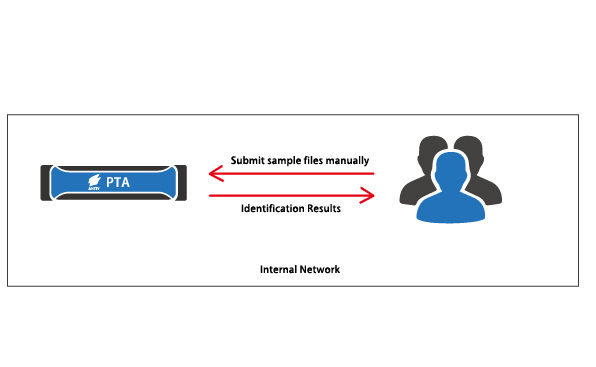
PTA Standalone Deployment Diagram
PTA can be deployed separately into the user’s internal network. Users submit files manually or using a batch upload tool via its Web interface. Then, PTA identify the files in depth and output the identification results. The identification results can be used for analysis and research of unknown samples, analysis of known virus samples, etc.
3. Interactive with third-party products to enhance third-party product safety appraisal capabilities
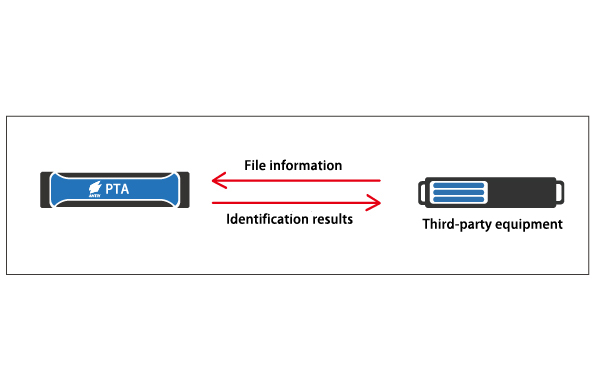
PTA and third-party device linkage diagram
Associated with the firewall: Provides file security attributes for third-party firewalls to help firewalls effectively block internal and external threats;
Associated with the FTP server: identification of files uploaded to the FTP server can be performed. The user can process the files according to the authentication result.
Associated with IPS: Enhances the threat identification capability of IPS products;
Associated with OA system: identify and analyze documents, identify documents based on identification results, and facilitate management of documents;
File storage server: Performs identification analysis on files on the server and manages files according to the identification results. Users use third-party products and Antiy PTA through the use of standard API interfaces. The third-party product will put the files into the Antiy PTA for identification.
