High-level Threat Intelligence Service
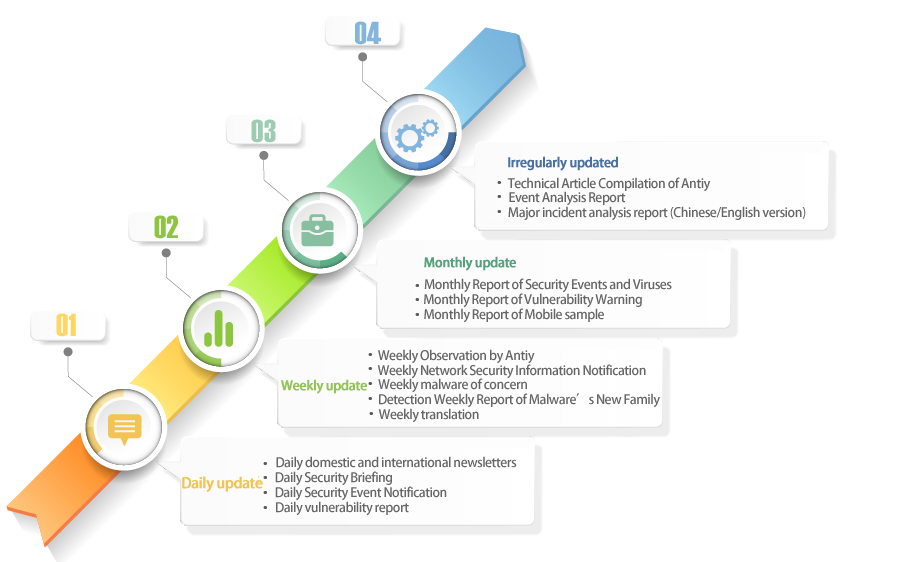
Introduction
Antiy High-level Threat Intelligence Service mainly provides decision-making and reference for information security authorities and functional departments of government agencies, industry customers, universities and research institutes and etc., including Antiy’s exclusive in-depth analysis report, exclusive technical translation, regular security information and notifications and etc., and offers a unique annual plan sharing mode and locking mode.
The service mainly relies on the materials generated by the threat intelligence analysis engineers through collecting, collating and studying. The High-level Threat Intelligence Service carries Antiy-related high-level threat reports, analysis, and translations. In addition, we also incorporate some public information currently formed by the network security situation at home and abroad in this scope.
Threat intelligence can provide solid evidence and detailed analysis of new attackers and threats. Such information can guide companies to make better planning and investment decisions on security to improve their security situation, while at the same time reducing unnecessary risks and expenses. In addition, threat intelligence can analyze certain threats that are not relevant to a particular industry or type of business, and help companies avoid placing limited resources in the wrong place.
The threat intelligence service of Antiy provides users with a better understanding of domestic and international security trends, major security incident analysis and solutions, and helps avoiding their potential risks. In the face of threats and challenges, Antiy is a capacity-based security vendor with system vision and solutions. Based on the independent innovation, the core technology products and services of threat detection and defense promote effective integration of active defense, threat intelligence, architecture security, and passive defense. It is committed to providing an unpredictable security capability that is difficult for attackers to bypass, achieving effective protection, highly automated and operational security business value.
