Persistent Threat Detection System (PTD)

Introduction
Full-traffic real-time detection, full-element traceability
Persistent Threat Detection System (PTD for short) is a network threat detection device independently developed by Antiy Labs. PTD enables full-traffic, high-precision and real-time threat capture and detection through out-of-path deployment, to locate threat sources and monitor various attack behaviors; improves the capability to detect and trace targeted attacks and advanced threats through full-element and fine-grained records of metadata, vulnerability data, asset information, security incidents, running status, audit logs, threat intelligence and other information, to achieve continuous detection of potential threats and unknown threats. Under the current situation where high-value assets are increasingly attacked, PTD focuses on protection of critical information infrastructure and important IT assets, integrates network traffic capture detection, file restoration and file analysis, enabling users to continuously collect, discover and respond to threats in a timely manner.
Features
1. Multi-dimensional traffic capture and monitoring
PTD supports full-traffic detection from multiple levels such as packets, flows, sessions, files, protocol metadata, network behaviors, file behaviors, etc. At the same time, information such as threat reputation, threat names and core behaviors can be obtained. Multi-level detections can ensure the acquired data are more abundant, the detection contents are more varied and the methods are more diversified. PTD can monitor the scan and detection activities before the attack, and the C&C channels established for websites and mailboxes. Combined with the situation analysis technology, it can improve the rapid defense deployment and threat locating capabilities of high-value targets within the network.
2. Unknown threat monitoring and discovery
PTD can detect more than 8 million kinds of viruses, Trojans, worms and other malicious code, as well as a variety of network attacks, and accurately provide virus types, names, variant versions, risk levels, capabilities and other related information, to help users get the most accurate detection results.
Combined with Persistent Threat Analysis System (PTA for short), it can improve users’ capability to discover unknown vulnerabilities, unknown malicious programs, as well as C&C commands and channels of remote Trojans.
3. Traceability and forensic analysis
PTD uses unique threat tracking technology to continuously track known and unknown advanced threats. By providing threat tracking packages on a regular basis, it helps users control threats within the network in real time and detect advanced threats in advance, to defend advanced threats. Threat tracking is conducted for specific threat incidents and can assist relevant departments in emergency forensics and other work.
Advantages
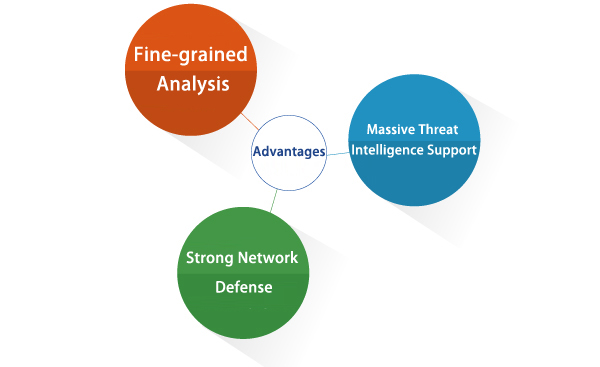
1. Flow-traffic full-element collection, fine-grained analysis
PTD performs protocol analysis and content restoration for the data in the network traffic, and collects network metadata such as IPs, domain names, URLs, files and accounts information in the process.
PTD can perform simulation execution and vectors extraction for executable payloads, to obtain the behavior characteristics of the payloads. Rich data can support key threat revealing and situation tracking.
2. Tagged filtering and custom detection, to build network defense capabilities that can’t be foreseen by attackers.
PTD tags network incidents, and various tags are combined to create an incident scenario. The detection rules are then refined according to the scenario, and the threat was finally detected through specific detection rules. PTD tailors detection rules based on the characteristics of the user’s network infrastructure, enabling each user to build its own unique threat monitoring strategies based on its business characteristics and application scenarios, and in conjunction with its in-depth scenario association analysis capabilities, to provide users with network defense capabilities that can’t be foreseen by attackers.
3. Autonomous threat detection engine, massive threat intelligence support
Relying on Antiy’s 17 years of professional antivirus experience and capability accumulation, based on Antiy’s self-developed AVL SDK antivirus engine, PTD can filter a large number of known malicious programs. AVL SDK can detect network data flows, URLs, host files, etc. As a fast network virus detection engine, AVL SDK can use the local virus database with 30 million high-quality virus signatures built in, and detect more than 8 million virus samples. Relying on a powerful virus database, PTD can directly identify known threats. It can not only significantly increase the recognition rate, but also can significantly reduce the detection noise of dynamic analysis, thus making the system more focused on analyzing unknown advanced threats.
Application Scenarios
1. Internet deployment
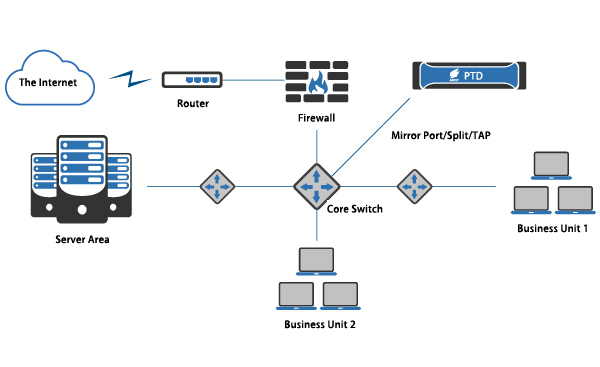
Figure 1 Screenshot of running egdata.a
PTD can be connected to the mirroring port of the core switch of the user’s network, to detect traffic in and out of the user’s network in real time.
2. Intranet deployment
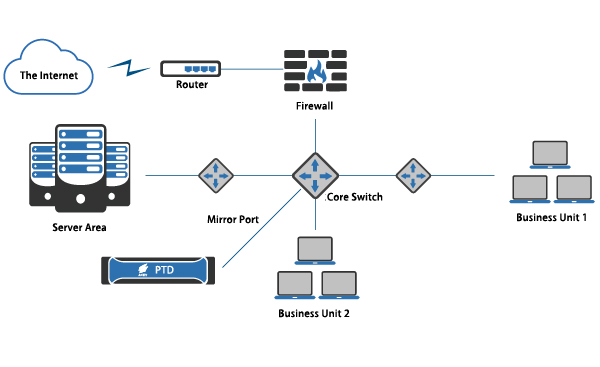
PTD Intranet Deployment Diagram
PTD can be flexibly deployed at the mirroring port of any switch in the intranet. It can detect specific service content, to detect the lateral movement of the virus in the network and locate the source of the threat.
3. Distributed deployment
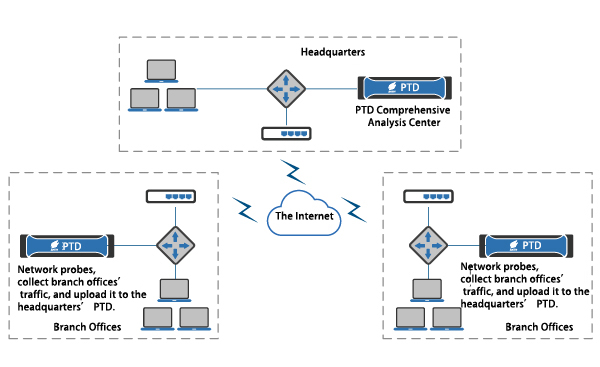
PTD Distributed Deployment Diagram
PTD supports multi-level distributed deployment, which is applicable to scenarios in which multiple branches and centers uniformly present detection data.
4. Linkage deployment
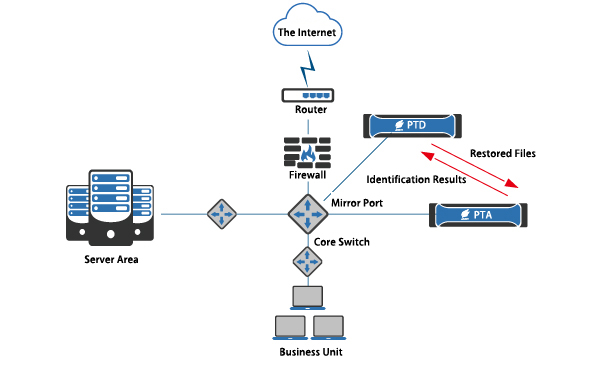
PTD Linkage Deployment Diagram
PTD can be linked with PTA. Using PTA’s excellent file analysis and identification capabilities, it presents the network security situation more accurately.
