Analysis of phishing attacks by “X Elephant” group against scientific research institutions in china
1.Overview
Recently, Antiy CERT (Security Research and Emergency Response Center) discovered during daily email monitoring that overseas APT attack organizations imitated the official organization of our “慧眼行动” and sent phishing emails to relevant scientific research institutions and dropped Trojan horses in the form of attachments. to carry out subsequent attacks. The email contains a compressed package attachment, and the compressed package contains a constructed executable file. This file is based on three disguise methods: file name, icon and bundling with normal files, to simulate a reporting client for related activities. After opening the executable file, it will connect to the attacker’s server to download the subsequent attack payload, and finally establish a pipeline SHELL between the victim machine and the attacker’s C2 server through the backdoor to achieve remote control.
Antiy CERT has basically confirmed that the relevant attacks originated from a country in South Asia. However, there is currently insufficient information to determine whether they are related to the known threat actors with the same national background that Antiy has named , but it is not yet possible. It is completely determined that it is a new attack organization. According to Antiy’s naming rules for threat actors, ” X Elephant” is temporarily used as its name. We will continue to monitor, track and analyze the attacker’s subsequent attack activities, and will be included in the attribution conditions. As it matures, revise its organizational designation.
2.Attack activity analysis
2.1 Attack process analysis
The attacker sends a spear phishing email to the target by impersonating the identity of the official organization of “慧眼行动”. The attacker tricks the recipient into running an initial lure program disguised as declaration client software in the email attachment. This program is the first stage. The downloader, on the one hand, downloads and runs the legitimate “慧眼行动” official software and displays it to the attack target, and on the other hand, downloads and runs the second-stage downloader. After the second stage downloader is executed, it will decrypt a link address, download and run the final backdoor program. The function of the backdoor program is relatively simple. It mainly creates a SHELL channel with the C2 server to achieve remote access to the victim machine. Sample The delivery and execution process is shown in Figure 2-1 .
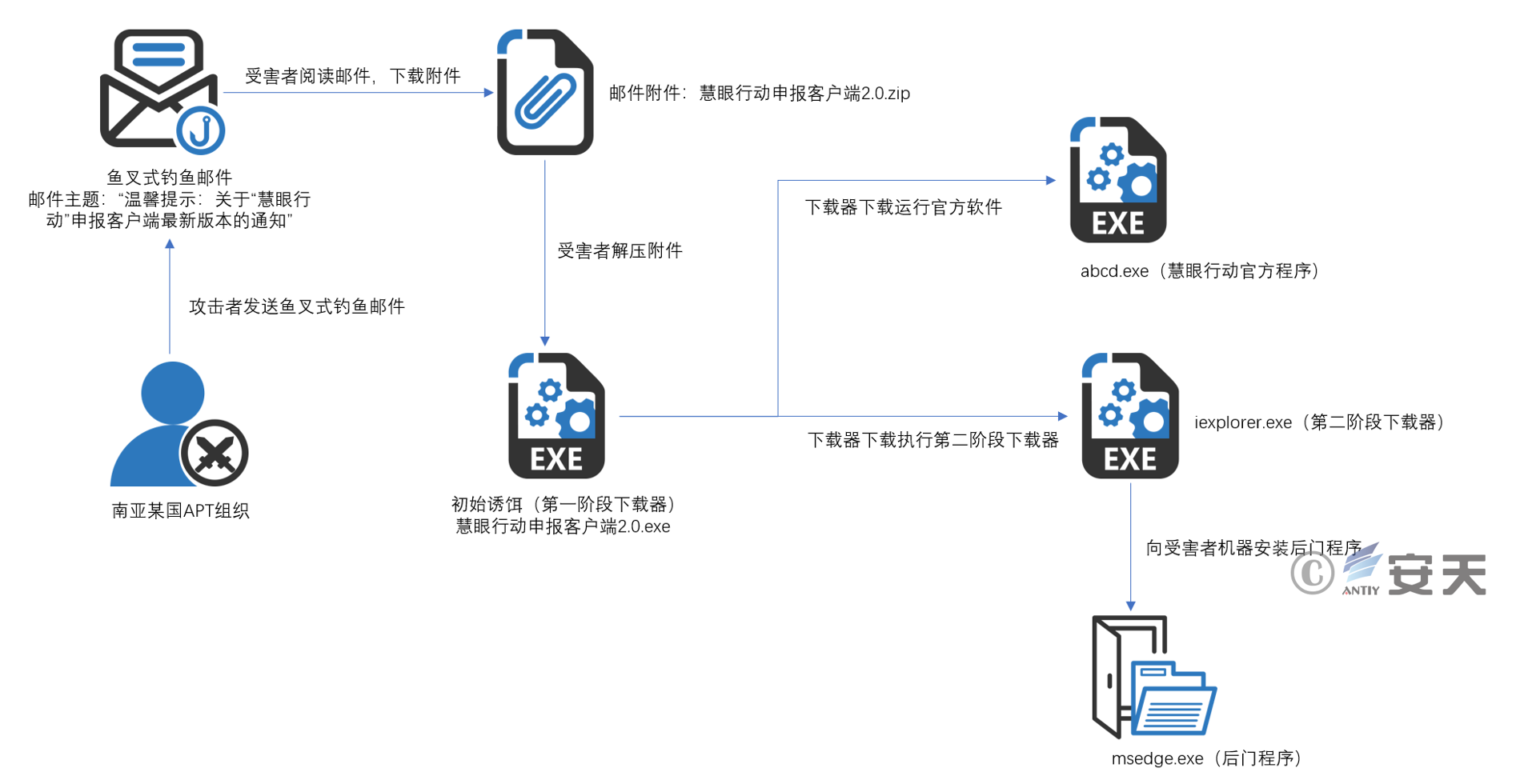
Figure 2-1 Sample delivery and execution flow chart
2.2 Spear fishing email analysis
The attack email is shown in Figure 2-2 . The sending email address is info@ * . The domain name was registered one day before the attack email was sent.
The subject of the attack email is “Warm reminder: Notification about the latest version of the “慧眼行动” application client”, and the email uses the title “Dear Teacher”, which is in line with Chinese naming conventions. The body of the email is specifically structured to induce the recipient to open the executable file in the installation attachment in the name of “recent reports of heavy traffic and frequent failures on the client. The old version has been discontinued.” At the same time, there are obvious errors in the expression of relevant content, which does not conform to Chinese expression habits. It is suspected that someone in the attack team has a Chinese learning background and is not proficient in Chinese, or the content is generated based on the attacker’s native language or English and the use of machine translation after constructing the content. The email attachment is a compressed package named “慧眼行动申报客户端2.0 “. The compressed package is in ZIP compression format. After decompression, it is an exe executable program with the same name, which is a downloader for delivering malicious Trojans.
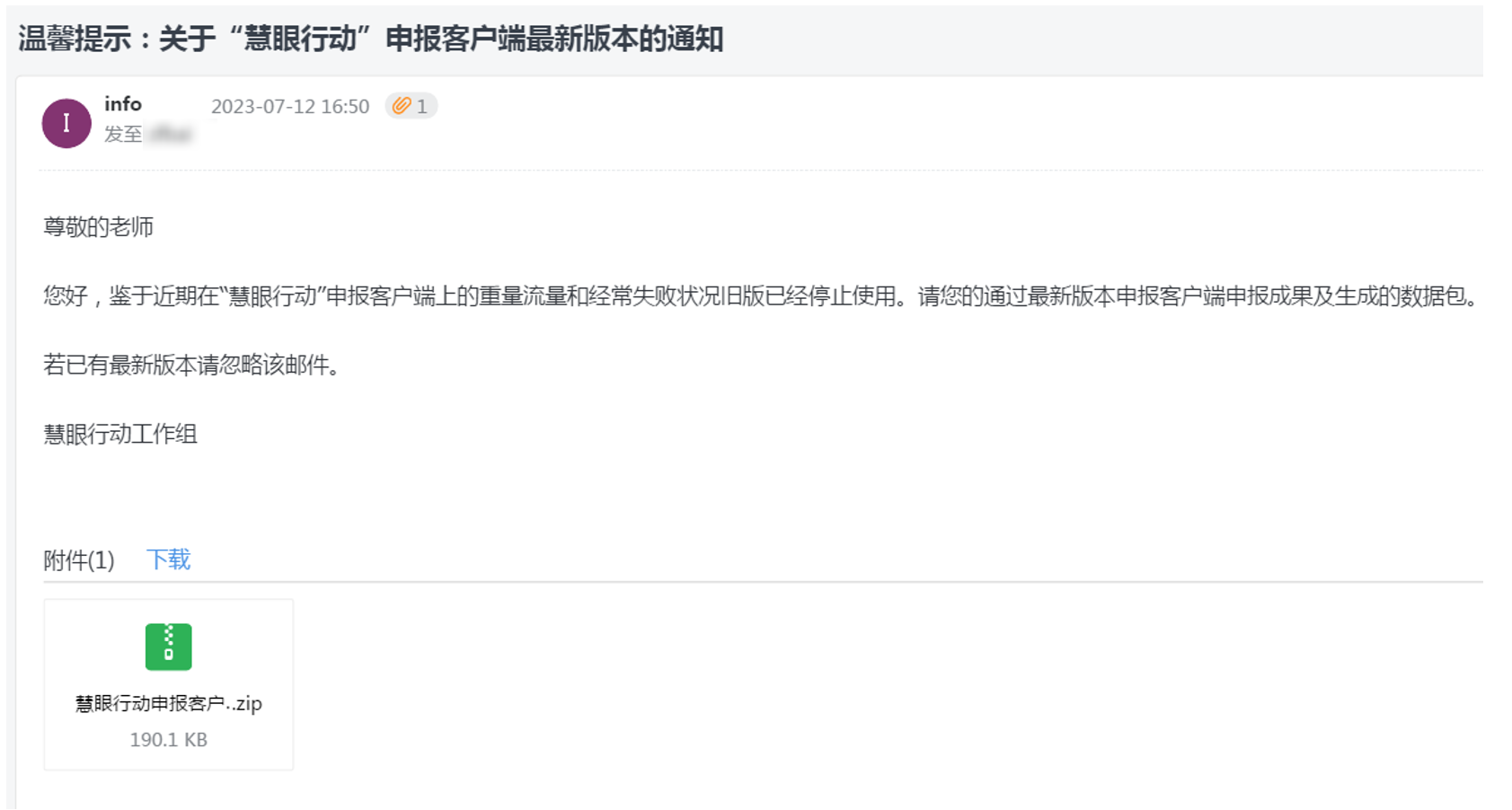
Figure 2-2 Content of phishing email
2.3 Initial lure file analysis
surface twenty one sample label
|
Virus |
Trojan[Downloader]/Win64.Agent |
|
original |
慧眼行动申报客户端2.0.exe |
|
Processor |
x86-64 |
|
File |
301 KB (308,224 |
|
file |
BinExecute/Microsoft.EXE[:X64] |
|
Timestamp |
2023-07-12 12:45:09 |
|
digital signature |
none |
|
Packing type |
none |
|
compiled language |
C/C++ |
The attack payload function is a Trojan downloader. This sample uses obfuscation to hide the C2 address in meaningless strings, as shown below. The two meaningless strings are obfuscated C2 addresses. The sample enters a specific Parameters (58h and 57h in the figure below), the real C2 address is parsed through the sub_140001FB0 function.
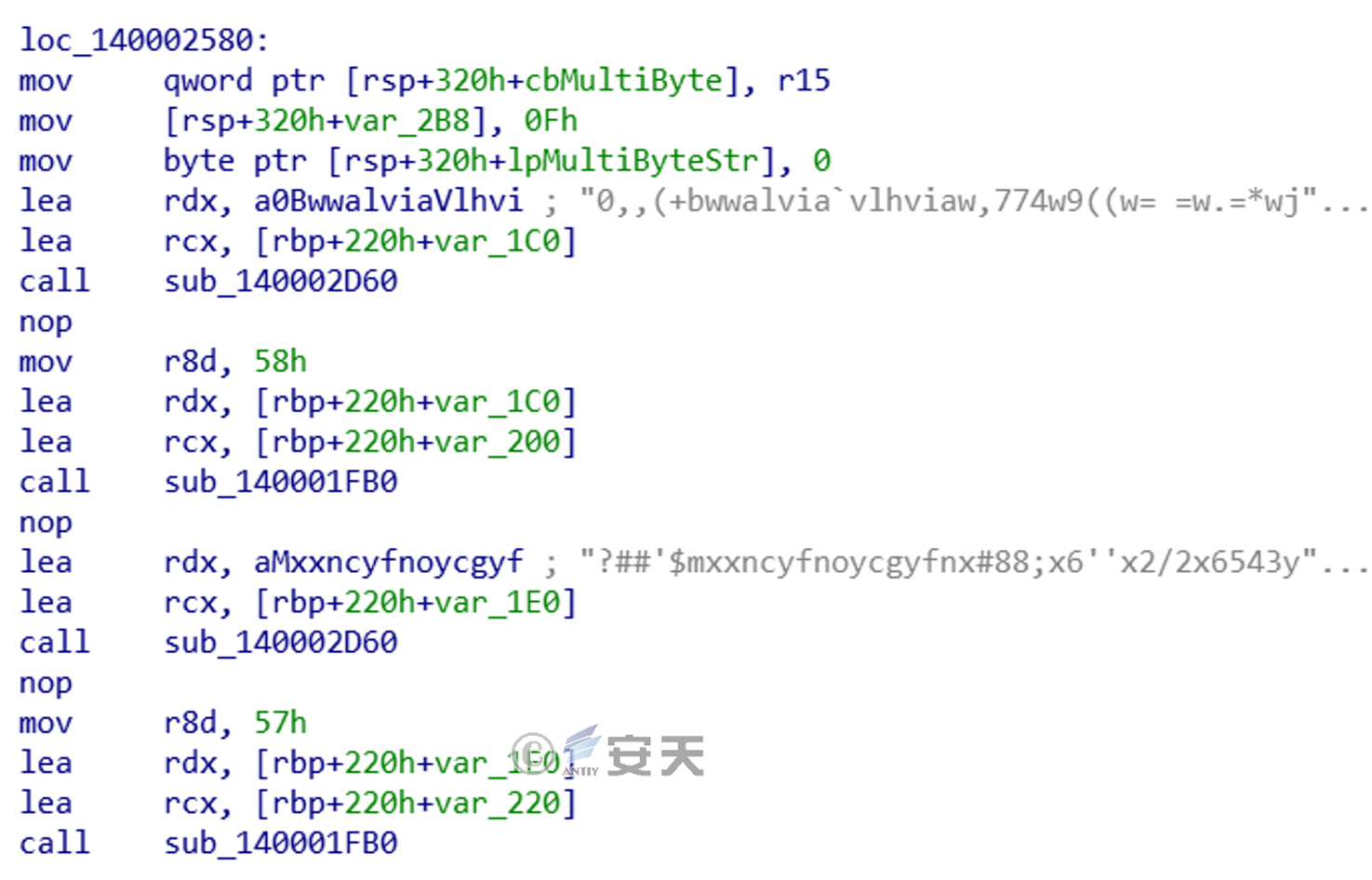
Figure 2-3 Obfuscated C2 string
The sub_1400001FB0 function gradually parses out the C2 address by using the input parameters (58h and 57h) to perform XOR, as shown below:
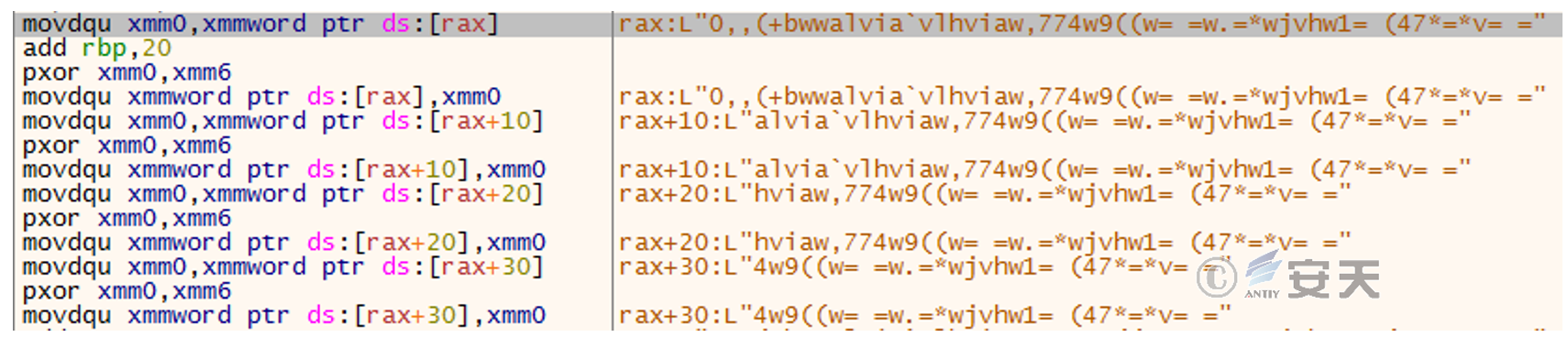
Figure 2-4 Initial obfuscated string
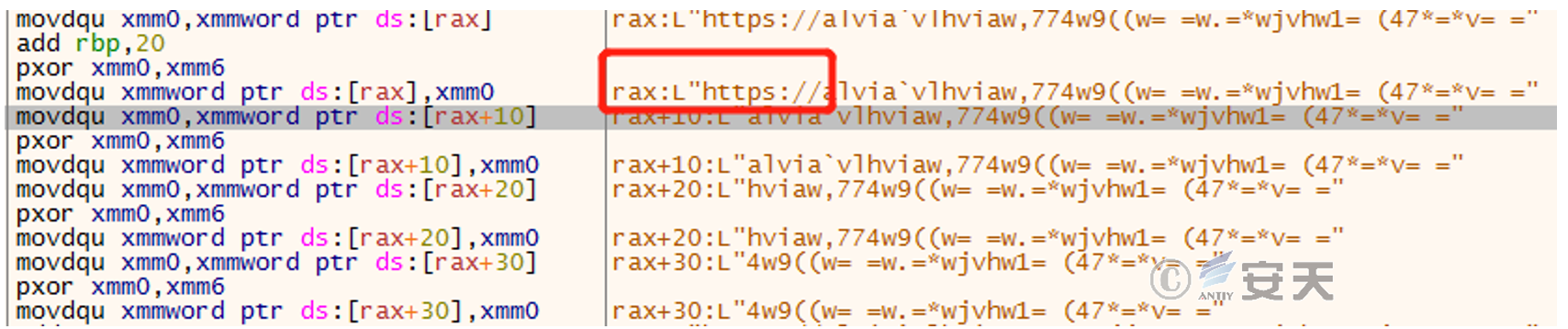
picture 2-5 String after first XOR
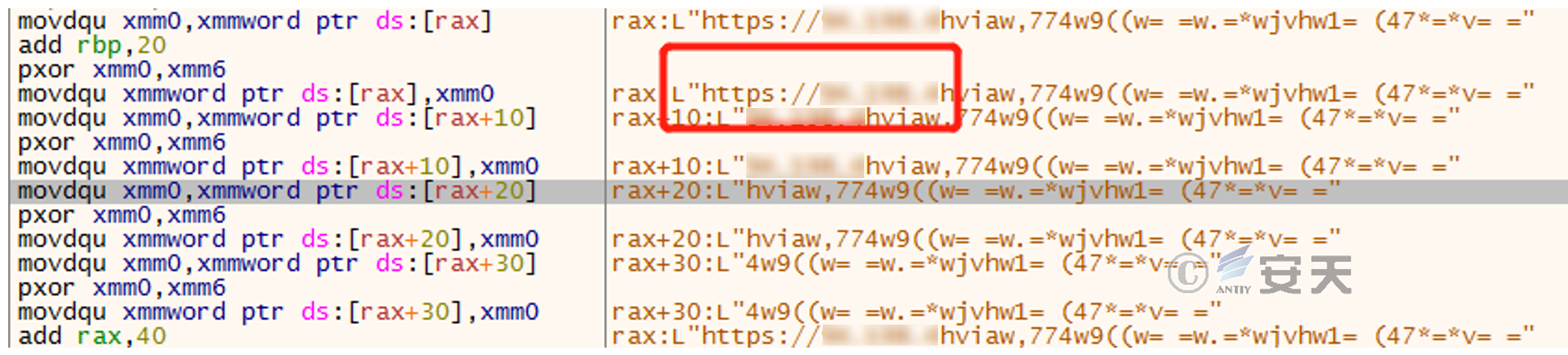
Figure 2-6 String after second XOR
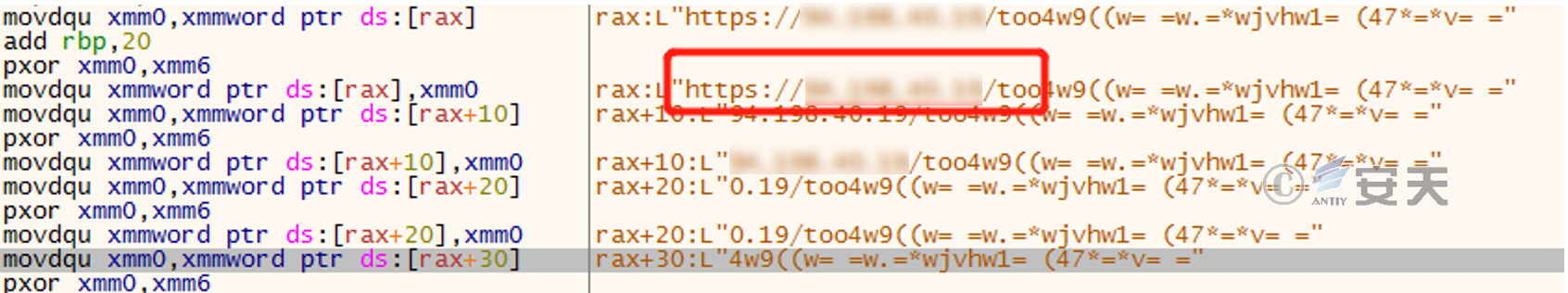
Figure 2-7 String after third XOR
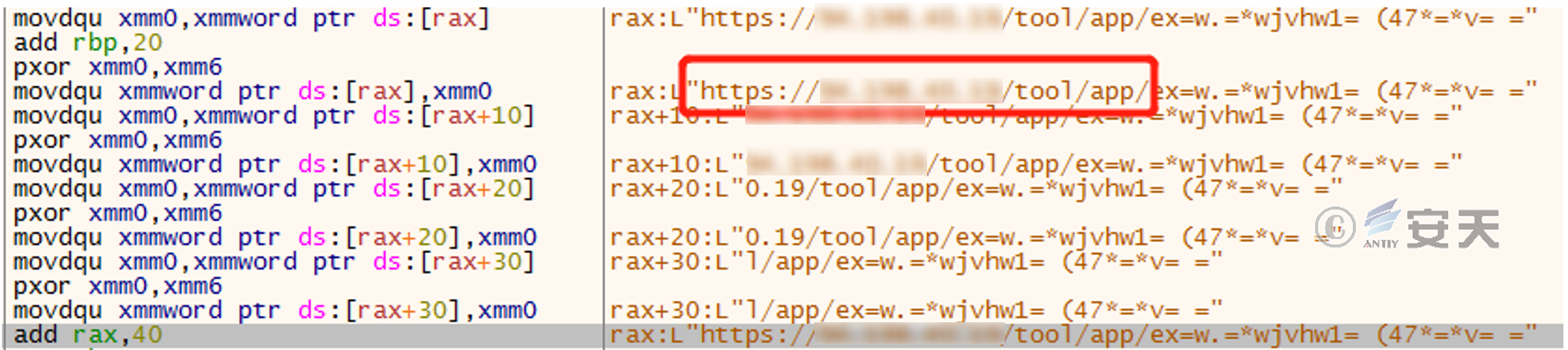
Figure 2-8 String after the fourth XOR
For other obfuscated strings, XOR is performed character by character in a loop, as shown in Figure 2-7 below.
Figure 2-9 XOR character by character
Finally, the obfuscated string is parsed into the complete download address https://94.198. * . * /tool/app/exe/ver/2.0/iexplorer.exe. In the same way, another obfuscated string is parsed and the second download address https://94.198. * . * /tool/app/exe/abcd.exe is obtained.
the malicious code in the C2 is downloaded to the user directory of the local host by calling the URLDownloadToFileW API.
2.4 Normal program analysis
This sample is the official software of “慧眼行动” and is a normal software downloaded by attackers to confuse victims.
Figure 2-10 Official software installation guide
2.5 Downloader analysis
surface twenty two sample label
|
Virus |
Trojan[Downloader]/Win64.Agent |
|
original |
iexplorer.exe |
|
Processor |
x86-64 |
|
File |
107 |
|
file |
BinExecute/Microsoft.EXE[:X64] |
|
Timestamp |
2023-07-11 15:50:02 |
|
digital signature |
none |
|
Packing type |
none |
|
compiled language |
C/C++ |
This sample has similar functions to the 2.3 sample . It also uses obfuscation to hide the C2 address in a meaningless string. By cyclically subtracting the string by 2 in units of characters, the inversion of the download address is finally obtained. Through this download The address downloads the malicious code msedges.exe to the temporary file directory of the local host.
2.6 Backdoor analysis
This sample is downloaded from the C2 server through the iexplorer.exe downloader. Its actual function is to design a simple rebound SHELL backdoor program.
surface twenty three sample label
|
Virus |
Trojan[Backdoor]/Win64.AGeneric |
|
original |
msedges.exe |
|
Processor |
x86-64 |
|
File |
1.29 |
|
file |
BinExecute |
|
Timestamp |
2023-07-11 15:04:37 |
|
digital signature |
none |
|
Packing type |
none |
|
compiled language |
C/C++ |
|
VT first upload time |
2023-07-17 08:14:40 |
|
VT test results |
11 / 69 |
The connection address of the backdoor is 4 6.249. *.* and the port is 4 43 .
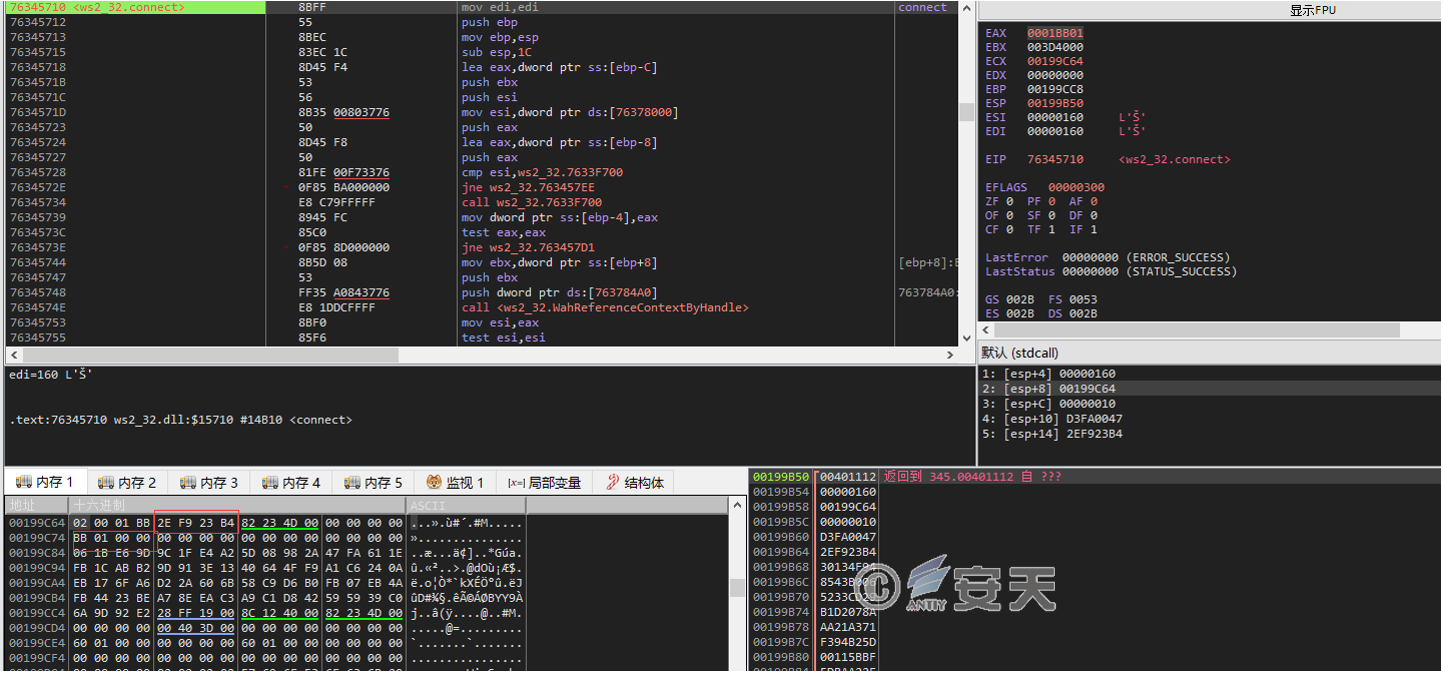
Figure 2-11 Connect to C2 server
C2 ‘s response data to the backdoor is in the form of “control code + data”. The data can be a path or command, etc. The control instructions are as follows:
a). When the control code is 0, C 2 response is followed by “command”, and ” cmd /c command” is executed through the created pipeline
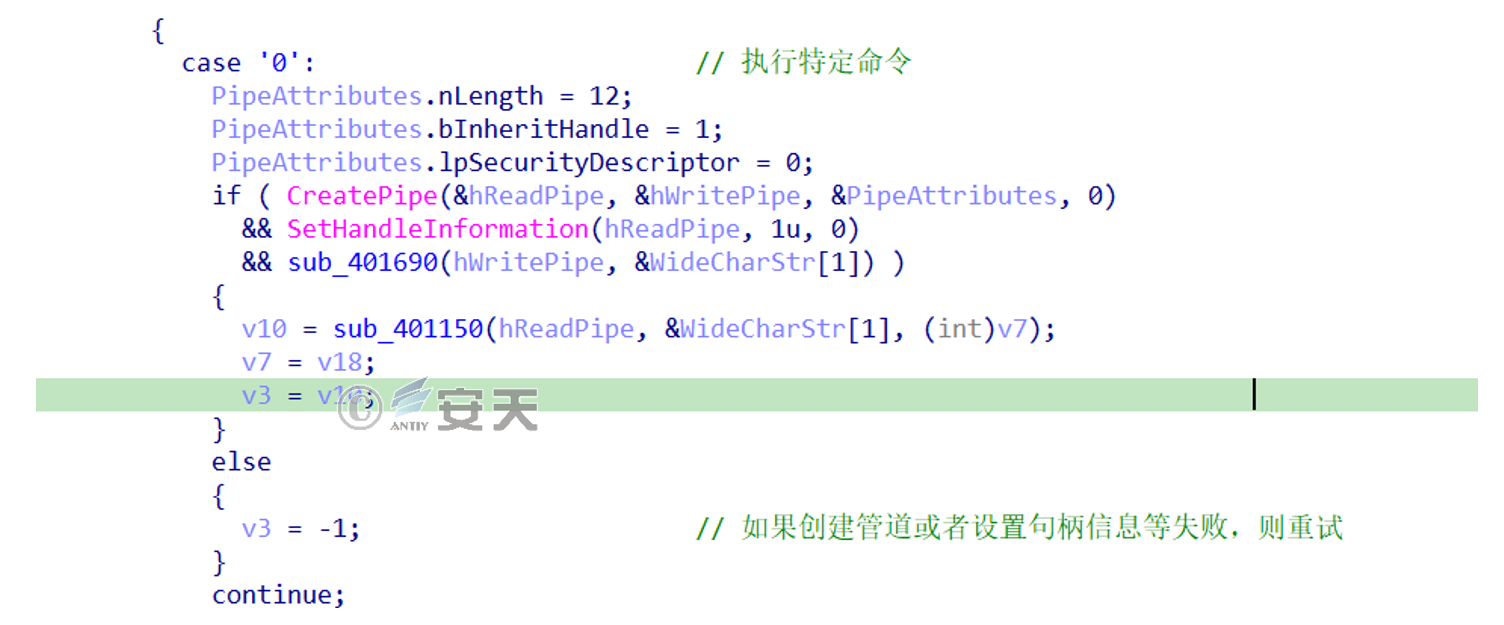
Figure 2-12 control code is 0
b ). When the control code is 1, it is followed by the path, which is used to switch the working directory.
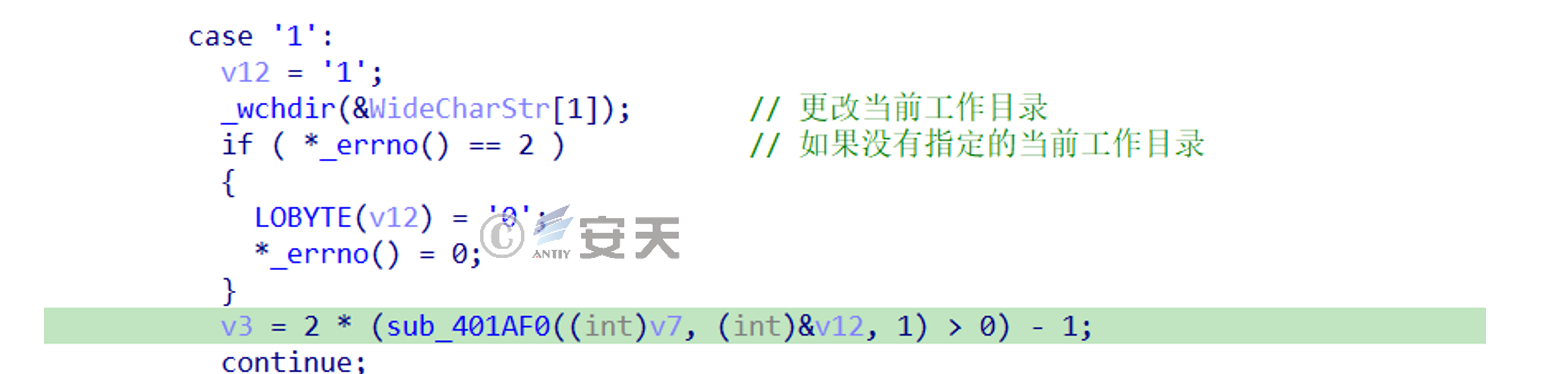
Figure 2-13 The control code is 1
c ).When the control code is 2, clean up the traces and exit the process
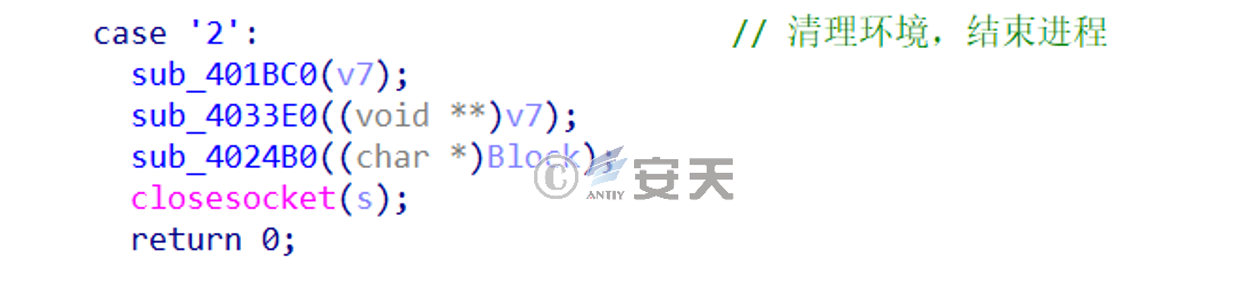
Figure 2-14 The control code is 2
d ). When the control code is 5 , clean up the traces and wait 10 seconds to restart the above process.

Figure 2-15 The control code is 5
e ). When the control code is 6, wait for 5 seconds and restart the above process without cleaning the traces.

Figure 2-16 The control code is 6
3.Attack purpose analysis
“慧眼行动” is a collection activity for scientific research results in my country. According to the official website: “慧眼行动” is based on extensive scanning of local universities, institutes affiliated with the Chinese Academy of Sciences, private enterprises, local state-owned enterprises, provincial/municipal scientific research institutions, industry scientific research institutions, as well as national laboratories, national key laboratories, and local innovation alliances. We will use the collective innovation forces of the whole society to discover and select public innovation achievements with major equipment application prospects or technological leadership, and support special actions for rapid transformation and application in the equipment field.
Based on the analysis of the attack process and the relevant information they counterfeited, it can be seen that the attackers target universities, scientific research institutes, innovative enterprises, scientific research institutions, etc. in my country, and try to achieve remote control of the computers of relevant scientific researchers through social engineering disguises, trying to steal relevant information. Scientific research information results, and other related activities. Once the recipient is deceived into executing it, or mistakenly clicks on it to execute the relevant Trojan. The computer host will be completely controlled by the attacker. The attacker can not only obtain all files on the host and related account credentials and other information. It will also use the corresponding host and identity as a springboard to conduct lateral movement and trust chain attacks, which can bring serious security threats.
4.Attack mapping from a ATT&CK framework perspective
This series of attack activities involves a total of 10 technical points in 8 stages of the ATT&CK framework . The specific behavior is described in the following table:
surface 4-1 Technical behavior description table of this attack activity
|
ATT&CK stage |
specific |
Comment |
|
reconnaissance |
Collect victim identity |
Collect victim’s online |
|
Collect victim |
Collect information about |
|
|
resource |
Get infrastructure |
Build load distribution |
|
Capability development |
R&D and production of |
|
|
initial access |
Phishing |
Attackers deliver Trojans |
|
implement |
Inducing users to execute |
The initial lure is |
|
defense evasion |
Counterfeit |
Attack components imitate |
|
command and |
Use standard |
The backdoor program sets |
|
data exfiltration |
Use C2 channel backhaul |
An attacker may send data |
|
Influence |
Manipulate data |
An attacker may manipulate |
Mapping the threat behavior technology points involved to the ATT&CK framework is as shown in the figure below:
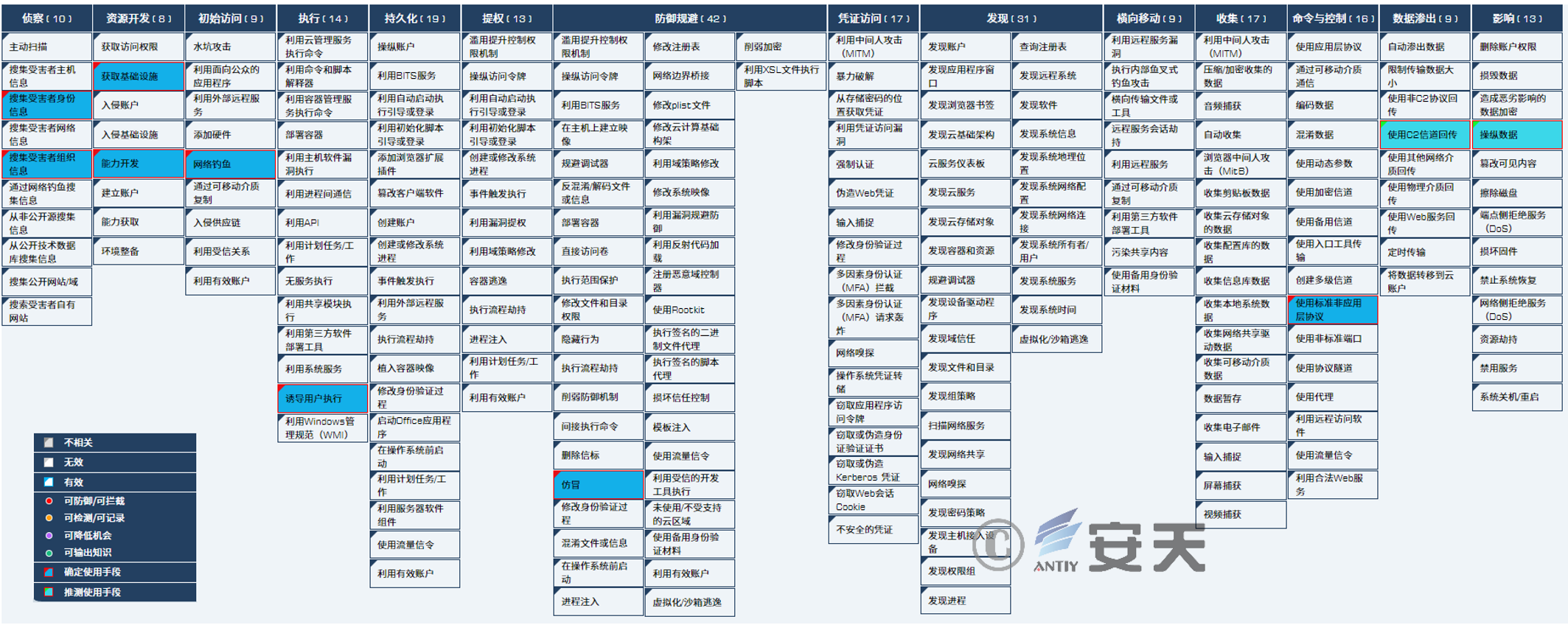
Figure 4-1 This attack corresponds to the ATT&CK map
5.Protection recommendations
In the past two years, overseas APT attack organizations have imitated relevant ministries and commissions in China, and phishing activities have occurred frequently. Attackers may use the communication and distribution of literature reports, project declarations, and honorary qualification applications as materials to send phishing emails through carefully constructed and imitated subject emails. Use the fake phishing website link included in the email body to steal the target email account; deliver malicious code through attachments, etc., in an attempt to control the target host or steal sensitive information within the host. This type of phishing email attack method does not seem to have higher technical capabilities, but it is actually extremely harmful. Firstly, its implementation cost is extremely low and easy to implement. Secondly, it does not need to penetrate the target network boundary and in-depth protection. It only needs to construct relevant emails to reach the target person’s terminal directly. Third, it can be put into large-scale batches.
Faced with such precise counterfeit phishing email attacks, we need to take precise measures:
5.1 Security suggestions for government, enterprise, and scientific research institutes
1. The ultimate target of phishing email attacks is the users of endpoint systems, which are the last line of defense against threats. It is recommended to use endpoint security protection software with strong virus scanning and killing capabilities, active defense capabilities and phishing attack detection and interception capabilities, such as Antiy Smart A Terminal Defense System.
2. Key personnel, especially those who frequently use emails for external communication and interaction, are recommended to increase the protection level and use a whitelist protection strategy based on terminal protection software. All new executable files are reported to the management center for storage, and can only be run based on the review and confirmation of network administrators. The white-defense function of terminal protection software should provide a configuration strategy based on a combination of signature certificates, file hashes , file paths, etc., to ensure the creation of a trusted environment while detecting the trusted operation capabilities of the network management.
3. It is recommended that government and enterprise institutions register independent ” . cn ” domain names and assign work mailboxes to all staff. It is not recommended that government and enterprise institutions use free Internet mailboxes to host work connection activities.
4. For medium and large institutions and sensitive institutions, it is recommended to deploy email services based on a safe and reliable enterprise email system, strengthen relevant server security policies, monitoring strategies, and email threat linkage detection mechanisms, and aggregate email-related system logs and corresponding monitoring logs into Antiy XDR and other management platforms perform unified monitoring.
5. For government and enterprise institutions that use Internet public cloud mailbox services, network managers also need to monitor relevant security events and aggregate exportable security logs to Antiy XDR and other management platforms.
6. Set up traffic monitoring links on the corporate intranet and Internet exits, such as Antiy Tanhai NDR products, to continuously monitor and respond to phishing email placement, phishing link clicks, and C2 connections after Trojans are implanted .
5.2 Safety suggestions for organizers of relevant scientific research and academic activities
1. Use the institution’s domain name mailbox to make relevant work contacts, use the official website domain name to publish relevant reporting portals, provide reporting software downloads, and do a good job in protecting the security of the corresponding website itself.
2. Website access and file downloads use the HTTPS encryption protocol to avoid access hijacking and bundled delivery.
3. Put forward clear requirements for its own suppliers, such as related clients, installation packages and binary programs, etc., and require security protection of the signing environment to avoid certificate theft, so as to ensure that the relevant software is identifiable and traceable to facilitate its own security protection The software adds policy rules.
4. Provide safety reminders to those who may participate in related activities, and clarify elements such as work website, work mailbox, official website download address, and program signature information. Security rules such as explicitly not sending binary files directly in attachments.
5.3 Security recommendations for system end users
1. Install endpoint security protection software provided by the unit / or selected by the individual with strong virus killing capabilities, active defense capabilities, and phishing attack detection and interception capabilities .
2. When receiving relevant emails, check whether the sender’s email address is consistent with the relevant organization. For emails from untrusted domains, measures will be taken such that attachments are not opened, links are not clicked, and QR codes are not scanned .
3. Adjust system-related configuration policies, such as choosing to display known format extensions, to prevent attackers from using software icons such as documents and pictures to trick attackers into clicking on executable files.
Since the prevention and management of phishing attacks involves a large number of security elements, it is difficult to provide all security suggestions in one analysis report. If you need anti-phishing solutions or related products and training services, please contact Antiy.
