Analysis of LockBit Ransomware Samples and Considerations for Defense Against Targeted Ransomware
1.Overview
Recently, there has been an incident involving a financial institution falling victim to a ransomware attack. Information from various sources indicates a close association with the LockBit ransomware attack group. The use of the term “close association” by the Antiy CERT is qualitative due to LockBit operating as an attack organization based on the “Ransomware as a Service” (RaaS) model. They establish the infrastructure supporting ransom attacks, including the development and release of ransom attack malicious code payloads, provision of customized builders, creation of a unified ransom attack interface, and establishment of virtual currency payment channels. This enables various attack organizations and individuals to conduct operations by leveraging their “services.” In RaaS, the organization providing the service and the entities carrying out the attacks are typically not the same organization or individuals. They may even operate back-to-back. Moreover, payments are often conducted using encrypted digital currencies such as Bitcoin, adding significant complexity to comprehensive tracing and analysis of the event.
LockBit was named the most active ransomware attack group globally in 2022. It develops ransomware targeting various host systems and platforms, including Windows, Linux, macOS, and VMware virtualization. The ransomware generator allows for easy customization through simple interactions. LockBit encrypts only the first 4K data of the file header, resulting in a significantly faster encryption speed compared to other ransomware that encrypts the entire file. Due to the overwrite of sectors corresponding to the original file, victims cannot recover plaintext data before encryption through data recovery methods. The organization was first identified in September 2019, initially known as the ABCD ransomware due to the .abcd file extension on encrypted files. In June 2021, LockBit released version 2.0, introducing features to delete volume shadow and log files. It also launched the exclusive data stealing tool, StealBit, adopting a dual extortion strategy of threatening to expose (sell) enterprise data and encrypting data. In August 2021, the group’s attack infrastructure expanded to support DDoS attacks. In June 2022, the ransomware was updated to version 3.0, and due to code overlap with BlackMatter ransomware, it is also referred to as LockBit Black. This reflects potential personnel movement and capability exchange between different ransomware groups. Several organizations using LockBit RaaS have carried out numerous attack operations. They invade victim systems through third-party credential acquisition, weaponizing vulnerabilities, and deploying other malicious software. After infiltrating, they deploy ransomware, leading to a large number of victims facing ransom demands and data leaks. LockBit has become the most active ransomware attack group, even engaging in proactive spreading and PR activities.
2.Typical Cybersecurity Incidents in Recent Years
Attackers utilizing the LockBit ransomware organization’s RaaS services primarily gain initial access to victim systems through third-party credential acquisition, weaponizing vulnerabilities, and deploying other malicious software. After stealing data files, they deploy the LockBit ransomware to achieve encryption. The organization has a considerable number of affiliated members, and its Tor website sees almost daily additions of victim information from around the world. Since adopting the dual extortion strategy of “threatening to expose enterprise data + encrypting data for ransom,” the Tor website has published information on over 2,200 victim enterprises. As of 2023, more than 900 victim enterprise records have been released. If affiliated members and victim enterprises negotiate privately, their information is not disclosed on the Tor site, indicating that the actual number of victim enterprises may surpass the publicly disclosed figure.
Table 2.1: List of Typical Incidents Encountering LockBit Ransomware Attacks”
|
Date |
Victim unit |
Influence |
|
August 2021 |
Irish IT consultancy Accenture |
Stealed approximately 6 TB of data and demanded a ransom of $50 |
|
January |
French |
Part of the data was made public; in |
|
February 2022 |
Bridgestone Americas Branch |
The company |
|
June |
US |
Some data was stolen |
|
July 2022 |
French telecom operator La Poste Mobile |
As a result, |
|
October |
Bank |
Some data was stolen and a ransom of 50 |
|
November 2022 |
Continental |
Stealed about 40 |
|
December |
California |
Approximately 76 GB of data stolen |
|
January 2023 |
Royal Mail |
International |
|
June |
TSMC |
Some data was stolen and a ransom of $70 |
|
August 2023 |
Montreal Electric Service Commission, Canada |
Approximately 44 |
|
October |
Boeing |
Approximately 43 GB of data stolen |
3.Overview of Attack Organizations and Corresponding Attack Situations
Table 3.1: Basic Information of LockBit Attack Organization
|
Organization Name: |
LockBit |
|
Former Name |
ABCD |
|
Appearance Time |
September 2019 |
|
Typical Breach Methods |
Apart from phishing attacks, third-party credential acquisition, |
|
Typical Encryption Suffix |
9-digit individual ID composed of random |
|
Decryption Tools |
No publicly available decryption tools discovered as of now |
|
Targeted Systems for |
Windows, Linux, macOS, VMware, etc. |
|
Operational Mode |
Ransomware as a service, based on ransom payment and data sales |
|
Modes of Intrusion |
Encryption-induced paralysis, data theft, |
|
Commonly Targeted Industries |
Finance, services, construction, education, IT, manufacturing |
|
Common Countries/Regions |
United States, United Kingdom, Germany, |
|
Multiple Ransom Combinations |
Yes |
|
Ransom Letter Sample |
|
4.Typical Tactics, Techniques, and Procedures (TTPs) in the Historical Linked Cyber Attack Activities
Organizations leveraging the LockBit RaaS infrastructure for ransomware attacks involve a considerable number of personnel with diverse operational styles, and many incidents lack detailed disclosure. Analyzing the entire attack lifecycle, including entry points, intrusion methods, lateral movement, and paths for stealing critical assets, is challenging due to limited information. We have compiled a list of common tactics and techniques based on the clues currently available and annotated them using the ATT&CK framework.
Figure 4.1: Common Tactical Behavior Patterns in LockBit-Related Ransomware Attacks
The corresponding list is as follows:
Table 4.1: Common Tactical Behavior List in LockBit-Related Ransomware Attacks
|
ATT&CK Stage |
Specific Behavior |
Notes |
|
Initial access |
Watering Hole Attack |
Implanting malicious code in websites frequently visited by the |
|
Exploitation of Public-Facing Applications |
Exploiting vulnerabilities to access the victim’s system, such as |
|
|
Exploitation of External Remote Services |
Exploiting RDP to access the victim’s network |
|
|
Phishing |
Using phishing and spear-phishing to access the victim’s network |
|
|
Use of Valid Accounts |
Obtaining and abusing credentials of existing accounts as a means |
|
|
Implement |
Using commands and script interpreters to execute malicious |
Deploying with batch scripts |
|
Using third-party software deployment tools |
Deploying with the Chocolatey command-line package manager |
|
|
Utilizing system services |
Executing commands or payloads using PsExec |
|
|
Persistence
|
Perform boot or login using autostart |
Enable automatic execution for persistence |
|
Valid account |
Use compromised user accounts to maintain persistence on target |
|
|
Elevate privileges
|
Abuse of elevated control mechanisms |
Use ucmDccwCOM method in UACMe to bypass UAC |
|
Perform boot or login using autostart |
Enable automatic login for privilege escalation |
|
|
Modify using domain policy |
Create group policies for lateral movement and the ability to force |
|
|
Use a valid account |
Escalating privileges using compromised user accounts |
|
|
Defense evasion
|
Execution scope protection |
Entering the correct parameters will decrypt the main component or |
|
Weaken defense mechanisms |
Use tools such as PCHunter, PowerTool, and Process Hacker to |
|
|
Delete beacon |
Clear Windows event log files, ransomware self-deletes |
|
|
Obfuscated files or information |
Encrypted data will be sent to its command and control (C2) |
|
|
Credential access
|
Brute force cracking |
Use VPN or RDP brute force to achieve initial access |
|
Get the credentials from where the password is stored |
Use PasswordFox to get the password of Firefox browser |
|
|
Operating system credential dump |
Use ExtPassword or LostMyPassword for obtaining operating system |
|
|
Discover
|
Scan network services |
Scan target network using SoftPerfect |
|
Discover system information |
Enumerate system information including hostname, host |
|
|
Discover system location |
Computers whose language settings match the defined exclusion list |
|
|
Lateral movement |
Utilize remote services |
Move laterally across the network and access domain controllers |
|
Collect |
Compress/encrypt collected data |
Use 7-zip to compress or encrypt collected data before stealing it |
|
Command and control
|
Use application layer protocols |
Using FileZilla for C2 Communication |
|
Use standard non-application layer protocols |
Establishing a SOCKS5 or TCP tunnel from the reverse connection |
|
|
Use protocol tunneling |
Use Plink to automate SSH operations on Windows |
|
|
Utilize remote access software |
Remote control using tools such as AnyDesk, Atera RMM or |
|
|
Data exfiltration
|
Automatic exfiltration of data |
Use StealBit custom penetration tools to steal data from target |
|
Using web service postbacks |
Use public file sharing services to steal a target’s data |
|
|
Influence |
corrupted data |
Delete log files and empty recycle bin |
|
Data Encryption That Causes Harmful Impact |
Encrypt data on target systems to disrupt system and network |
|
|
Tampering with visible content |
Change the host system’s wallpaper and icon to LockBit 3.0 |
|
|
Disable system recovery |
Delete shadow copies on disk |
|
|
Disable service |
Terminate specific processes and services |
5.Analysis of LockBit for Windows 3.0 Version Samples
Due to RaaS-supported ransomware attacks being carried out by multiple organizations utilizing a unified attack infrastructure, these organizations rely on their individual attack capabilities and access resources. They employ a common set of foundational code versions, iterating and refining payloads to evade detection. Therefore, RaaS combined with targeted ransomware analysis involves a multifactorial comprehensive examination, particularly focusing on the analysis of attack infrastructure, tactics, and sample attacks separately. LockBit has payloads targeting various common system platforms. In this article, we will first release a historical analysis of its For Windows 3.0 version, followed by the analysis of other samples in subsequent releases.
Table 5.1: Sample Labels
|
Virus family name |
Trojan/Win32.LockBit |
|
MD5 |
38745539B71CF201BB502437F891D799 |
|
Processor architecture |
Intel 386 or later, |
|
File size |
162.00 KB |
|
file format |
BinExecute/Microsoft.EXE[:X86] |
|
Timestamp |
2022-06-27 |
|
digital signature |
none |
|
Packing type |
none |
|
compiled language |
C/C++ |
|
VT first upload time |
2022-07-03 16:18:47 |
|
VT test results |
64/72 |
Note: You can find more information about the LockBit virus family by searching for “LockBit” on the Virusview.net computer virus classification encyclopedia.
After the execution of LockBit 3.0 ransomware, it releases .ico and .bmp files in the %PROGRAMDATA% path. These files are used as icons for subsequently encrypted files and modified desktop wallpaper.
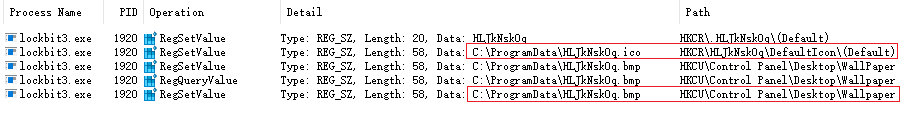
Image 5.1: Additional File Extensions
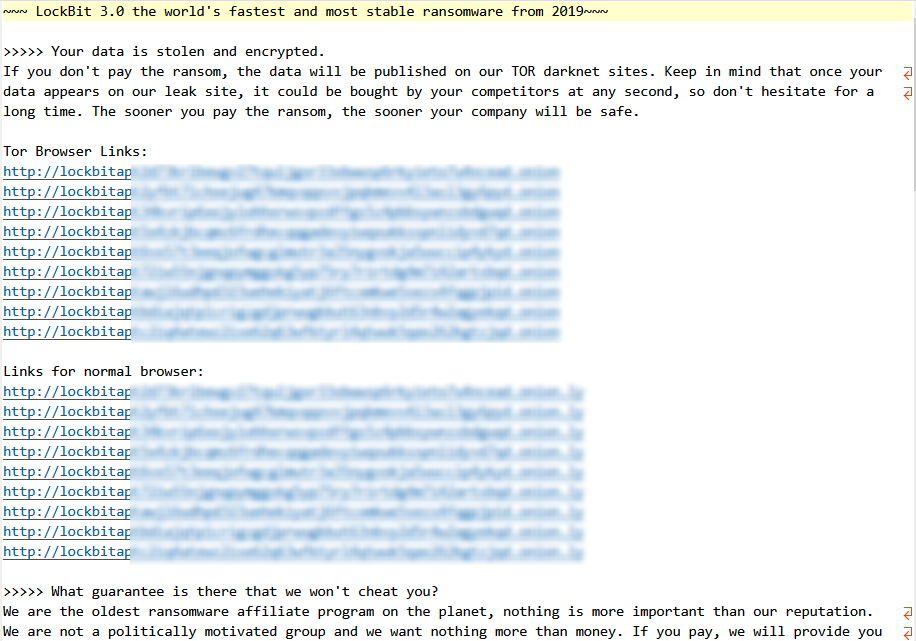
The ransomware releases a ransom note containing a Tor address for ransom communication.
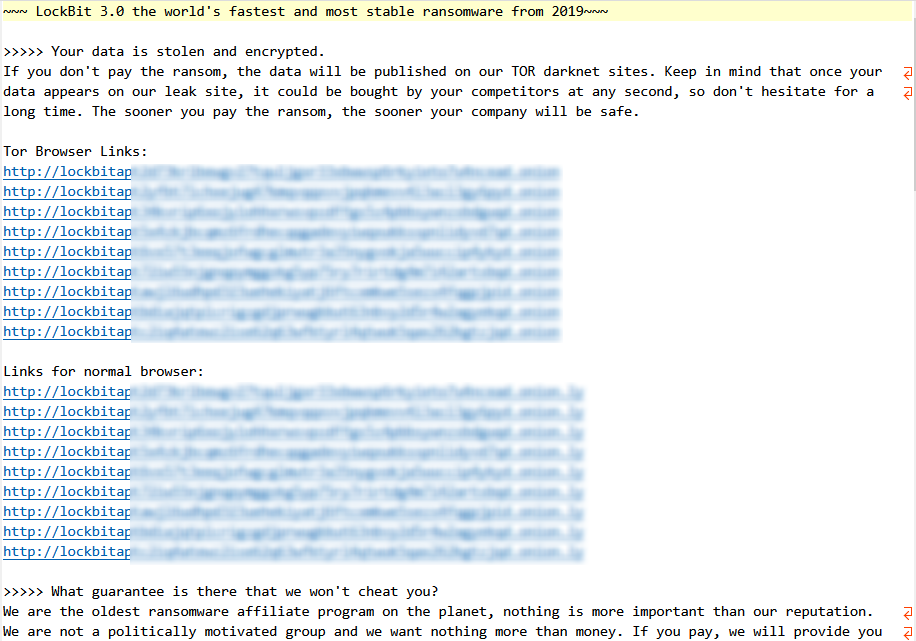
Image 5.2: Ransom Note
The modified desktop background is as shown in the following image.
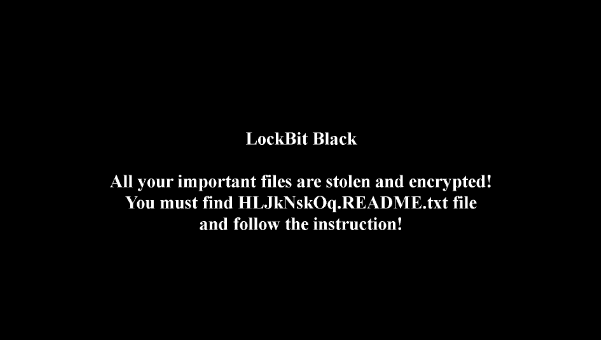
Image 5.3: Modified Desktop Background
LockBit 3.0’s code segment is encrypted, and upon execution, it decrypts based on the provided “-pass” command-line parameter. Without the correct password, execution is not possible. This method is employed to prevent the analysis of the core functionality.
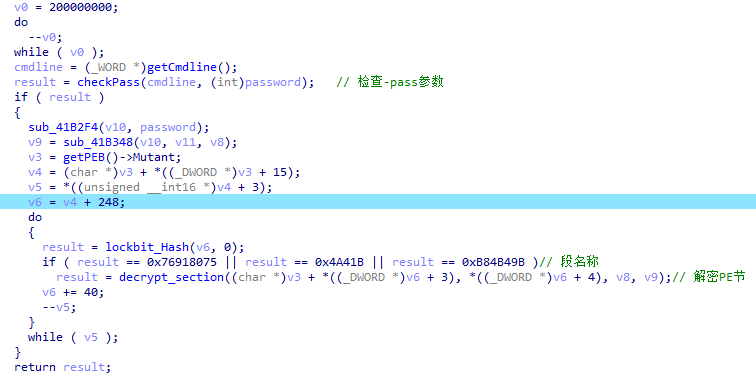
Image 5.4: Decryption of the Code Segment
It uses the NtSetThreadInformation function to set the thread information to ThreadHideFromDebugger, aiming to interfere with analysts and researchers during the analysis process.
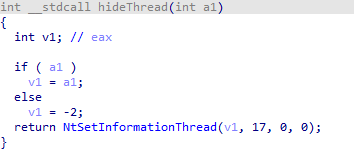
Image 5.5: Code Segment for Analysis Interference
It detects the system language, and if it is a specific language, it exits the program and ceases further execution.
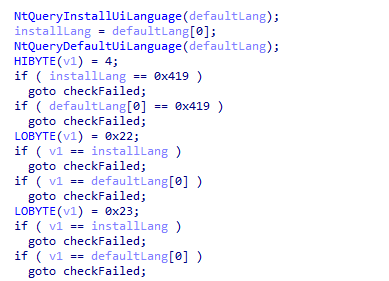
Image 5.6: Language Check
The specific list of checked languages is as follows. By observing the systems it avoids, it’s evident that the LockBit organization itself exhibits strong Eastern European characteristics.
Table 5.2: List of Checked Languages
|
System Language |
Arabic (Syria) |
Russian (Moldova) |
|
Armenian |
Russian (Russia) |
|
|
Azerbaijani (Cyrillic Azerbaijani) |
Tajik (Cyrillic Tajikistan) |
|
|
Azerbaijani |
Turkmenistan |
|
|
Belarusian (Belarus) |
Tatar (Russia) |
|
|
Georgian |
Ukrainian |
|
|
Kazakh (Kazakhstan) |
Uzbek (Cyrillic Uzbekistan) |
|
|
Kyrgyzstan |
Uzbek (Latin |
|
|
Romanian (Moldova) |
|
It creates multiple threads for encryption and sets these threads to be hidden.
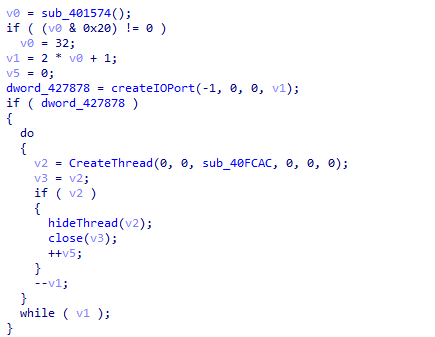
Image 5.7: Create a file encryption thread
6.Targeted Ransomware Attacks: Challenges to Cybersecurity and Considerations for Response
From the perspective of the consequences and losses caused by targeted ransomware attacks, we must alter our perception paradigm regarding the interplay between security risks and value. As targeted ransomware attacks have evolved into a combination of data theft, system and business paralysis, data trafficking, and exposure, the maximal risk is not only the irrecoverable breakdown of systems and business operations. Simultaneously, there is the looming danger of the core assets of the attacked enterprise—user information, critical data, documents, records, code, and more—being sold or exposed, resulting in more significant ripple effects. From a long-term perspective in both domestic and international contexts, a significant proportion of improvements in the security posture of government and enterprise institutions do not stem from proactive measures to enhance defense capabilities. Many enterprises and institutions consider the most probable security risk not to be a direct attack but rather the failure to meet compliance standards, leading to penalties. Consequently, this has established a logic of low-level construction and operation involving investment, compliance, and immunity. The consequences brought about by targeted ransomware attacks force IT decision-makers to assess extreme risks and evaluate the value of cybersecurity work through the lens of potential extreme losses. Avoiding prolonged business interruptions, irrecoverable data loss, the purchase of stolen data assets by competitors, or severe devaluation due to exposure are all extreme situations that IT decision-makers in every organization must address. An objective understanding of the threat scenario is a prerequisite for effective cybersecurity defense. Consequence deduction based on a baseline mindset is also part of this scenario. In terms of budget allocation, we typically use the proportion of cybersecurity spending to overall IT spending as a metric. This often places cybersecurity in a subordinate, auxiliary, or suppressed position within the broader IT landscape. Whether the consequences of cybersecurity risks should be the primary metric for security investment is also a point for consideration.
Looking at the operational mode of targeted ransomware attacks, we must recognize that, before the encryption and paralysis actions are triggered, there is a highly customized operational process similar to APT attacks. Attackers or professional attack teams exhibit a firm intent to attack, high-level capabilities, ample exploit resources, and access to a significant amount of exploitable vulnerability intelligence and attack entry resources. Some attackers may even be insiders. This is the reason why targeted ransomware attacks relying on RaaS can succeed repeatedly, even against large organizations with strong IT operational capabilities and defense investments. Whether serving as the last line of defense in ransomware protection through host system defenses or as the final means of response in backup and recovery, both are single points of failure. They play a partial role in detecting and blocking attacks, reducing the success rate of attacks, increasing the cost of attacks, and lowering the risk of losses within their own capability scope. However, they cannot single-handedly counter systematic attacks. We must seriously point out that equating targeted ransomware attacks to the early indiscriminate spread or widespread deployment of ransomware is a simplistic view. Considering ransomware defense as a straightforward battle between encryption paralysis and backup recovery is a highly outdated and one-sided security perspective. If there isn’t a comprehensive protection system and operational mechanism in place, and relying solely on data backup and recovery to address ransomware attacks is akin to having only one goalkeeper facing an entire opposing team.
From the characteristics of the kill chain in targeted ransomware attacks, we must firmly believe in a systematic approach and practical measures for preventing such attacks. In the face of systematic attacks, it is essential to insist on moving the defense perimeter forward, deploying proactively, creating depth, and establishing a closed-loop operation. Enhancing the ability to detect and intercept attackers’ reconnaissance and activities in the peripheral zones is crucial. This helps reduce the likelihood of attackers reaching the core zones. Improving the manageability of networks and assets is foundational work: actively shaping and reinforcing the security environment, strengthening constraints and management of the attack surface, controlling the upstream entry points in the supply chain, and initiating comprehensive log audit analysis and monitoring operations. Constructing defense in depth from the topological to the systemic side is key. Implementing layered defenses against attacker behaviors such as detection, delivery, vulnerability exploitation, code execution, persistence, and lateral movement is crucial. Special emphasis should be placed on building robust protection on the host and system side, serving as the last line of defense and a fundamental part of the overall defense. Building fine-grained governance capabilities around the identification and control of execution entities is vital. Ultimately, the protection system should achieve real-world operational effectiveness by perceiving, disrupting, blocking, and presenting the kill chain of targeted attacks.
Appendix 1: Partial Efforts by Antiy to Assist Regulatory Authorities, Clients, and the Public in Addressing Ransomware Attacks
ANTIY has consistently been dedicated to enhancing customers’ effective defense capabilities and working collaboratively with them to improve understanding and awareness of security.
ANTIY has been actively monitoring the evolution of ransomware attacks, consistently releasing threat assessment reports. On June 14, 2006, the company intercepted and analyzed the earliest domestic ransomware, redplus (Trojan.Win32.Pluder.a). Subsequently, they published important reports such as “Unveiling the True Face of Ransomware” (2015) [2], “In-Depth Analysis Report on ANTIY’s Response to Ransomworm ‘WannaCry'” [3], “Analysis of the Ransomware Sodinokibi Operation Organization” [4], and “Sample and Follow-up Analysis of Ransomware Attack on a US Fuel Pipeline Company” [5]. Particularly noteworthy is their prediction, made five months before the widespread outbreak of the WannaCry ransomworm, that ransomware attacks would trigger a resurgence of worms [6]. During the WannaCry ransomworm incident, ANTIY swiftly conducted analysis and provided users with protection manuals [7], startup guides [8], as well as immune tools, specialized killing tools, memory key retrieval, and recovery tools. In response to the “PETYA” ransomware disguised as a ransom attack, ANTIY was quick to accurately assess that it might not be a typical ransom attack. ANTIY CERT continuously tracks various ransomware families and RaaS attack organizations. They have released sample analysis reports and protection recommendations for popular ransomware families such as LockBit [9], GandCrab [10], and Sodinokibi. Notably, they launched a special series of articles titled “Understanding Ransom Attacks and Harms from Eight Perspectives” [11][12][13][14][15][16] on their vertical response platform, aiding governmental and enterprise clients, as well as the public, in understanding ransom attacks and enhancing awareness. In 2021, to strengthen prevention and response to ransomware attacks, under the guidance of the Network Security Management Bureau of the Ministry of Industry and Information Technology, the China Academy of Information and Communications Technology, in collaboration with ANTIY and other units, compiled and released the “Ransomware Security Protection Manual” [17]. This manual provides detailed and itemized recommendations on how to prevent ransomware attacks.
ANTIY relies on its independently developed AVL SDK antivirus engine to support its products and the collaborative ecosystem with engine partners in detecting and removing malicious code, including ransomware, with precision. The ANTIY Intelligent Terminal Defense System and the Ruijia Cloud Protection System are based on the fundamental concept of ANTIY’s execution entity governance. They assist clients in shaping a trusted and secure host environment. On the endpoint, ANTIY Intelligent Terminal Defense System establishes a combination of security mechanisms, including system reinforcement, host intrusion prevention system (HIPS), scan filtering, execution control, behavior protection, and focused data protection. These mechanisms create multiple layers of defense against ransomware attacks. The focused data protection mechanism, in particular, is designed to intercept bulk file reads and writes. In cases where other security mechanisms are bypassed and rendered ineffective, it attempts to achieve behavior interception and stop-loss. However, ANTIY does not believe in a one-size-fits-all solution for cybersecurity. The company is committed to ensuring that its engine and each product can maximize their value in their operational positions and undergo real-world testing in confrontations. For more information, you can refer to “ANTIY Products Help Users Effectively Defend Against Ransomware Attacks” [18].
Appendix 2: Reference
[1] “Ransomware attack on China’s biggest bank may have hit US Treasury market” [R/OL]. (2023-11-10), https://www.cnn.com/2023/11/10/investing/icbc-ransomware-attack-hnk-intl/index.html.
[2] ANTIY. “Unveiling the True Face of Ransomware” [R/OL]. (2015-08-03), https://www.antiy.com/response/ransomware.html
[3] ANTIY. “In-Depth Analysis Report on ANTIY’s Response to Ransomworm ‘WannaCry'” [R/OL]. (2017-05-13), https://www.antiy.com/response/wannacry.html
[4] ANTIY. “Analysis of the Ransomware Sodinokibi Operation Organization” [R/OL]. (2019-06-28), https://www.antiy.com/response/20190628.html
[5] ANTIY. “Sample and Follow-up Analysis of Ransomware Attack on a US Fuel Pipeline Company” [R/OL]. (2021-05-11), https://www.antiy.com/response/20210511.html
[6] ANTIY. “Review and Outlook of Network Security Threats in 2016” [R/OL]. (2017-01-06), https://www.antiy.com/response/2016_Antiy_Annual_Security_Report.html
[7] ANTIY. “ANTIY’s Protection Manual for WannaCry Ransomware” [R/OL]. (2017-05-13), https://www.antiy.com/response/Antiy_Wannacry_Protection_Manual/Antiy_Wannacry_Protection_Manual.html
[8] ANTIY. “ANTIY’s Monday Startup Guide for WannaCry Ransomware” [R/OL]. (2017-05-14), https://www.antiy.com/response/Antiy_Wannacry_Guide.html
[9] ANTIY. “ANTIY’s Effective Protection against LockBit2.0 Ransomware” [R/OL]. (2021-09-20), https://www.antiy.cn/observe_download/observe_296.pdf
[10] ANTIY. “GANDCRAB Ransomware Focuses on ‘Dash’,” ANTIY’s Effective Protection [R/OL]. (2018-02-28), https://www.antiy.com/response/20180228.html
[11] ANTIY. “Four Role Divisions in Ransom Attacks” [R/OL]. (2021-11-23), https://mp.weixin.qq.com/s/oMneQmmYQF5B4nWVulJl1g
[12] ANTIY. “Two Typical Patterns of Ransom Attacks” [R/OL]. (2021-11-23), https://mp.weixin.qq.com/s/nrbVpjA2-jfTzjojbyFpJA
[13] ANTIY. “Analysis of the Ransom Attack Kill Chain” [R/OL]. (2021-11-24), https://mp.weixin.qq.com/s/24bIz-e4_Ts-Th0ecCWfgQ
[14] ANTIY. “Four Ransom Types and Five Attack Characteristics” [R/OL]. (2021-11-25), https://mp.weixin.qq.com/s/RL4E9v4wvazgj2UNdbMypA
[15] ANTIY. “Ten Typical Ransomware Families” [R/OL]. (2021-11-26), https://mp.weixin.qq.com/s/Jmz58xQBcytCIWx51yxBTQ
[16] ANTIY. “Trends in Ransom Attack Development” [R/OL]. (2021-11-26), https://mp.weixin.qq.com/s/1wehEDr7dTo-wdJYzfoS-A
[17] China Academy of Information and Communications Technology. “Ransom Virus Security Protection Manual” [R/OL]. (2021-09), http://www.caict.ac.cn/kxyj/qwfb/ztbg/202109/P020210908503958931090.pdf
[18] ANTIY. “ANTIY Products Help Users Effectively Defend Against Ransomware Attacks” [R/OL]. (2021-11-01), https://mp.weixin.qq.com/s/nOfhqWiw6Xd7-mvMt2zfXQ