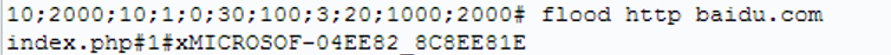Comprehensive Analysis Report on Ukraine Power System Attacks
Comprehensive Analysis Report on Ukraine Power System Attacks
1 Event Overview
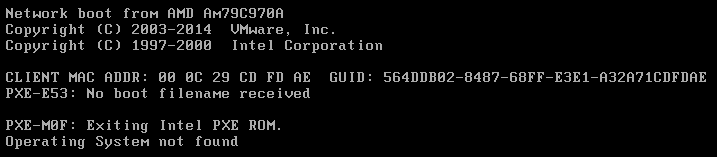
December 23, 2015, the Ukrainian power sector suffered malware attacks. Ukrainian news media TSN reported on the 24th: “At least three power regions were attacked, leading to hours of blackouts at around 15:00 local time. Attackers invaded the monitoring and management system. More than half of the region and part of the Ivan-Frankovsk region suffered hours of outages.”[1]
Kyivoblenergo power company announced: “The company was compromised, resulting in failures of 7 substations of 110KV and 23 substations of 35KV, and 80,000 users powering down.”
Security company ESET was the first to disclose the related malware on January 3, 2016 [2], pointing out that the Ukrainian power sector was infected by BlackEnergy. BlackEnergy was used as a backdoor, and released KillDisk to destruct data and slow system recovery. An SSH program with a backdoor was also found in other servers. Attackers can connect to the infected hosts at any time based on the built-in password [3] [4] [5] [6]. BlackEnergy once was used by the hacker team “Sandworm” to attack European and American SCADA industrial control systems in 2014. The security firm iSIGHT Partners released a report back then. It also released a report on January 7, 2016, directly connecting this event to “Sandworm”. In its 2014 “Sandworm” report, iSIGHT Partners believed the team was closely associated with Russia [7].
Russia and Ukraine are the most important countries in the CIS (Commonwealth of Independent States), which are entangled in complex historical relations. After the disintegration of former Soviet Union, Ukraine was gradually pro-Western. Russian President Vladimir Putin said at the NATO-Russia summit meeting in 2008 that, if Ukraine joined NATO (North Atlantic Treaty Organization), Russia would withdraw the eastern Ukraine and Crimea (which were transferred from Russia to Ukraine in 1954 by the then Soviet leaders). In early 2010, the pro-Russian Viktor Yanukovych was elected president of Ukraine, relations between the two countries improved again. But due to the turbulent political situation in Ukraine, especially the Crimea crisis occurred in 2014, Ukraine terminated most of its cooperation with Russia, and their relations deteriorated again. Energy supply around natural gas has been the main focus of the game between the two countries. March 16, 2014, Crimea launch a national referendum: establishing the new Republic of Crimea, leave Ukraine to join the Russian Federation. In the early morning of November 22, 2015, Ukraine cut the power of Crimea, nearly 2 million people were affected. December 23, 2015, the Ukrainian state power sector was attacked, which caused an outage.
In addition to ESET, several security companies and security organizations follow up a series of related events. January 9, 2016, the US security organization SANS ICS released a report, analyzing the attack process of Ukraine substation SCADA system attacks. January 15 2016, CERT-UA news reported that the network of Ukraine’s largest airport–Kiev Borispol airport–suffered BlackEnergy attack. January 28, 2016, analysts at Kaspersky Lab found BlackEnergy samples related to Ukraine STB television attacks. February 16, 2016, security experts at Trend Micro found BlackEnergy KillDisk samples in the system of a Ukrainian mining company and rail operator.
Antiy Labs, Sifang and Fudan University established a joint analysis team on January 5, 2016, officially launching the analysis on this incident. January 9, the team completed the basic sample analysis; January 23, completed the preliminary analysis report, and distributed the report in seminars of Professional Committee of Computer Security of China Computer Federation; February 24, the final report was published.
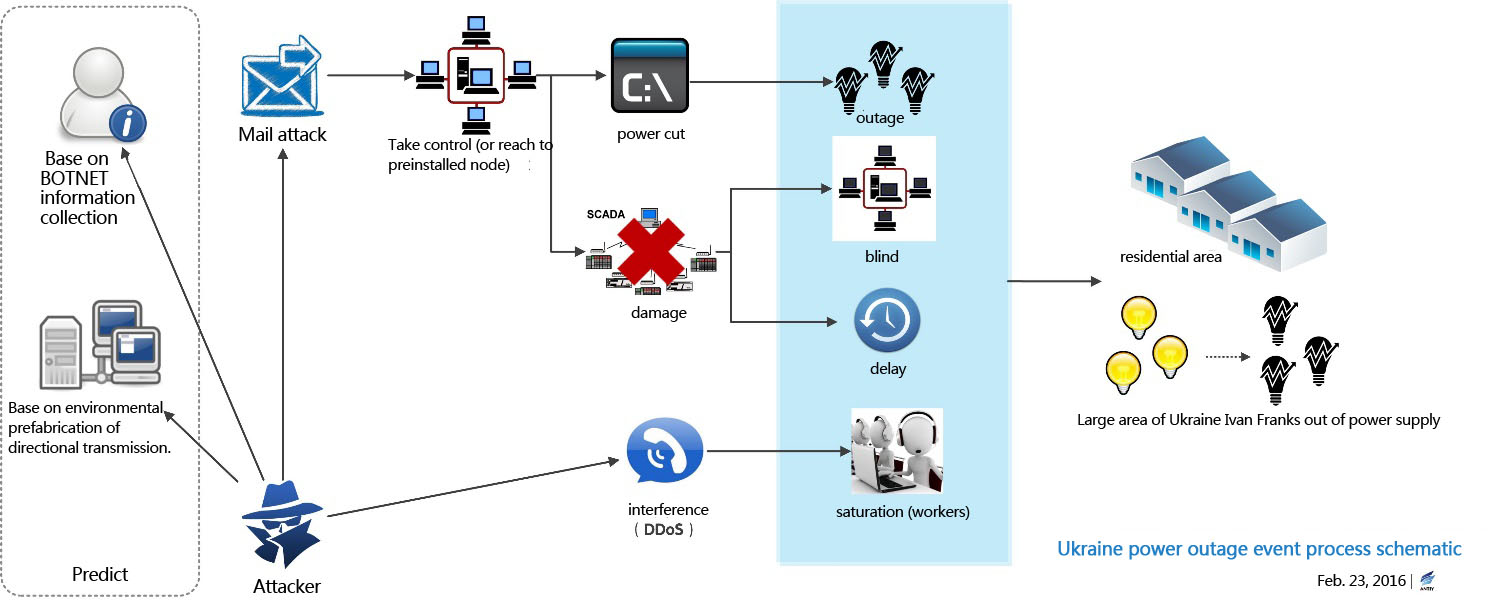
Based on overall event tracking, electricity system analysis and associated sample analysis, the joint analysis team concluded the attack: took the power infrastructure as the goal; BlackEnergy and other related malware as the main tool; conducted preliminary data acquisition system and environmental presets via BOTNET; sent malware payload via emails; sent power off commands via remote control SCADA nodes; destroyed SCADA system to slow system recovery; used DDoS service calls as interference; finally completed an information warfare level cyber attack.
Of particular note is that, the point of attack is not in the power infrastructure, nor did it use 0-day vulnerability, but completely reached by implanting malware in PCs. Its costs are significant reduced compared to Stuxnet [8] [9], Equation [10] [11] [12] and other attacks, but it is equally direct and effective.
2 Power System Overview and Outage Causes
2.1 Power System Overview
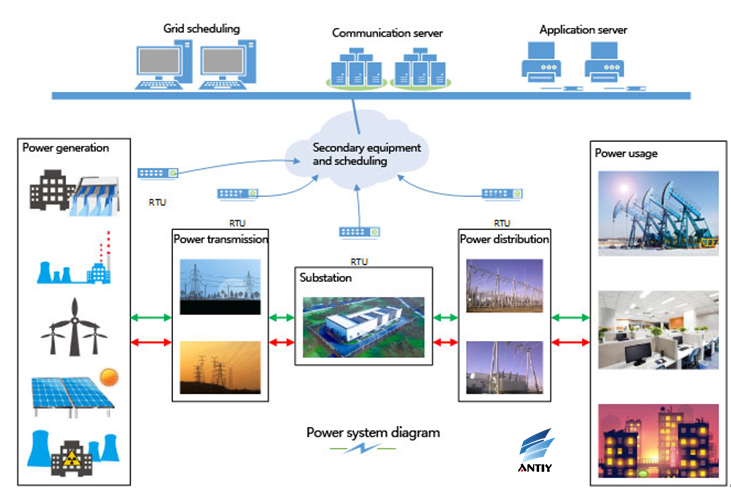
The power system is a set of production and consumption systems, composed of power plants, power transmission and transformation line, power supply and distribution plants, electricity usage and other aspects. The whole process is as follows: the power supply (power plants) boosts to a certain level in booster substations, then transmitted to the load center substation via the transmission lines, steps down to a certain level, and then connected to the user via distribution lines. In the overall power system, nodes using computers are mainly in power generation, substation and dispatch center.
Figure 1: Power system diagram
2.2 Introduction to Power System Links
2.2.1 Booster Substations
Figure 2: Booster substations
Booster substations can convert the AC voltage less than 20KV to demanded voltage levels. Its main devices include: step-up transformers, circuit breakers, disconnectors, voltage and current transformer, relay protection, etc.
2.2.2 Transmission Line
Figure 3: Transmission line
Transmission grid: convert power supply to high voltage via transformers and transmit to all substations.
Distribution grid: convert the high voltage into low voltage and supply to individual users.
Transmission line: 110KV, 220KV, 330KV, 500KV, 750KV, 1000KV.
2.2.3 Step-down Substation
Figure 4: Step-down substation
Reduce the high voltage power, and supply to the regional power grid, regional grid or end-users
According to the functions in the system, step-down substation can be divided into: hub substation, intermediate substation, reginal substation and terminal substation.
Figure 5: 500KV hub substation
Figure 6: 220KV intermediate substation
Figure 7: 110KV reginal substation
Figure 8: 35KV terminal substation
2.2.4 Distribution Grid
As the power distribution section, distribution grid distributes and sends power to various types of users. Distribution facilities includes distribution lines, distribution substation, distribution transformers, etc.
2.3 Substation Automation System Overview
The difficulty lies that, the joint analysis team can’t obtain more precise information of Ukraine power system. Related information disclosed is that, the affected substations are 110kV and 35kV substations. The team can only make “common sense” judgment based on such information. Typically, high-voltage grids (≥AC 750kV and DC ± 400kV) are mainly inter-regional transmission grids. AC 500kV, 330kV, 220kV and 110kV transmission grids are mainly regional grids; 35kV and 10kV grids are the main distribution and rural grids. Among these, 110kV and 35kV substations are closer to the end users.
For an actual substation, devices related to high voltage power, including isolation switch (knife switch), circuit breakers, transformers, PT, CT, etc, are usually called primary equipment. Protection, measurement, monitoring and remote control devices, including protection (relay protection), instrumentation, central signal and remote devices, are called secondary equipment. Signal lines and communication lines that the secondary equipment requires are called secondary lines. The core of Substation Comprehension Automation System (hereinafter referred to as substation automation system) is to computerize the secondary equipment system, integrating substation protection, measurement, monitoring and remote control in one, replacing conventional substation secondary equipment, and simplifying secondary lines. Substation automation system is the basis of ultimate realization of unmanned substation.
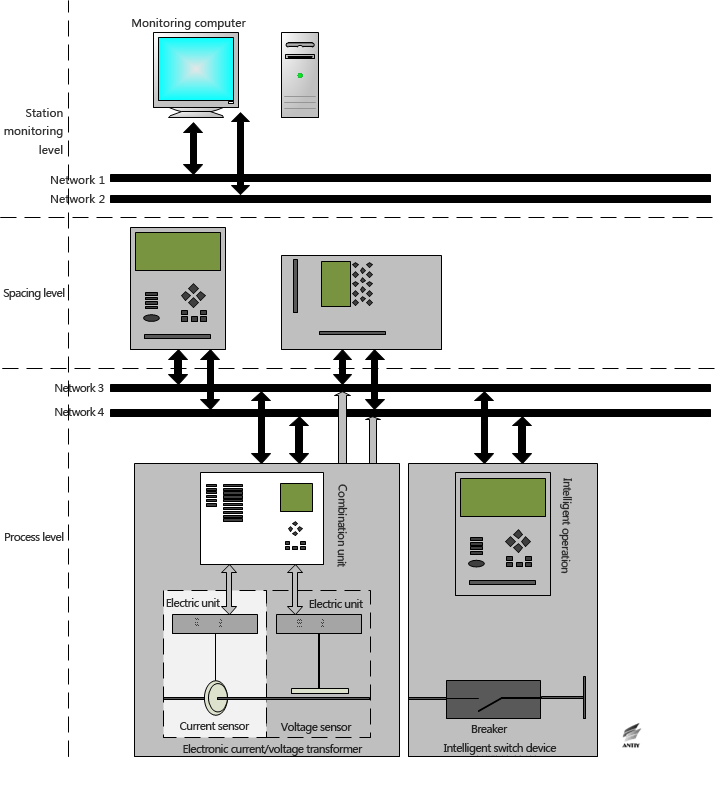
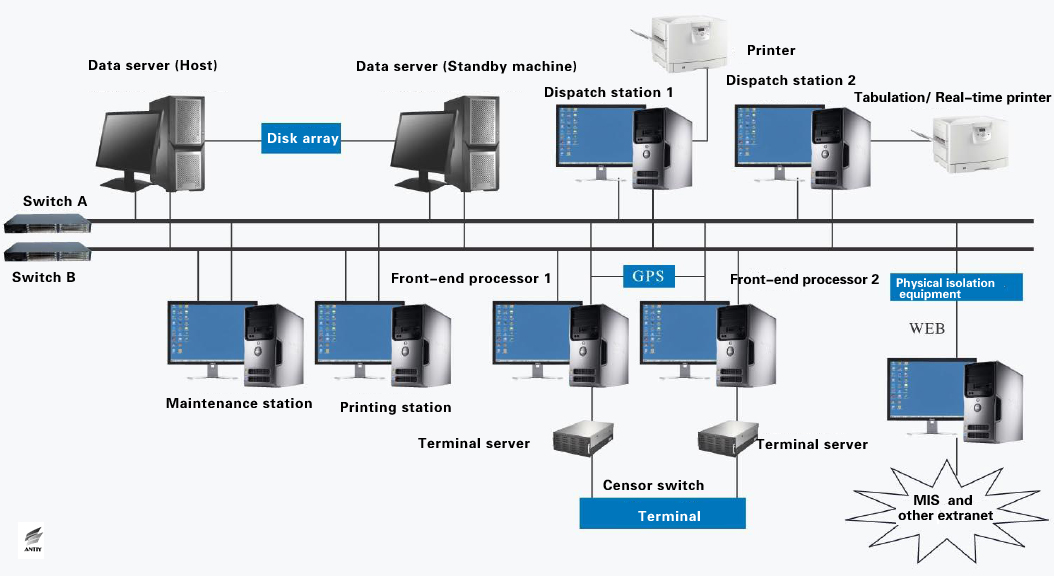
In the chemical industry and other industrial systems, industrial control systems are mainly process control systems (PCS), belonging to closed-loop automatic control systems. Instrumentation control systems and DCS (Distributed Control System) both belong to process control systems. But for substation automation systems, manual monitoring (open-loop control) is still the main part. They require “four remote” features: telemetry, remote communication, remote control and remote adjustment. In addition to relay protection systems that need to independently realize automatic protection control, substation automation systems are generally considered to belong to the human monitoring-based SCADA (data acquisition and control systems), and are somewhat similar to DCS (but not identical architecture). A possible substation SCADA architecture is shown in Figure 9.
Figure 9: One possible substation SCADA architecture
If we compare substation SCADA with general industrial DCS, then the process level corresponds to DCS field instrument level, directly connecting to circuit breakers, transformers, PT, CT and other primary equipment, completing the final telemetry, remote control and other functions. The spacing level corresponds to DCS field control level. Especially, the relay protection devices are automatic control, equivalent of a DCS field control station. The station control level corresponds to the DCS HMI (Human-Machine Interface), configuration and other aspects, which are currently based on PC and corresponding software. Station level network is equivalent to the Industrial Ethernet network (industrial intranet); the process level network is equivalent to the fieldbus. For intelligent substations, they currently use Ethernet-based IEC 61850 standard communication protocol. For non-intelligent substations, the process level and the spacing level have no standard communication protocol. The communication protocol is generally determined based on process level device (RTU, etc.).
2.3.1 PC and Windows-Intel architecture’s position in the substation automation system
Industrial control system has a longer history than PC systems. The early industrial system is relatively low-level and original analog control system, using meters to display feedbacks, with no PC systems. When PC systems first entered industrial control systems, they didn’t play the core role, mainly monitoring human-machine interfaces (HMI workstations). But along with the gradual integration of industrialization and information technology, versatile PC systems (including servers), with its standard architecture, rich software systems and other advantages, gradually began to play a more pivotal role in the industrial control systems. Especially, they took automatic control, configuration and other work (engineering station, operation and maintenance of computers, etc.), thus obtaining the ability to directly manipulate the actual production processes.
Typically, for substations of 220kV and above, the monitoring systems (belong to SCADA station control level) usually use Unix, Linux and other operating systems. For 110kV and 35kV substations, the monitoring systems usually use Windows operating system. Currently, Russia and other former Soviet republics are abounded with 110kV and 35kV substations, the monitoring systems mainly use Windows operating system. It should be noted that, no operating system can be 100% “immune” to attacks. Any node system at any critical position and the software wherein inevitably face security challenges, which is not essentially related to what their operating system is. Given the rich resources, cost acceptance ability and strong will of APT attackers, any kind of operating system can’t avoid attacks.
SCADA system is a computer-based process control and dispatch automation system. It can monitor and control on-site equipment, to achieve data acquisition, equipment control, measurement, parameter adjustment, signal alarm and other functions. With the extensive application of the smart grids, PC nodes plays an increasingly important role in the entire grid system. In the substation’s SCADA system, PCs collect large amounts of data in real time, make summaries and analysis, and send them to human-machine interface for displaying. Meanwhile, based on the statistical analysis data, PCs deploy power in real time, and give corresponding control instructions. In addition, PCs can remotely configure DCS system.
For some industrial control system designers: in DCS, the core of automatic control is the field control station composed of IPC (Industrial Personal Computer), embedded systems or PLC (Programmable Logic Controller), which belongs to the filed control level; in substation SCADA, the core is relay protection devices (substation of 35kV and below may use protection and control integration devices), belonging to the spacing level. Both filed control station and relay protection device run independently. Filed control station and relay protection devices can operate independently, achieving complete control and protection functions. This architecture design is called distribution principle, also known as “decentralized control + centralized monitoring” mode. In this mode, if the upper SCADA system fails, it is possible that the whole system is still capable of normal operation for some time. On the premise of single point failure caused by non-subjective damage and urgent incident, this risk control mode id effective. But in advanced cyber attacks or even information warfare scenarios, attackers obtain control of the SCADA system based on environmental preset, oriented invasion penetration, etc., this simple distribution principle alone is not enough.
2.4 Attack Methods Leading to Power Outages
Currently, substation SCADA system can realize remote data acquisition, remote device control, remote metering, remote parameter adjustment, signal alarm and some other functions. There are a number of ways to cause power outages through SCADA, such as:
- Control the operation of remote devices, such as circuit breakers and knife switch. This approach is relatively straightforward, i.e., directly cutting off the power lines, resulting in the corresponding outages.
- Modify the equipment operating parameter, such as modifying the setting current value of the relay protection device. When the setting current value is reduced, normal load will be mistaken for overcurrent, protection action will be launched, causing some damage, such as breaker tripping.
For the attackers in Ukraine power outage incident, they can use several methods to complete the above operations after obtaining the control of the SCADA system.
- Directly control over program interface of the system of substation via malicious code
Once the attacker gained control of the SCADA system of substation (eg SCADA management workstation nodes), he can gained an operation interface and the operation rights which is the same with that under control of SCADA operator (including keyboard input, mouse clicks, command line and interactive configuration operation). Any local operation of the operator (such as login password, etc.) can be captured by attacker, and the USB device uses login authentication method such as USB KEY maybe connected with the device by default. Thus, an attacker can conduct remote control over the switch to turn off the power; he can also change the parameters of a remote device to cause power grid failure or power failure.
- Take control of power equipment through the fake tampered malicious code
Attack can also take control of power equipment through calling or hijacking API interface and tampering command line except from directly manipulating the interface. Now, communication networks that under the control of SCADA substation have on special designed secure encryption communications protocol. After the attacker gained control over different nodes, he can built or temper communication (such as IEC 61850 communication clear text) between SCADA monitoring software and the spacer layer devices without any technical obstacle, so an attacker take control of electrical equipment of process level over construct or intercept instructions, he can also manage the operating status of devices, change the equipment operating parameters to cause grid failure or power failure.
The two methods stated above can not only achieve interactive job on the premises of remote control, but also achieve command preset, timing trigger and the condition trigger. Such an attack can conduct even without communicate with attacker. An attack can also utilize keyboard and mouse behavior preset to accomplish the first method.
2.5 Procedure Analysis
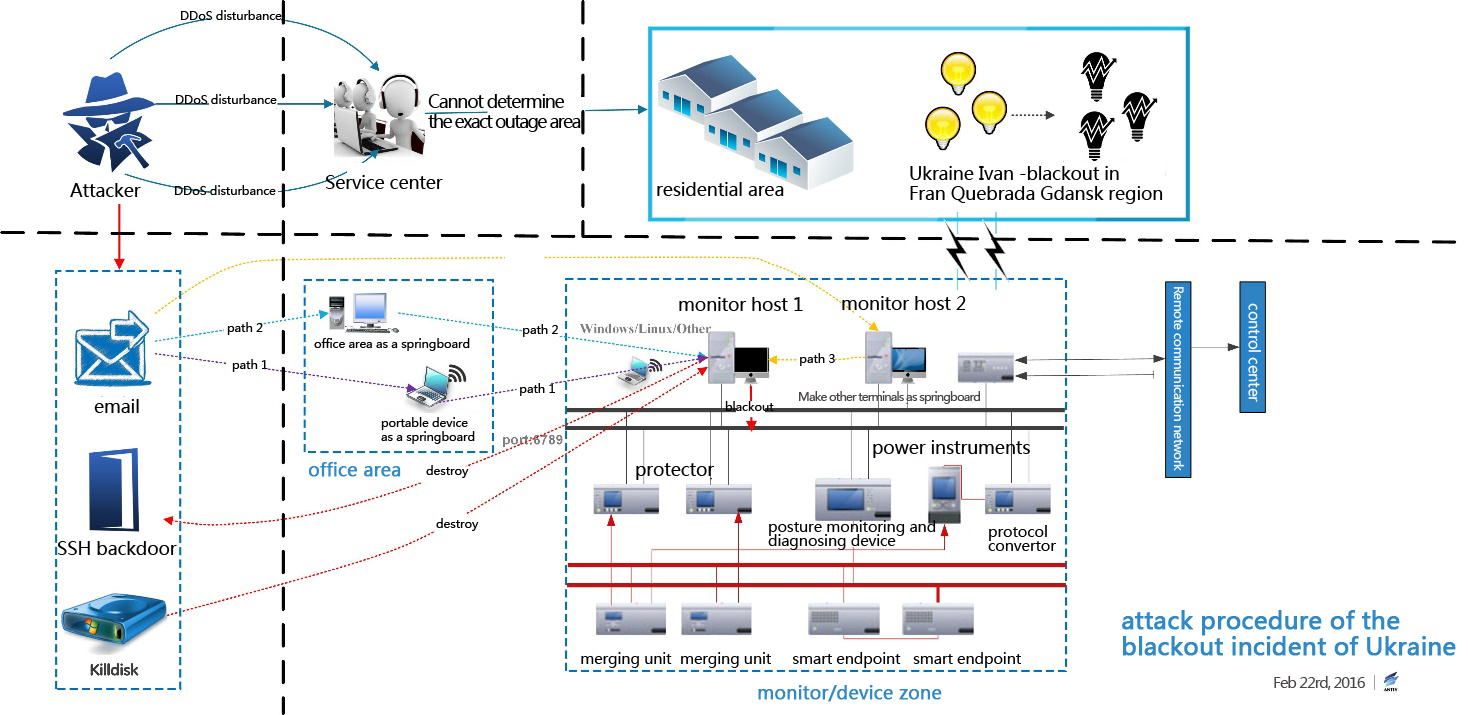
According to the above analysis of the substation system based and the public available sample, we believe the attacker will utilize spear phishing or other means to conduct an attack. First, BlackEnergy will be planted into “stepping stones”, then a standpoint will be built via BlackEnergy, then he will start lateral penetration on the basis of “stepping stones”, finally he will take control of the critical host of monitoring / setting area. Meanwhile, because of BlackEnergy has formed scalable botnet, there may exist the possibility that the attacker has finished the preset of preliminary environmental in the Ukrainian power system.
After gained control of the SCADA system, the attack will send out certain command to turn off power, then he will cover the MBR and some sectors to make the system cannot bootstrap after reboot; he will also clean the system log, cover the format of document file and other important files to steal date. Under such circumstance, it’s difficult to restore the system, what’s worse, the failure of upper fault feedback and display make researchers cannot effectively facilitate the resume work.
On the one hand, the attacker conducted online attack against the substation; on the other hand the attacker also conducted some offline attack such as telephone DDoS attacks against the customer service center of the substation. The whole attack procedures are showed below:
Figure 10 Attack procedure of the blackout incident of Ukraine
3 Analysis of the attack group and BlackEnergy
3.1 SandWorm
SandWorm group is discovered by iSIGHT in October 2014, iSIGHT believe that this group is Russia-related, the group uses vulnerability and malware to conduct attacks against the target that they interested in, the main targets include: North Atlantic Treaty Organization (NATO), Ukrainian-governmental organizations, governmental organizations in Western Europe, companies which belong to energy sector, telecommunications companies in Europe, and academic organizations in United States.
In this incident that the substation in Ukraine suffered from, xls documents that contained with malicious macro code were used by the attacker, after analyzing this document we found that the features of the malicious code it released are very similar with that of SandWorm group (such as release FONTCACHE.DAT file, add a shortcut that with format name CLSID via start the directory, all released files are programs of BlackEnergy botnet). Therefore, we believe this incident maybe related to SandWorm group.
3.2 BlackEnergy
BlackEnergy is a rather popular attack tool, it usually used in automated criminal activities, and it can be purchased from the underground market of Russia, the first time it is discovered can date back to 2007. The software was originally designed to create botnets, conduct DDoS attacks and steal banking credentials, later it is upgraded to support various components.
Because the characteristics of multi-component and multipurpose of BlackEnergy, it has been used for different purposes by several groups. For example, it can be used to conduct DDoS attacks, send spam, steal passwords, steal banking credentials and search for files of specific types. In recent years, it usually exploited by attackers to conduct attacks against Ukrainian government, industrial control systems, and even routers, etc.. More information on BlackEnergy sample that exploited by attackers in this incident, please see the analysis of the loaded file in The Analysis of SandWorm Related Rhreat (CVE-2014-4114). [13]
BlackEnergy has formed BOTNET system, this system is critical to collecting infrastructure and important nodes related information. And it can detect the infected objectives by configuring build_id value, then it will chose the more vulnerable systems to conduct in-depth attack.
3.3 History of version evolution
3.3.1 BlackEnergy1
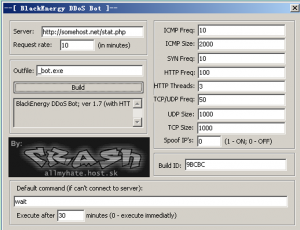
BlackEnergy tool has a builder application, the following figure shows the BlackEnergy builder application (BlackEnergy1) which is discovered in 2007, it is mainly used for the implementation of DDoS attacks.
Figure 11 Builder application of BlackEnergy1
BlackEnergy botnet can start the parameters of controlled “flood” command, for example: ICMP ping floods, TCP SYN flood, UDP traffic flood, binary package flood, DNS request floods, etc..
The program of the host belongs to WEB program, and it can pass back the related information of infected machine to C&C server after Base64 encoding.
Figure 12 Base64 Encryption
Figure 13 Decrypted date
The content of decoded Base64 is configuration information which has a up-line ID number, configuration information of BlackEnergy also contains build_id value which is a special string, and it is used to identify infected individuals, such as:
| build_id | Target industrial |
|---|---|
| en | Energy |
| tel | Telecommunication |
| trk | Transportation |
| … | other unknown ID |
Table 1 build_id
Generally, The Filename that released by BlackEnergy 1 is mssrv32.exe, and this process will be injected into Svchost.exe to launch DDoS attacks when there is an opportunity.
3.3.2 BlackEnergy2
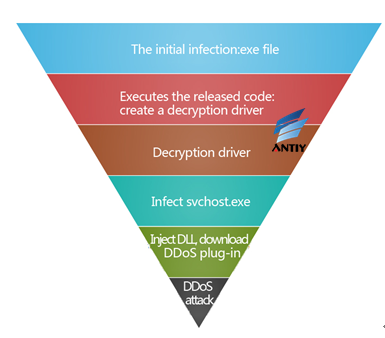
BlackEnergy 2 is still a botnet program which contains the function to launch DDoS, but it has added encryption software to encrypt itself to bypass the detection of anti-virus software. This version will release driver file first, and set the file to run in service mode, then the driver program will be injected into system processes, then a sample will connect remote server to download components of DDoS attacks, and to launch DDoS attacks based on the profile.
Figure 14 Schematic Diagram of BlackEnergy2
BlackEnergy2 malicious program is not only powerful, but also can be widely used and very easy to deploy and manage. It Supports upgradeable components (added module), and it is easier to modify and extend its functionality. Hackers can issue commands by remote control center to quickly finish the installation and upgrade of components.
BlackEnergy 2 has three components, namely SYN, HTTP, DDoS attack components, all components will be loaded into memory and executed, and then attacker can start an attack against the remote server.
For most installer of BlackEnergy 2, all the installer names are msiexec.exe. And msiexec.exe is a system process that is part of Windows Installer, and it is used to install Windows Installer package (MSI), it is also used by BlackEnergy for some malicious purpose.
3.3.4 BlackEnergy3
F-Secure released a report in September 2014, they claimed that they have found a variant, the author has rewrote the code of this version and the configured date are all saved in different format. It doesn’t use driving component any more. We call this new variant BlackEnergy 3. But attack incidents that related to this new version are still rare.
3.4 Attack tools/Components
BlackEnergy component is a DLL library file, it will be encrypted before send to botnet, after decrypting the received DLL component, it will be placed in the allocated memory. Then it will wait for the appropriate command. For example: send spam, steal confidential information, create a proxy server, and launch DDoS attacks in appropriate time.
| Name of components | Features |
|---|---|
| SYN | SYN attack |
| HTTP | http attack |
| DDOS | DDoS attack |
| spm_v1 | spamming |
| Ps | password stealing |
| ibank.dll | banking credentials stealing |
| VSNET | Propagation and reflection payload |
| weap_hwi | compiling the DDoS tools which run in the ARM system |
| FS | searching for certain types of file |
| DSTR | rewrite with random data |
| RD | remote desktop |
| Ciscoapi.tcl | attack against router of Cisco |
| KillDisk | delete MBR, make the system cannot startup |
Table 2 Popular Attack Components of BlackEnergy
3.5 Evolution and historical incidents on BlackEnergy
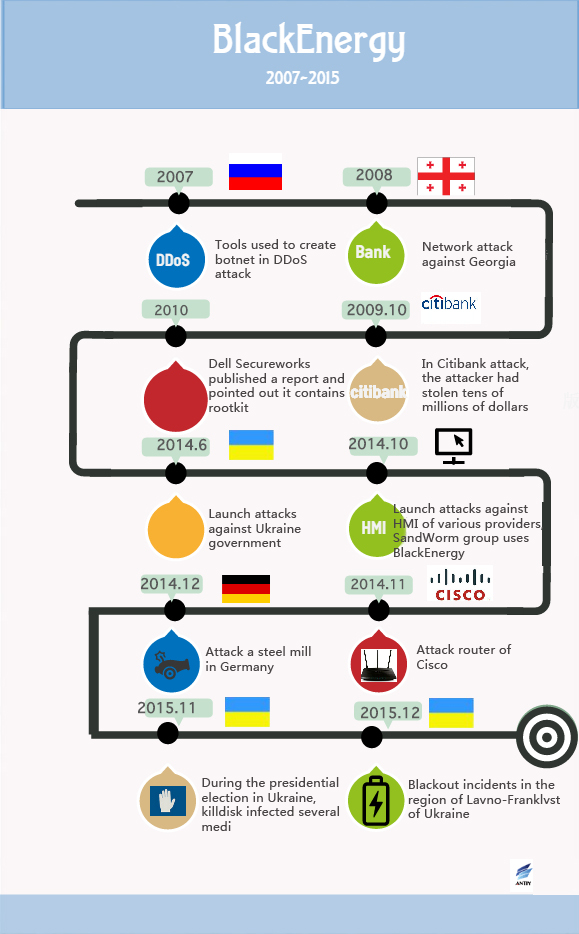
Figure 15 Historical incidents on BlackEnergy
- 2007
The first version of BlackEnergy appeared in 2007, and it is used to launch DDoS attacks, create botnets and steal banking credentials and so on.
- 2008
During the Russian-Georgian conflict, BlackEnergy is used to conduct cyber attacks against Georgia.
- 2009
In Citibank attack, the attacker had stolen tens of millions of dollars.
- 2010
BlackEnergy2 is released in 2010, the new version supports more plug-in features.
- 2014
The new version BlackEnergy defined Ukraine and Poland as its attack targets。
- Octorber 2014
BlackEnergy attacks HMI of several providers, the victims include GE、Advantech WebAccess、SiemensWinCC。
- 14th Octorber ,2014
iSIGHT discovered BlackEnergy sample which is delivered via CVE-2014-4114.[14] Antiy Labs did a replay analysis on related samples and publish a report named Analysis on SandWorm (CVE-2014-4114) Related Threat on 15th October ,2014. [13]
- November 2014
Attack the devices of Linux and Cisco.
- December 2014
The Information Security Report which is published by German Federal Office for Information Security (BSI) published in 2014 revealed that there is a cyber attack against the infrastructure of one German mill, and the attack has caused significant physical damage, relevant reports indicate that the incident may be related to BlackEnergy. Antiy Labs did an instant follow-up analysis after the report is published, and put forward an analysis report on BlackEnergy the next day.
- November 2015
During the presidential election in Ukraine, killdisk infected several media agencies.
- December 2015
Ukraine government asserted that BlackEnergy should responsible for the blackout incidents in the region of Lavno-Franklvst of Ukraine.
4 Sample Analysis
4.1 Leading Document
After associating relevant public samples, Antiy CERT gained the original email which sent the leading document. This email is used as attack tool in the attack against Media of Ukraine, the attacker injected malicious macro code into one file, once the file is opened, the target system will be infected.
This file is different from what we used to see in APT attacks, although it uses email and Office document as a lure, it doesn’t use zero-day and other form of format overflow, it is more like a traditional macro viruses. This shows whether use “advanced attack techniques” (such as format overflow, zero-day) or not is related to adaptability of targets.
Figure 16 Details of the email
This is a common practice of targeted attacks. first, attacker s will send an email that with embedded malicious file to the target, if the target host has security risks, then it will automatically run the macro code, after opening the attachments (Excel) it will show the following message, in order to induce the victim to start the macros, the attacker will alert the victim in Ukrainian, it reads: “Note that! This document is only supported by a newer version of Office, to display the contents of the document, you must enable macros. “
Figure 17 Content of Excel
After analyzing the macro code, we found that the macro code is composed of two parts, first the macro code defined 768 arrays via 25 function, then binary data (PE file) will be written in array as backup, please see figure 18 on details:
Figure 18 Macro code
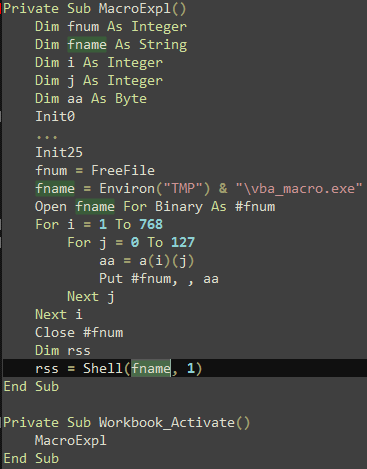
Then the binary data will be wrote in specified disk file through a loop (the path is:% TEMP% \ vba_macro.exe), then this file (BlackEnergy Dropper) will be executed, it will release BlackEnergy Dropper after several times of decryption, and download plug-in through BlackEnergy, and then launch attacks against the system.
Figure 19 Generate the PE
4.2 Dropbear SSH
This sample is generated after an attacker tampering parts of codes of SSH server program, which is an open source SSH software Dropbear SSH. [15]
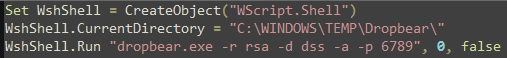
An attacker can start this SSH service endpoint by making use of a VBS file, this VBS reads as follows:
Figure 20 Content of VBS
VBS script starts SSH program, and open the 6789 port to wait for a connection, such an attacker can connect to the victim machine in internal network.
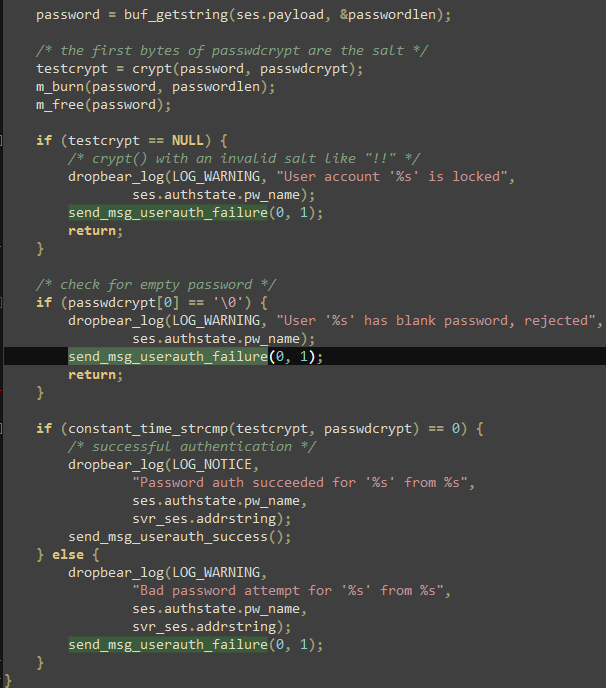
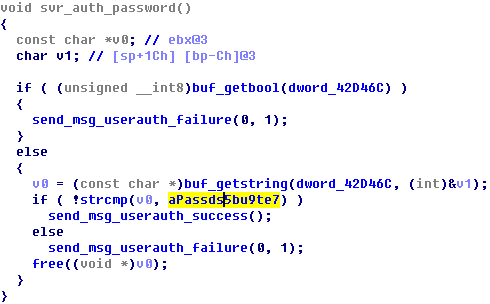
This SSH program is compiled by attacker on the basis of Dropbear SSH source code, the attacker added a fixed password “passDs5Bu9Te7” into the program, so this password is a necessity to connect to the SSH service, the following figure shows the original Dropbear SSH source code and the modified one:
Figure 21 Dropbear SSH
Fgirure 22 Dropbear SSH Code with backdoor
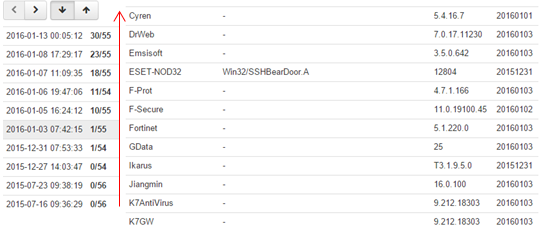
Security researches of Antiy believe this Dropbear SSH is just the SSH management tool which Ukrainian power sector used, if there is Dropbear SSH that contains backdoor, it may also be the results of preset of the attack environment. Meanwhile attackers regard open source code as the base, they create suspicious features so as to evade the detection of security software purposes. From the detection results that showed in figure 23 we know that this sample can evade all detections in the early period, then it can be detected by ESET because its sample is captured by ESET. After that, it can be detected by other providers.
Figure 23 History testing results
4.3 KillDisk
KillDisk are also the components used by attackers, the main purpose is to erase evidence and damage system. After the samples being executed, it will traverse file to erase, wipe disk MBR, damage files, and finally force to shut down the computer.
4.3.1 Sample labels
| Virus name | Trojan/Win32.KillDisk |
|---|---|
| Original file name | c7536ab90621311b526aefd56003ef8e1166168f038307ae960346ce8f75203d |
| MD5 | 7361B64DDCA90A1A1DE43185BD509B64 |
| Processor architecture | X86-32 |
| File size | 96.0 KB (98,304 bytes) |
| File format | BinExecute/Microsoft.EXE[:X86] |
| Timestamp | 3693DD58->1999-01-07 06:02:00 |
| Digital signature | No |
| Shell type | No |
| Compiling language | Microsoft Visual C++ 8.0 |
Table 3 Sample labels
4.3.2 Sample installation process
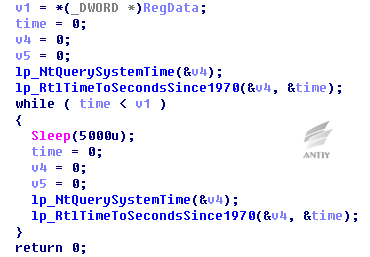
The samples have the function of delay trigger, when starts the sample, a parameter is needed to add to specify about after how many minutes should samples perform malicious operations. Samples will make the input parameters multiply by 60 and change to seconds, and then use RtlTimeToSecondsSince1970 function to obtain the current number of seconds to plus, and write the value into registry.
Figure 24 Writing into registry
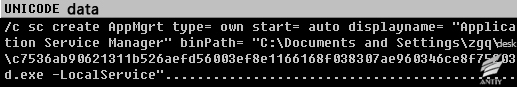
ShellExecuteW is used to call cmd.exe and install, parameters are as follows:
Figure 25 Add services
After the installation, the sample will execute a loop operation, determine if the time of current system is larger than the value in registry, if it is, execute malicious operation; if it is not, continue to execute loop operations.
Figure 26 Delay operations
4.3.3 Analysis of sample functions
4.3.3.1 Cover MBR and part sector
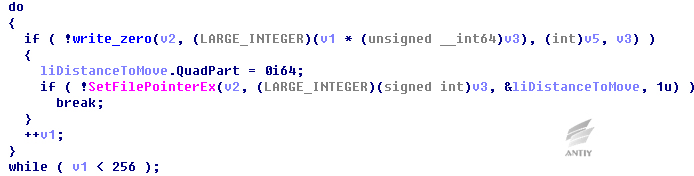
Samples will destroy disk in system, write “\ x00” into the top 0x20000 bytes in disk and make system cannot normally boot after restart.
Erase the former ten disks of system, open disk and access to handle.
Figure 27 Traverse disk
Erase from the initial position of disk, each time write“\x00”with 0x200 bytes and execute operations 0x100 times.
Figure 28 Disk erasing
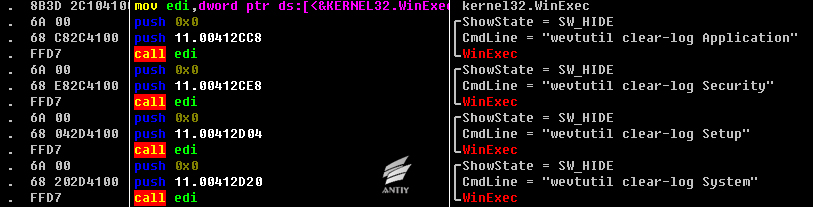
4.3.3.2 Clear system log
If the erasing of some sectors can properly complete, the sample will clear system log to increase the difficulty of later analysis, as Figure 29:
Figure 29 Log clearance
4.3.3.3 Process traverse and process clearance
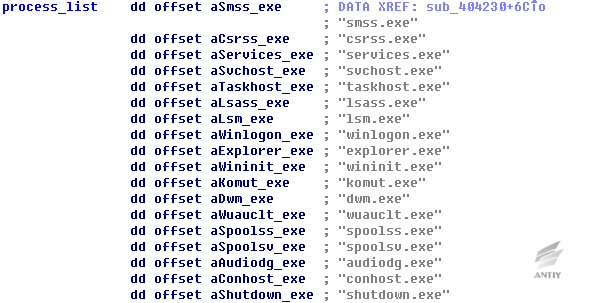
Then samples will traverse the process in system, if the process name exists in the list below, then release it; otherwise, it will end the process.
Figure 30 Process list
From the table, most are the key process of system except for komut. Exe. Samples end other processes to extract more system resources and make file erasing more effective, meanwhile, the avoidance of manslaughter of system processes affects system operation.
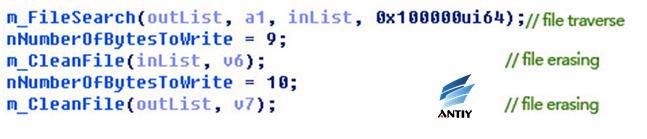
4.3.3.4 File erasing
This operation is performed by a newly created thread. It will first to traverse all files in disk and divide them into two categories according to different file suffixes, finally using random numbers to erase the files. Figure 31 is part code:
Figure 31 File erasing
Traverse of function m_FileSearch to file can get inList and outList. If the file suffix exists in the table below, the file path stores in inList; Otherwise, in outList.
Table 4 Suffix list
Because it is running on thread, it cannot guarantee that all files are damaged. The sample firstly erases the files in inList, therefore, the attacker wants to destroy the files with suffix above. If time is enough, he wants to destroy other files in system. The size of erased files is around 8.03 KB.
4.3.3.5 End process
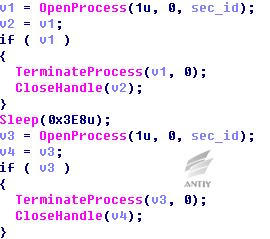
Seek sec_service. exe. by traversing system process, if there is the process, end it, and execute twice.
Figure 32 End process
If there is no this process, determine whether there is sec_service service, if it is, stop it and delete it.
4.3.3.6 Shutdown operation
When the above operations are completed, the samples will shut down computer.
Figure 33 Shutdown operation
After the execution of this command, it will turn off after 5 seconds, and the sample will also traverse the system in the 5 seconds and end three system processes, csrss.exe, smss.exe and lsass.ex. It is suspected that the attacker worries about that interference of these processes makes it cannot restart.
And after the shutdown, due to the MBR has been destroyed, the system is unable to complete the bootstrap.
4.3.3.7 Other samples
There are four samples about KillDisk and the sample that analyzed above is the most powerful one. We also analyzed the other three samples, and found that their functions are basically the same, multiple functions are exactly the same, the timestamps of former three samples are close to each other. Therefore, it can infer that the four samples are compiled through constant modification of the same set of code from the same team, and the timestamp of the last sample is modified. Here is the contrast information between them:
| Sample MD5 | Size | PE timestamp | Functions |
|---|---|---|---|
| CD1AA880F30F9B8BB6CF4D4F9E41DDF4 | 88 KB(90,112 bytes) | 562B8636->2015-10-24 21:23:02 | Wipe the former 256 sectors of the disk Erase the 16 kinds of files with specific suffix End process that out of the list Restart the system |
| 66676DEAA9DFE98F8497392064AEFBAB | 124 KB(126,976 bytes) | 562B8C4F->2015-10-24 21:49:03 | 16 kinds of files with specific suffix file increase to 18045 kinds |
| 72BD40CD60769BAFFD412B84ACC03372 | 108 KB(110,592 bytes) | 562BCBB2->2015-10-25 02:19:30 | Add the function that can add itself to service, add registry operation, and increase difficulty of analysis by dynamic function access. |
| 7361B64DDCA90A1A1DE43185BD509B64 | 96 KB(98,304 bytes) | 3693DD58->1999-01-07 06:02:00 | Add timing function, add judgement of process komut.exe, add ending process sec_service.exe, add close service sec_service, transform string and increase difficulty of analysis. |
Table 5 File contrast
4.4 Degree of disk damage
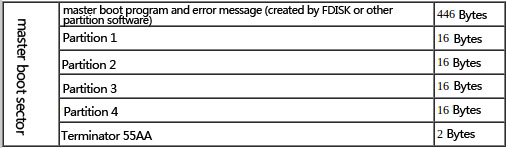
Samples will wipe the former 0x20000 bytes of disk. The size of each sector is about 0x200 bytes, in other words, the sample will wipe the former 256 sectors of disk.
The first sector is the MBR as below:
Figure 34 MBR construction
Construction of distributions:
Figure 35 Construction of distributions
The sector of system boot sector (BOOT) is determined by Distribution 1. We use Win XP and Win 7 to test respectively, here is the result:
| Operating system | Disk format | MBR address | Boot sector address | Damage result |
|---|---|---|---|---|
| Win XP | NTFS | 0x00-0x200 | 0x7E00-0x8000 | MBR and boot sector are damaged |
| FAT32 | 0x00-0x200 | 0x7E00-0x8000 | MBR and boot sector are damaged | |
| Win 7 | NTFS | 0x00-0x200 | 0x100000-0x100200 | Only MBR damaged |
| FAT32 | Do not test because the distribution format of FAT32 cannot install Windows 7 system | |||
Table 6 Test result
Samples will certainly destroy the MBR and make system cannot normally boot, but whether it will damage the system boot sector and the degree of damage size cannot be sure. It depends on the size of the disk, the partitioning tool as well as the installed operating system and so on.
4.5 Recoverable degree test
The following test is ongoing after wiping disk MBR and before samples being wiped out. And we do a recovery test to the disk that wiped by samples. First, we use PTDD Partition Table Doctor to reconstruct disk MBR, and then rebuild the partitioned Table, to test if the recovered disk can normally boot and if the files are complete.
The two repair work will only modify the first sector of the disk, including the master boot program error message, four partitions and terminator.
Testing of two hard disks: one is XP system, the content of Partition 1 is within the former 256 sectors and has been damaged; the second is Windows 7 system, the content of Partition 1 is not in the former 256 sectors and has not been damaged.
- XP system disk repair
Before repairing disk, system partition cannot been found because the MBR has been damaged, the error message of system is as below:
Figure 36 MBR lost
As the system startup files have been damaged, the error below will appear after the reparation of MBR:
Figure 37 System files being damaged
- Win7 system disk reparation
After reconstruction of disk MBR, using the tool cannot find disk partitions and artificial search is needed to determine the location and size, so write the information into the corresponding position of MBR sector.
Running system will cause this error:
Figure 39 System error
Use WinPE to login system and use command bcdedit to repair, namely:
Table 7 Repair command
Boot normally.
Through tests above, it can be seen that if the content of Partition 1 and MBR are wiped by samples, only MBR can be repaired and Partitions 1 content cannot be repaired as well as startup. If only the MBR is wiped, it can be repaired and normal boot.
But after being executed, samples erase the disk files in the system, even if the MBR being repaired, the damaged system files cannot recover.
5 Summary
Figure 40 Summary of Ukraine power outage attacks
Just as we point out at the beginning: it is a high-standard network attack that takes BlackEnergy related malware as the main attack tools; an data acquisition and environmental preset through BOTNET system; take mail sending malware load as the final attack; making command via remote control node SCADA to cut power; to make sluggish recovery and state blindness by destroying SCADA system; use DDoS phone calls as interference, and finally reaches the goal of long-time power outages and makes the society at a mess.
The subject of this attack is critical infrastructure which makes people naturally think of “Stuxnet worm” six years ago. Comparing the elements of related events, we can got that different attack organizations have a completely different style, if the A2PT attack as “Stuxnet” is typical for 0Day, complex encryption strategies, PLC and firmware and so on; And the “success” of Ukraine attack is completed without any 0Day and attack components in production system side, but only relies on the assignments of PC client, obviously the attack cost is much lower than Stuxnet.
| Stuxnet | Ukraine substation attack | |
|---|---|---|
| Main targets | Iran’s nuclear facilities | Ukraine's power system |
| Associated attacking targets | Foolad Technic Engineering Co (produces automation system for Iran's industrial facilities) Behpajooh Co.Elec & Comp.Engineering (develop industrial automation system) Neda Industrial Group (provides automation services to industrial control field) Control-Gostar Jahed Company (industrial automation company) Kala Electric (a major supplier of uranium enrichment centrifuge equipment) | Kiev Borispol airport, largest in Ukraine Ukraine mining company Ukraine rail operators Ukraine’s state-owned power companies UKrenergo Ukraine TBS |
| Targets | upper computer (Windows, WinCC), PL Control system, PLC | Office machines (Windows), upper computer (Windows) |
| Consequence | Greatly delayed Iran's nuclear program | Large area of Ukraine Ivano-Frankivsk power outage |
| Core attack principle | Modify centrifuge stress parameters, modify centrifuge rotor speed | Take order to cut power by controlling the SCADA system |
| Vulnerabilities used | MS08-067 (RPC Remote execution vulnerability) MS10-046(shortcut file parsing vulnerability) MS10-061(printer daemon services vulnerability) MS10-07(Kernel mode driver) MS10-092(Task planning process vulnerability) WINCC Password hard-coded | Undiscovered |
| Attack entrance | USB ferry Workers implanted (suspected) | Send documents with malware macros |
| Front information acquisition and environment preset | May relates to DUQU, FLAME[16][17] | Collecting with strike |
| Communications and control | Highly encrypted communication and control system | Relatively easy |
| Malware modules | Large rigorous system module with a high degree of reusability | Module system, has the reusability |
| Anti-analyzed ability | High strength of local encryption, complex invocation mechanism | Relatively simple and easy to analysis |
| Digital signature | Piggybacking digital signatures of three mainstream manufacturers | Without digital signature |
| Attack cost | High development cost High maintenance costs | Relatively low |
Table 8 Contrast of Stuxnet event and Ukraine substation attack
It also reminds us that we need to review again on the so-called APT attacks or Cyber War evaluation standard. The quality of an event does not depend on the stereotype of literal meaning, but the comprehensive factors as deep motivation and ability. As for the attack group, all means are available as long as it can finish the homework. We will still encounter attackers as “Stuxnet” and “Equation”, but the general network attacking tools, commercial malware, modified open source tools, 1Day vulnerability, traditional macro viruses, etc., will also be more likely to be used to attack on key objectives. On the condition that commercial weaponry and open source tools are widely used, it is more difficult to determine the source of attack by malware itself. And on a more offensive and defensive posture, underground infrastructure of black industry is forming, and a cynical multilateral mechanism of sharing information, and the uncertainty of data flow from ordinary Botnet collection, and therefore become the information source of strategic attacker. And the common malware infection, pirated mirror with weakening security, with malware localization, crackers, etc., are objectively lowered the threshold of attackers. It is childish to relying on threat intelligence to detect advanced threats and ignore some “common” malware infection events.
As the IT managers of key infrastructure, especially the industrial control system, they need to discard the false sense of security of “physical isolation”: the traditional network isolation security is largely ensured by closed space, the confined space scene based on physical security measures increase the attack cost and increase the cost of touch attack. But social infrastructure needs to effectively cover the society in depth, especially as grid that is destined to present a huge physical space covering force system and needs a lot of ways to use unattended equipment. Therefore, these isolated points are that they may be out of work and may be the entrance of an attack.
In key infrastructure defense and input ratio, when people think that the attacks on critical infrastructure will not happen, Ukraine outage event reminds us that most of the instrument panels and control panels are replaced by PC devices which will face more threats. If PC node as SCADA is being attacked, the attacker can almost do everything. In order to guarantee the security of PC node and TCP/IP network in system, the defense ability needs to be improved by network capture and detection, sandbox automated analysis, white list plus security baseline, etc.; improve the IT governance by combining with traditional methods such as firewall, patch and strengthen configuration and anti-virus. At the same time, we also need to put more and more meticulous work in the security of the internal security strategy and management and external supply chain.
Appendix 1: Acknowledgement
Antiy has won the support and help from some experts, scholars and researchers during the whole analysis process of this attack incident. Here we would like to thank Huang Sheng, Professor Wang Yong from the Information Security Department of Shanghai University of Electric Power and student Zheng Xiong from North China Electric Power University for giving advices for the report.
Appendix 2: Relevant HASH samples
XLS with Macro SHA1:
AA67CA4FB712374F5301D1D2BAB0AC66107A4DF1
8C26C70FBFFE7F250AAFF234BE9A014A996930BC
BlackEnergy SHA1:
4C424D5C8CFEDF8D2164B9F833F7C631F94C5A4C
46F901106C7020C860D71E0C7E709E0F5B3DEDD8
Dropbear SSH SHA-1:
166D71C63D0EB609C4F77499112965DB7D9A51BB
VBS SHA-1:
72D0B326410E1D0705281FDE83CB7C33C67BC8CA
KillDisk SHA-1:
16F44FAC7E8BC94ECCD7AD9692E6665EF540EEC4
6D6BA221DA5B1AE1E910BBEAA07BD44AFF26A7C0
F3E41EB94C4D72A98CD743BBB02D248F510AD925
8AD6F88C5813C2B4CD7ABAB1D6C056D95D6AC569
Appendix 3: Timeline of the incident analysis and follow-up
Antiy has formed temporary analysis team since the incident of Ukraine power system was reported. Here is the timeline of the incident analysis and follow-up:
| Time | Description |
|---|---|
| 2015-12-23 | The national power departments of Ukraine were attacked by malware. |
| 2016-01-05 | A joint analysis team was created by Antiy, Beijing Sifang Automation Co. Ltd. and Fudan University after the incident. |
| 2016-01-06 | Started to analyze the relevant samples and collect related reports. |
| 2016-01-09 | Almost finished sample KillDisk of the incident. Then we looked up related materials affected by it to find out whether it involved with industry control configuration, SCADA and HMI. Meanwhile, we found more samples to analyze. |
| 2016-01-10 | Analyzed other samples of the incident. |
| 2016-01-11 | Collected relevant materials of power system for study. Several domestic vendors have released the analysis report on malware BlackEnergy of Ukraine power system. |
| 2016-01 (11-15) | There was news about the incident released one after another. |
| 2016-01-14 | We formed the outline and chapter division. |
| 2016-01-17 | We invited electric power experts to give speeches about the power system. Meanwhile, Ukraine found that the airport has also been attacked by BlackEnergy. |
| 2016-01-18 | We have written the draft of the comprehensive analysis report. |
| 2016-01-23 | Finished preliminary analysis report, and reported to the First Research Institute of the Ministry of Public Security. |
| 2016-02-24 | Released the final version of the Comprehensive Analysis Report of Ukraine Power System. |
Table 9: Timeline of the incident analysis and follow-up
Appendix 4: The time chain and related links
| No. | Time | Vendor/ Institution | Introduction | Link |
|---|---|---|---|---|
| 1 | 2015-12-30 | SANS[18] | Current Reporting on the Cyber Attack in Ukraine Resulting in Power Outage The power outage was described as technical failures taking place on Wednesday, December 23 that impacted a region around Ivano-Frankivisk Oblast. One report suggested the utility began to disconnect power substations for no apparent reason. The same report goes on to describe a virus was launched from the outside and it brought down the "remote management system" (a reference to the SCADA and or EMS). | https://ics.sans.org/blog/2015/12/30/current-reporting-on-the-cyber-attack-in-ukraine-resulting-in-power-outage |
| 2 | 2015-12-31 | Reuters | Ukraine to probe suspected Russian cyber-attack on grid Ukraine investigated a suspected cyber-attack on its power grid, the energy ministry said on Thursday, and blamed on Russia. | http://news.yahoo.com/ukraine-investigate-suspected-computer-attack-energy-grid-142725080.html |
| 3 | 2016-01-01 | SANS[19] | Potential Sample of Malware from the Ukrainian Cyber Attack Uncovered The SANS ICS team recently gained access to a sample of malware that came from the network of the Ukrainian site targeted in the cyber attack that led to a power outage. | https://ics.sans.org/blog/2016/01/01/potential-sample-of-malware-from-the-ukrainian-cyber-attack-uncovered |
| 4 | 2016-01-04 | we live Security | BlackEnergy trojan strikes again: Attacks Ukrainian electric power industry Around half of the homes in the Ivano-Frankivsk region in Ukraine were left without electricity for a few hours on Dec 23, 2015. According to the news media outlet TSN in Ukrainian, the power outage was caused by a “hacker attack” utilizing a “virus”. | http://www.welivesecurity.com/2016/01/04/blackenergy-trojan-strikes-again-attacks-ukrainian-electric-power-industry/ |
| 5 | 2016-01-05 | Symantec | Destructive Disakil malware linked to Ukraine power outages also used against media organizations A highly destructive Trojan (detected by Symantec as Trojan.Disakil), reportedly used in recent attacks against the Ukrainian power grid system, was also earlier used against media targets in the same country. Symantec telemetry confirms that several computers in a major Ukrainian media company were compromised by Disakil in late October and may have been destroyed by the malware. | http://www.symantec.com/connect/blogs/destructive-disakil-malware-linked-ukraine-power-outages-also-used-against-media-organizations |
| 6 | 2016-01-05 | Infosecurity | Sandworm Team Could Be Behind Ukraine Power Grid Attack The suspected cyber-attack on the Ukrainian power grid by Russian hackers could be the work of the Sandworm Team, according to researchers. iSIGHT Partners told Infosecurity that it believes that the Sandworm Team, which previously targeted US and European SCADA systems in 2014, is likely to blame if the BlackEnergy malware is found to be behind the attack, which we previously reported. BlackEnergy is the malware of choice for the group, and renewed BlackEnergy activity has been uncovered throughout the past year in Ukraine, affecting government, telecommunications and energy sector organizations in the country. During Ukrainian elections for instance, BlackEnergy malware was allegedly used in destructive attacks against Ukrainian media. | http://www.infosecurity-magazine.com/news/sandworm-team-ukraine-power-grid/ |
| 7 | 2016-01-05 | ARS technica | First known hacker-caused power outage signals troubling escalation Highly destructive malware that infected at least three regional power authorities in Ukraine led to a power failure that left hundreds of thousands of homes without electricity last week, researchers said. The outage left about half of the homes in the Ivano-Frankivsk region of Ukraine without electricity, Ukrainian news service TSN reported in an article posted a day after the December 23 failure. The report went on to say that the outage was the result of malware that disconnected electrical substations. | http://arstechnica.com/security/2016/01/first-known-hacker-caused-power-outage-signals-troubling-escalation/ |
| 8 | 2016-01-06 | DatacenterDynamics | Alleged hacker attack brings down power grid in Ukraine Hackers have allegedly brought down the power grid in Ivano-Frankovsk, Ukraine, marking the first time such an attack has been successfully carried out in the wild. According to the local news agency TSN, on 23 December more than half of the residents of the region were left without electricity for several hours. | http://www.datacenterdynamics.com/security/alleged-hacker-attack-brings-down-power-grid-in-ukraine/95448.article |
| 9 | 2016-01-07 | isight partners | Sandworm Team and the Ukrainian Power Authority Attacks The SANS ICS blog confirms conclusions previously reached by iSIGHT regarding the nature of the Ukrainian attacks (specifically the role of destructive malware and phone disruption) and attribution to Sandworm Team. iSIGHT Partners believes this incident is a milestone because it is the first major cyber-attack to substantially affect the civilian population and because of the overwhelming importance of the grid to multiple reliant sectors. Furthermore, Sandworm Team’s previous interest in US and European critical systems underscores the threat they pose (see below for more on Sandworm Team.) | http://www.isightpartners.com/2016/01/ukraine-and-sandworm-team/ |
| 10 | 2016-01-09 | SANS[20] | Network coordinated attack -- The Deduction and Enlightenment of Ukraine Power Outage Information security organization SANSICS made it clear that the power outage in Ukraine was identified as a network coordinated attack in January 9, 2016. | http://ics.sans.org/blog/2016/01/09/confirmation-of-a-coordinated-attack-on-the-ukrainian-power-grid?utm_source=hs_email&utm_medium=email&utm_content=25135530&_hsenc=p2ANqtz-87XLhYBXFcESdxOIJIB8DSoYBZ5sPrfHQv9xNUp11BwFsfcUBouRDj-R7y6YcJY2BsrUeKvRVbwO4lPcVAPgHLmDrj7w&_hsmi=25135530 |
| 11 | 2016-01-14 | McAfee | Updated BlackEnergy Trojan Grows More Powerful In late December, a cyberattack caused a power outage in the Ukraine, plunging hundreds of thousands of citizens into darkness for hours. Threat researchers soon confirmed that the BlackEnergy malware package, first developed in 2007, was the culprit. They also discovered that the malware has been significantly upgraded since its first release. | https://blogs.mcafee.com/mcafee-labs/updated-blackenergy-trojan-grows-more-powerful/ |
| 12 | 2016-01-19 | Hackread | Ukraine Airport’s Computer Networks Infected with Malware The discovery was made public by a report from Reuters. The report stated that the IT network of Boryspil International Airport, which is located nearby Kiev, has been infected by malware. | https://www.hackread.com/ukraine-airports-computer-networks-infected-with-malware/ |
| 13 | 2016-01-20 | we live Security | New wave of cyberattacks against Ukrainian power industry The cyberattacks against the Ukrainian electric power industry continue. Yesterday (January 19th) we discovered a new wave of these attacks, where a number of electricity distribution companies in Ukraine were targeted again following the power outages in December. What’s particularly interesting is that the malware that was used this time is not BlackEnergy, which poses further questions about the perpetrators behind the ongoing operation | http://www.welivesecurity.com/2016/01/20/new-wave-attacks-ukrainian-power-industry |
| 14 | 2016-02-12 | CNN | U.S. official blames Russia for power grid attack in Ukraine Russia was behind a December cyber-attack on Ukraine's power grid that caused widespread power outages, a senior Obama administration official said Thursday. Elizabeth Sherwood-Randall, deputy Energy Secretary, made the comments to a gathering of electric power grid industry executives, according to an U.S. official familiar with her presentation. | http://edition.cnn.com/2016/02/11/politics/ukraine-power-grid-attack-russia-us/ |
| 15 | 2016-02-13 | Trend Micro | BlackEnergy infected also Ukrainian Mining and Railway Systems BlackEnergy was in the headlines when the security industry examined the power outage occurred in Ukraine in December 2015. | http://securityaffairs.co/wordpress/44452/hacking/blackenergy-mining-and-railway-systems.html |
Table 10: The time chain and related links
Appendix 5: References
- Ukraine media: Из-за хакерской атаки обесточило половину Ивано-Франковской области
- cys-centrum:Киберугроза BlackEnergy2/3. История атак на критическую ИТ инфраструктуру Украины
https://cys-centrum.com/ru/news/black_energy_2_3
- ESET:BlackEnergy by the SSHBearDoor: attacks against Ukrainian news media and electric industry
- BlackEnergy trojan strikes again: Attacks Ukrainian electric power industry
- BlackEnergy and the Ukrainian power outage: What we really know
- New wave of cyberattacks against Ukrainian power industry
http://www.welivesecurity.com/2016/01/20/new-wave-attacks-ukrainian-power-industry/
- Arstechnica: First known hacker-caused power outage signals troubling escalation
- Wikipedia: Stuxnet
https://en.wikipedia.org/wiki/Stuxnet
- Antiy: Report on the Worm Stuxnet Attack
https://www.antiy.net/p/stuxnet-analysis/
- Wikipedia: Equation Group
https://en.wikipedia.org/wiki/Equation_Group
- Antiy: A Trojan That can Modify the Hard Disk Firnware ——A Discovery to the Attack Components of the EQUATION Group
https://www.antiy.net/p/a-trojan-that-can-modify-the-hard-disk-firmware/
- Antiy: Analysis on the Encryption Techniques of EQUATION Components
https://www.antiy.net/p/analysis-on-the-encryption-techniques-of-equation-components/
- Antiy: A Comprehensive Analysis Report on Sandworm-Related Threats (CVE-2014-4114)
- iSIGHT discovers zero-day vulnerability CVE-2014-4114 used in Russian cyber-espionage campaign
http://www.isightpartners.com/2014/10/cve-2014-4114/
- SSH DropBear
https://matt.ucc.asn.au/dropbear/dropbear.html
- Wikipedia:Flame
https://en.wikipedia.org/wiki/Flame
- Antiy: Analysis on the Flame
- Current Reporting on the Cyber Attack in Ukraine Resulting in Power Outage
- Potential Sample of Malware from the Ukrainian Cyber Attack Uncovered
- SANS:Confirmation of a Coordinated Attack on the Ukrainian Power Grid
Appendix 6: The relevant research Antiy has done in industry control field
The Microelectronics and Embedded Security R&D Center of Antiy (Antiy MES R&D Center) has been committed to the research in the field of hardware security and made continuous personnel investment. Therefore, Antiy has better technology accumulation after many years of hard work in the field of industrial control security. From the earliest analysis on Stuxnet event to the security research of railway system, the security threat research of hydropower system and the new threat exploitation of signal security, Antiy MES R&D Center has been continuously tracking the latest hardware security incidents and providing the latest hardware security threat analysis.
- “Stuxnet” incident and related analysis
Antiy was one of the earliest vendors that provide early warnings for Stuxnet threats. The relevant analysis work of Antiy was regarded as the most detailed and thorough.
The main accomplishments are as follows:
- The trigger and simulation of conditional propagation of Stuxnet
- The real exhibition and analysis of the influential process of PLC and centrifuge by Stuxnet
- Homology determination and analysis between Stuxnet and Duqu
- The follow-up analysis on Flame
In order to exhibit the function process of PLC and centrifuge by Stuxnet, Antiy established “the simulation environment of industry control system of Antiy” which can embody the structure and industry control environment. The environment includes the simulation presentation of operation environment and real-time monitor. It can finish several operation process presentations and the offensive and defensive demo. The following figure is the industry control experiment zone established by Antiy and the simulation environment.
Figure 41 The simulation environment of Antiy industry control system
2. Seucurity research of railway system
Antiy has made special report with long passage about the potential security issues faced by high-speed rail. The report includes the security threat analysis on the following aspects of high-speed rail: the tractive power supply system, the environment monitoring system, the train control system, the train control center system TCC, the shunting monitoring system and the vehicle identification system.
Figure 42 The train control center system TCC
3. The security threat research of hydropower system
Antiy has established the “Simulation Environment of Antiy Small Hydropower Demonstration System” based on hydropower system. The environment is composed of engineer station, operator station, SCADA server, contact manager and PLC control system, which embodies the real work environment of hydropower system and makes contribution to the deep study and analysis about the security issues of power system.
Figuer 43 Simulation Environment of Antiy Small Hydropower Demonstration System
4. The new exploitation of hardware and signal security
Antiy MES R&D Center has paid continuous attention to the new threats of hardware signal field and presented the research results in several years of conferences of XCON, ISF and XDEF respectively.
- Host attack that based on peripherals (XCON 2008)
During XCON 2008, Antiy restored the fact that the devices sale to foreign countries by America has been implanted with “virus chip” based on the US-Iraq War. Once the war started, America can launch the machine of “virus chip” remotely. After the war was started, America military firstly carried out the electronic war against Iraq military base and started the “virus chip” which can connect to the printer path to attack the host and make the host execute pre-determined operations in order to realize the function of controlling and damaging the host.
Figure 44 The component of virus
- Monitoring of Bluetooth signal (XCON 2009)
Regarding the data security of common 2.4GHz wireless keyboard as the blueprint, Antiy has explained the potential risks and remote monitoring of the low-cost 2.4GHz wireless keyboard through cracking, monitoring and restoring the input data of a 2.4GHz wireless keyboard so as to access the important information that user has input, which warns that the insecurity of wireless keyboard has become real.
Figure 45 The cracked and monitored 2.4GHz wireless keyboard
- The field bus security of industry control system(ISF 2011)
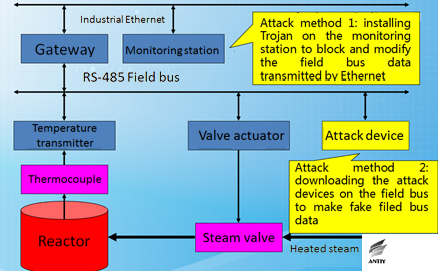
Antiy analyzed on the field bus security of industry control system during ISF conference in 2011. Fieldbus is the name of a family of industrial computer network protocols used for real-time distributed control and follow some or all the communication protocols of connecting examples of ISO and OSI development system. The report provided by Antiy has gave effective attack methods and some suggestions for advancing current field bus security though the link of temperature control of chemical plant reactor.
Figure 46 The attacking diagram of temperature measurement and control link of the chemical plant reactor
- The security of software defined radio (ISF 2012)
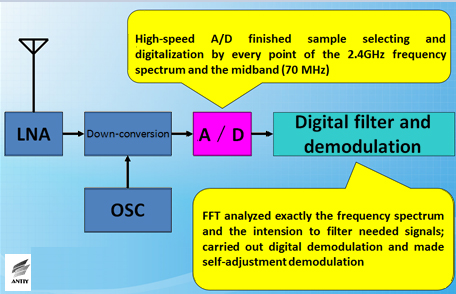
Antiy analyzed the wireless communication security of software defined radio technology during the ISF conference in 2012. The most basic signal of wireless communication is RF which is formed by adjusting baseband signal to carrier. Finally, all the signals send and received by antenna belong to RF. Applying software defined radio to handle RF signal can be multiplier for attacks against wireless communication.
Figure 47 The structure diagram of handling RF and IF signals by using defined radio
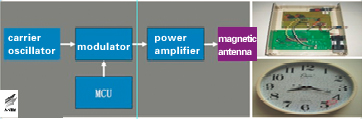
- The distraction and attack against long wave timing signal (XCON 2012)
Antiy presented the time security risks by making the time security as the blueprint during XCON 2012. The report presented by Antiy discovered the fact that the industrial and civic timers were out of the security range except for PC scenarios. It also discussed, analyzed and summarized the phenomenon with some thinking of the research team and the distraction demo.
Figure 48 The attacking device and frame and the attacked clock
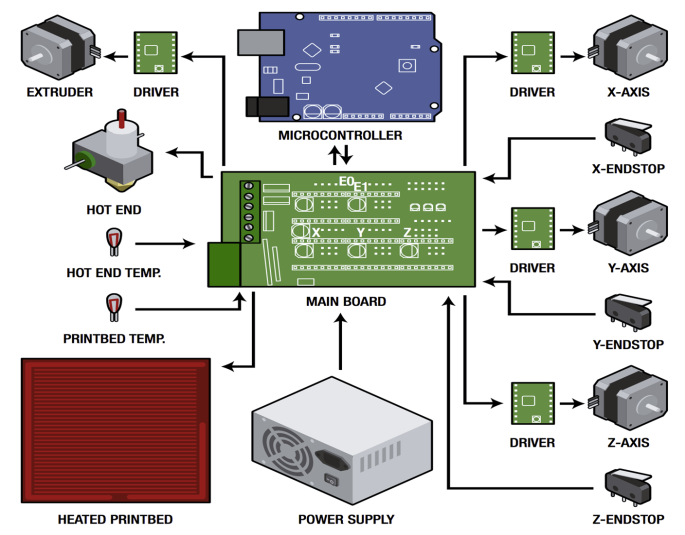
- The security of 3D printers (XCON 2013)
Antiy has introduced the relevant file structure, instruction format, operation environment and processing of recent emerging technologies of 3D printing and three dimensional modeling and rapid prototyping comprehensively during XCON 2013. Antiy analyzed the security vulnerabilities of 3D printing technology and potential influence. It also discussed the attack thinking, method and possibility of 3D printer and 3D-printed objects.
Figure 49 Electrical structure diagram of 3D printer
- Analysis and defense solutions of short range wireless attack that based on software defined radio (XDEF 2013)
During the XDEF conference in 2013, Antiy analyzed the short range wireless attack that based on software defined radio and provided complete software and hardware solution of attacking 433MHz short range communication (such as the car keys ).
Figure 50 Diagram of software defined radio against hardware frame
- The security of wireless signals (XCON 2014)
During XCON 2014, Antiy summarized several signal transmission forms and exploitation measures, and discussed related privacy leaks and protection issues. The research team showed its trying for detection, positioning and communication payload feature identification of several signals except for Wi-Fi. It also demonstrated the positioning and identification of wearable device signal.
Figure 51 A variety of security factors that need to be thought about in short range wireless communication
- The security of smart home (XCON 2015)
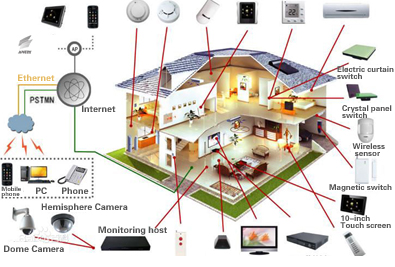
Antiy has analyzed and researched the information security of smart home during XCON 2015. The research team showed the analysis of software and hardware structure of smart cleaning robot and explained the potential risks. The report displayed by Antiy was expected to arouse the attention for smart home security through showing the HACK progress to the smart cleaning robot.
Figure 52 Diagram of modern smart home
Appendix 7: About Antiy
Starting from antivirus engine research and development team, Antiy now has developed into an advanced security product supplier with four research and development centers, nationwide detection and monitoring ability as well as products and services covering multiple countries. With a fifteen-year continual accumulation, Antiy has formed massive security knowledge and promoted advanced products and solutions against APT with integrated application of network detection, host defense, unknown threat identification, data analysis and security visual experiences. With the recognition of technical capacity by industry regulators, customers and partners, Antiy has consecutively awarded qualification of national security emergency support unit four times and one of the six of CNNVD first-level support units. Antiy detection engine for mobile is the first Chinese product that obtained the first AV – TEST (2013) annual awards and more than ten of the world’s famous security vendors choose Antiy as their detection partner.
More information about antivirus engine: https://www.antiy.net