COMPREHENSIVE ANALYTICAL REPORT ON THE MAJOR VULNERABILITY DISCOVERED IN WPA2 WI-FI SECURITY PROTOCOL
Comprehensive Analytical Report on the Major Vulnerability Discovered in WPA2 WI-FI Security Protocol
Draft: 22:08 PM October 17, 2017
Published: 12:00 PM October 23, 2017
Updated: 12:00 PM October 23, 2017
1 Overview
October 15, Mathy Vanhoef, postdoctoral security researcher at Leuven University in Europe, disclosed the critical vulnerability of the Wireless Network (Wi-Fi) Protection Protocol standard WPA2 [1,2], which allows attackers listen for Wi-Fi traffic between the computer and the access point within the Wi-Fi range. The vulnerability affects the protocol itself and is valid for WPA and WPA2, so all the software or hardware that supports WPA / WPA2 protocol are affected.
After the disclosure of the vulnerability, engineers from Antiy and Lianshi Networks made a quick response, and analyzed it together to form this report.
2 Vulnerability Analysis
WPA stands for Wi-Fi Protected Access, including two standards WPA and WPA2, is a protocol for protection of wireless network (Wi-Fi) [3]. WPA implements most part of the IEEE 802.11i standard, which is the transition plan for replacing the WEP before 802.11i is complete, and then will be replaced by WPA2. Since both WPA and WPA2 are based on 802.11i, they are almost identical at the technical level, with the main difference being that WPA2 requires a more secure CCMP. WPA and WPA2 use the four-way handshake defined in 802.11i, and the client (Station, STA) and access point (AP) authenticate each other with a four-way handshake, and negotiate the session key called Pairwise Transient Key PTK. PTK is generated by Pairwise Master Key (PMK), ANonce, SNonce and both MAC addresses, etc. PMK is generated by the information that both parties know like login password. And the temporary key (Temporal KEY, TK) used for subsequent normal data encryption is derived from PTK. The relationship between each key and parameter is shown in the following figure:
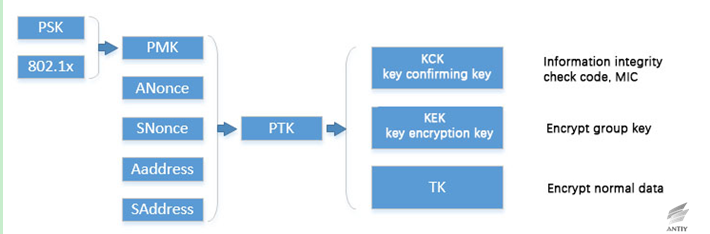
Figure 2‑1 The relationship between four key handshake and parameter in four-way handshake
The process of four-way handshake can be summarized as follows:
1)AP sends its own ANonce to STA;
2)STA generates SNonce and calculates PTK, and then sends SNonce and information integrity check code MIC to AP;
3)AP receives SNonce, calculate PTK (At this time both have PTK), the group key GTK will be encrypted and sent to the STA with MIC;
4)STA receives GTK, installs PTK and GTK, sends ACK to confirm. AP installs PTK after confirming.
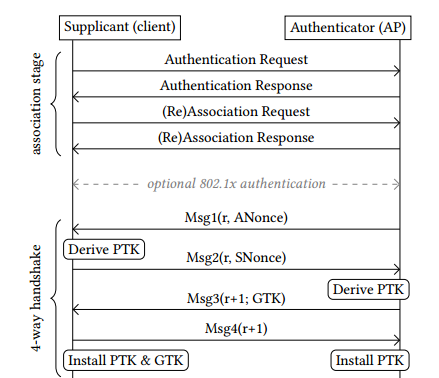
Figure 2‑2 Four-way handshake process
Vanhoef named the disclosed vulnerability attack as KRACK (Key Reinstallation Attack), where attackers use the man in the middle (MITM) to attack the third phase of four-way handshake interaction verification of WPA / WPA2 protocol within the Wi-Fi range. At this point the victim has installed a key, after replaying attacks by MITM, it will force victims to use the previous keystream to encrypt data. Since WPA / WPA2 is symmetric encryption, it is possible to obtain reusable keystreams through ciphertext of simple plaintext. The attacker can decrypt Wi-Fi traffic data once the keystream is obtained.
2.1 Principles
The core use of this vulnerability is the key reinstallation, which is based on the four-way handshake process when the connection is established in the WPA / WPA2 protocol. During the four-way handshake, the AP and the client will negotiate an encryption key for encrypting the next communication data, and the client verifies the MIC after receiving the third handshake from the AP (message 3). If the encryption key is installed correctly to encrypt the normal data frame, and send a response to the AP as a confirmation. According to the protocol rules, if the AP can not receive the confirmation correctly, it will cause the data to be retransmitted and resend the message 3. The client will reinstall the same session key each time message 3 is received. An attacker can use this handshake process to send a message 3 in a violent incremental manner, thereby forcing the resetting of the number of incremental packets used by the data privacy protocol and receiving the replay counter, resulting in key reuse. An attacker could replay, decrypt and / or fake a packet in this way.
KRACK attacks can be divided into four kinds of scenarios:
1) Key reinstallation attack when the client (victim) accepts the unencrypted retransmission of message 3;
2) Key reinstallation attack when the victim only accepts the encrypted retransmission of message 3;
3) Instant key installation for handshake attack on the group key;
4) The delay key installation of the group key handshake.
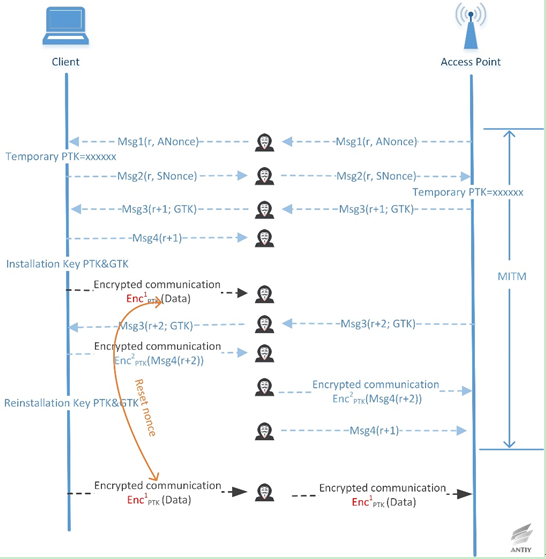
Figure 2‑3 Key reinstallation attack when the client (victim) accepts the unencrypted retransmission of message 3
Figure 2-3 shows the attacker decrypts a ciphertext packet attack process. If the attacker knows the plaintext of the first transmitted ciphertext packet, the keystream used to encrypt the plaintext data can be recovered. Since the design of the four-way handshake protocol allows PTK and GTK to be reinstalled by retransmitting the message 3 and resetting the nonce value of the packet to be sent, therefore the client will encrypt the next packet with the same key stream, leading to the next ciphertext packet sent by the client decrypted.
The above decryption process is based on the premise that the attacker knows the first packet plaintext, but the attacker sometimes can not predict all the field values in the packet (such as a random field that may exist), so the attacker may need to retransmit the message 3 to collect more data for decryption. Figure 2-3 shows only the attack process to restore a ciphertext packet, but the attacker can pass multiple retransmissions and select the retransmission time (waiting for the client to send enough data before retransmission), or even force the client to re-execute the four-way handshake protocol to achieve the purpose of decrypting multiple packets through authenticating the client.
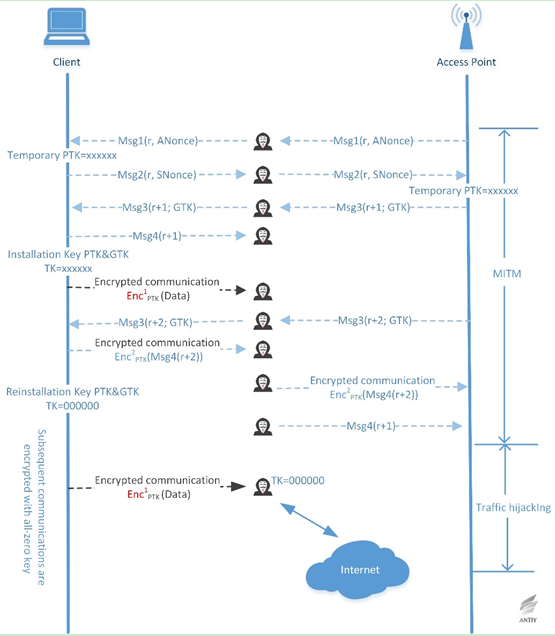
Figure 2‑4 Use all-zero key to replace real key attack when the unencrypted retransmission of message 3 is accepted
Since the error implementation of key reinstallation attack after version 2.4 and 2.5 of wpa_supplicant (Android 6 and the above) receives the retransmitted message 3, so that encryption key TK is set to all zero after that. This error greatly simplifies the ciphertext recovery attack, based on the all-zero key, the attacker can decrypt the subsequent packets sent by the client without the need of knowing the plaintext. Considering the above condition, the attacker can achieve the client traffic hijacking, monitoring and tampering all the data sent by the client after forcing it to use all-zero key by MITM.
2.2 The cipher analysis of nonce reuse in KRACK attack
The consequences of the Nonce reuse are closely related to the confidentiality protocol of the data used. The data encryption algorithms adopted by TKIP, CCMP and GCMP are stream cipher RC4, authenticated encryption algorithm AES-CCM and AES-GCM, respectively. The encryption part of AES-CCM and AES-GCM is based on the stream encryption of CTR mode. It can be considered that all these three protocols adopted stream encryption, that is, the key stream generated by the plaintext data and the algorithm get XOR bit by bit to achieve ciphertext data. The problem with stream encryption is always generating the same keystream when reusing nonce with key-fixed conditions. This feature can be used to decrypt the packet.
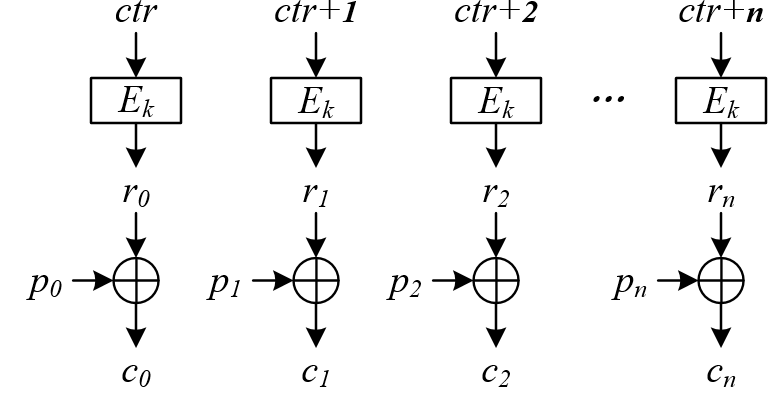
Figure 2‑5 The diagram of the encryption process in CTR mode
The diagram above shows the process of encrypting plaintext message ![]() by using the key k and counter ctr in CTR mode, of which
by using the key k and counter ctr in CTR mode, of which ![]() represent the packet length, respectively (When using AES algorithm, it is 128 bit, and the length of the plaintext message is not necessarily the integer multiples of the packet length). It is worth noting that some of the details involved in the application of the CTR mode for encryption are not shown in the CCM and GCM modes. In the case of correct use, the value of the counter ctr is continuously accumulative (the value does not repeat!) and generates the key stream
represent the packet length, respectively (When using AES algorithm, it is 128 bit, and the length of the plaintext message is not necessarily the integer multiples of the packet length). It is worth noting that some of the details involved in the application of the CTR mode for encryption are not shown in the CCM and GCM modes. In the case of correct use, the value of the counter ctr is continuously accumulative (the value does not repeat!) and generates the key stream ![]() with strong pseudo random characteristics under the action of algorithm and key. Then, the correspondent ciphertext is:
with strong pseudo random characteristics under the action of algorithm and key. Then, the correspondent ciphertext is:
![]()
The encryption process based on the stream cipher RC4 in TKIP is similar with this, so we will not repeat here.
In the attack of KRACK, it is possible to force the victim to reuse nonce by replaying message 3, resulting in the repetition of the same counter ctr value in the above encryption process. In the condition of the same key and the same counter ctr, it will generate the same value of key stream ![]() . Then the attacker can decrypt the packet accordingly. We use KeyStream to represent the key stream, P1 and P2 to represent the plaintext data. If the KeyStream, P1, and P2 have the same bit length, the ciphertexts corresponding to the plaintext are:
. Then the attacker can decrypt the packet accordingly. We use KeyStream to represent the key stream, P1 and P2 to represent the plaintext data. If the KeyStream, P1, and P2 have the same bit length, the ciphertexts corresponding to the plaintext are:
C1 = P1 ^ KeyStream
C2 = P2 ^ KeyStream
of which ^ expresses the XOR operation bit by bit. The attackers can collect the ciphertext C1and C2. If the attackers know that the ciphertext corresponds to the plaintext P1, then they can restore the information of the plaintext P2:
:P2 = C2 ^ keystream = C2 ^ (P1 ^ C1)
In practice, packets with known content can be found usually, so it can be considered that the ciphertext packets can be decrypted according to the above process when reusing nonce in the condition of fixed key. Even if the packets with known content cannot be accessed, it may be decrypted to restore the plaintext in the condition of having enough knowledge of the message type (for instance, the message belongs to English character). It is worth noting that the nonce reuse will cause the ciphertext packets to be decrypted, but it would not lead to the leak of key TK, PTK, PMK and the login password of WiFi. Therefore, the WPA2 password system is only bypassed and has not been breached. The security of block cipher algorithm (AES) itself has ensured the encryption key k cannot be leaked even in the condition of known input ![]() and output
and output ![]() .
.
The three data encryption protocols of TKIP, CCMP and GCMP also provide data integrity protection except for data confidentiality. However, reusing nonce in different data encryption conditions will bring different levels of security risks in terms of data integrity protection.
When using the TKIP protocol, the attacker can further attack the Michael algorithm to access the corresponding MIC key after decrypting the complete TKIP packet (including the MIC field). This is due to the vulnerability of the Michael algorithm itself. In the conditions of given plaintext data and MIC value, the attacker can restore the MIC key. Then the attacker can forge a data frame in the data transmission direction (TKIP uses different MIC keys in different data transmission directions) with the recovered MIC key.
When using CCMP protocol, although studies have demonstrated the possibility of data forgery attack in the condition of reusing nonce, the attack is on the theoretical level and difficult to generate real forgery packet in practice, which can only perform replay attacks and packet decryption.
The security problem caused by nonce reuse is most serious when using the GCMP protocol. The nonce reuse enables the attacker to recover the authentication key (H) in the GCM mode. Since the GCMP protocol uses the same key for data protection in both directions of the data transmission, this endows the attacker the ability to forge packet in both directions of the data transmission. As a working mode of authentication encryption, the GCM mode is a combination of the CTR encryption algorithm and the GHASH authentication algorithm. The CTR algorithm section encrypts directly by adopting the key k passed to the GCM mode, while the authentication subkey H required for the GHASH operation is the 128-bit ciphertext value obtained by the AES algorithm using the key k to encrypt all 128 bits of all 0 plaintext. The French cryptologist Joux pointed out that the attacker can recover the value of the authentication subkey H (note that the input key of GCM cannot be inferred from the value of H, which is guaranteed by the security of the AES algorithm itself) when reusing nonce. After the attacker gets the value of H, the data integrity provided by GCMP performs practically no function, so the attacker can forge the packet.
Overall, the KRACK attack has a significant impact on TKIP and GCMP, and attackers can replay, decrypt, and forge packets. Though the attackers cannot forge CCMP, as long as they can get the serial number, they could hijack the TCP stream and inject the malicious data based on the characteristics of the TCP/IP protocol, which also results in serious consequences.
3 Vulnerability Impacts and Response
This vulnerability allows adversary to decrypt Wi-Fi flow data, reassemble packet, hijack TCP connections, and inject malicious content into HTTP connections, etc. KRACK attacks are common, which apply to all types of devices that connect or use the Wi-Fi network through WPA/ WPA2. It is effective to personal and corporate networks and any cryptographic kits (WPA-TKIP, AES-CCMP and GCMP), including Android, iOS, Windows, Linux, MacOS, OpenBSD, embedded and Internet of Things (IoT) devices, especially for Android 6 and more advanced versions. Researchers have indicated that it may make a “perfect attack” targeted to wpa_supplicant of Android 6 system client, the attack technology of which is easy to implement. According to mobile security statistics of Antiy, Android 6 accounts for about 41.9% of Android devices.
Due to the large-scale impact of this vulnerability, vendors have initiated responses or released patches. Responses made by some vendors are shown as follows:
Table 3‑1Responses Made by Some Vendors[4]
| Vendor’s Name | Official Response | Notes | Date of Last Detection | Date of Recent Update | |
| Apple | No official response; an unofficial response released through twitter. | Apple has confirmed wpa2 vulnerability,and fixed the vulnerability in iOS, acOS, tvOS, and watchOS of beta version. | Oct. 17, 2017 | Oct. 17, 2017 | |
| Arch Linux | wpa_supplicant,hostapd | N/A | Oct. 16, 2017 | Oct. 16, 2017 | |
| AVM | Link | This security issue is being investigated and will be updated when needed to be released. EOM and EOS products will also be updated according to the content in the link. | Oct. 17, 2017 | Oct. 17, 2017 | |
| Cisco | Link | Cisco said wireless products were affected by these vulnerabilities. | Oct. 16, 2017 | Oct. 16, 2017 | |
| Debian | Link | Patches are added to fix the WPA protocol vulnerability.(CVE-2017-13077,CVE-2017-13078,CVE-2017-13079,CVE-2017-13080,CVE-2017-13081,CVE-2017-13082,CVE-2017-13086 ,CVE-2017-13087,CVE-2017-13088). | Oct. 16, 2017 | Oct. 16, 2017 | |
| Fedora | Link | Fixed version, which can be installed manually. | Oct. 17, 2017 | Oct. 17, 2017 | |
| FortiNet | Link | FortiAP 5.6.1 is used to fix the following vulnerabilities:
CVE-2017-13077 CVE-2017-13078 CVE-2017-13079 CVE-2017-13080 CVE-2017-13081 CVE-2017-13082 |
Oct. 16, 2017 | Oct. 16, 2017 | |
| FreeBSD Project | Link | It is based on wpa_supplicant 2.5. It is recommended to use a wired connection or install the security/ wpa_supplicant port or package until the fix patch is complete. | Oct. 16, 2017 | Oct. 16, 2017 | |
| HPE Aruba | Link | N/A | Oct. 16, 2017 | Oct. 16, 2017 | |
| Intel Corporation | Link | N/A | Oct. 16, 2017 | Oct. 16, 2017 | |
| LineageOS | Link | N/A | Oct. 17, 2017 | Oct. 17, 2017 | |
| Linux | Patch Link | wpa_supplicant 2.4 and more advanced version have been affected. wpa_supplicant v2.6 has been affected. | Oct. 16, 2017 | Oct. 16, 2017 | |
| Microsoft | Patch Link | When you click the link, accept EULA, and then click the link again. | Oct. 16, 2017 | Oct. 16, 2017 | |
| Mikrotik | Link | The fixed version was released last week, so if you often upgrade the device, you do not need further operations. | Oct. 16, 2017 | Oct. 16, 2017 | |
| OpenBSD | Link | For OpenBSD 6.1 and 6.0, an errata patch for the wireless stack has been released. A state transition error may cause the old WPA key reinstallation. The binary update for amd64 and i386 platform can be obtained through the syspatch procedure. The source code patch can be found on the corresponding errata page. Since this will affect the kernel, it will need to be restarted after patching. | Oct. 16, 2017 | Oct. 16, 2017 | |
| Red Hat, Inc. | This vulnerability may impact the wpa_supplicant version provided by Red Hat Enterprise Linux 6和7 LINK, Link | N/A | Oct. 16, 2017 | Oct. 16, 2017 | |
| Sophos AP | Link | N/A | Oct. 17, 2017 | Oct. 17, 2017 | |
| SUSE/openSUSE | Link | N/A | Oct. 16, 2017 | Oct. 16, 2017 | |
| TP-Link | Link | N/A | Oct. 17, 2017 | Oct. 17, 2017 | |
| Ubuntu | Link | In Ubuntu 17.04,Ubuntu 16.04 LTS and Ubuntu 14.04 LTS, Wpasupplicant and hostapd can be directly updated. | Oct. 16, 2017 | Oct. 16, 2017 | |
| WatchGuard | Link | Oct., 15, 2017 (Sunday): AP120,320,322,420: 8.3.0-657 version, only cloud model.
Oct., 30, 2017 (Monday): AP300: 2.0.0.9 version,AP100,102,200, 1.2.9.14 version,AP120,320,322,420: 8.3.0-657 version,non-cloud (GWC Model). |
Oct. 16, 2017 | Oct. 16, 2017 | |
| WiFi Alliance | Link | Users should refer to the Wi-Fi device vendor’s website or security advice to determine whether their device has been affected and has installed available updates. | Oct. 16, 2017 | Oct. 16, 2017 | |
Note:
If the link in the table cannot be opened, you can get it from reference 4.
We have analyzed eight patches mentioned in the above table, the role of the principle of each patch is as follows:
TK should be avoided being reinstall to the driver part in the handshake stage Reassociation-Response, thus to prevent the key reinstallation attack.
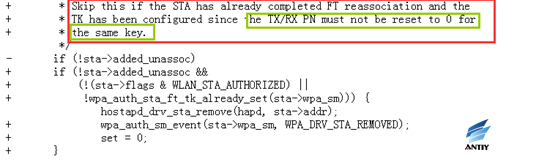
In addition, the configuration is allowed only when the TK confirmation has been uninstalled and the reinstallation is not allowed (only one configuration is allowed)
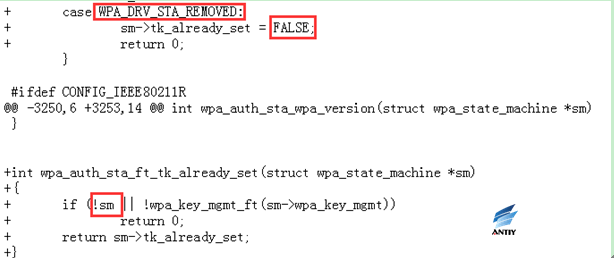 2. rebased-v2.6-0002-Prevent-reinstallation-of-an-already-in-use-group-ke.patch
2. rebased-v2.6-0002-Prevent-reinstallation-of-an-already-in-use-group-ke.patch
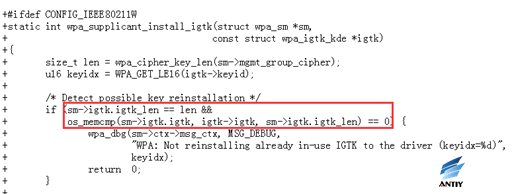
Tracking the GTK and IGTK currently in use, when a message of the first handshake phase or a WNM-sleep mode response is received (possibly retransmitted), not installing a new key if the key is already in use. This prevents the attacker from cheating the client to reset or change the behavior of the sequence counter associated with the group key.
When installing igtk:
When WNM – sleep mode responds:
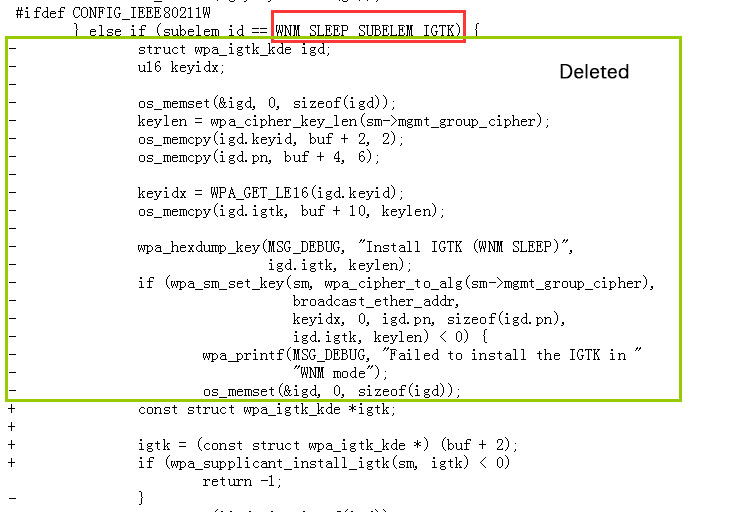 3. rebased-v2.6-0003-Extend-protection-of-GTK-IGTK-reinstallation-of-WNM-.patch
3. rebased-v2.6-0003-Extend-protection-of-GTK-IGTK-reinstallation-of-WNM-.patch
This patch traces the last configured GTK / IGTK value, in conjunction with the EAPOL-Key frame and the WNM-sleep mode frame, because when the GTK / IGTK of these two different mechanisms changes, tracking a single value is not sufficient to detect the possible behavior of the key reconfiguration.
Record Igtk in both modes:

Record Igtk in both modes:
 4. rebased-v2.6-0004-Prevent-installation-of-an-all-zero-TK.patch
4. rebased-v2.6-0004-Prevent-installation-of-an-all-zero-TK.patch
Track whether the PTK has been installed to the driver, and TK has been cleared from memory. This prevents the attacker from cheating the client to install all-zero TK.
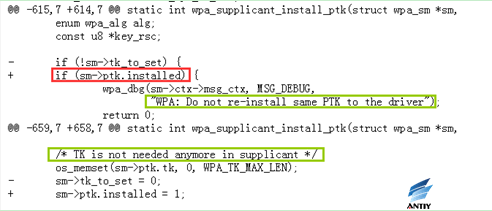 5. rebased-v2.6-0005-Fix-PTK-rekeying-to-generate-a-new-ANonce.patch
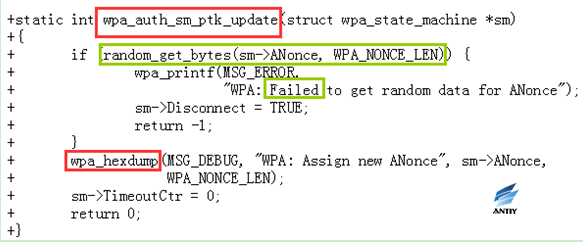
5. rebased-v2.6-0005-Fix-PTK-rekeying-to-generate-a-new-ANonce.patch
The authorization state machine for PTK rekeying bypasses the authenication2 state while the nonce is generated, and enters the PKT-START state directly, since there is no need to re-confirm the PMK at this time, it may result in nonce not being “random” or other problems.
For this problem, when you switch to the PTKSTART state, a new ANonce is generated.
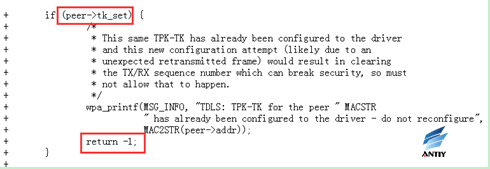
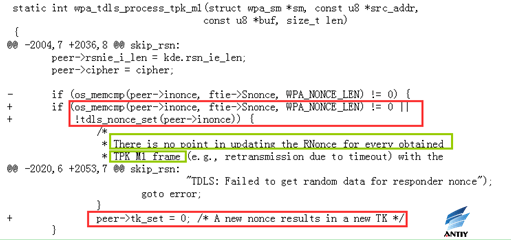
 6. rebased-v2.6-0006-TDLS-Reject-TPK-TK-reconfiguration.patch
6. rebased-v2.6-0006-TDLS-Reject-TPK-TK-reconfiguration.patch
When TPK-TK is successfully configured, it is forbidden to reconfigure the same parameters to the drive.
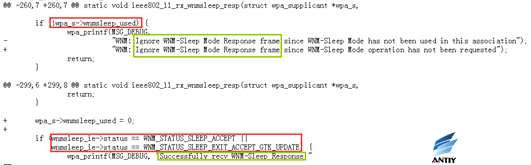
 7. rebased-v2.6-0007-WNM-Ignore-WNM-Sleep-Mode-Response-without-pending-r.patch
7. rebased-v2.6-0007-WNM-Ignore-WNM-Sleep-Mode-Response-without-pending-r.patch
If WNM-sleep mode is not already used, the corresponding WNM-sleep mode request is ignored. This avoids unexpected retransmission of data frames.
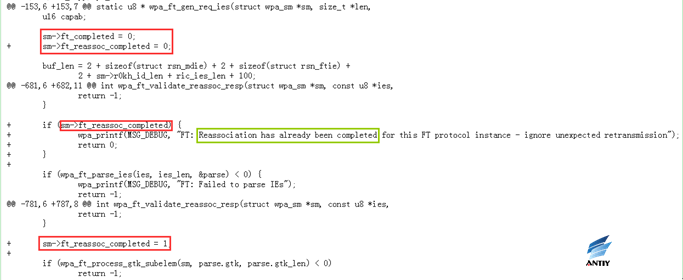
 8. rebased-v2.6-0008-FT-Do-not-allow-multiple-Reassociation-Response-fram.patch
8. rebased-v2.6-0008-FT-Do-not-allow-multiple-Reassociation-Response-fram.patch
The driver part opens a connection event unless the client explicitly requests a new one. However, reconfiguring the same pair of keys or group keys can lead to nonce reuse problems, so additional checks are required to avoid malicious attacks, including accidental receipt of retransmitted packets due to some environmental factors.
4 Conclusion
KRACK vulnerabilities are mainly used to attack the four-way handshake process of WPA / WPA2. Instead of using AP access point, this kind of attack is against the client. Therefore, it is possible for the user not to update their routers. For ordinary home users, they should pay more attention to the security bulletins from endpoint vendors, and update the configuration or patch, giving priority to update the laptop and smart phones and other clients.
The use of the vulnerability did not destroy the cryptosystem itself, what is actually attacked is the implementation process, so this kind of attack can almost bypass all the security monitoring equipment. In a well-implemented network environment, this vulnerability can be used to make foundation for the follow-up attacks through a good implementation of Wi-Fi.
It is relatively easy for most WPA2 home and commercial wireless application users to upgrade the client. However, it will have a huge impact on millions of IoT wireless devices that are difficult to update. Please keep vigilant, we will continue to pay attention to the relevant events and make active response.
Appendix 1: References
- Mathy Vanhoef, Frank Piessens. Key Reinstallation Attacks.
- Mathy Vanhoef, Frank Piessens. Key Reinstallation Attacks: Forcing Nonce Reuse in WPA2.
https://papers.mathyvanhoef.com/ccs2017.pdf
- WPA.
https://zh.wikipedia.org/wiki/WPA
- Kristate, Vendor Response.
https://github.com/kristate/krackinfo#vendor-response-complete
Appendix 2: About Antiy
Antiy is a leading provider of threat detection and defense technology, whose enterprise mission is to enhance users’ ability to deal with cyberspace threats and improve their awareness of threats. Relying on independent advanced core technologies including series products of threat detection engines and experts team, Antiy can provide users with products, solutions and services related to endpoint protection, traffic monitoring, threat intelligence and situational awareness.
Antiy has fostered nationwide detection and monitoring capability with our products and services covering multiple countries. With effective combination of techniques and products of both big data analysis and security visualization, Antiy expands the group work competence of engineers and shortens the product response cycle by massive automation sample analysis platform. With years’ continual accumulation of massive security threat knowledge library, Antiy promotes the solution of situational awareness and monitoring and early warning that targets against APT and at scale network and critical infrastructure, combining with the experience of integrated application of big data analysis and security visualization.
More than a hundred famous security vendors and IT vendors select Antiy as their partner of detection capability. The antivirus engine of Antiy has provided security protection for nearly a hundred thousand network devices and security devices and more than eight hundred million mobile phones. The mobile detection engine of Antiy was the first Chinses product that won AV-TEST reward in the world, it is the only one whose detection rate is 100% for twice in the Mobile Security Product Test 2015 organized by the international certified authority AV-C.
The technical strength of Antiy has been recognized by industry management organizations, customers and partners. Antiy has consecutively been awarded the qualification of national security emergency support unit five times and one of the six of CNNVD first-level support units.
Antiy is the significant enterprise node of China emergency response system, which has provided early warning, in-depth analysis or systematic solutions for major security incidents, such as Code Red II, Dvldr, Stuxnet, Bash Shellcode, Sandworm, Equation, White Elephant, WannaCry, etc.
| More information about Antiy Labs: | https://www.antiy.net |
| More information about enterprise security company: | http://www.antiy.cn |
| More information about Antiy AVL TEAM: | http://www.avlsec.com
|
Appendix 2: About Lianshi
Lianshi Networks is an innovative service provider focused on business application security and data security. It started the CASB implementation model based on the entrusted security agent technology, and independently developed the CipherGateway service application security gateway, which can integrate the security mechanism (closely related to businesses) to the application system without modifying it. This can nearly build the security capabilities inside for the application, so that enterprises can enrich the application system security features in an unprecedented way, to deal with business application security and data security risks from the start.
| More information about Lianshi: | http://www.ciphergateway.com |
Wechat ID : CipherGateway

