THE ANALYSIS OF EQUATION DRUG —THE FOURTH ANALYSIS REPORT OF EQUATION GROUP
the Analysis of EQUATION DRUG
—the FOURTH analysis REPORT OF Equation group
Antiy CERT
Download 
Draft: January 13, 2017 16:00
Published: January 16, 2017 10:00
Updated: January 25, 2017 14:30
Words for This Version
On the basis of previously published reports, Antiy CERT has provided Module Building Blocks Host Operating figure of Equation Group. This figure displays an assembly of the modules that split the host intelligence job in terms of “atomization”, and we have made deeper analysis of some of the modules. Still, what we have analyzed are only a small part of all the modules.
A few days ago, Antiy CERT released un unfinished analysis report which we tentatively referred to as the “outline”, however, this not because we hope a “prompt action and quick decision”, thus to hastily release a bit of superficial progress, the reason is that we want to get more suggestions and criticisms. Fortunately, the experts gave pertinent and sharp advice on the previous version. This makes us to realize that we are lost (when we analyze the module group from 2007 to 2008) in the same situation as analyzing “Flame”, though we believe ourselves are much soberer than before. This complex collection includes many “jigsaw puzzles”, each of which is with meaningful pattern. We explore one by one and find they can build a huge maze. The reason why the maze is confusing, not because it is a dead end everywhere, but because it looks there are exports everywhere, and all the bricks can not provide the entrants with enough tips. Now, what we hope most is not a pen which can make the mark, but the wings which can fly in the sky to overlook the whole maze. This is certainly a self-expectation to improve analytical methodology, though we do not have wings, we should be trained to consonance.
At present, the building blocks reduction work has just started, and we feel a little pleased to release this report before the Chinese Spring Festival. Network security is bound to be always vigilant and diligent, and our analysis will continue. Even the moment fireworks and firecrackers are rising into dark night, we still need to focus on disassembly code and threat situation.
Here, we want to thank the experts and colleagues for the attention and support and thank customers for choosing our products and services! Happy Spring Festival!
Background
During the past two years, Antiy has released three analysis reports of Equation Group. We made much analysis on a number of its modules and got the report A TROJAN THAT CAN MODIFY THE HARD DISK FIRMWARE —— A Discovery to the Attack Components of the EQUATION Group, [1] in which we analyzed and validate its mechanism to be written in hard disk firmware. The second report is named Analysis on the Encryption Techniques of EQUATION Components [2], in which we have cracked the encryption technology used by the Group. Then is the FROM EQUATION TO EQUATIONS —— Revealing the multi-platform operational capability of Equation Group [3], it is the first published analysis of Equation components for Solaris and Linux systems and it is also the public analysis report to prove the existence of these kinds of “Evils”.
Similar to the research and development of anti-APT products, APT analysis is also based on the accumulation of sufficient knowledge. Just as “Rome can not be built overnight”, what we did about this super and sophisticated Group past is tantamount to “Blind men and an elephant”. Once the errant clues fall into the range we have explored, we can release the achievement reserves quickly; but for a not fully explored field, it will take much more time for to carry on the analysis. Compared to the previously three report from Antiy, this one is a not so formed, thus named as “outline” version. We hope more friendly vendors and teams to pay attention on this Group and dig out the real “thing” behind it.
This report is based on the 61 files [4] of the Group which were released by Shadow Brokers on January 12th, 2017. After analyzing, we find some plug ins of the Equation Group component and DanderSpritZ (RAT) tools are contained in these 61 files. DanderSpritZ is one of the NSA (National Security Agency) spy tools. January 7, Shadow Brokers released Windows attack tool [5] also contains a large number of DanderSpritZ plug ins.
EquationDrug is a very complex module, which has been survival time for nearly 10 years, later replaced by the upgraded GrayFish. EquationDrug to GrayFish forms a platform-level malicious code architecture that has the ability to install and uninstall plug ins. We find more plug ins in EquationDrug from the 61 files. By analyzing and comparing, we observed that these ones are older than those we analyzed, but they are more comprehensive and have never been observed.
Equation Exposure and Results Timeline
Since 2013, Antiy has gradually discovered that there is an attacking organization with full-platform load attacking capability, and correlates and analyzes the related samples. During this process, we can feel the existence of an extremely large and invisible attacking organization. Unfortunately, we did not find what is real in the behind.
In February 2015, Kaspersky Lab exposed an attacking group called Equation Group [6], which was believed to be active for nearly 20 years and probably one of the most complex APT groups currently. Reports from Kaspersky Lab releases this group is the manipulator of Stuxnet and Flame. Contrast the existing clues, we find it is the super group that we have been tracing these years. Therefore, we published two reports to release the mechanism used to be written in hard disk firmware [1]and cracked parts of the encryption algorithms [2].
In March 2015, Kaspersky Lab published another analysis report based on the EquationDrug component (or platform) [7], and indicated the group was one of the major spyware components or platforms used by Equation. It can be dated back to 2001, and has been in use for a long time till today. Its architecture is similar to micro-operating system with kernel mode and user mode, and interacts with a custom interface. The component includes drivers, platform kernels (coordinators) and plug ins. Some of plug ins have unique IDs and version numbers, and are used to define the relevant functions.
In August 2016, a person (or organization) calling himself as “Shadow Brokers” claimed to have taken down espionage organization Equation Group [8], and publicly open auction of what they have got from the Group at the price of one million Bitcoins (about 560 million dollars). “Equation” is considered to be associated with NSA. To prove the authenticity of the successful invasion, Shadow Brokers released the encrypted versions of these tools on the open source project hosting platform GitHub, and intended to make a small amount of them in the form of clear text on January 13.
In August 2016, Kaspersky Lab confirmed that the exposure data were related to Equation by comparing that were exposed by Shadow Brokers [9]. In October, Shadow Brokers re-launched the auction of the attacking tools [10], and added that the data put on GitHub just accounted for 60 percent of what they really own.
In November, Shadow Brokers exposed a list of compromised servers [11], stating that the attackers were related to the NSA. According to the date of the list, the systems were invaded during the period from 2000 to 2010; controlled IPs and domains were distributed in 49 countries, mainly in the Asia-Pacific region; affected countries include China, Japan, South Korea, Spain, the United States, Germany, India and so on. Importing all the data to our early alerting platform Situation Awareness and Monitoring PreAlert, we get the following visualization figure.
The servers mentioned by Shadow Brokers may be Linux, FreeBSD and Solaris, which agrees with what Antiy has clearly stated during two technical meetings in the first half of 2016, namely the samples from Equation are for many systems, including Linux and Solaris. On November 5, we finally released the third analysis report of Equation, which analyzed parts of its payloads for Linux and Solaris.
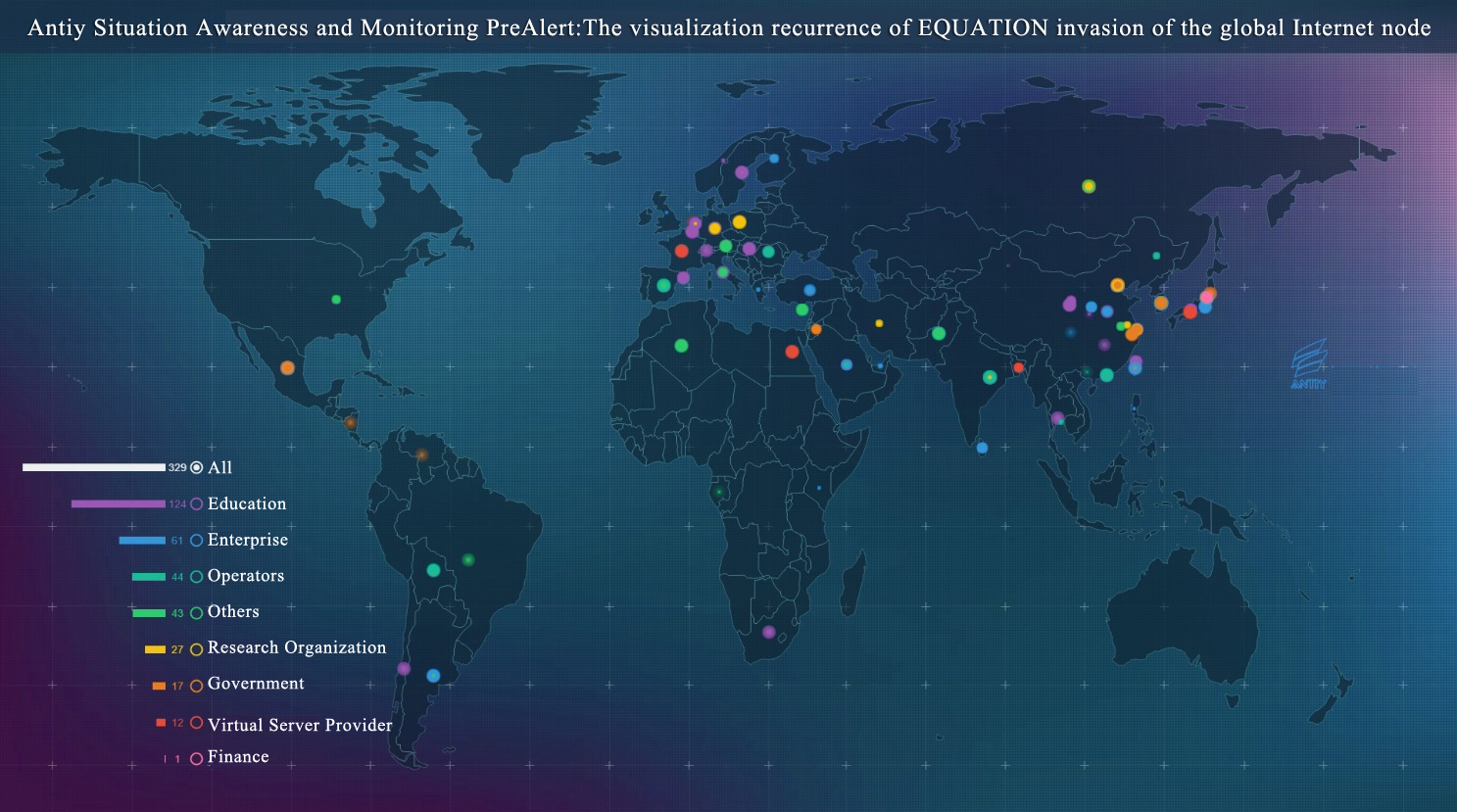
Figure 3-1 Antiy Situation Awareness and Monitoring PreAlert: The visualization recurrence of EQUATION invasion of the global Internet node
Antiy analysis team combed the above information of EQUATION, sorted out the time chain of the exposure and correlation analysis of Equation event.
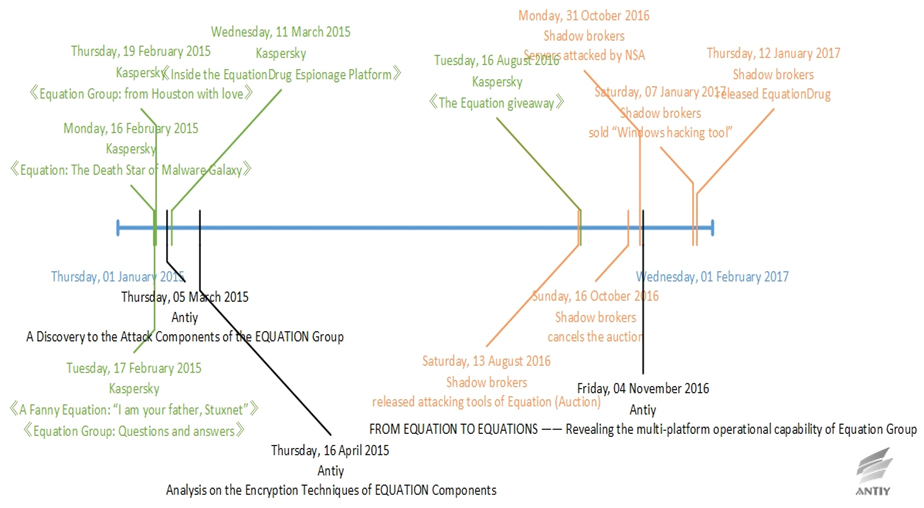
Figure 3-2 Time chain of the exposure and vendor analysis of EQUATION-related information
DanderSpritz Attack Platform
Antiy found that “EquationDrug” platform of EQUATION and “DanderSpritz” mentioned in the leaked documents have some internal links through the analysis of the leaked documents and the previous information on EQUATION.
- The leaked msgkd.ex_、ex_、msgks.ex_and msgku.ex_ are GROK plugins, the plugins or modules of “DanderSpritz”. The plugins have appeared on “EquationDrug” platform. Antiy found that the leaked GROK is the low version of the GROK plugin through the analysis.
- Some data on all kinds of exposed DLL plugins is the plugin ID. The plugin IDs start with 0x79, for example: 0x79A4 and 0x79D8. Similarly, the plugins on “EquationDrug” platform also have built-in IDs. They start with 0x80. There are similarities in the data structure of the plugin derived function parameters for both platforms.
Therefore, we can basically determine that the architecture design of “EquationDrug” attack platform used by EQUATION is the same with “DanderSpritz”. They may use different versions of the code. They may come from the same development team or highly shared resources team.
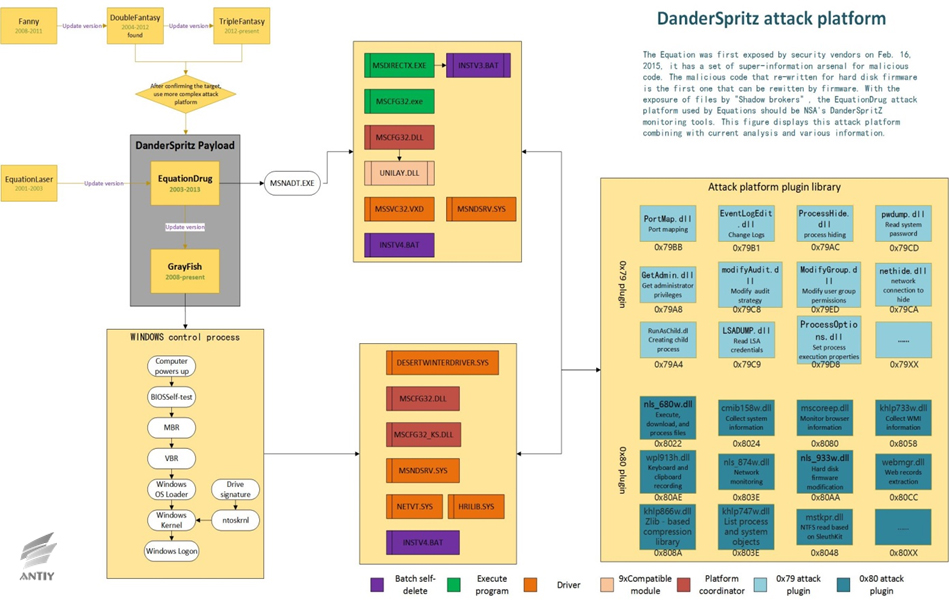
Figure 4-1 DanderSpritz attack platform for EQUATION
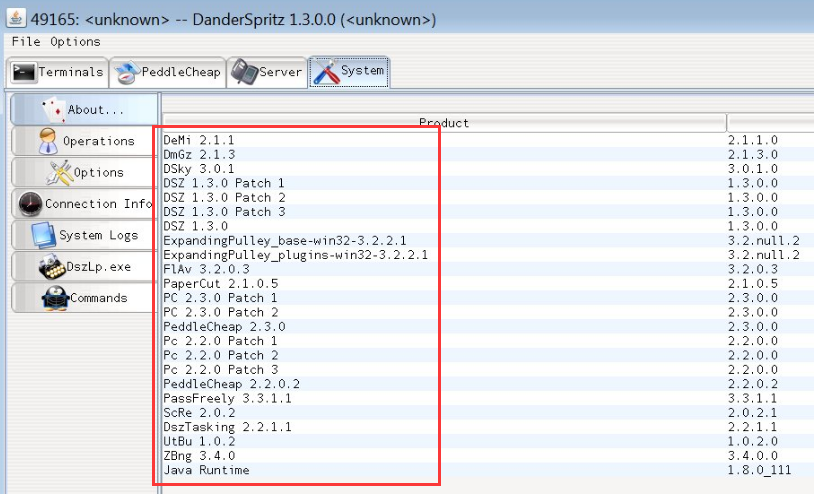
Figure 4-2 DanderSpritz attack platform screenshot leaked by Shadow Brokers
Most files exposed by “Shadow Broker” are attack plug-in on “DanderSpritz” platform. First, they are the file list, the other are 61 parts of the plug-in entity files. Attack tools and plug-ins are very abundant and standardized from the released files list HASH and screenshots, including remote control, exploit, backdoor, plug-in, etc. The content of DanderSpritz_All_Find.txt files has up to 7 thousand lines. They have hundreds of plug-ins. We analyzed and sorted out the 61 leaked files, according to the information in these 61 samples, they should belong to two categories: the test version and the release version. Test version contains some plaintext information. It is not encrypted. It used a regular function call. Its function call was changed to a more subtle dynamic call. The information does not exist in the release version. From the timestamp point of view, the generation time of the test version is about 5 seconds earlier than the release version. The test version is not intended to be used in real-world attacks. It is confirmed again from the side that these files were stolen from the development and custody scene, rather than captured in the attack.
Table 4-1 Partial list of plug-in functions for leaking entity files
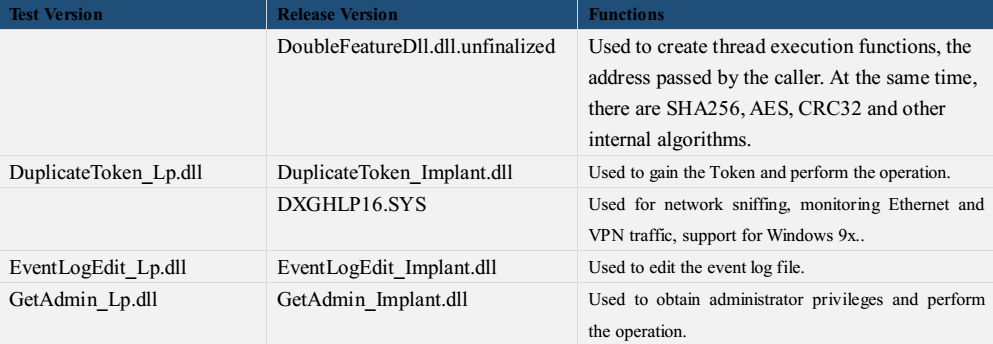
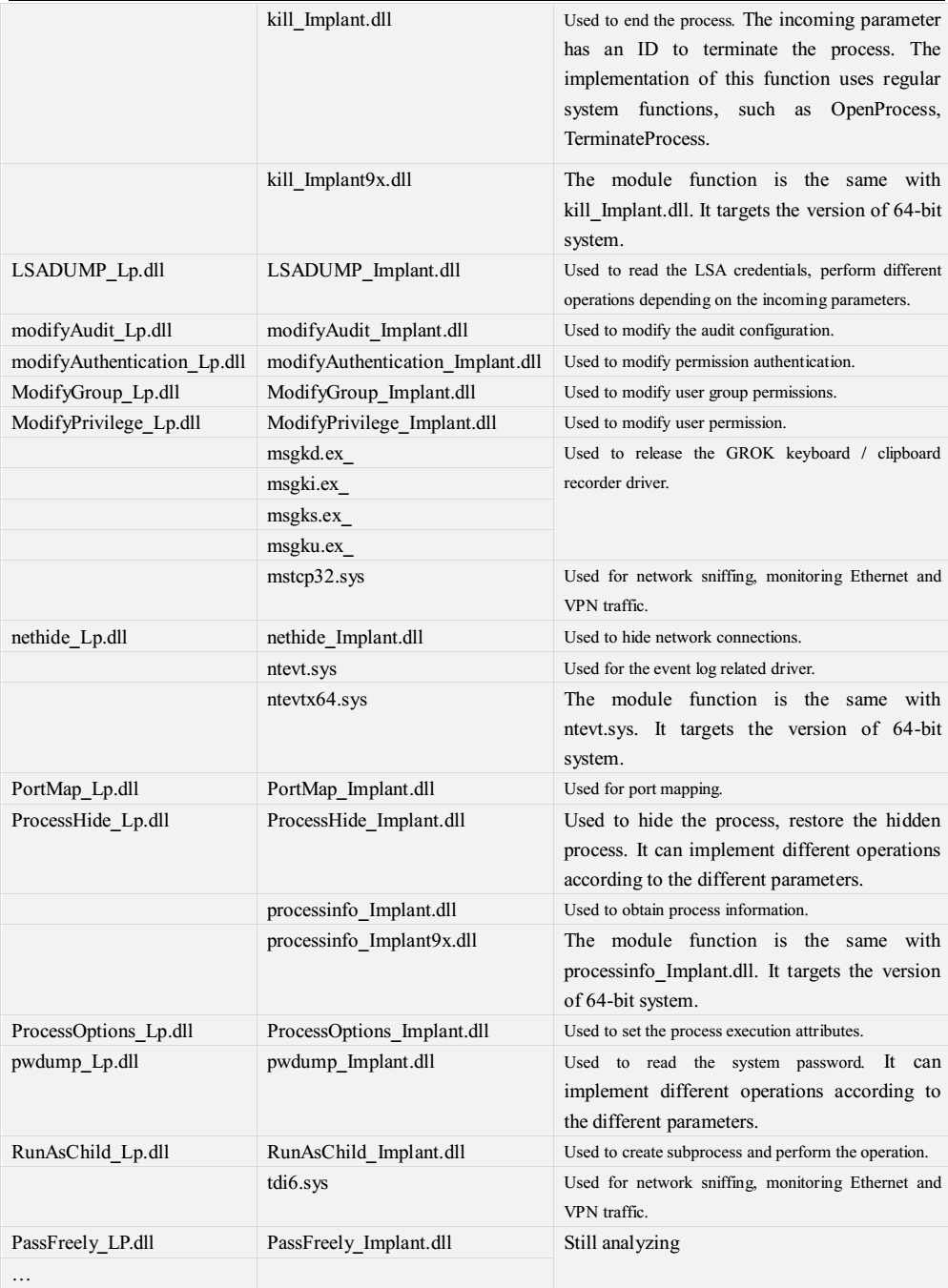
Table 4‑2 Speculation of plug-in function of leaked files
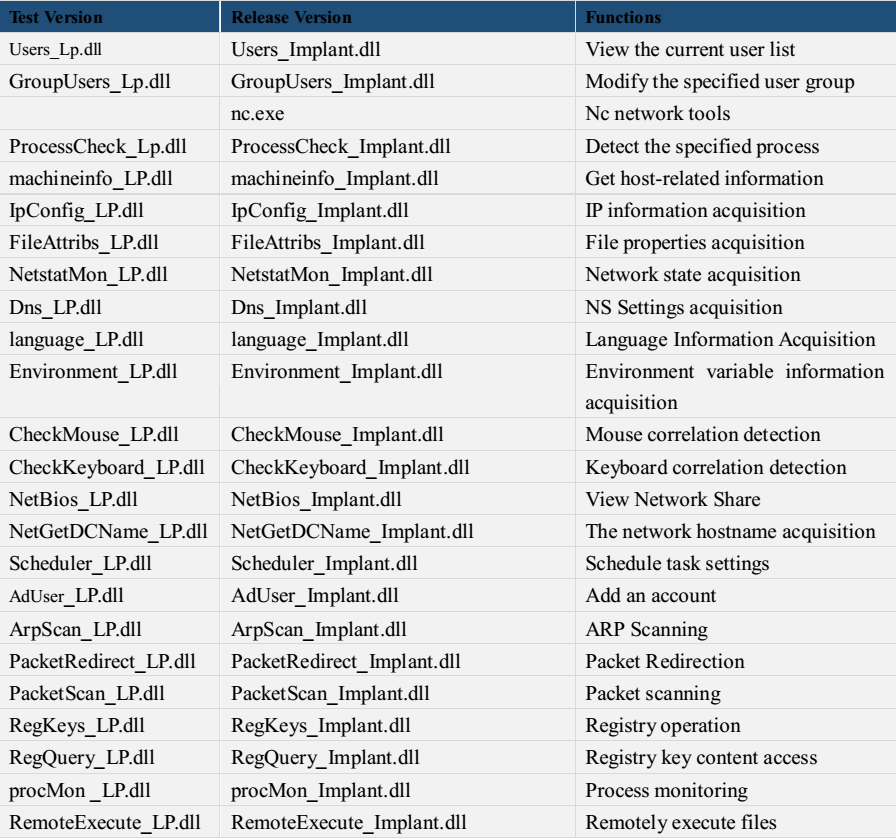
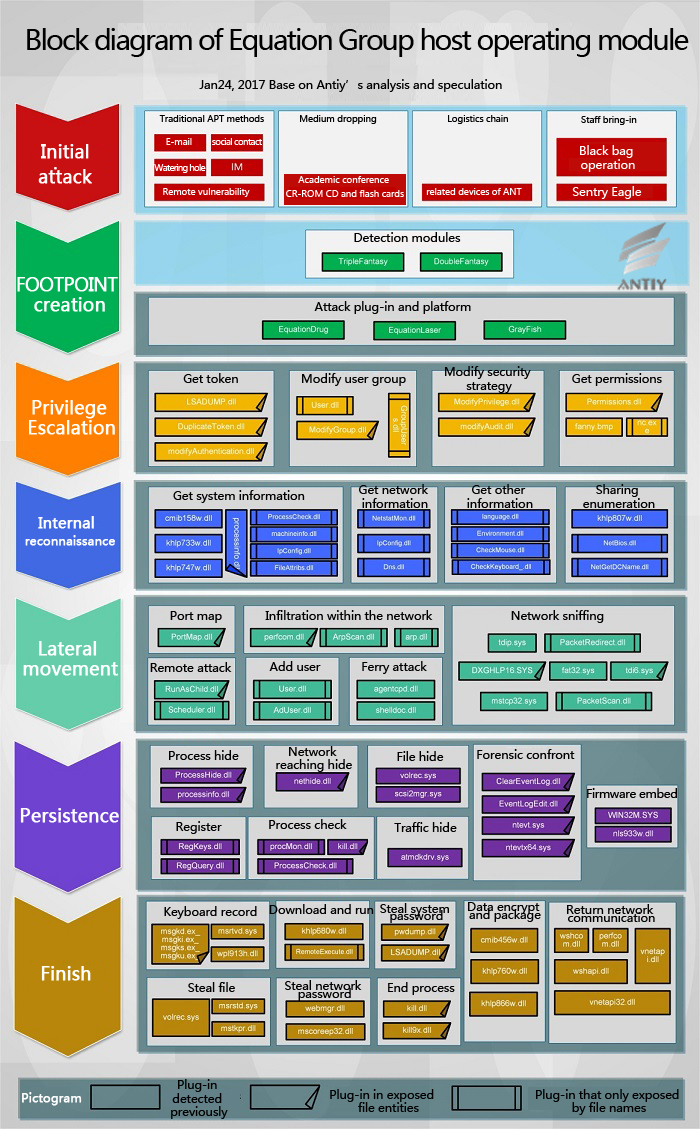
According to the analysis of some of the physical file functions and list and with the analysis from Kaspersky [7] and Antiy [1], we draw the” Block diagram of Equation Group host operating module.” From the figure, we can see that the attackers perform the corresponding functions through the combination of these plug-ins which reflects the following architectural style: there is no singular Trojan written with highly complex function. Even if a simple action such as access to system information operation, it will take the following actions as a separate small module, like getting the environment variables, language sets, network status, and so on. This will ensure that the system operations can be fully on-demand expansion, thus maximizing the operation to ensure the caution and silence. From the point of view of escape and confrontation in host security environment, these plug-ins are compiled in 2007; from the point of view of anti-virus technology development, it is the time that host active defense technology is coming into the mature stage. Active defense techniques generally use behavior-weighted method to determine unknown files, but the modules doing this “atomic” operation, are not accumulated to the threshold. This single function fragment is not only difficult to be found in the circumstances, it is difficult to be found even from the modern dynamic and static detection point of view. Each individual function fragment does not have any obvious malicious function, only the total scheduling platform coordinate the various functions of the plug-ins, it will show a variety of operating capability. This method also makes it difficult for security vendors to obtain the complete modules; in the absence of valid Loader, these modules are difficult to load in the sandbox, and thus difficult to effectively conduct behavior analysis. In this case, the analysis of them is more difficult than the Trojan that detects virtual environment to refuse the implementation.
Based on the file names, the functions of these modules are classified very clearly. In actual operations, these DLLs may be in shown some other forms, including the possibility of using digital signatures to steal the signature. In this case, the Version information of the partial driver file is also expected to be customized to the corresponding digital certificate information. The used file name may be consistent with the style of the system or application, or similar to the pre-compiled or temporary file skills used in Stuxnet [12], Duqu [13] and Flame [14].
Table 4-3 Digital Signatures for Samples in Series 3 A2PT Operations and File Naming Styles in Scenarios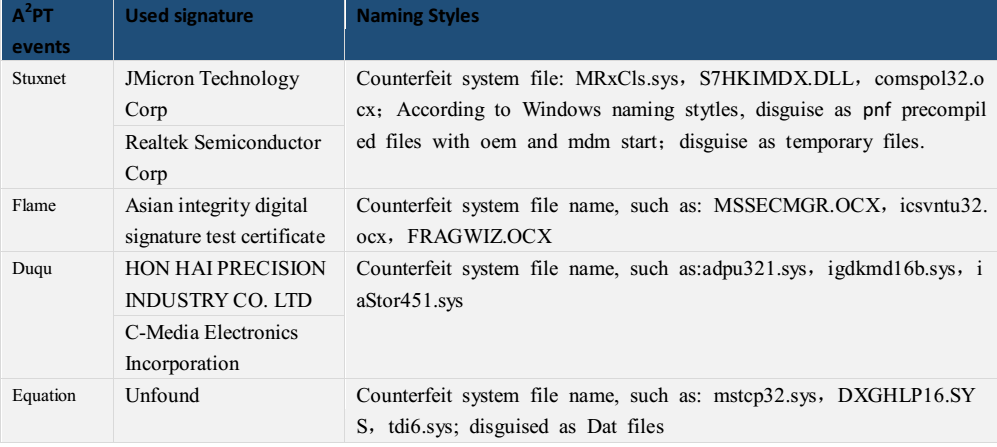
Of course, these modules may also be dropped without file fall to run, and direct run in memory without corresponding file entities.
Figure 4‑3 Block diagram of Equation Group host operating module
The word “DanderSpritz” was once exposed in the “Prism”, and DNT’s “DanderSpritz” was mentioned in the “FIREWALK” [16] tool of ANT, and both DNT and ANT belong to NSA network organization. This kind of attack equipment can be used for a variety of operating scenarios, network traffic capture and injection through the “FIREWALK” [16] tool make the victim host reachable to attacker’s remote control center, making the remote control into a tactical approach operation, such as hijacking through the logistics chain or insert or replace the device in the internal node. As long as start remote control tools, attacks with the combination of the nearest control and artificial operation can be achieved.
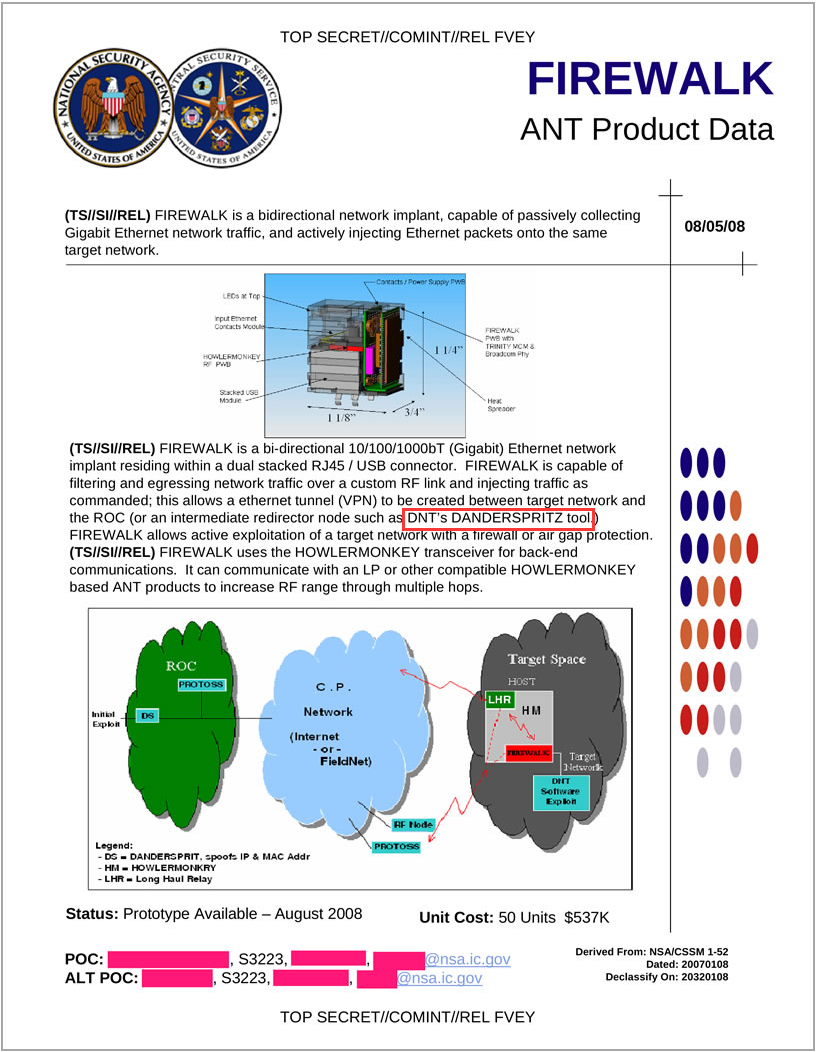
Figure 4-4 The exposed NSA-ANT network weapon FIREWALK by Snowden
NSA-ANT network weapons were exposed in the Snowden event as early as in 2013, including a total of 48 attack weapons. With the fermentation of the event, many media and organizations are constantly exposing them. Antiy’s analysis engineers attempted to draw the atlas of the relevant attack equipment according to all the current exposed information. The association mapping is also in further maintenance.
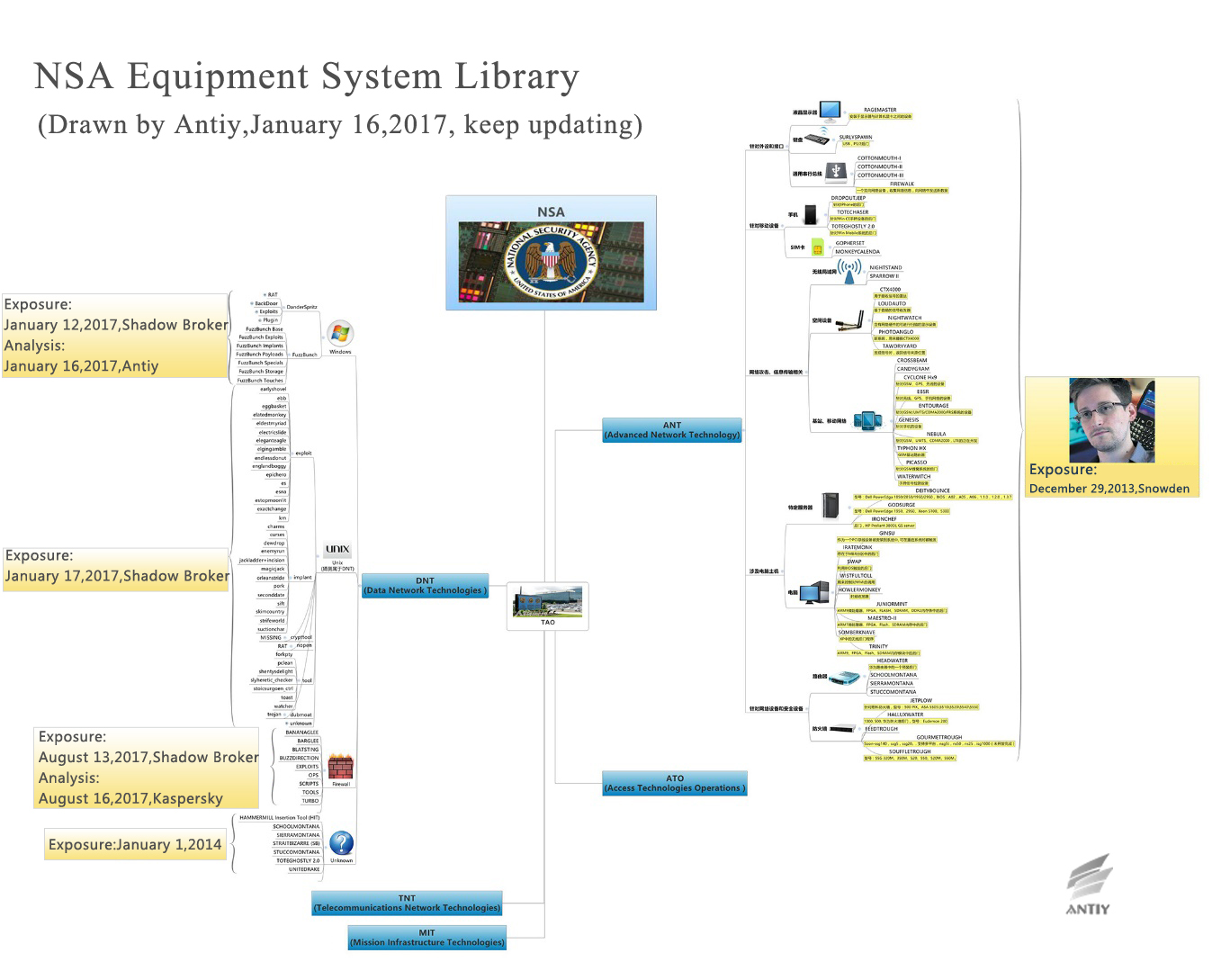
Figure 7 NSA-TAO attack equipment system (keep updating)
Analysis on Certain Components and Plugins (keep updating)
GROK Keyboard and Clipboard Recorder Driver
Through a follow-up analysis, Antiy CERT found that the exposed plug-in has a modular and anti-detection feature, and summarized the three characteristics of the attack plug-in according to the existing analysis:
- Every plug-in in DllMain function is not directly to achieve malicious behavior. When threat detection system that based on Sandbox-based detects the DLL form PE file, it usually calls Windows API LoadLibrary () to achieve the dynamic loading of objects to be detected, and run the DllMain function of the object to be detected to trigger the dynamic behavior of the object to be detected. But for these equation plug-ins, as the DllMain function does not behave maliciously (as shown in Figure 51), it can easily be seen as a non-malicious program by the sandbox.
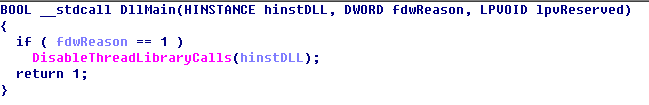
Figure 5-1 DllMain function has no malicious function
2. The derived function in each plug-in does not implement malicious functions directly. The Equation plug-ins provide only four functions that are serialized (not by name). In its function, the first derived function is responsible for receiving the callback function pointer or parameters passed in a specific data structure (As shown in Figure 5-2); the second derived function is responsible for releasing applied resources when necessary; the third derived function returns its kernel function pointer according to the call parameters; the fourth derived function is responsible for filling in the data structure provided by the caller and passing the plug-in version information to the caller. In addition to the fourth derived function does not strictly judge the parameters. It may generate an exception because of accessing null pointer. The derived function in each plug-in does not directly achieve malicious functions. Based on the sandbox-based threat detection system, it can not trigger malicious behavior by calling each derived function. Therefore, we can treat it as a non-malicious program.
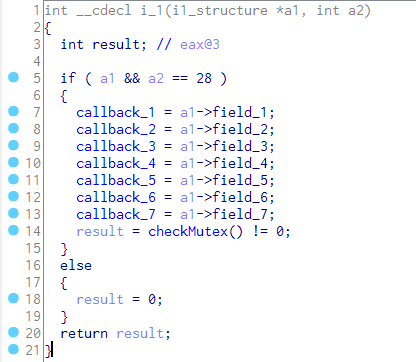
Figure 5-2 The callback function pointer or parameter in i1 function
3.Each plug-in can only achieve the most basic capabilities. The Equation plug-ins can only achieve the most basic functions. Even if the analysts master the plug-in call methods, pass the correct call parameters, can only perform the most basic program functions. And get the intermediate result of the program functions through callback function (such as process name, module name, user password). It is very difficult to distinguish these program functions from those of normal programs if not very experienced analysts. In addition to taking into account the scalability of the framework and the convenience of functional tailoring, it is possible to bypass the static detection mechanism of some anti-virus engines in this way.
Processinfo Plug-ins Traverse Process Module
Because of the complexity of these plug-ins, Antiy CET selected a relatively small file for analysis. Through the analysis we found that the process used to achieve the specified module traversal, and call the upper module default callback function.
Sample Tags
Table 5‑1 Sample Tags
Main Function
This plug in provides four functions that exported based on serial number.
Table 5‑2 Main function
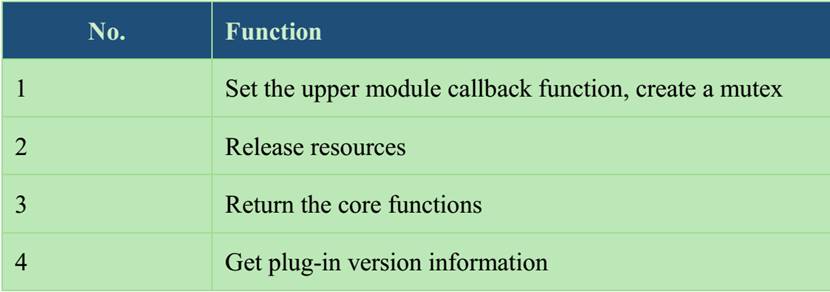
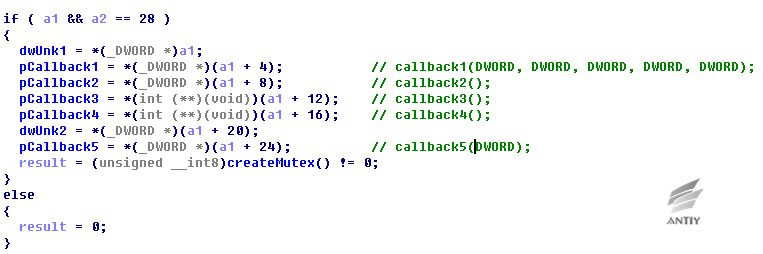
Figure 5‑3 Export Function 1 Set the upper module callback function
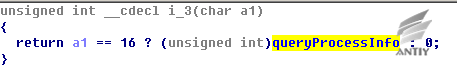
Figure 5‑4 Export Function 3 Return the core function address
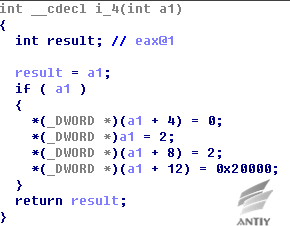
Figure 5‑5 Export Function 4 Get plug-in version information
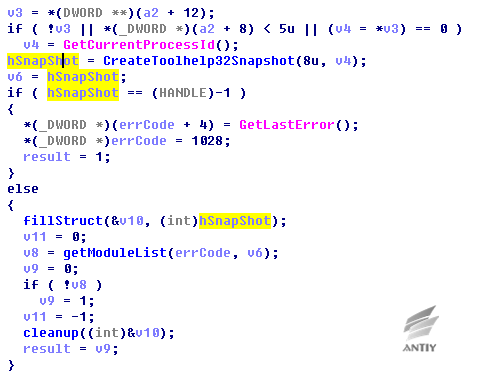
Figure 5‑6 Traverse specified process, set the current process default
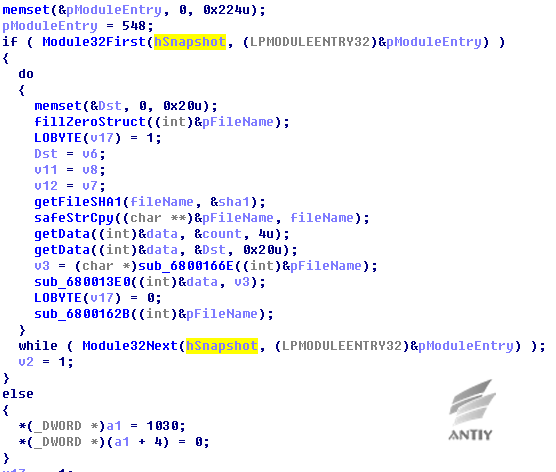
Figure 5‑7 Traverse specified process module, calculate file HASH (SHA1) of corresponding module
Kill_Implant Plug-in Attacking Process Module
The module is another relatively small file, Antiy CERT found that the main function of the plug-in is to end corresponding process according to incoming process ID.
Sample Tags
Table 5‑3 Sample Tags
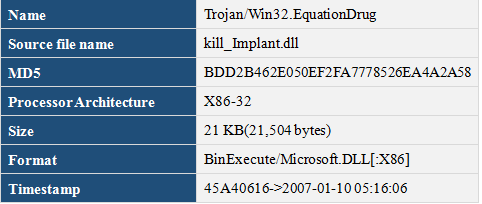
Main Function
Module caller passed in the process ID, the module uses OpenProcess to get handle, and then use TerminateProcess to end the corresponding process.
GROK Keyboard and Clipboard Recorder Driver
In addition to DLL plug-ins, the disclosed files also contain some EXE format, Antiy CERT found that several EXE files are the same with the previous equation platform GROK components, the exposure version is 1.2.0.1 which can decrypt from the resource section and release keyboard and clipboard recorder driver msrtdv.sys.
Sample lags
Table 5‑4 sample lags
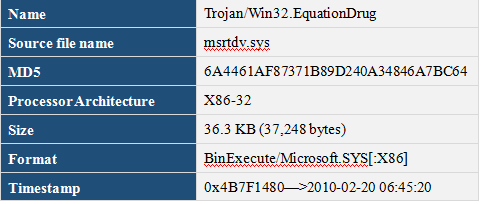
The malicious code sample is a keyboard recorder and clipboard monitoring tool, which is mentioned in previously reports by friend vendors, the comparison of their similarities is as below
Version
The sample contains the information about this version: file version is 5.1.1364.6430, source file name is msrtdv.sys, described as MSRTdv interface driver. This version is lower than the previously exposed version 5.3.1365.2180, the source file name and file description are different because of the exchange of “d” and “v”, one is “mstrdv.sys”, the other is “msrtvd.sys”.
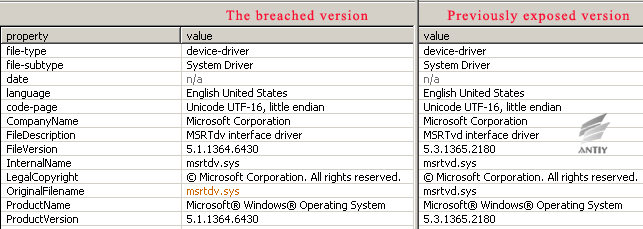
Figure 5‑9 The breached version and previously exposed version
Main Function
The main functions of these two versions are the same, which gather all the collected data by building specified process for dump program and compress the results to file “%TEMP%\tm154o.da” every 30 minutes. The previously exposed version includes multiple IoControlCode which correspond to different functions respectively.
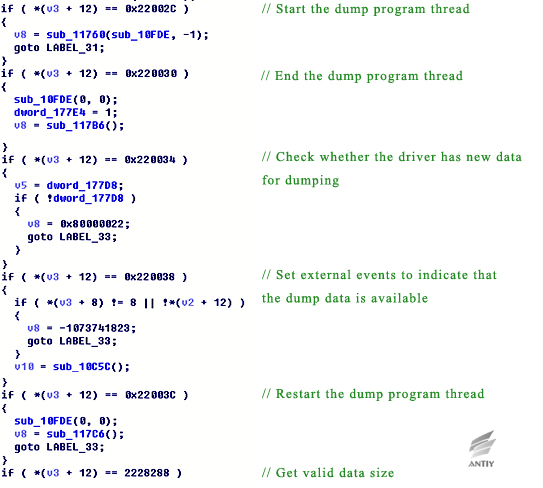
Figure 5‑10 Main function code of previously exposed version
In the sample breached, IoControlCode is only 0x22002C, but some of the main functions still exist and their similarities can be found by decompiled code.
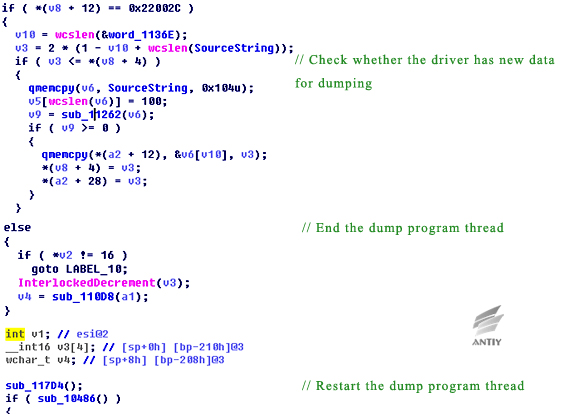
Figure 5‑11 Main function code of previously exposed version
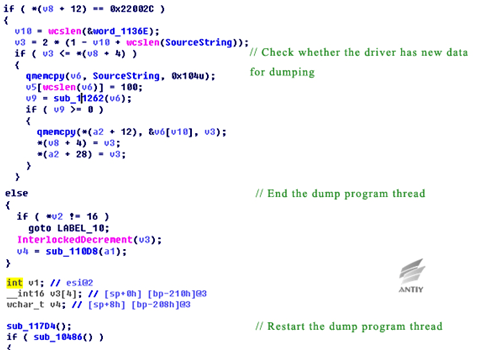
Figure 5‑12 Main function code of this breached version
From the above comparative analysis, the malicious code samples of the breached version should be a lower version, both the version information and functionality are lower than previous exposed version. This can also be proved by the GROK version number in the file DanderSpritz_All_Find.txt that breached by ShadowBroker which is only the low version of GROK component. However, these files are great valuable and provide new views for researchers.
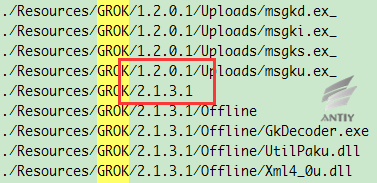
Figure 5‑13 Different version numbers of GROK component
Conclusion
The 61 files of Equation Group released by “Shadow broker” are helpful for global network security researchers to clarify the composition and architecture of the EQUATION-related attack platform. Especially the Debug version that can be observed, this is a rare chance to “internally” observe the launch of equation organization. With an analysis of relevant exposed information, we found more information about the attack platform, such as hundreds of attack plug-ins and “DanderSpritz” attack platform.
Through the analysis of relevant documents, we found that some components are similar with GROK components, and these components are the previously low version. In addition, our analysis also shows that “DanderSpritz” uses the same components and architecture as Equation Drug, and “DanderSpritz” may act as the Equation Drug attack platform used by Equation, and the design ideas of this module let more people see the formula of the organization and support system are so large and sophisticated, rigorous process, as well as the rich experience in weapons research and development.
Five years ago, in the longtime analysis of “Flame”, some experts have reminded us not to “only see the leaves but ignore the forest”, which makes us reflect the limitations of traditional analysis that studying from the entry, and began to try to analyze from micro-perspective to macro perspective.
The four years continuous tracking and analysis of Equation is valuable experience for Antiy to understand the highest level of attackers (A2PT, ‘advanced APT’). In-depth studies of the super-attackers with high-cost support and advanced concepts are also critical to improve the defense abilities of Antiy’s advanced threat detection and defense products as PTD, IEP and PTA, etc. However, for A2PT attackers, whether to effectively improve defense, or more comprehensive and in-depth analysis of the system, is not one security company can independently deal with. And there needs more coordination and continuously analysis. Based on this common understanding, in the Fourth Antiy Network Security Training Camp, Antiy and 360 Security and other security companies shared mutual recognition attempts on the capacity-based security vendors to the participating experts. Only form a positive and interactive system between institutional users and capacity-based security vendors can better defend the hazards from all sides.
We are vigilant, but not fear. For a defense war, in addition to a solid structure, defense and analysis, the conviction to win is a premise.
Antiy’s PTA (Persistent Threat Analysis System) can chase the attackers by their shadows.
Appendix 1: References
- Antiy:A TROJAN THAT CAN MODIFY THE HARD DISK FIRMWARE ——A Discovery to the Attack Components of the EQUATION Group
https://www.antiy.net/p/a-trojan-that-can-modify-the-hard-disk-firmware/
- Antiy:Analysis on the Encryption Techniques of EQUATION Components
https://www.antiy.net/p/analysis-on-the-encryption-techniques-of-equation-components/
- Antiy:FROM EQUATION TO EQUATIONS——Revealing the multi-platform operational capability of Equation Group
https://www.antiy.net/p/from-equation-to-equations/
- The Shadow Brokers closed, going dark
https://onlyzero.net/theshadowbrokers.bit/post/messagefinale/
- Stolen NSA “Windows Hacking Tools” Now Up For Sale!
http://thehackernews.com/2017/01/nsa-windows-hacking-tools.html
- Kaspersky:Equation: The Death Star of Malware Galaxy
http://securelist.com/blog/research/68750/equation-the-death-star-of-malware-galaxy/
- Kaspersky:Inside the EquationDrug Espionage Platform
https://securelist.com/blog/research/69203/inside-the-equationdrug-espionage-platform/
- Equation Group Cyber Weapons Auction – Invitation
https://github.com/theshadowbrokers/EQGRP-AUCTION
- The Equation giveaway
https://securelist.com/blog/incidents/75812/the-equation-giveaway/
- I just published “TheShadowBrokers Message #3”
https://medium.com/@shadowbrokerss/theshadowbrokers-message-3-af1b181b481
- Shadow Brokers reveals list of Servers Hacked by the NSA
http://thehackernews.com/2016/10/nsa-shadow-brokers-hacking.html
- Report on the Worm Stuxnet Attack
http://www.antiy.com/response/stuxnet/Report_on_the_Worm_Stuxnet_Attack.html
- Analysis and Introspection of Stuxnet, Duqu and Flame
http://www.antiy.com/resources/Analysis_and_Introspection_of_Stuxnet_Duqu_and_Flame.pdf
- Analysis on the Flame
http://www.antiy.com/response/flame/Analysis_on_the_Flame.html
- ANTProductData2013
https://search.edwardsnowden.com/docs/ANTProductData2013-12-30nsadocs
- Kaspersky:A Fanny Equation: “I am your father, Stuxnet”
http://securelist.com/blog/research/68787/a-fanny-equation-i-am-your-father-stuxnet/
- Kaspersky:Equation Group: from Houston with love
http://securelist.com/blog/research/68877/equation-group-from-houston-with-love/
- Kaspersky:Equation_group_questions_and_answers
https://securelist.com/files/2015/02/Equation_group_questions_and_answers.pdf
- Kaspersky:The Equation giveaway
https://securelist.com/blog/incidents/75812/the-equation-giveaway/
Appendix 2:About Antiy
Starting from antivirus engine research and development team, Antiy now has developed into a group level security enterprise with Antiy Labs as headquarters and both enterprise security company and mobile security company as two wings. Antiy always adheres to the belief of securing and protecting user value and advocates independent research and innovation, forming the layout of the capacity of the whole chain in the following aspects: security detection engine, mobile security, network protocol reduction analysis, dynamic analysis, terminal protection, and virtualization security and so on. Antiy has fostered nationwide detection and monitoring capability with our products and services covering multiple countries. With effective combination of techniques and products of both big data analysis and security visualization, Antiy expands the group work competence of engineers and shortens the product response cycle by massive automation sample analysis platform. With years’ continual accumulation of massive security threat knowledge library, Antiy promotes the solution of situational awareness and monitoring and early warning that targets against APT and at scale network and critical infrastructure, combining with the experience of integrated application of big data analysis and security visualization.
More than 30 famous security vendors and IT vendors select Antiy as their partner of detection capability. The antivirus engine of Antiy has provided security protection for nearly a hundred thousand network devices and security devices and nearly two hundred million mobile phones. The mobile detection engine of Antiy was the first Chinses product that won AV-TEST reward in the world. The technical strength of Antiy has been recognized by industry management organizations, customers and partners. Antiy has consecutively been awarded the qualification of national security emergency support unit four times and one of the six of CNNVD first-level support units. Antiy is the significant enterprise node of China emergency response system, which has provided alarms, in-depth analysis or systematic solution in a few severe security incidents, such as Code Red, Dvldr, Stuxnet, Bash Shellcode, Sandworm, and Equation and so on.
| More information about Antiy Labs: | http://www.antiy.com(Chinese)
https://www.antiy.net (English) |
| More information about enterprise security company: | http://www.antiy.cn |
| More information about Antiy AVL TEAM: | http://www.avlsec.com |
