AN ANALYSIS ON TARGETED TROJAN ATTACK WITH “INTERVIEW” AS A SOCIAL ENGINEERING TOOL
An Analysis on Targeted Trojan Attack with “Interview” as a Social Engineering Tool
By Antiy CERT
Download
First release: December 3, 2015, 10:21
Update: December 5, 2015, 5:21
1. Overview
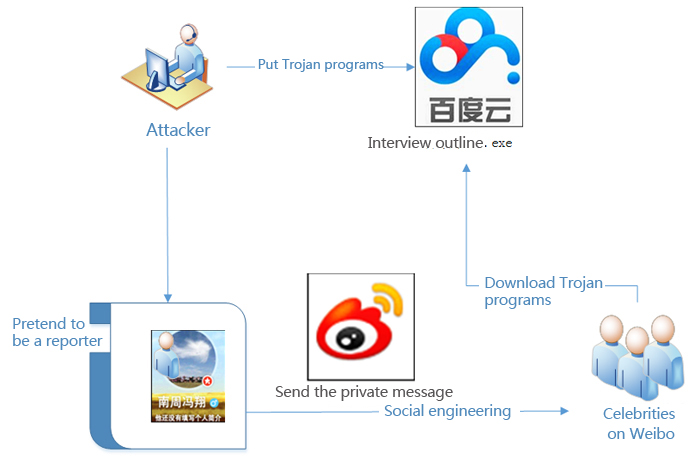
In the evening of December 2, 2015, Antiy earlier-warning monitor system perceived the following information: a famous writer released a message in the Sina Weibo (Note: Sina Weibo is the largest social network in China that specializes in providing microblog services, like Twitter), exposed that someone sent a malicious code link which is pretended as “Interview outline” file through Weibo private message function.
According to Weibo screenshot link, Antiy CERT downloaded the sample and performed the analysis. With the deep analysis, we collated the event process and its relevant malicious code mechanism.
2. “Interview” Event
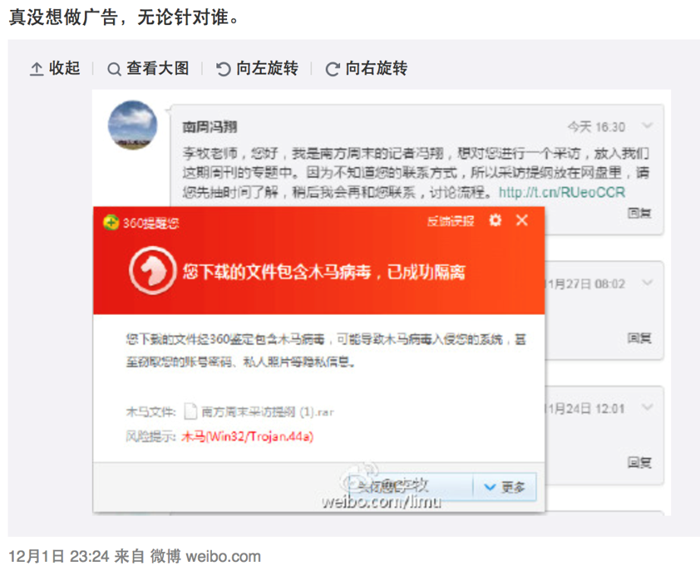
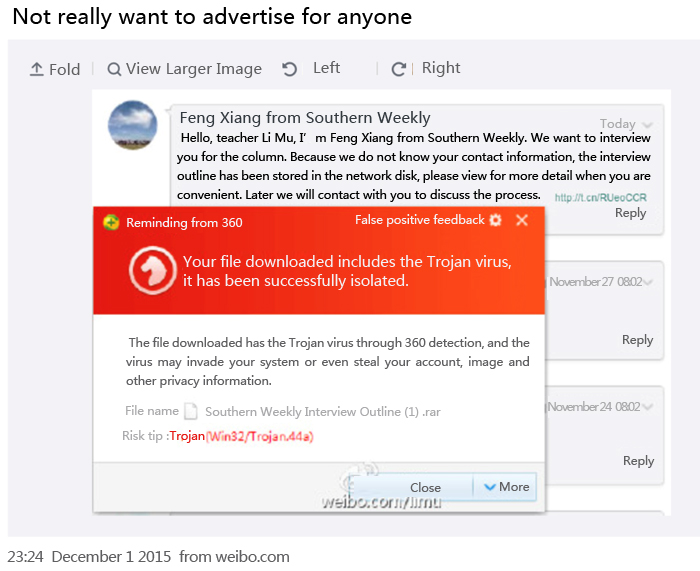
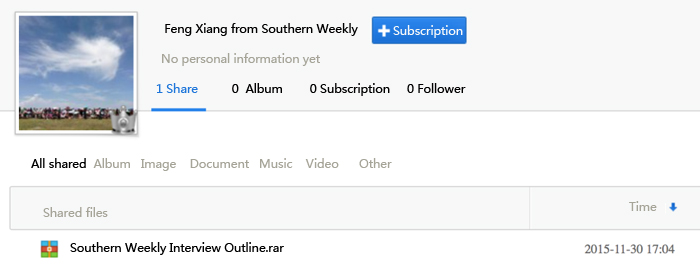
As shown, the blog was released on December 1, 23:24. A writer received “Interview outline” from a reporter called “Feng Xiang from Southern Weekly” (Southern Weekly is a comprehensive press in China), and the ““Interview outline” was stored in network disk because the report “does not known” his contact information. But, the file in the network disk causes an alert from anti-virus software.
Figure 1 An alert from the anti-virus software
Remark: This English version is translated and presented from the original version
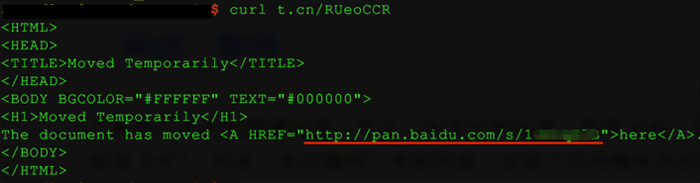
First, we find the true file link according to Weibo screenshot, as shown, the file link indicates Baidu Wangpan. (Note: Baidu Wangpan is a cloud storage service provided by Baidu, and users can store own files to Wangpan for sharing and view.)
Figure 2 The downloaded address alerted is Baidu Wangpan
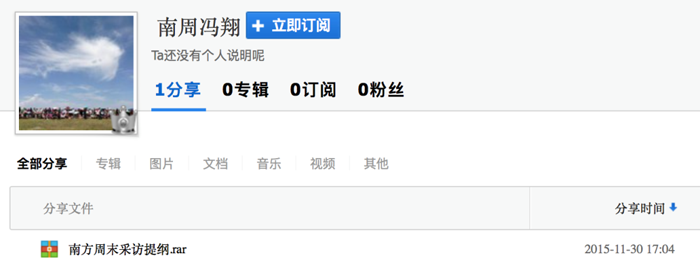
The owner of Baidu Wangpan is “Feng Xiang from Southern Weekly”; its creation time is 17:04 on November 30, 2015.
Figure 3 “Feng Xiang from Southern Weekly”
Remark: This English version is translated and presented from the original version
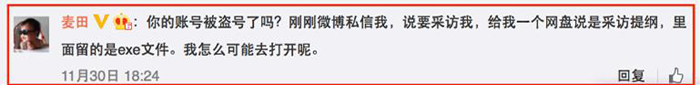
At the same time, we find that another Weibo celebrity raised doubts on November 30.
Figure 4 Doubts to “Feng Xiang from Southern Weekly”
Remark: This English version is translated and presented from the original version
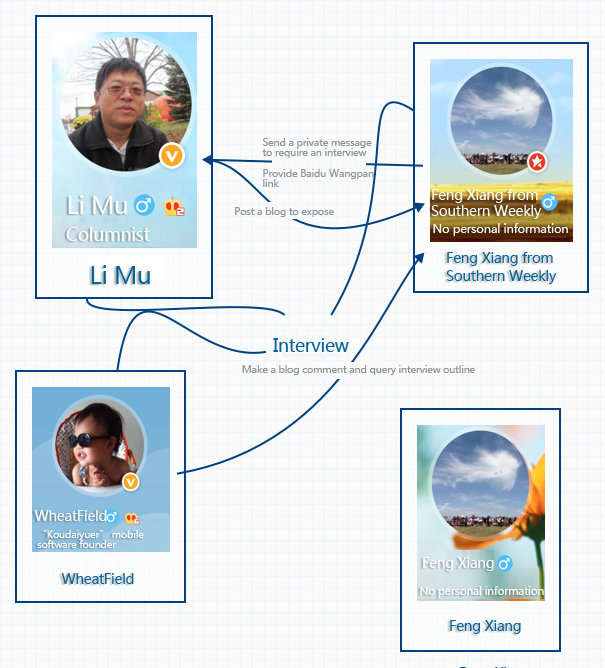
For this, we search the information about “Feng Xiang from Southern Weekly” through Weibo, and find that his fans only up to three hundred, while anther “Feng Xiang” has fans up to over 10 hundreds, and their avatar pictures are similar. Because the name of Sina Weibo can be changed freely, so we could not determine if the malicious code is sent by “Feng Xiang from Southern Weekly”. The relationship of characters is as follows:
Figure 5 The relationship of characters
Remark: This English version is translated and presented from the original version
They are so similar that we could not get the truth according their images. We have collated the event process:
Figure 6 Attack process
Although the attack uses the social engineering to cheat, but still now, no celebrities are “attacked”. We analyze the samples.
3. File Information
| File name | Southern Weekly Interview Outline.rar |
| MD5 | F2928482E9F7443EDED6B366AAD554F9 |
| File size | 1.16 MB (1,217,174 bytes) |
| File format | RAR archive data, v1d, os: Win32 |
There is only one EXE file in the package:
| Original file name | Southern Weekly Interview Outline.exe |
| MD5 | EA878E08F10057B2477090C8017AF587 |
| Processor architecture | X86-32 |
| File size | 5,238 KB (5,364,268 bytes) |
| File format | BinExecute/Microsoft.EXE[:X86] |
| File time | 2015-11-30 16:51:21 (From the package) |
| Timestamp | 53973C2B->2014-06-11 01:11:07(File timestamp can be fake.) |
| Digital signature | YES(Fake Microsoft Signature, invalid digital signature) |
| Development tool: | n/a |
| Shell tool: | n/a |
As shown, the EXE file is similar with Word document.
Figure 7 Southern Weekly Interview Outline Icon
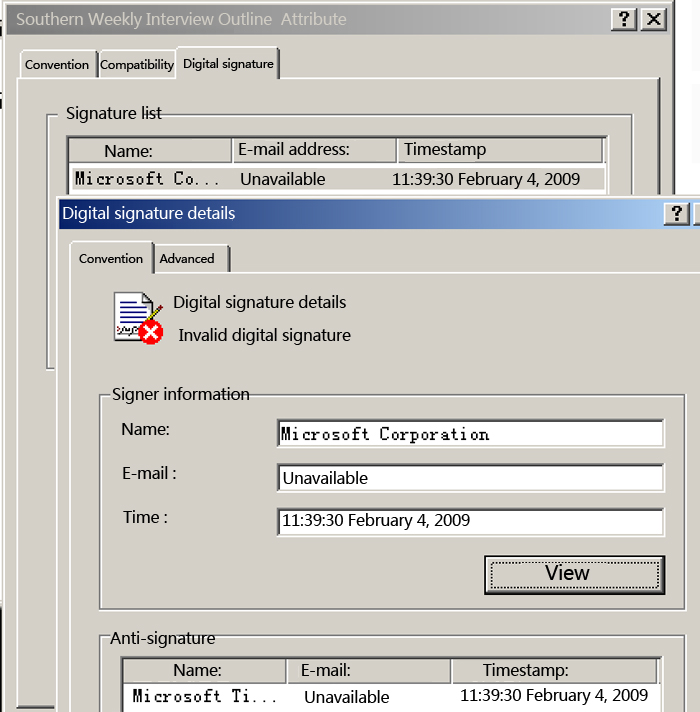
The file has digital signature, which cannot be verified online, so we suspect that a static fake digital signature has been applied.
Figure 8 Fake Microsoft digital signature
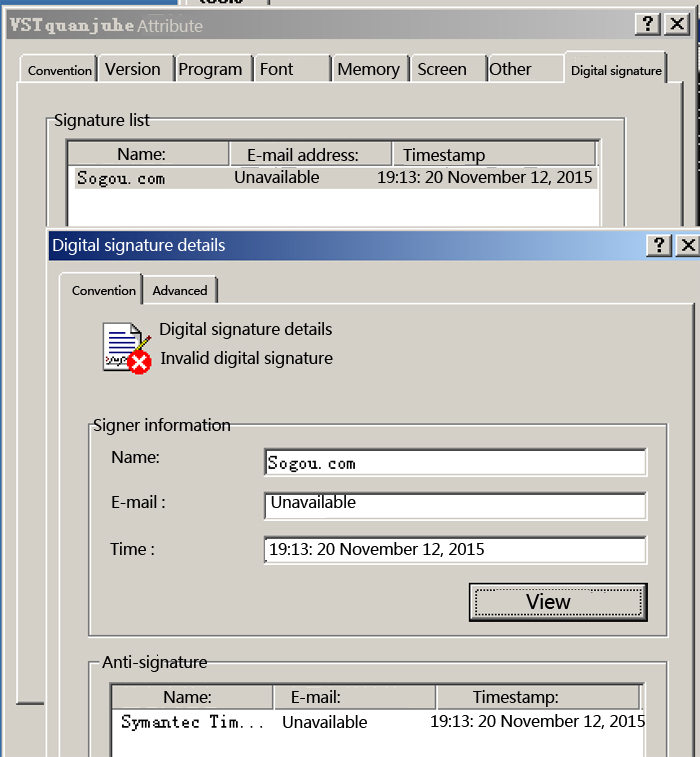
While the generated file VSTquanjuhe.com has the fake sogou digital signature:
Figure 9 Fake sogou digital signature of VSTquanjuhe.com
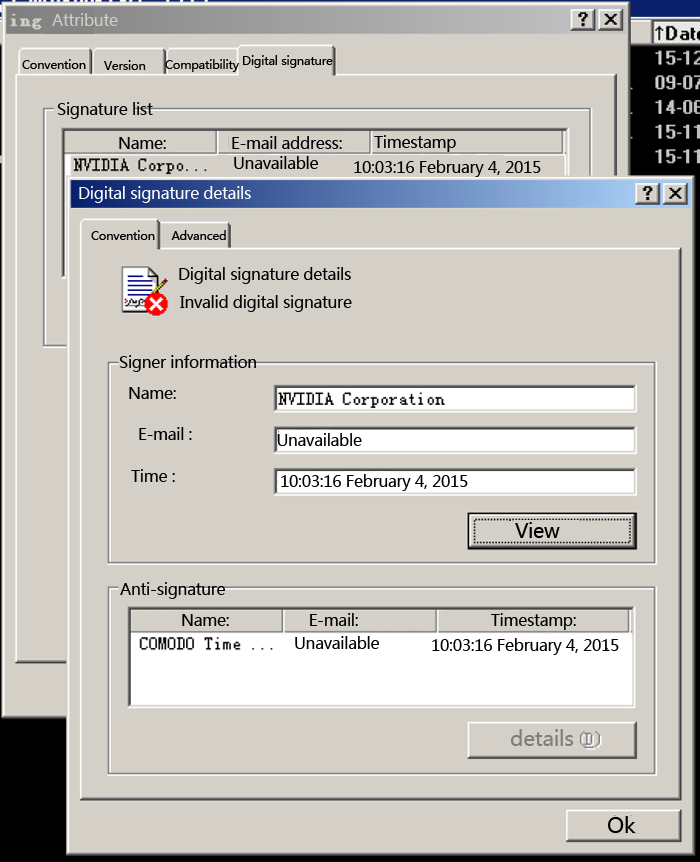
The generated file ing.exe has fake NVIDIA digital signature:
Figure 10 Fake NVIDIA digital signature of ing.exe
4. Sample Analysis
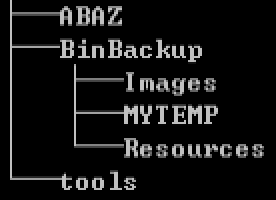
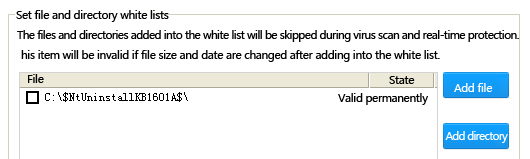
The program will create archive named “$NtUninstallKB1601A$” at root directory of C disk after operation, which includes BinBackup and tools. The whole directory architecture is as follows:
Figure 11 The whole directory architecture of archive that released by malware
The file names and file size in this directory architecture are as follows:
| Directory | File Name | File Size |
| .\ | bmd.vbe | 10.4 KB (10,698 bytes) |
| .\ | gsxt.bat | 1.26 KB (1,299 bytes) |
| ABAZ\ | 1.exe | 69.5 KB (71,168 bytes) |
| ABAZ\ | sl2.db | 70 bytes (70 bytes) |
| ABAZ\ | speedmem2.hg | 21.0 KB (21,504 bytes) |
| ABAZ\ | XueTr.dll | 261 KB (267,776 bytes) |
| ABAZ\ | XueTrSDK.sys | 362 KB (370,688 bytes) |
| BinBackup\MYTEMP\ | 8.3f | 169 bytes (169 bytes) |
| BinBackup\ | abc.os | 3.00 KB (3,072 bytes) |
| BinBackup\ | abc1601.dat | 341 KB (350,190 bytes) |
| BinBackup\ | inst.ini | 293 KB (300,990 bytes) |
| BinBackup\ | lang1.lnk | 3 KB (3,172 bytes) |
| BinBackup\ | lang2.lnk | 3 KB (3,338 bytes) |
| BinBackup\ | links.ini | 404 KB (413,742 bytes) |
| BinBackup\ | mew.1r | 42.6 KB (43,646 bytes) |
| BinBackup\ | mtfile.tpi | 86.3 KB (88,462 bytes) |
| BinBackup\ | os.bat | 242 bytes (242 bytes) |
| BinBackup\ | super.inf | 7.01 KB (7,180 bytes) |
| BinBackup\ | test1.pfx | 107 KB (110,030 bytes) |
| BinBackup\ | test2.pfx | 95.1 KB (97,484 bytes) |
| BinBackup\ | ua.lnk | 1 KB (1,046 bytes) |
| BinBackup\ | ub.lnk | 1 KB (668 bytes) |
| BinBackup\ | Win1.bat | 1.53 KB (1,570 bytes) |
| BinBackup\ | Win2.bat | 764 bytes (764 bytes) |
| Tools\ | cmd.exe | 336 KB (344,576 bytes) |
| Tools\ | ing.exe | 192 KB (197,320 bytes) |
| Tools\ | ua.exe | 483 KB (495,568 bytes) |
| Tools\ | VSTquanjuhe.com | 51.5 MB (54,035,320 bytes) |
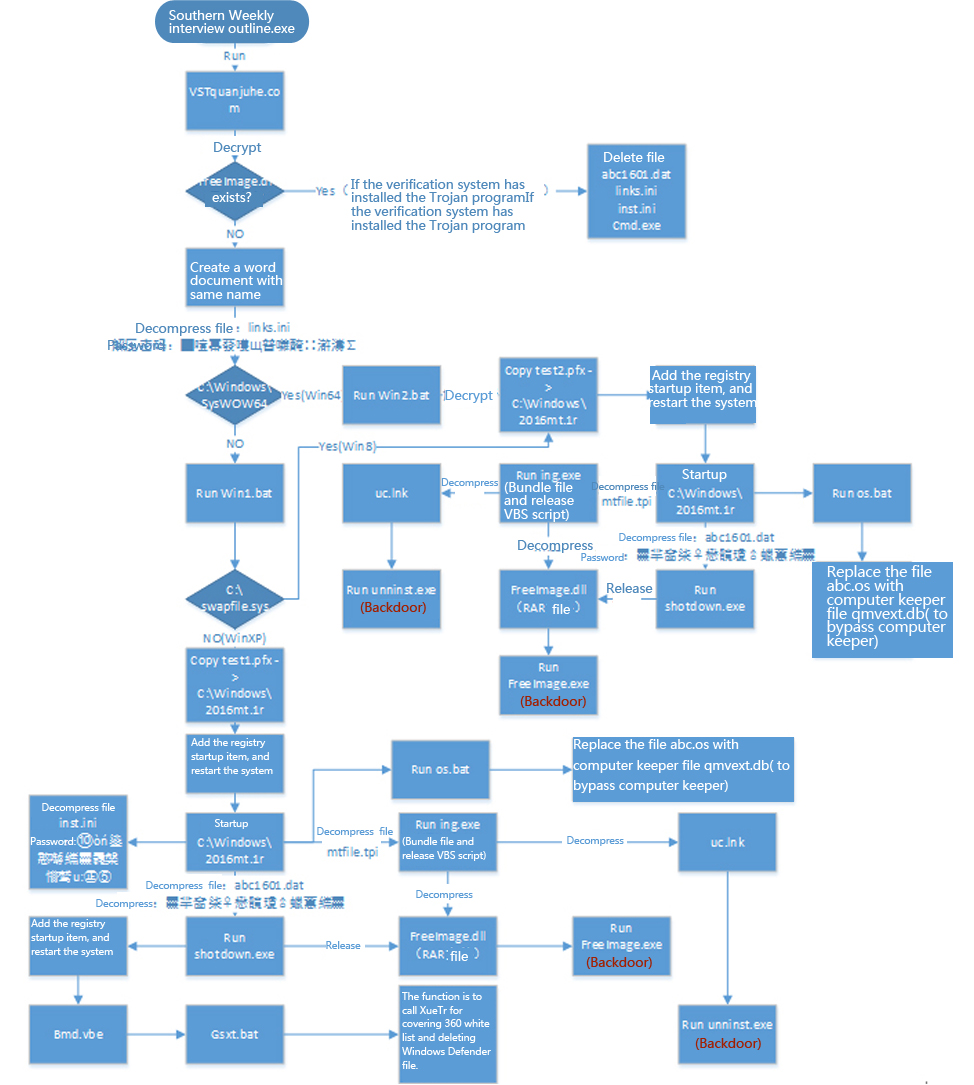
The flow chart of sample execution is as follows:
Figure 12 Flow chart of sample execution
The sample is a self-extracting program, it uses more than a dozen encryption scripts to execute malicious functions, encrypts after being executed and runs unzipped program VSTquanjuhe.com. It uses identification to check whether there is “C:\\$NtUninstallKB1601A$\\BinBackup\\Images\\FreeImage.dll” to check if it is runningVSTquanjuhe.com. Use extremely complex unzip passwords to unzip links.ini and identified whether there is a folder “C:\Windows\SysWOW64” to check whether the system version has a 64-sit operating system, and 32-bit operating system and 64 – bit operating system call for different encryption scripts to execute. 32-bit operating system (except Windows 8) adds registry startup by script, and restarts the operating system, and then reuses complex passwords to decrypt multiple files. After being unzipped, the excusable file shotdown.exe,shotdown.exe will release a encrypted RAR file called FreeImage.dll. By restarting the system, it uses decryption script and manual anti-virus tools “XueTr” covering 360 security software white list file, and delete anti-virus software Windows Defender file, running unzipped files ing. exe (bundle files, release VBS script), using the ing. exe to release script unzipped RAR file FreeImage.dll to get a backdoor and then run. The program file can use the method of replacing files to add rules to bypass Tencent computer butler detection. The 64 – bit operating system and the branch function of Windows 8 system is the same as the 32-bit operating system. The main difference is to restart the system once instead of twice, uncover 360 security software white list file. Their ultimate goal is to run two backdoor.
5. Derivative File Analysis
| File path name | Main functions |
| ABAZ\1.exe | XueTr Command line version for BAT and VBS script calls, to duplicate and delete files. |
| ABAZ\XueTr.dll | XueTr depends on dynamic link library file. |
| ABAZ\XueTrSDK.sys | XueTr depends on driver file. |
| Tools\ua.exe | RAR command line tools for BAT and VBS script calls, to unzip the files. |
These derivative files are four common utility class programs.
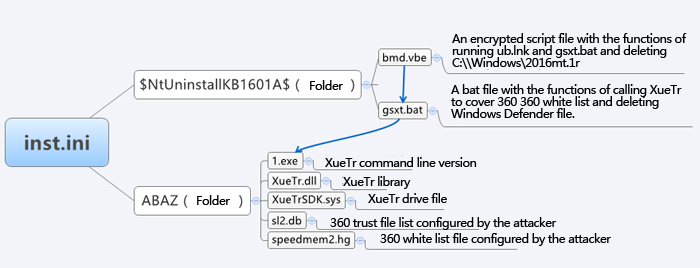
5.1 Calling relationship and function description of Inst.ini unzip file
Init.ini File uses ini as extensions, but it is actually a RAR file package.
Figure 13 inst.ini unzip file function
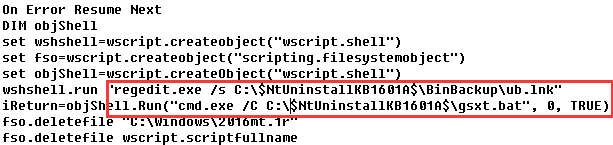
bmd.vbe is an encrypted script file, which contains multilayer encryption, the eventually decrypted code is as follows:
Figure 14 bmd.vbe decrypted plaintext code
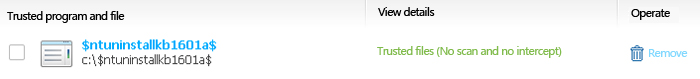
Its main function is to add the registry startup: “C:\$NtUninstallKB1601A$\BinBackup\ub.lnk”. Then it calls gsxt.bat to replace the security software white list file to achieve the goal of bypassing security software killing.
Figure 15 Replace security software white list
Therefore, it can be found that the function of inst.ini is to add ub.lnk startup, and attempt to bypass security software killing.
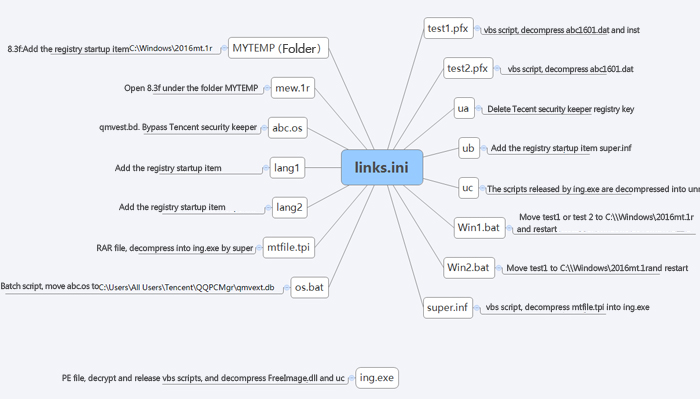
5.2 links.ini unzip files and basic function description:
links.ini uses ini as extensions, but it is actually a RAR file package.
Figure 16 links.ini unzip files function description
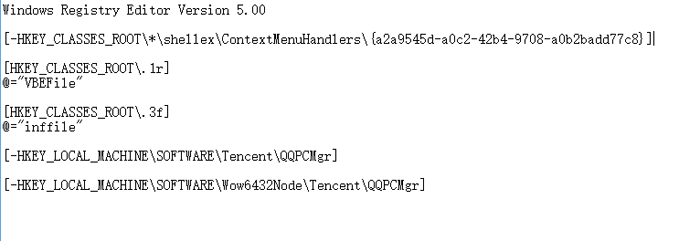
File ua.lnk deletes the start menu and Tencent Security Steward registry entries, and modifies files with suffix as .1r and .3f , which can open in the form of vbe and inf .
Figure 17 ua.lnk code
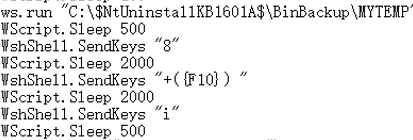
Unzipped files in the vbe varies script uses JScript Encode algorithm to encrypt, such as code snippet of mew. 1 r script is as below:
Figure 18 Encrypted mew.1r code
Script’s multiple encryption and repeated decrypted plaintext code snippet is shown below. The script is used to open the MYTEMP folder and call the SendKeys function to simulate the keyboard operation, realize the selected configuration file 8.3 f (inf format in fact) and perform the operation of registry installation:
Figure 19 Encrypted mew.1r part code
5.3 Backdoor Analysis
The terminal goal of this incident is to install backdoor program in user’s system. We have found two backdoor programs according to above analysis:
| Original File Name | FreeImage.exe | unninst.exe |
| MD5 | 66FF6F32FF7096206B48D8006854C568 | 2A0C3E7262AD136D9D776A99E18A03CB |
| Processor Architecture | X86-32 | X86-32 |
| File Size | 686 KB (702,464 bytes) | 660 KB (676,352 bytes) |
| File Pattern | BinExecute/Microsoft.EXE[:X86] | BinExecute/Microsoft.EXE[:X86] |
| Time Stamp | 4981F684->2009-01-30 02:33:40 | 4981F684->2009-01-30 02:33:40 |
| Digital signature | None | None |
| Developing Tool | Borland Delphi 6.0 – 7.0 | Borland Delphi 6.0 – 7.0 |
| Shell Tool | None | None |
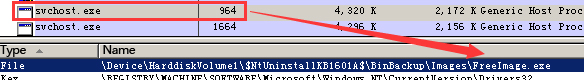
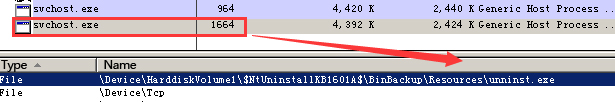
These two backdoor are of the same local action: enabling system program svchost.exe and injecting into it.
FreeImage.exe injection:
Figure 20 FreeImage.exe injects into svchost.exe
unninst.exe injection:
Figure 21 unninst.exe injects into svchost.exe
The online address can be found by code analysis:
| Domain Name | Port | IP | Geography Address | |
| FreeImage.exe | C***la.meibu.net | 3529 | 115.**.***.239 | BGP Data Center of Aliyun, Tsingtao, Shandong |
| unninst.exe | 1048****er.meibu.net | 3529 | 115.**.***.239 | BGP Data Center of Aliyun, Tsingtao, Shandong |
The jumping address of the dynamic domain is 115.**.***.239. It can be concluded that the backdoors belong to the same network action and function. Meanwhile, according to the analysis took by Antiy CERT analysts on backdoor code and online data package, it can be deduced that the backdoors are generated by the same remote generator. And the remote control software is the specific version of RemoteABC that is modified by Hupigon source code.
The remote control software owns the following functions:
- File management
- Process management
- Service Management
- Sharing management
- Plug-in management
- Enabling video and audio remotely
- ……
6. Summary
According to above analysis result, it indicates that the attackers in this incident have the following operating features:
- Faking ID with the help of Weibo
- Dropping malware to targeted people by Baidu Wangpan
- Bypassing the protection mechanism provided by system security tools by using the tool software that is usually used to deal with malware
- Compromising the security tool software through making use of the vulnerabilities of known security tool software
We have concluded the following enlightenment according to above features:
- The Internet companies should strengthen the monitoring and governance of user’s fake ID.
- The online storage vendor should strengthen the security detection of storage content to avoid being used to spread malware.
- The developers of tool software should try to add obvious confirming functions of user interaction when they develop functions that might bypass or compromise system security mechanism to avoid being used maliciously.
- The developing vendors of security tools should release the upgrading patch immediately after they found security vulnerabilities and suggest users’ upgrading to avoid attackers’ bypassing, which would result in bringing false impression to users.
Appendix 1: Sample MD5 in This Incident
| 0C5261CB53CF17E0A03CA1E6A230430B | 29017A44550FBC8AA4D64820044F54EC |
| 1E6726ED20B88CD2C3E546306E5A3C72 | 34220AFE857F99A493F4171482E7E8FE |
| 2A0C3E7262AD136D9D776A99E18A03CB | 480145BA7EE820C20AB7D2AD97F95005 |
| 3B86EC0243AB626A11787DA0C53C302A | A133284DA52E3CC848C175D73732E88A |
| 3EE804C0D1AB806BB837FE061A80B457 | AFFB80A87F53E67CA886935E44D2BB6E |
| 5D47C0554EE28E8532F0430CF8235195 | B3E18430E5353F6FEF2E787551A78921 |
| 35D779D412FA3682330162FAEDC7D26E | B60F57B01A0382C9D9372E78D95D6386 |
| 40E292484019A58AD3AA5C99EF993614 | B5713261E7338431FF430DE6E1ACE47A |
| 44FADA41819963DD353E62026011F6D5 | BDB0A5261D139F7B4804C6B03A3E909F |
| 45ADCB2BDD43FB32F4BA9542E7788F13 | C0C457F28C7657FB5B99E2CDD447EED9 |
| 53F88B226236125C816B795BFB8E239E | D2B983C66658C8A3DEF1E77E12AB8689 |
| 66FF6F32FF7096206B48D8006854C568 | EB5F29A9A9EDCD600F2846403E4B4223 |
| 110F6A386798757904892EDB5866A453 | F0F1038A3F455EAFEAB73944CC09FC08 |
| 887E9654A1E8C956013BB5961A4FDC6B | FB24C79B390D3CA14755C1F3DF3E6600 |
Appendix 2: About Antiy
Starting from antivirus engine research and development team, Antiy now has developed into an advanced security product supplier with four research and development centers, nationwide detection and monitoring ability as well as products and services covering multiple countries. With a fifteen-year continual accumulation, Antiy has formed massive security knowledge and promoted advanced products and solutions against APT with integrated application of network detection, host defense, unknown threat identification, data analysis and security visual experiences. With the recognition of technical capacity by industry regulators, customers and partners, Antiy has consecutively awarded qualification of national security emergency support unit four times and one of the six of CNNVD first-level support units. Antiy detection engine for mobile is the first Chinese product that obtained the first AV – TEST (2013) annual awards and more than ten of the world’s famous security vendors choose Antiy as their detection partner.
More information about antivirus engine:
http://www.antiy.com
More information about Antiy anti-APT products:
http://www.antiy.cn