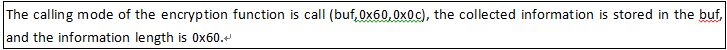AN ANALYSIS REPORT OF DDOS SAMPLE WITH THE DIGITAL SIGNATURE
An Analysis Report of DDoS Sample with the Digital Signature
By Antiy PTA Team
1 Overview
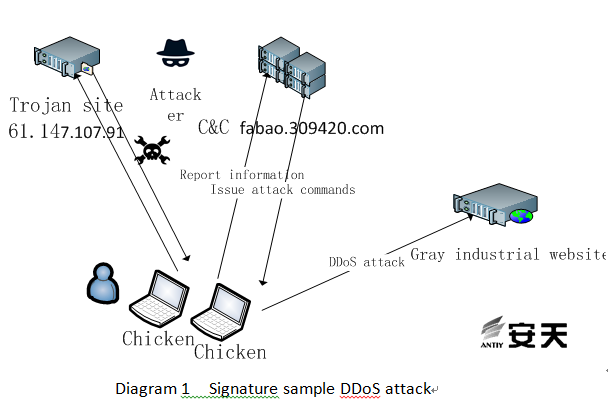
Recently, a malicious DDoS program with the expired signature has been detected by Antiy PTA team through the situation awareness system. The digital signature of the sample is stole from NHN USA Inc. (NHN brands range from the largest search engine website; and U.S. subsidiary is mainly engaged in online game development.). The digital signature has been expired for evading the antivirus software testing, and may be spread widely at underground market as it has been used in many samples. The DDoS sample includes many DDoS attacks, and mainly targets domestic online platforms, such as online diet pill, online gambling and electronic trading platforms. The goal of attacking the grey or illegal website may be to racketeer or compete. Through the detect and analysis of PTA device, the virus is a malicious DDoS sample, which releases rasmedia.dll to system32 directory, installs WinHelp32 service and runs CMD to self-delete; in addition, it can establish two threads to prevent the service from self-deleting and conduct DDoS attacks respectively. The attacker uses fabao.309420.com:7002 as C2 to communicate with the DDoS sample and distribute attack tasks. Within a short time, we found that several websites have been attacked with DDoS.
2 Sample analysis
2.1 Sample label
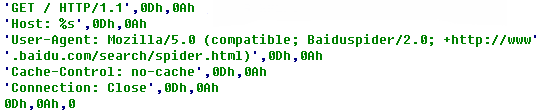
The PTD detects a malicious code transmission event of hxxp://61.147.107.91:8082/get.exe; its details are as follows:
| Virus name | Trojan[Backdoor]/Win32.DDOS |
| Original file name | get.exe |
| MD5 | b8f83b1e12ac61d8045a44561c5b7863 |
| Processor architecture | X86-32 |
| File size | 327.19 KB |
| File format | BinExecute/Microsoft.EXE[:X86] |
| Timestamp | 2015-10-28 14:07:22 |
| Digital signature | NO |
| Shell type | None |
| Compiled language | Compiler/Microsoft.VISUAL_C[:v6.0] |
| First VT upload time | 2015-12-06 |
| VT testing result | 47/55 |
2.2 Running process
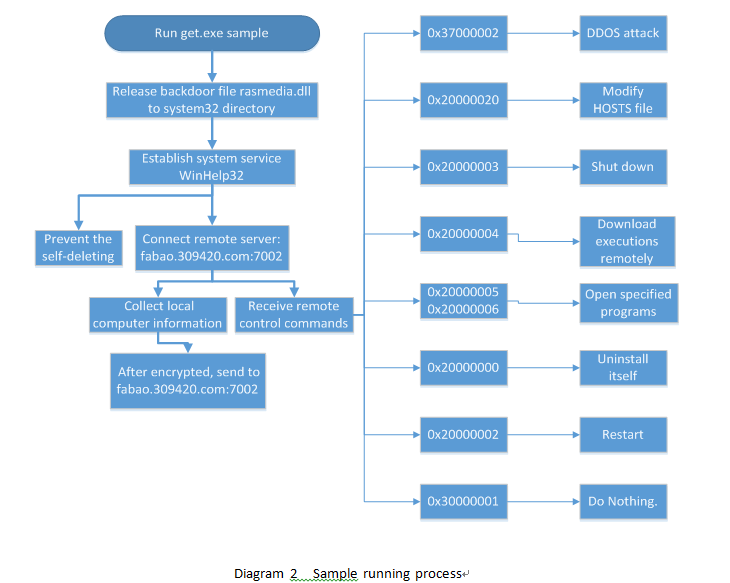
After running, the virus sample releases rasmedia.dll file to system32 directory, installs WinHelp32 service and runs CMD to self-delete. The service program is invert-connected to fabao.309420.com:7002 for reporting the victim’s computer information; two threads are established to prevent the service from self-deleting and receive DDoS attack commands form the server respectively.
2.3 Detailed analysis
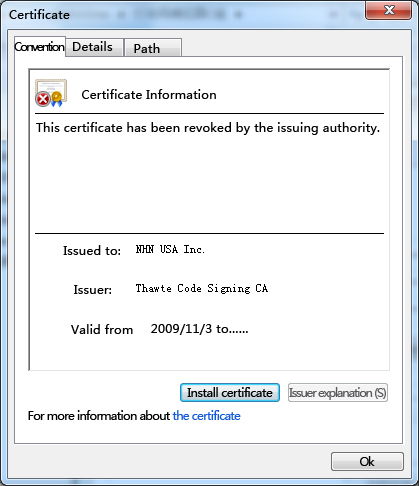
The sample includes information about the digital signature of NHN USA Inc., which has been expired with the valid period from November 3, 2009 to October 29, 2011.
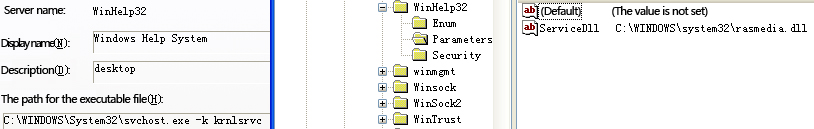
With the running of the sample get.exe, the backdoor file rasmedia.dll is released to system32 directory; for each release, the file end will be filled randomly with data to create different file hashes, and as releasing the file to system32 directory will be failure on the system which has opened UAC, rasmedia.dll will be dynamically loaded and started up as a service through calling the Install function exported. Finally, the sample get.exe calls cmd.exe to implement the self-delete. Service attribute information and dll path are as follows:
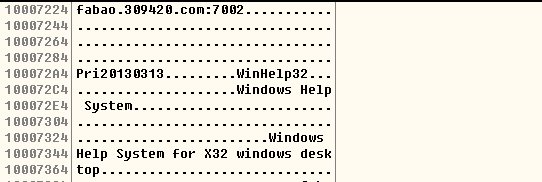
With the start of WinHelp32 service, the corresponding backdoor dll file is loaded and run. First, dll can decrypt dynamically the domain port to be connected: fabao.309420.com:7002 and other information, just for later use:
Then, rasmedia.dll creates two main threads: one is applied for preventing itself from deleting; another is for getting remote commands through the internet to implement the relevant operations, such as DDoS.
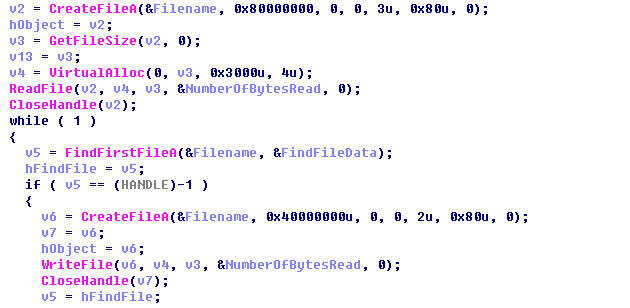
In order to prevent from being deleted, its own data are first read and stored in the buffer area, and if own files are not included after recycle judgments, the content in the buffer area would be rewritten into the files; the main code is as follows:
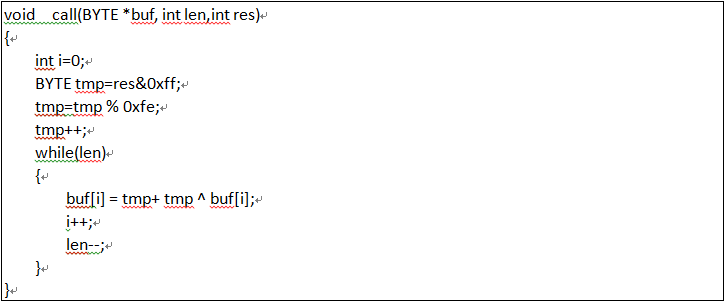
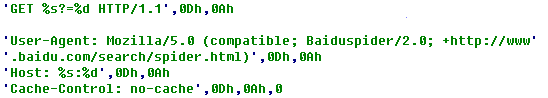
Another thread: first, the local host information are collected, such as name, system edition and disk size; and then encrypted and sent to the remote control end; its encryption algorithm is as follows:
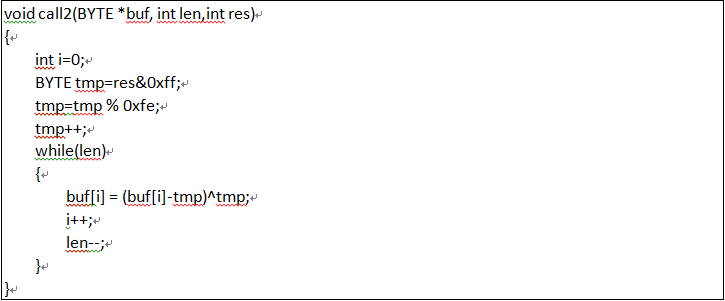
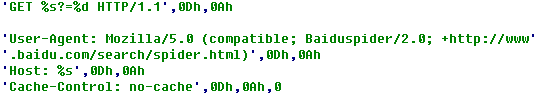
Then, dll obtains data from fabao.309420.com:7002 continuously, the format analysis to data decrypted will be conducted again, and the decryption algorithm is as follows:
Through the above two functions, we found that the encryption function is corresponding with the decryption function.
Data communication protocol: Control command (4 bytes) + data size (4 bytes) +data
Then the relevant operations are executed through matching control codes, and the control codes received are often 0x31000002 and 0x32000002, which are related with DDOS. In the case of 0x31000002, the decrypted data are as follows:
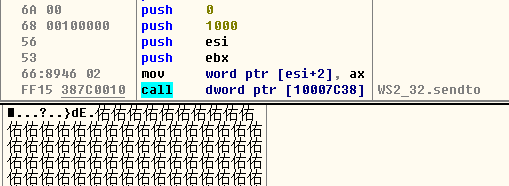
In this situation, an IP address is obtained, then several threads will be established by dll to conduct DDOS attack to the obtained IPs continuously with the data package size of 0x1000 and the randomly generated content; the code is as follows:
In the case of 0x32000002, the decrypted data are as follows:
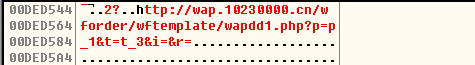
A website with parameters is obtained here:
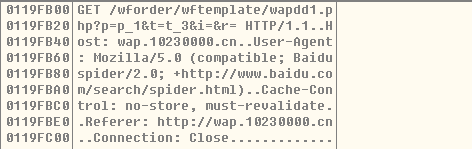
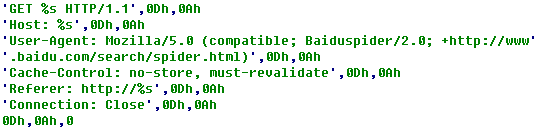
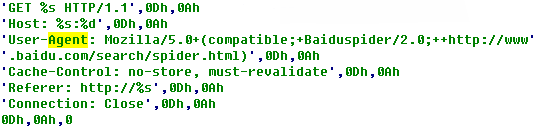
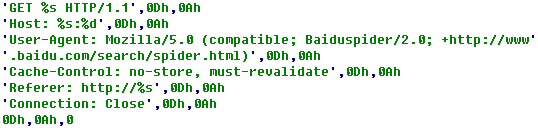
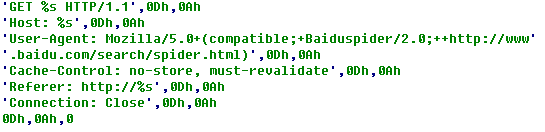
Then several threads are established to launch a large number of GET requests so that to cause DDoS attacks; and the GET requests are as follows:
As shown above, the GET request data are filled by templates which are prepared in advance, and the corresponding templates are:
Certainly, up to 10 templates are included in the dll; some of them are listed below:
First:
Third:
Fourth:
Fifth:
Sixth:
Besides the above functions, the dll file also provides other remote control functions. Through analyzing, the number of control commands in the DLL backdoor is up to 20, including:
| Control code | Function |
| 0x37000002 | DDoS |
| 0x41000001 | DDoS |
| 0x37000001 | DDoS |
| 0x32000004 | DDoS |
| 0x33000001 | DDoS |
| 0x36000001 | DDoS |
| 0x32000002 | DDoS |
| 0x31000005 | DDoS |
| 0x32000001 | DDoS |
| 0x31000003 | DDoS |
| 0x30000001 | Do nothing |
| 0x31000001 | DDoS |
| 0x31000002 | DDoS |
| 0x20000020 | Modify HOSTS |
| 0x20000003 | Shut down |
| 0x20000004 | Download executions remotely |
| 0x20000005 | Open specified programs |
| 0x20000006 | Open specified programs |
| 0x20000000 | Uninstall itself |
| 0x20000002 | Restart |
3 Network structure analysis
3.1 Network infrastructure
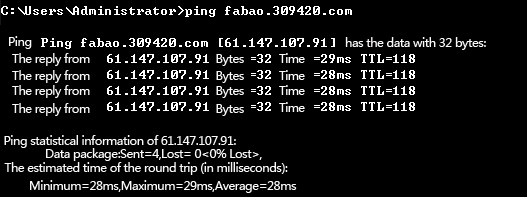
According to the sample analysis, the attacker uses 61.147.107.91 directed by fabao.309420.com:7002 as a server to distribute DDoS attack tasks, while another port of the IP is acted as the Trojan download server. And no webs are deployed on the domain. As TTL return value from ping is 118, we guess that the operation system may be Win NT/2000/2003/XP. This domain points several IPs at different time periods. The hacker group is originated in 2013 with all IPs of Yangzhou Telecom in Jiangsu Province.
| Domain name | IP port | Operation system | Earliest time | Function | Description |
| fabao.309420.com:7002 | 61.147.107.91:7002 | Windows 2003 | 2015-10-12 | C2 server | |
| 61.147.107.91:8082 | Windows 2003 | 2015-10-12 | Trojan server | ||
| fabao.309420.com:7002 | 61.147.70.142:7002 | Windows 2003 | 2015-11-19 | C2 server | |
| fabao.309420.com:7002 | 61.147.103.178:7002 | 2015-06-18 | C2 server | ||
| fabao.309420.com:7002 | 61.147.103.117:7002 | 2013-06-03 | C2 server | ||
| fabao.309420.com:7002 | 61.147.103.99:7002 | 2013-04-17 | C2 server |
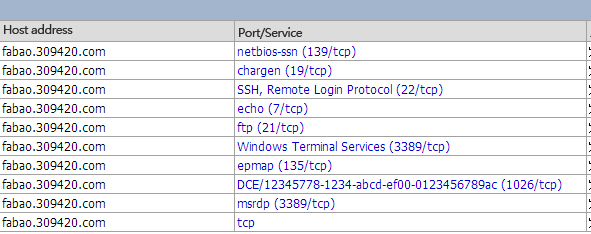
We found that an X-Scan server has been used and the following ports are opened: 135, 139, 21, 22, and 3389
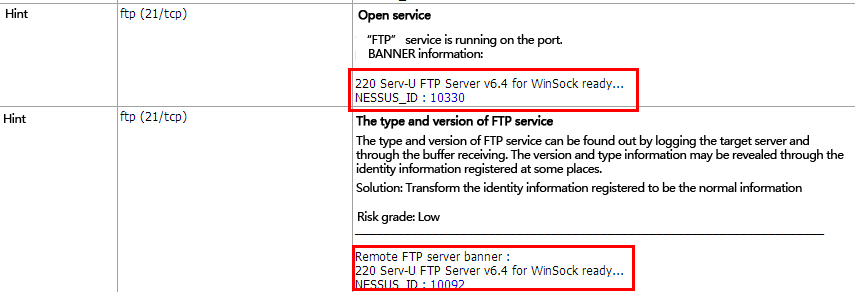
After testing, Serv-U FTP Server v6.4 is running at the port 21.
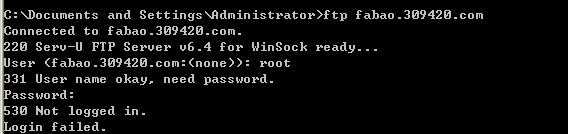
After trying to login, we found the root user has existed:
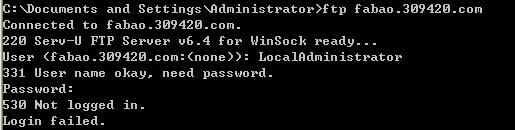
Default administrator of Serv-U: LocalAdministrator, default password: #l@$ak#.lk;0@P; after trying to login, we found the default administrator has existed, but the default password has been changed.
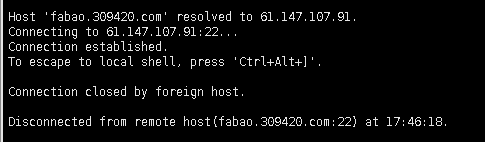
We found the target server has opened the port 22 and SSH service, and after trying to connect, we got the following content, and suspect the IP may be limited.
The target server also has opened the port 3389 and connected with remote desktop connection service provided by the system. The target server system is Windows Server 2003, just as expected.
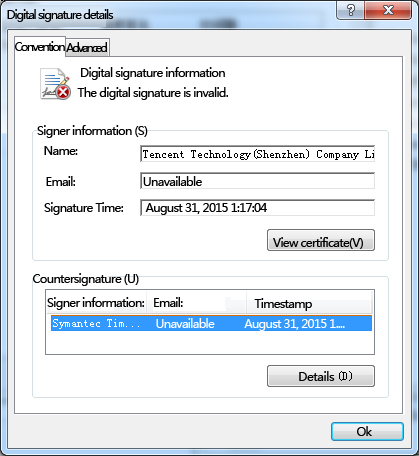
Up to now, no weak passwords have been found. The fake Tencent digital signature is applied by the sample 84747986208f11f326a890451988064f that communicates with the control terminal to evade the test.
4 Harmful impacts
4.1 Victim websites
Through monitoring, we found that the following targets have been attacked:
| Control code | Function |
| http://wapkk.xford.cn/ | Diet pills |
| http://le.bjwcyls.com/ | New year payment |
| http://pqt.zoosnet.net | Web business |
| http://www.dfr4fs.com | Card games |
| http://www.sbuluo.com | Perfume |
| http://www.a0686.com | Entertainment places |
| http://mmmoffice.com/ | |
| http://xs.igreenport.com.cn/ | |
| http://www.10230000.cn/ | Wholesale |
| http://www.qiuyun.sh.cn/ | |
| http://flm.flmapp.com/ | |
| http://xq2015.228.zj.cn/ | |
| http://vip6.airuis.net/ | |
| http://wapkf.huxiwa.cn/ | |
| http://wap.1008tuan.com/ | |
| http://www.shop3m.cn/ | |
| http://flm.alibag.cn/ | |
| http://le1s.xndnhc.com/ | |
| http://www.gzmfl.cn | |
| http://willittt.aliapp.com | |
| http://183.131.85.140:888 | |
| http://guanfang123.aliapp.com | |
| http://wap.pichia.cn | |
| http://mjgw.weizhangchaxun.com.cn | |
| http://aaa8.shengmingjiguang.cn | |
| http://flm.flm315.com | Make money online |
| http://vip6.zyhlwlc.com |
5 Hacker Trail
5.1 Inferences about the attacker
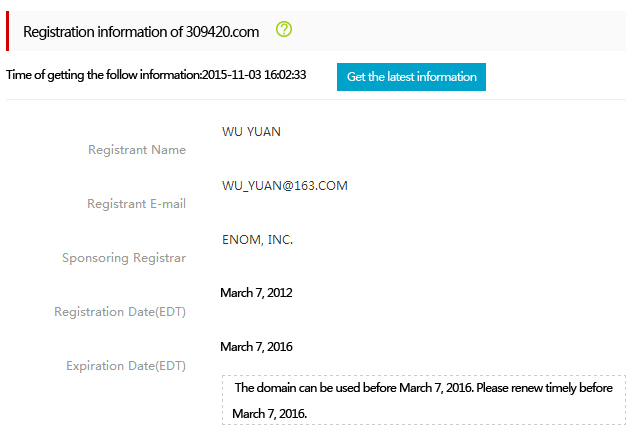
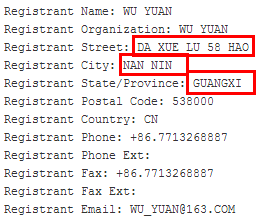
The PTA device extracts C2 to lock the domain name fabao.309420.com and through querying whois, the registration information is as follows:
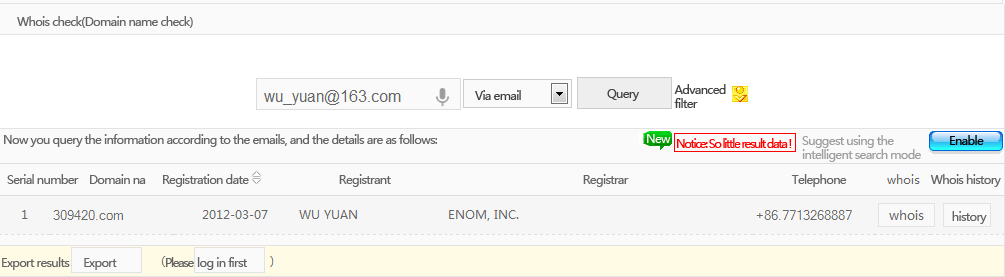
According to English information registered, the domain name is registered at Daxue Road 58, Nanning, Guangxi province, and the phone number 0771-3268887 in Nanning of Guangxi may be used. Through inputting the domain name, we obtain the 163 mailbox registered. According to the mailbox, we search the domain name applied:
Only 309420.com is applied.
5.2 Profitability analysis
The attack targets are mainly grey websites, which are characterized by the fierce competition in the corresponding industry. If a new online diet pill sale joins the online websites, it would also be attacked.
6 Summary
The DDoS attack group uses the expired signature and the fake digital signature to evade the antivirus software testing, bringing a great shock to the trust chain of the trusted system. Currently, antivirus software vendors have improved the tests to the digital signature, including valid period, forgery and so on.
7 Related information
The List of MD5
0b149f4ea7618a1d009409e889541b89
82d25d47c82246aed948031597141763
84747986208f11f326a890451988064f
801905dd2ff5b92355ba4c21a9ec1477
b8f83b1e12ac61d8045a44561c5b7863
7afeb59f339d3af22b8b1f51b8e01f15
4f6f7e8d6400fad699793449834153c1
087e5fbde0dec2d19eafbf749433792c
2ec8c7c9a3b051e2b44d74ebe4f53aa4
429b2d49ebf58634df7c6d2def01b406
685157a415112954f94a2ea7cfd796f4
b7d9c12c12a86fcea50371a0fe545641
9d390bd6a71eb4e2a0d3ba8d1fead3c6
572b568cfd3ce67b81ed980cfa6520b0
84bb036c3ee8681dec8e98c6356190b7
Appendix I: References
- NHN USA
http://www.nhnentusa.com/usa/index.nhn
Appendix II: About Antiy
Starting from antivirus engine research and development team, Antiy now has developed into an advanced security product supplier with four research and development centers, nationwide detection and monitoring ability as well as products and services covering multiple countries. With a fifteen-year continual accumulation, Antiy has formed massive security knowledge and promoted advanced products and solutions against APT with integrated application of network detection, host defense, unknown threat identification, data analysis and security visual experiences.
With the recognition of technical capacity by industry regulators, customers and partners, Antiy has consecutively awarded qualification of national security emergency support unit four times and one of the six of CNNVD first-level support units. Antiy detection engine for mobile is the first Chinese product that obtained the first AV – TEST (2013) annual awards and more than ten of the world’s famous security vendors choose Antiy as their detection partner.
| More information about antivirus engine: | http://www.antiy.com |
| More information about Anti-APT products | http://www.antiy.cn |
Appendix III:Document update log
| Updated date | Updated version | Updated content |
| yyyy-mm-dd 00:00 | ||
| yyyy-mm-dd 00:00 | ||
| yyyy-mm-dd 00:00 | ||
| yyyy-mm-dd 00:00 |