ANALYSIS OF GENERIC PASSWORD FOUND IN CRYPTKEEPER
ANALYSIS OF GENERIC PASSWORD FOUND IN CRYPTKEEPER
Antiy CERT
Draft: February 02, 2017, 15:00
Published: February 02, 2017, 15:00
Updated: February 02, 2017, 15:00
Background
On January 31, 2017, an article entitled “Cryptkeeper Linux Encryption App Fails at Job, Has One Letter Skeleton Key -” P “” was published on Softpedia, which mentioned CryptKeeper application used in Debian 9 had a BUG,which can allow the password set by the user for the encrypted folder to be replaced with the single character “p”, thereby making the character “p” as the general password for decrypting the folder encrypted by it.
The article cites the bug information submitted by Kirill Tkhai on January 26, 2017, in the debian community (bugs.debian.org). Searching through linkedin found, Kirill is currently working at the headquarters of the Russian-based virtualization software vendor Virtuozzo.
To verify the accuracy of this message, Antiy CERT has analyzed the source code of the involved module.
Event Verification and Analysis
CryptKeeper is an encrypted folder management software for Linux, which has the functions of installing and uninstalling encfs folder, changing folder password, creating new encrypted folder, and integrating with default file manager. CryptKeeper is written in GTK library; the encfs module is encapsulated at the bottom, and AES-192/256 algorithm is used to encrypt the file.
The code that generates the problem is located in cryptkeeper / src / encfs_wrapper.cpp, in which the author uses the parameter -S (Stdinpass) of encfs to read the password entered by the user from the standard input.
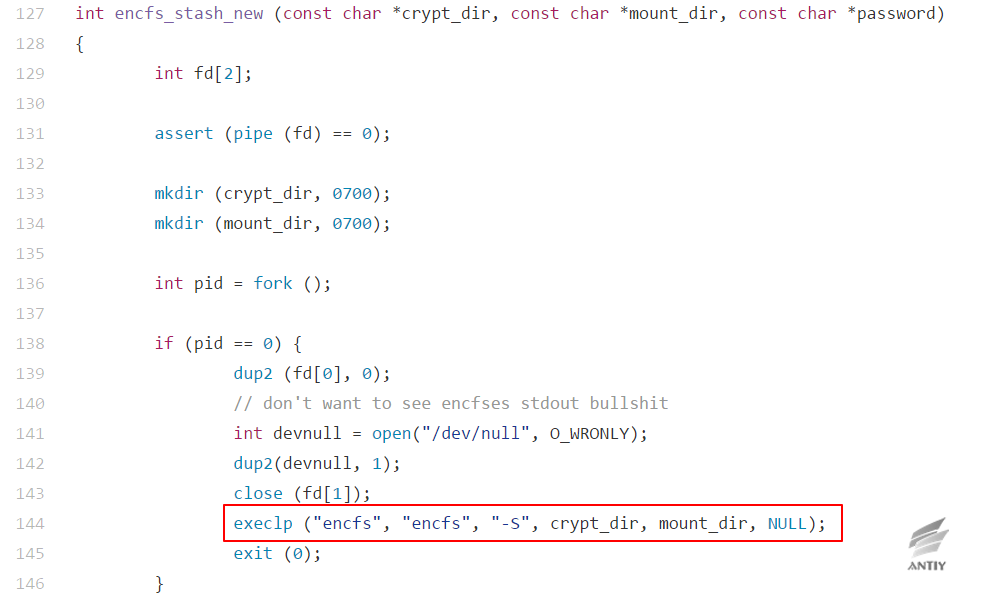
In the older version of encfs, two options are given to allow the user to manually select an encrypted mode:
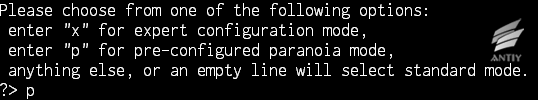
According to the old encfs setting, CryptKeeper hard-coded the “p \ n” option in the code to simulate keyboard input, thus to select paranoia mode (with higher encryption strength):
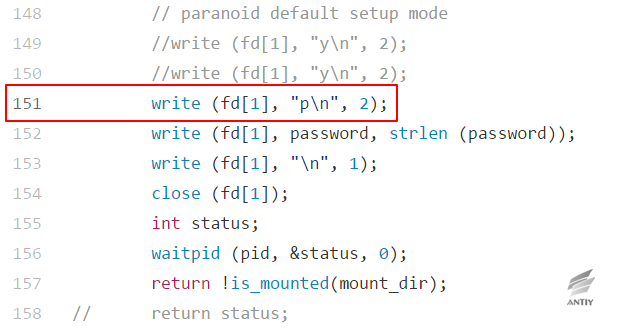
The incident involved in the Debian 9 is still in beta (unstable) stage, which uses the newer encfs (1.9.1-3 version). The new version of encfs no longer reads the pattern during the parsing of the parameter -S, but uses the preconfigured standard mode and reads the password directly from the input:
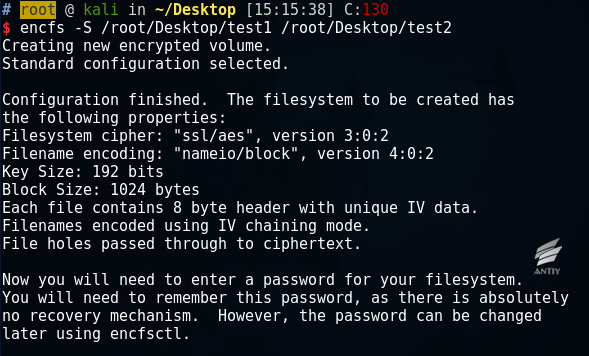
The corresponding process can also be seen in the source code, in which the Boolean variable useStdin is set when the parameter is –S, and read password through fgets.
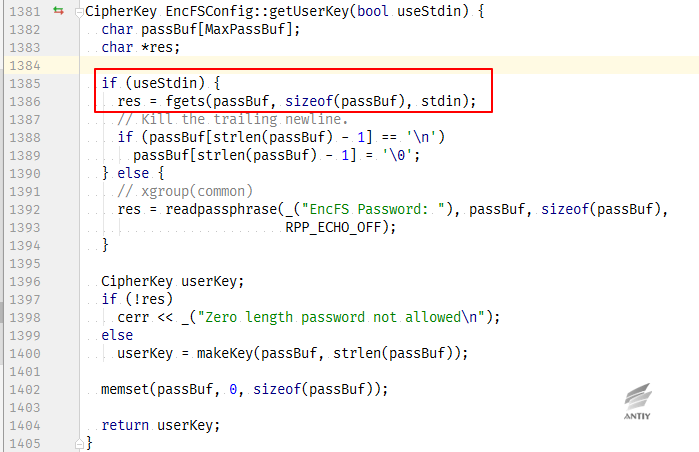
Encfs -related code that caused the problem of CryptKeeper is submitted by the author in September 2016.
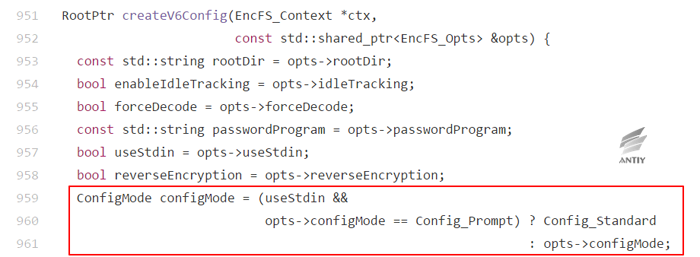
In the new version of encfs, the specified pattern is as follows:
In the old version, the specified pattern used a different code:
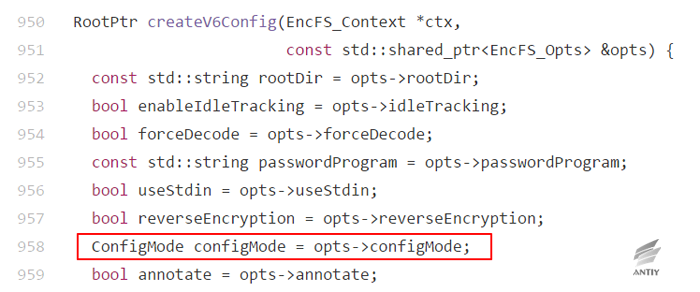
That is, whether or not useStdin (-S) is specified for the same Config_Prompt pattern, the behavior is inconsistent in both versions. In the new version, standard pattern is used if -S is specified and the pattern is Config_Prompt.
Therefore, the hard-coded “p \ n” value in CryptKeeper is treated directly as a password by encfs, and the actual password to be used is discarded. Since the S-pattern turns off the input echo, the BUG is not easy to find.
When the users reload, enter the original password, you will get the following “password error” prompt:
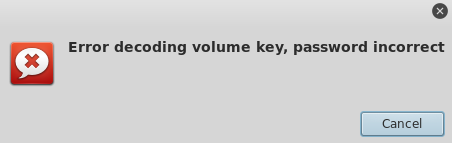
The Impact of the Event
The impact scope of the event is limited, the reasons are as follows:
1.Number of CryptKeeper users is small, the author even once stopped the maintenance;
2.The Bug is currently only appeared on the system used in the latest version of encfs (1.9.1-3), and this version has not been adopted by many releases;
3.After the event, the author of CryptKeeper has removed the software from the official Debian 9 source and will re-upload the software after repair.
However, for CryptKeeper users, the impact of the event is malicious. On the one hand, unknowing users can not access their encrypted documents once they are unmounted; on the other hand, the user data has no encryption strength in front of the attacker, and the privacy data can be easily decrypted and obtained.
About CryptKeeper Author
Tom Morton, author of CryptKeeper. His reserved e-mail is t-morton@blueyonder.co.uk and blueyonder.co.uk is registered as Virgin Media. Currently, both blueyonder.co.uk and virginmedia.com point to the same page. Virgin Media is a UK-based company that provides businesses and consumers with fixed and mobile telephony, television and broadband Internet services.
In 1995, he received a bachelor’s degree in political science from the University of Bristol to study American politics, international relations, political theory, and Thatcherism. The author started the CryptKeeper project at github during the period of Virgin Media’s Executive Planning Director. The code was first submitted on July 12, 2007. The current author serves as Senior Vice President (SVP Strategy) in U.S. R / GA company.
Conclusions
Through the above analysis, it can be found that the direct cause of this incident is not the hard-code in CryptKeeper, but the change of parameters supported by encfs. However, the hard-code of CryptKeeper source code already has security risks since 2007, and it is amplified because of encfs’s modification until 2016, which ultimately becomes a common password that can be used by attacker to crack encrypted data. It is a case that is worth in-depth thinking.
Appendix 1: References
- The original news
- News sources
https://bugs.debian.org/cgi-bin/bugreport.cgi?bug=852751
- Wikipedia的Virgin Media items
https://en.wikipedia.org/wiki/Virgin_Media
- Author’s linkedin:
http://www.linkedin.com/in/realtommorton
- CryptKeeper source code
https://github.com/tomm/cryptkeeper
- encfs source code
https://github.com/vgough/encfs
- Heartbleed vulnerability(CVE-2014-0160)FAQ,Antiy Labs
http://www.antiy.com/response/heartbleed_faq.html
- “Analysis and Summarization of Unofficial Version of XcodeGhost”,Antiy Labs
http://www.antiy.com/response/xcodeghost.html
Appendix 2:About Antiy
Starting from antivirus engine research and development team, Antiy now has developed into a group level security enterprise with Antiy Labs as headquarters and both enterprise security company and mobile security company as two wings. Antiy always adheres to the belief of securing and protecting user value and advocates independent research and innovation, forming the layout of the capacity of the whole chain in the following aspects: security detection engine, mobile security, network protocol reduction analysis, dynamic analysis, terminal protection, and virtualization security and so on. Antiy has fostered nationwide detection and monitoring capability with our products and services covering multiple countries. With effective combination of techniques and products of both big data analysis and security visualization, Antiy expands the group work competence of engineers and shortens the product response cycle by massive automation sample analysis platform. With years’ continual accumulation of massive security threat knowledge library, Antiy promotes the solution of situational awareness and monitoring and early warning that targets against APT and at scale network and critical infrastructure, combining with the experience of integrated application of big data analysis and security visualization.
More than 30 famous security vendors and IT vendors select Antiy as their partner of detection capability. The antivirus engine of Antiy has provided security protection for nearly a hundred thousand network devices and security devices and nearly two hundred million mobile phones. The mobile detection engine of Antiy was the first Chinses product that won AV-TEST reward in the world. The technical strength of Antiy has been recognized by industry management organizations, customers and partners. Antiy has consecutively been awarded the qualification of national security emergency support unit four times and one of the six of CNNVD first-level support units. Antiy is the significant enterprise node of China emergency response system, which has provided alarms, in-depth analysis or systematic solution in a few severe security incidents, such as Code Red, Dvldr, Stuxnet, Bash Shellcode, Sandworm, and Equation and so on.
| More information about Antiy Labs: | http://www.antiy.com(Chinese)
https://www.antiy.net (English) |
| More information about enterprise security company: | http://www.antiy.cn |
| More information about Antiy AVL TEAM: | http://www.avlsec.com |
