Association Analysis on Some Group Mail Samples Using Social Engineering Techniques
Association Analysis on Some Group Mail Samples Using Social Engineering Techniques
Antiy Labs
First release time: 16:37, April 28, 2015
Update time of this version: 16:37, May 27, 2015
Contents
2.1 Extraction of Metadata of the E-mail
2.3 Description of Local Behaviors
2.4 Description of Network Behavior
3.3 Description of Local Behavior
3.4 Description of Network Behavior
4.1 Structure Chain Comparison
4.6 An Analysis on Attacking Time
1 Background
In recent years, the bait mailbox of Antiy has captured massive malicious emails that uses social engineer techniques to carry out batch propagation. The analysts of Antiy extracted randomly two emails with the same attachment attack method for starter of analysis. The capture data of the first email is April 11, 2015. It is the phishing email that disguises as JPMorgan Chase & Co.. It contained a ZIP compression package that became PE file with PDF icon after being decompressed. The PE file would donwload other files from the backend after it was operated. The capture date of the other email is Aril 13, 2015. The attachment behaviors of them were the same. The CERT analysts of Antiy analyzed the first email sample, then related the propagation methods, techniques of attachment files of both emails, and finally carried out complete correlation analysis and summary by extracting similar features and digging up more similar emails.
2 Analysis of E-mail 1
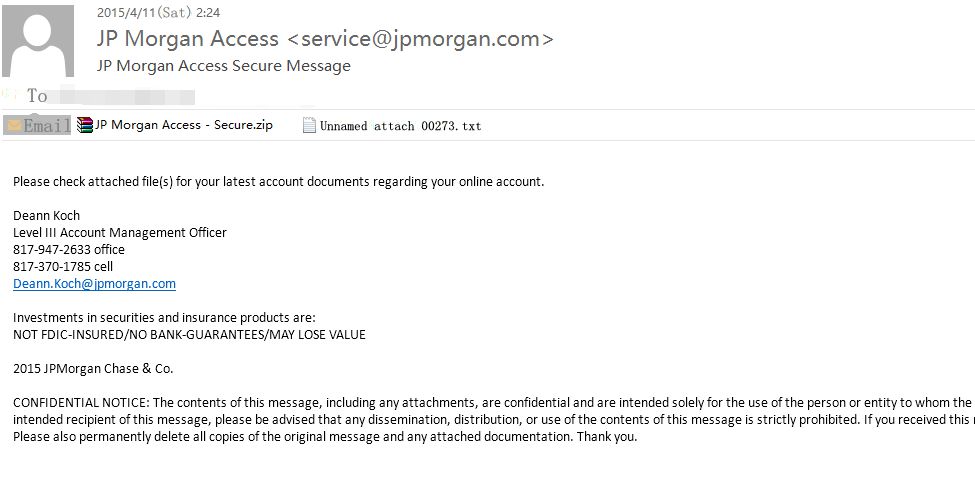
Content of the first e-mail:
Figure1: Content of original e-mail
2.1 Extraction of Metadata of the E-mail
| E-mail subject | JP Morgan Access Secure Message |
| Time for sending | 2015/4/11 (Saturday) 2:24 |
| Sender | JP Morgan Access [service@jpmorgan.com] |
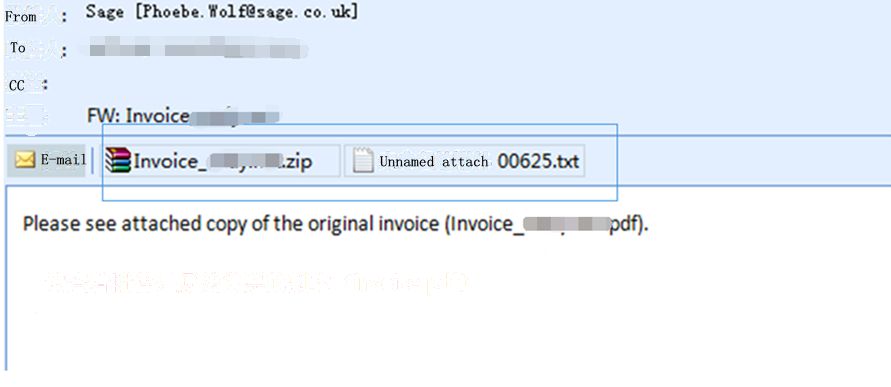
| Name of attachment 1 | JP Morgan Access – Secure.zip |
| Name of attachment 2 | Unnaming attachment 00273.txt |
This email was sent by disguising as JPMorgan Chase & Co..
Note: JPMorgan Chase & Co. is an American multinational banking and financial services holding company. It is the largest bank in the United States, with total assets of US$2.6 trillion. It is a major provider of financial services, and according to Forbes magazine is the world’s third largest public company based on a composite ranking. The hedge fund unit of JPMorgan Chase is the second largest hedge fund in the United States. (From Wikipedia)
The email uses social engineering technique to lure users to open. Social engineering attack refers to psychological manipulation of people into performing actions or divulging confidential information for the purpose of information gathering, fraud, or system access. The social engineering attack method of email malware is: luring victims to click attachment by sending emails with fraud and camouflag subjects. This email makes use of the huge user groups of JPMorgan Chase& Co to lure user to click attachment for checking bills by making the sensitive topic of on-line bank accounts as bait. Moreover, the “Confidential notice” claims that the content is confidential. Even if users don’t have the on-line bank account of JPMorgan Chase& Co or receive the email mistakenly, they would also be interested in the attachment out of curiosity after finding the confidential content.
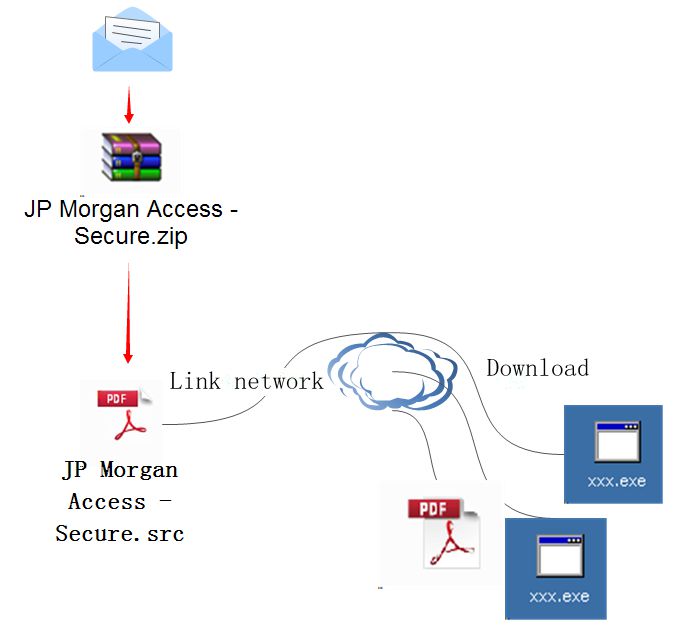
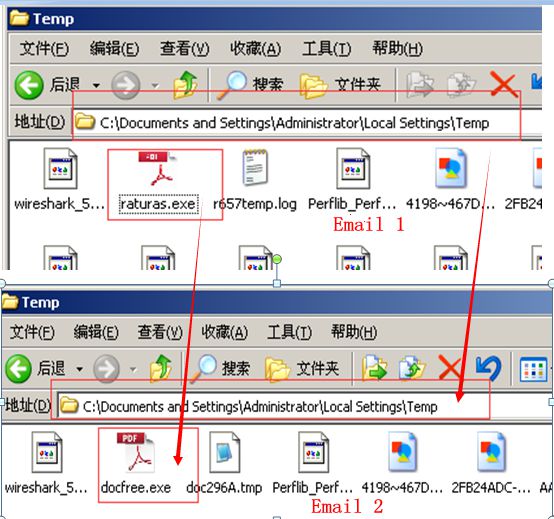
The email attachment is a ZIP package that belongs to downloader virus. The ZIP package is the file with PDF icon and src extention name that is for screen protection program. In fact, it is a PE executable program that can operates PE file automatically by double clicking under the unfamiliar situation.
The following is the figure of email structure and behavioral chain.
Figure2: Structure+ Behavioral chain
2.2 Sample Analysis
Sample tag:
| Virus name | Trojan[Downloader]/Win32.Upatre |
| Original file name | JP Morgan Access – Secure.src |
| MD5 | 32E1F5DED6E9C573293BB6343F785A9F |
| Handler architecture | X86-32 |
| File size | 24,064 bytes |
| File format | BinExecute/Microsoft.EXE[:X86] |
| Time stamp | 2004-09-05 12:06:14 |
| Digital signature | NO |
| Shell type | None |
| Compiler language | Microsoft Visual C++ |
| First upload time on VT | 2015-03-02 |
| Detection result of VT | 48 / 57 |
| Sample characterization | Downloader |
2.3 Description of Local Behaviors
General description:
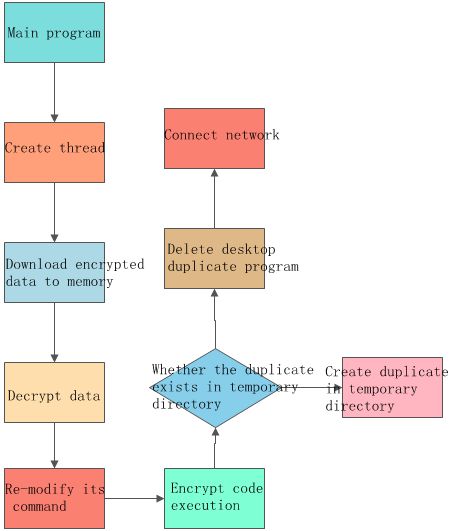
The sample is a kind of executable file with the size of 24KB that has the functionality of anti-debugging. It needs to experience a series of decryption steps to decrypt malware. It makes use of Windows message mechanism to create hidden window and write code into custom functions. After its operation, it would check whether the process duplicate exists in temporary directory: if so, it continues to operate; if not, it copies itself into temporary directory and changes its name as “raturas.exe”. It modifies commands by itself, and encrypts and stores key code in its own process in the form of file. After it decrypts the encrypted data, it carries out another new round of downloading its own process in order to download other process files from network.
Detail description:
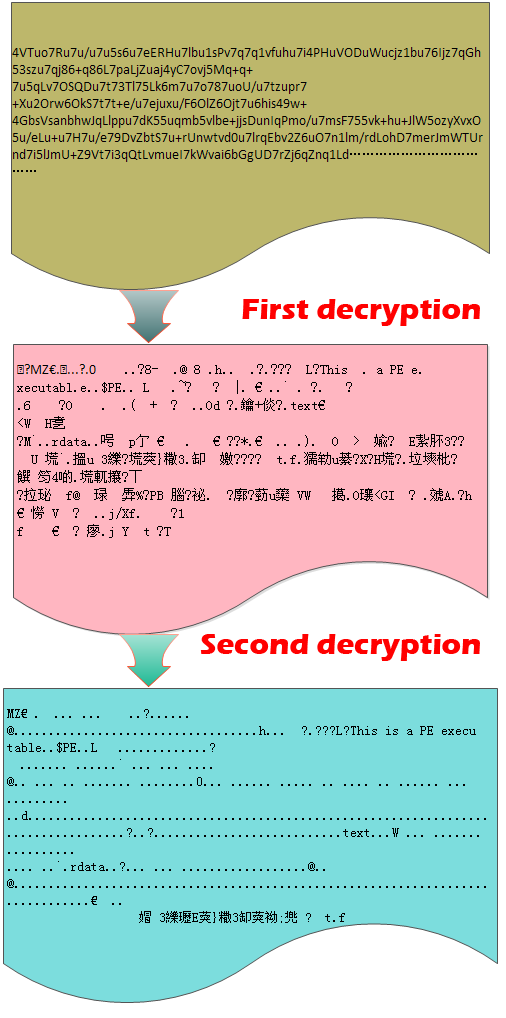
The malware creates a thread firstly, then carries out thread switch by message mechanism and puts the thread at the custom functions of message for operation. The malware puts encrypted data in memory 810000, and then experiences the following decryption 1 code field to operate primary decryption. It stores the decrypted data in 820000 filed. Thereafter the malware has finished primary decryption. Then it experiences the second decryption via 403CCC. The finished data is put in 83000, which is a new PE executable file.
Figure 3-1: First decryption
Figure 3-2: Second decryption
Figure 4: Decrypted data
Upon completion of the decryption, the malware creates a sub-process. Then, it applies space, writes code and executes code in the sub-process. Then, the sub-process starts running and connects to the network.
2.4 Description of Network Behavior
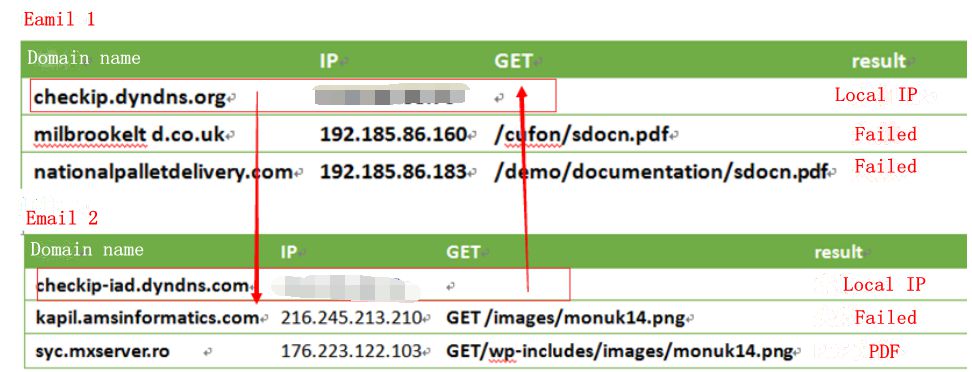
Once executed, the malware communicates with the remote server to download files. It visits the following domain names and servers:
| Domain Name | IP | GET | result |
| checkip.dyndns.org | ********** | Local IP | |
| milbrookelt d.co.uk | 192.185.86.160 | /cufon/sdocn.pdf | Failed |
| nationalpalletdelivery.com | 192.185.86.183 | /demo/documentation/sdocn.pdf | Failed |
| 190.111.9.129 | Failed |
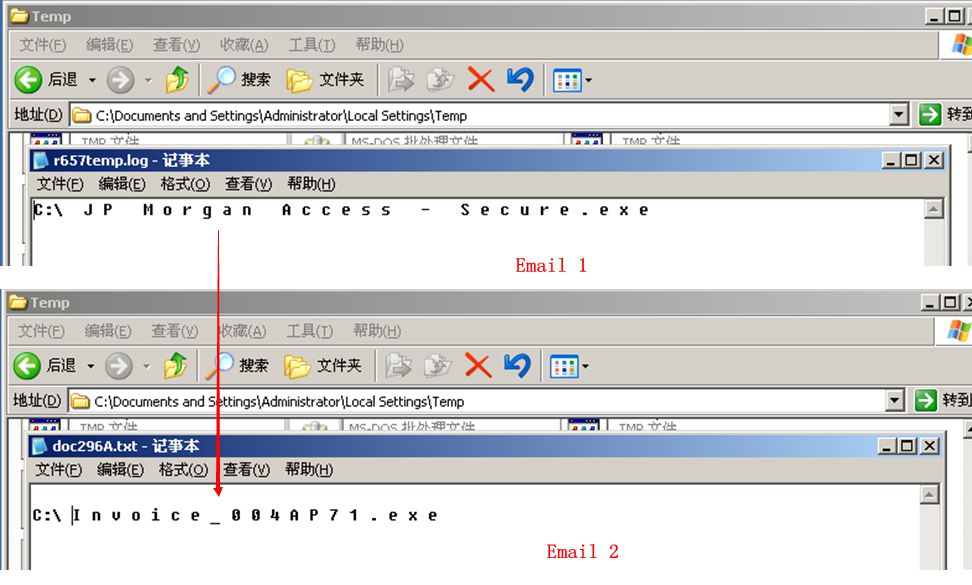
1) First, the malware creates a TXT file named r657temp.log in the system temporary directory, the content is:
| C : J P M o r g a n A c c e s s – S e c u r e . e x e |
Then, it calls the “delete” command to get the file deleted. The PE file is a copy created by the sample.
2) The malware connects to domain name checkip.dyndns.org, though which the local IP address can be obtained. The malware uses this domain name to test whether the network connectivity is normal. After obtaining the local IP address, it links to milbrookelt d.co.uk and nationalpalletdelivery.com to download the specified files. Finally, it links to IP address 190.111.9.129. These steps loop. The following figure shows the entire process of the malware.
Figure 5: Program flow chart
2.5 Sample Summary
The email first uses social engineering method. When the user click on an attachment, the file copy is hidden in the temporary directory and executes network connection. The sample is a “downloader”, not involving any startup function. Its code is both concise and effective.
3 Analysis of Email 2
Figure 6: Body of the email
3.1 Email Metadata Extraction
| Subject | Invoice***** |
| Sensing time | 2015/4/14 12:24 |
| Sender | ****** |
| Name of Attachment 1 | Invoice_***.zip |
| Name of Attachment 2 | unnamed attachment 00625.txt |
3.2 Sample Tag
| Name | Trojan[Downloader]/Win32.Upatre |
| Original filename | Invoice_004AP71 |
| MD5 | 6093329DBDA17782BB8DC31CF223A188 |
| Processor architecture | X86-32 |
| File size | 31232 bytes |
| File format | BinExecute/Microsoft.EXE[:X86] |
| Timestamp | 2006-05-11 20:46:41 |
| Digital signature | NO |
| Shell type | none |
| Compilation language | Microsoft Visual C++ |
| VT first update | 2015-04-13 |
| VT test results | 41 / 56 |
| Sample characterization | Downloader |
3.3 Description of Local Behavior
The local behaviors are the same with those of email 1 sample.
3.4 Description of Network Behavior
| Domain name | IP | GET | result |
| checkip-iad.dyndns.com | ** | Local IP | |
| kapil.amsinformatics.com | 216.245.213.210 | GET /images/monuk14.png | Failed |
| syc.mxserver.ro | 176.223.122.103 | GET/wp-includes/images/monuk14.png | PDF file |
When the attached file executes, it tries to download 2 files to the machine and executes them. One download fails and the other is a PDF file. As is shown in Figure 7, the PDF file appears to be real, but actually, it finishes downloading malware before being opened.
Figure 7: PDF file
The content of the PDF file doesn’t correspond with that of the social engineering email (invoice-related). Analysts from Antiy Labs speculate that mass emails using several social engineering techniques causing confusion. The second explanation is the email author failing to consider the consistency. Another possibility is: attackers do this on purpose, trying to convince users it is not a “junk” email.
4 Homology Analysis
Two emails were both captured in April 2015. We analyzed the homology between them by observing the overall structure and the code of the attachment. We assumed they are from the same author’s batch attack. Below is the association and comparison from 3 aspects.
- structure chain
- code behavior
- code structure
4.1 Structure Chain Comparison
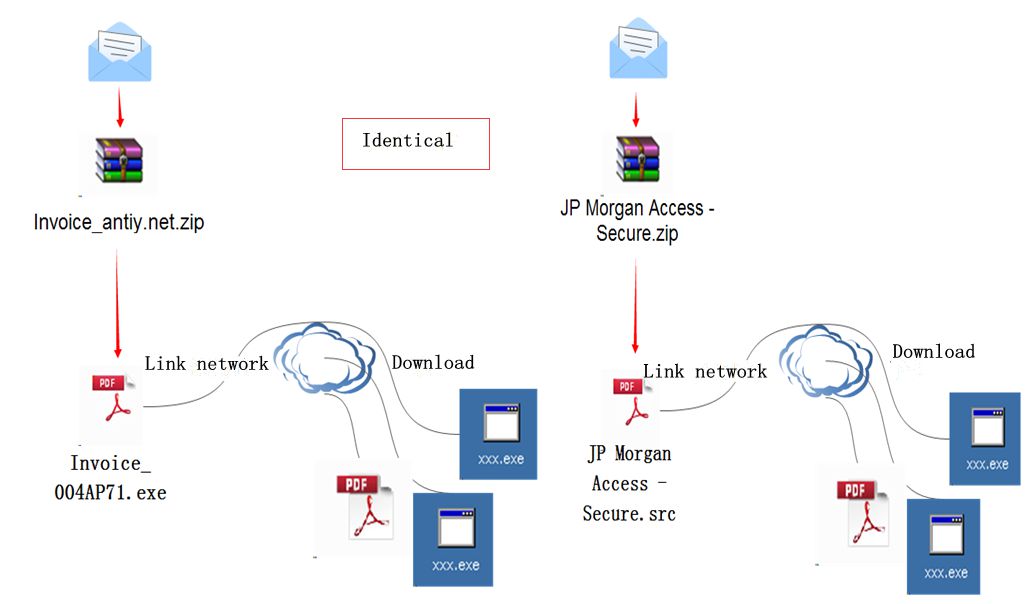
Figure 8: Structure + behavior chain comparison
The structure chains of the two emails are almost identical. They are a compressed package, which extracts a PE file with a PDF icon. The PE file downloads other files from the network once executed.
4.2 Code Behavior
Figure 9: Similar derived file directories and icons
As shown above, the samples create a copy in the temporary directory once executed. In email 1, the file name is raturas.exe; in email 2, the file name is docfree.exe. They both call CMD command line by creating a text file in the temporary directory, so as to delete the copy in Disk C.
Figure 10: Sample’s self-deletion method
4.3 Code Structure
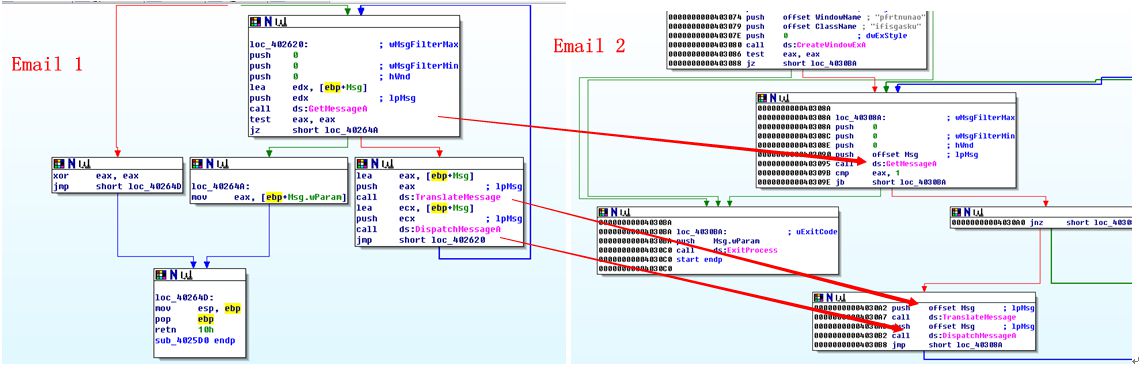
Figure 11: Message mechanism
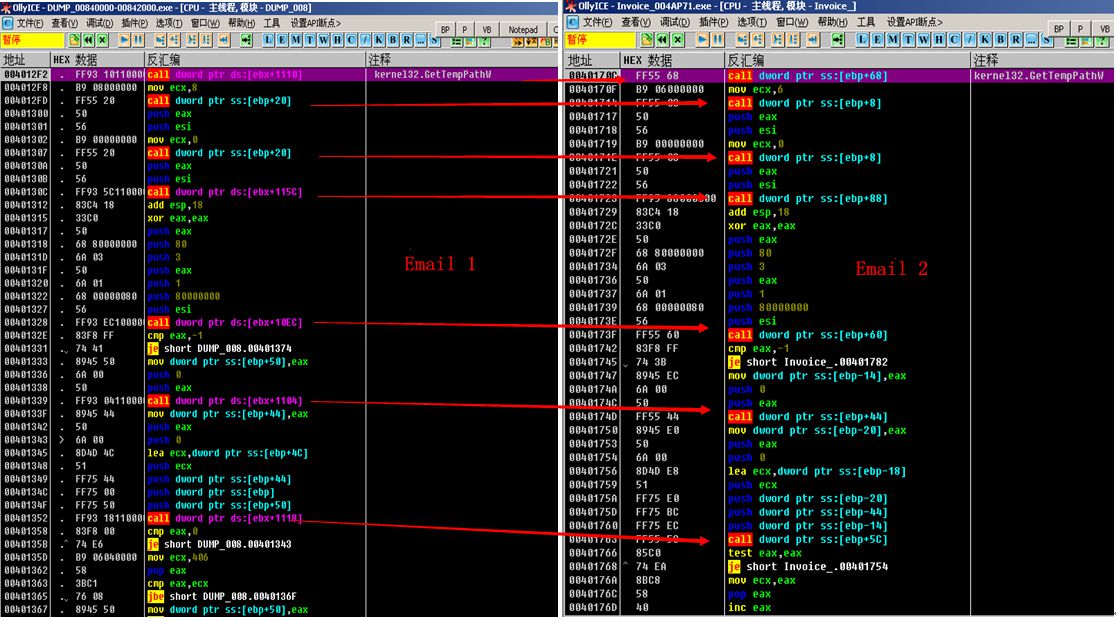
Figure 12: Structure of decrypted code
The two samples both write codes based on the message mechanism, writing the malware into the custom functions. They both decrypt the code for execution, and all APIs are accessed dynamically. As shown above, the code structures of the two samples are almost identical.
4.3.1 Network Behavior
Figure 13: Similarity of network behaviors
The two samples both first visit domain name checkip-iad.dyndns.com to test the network connectivity status. So, their networking method is also consistent.
4.4 Summery
By analyzing the structure, structure chain, sample local behavior, network behavior, sample code and other aspects of the two emails, we found they are highly homologous.
Based on the structure chain, attachment behavior and code structure, Antiy analysts extract more emails from the database for batch analysis.
4.5 Social Engineering Method
Through the characteristics of attachment and genetic relationship of structures, security analyst of ANTIY CERT extracted 110 emails, the size of the attachments are between 23 ~ 32kb, some of these emails treat bank cheque as a decoy while some treat a copy file as a decoy. Statistically we adopted labeling to these emails, as a result there are 14 kinds of tags:
- document
- credit detection
- no text
- fixed signature
- greetings
- salary
- annual report
- scanned copy
- bank statement
- transaction
- auto insurance
- cooperation partner
- online bank upgrade
- password reset
Classification Declaration:
- Document
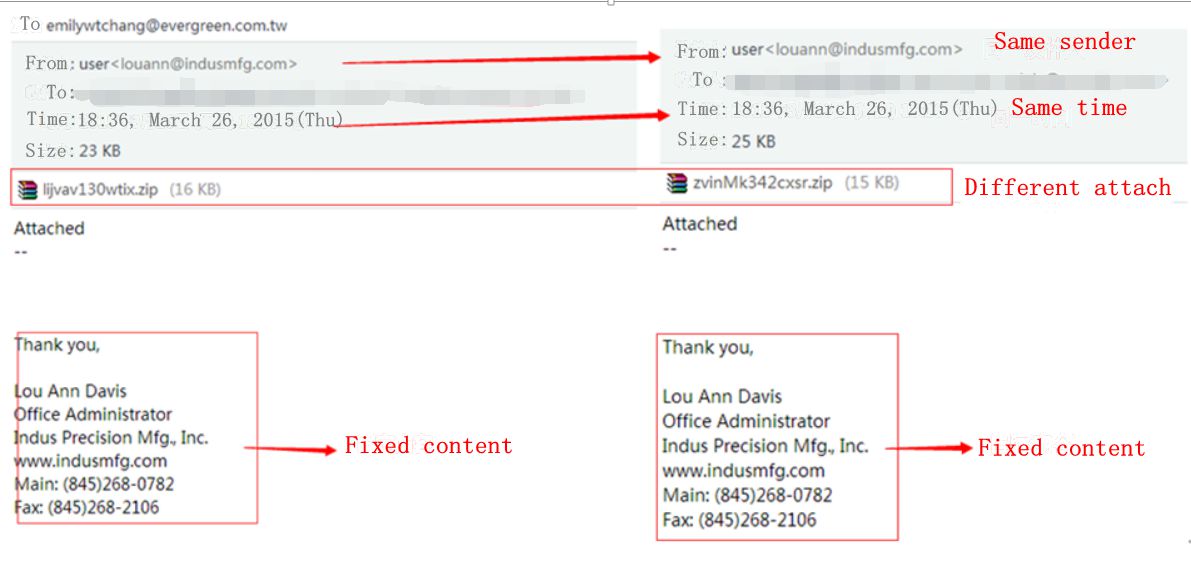
Attachments of this kind of phishing email all added word document in its names. While the topics and texts varying from time to time, including bank cheque or no text etc.. Please note that the attack codes that these attachments contained are same. For example:
Figure 14: An Example of an Email which its Text Related to Cheque
Figure 15: An Example of an Email which its Text Related to Bank
- No Text
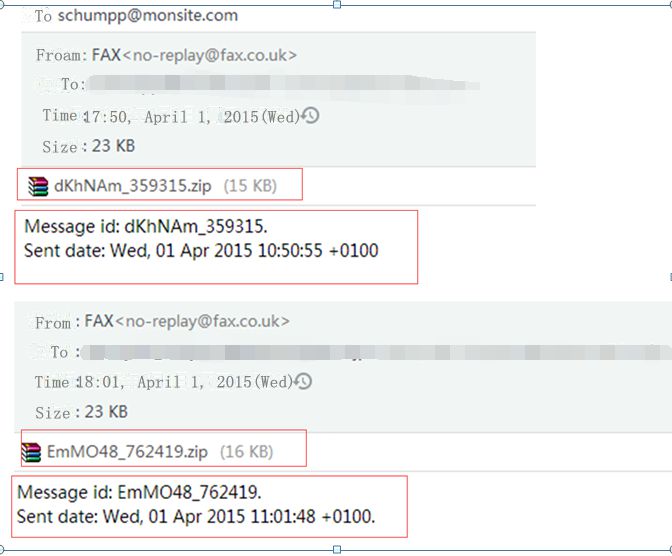
Figure 16: An Email Has No Text
Such kind of email has no text:
Message id: EmMO48_762419.
Sent date: Wed, 01 Apr 2015 11:01:48 +0100.
Such kind of email has no text:
- Fixed Signature
Figure 17: Fixed Signature
Through analysis, we observed that the attack time and attacker maybe same of one kind of email, as shown above, in the next section we will do a polymerization analysis on these 110 email about their sending time.
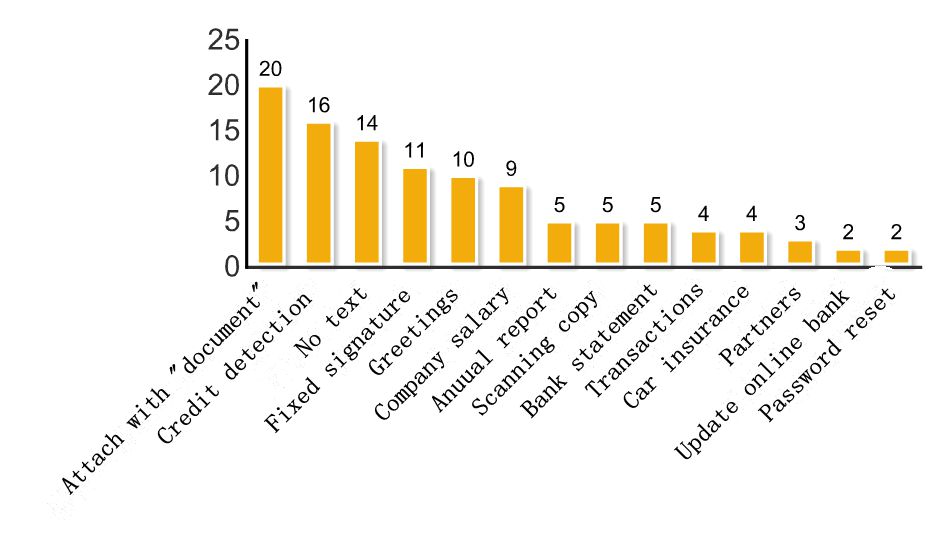
The picture below shows that most phishing emails choose to add word document to the name of attachment, credit detection, no text, fixed signature and greeting also are the common techniques for attacking.
Figure 18: Attack Technique Statistics
4.6 An Analysis on Attacking Time
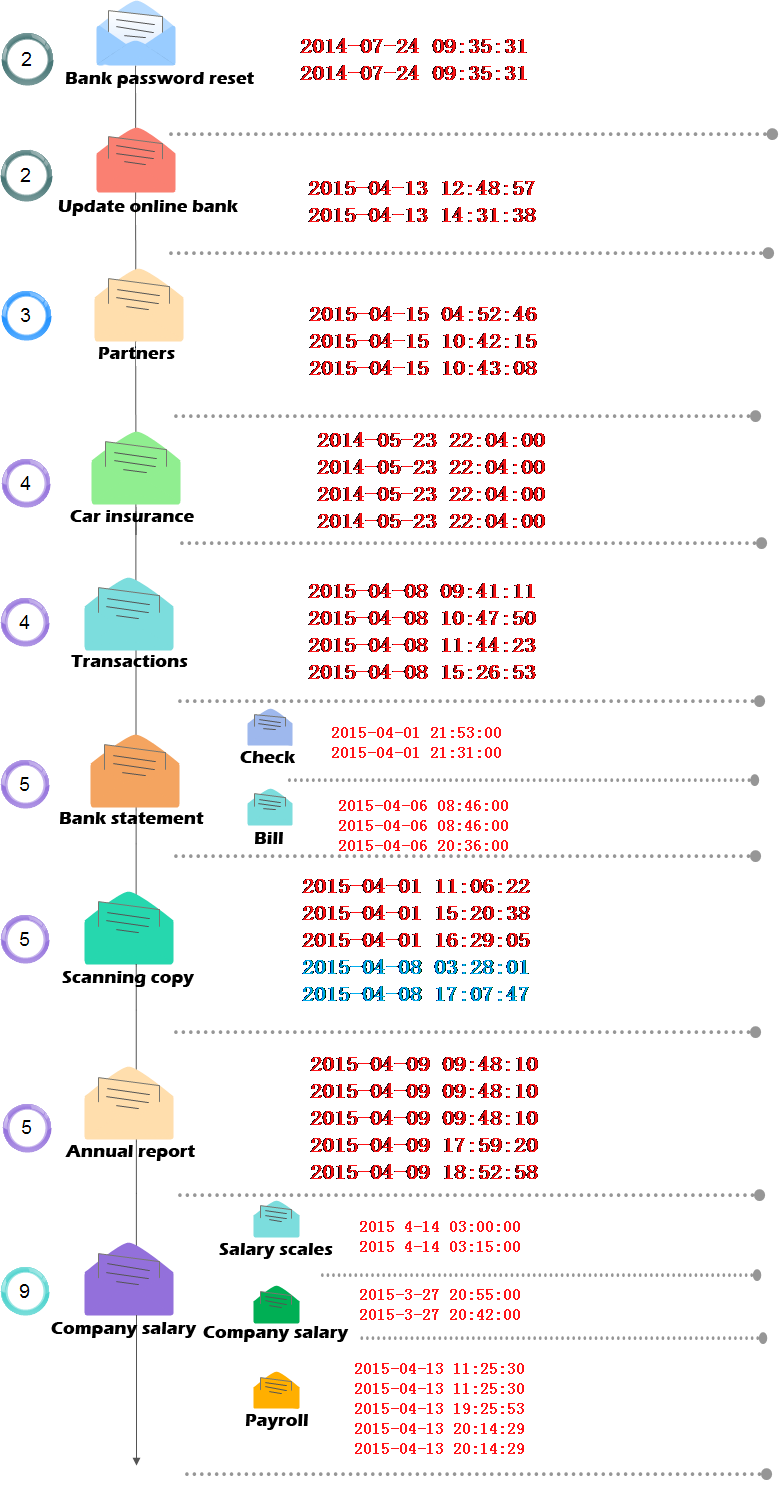
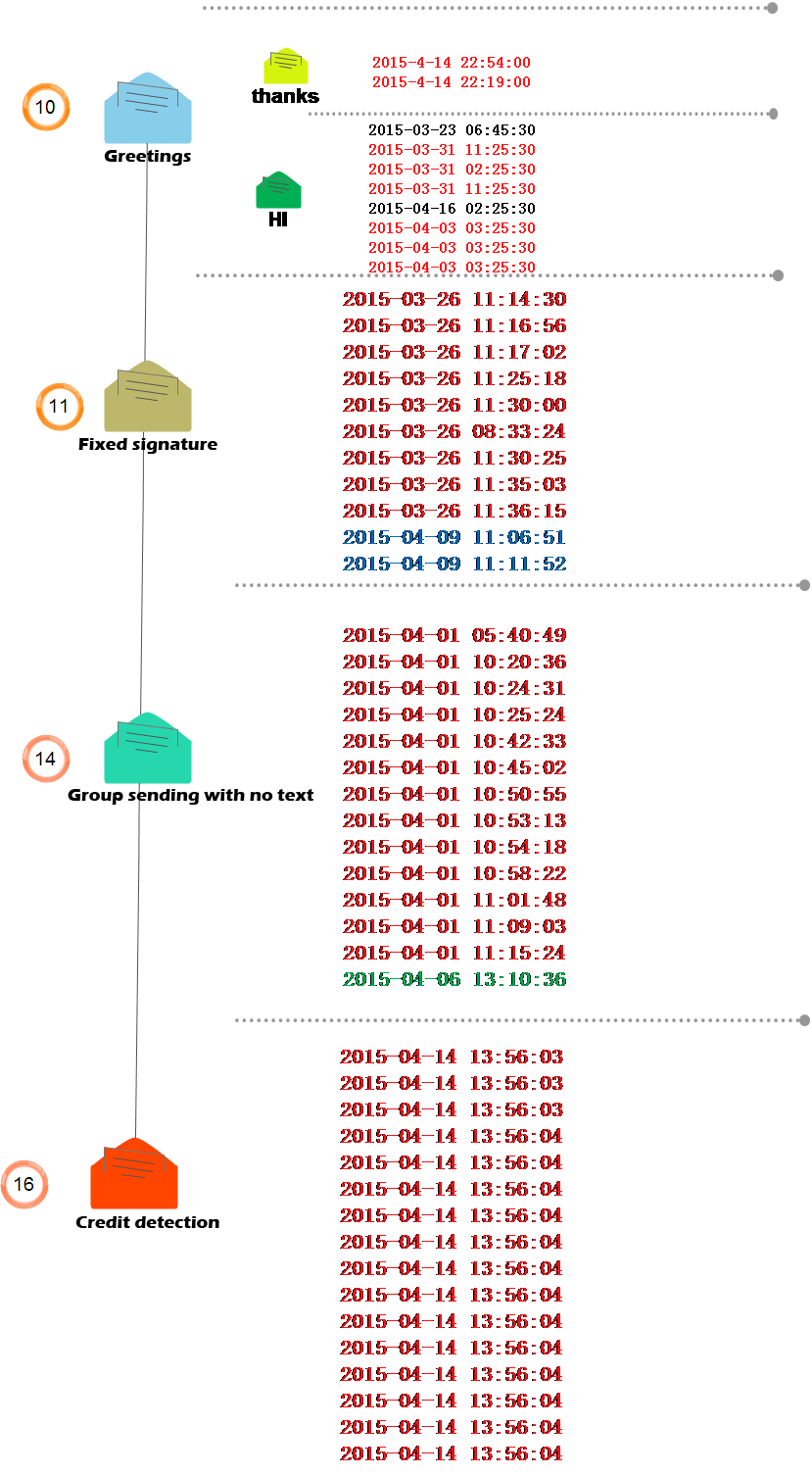
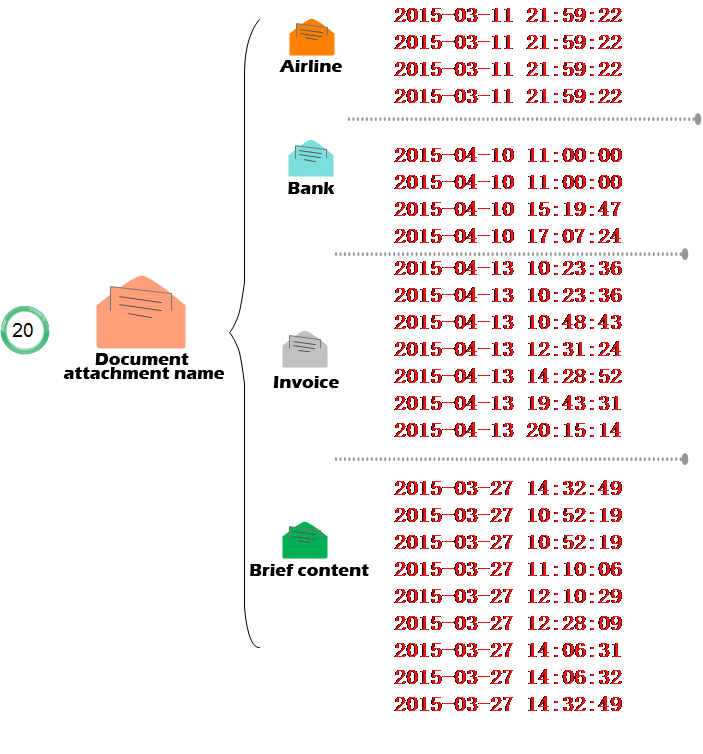
After analyzing the social engineering techniques and sending time of these 110 emails, we observed that almost all the emails which use the same social engineering technique were sent at a fixed time. See the figure below:
Figure 19: Extracting the Attacking Time of All Samples
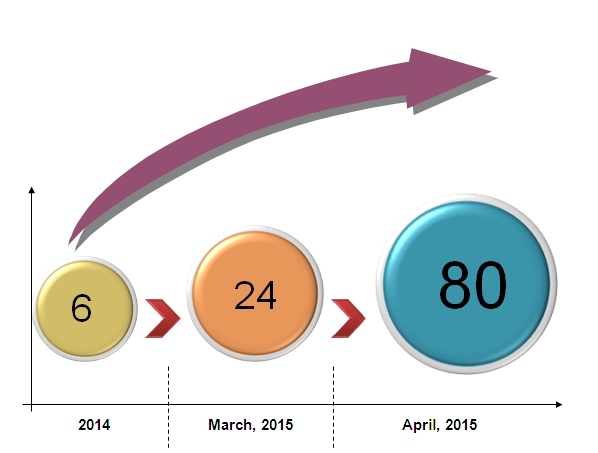
Figure 20: Time and Number of Attacks
Through time extraction of the attacks and analyzing, we observed that for the same kind of email, attackers are prefer mass sending, in other words, attackers will launch a large-scale attack at a certain time point. We also found that, the emails which are similar with what we analyzed now were detected as early as 2014, in March 2015, there appears a batch of attacks, and in April 2015, attacker launched a large-scale attack.
5 Conclusion
Phishing attacks is common in nowadays, as early as 1999,there is an out breaking of Happy99 virus, Melissa viruses, the two were regrade as the ancestor of e-mail virus, later following the Melissa’s source code, the LoveLetter and Magistr appeared. These viruses belong to the “worm” type, with the ability of self-diffusion, wide spreading and quick spreading, they brought a lot of pressure to network, meanwhile the are likely to be perceived and detected. But the entries of today’s email are totally different from the old fashioned “naive virus era”, there are macro viruses and other binary samples sent by API automatically, also there is APT attacks. The methods of attacks from e-mail attacks, phishing attacks, to spear phishing attacks. Now attackers use sophisticated methods instead of rough way in the past. Attack targets vary from “proliferation”, “strafe” to “snipe”.
Although the samples used for analyzing are not highly directional, it may exhibit the characteristics of selectively sending. This will also bring some lost to the victims. After introducing more sophisticated social engineering skills, there must be a certain percentage of users will be deceived in the attack. To victims, such kinds of attack lead to the same consequences to them as directional attack. As ANTIY CERT indicated in the report WPS Samples: The Blackmailer that we published before. Email threats still rampant in such an environment that browser, host, server system are strengthening, email threats is a good way to connect with users directly, which means that the email attack will last a long time, no matter it’s advanced threats, or botnets diffusion and other type of cybercrime.
(Liang Hongzhi at National Computer Virus Emergency Response Center did a great contribution to compile this report)
Appendix 1: References
- WPS Samples: The Blackmailer
- Link Address: http://www.antiy.com/response/CTB-Locker.html
Appendix 2: About Antiy
Anity Labs has developed as leading provider of advanced security products with four R&D centers, monitoring and warning capability covers nationwide, products and services radiates several countries. Starting from an antivirus engine R&D team, Anity has formed massive security threat knowledge library after 15 years’ accumulation, and put forward advanced products and solutions against APT (Advanced Persistent Threat) through combining with the experience of application network detection, host protection, evaluation of unknown threats, big data analysis and security visualization. The technical strength of Anity has been confirmed by industry administrative institutions, clients and our partners. Anity has earned the qualification of nation-level security emergency support units four years in a row. Anity is one of the six first-level support units of CNNVD. The mobile detection engine of Anity is the first Chinese product that won the annual award of AV-TEST (2013), More than ten security vendors around the world choose Anity as their partners of detection capability.
| For more information about antivirus engine of Antiy: | https://www.antiy.net |
| For more information about anti-APT products of Antiy: | http://www.antiy.cn |