Temporary Solution for Adobe Zero-day Vulnerability (CVE-2011-0609)
On March 16, 2011, Antiy CERT intercepted a malware sample targeting a vulnerability in Adobe products. Antiy engineers have confirmed that the vulnerability has been widely exploited. Attackers can send an Excel (.xls) document with an embedded Flash (.swf) file as an attachment. If users open the attachment, the attack will execute. Adobe has confirmed that current versions of Adobe Flash Player, Adobe Reader and Acrobat all have the problem. The vulnerability can be exploited in Windows, Mac, Linux and Solaris.
Currently, Adobe hasn’t released patches or related updates, but the attack programs have been publicized on the Internet. We predict that attacks exploiting this vulnerability will be frequent in the near future and suggest users be careful.
Temporary Solutions
The vulnerability cannot bypass DEP (Data Execution Prevention), so users can enable DEP to protect the computer. In addition, the 64-bit office 2010 system is not infected, because the vulnerability can only affect Win32 systems. Whenever users open an office document from an email attachment or the network, the sandbox mechanism will be triggered by office 2010.
We suggest that users use Microsoft’s EMET (Enhanced Mitigation Experience Toolkit). It is a security tool that targets emergent vulnerabilities. It uses DEP, SEHOP, and ASLR techniques to protect users even with no patches installed.
EMET website: http://go.microsoft.com/fwlink/?LinkID=200220&clcid=0×409
Configuration of EMET
1. Download EMET. The .Net Framework 2.0 is needed if we want to install EMET, as shown in Figure 1. After the installation, find and run the main program from the start menu, as shown in Figure 2
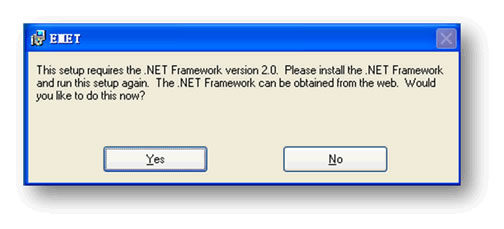
Figure 1: .Net Framework 2.0 is needed
Figure 2: Start the EMET
2. Click “Configure Apps” as shown in Figure 3.
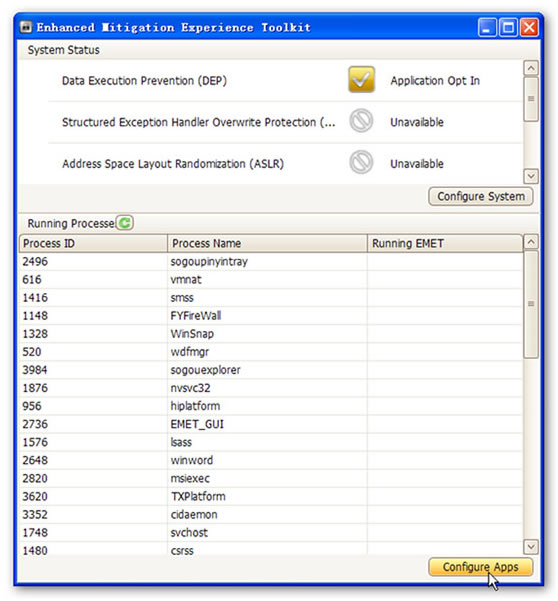
Figure 3: Config the EMET
3. Click “Add” as shown in Figure 4.
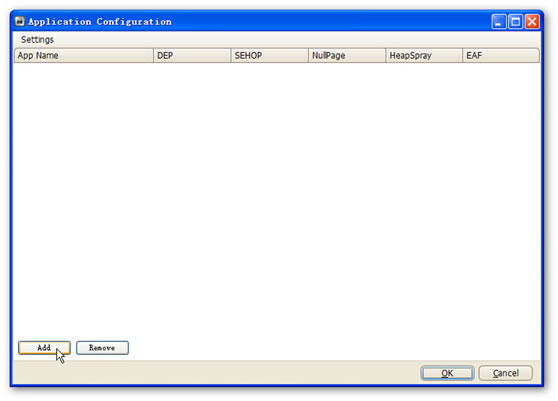
Figure 4
4. Find the installation path of Office, choose excel.exe and click “open”. For example: C:\Program Files\Microsoft Office\Office12\excel.exe, as shown in Figure 5 and 6.
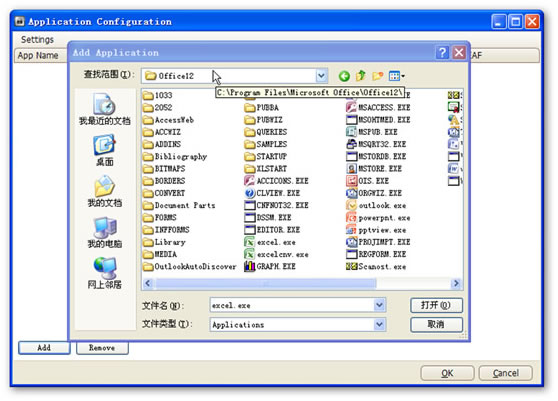
Figure 5: Choose excel.exe
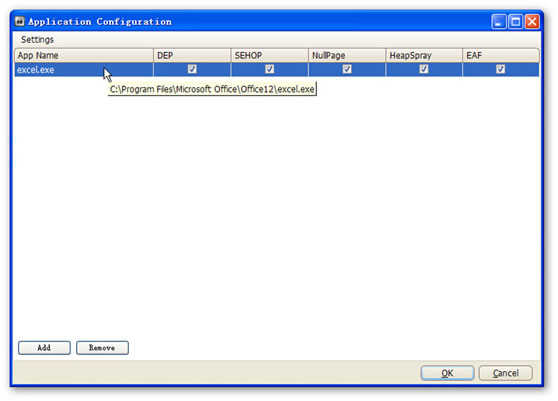
Figure 6: Click “OK” to Finish the Configuration
5. If you want to open the defense measures for other components, you can repeat the above steps.
Security Suggestions
Before official patches are published, Antiy engineers suggest that users be cautious about links or files from unknown sources. Users should update their antivirus software to the latest version and use it while surfing the Internet. Please pay attention to Adobe’s official latest news to obtain patches or update programs.
Adobe official website: http://www.adobe.com
Adobe security bulletin: http://www.adobe.com/support/security/advisories/apsa11-01.html
