TECHNOLOGICAL AND CHARACTERISTIC ANALYSIS OF NEW VARIANT OF RANSOMWARE FAMILY TESLACRYPT
Technological and characteristic analysis of new variant of Ransomware family TeslaCrypt
Antiy CERT
First Edition: 17:44, Apr.7, 2016
Pub Date: 14:23, Apr.8, 2016
Update: 10:07, Apr.8, 2016
1 Introduction
Antiy CERT recently found a new variant of ransomware TeslaCrypt, named TeslaCrypt 4.0, it has many characteristics, such as: do not modify the original file name after encryption, against security tools, own a PDB path, self-start through CMD, use unconventional function call, the same domain name can download multiple ransomware, etc. In particular, common ransomware will modify the extensions of encrypted files after infecting victim hosts, such as TeslaCrypt early version (.vvv,.mp3,.ccc、.abc,.ttt, etc), other ransomware Locky, CTB-Locker(.Locky,.oinpgca). But the latest variant of TeslaCrypt will do not modify the original file name extensions after encryption.
Ransomware TeslaCrypt was found in February, 2015 [1] which is modified on the basis of Cryptolocker. In its first version, TeslaCrypt claimed to use asymmetric encryption algorithm RSA – 2048, but it actually used symmetrical AES encryption algorithm, and then Cisco released a decryption tool that can decrypt files that is encrypted by TeslaCrypt when key. dat file is found [2];But in the subsequent multiple versions, ransomware TeslaCrypt began to use asymmetric RSA encryption algorithm and the encrypted files cannot decrypt without a key. Antiy CERT found that TeslaCrypt 4.0 emerges in March 2016 and use RSA – 4096 encryption algorithm.
The emergence of ransomware is associated with many factors, and one important factor is the high maturity of anonymous Internet and anonymous payment. After the Spring Festival of 2016, ransomware Locky started to outbreak and many global security vendors have released corresponding reports. Antiy CERT also released “the first Bitcoin ransomware ‘Locky’ with Chinese prompts” [3]. At the end of March 2016, G-data and Trend Micro released the report of Petya ransomware that modifies MBR and encrypts entire hard disk; In early April 2016, Antiy CERT began to track ransomware TeslaCrypt 4.0.
2 Transmitting ways
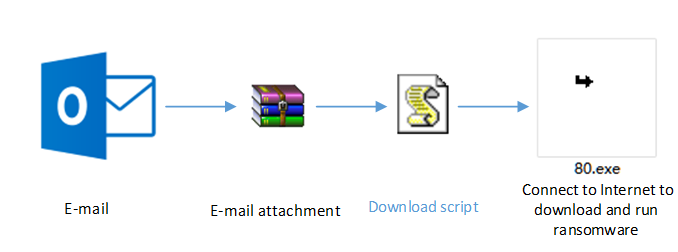
Ransomware TeslaCrypt uses website drive-by download and E-mail to transmit. Drive-by download is rarely used in domestic, but browser vulnerabilities (Chrome, Firefox, Internet Explorer), Flash vulnerabilities and Adobe Reader vulnerabilities are common ways to transmit; And E-mail is often used to transmit ransomware and multiple ransomware events found by Antiy CERT are also transmitted by E-mail.
Figure 1 Ransomware transmitted by E-mail
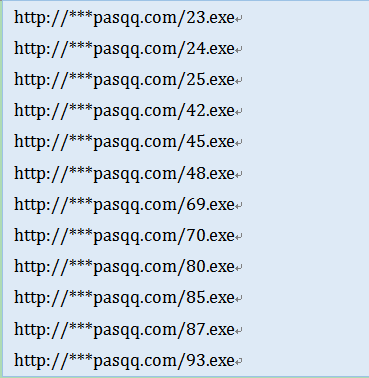
When analyzing TeslaCrypt download addresses, Antiy CERT researchers found that multiple TeslaCrypt 4.0 programs are stored in the same domain name, and file HASH is not identical. For example, domain name http://***pasqq.com can download the TeslaCrypt 4.0 address, as follows:
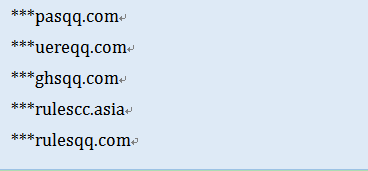
In addition, the ransomware addresses in other domain names are the same as above, such as: 23.exe, 24.exe, 25.exe … 93.exe. To April 7, 2016, 14, Antiy CERT found more than 50 domain names with ransomware TeslaCrypt 4.0, part of which have expired.
Part of domain names that can download ransomware TeslaCrypt 4.0:
3. Sample analysis
Antiy CERT had found nearly 300 ransomware TeslaCrypt 4.0 in total. The researchers analyzed some newly found samples.
3.1 Sample label
| Virus name | Trojan[Ransom]/Win32.Teslacrypt |
|---|---|
| Original file name | 80.exe |
| MD5 | 30CB7DB1371C01F930309CDB30FF429B |
| Processor framework | X86-32 |
| File size | 396 KB (405,504 byte) |
| File format | BinExecute/Microsoft.EXE[:X86] |
| Timestamp | 5704939E -->2016-04-06 12:42:06 |
| Digital signature | NO |
| Shell | NO |
| Compiled language | Microsoft Visual C++ |
| VT first upload time | 2016-04-06 04:07:00 UTC |
| VT detect result | 28/57 |
3.2 Use RSA4096 encryption algorithm to encrypt files, but do not modify original file name
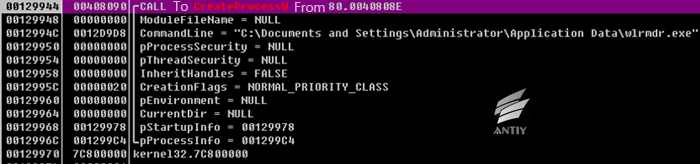
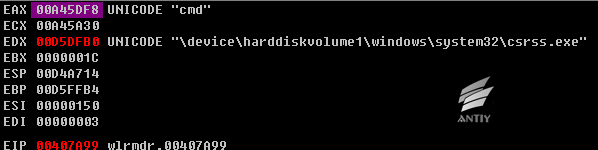
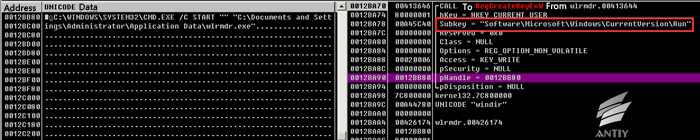
After being executed, it will copy itself to % Application Data % folder, renamed as wlrmdr.exe, set itself property as hiding, and then use CreateProcessW to create process.
Figure 2 Create wlrmdr.exe process
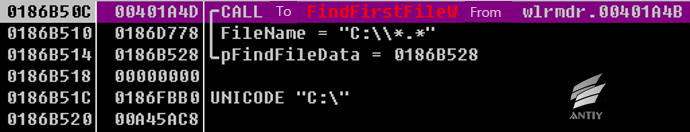
The samples use CreateThreadt to start thread and encrypt all files in disk in the newly created process. First, samples use GetLogicalDriveStringsW to obtain all logical drives and use FindFirstFileW and FindNextFileW to traverse all files and encrypt.
Figure 3 Traverse files in disk
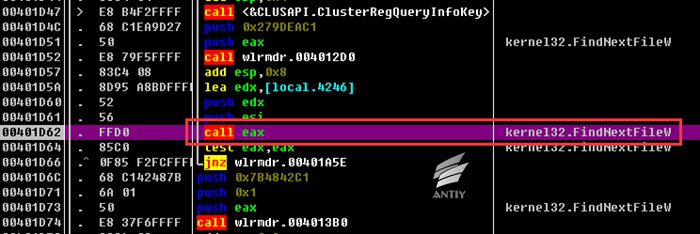
The encrypted function address is 0x0040190A.
Figure 4 Encrypt the traversed files by calling encrypted function
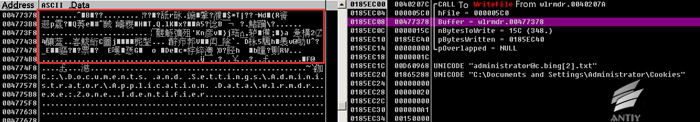
After encrypting with RSA4096 algorithm, it calls WriteFile to write the encrypted data to the file without modifying file name.
Figure 5 Write the encrypted data into file
The comparison of encrypted files:
Figure 6 The comparison of encrypted files
3.3 Confrontation security tools
The sample would check whether the system contains process with strings and hide the process so that the users cannot find these tools:
| “taskmg” | Task manager |
|---|---|
| “regedi” | Registry manager |
| “procex” | Process analysis tool |
| “msconfi” | System configuration |
| “cmd” | Command Prompt |
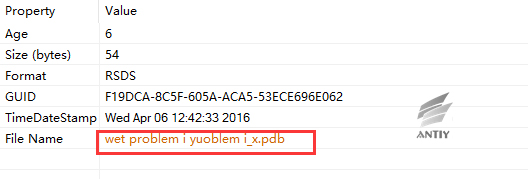
3.4 With PDB information
The sample has PDB information with the file name “wet problem i yuoblem i_x.pdb”.
Figure 8 The debugging information of sample contains PDB information
The sample calls RegCreateKeyExW, using CMD to start its own code to be written into the registry. Therefore, it can be started with the powerboot.
The sample uses many unconventional function calls and skips to prevent security staff to analyze the virus.
Figure 10 Unconventional function call
Figure 11 Unconventional skip
3.7 The encrypted file format of TeslaCrypt 4.0
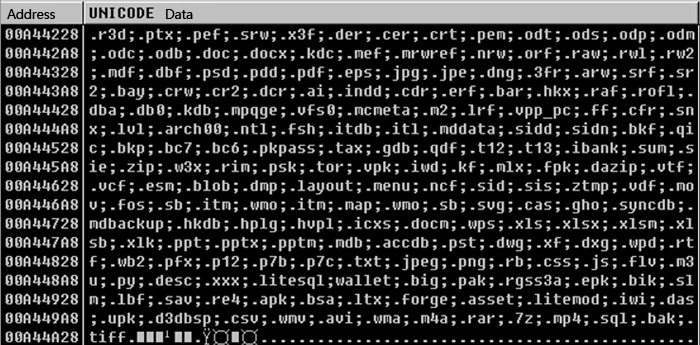 Figure 12 3.7 The encrypted file format of TeslaCrypt 4.0
Figure 12 3.7 The encrypted file format of TeslaCrypt 4.0
4 Summary
The ransomware poses great threats to both individual users and enterprises. The encrypted files cannot be restored, which will bring great loses for users. If you want to solve the threat problems of ransomware, you should install security products, protection and backup products. In addition, users should pay more attention to the mails that they have received, open the email attachments or click the links carefully, especially the emails from strangers.
Antiy Intelligent Endpoint Protection System (IEP) can prevent the ransomware from encrypting files when users clicked to operate the ransomware by mistake.
Antiy Threat Analysis System (PTA) can identify unknown ransomware automatically.
Appendix 1: References
[1] Uncovering the Face of Ransomware
https://www.antiy.net/p/uncovering-the-face-of-ransomware/
[2] http://www.freebuf.com/sectool/66060.html
http://blogs.cisco.com/security/talos/teslacrypt
[3] First Bitcoin ransomware with chinese prompts“locky”
https://www.antiy.net/p/first-bitcoin-ransomware-with-chinese-promptslocky/
Appendix 2: More than 50 domains that spread ransomware found by Antiy CERT
Appendix 3: The C&C address found by Antiy CERT
addagapublicschool.com/binfile.php
kel52.com/wp-content/plugins/ajax-admin/binstr.php
closerdaybyday.info/wp-content/plugins/google-analytics-for-wordpress/vendor/composer/installers/tests/Composer/Installers/Test/binfile.php
coldheartedny.com/wp-content/plugins/wordpress-mobile-pack/libs/htmlpurifier-4.6.0/library/HTMLPurifier/DefinitionCache/Serializer/URI/binfile.php
thejonesact.com/wp-content/themes/sketch/binfile.php
theoneflooring.com/wp-content/themes/sketch/binfile.php
mahmutersan.com.tr/wp-content/plugins/contact-form-maker/images/02/03/stringfile.php
myredhour.com/blog//wp-content/themes/berlinproof/binstr.php
controlfreaknetworks.com/dev/wp-content/uploads/2015/07/binstr.php
sappmtraining.com/wp-includes/theme-compat/wcspng.php
controlfreaknetworks.com/dev/wp-content/uploads/2015/07/wcspng.php
vtechshop.net/wcspng.php
sappmtraining.com/wp-includes/theme-compat/wcspng.php
shirongfeng.cn/images/lurd/wcspng.php
198.1.95.93/~deveconomytravel/cache/binstr.php
helpdesk.keldon.info/plugins/editors/tinymce/jscripts/tiny_mce/plugins/inlinepopups/skins/clearlooks2/img/binfile.php
hotcasinogames.org/binfile.php
goldberg-share.com/wp-content/plugins/contact-form-7/includes/js/jquery-ui/themes/smoothness/images/binfile.php
opravnatramvaji.cz/modules/mod_search/wstr.php
studiosundaytv.com/wp-content/themes/sketch/binfile.php
theoneflooring.com/wp-content/themes/sketch/binfile.php
hotcasinogames.org/binfile.php
pcgfund.com/binfile.php
kknk-shop.dev.onnetdigital.com/stringfile.php
forms.net.in/cgi-bin/stringfile.php
casasembargada.com/wp-content/plugins/formcraft/php/swift/lib/classes/Swift/Mime/HeaderEncoder/stringfile.php
csskol.org/wp-content/plugins/js_composer/assets/lib/font-awesome/src/assets/font-awesome/fonts/stringfile.php
grosirkecantikan.com/wp-content/plugins/contact-form-7/includes/js/jquery-ui/themes/smoothness/images/binarystings.php
naturstein-schubert.de/modules/mod_cmscore/stringfile.php
vtc360.com/wp-content/themes/vtc360_maxf3d/ReduxFramework/ReduxCore/inc/extensions/wbc_importer/demo-data/Demo2/binarystings.php
starsoftheworld.org/cgi-bin/binarystings.php
holishit.in/wp-content/plugins/wpclef/assets/src/sass/neat/grid/binarystings.php
minteee.com/images/binstr.phpnewculturemediablog.com/wp-includes/fonts/wstr.php
drcordoba.com/components/bstr.php
Appendix 4: About Antiy
Starting from antivirus engine research and development team, Antiy now has developed into an advanced security product supplier with four research and development centers, nationwide detection and monitoring ability as well as products and services covering multiple countries. With a fifteen-year continual accumulation, Antiy has formed massive security knowledge and promoted advanced products and solutions against APT with integrated application of network detection, host defense, unknown threat identification, data analysis and security visual experiences. With the recognition of technical capacity by industry regulators, customers and partners, Antiy has consecutively awarded qualification of national security emergency support unit four times and one of the six of CNNVD first-level support units. Antiy detection engine for mobile is the first Chinese product that obtained the first AV – TEST (2013) annual awards and more than ten of the world’s famous security vendors choose Antiy as their detection partner.
More information about antivirus engine: https://www.antiy.net