Analysis of Multi-layer Concealed Payload Decryption and Driver-level Blinding Countermeasures | Technical and Tactical Tracking of “Swimming Snake” (Silver Fox)
The original report is in Chinese, and this version is an AI-translated edition.
1.Overview
Antiy CERT recently found that the “Swimming Snake (Silver Fox)” black production gang is tring to avoid anti-virus software detection through multi-stage load decryption and a variety of drive-level confrontation technology. It mainly involves two methods. the first kind of attack method is to complete hierarchical decryption and payload loading through different components, hide core malicious payload through multiple rounds of encryption processing, and at the same time, build 80 alternative C2 addresses for encrypted storage. In that invention, component collaboration and multi-layer concealment mechanism are combined to combat security software; and in the second type of attack method, attack components are released through multiple encrypted compressed package files. Blind EDR, terminate the designated security software process, hide the process and network connection, and execute Winos remote control Trojan in the mode of “white plus black.”
The “Swimming Snake” black production gang and other security enterprises, also known as “Silver Fox” and “Valley Gang,” mainly targeted at domestic users to carry out attacks and fraud activities. In the second half of 2022, Antiy discovered and analyzed the early activities of the snake group, including disguised as a common software download site, poisoning the search engine SEO and mass-sending of phishing emails. In the load execution stage, it is often executed in the “white plus black” mode, and further spread through instant messaging software (such as WeChat and enterprise WeChat). Its main way of profit is to induce users to join groups through instant messaging software to commit fraud, but also to the infected host computer to form the ability to steal secrets, possibly to conduct other activities such as data trafficking. The malicious files it spreads are characterized by a large number of variants, rapid iteration of kill-free technology, and the attack targets involve a large number of individual users and a number of industries, which pose a wide and serious threat.
The “Swimming Snake” gang is likely to operate under the cyber crime model of FaaS (Fraud as a Service), in the form of commodification and sale or rental on demand, Provide other criminals with attack methods, tools, and infrastructure that significantly lower the threshold for committing cyber fraud.
The terminal defense system (IEP) of Antiy has the driver-level main defense module, the detection capability based on AVL SDK and the defense points of kernel and application layer, which can effectively block the remote control Trojan attack chain.
Users can download and use the “Swimming Snake” special screening tool to detect such threats on the Antiy vertical response platform (https://vs2.antiy.cn).
2.Technical review
2.1 Poisoning of SEO Technology in Search Engine
“Swimming Snake (Silver Fox)” black production uses search engine SEO technology to carry on poison attack, make its build imitative download website in the search result the rank of be ahead. Identify phishing website please refer to the released report of Antiy “Swimming Snake (Silver Fox)” Black Production Intensive Phishing of All Kinds of Popular Applications: Anti-fake of WPS Download Site” for phishing website identification and prevention.
Figure 2-1 A malicious website that imitates “YouDao Dict”.
Figure 2-2 A malicious website that imitates “WPS”.
2.2 Sample execution process
After the first type of sample is run, the normal “NetEase translation installation software” is released, and the VBS script is executed covertly. The VBS script queries whether there are 360 * * * .exe, QQ * * * .exe and Hips * * * .exe processes by executing WMI, and selects different attack components according to the results. Although these attack components are different, they all use the same decryption means to decrypt the “_ 8” file to get the NHQDX. jpg file. The file decrypts the data at the specified offset to obtain the Gh0st remote control Trojan variant, and selects the corresponding 80 built-in C2 addresses according to the instal. ini configuration file to decrypt. Consysfun.png is a remote control plug-in that is encrypted and the attacker sends instructions to the remote control Trojan horse to call the specified function in the remote control Trojan horse plug-in “Consys21.dll.”
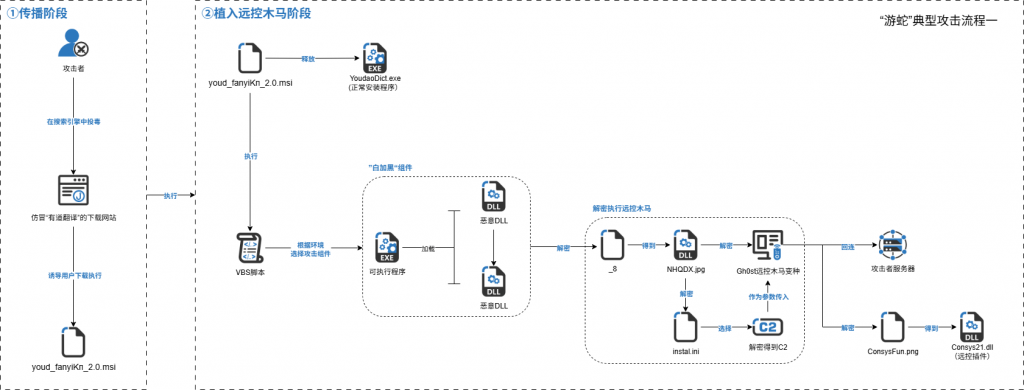
Figure 2-3 Flow chart of first type sample execution
After the second type of sample is run, the WPS installation program and the malicious program which execute normally are released, and the malicious program releases a plurality of attack components in a specified path, Blind EDR, terminate the designated security software process, hide the process and network connection, and execute Winos remote control Trojan in the mode of “white plus black.” Winos is a remote control Trojan with high frequency in the past two years, which is modified by Gh0st remote control and supports the execution of various function modules in the form of plug-in.
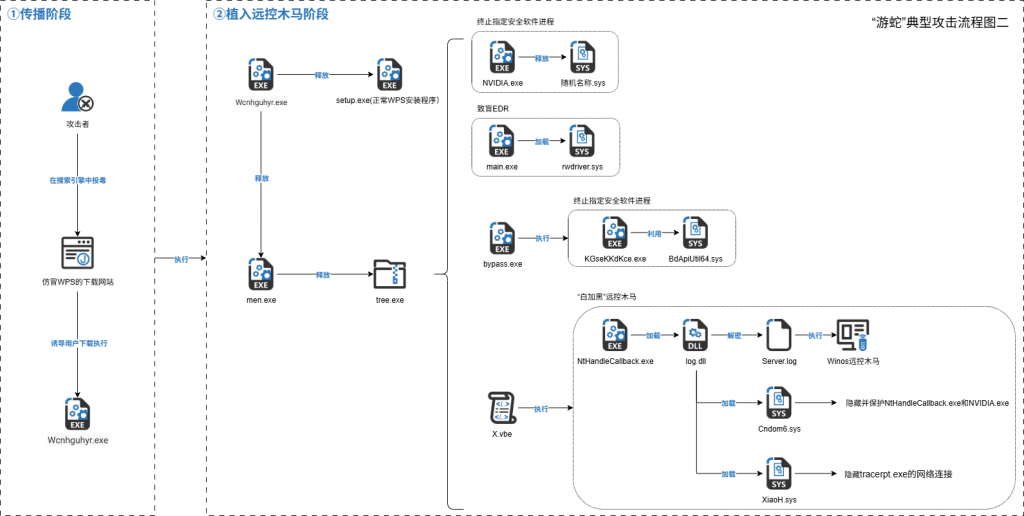
Figure 2-4 Flow Chart of Type II Sample Execution
3.Sample analysis
3.1 Method Analysis of Decrypting Multi-stage Load against Software
3.1.1 Initial decoy document
Table 3-1 Sample Label
| Virus name | Trojan / Win32.SwimSnake |
| Original file name | Oud _ fanyiKpi _ 2.0. msi |
| Md5 | 42ddb89706155089a04b9eba5e661516 |
| Processor architecture | Intel 386 or later processors and compatible processors |
| File size | 221 MB (232,657,920 bytes) |
| File format | Windows Installer |
| Time stamp | Forgery |
| Digital signature | None |
| Shell type | None |
| Installation Procedure | Microsoft Windows Installer |
After youd _ fanyiKpi _ 2.0. msi runs, it will release the normal NetEase channel translation installation software to the path selected by the user for installation (default is “% appdata%\ Netyoydd”), and create a shortcut on the desktop. In C:\ ProgramData, a set of white and black component file are released for subsequent selection of attack payload therefrom.
The core components and functions involved in this sample are described in the following table:
Table 3-2 Description of Documents and Functions
| Document name | Functions |
| Binary. _ BF84D321CFCEFEA02F92AC3F19AB7EFD | The MSI installer obscures the VBS scripts that are executed |
| Xfyeck61gv.exe (white file) | “White plus black” component, stardict-editor.dll decrypts the _ 8 file, and dll1.dll loads the decrypted payload. |
| Stardict-editor.dll | |
| Dll 1.dll | |
| _ 8 | Encrypted file: Encrypted first layer payload, decrypted is a DLL file named NHQDX. jpg, which contains encrypted remote Trojan payload and 80 encrypted C2 addresses. Remote control Trojan is a DLL file named NH. dat. |
| Instal.ini | Encrypted file: This file contains the encrypted id value, and NHQDX. jpg selects the corresponding C2 address according to the value. |
| Consys21.png | Encrypted file: The encrypted remote control plug-in, after decryption, is a DLL file named Consys21.dll. The attacker sends an instruction to the remote control Trojan horse by calling the function specified in the plug-in. |
3.1.2 Hidden execution of VBS script
In that installation process, the malicious MSI installation program covertly executes the VBS script, create specially named folders masquerading as system-related (including random character identification), And the released designated files will be copied to the system program directory, public document directory and other locations to complete the file landing and hiding deployment.
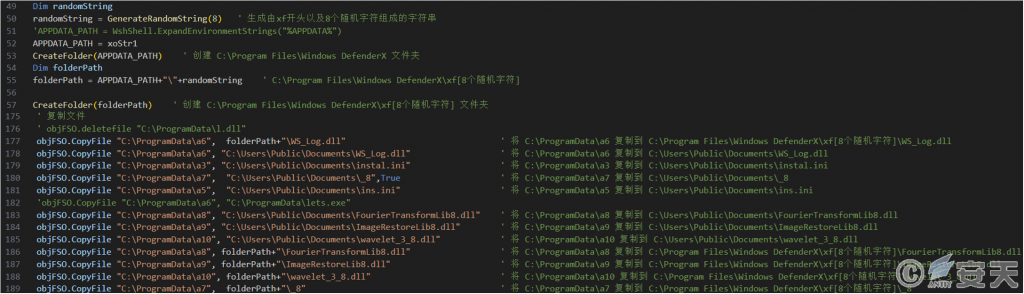
Figure 3-1 Create a Folder and Carry out a File Copy Operation
Inquire whether the target device has 360 security guard process (360 * * * .exe), QQ computer housekeeping process (QQ * * * .exe), and teflon security software process (Hips * * * .exe) through WMI; Execute different component files based on the above query results, and delete other subsequent useless files. Although these attack components differ, the core process for decrypting and executing remote control Trojans is the same.
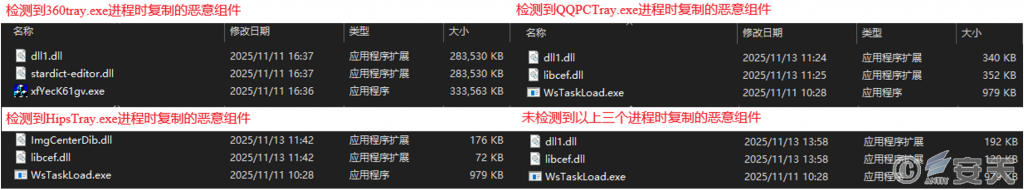
Figure 3-2 4 types of malicious components involved in the sample
The first layer of payload is decrypted
The malicious DLL files in the four groups of malicious components adopt the same decryption logic (only the code implementation details are slightly different, and the first group is taken as an example below): The first DLL file reads the specified file first, and the “+” character is removed. Then perform subtraction and exclusive-OR operation on the content with 0x7E as the key, and then call the second DLL and transfer the decrypted data to the second DLL, which will perform PE parsing on the received content and find the export function corresponding to the file formerly named NHQDX. jpg. The load is finally completed.
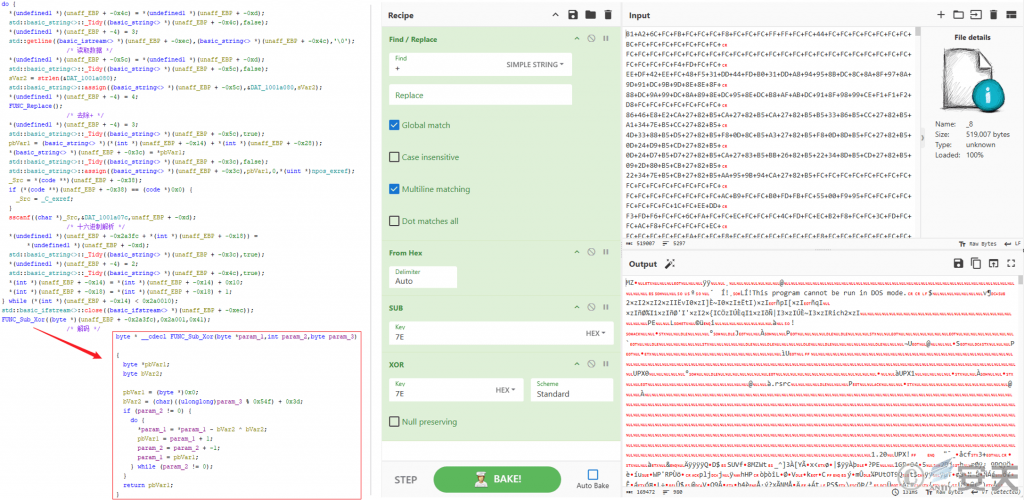
Figure 3-3 Decrypting the _ 8 File by a stardict-editor.dll
Decipher remote control Trojan horse
Nhqdx. jpg copies the encrypted remote control plug-in to a specified location, and then the creating thread decrypts its own data by using the data at its own 0x282D0 offset as a key to decrypt its own content with a length of 0x10200 at its 0x180D0 offset, Finally, the remote control Trojan load is obtained and loaded.
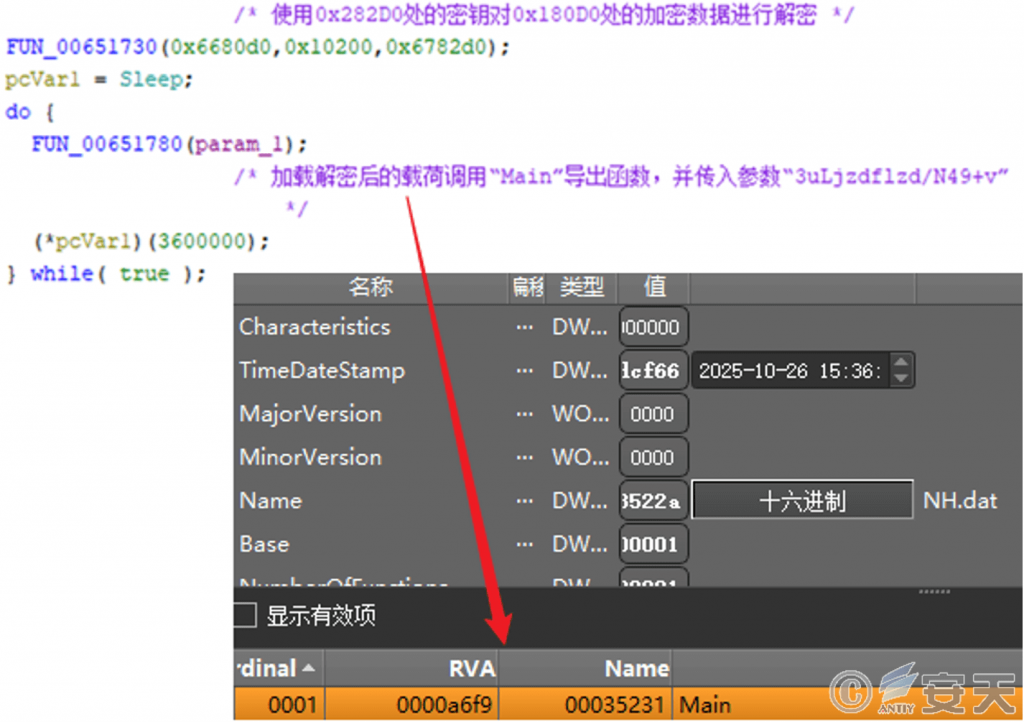
Figure 3-4 Load the remote Trojan payload obtained by decryption and passes in the specified parameters
There are 80 encrypted C2 server address strings in the NHQDX. jpg file, which gets the value of its id by reading the instal. ini file, The id value (80 for this sample) is decoded and the corresponding C2 address therein is selected based on the value. The remote control Trojan receives the encrypted C2 address string when it is loaded, uses Base64 decoding to perform subtraction and exclusive OR operations, and restores the C2 address. The list of C2 addresses contained in NHQDX. jpg is shown below.
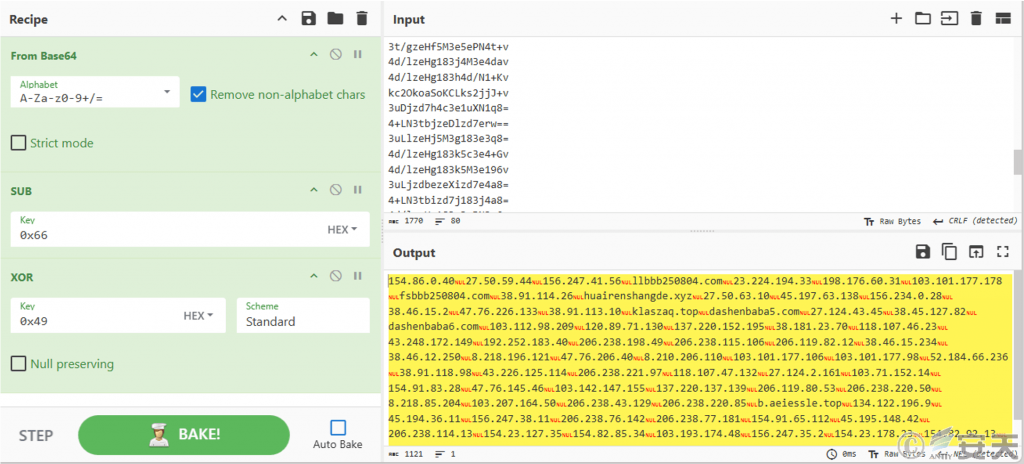
Figure 3-5 C2 Address List Obtained by Restoring
3.1.3 Remote control Trojan decryption and execution
The Method of Communication Encryption
The remote control Trojan NH.dat collects information such as system version, host name, running time and date, and running status of specific process according to a user-defined structure; first, the information is compressed by Zlib. Then the key “qQ996545” is encrypted by RC4 algorithm, and the total size of the packet and the original size of the original data are added before the processed packet.
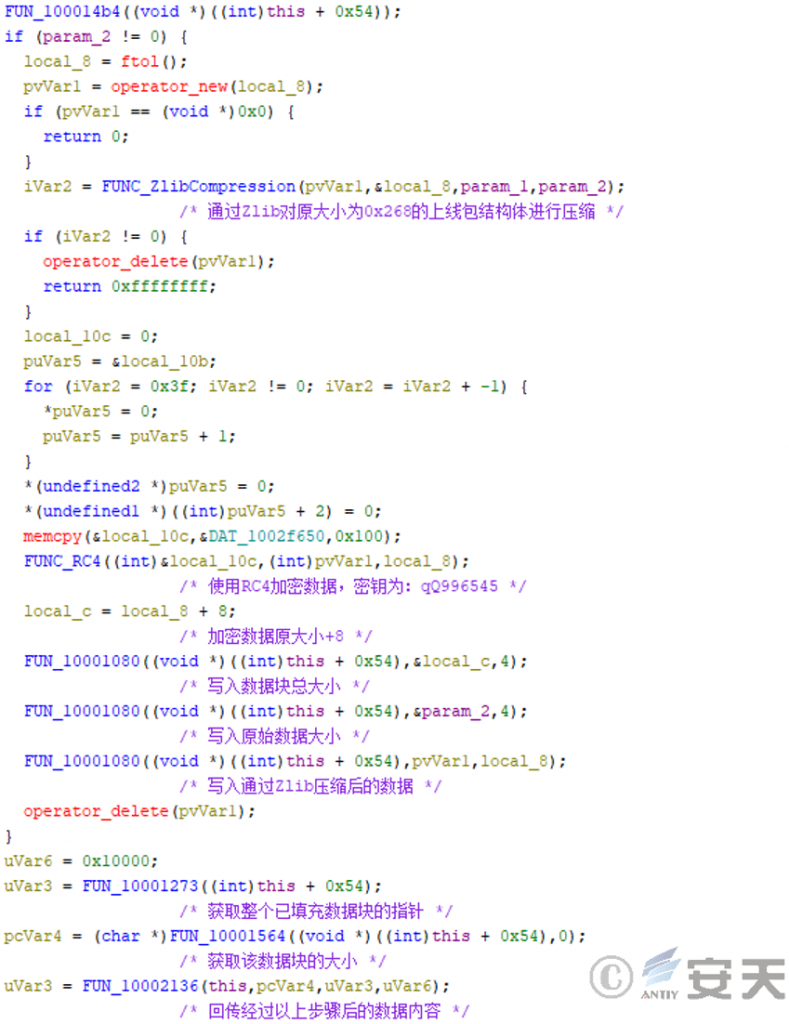
Figure 3-6 Encryption Method for Communication Content by Remote Trojan
And the remote Trojan adds fixed 0x66 and 0x9c in the header when constructing the online package.

Figure 3-7 Decrypting the online package
Decrypt to get the remote control plug-in
The remote control Trojan file contains a DLL file whose file header is modified, and after the file header is restored, the DLL file decrypts “ConsysFun. png” to obtain the remote control Trojan plug-in originally called “Consys21.dll.”
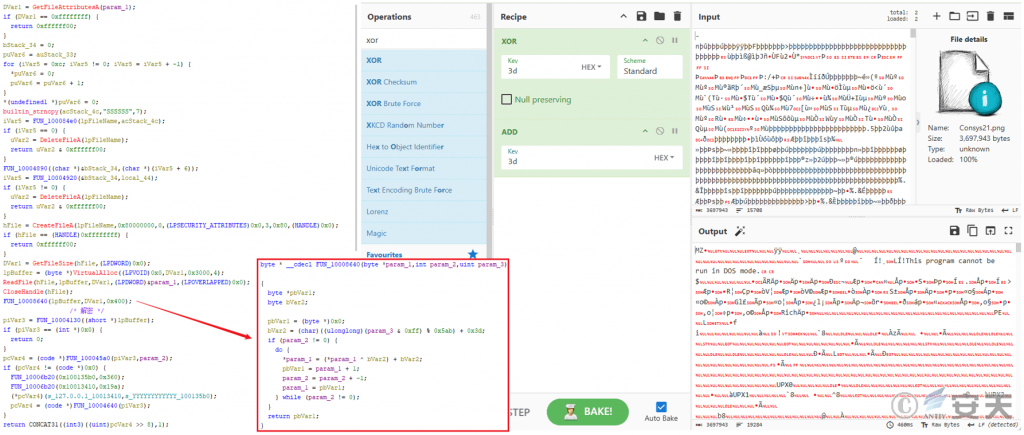
Figure 3-8 Decrypting the ConsysFun .png file
The attacker sends instructions to the remote control Trojan horse, and calls the export function specified in the remote control Trojan horse plug-in “Consys21.dll.” Instructions and the corresponding functions called are shown in the following table.
Table 3-3 Instructions and Corresponding Functions and Functions
| Instructions | Call the Consys21.dll function | Functions |
| 0, 0x20 | Dllstartrun | Execute the plug-in |
| 1 | Dllfile | Obtain the disk information and remaining space in the system |
| 2 | Dllscreen | Capture screen |
| 3 | Dllvideo | Camera video viewing |
| 4 | Dllkeybo | Keylogger |
| 5 | Dllaudio | Voice monitoring |
| 6 | Dllsyste | Gets information about the processes running in the system and their modules |
| 7 | Dllshell | Remote execution of cmd commands |
| 0x13 | Dllmsgbox | Pops up a message box with the header and information specified by the attacker |
| 0x15 | Dllserst | Get the server information |
| 0x16 | Dllserma | Get the service information in the system |
| 0x17 | Dllreg | Registration Form |
| 0x18 | Dllddosopen | Perform DDoS |
| 0x19 | Dllddosstop | Stop DDoS |
| 0x1f | Dllproxyopen | Opening agent |
| 0x23 | Dllscreenhi | Screen monitoring of different function types |
| 0x24 | Dllscreenhivr | |
| 0x25 | Dllscreenhis |
3.2 Use of multiple groups of driver files to combat security software manipulation analysis
3.2.1 Initial Bait Document
Table 3-4 Label of Initial Bait Document Sample
| Virus name | Trojan / Win32.SwimSnake |
| Original file name | Wcnhguhyr.exe |
| Md5 | 05946b9848551eb738c9fdf748af0ff2 |
| Processor architecture | Intel 386 or later processors and compatible processors |
| File size | 106 MB (111,626,778 bytes) |
| File format | Binexecute / Microsoft.EXE [: X86] |
| Time stamp | Forgery |
| Digital signature | None |
| Shell type | None |
| Installation Procedure | Inno Setup Module (5.5.0) |
The sample is packaged with InnoSetup, disguised as a WPS installer, and runs to release multiple files from the sample to C:\ ProgramData\ Windows Data.
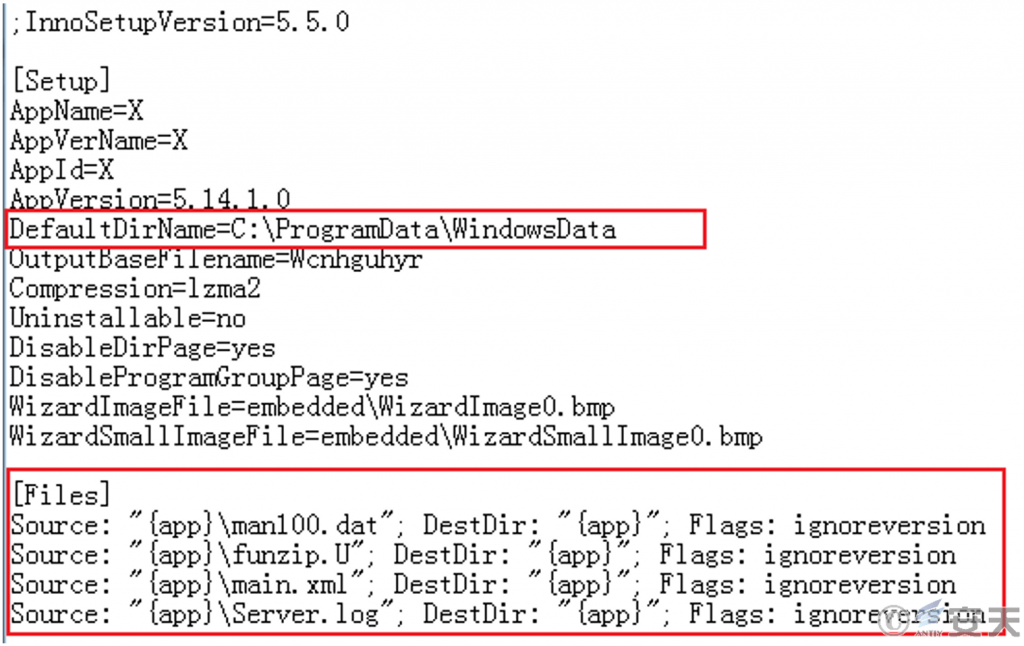
Figure 3-9 Packing information
The funzip.U file contains the 7za decompression tool encoded by Base64, which decompresses the main.xml file with the password “htLcenyRFYwXsHFnUnqK,” and obtains the programs “men.exe” and “setup.exe.” the former is a malicious program. The latter is a normal WPS installer.
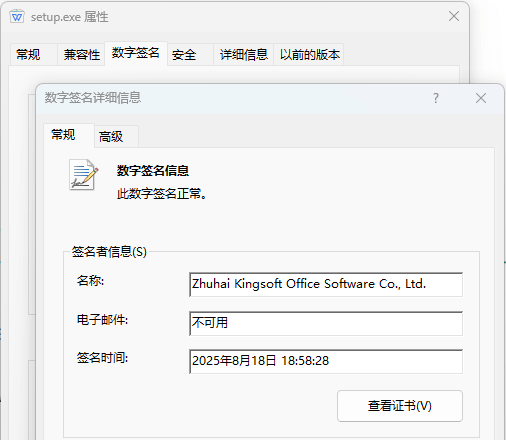
Figure 3-10 setup.exe is a normal WPS installer
3.2.2 Release the execution attack component
Men. exe executes the command to find and enable the network adapter on the computer that is currently disabled to confirm network connectivity.
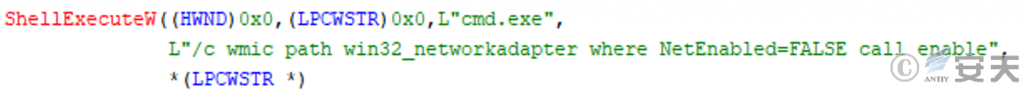
Figure 3-11 Enable the network adapter in the disabled state
Subsequently, the men.exe program releases and decompresses more core malicious components in C:\ Users\ Public\ Documents\ Windows Data, including anti-component and remote control Trojan component of “white plus black.”
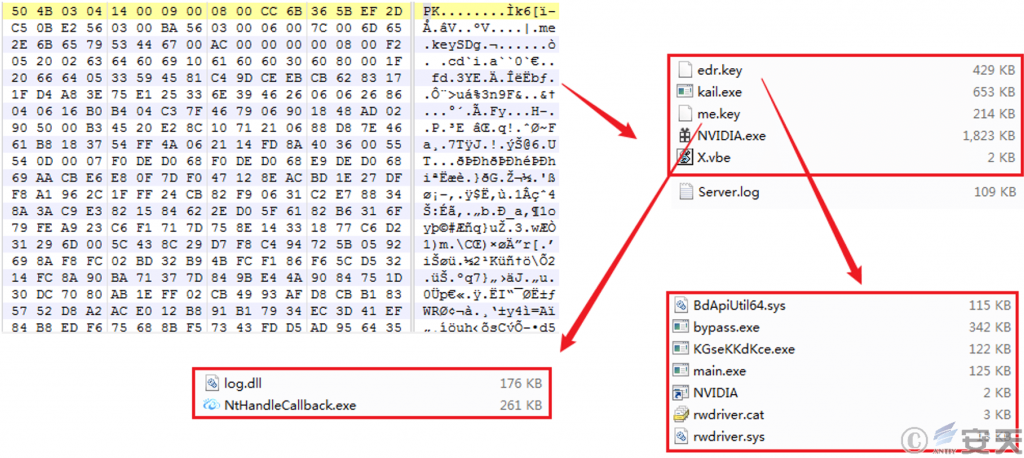
Figure 3-12 Release of multiple attack components
All core components and functions involved in this sample are described in the following table:
Table 3-5 Description of Documents and Functions
| Document name | Functions |
| Main.exe | Blinding EDR: Use an open source project to clear multiple kernel callbacks to avoid monitoring and detection of specified security products. |
| Rwdriver. sys | |
| Nvidia.exe | Terminate the process related to designated security software: Use the driver file of a company’s software to terminate the process related to designated security products, such as 360, Velvet, and Tencent Computer Butler. |
| [Name randomly] .sys (white file) | |
| Kgsekdkce.exe | Terminate the processes related to the designated security software: Use a driver file (BdApiUtil64.sys) to terminate the designated process, and the target involves the processes related to the security products such as 360, Velvet, and Tencent Computer Butler. |
| Bdapiutil64.sys (white file) | |
| Bypass.exe | Tools to bypass the UAC. |
| Nthandlecallback.exe (white file) | “White plus black” attack component, log. dll is malicious DLL, Server. log is the online module of Winos remote control Trojan encrypted by RC4. |
| Log.dll | |
| Server. log | |
| Cndom6.sys | Process Hiding: Hook the relevant API, and return a custom function to achieve process hiding, prevent other processes from obtaining or copying the target process handle. |
| Xiaoh.sys | Process Hiding: To hide the network connection of the target process by performing nsiproxy.sys hook. |
3.2.3 Functional Analysis of Core Components
Blind EDR (unable to monitor and respond properly)
Main.exe and rwdriver. sys adopt the open source project to clear a variety of kernel callbacks to shield the monitoring of process creation, thread creation, module loading, handle, registry, file reading and writing by designated security products. In order to circumvent that detection.
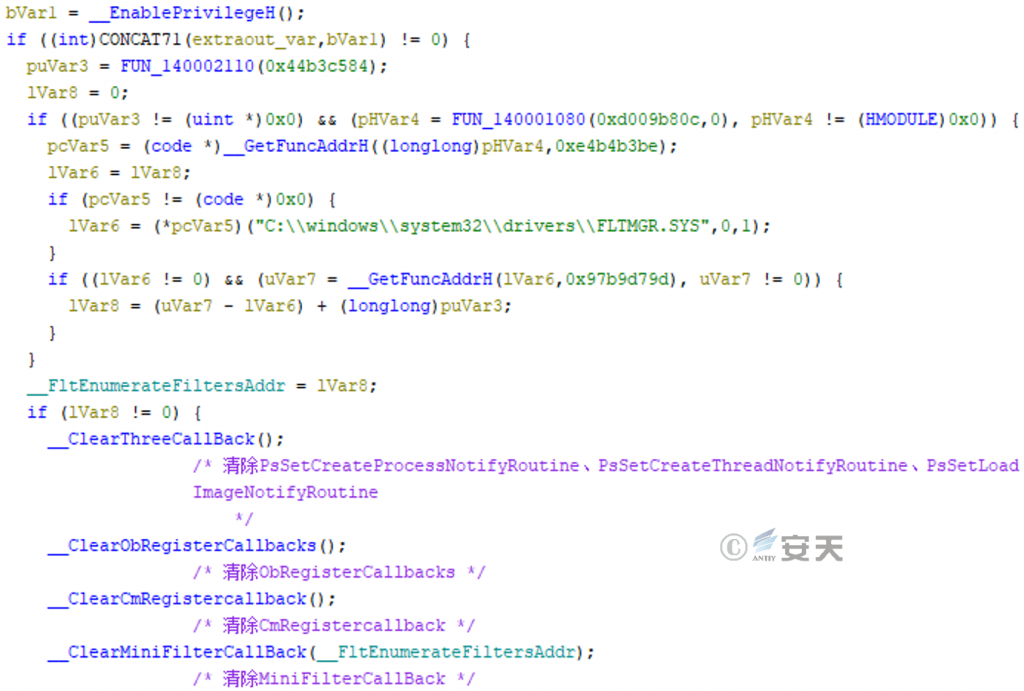
Figure 3-13 Blinding EDR
In that program, the name of the target drive file is Hash-processed to avoid the identification and killing of anti-virus software, Driver files related to security products such as Windows Defender, Kaspersky (Enterprise Edition), Velvet, Trend Micro, Qihoo 360, Tencent, and Qi-Anxin.
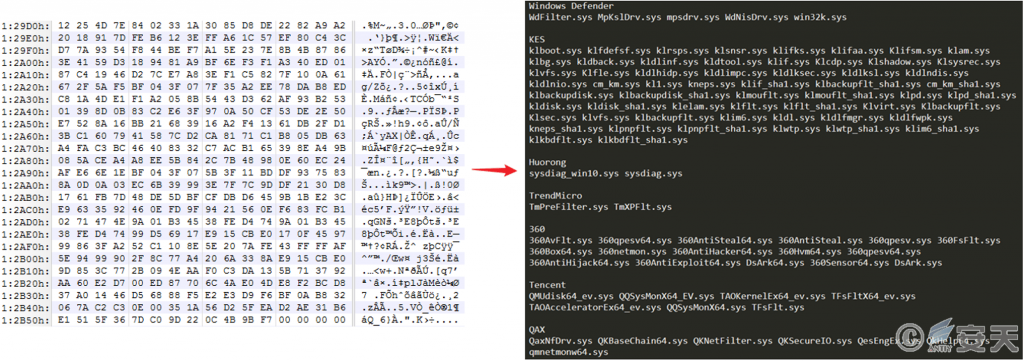
Figure 3-14 Target Drive File
Stop the specified security software process
The following two groups of components use BYOVD, an attack technique that bypasses system security by using legitimate but vulnerable driver files, aiming to exploit the kernel permissions of the driver files for malicious operations.
Component 1:
After NVIDIA .exe execution, a randomly named drive file, which belongs to a company software product and has a normal digital signature for that company, is released in the path% temp%.

Figure 3-15 Drive File Information for Malicious Use
The attacker takes advantage of the vulnerability of the driver file to hijack and sends control code to it to terminate relevant processes of designated security software. the target involves relevant processes of security products such as Qihoo 360, Velvet, and Tencent Computer Butler.
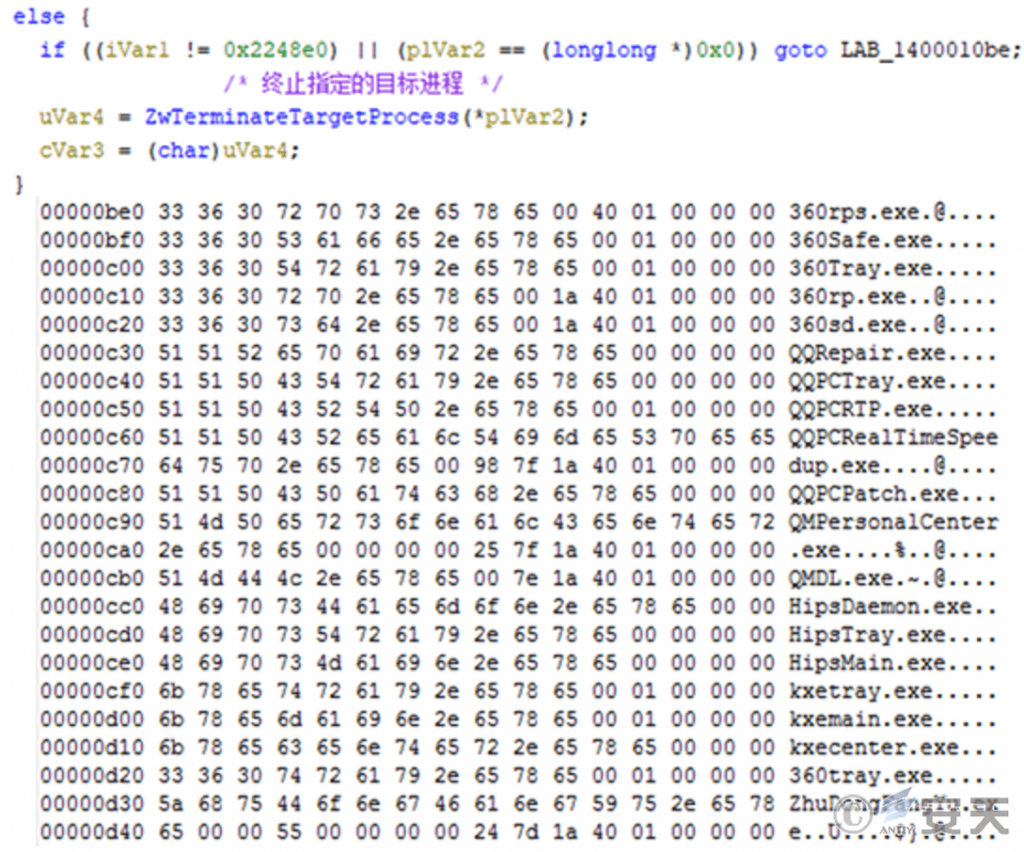
Figure 3-16 Hijack Driver File Termination Specified Target Process
Component 2:
Bdapiutil64.sys is a driver file with the company’s normal digital signature.
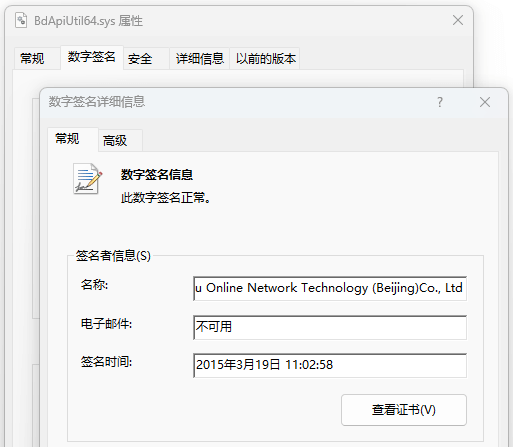
Figure 3-17 BdApiUtil64.sys File Information
Kgsekdkce.exe creates BdApiUtil64.sys as a service, and traverses the process to find out whether there is a designated security software process, and the target involves processes related to security products such as Qihoo 360, Velvet, and Tencent Computer Butler.
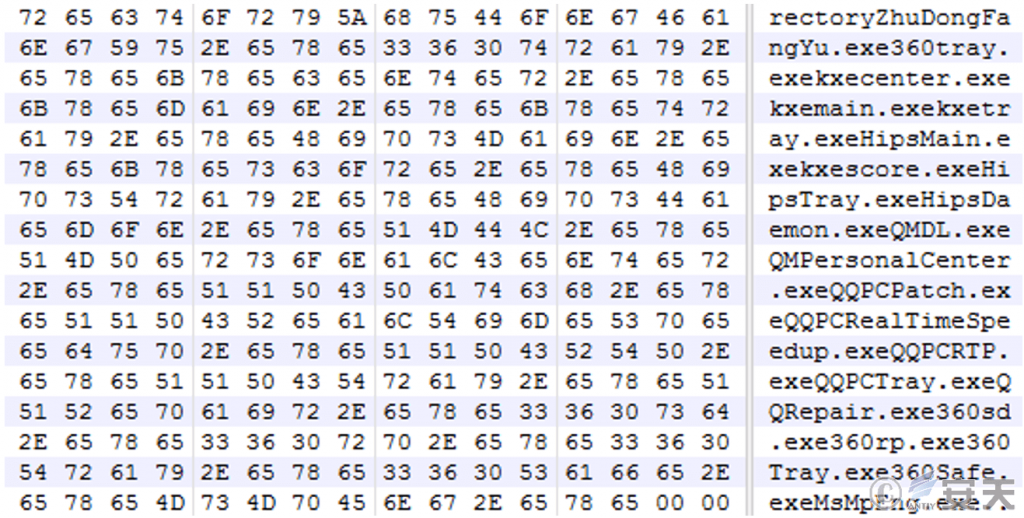
Figure 3-18 Target Process
Hijacking the drive file BdApiUtil64. sys sends it a control code 0x800024b4 to terminate the specified process as shown in the figure above.
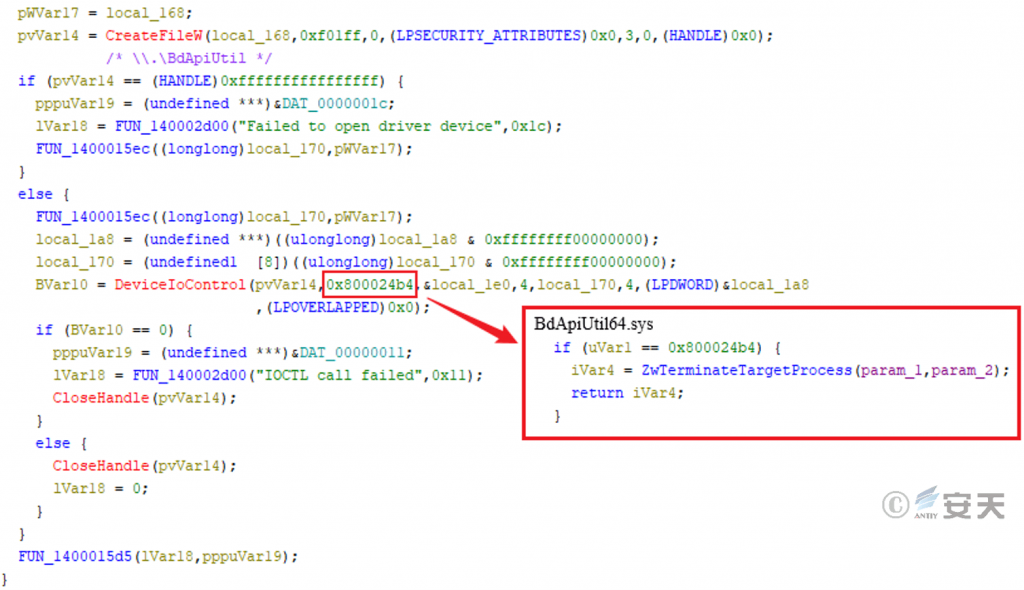
Figure 3-19 Hijacking BdApiUtil64. sys Terminating the Specified Target Process
Stop the security software process by bypassing the UAC
Bypass. exe is a shortcut to C:\ Users\ Public\ Documents\ Windows Data\ NVIDIA .lnk by bypassing the UAC tool and calling the COM interface to create a right-lifting object.
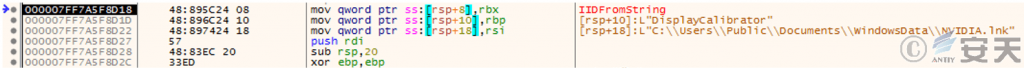
Figure 3-20 Executing NVIDIA .lnk Shortcut
This shortcut is used to execute C:\ Users\ Public\ Documents\ Windows Data\ KGseKdKce.exe, which hijacks the BdApiUtil64.sys driver file to terminate the specified security software process.
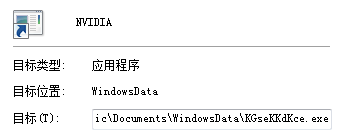
Figure 3-21 NVIDIA .lnk for executing KGseKdKce.exe
“White plus black” remote control Trojan component
Using NtHandleCallback.exe, which has a normal digital signature, loads the malicious file log.dll, which executes 3 threads, and its overall function is as follows.
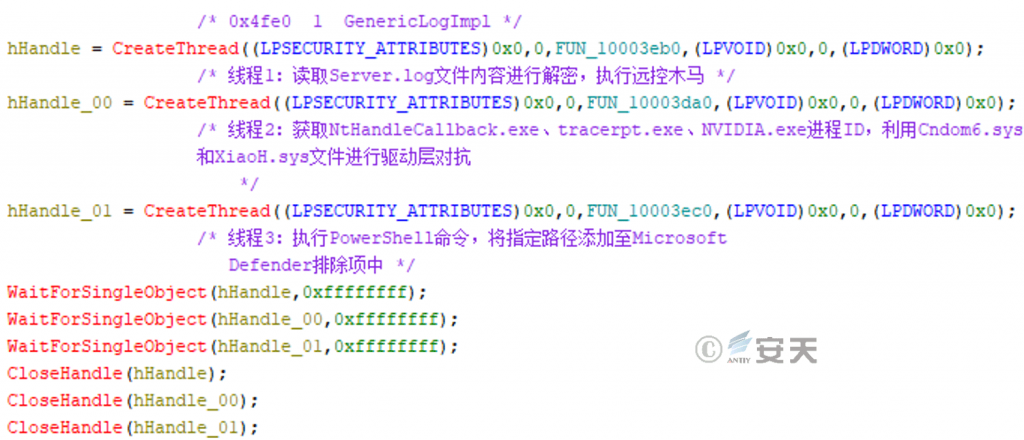
Figure 3-22 Overall Function of Malicious File Log.dll
Thread 1 of log.dll decrypts the Server. log file by RC4 using the decryption key “? Bid @ locale @ std,” obtains the online module of the Winos remote control Trojan and executes the module.
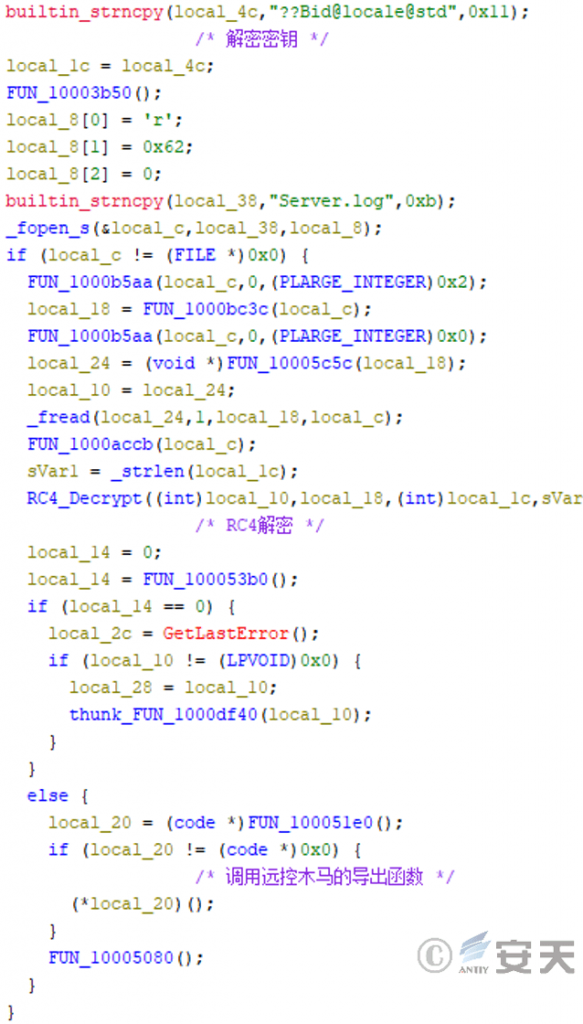
Figure 3-23 Decrypting and executing remote control Trojan horse
The online module of the Winos remote control Trojan horse contains the configuration information with inverted string, including the C2 address and port, grouping, version number, whether to enable some function, etc.

Figure 3-24 Configuration Information Used by the Sample
The online module will then inject the received login module into the tracerpt.exe system process.
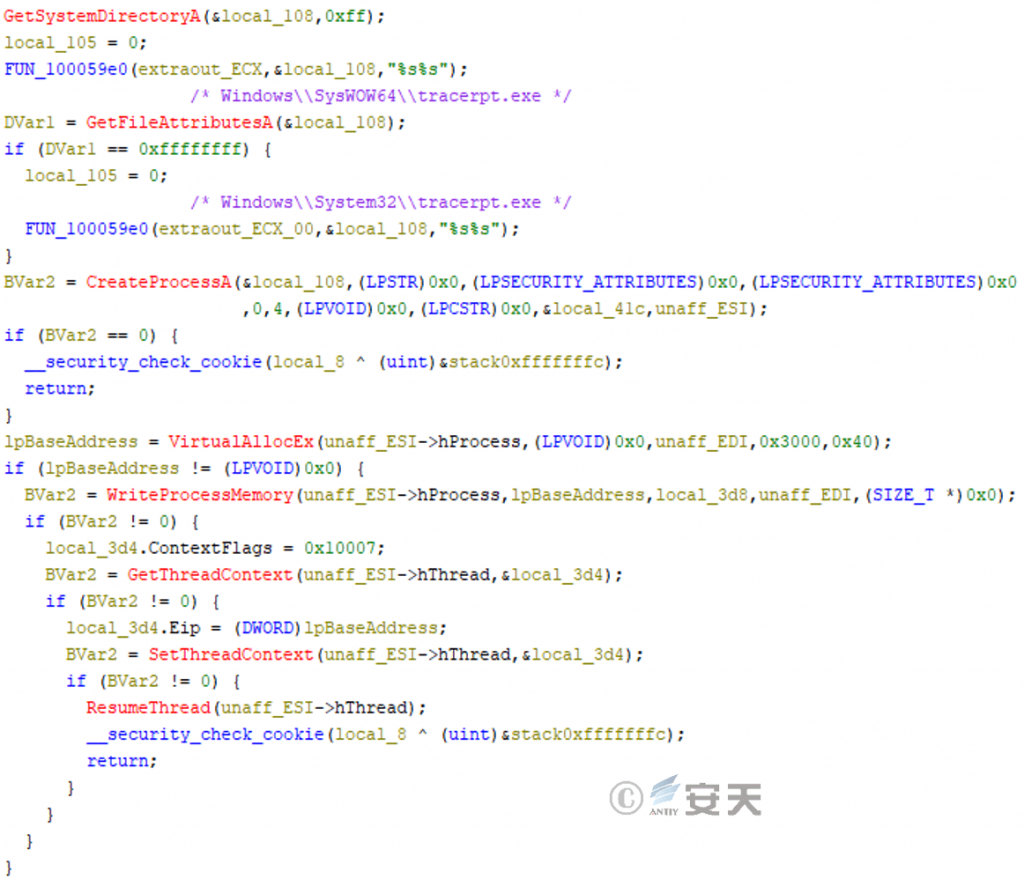
Figure 3-25 Injecting the tracerpt.exe process
Use the driver file to hide the process
Thread 2 of log.dll hides and protects the target process and the network connection of the target process by using two driver files, Cndom6. sys and XiaoH. sys.
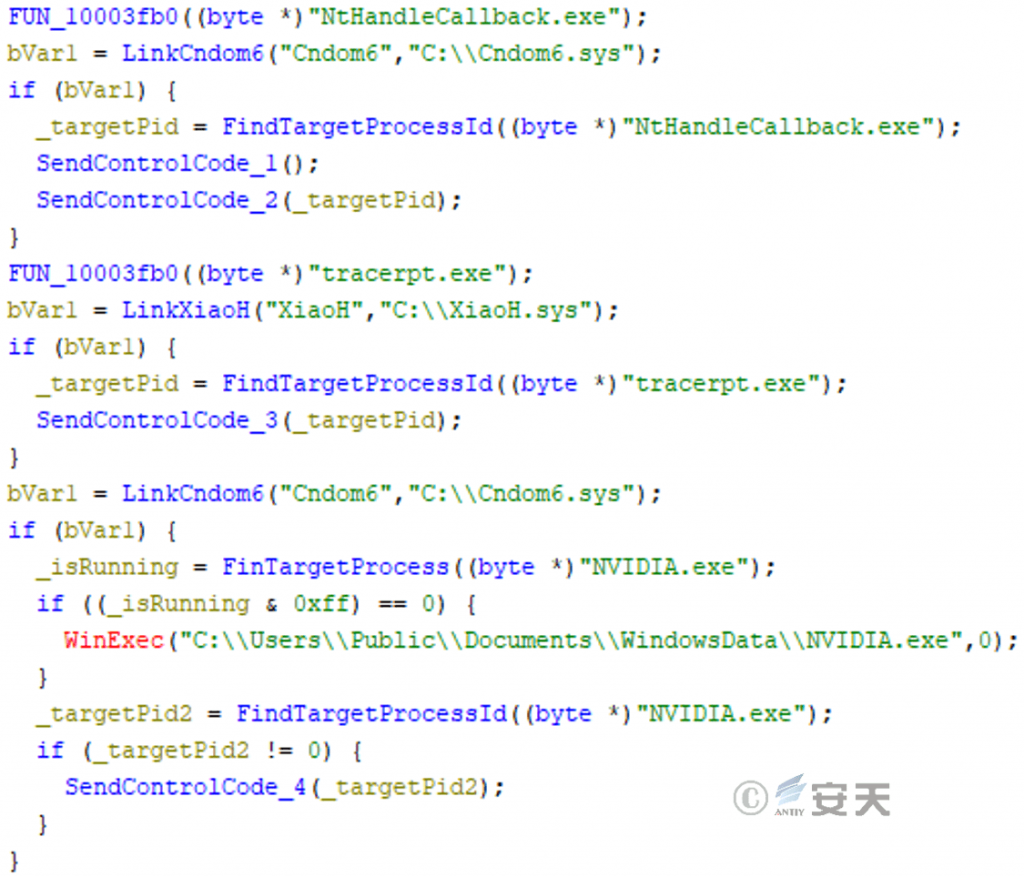
Figure 3-26 Main functions of the log.dll thread 2
Hide and protect that target proc
Cndom6.sys is a malicious driver file that contains an expired digital signature for a company. The attacker signs the drive file using an unrevoked certificate issued before July 29, 2015, so that the drive file will function properly with signature verification.
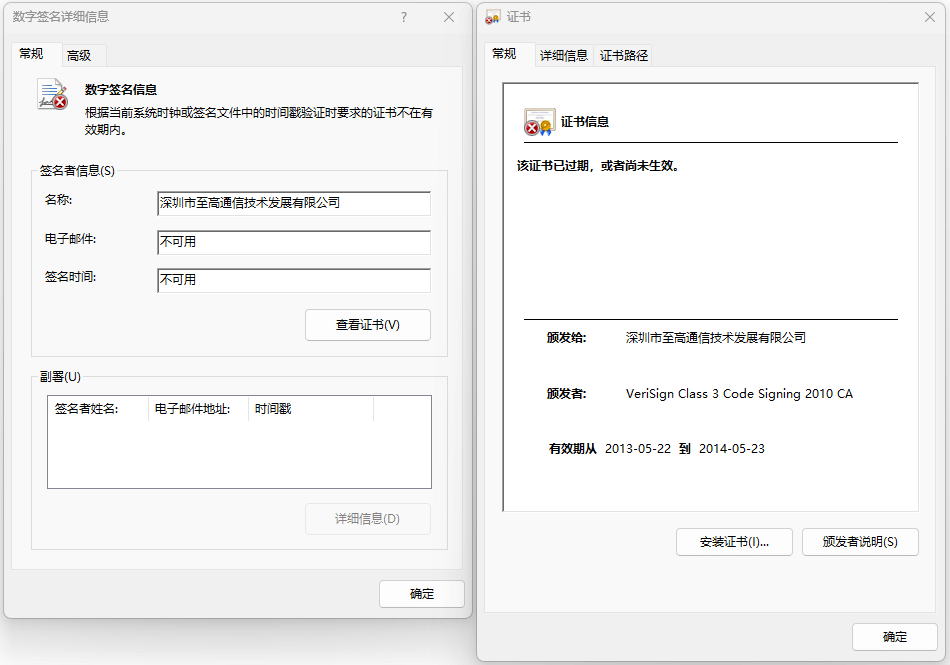
Figure 3-27 Expired Digital Signatures Used by Canndom6.sys
After log .dll loads Cndom6.sys, the driver file will perform Hook on the relevant API and return a custom function to hide the process and prevent other processes from obtaining or copying the target process handle. In order to prevent that target process from bee discovered or operated.
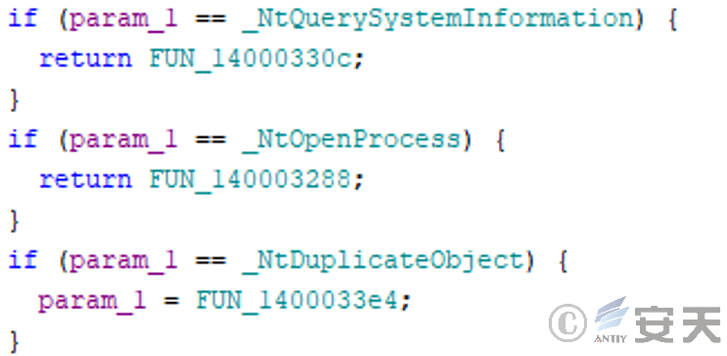
Figure 3-28 Hooks mainly for three APIs
Hook is perform on NtQuerySystemInformation (Windows system kernel API function, which is use to query system information), and if matching to that target process ID, the chain is broken to hide the process.
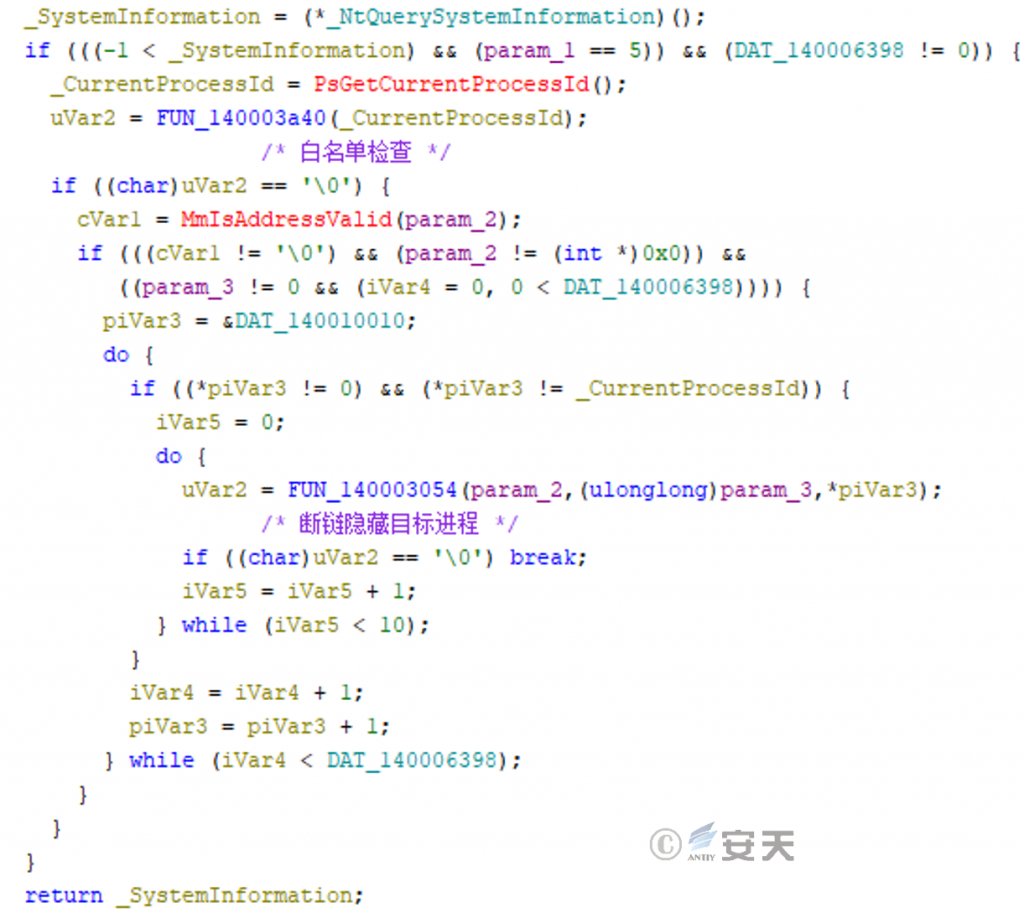
Figure 3-29 Hidden Target Processes
Hook that NtOpenProcess (Window system kernel API function, used to open the handle of the process object and set the access right), and if match the target process ID, return 0xc0000022 to prevent other processes from obtaining the target process handle.
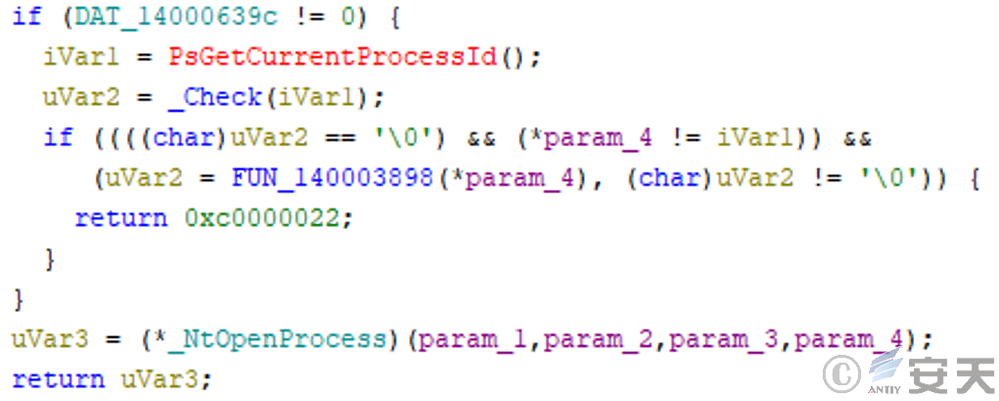
Figure 3-30 Block other processes from obtaining a target process handle
Hook that NtDuplicateObject (Window system kernel API function for copy object handle) and returns 0xc0000022 to prevent other process from copying the target process handle if it matches the target process ID.
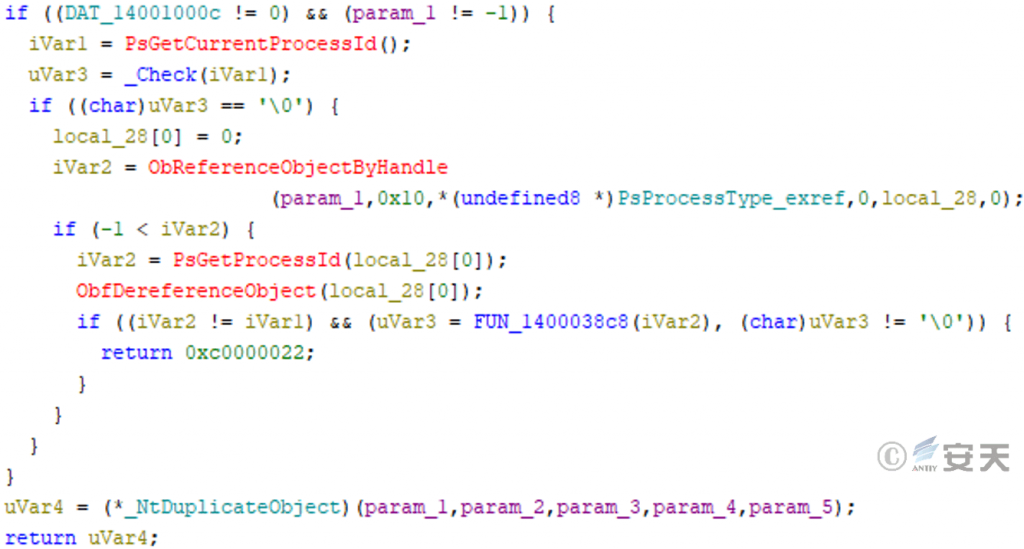
Figure 3-31 Preventing other processes from copying the target process handle
Hide the network connection of the target process
Xiaoh. sys is a malicious driver file that contains an expired digital signature of a company. The attacker also signs the drive file with an unrevoked certificate issued before July 29, 2015, so that the drive file can run properly through signature verification.
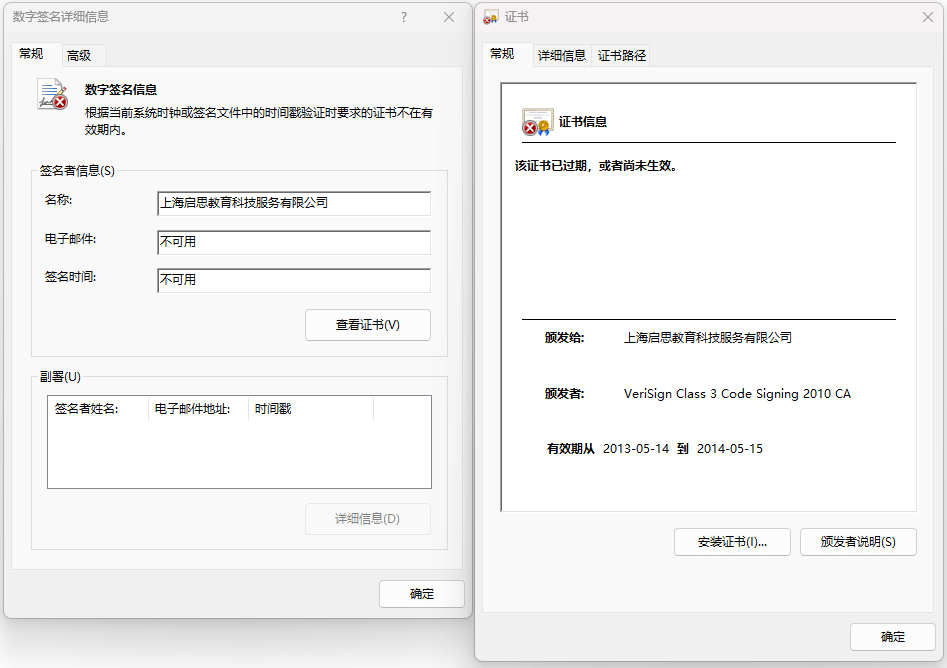
Figure 3-32 Expired Digital Signatures Used by XiaoH. sys
After log .dll loads XiaoH. sys, the driver file obtains its driver object and performs HOOK on IRP _ MJ _ DEVICE _ CONTROL for the system driver file of nsiproxy.sys, thereby hiding the network connection of the target process.
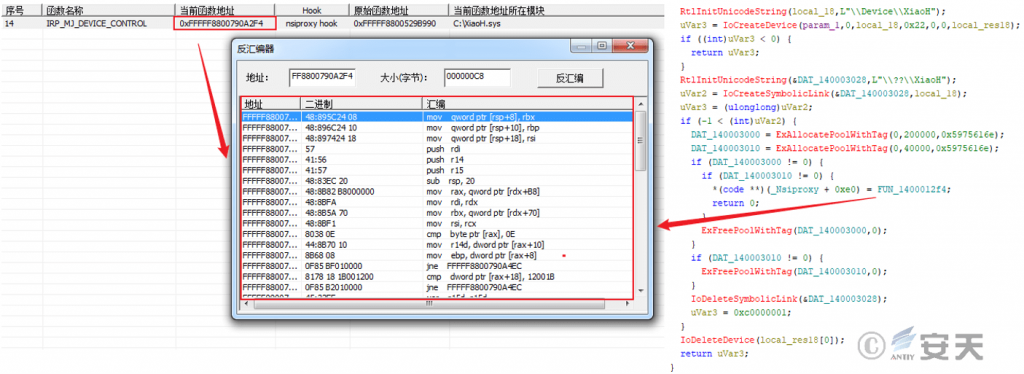
Figure 3-33 Hidden target process network connection
Adds the specified path to the Microsoft Defender exclusion
Thread 3 of log.dll executes the PowerShell command to add the specified path to the Microsoft Defender exclusion.
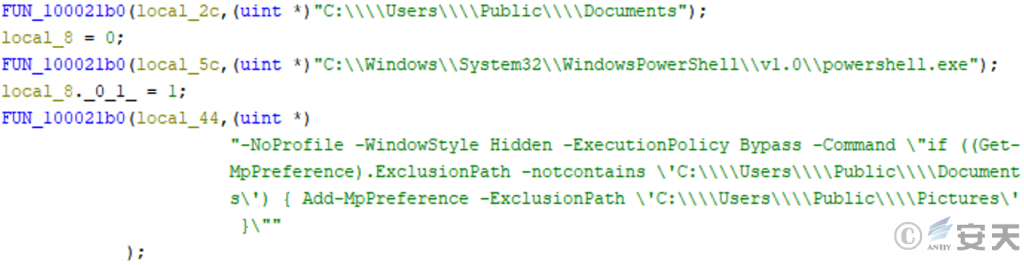
Figure 3-34 Adding a Specified Path to a Microsoft Defender Exclusion
4. Use tools to check the threat of “Swimming Snake (Silver Fox)
Users can download and use the special screening tool “Swimming Snake” on the Antiy vertical response platform (https://vs2.antiy.cn) for screening. The “Swimming Snake” special troubleshooting tool can be used to troubleshoot the loaders placed by the “Swimming Snake” gang in attack activities and remote control Trojans loaded into memory.
Figure 4-1 Safety Vertical Response Platform
In order to more accurately and comprehensively eliminate the threats existing in the victim host, customers may contact Antiy’s emergency response team (cert @ antiy.cn) after using the special screening tool to detect the threats.
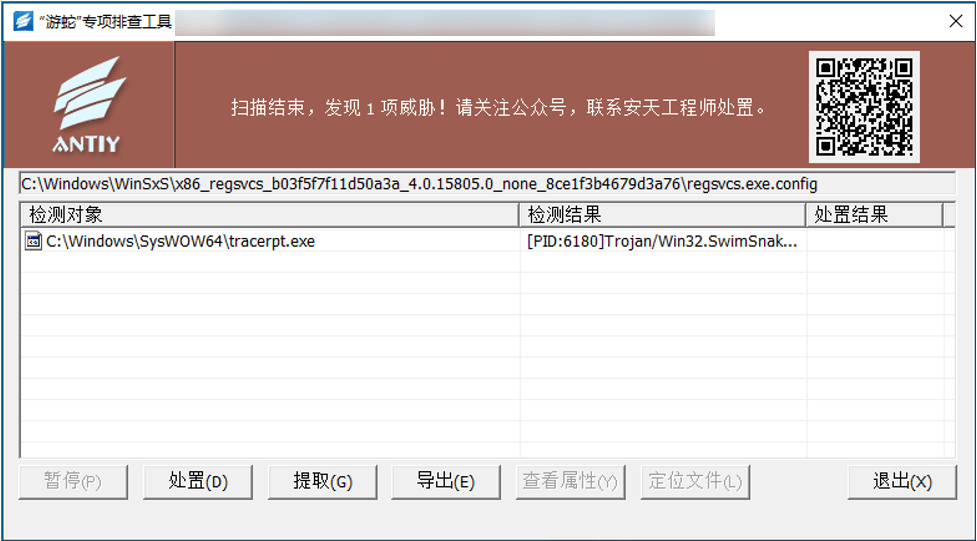
Figure 4-2 Malicious process injected into remote control Trojan detected by the “Swimming Snake” special troubleshooting tool
5.The Antiy IEP terminal defense system helps users defend against the Swimming Snake threat
As an enterprise-level terminal security protection product for office machines, servers and other terminals, the Terminal Defense System of Antiy IEP helps users effectively protect against snake attacks through multi-dimensional protection against the attack characteristics of snake viruses.
5.1 Based on Antiy AVL SDK threat detection engine, the virus will be killed upon landing
IEP is embedded into Antiy AVL SDK anti-virus engine to scan file objects, storage objects, sector objects, memory objects and registry data objects, and judge whether the detection objects are known or suspected viruses. In order to realize accurate judgment, investigation and killing. In particular, it can nest and scan that compressed package object, and scan the memory object based on the memory map, so that a variety of camouflage and kill-free methods can not be hidden. In case 1 and case 2, when the user stores the malicious files youd _ fanyiKП _ 2.0. msi and Wcnhguhyr.exe locally, an alarm will be generated immediately, and the malicious files will be cleared, without giving the chance to start the virus.
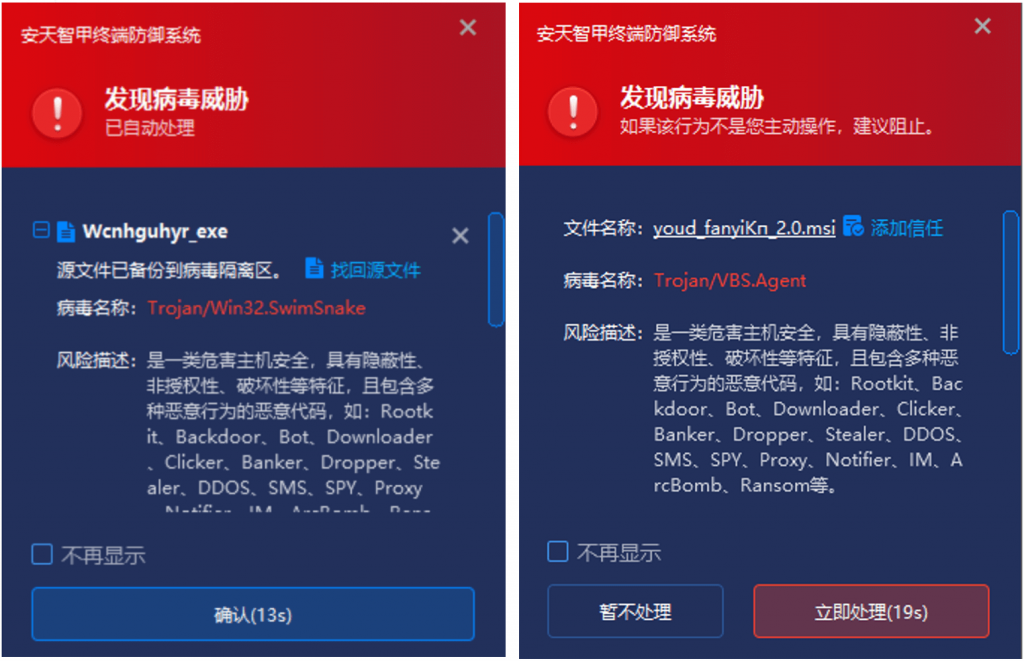
Figure 5-1 Alarm and Automatic Elimination of Virus Immediately upon Landing
5.2 Based on the core-level active defense capability, real-time interception of attacks or high-risk behaviors
The core active defense module of Antiy IEP can monitor the whole process of process startup in real time, detect and judge the risk of process behaviors and parameters, and especially intercept high-risk operations implemented by system processes. In that case of this second case, When a malicious program registers a load driver through the sc create rwdriver binPath = “C:\Users\Public\Documents\WindowsData\rwdriver.sys” type = kernel start = demand, The module accurately identifies its driver registration behavior, and after verification, finds that the reputation of the directory where the target driver is located is high-risk and lacks valid digital signature, and then blocks the registration and loading process, and successfully blocks the implantation of malicious drivers.
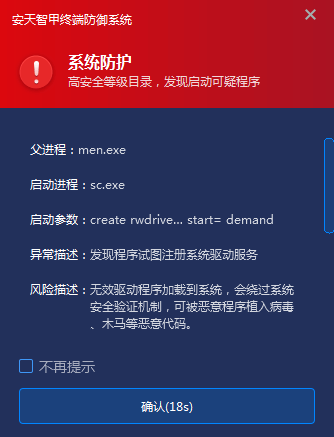
Figure 5-2 Intercept when a malicious program loads a driver
In addition, IEP has a registry protection module to monitor key registry entries in real time. In this case 2, the intellectual will monitor the creation of HKLM\ System\ CurrentControlSet\ Services, and perform depth detection on the ImagePath pointing files of all services registered under the path. Once a document is determined to be a risk-driven document based on multi-dimensional risk assessment such as document path characteristics, attribute information and signature validity, the registration of the document to the system service shall be rejected immediately. Form a double defensive closed loop of “process behavior interception + registry source control.”
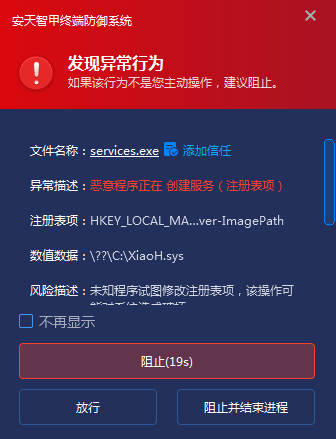
Figure 5-3 Defense against abnormal registry operations detected by IEP
IEP can also monitor the execution behavior of program commands in real time, determine whether there is safety risk in the execution of commands by analyzing the contents of commands and the maliciousness of the execution program, and intercept the risk behavior immediately. In this case 2, the malicious program’s attempt to add itself to the Windows Defender exclusion list through the PowerShell command will be perceived by the defense rule in real time. The system will conduct risk assessment in combination with the parent process directory, file characteristics, attribute information, signature information and other dimensions, and once it determines that there is a risk, the system will immediately stop the PowerShell operation and terminate the parent process.
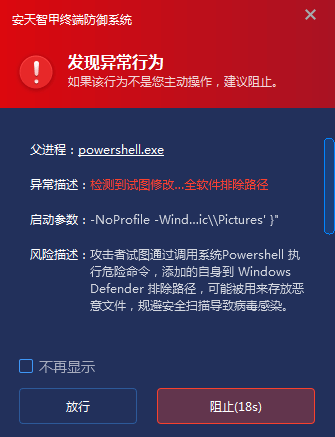
Figure 5-4 Immediately Intercept when Dangerous Command is Executed
IEP has special download protection functions for downloading files, including prohibiting the execution of executable program of the IM directory, blocking invalid signature files downloaded by the browser, and blocking the operation of files with dual extension. And restrict the execution of files such as PE and LNK by specific directories to form a layered protection system. In this case 2, the malicious file NtHandleCallback.exe is released to the C:\ Users\ Public\ Documents\ directory. When the conventional virus detection fails to identify the threat, the control strategy of IEP is triggered immediately, according to the rule that “Documents directory is the file storage area, and executable files are usually not stored.” Directly block the execution of any PE file under the directory, so that the malicious program is effectively blocked by the protection of the policy layer outside the detection mechanism
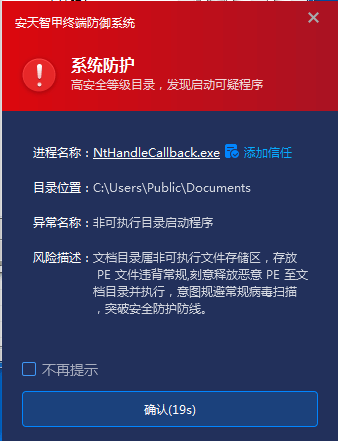
Figure 5-5 The downloading protection function of the intelligent armor blocks the abnormal activation behavior
IEP has memory protection capabilities, which can monitor system memory variables in real time. In the events of Case One and Case Two, when the attacker writes shellcode into the memory, the active defense will detect it. When this memory is executed, the detection mechanism will be triggered. If malicious behavior is found, it will proactively notify the user and stop the program from continuing to execute.
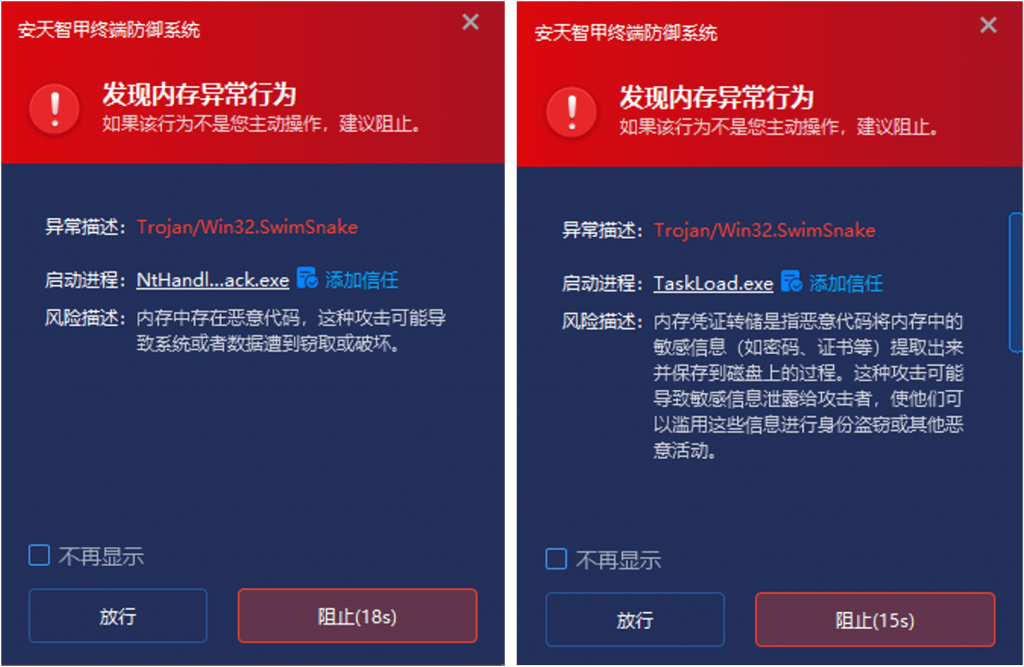
Figure 5-6 Abnormal behavior of memory detected by memory protection function of IEP
IEP can effectively protect remote control Trojan, malicious C2 access and other behaviors through distributed firewall module, and IEP can monitor network traffic in and out of stack data in real time. In combination with accurate detection of threat intelligence, malicious address are intercepted to form a low-level network protection screen.
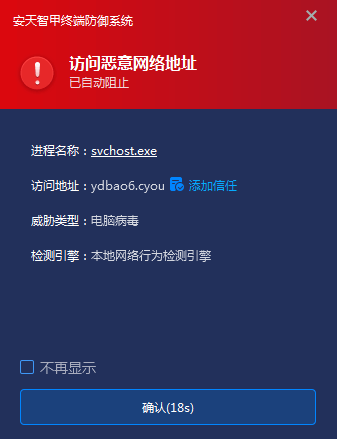
Figure 5-7 Real-time detection of the access address of the program, and once the access malicious address is found, it is immediately intercepted
5.3 Provide a unified management platform to help administrators efficiently carry out security management
IEP also provides a unified management platform for users, through which administrators can view details of threats within the network in a centralized manner and handle them in batches, thus improving the efficiency of terminal security operation and maintenance.
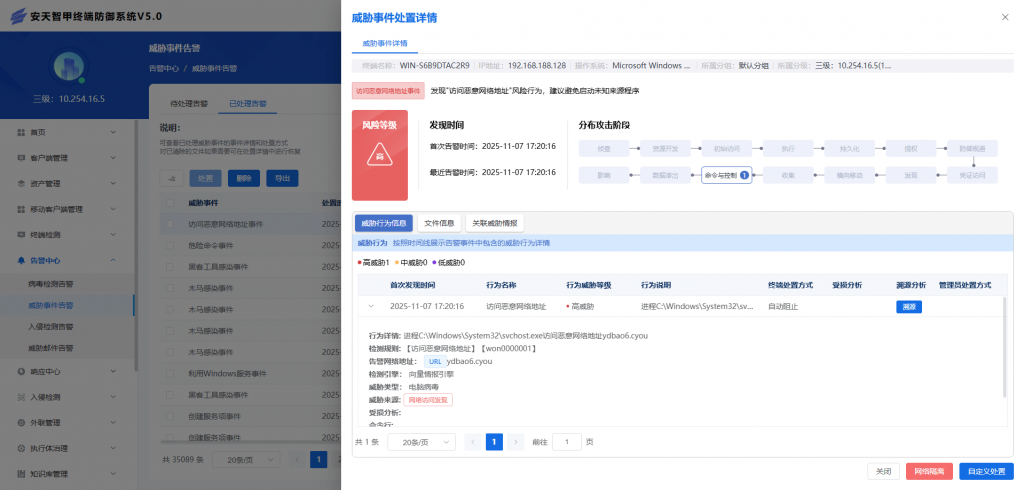
Figure 5-8 Provide a unified management platform, and remotely handle threats with one click
6. IoCs
| IoCs |
| 05946b9848551eb738c9fdf748af0ff2 |
| Ddb9a28b72098ee0ec2308d90f2e0334 |
| E4234abffc87519afac9705ca73b7c30 |
| 04264646287bb028ad5280cf4da39358 |
| Da0d77e9ac7a60f67d55256e55307713 |
| 0d9b54b8bfe67ce90a98102d763345f9 |
| 5231a08c5286803e300ac657e37272f8 |
| 8a7442439ef37055d790a724ba48bee0 |
| C2a1e8510738ddf23b839eef223f7bec |
| 893edfa3a3a71d71ca670424e554e04c |
| C416a4664a84a5bd4f8f032472e56cdd |
| 0462f77ae086e8cdc48f9a21758fd67e |
| 212fc4b489c15436de3e34ac96e1207b |
| 08cfaac200ed8052a63020f115c6a75a |
| 07c8b3bf5ef18bdd646980f765de0fc6 |
| E059cf1f916302a0ff91b0061da1c14 |
| 42ddb89706155089a04b9eba5e661516 |
| 234ccbcb8460721aa990a350d2237036 |
| 0d7d0cf8a31422cd9a88fa90ad7560eb |
| B6ede7ecbb980723ec43c7b1bde059b9 |
| 8dc9c86cf33fc0cbc20cfd3cb6f5d3a3 |
| 1c993a7b64d9e7c3379ab8849d6f17d4 |
| B6ede7ecbb980723ec43c7b1bde059b9 |
| 0d7d0cf8a31422cd9a88fa90ad7560eb |
| 0c9b34b15361b87b738dc06fc4194086 |
| 5b81e82e3c4594d82085f6a0e0563a07 |
| 18a4dff46a1bae8e317a999a1837f8f2 |
| 154.86.0 [.] 40: 443 |
| Https [:] / / www.bg-wps.com |
| Https [:] / / pub-3d7ecf8d8ed94374b9fb10d61138bd72.r2.dev / Wjfrpsl.zip |
| Ydbao6 [.] you: 9000 |
Since 2022, Antiy CERT has released 17 analysis reports on “Swimming Snake” related activities.
List of Antiy’s historical reports on the threat of “Swimming Snake”.
[1] Analysis of attacks on remote control Trojans placed by falsifying Chinese Telegram websites [R/OL]. (2022-10-24)
Https: / / www.antiy.cn / research / notice & report / research _ report / 20221024.html
[2] Analysis of attacks on remote control Trojan delivered by cloud note-taking platform [R/OL]. (2023-03-24)
Https: / / www.antiy.cn / research / notice & report / research _ report / 20230324.html
[3] Analysis of gangs using cloud note-taking platform to deliver remote-controlled Trojans [R/OL]. (2023-03-30)
Https: / / www.antiy.cn / research / notice & report / research _ report / 20230330.html
[4] Analysis of large-scale attacks launched by “snake-swimming” gangs against domestic users [R/OL]. (2023-05-18)
Https: / / www.antiy.cn / research / notice & report / research _ report / 20230518.html
[5] Analysis of recent fishing attacks by “snake swimming” gangs [R/OL]. (2023-07-11)
Https: / / www.antiy.cn / research / notice & report / research _ report / TrojanControl _ Analysis.html
[6] Analysis of the activities of the “Snake Runner” gang in using WeChat to spread malicious codes [R/OL]. (2023-08-22)
Https: / / www.antiy.cn / research / notice & report / research _ report / SnakeTrojans _ Analysis.html
[7] Special Analysis Report on “Swimming Snakes” and Black Producers [R/OL]. (2023-10-12)
Https: / / www.antiy.cn / research / notice & report / research _ report / SwimSnakeTrojans _ Analysis.html
[8] Analysis of the new round of attacks against financial personnel and e-commerce customer service by the “Snake Swimming” gang [R/OL]. (2023-11-11-11)
Https: / / www.antiy.cn / research / notice & report / research _ report / SwimSnake _ Analysis.html
[9] Analysis of the recent attack activities of the “Swimming Snake” black farm [R/OL]. (2024-04-07)
Https: / / www.antiy.cn / research / notice & report / research _ report / SwimSnake _ Analysis _ 202404.html
[10] Analysis of phishing attacks by “snake-swimming” gangs using malicious documents [R/OL]. (2024-06-21)
Https: / / www.antiy.cn / research / notice & report / research _ report / SwimSnake _ Analysis _ 202406.html
[11] The phishing download website spreads the threat of “Swimming Snake,” and the malicious installer hides the remote control Trojan [R/OL]. (2024-12-20)
Https: / / www.antiy.cn / research / notice & report / research _ report / SwimSnake _ Analysis _ 202412.html
[12] “Swimming Snake” attacks wreak havoc with black products, and quick start special investigation and handling [R/OL]. (2025-04-23) https: / / www.antiy.cn / research / notice & report / research _ report / research _ report / SwimSnake _ Analysis _ 202504.html
[13] The black production of “Snake” uses fake WPS Office download stations to spread remote control Trojan horses [R/OL]. (2025-05-15)
Https: / / www.antiy.cn / research / notice & report / research _ report / SwimSnake _ Analysis _ 202505.html
[14] “Swimming Snake (Silver Fox)” attacks by the latest variety of black production [R/OL]. (2025-08-17)
Https: / / www.antiy.cn / research / notice & report / research _ report / SwimSnake _ Analysis _ 202508.html
[15] The spreading of black products and continuous tracking of techniques and tactics of snake (Silver Fox): Analysis of attack methods of imitation FinalShell management software [R/OL]. (2025-09-19)
Https: / / www.antiy.cn / research / notice & report / research _ report / SwimSnake _ Analysis _ 202509.html
[16] Snake Runner (Silver Fox) “Black production intensive imitation of all kinds of popular applications: Wps download station anti-fake album [R/OL]. (2025-10-10)
Https: / / www.antiy.cn / research / notice & report / research _ report / SwimSnake _ Analysis _ 202510.html
[17] Delete such files immediately upon receipt! Avoid falling into the trap of “Swimming Snake” [R/OL]. (2025-10-23)
Https: / / www.antiy.cn / research / notice & report / research _ report / SwimSnake _ Report _ 202510.html


