Analysis of Torii’s Remote-Controlled Cyber Attacks by the OceanLotus Organization
The original report is in Chinese, and this version is an AI-translated edition.
1.Overview
Recently, Antiy CERT has captured a number of active remote control Trojans for the Internet of Things, and the attackers behind it are not for economic benefit. After attacking a considerable number of Linux hosts, servers and Internet of Things equipment of important government and enterprise units in China. The Trojan horse has rich command control ability, and on the C2 return link, the real command control server is hidden by the domestic and overseas IOT devices that are attacked in advance as the traffic springboard. Through correlation tracing, Antiy CERT found that the Trojan horse belonged to the upgraded version of Torii botnet family [1], and had certain homology and difference with the same remote control Trojan horse organized by Lotus. Moreover, there is overlap between the network assets based on the network assets and the attack activities organized by the early sea lotus group.
Finally, Antiy CERT found that the Torii family is likely to be the third mature and commonly used remote control equipment for Linux hosts, servers and IoT platforms in Hytera, in addition to the two-headed dragon family [2] and the Buni family [3].
Table 1-1 Characteristics of attack activities ‑
| Key Points of Events | Feature content |
| Attack time | It dates back to 2017 and is active today |
| Organization involved | Sea Lotus (APT-TOCS) |
| Overview of the event | Sea Lotus uses Torii to remotely control cyber attacks against our country |
| Attack the target | China |
| Method of attack | Voucher explosion, vulnerability attack, etc |
| Weapons and tools | Torii remote control |
| Intent to attack | Stealing secrets |
2.Analysis of attack activities
2.1 Introduction to the event
The remote control family involved in the attack, also known as Torii, has been traced back to the results that the remote control is likely to be developed and operated by the sea lotus group. The attacks involved in remote control were first disclosed in 2018, when the earliest activity dates back to 2017 due to their complexity, when the industry considered the next generation of IoT botnets. It has been found that it spreads through weak password explosion, vulnerability attack and other means, because it is mainly used for targeted attacks, and will not scan other devices in the whole network based on infected devices. In addition, that infect equipment will not be used for mine excavation, extortion, DDoS and other activities, so that it has been in a relatively good hidden state for five year.
The remote control has rich functions and wide adaptation. it supports the generation of loads of CPU architectures such as ARM, x86, x64, MIPS, SPARC, PowerPC, SuperH, Motorola 68000, etc. Capable of deep information theft and control of servers, IoT devices and office hosts running in the above architecture, in addition to more than 10 groups of command control capabilities.
In recent years, Torii has been active in network attacks against China organized by Lotus, and attackers have installed traffic forwarding tools by attacking domestic public network routers, cameras and other network equipment as a springboard. The theft and control traffic from the device that will be embedded in the Torii Trojan horse is forwarded to the real Torii remote control C2 server via one or more skips. Based on the available springboard and the real C2 to find the domestic controlled conditions, it is found that there were over 17,000 suspicious controlled traffic accesses in the first half of 2022, and Torii has preliminarily established a botnet size in China.
2.2 Analysis of remote control function
2.2.1 Adversarial analysis capability
1.Character encryption
Most sensitive strings are encrypted, and the runtime decryption algorithm is a custom round-robin exclusive-or:
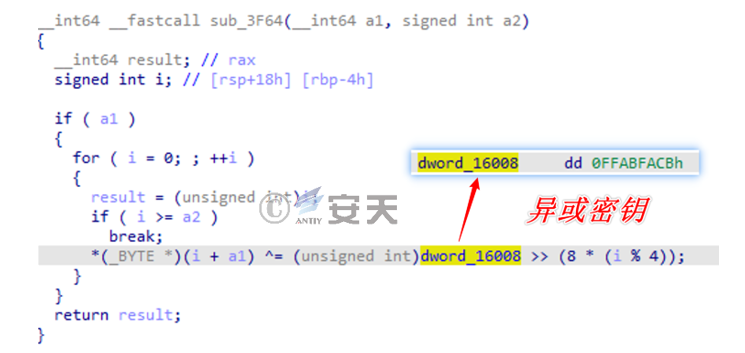
Figure 2-1 Character decryption function ‑
After Trojan executes, carry on sleep () function first sleep, sleep time is defaulted to 60 seconds or according to pass parameter and user-defined, this can combat part of the automation analysis such as sandbox.

Figure 2-2 Dormancy after Operation ‑
The child process after the parent process exits, the process name is named as a string randomly generated by the regular expression, which can resist the screening detection based on the process name.
Figure 2-3 Sub-process name are randomized ‑
Although the trojan mainly uses the port 443 to communicate, the process actually does not use the TLS encryption, but uses the RC4 encryption to reverse the sequence:
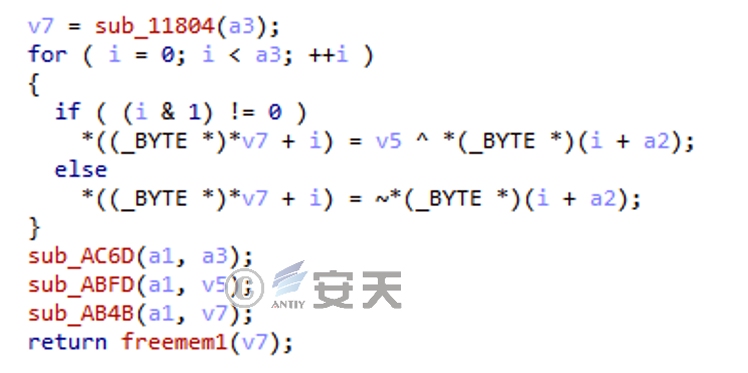
Figure 2-4 Communication traffic encryption algorithm ‑
Although the above description of this attack is not fully understood, judging from the attack process in the history of the Torii family, this remote control should also have a first-stage parent body, which is Dropper, which is responsible for releasing the remote control. Will be the remote control landing position from the directory table and camouflage normal file name table these two tables are random combination.
Table 2-1 Landing position is randomly combined by two tables ‑
| Table of Contents | File name table |
| / usr / bin | Setenvi |
| / usr / lib | Bridged |
| Home _ PATH | Swapper |
| / system / xbin | Natd |
| / dev | Lftpd |
| $LOCATION _ OF _ 1ST _ STAGE | Initenv |
| / var / tmp | Unix _ upstart |
| / tmp | Mntctrd |
| . |
2.2.2 Ability to steal information
In addition to using system functions to obtain host names and MAC addresses, the Trojan horse will also obtain rich system software and hardware information by decrypting a batch of shell commands, such as:
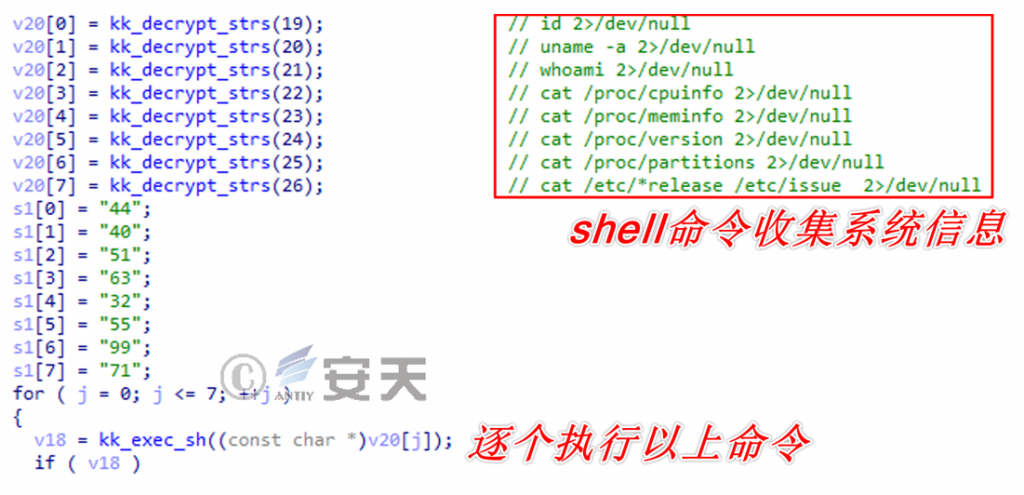
Figure 2-5 Perform the collection of information ‑
The collated shell commands and collection objects are shown in Table 22. ‑
Table 2-2 Information collection command correspondence information ‑
| Shell command | Corresponding information |
| Id 2 > / dev / null | User id |
| Uname-a 2 > / dev / null | Operating system information |
| Whoami 2 > / dev / null | User name |
| Cat / proc / cpuinfo 2 > / dev / null | Processor information |
| Cat / proc / meminfo 2 > / dev / null | Amount of memory |
| Cat / proc / version 2 > / dev / null | |
| Cat / proc / parts 2 > / dev / null | Partition block allocation information |
| Cat / etc / * release / etc / issue 2 > / dev / null | System identification |
2.2.3 Remote control capability
The functions of remote control are sorted out, including control and stealing local files, command execution and payload downloading, as listed in Table 23. ‑
Table 2-3 Command control functions ‑
| Instructions | Main functions |
| 0xbb32 | Download file from C2, MD5 check and save |
| 0xe04b | Searches for the specified file and returns the size |
| 0xebf0 | Gets the heartbeat or ping |
| 0xf28c | Read the contents of the file at the specified offset to C2 |
| 0xc221 | Download the file from the specified URL |
| 0xdeb7 | Delete the specified file |
| 0xa16d | Gets the timeout value |
| 0xa863 | Download file from C2 with permission flag rwxr – xr – x and execute |
| 0xae35 | Executes the given shell command, and the result returns C2 |
| 0x5b77 | Gets the heartbeat or ping |
| 0x73bf | Gets the heartbeat or ping |
The C2 address of the remote control connection is solved by the same decryption algorithm. in the attack, both the real C2 server connected directly and the forwarding port connected to the domestic springboard exist, and then go to the next hop:
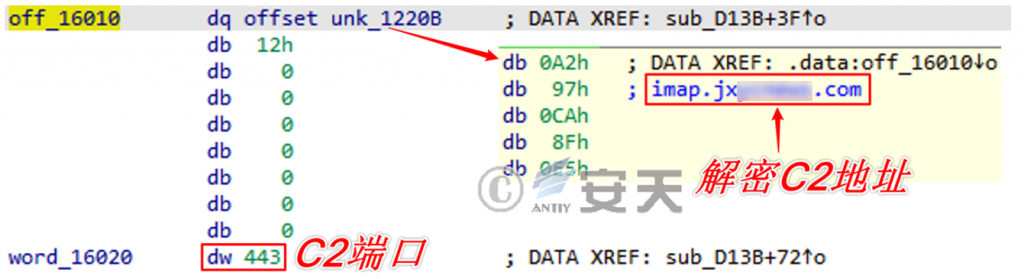
Figure 2-6 Direct Connection to C2 Server ‑
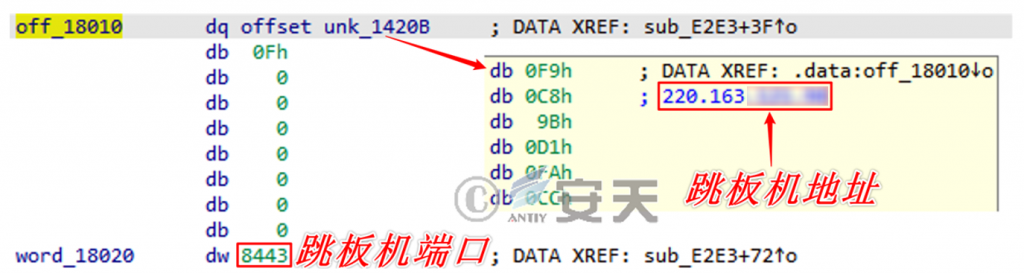
Figure 2-7 Connecting Springboard Machine and Forwarding Port ‑
3.Backhaul Link Analysis
When the C2 address hard-coded by the Trojan horse is the springboard, the springboard is generally an IoT device, mainly home-made router, home-made VPN device, public network camera, etc., and malicious traffic of TCP protocol enters the device through 8443, 8773 and other ports. It is then forwarded to the real C2 server or to a more layered springboard.
In terms of services run by the springboard device, it is possible for an attacker to gain system execution rights through 0day or even 0day vulnerability attacks. In the past, Lotus has used self-developed or open-source forwarding tools and firewall forwarding rules to realize traffic forwarding on the IoT springboard, but it has not further grasped the internal information of the springboard. Guess the same is true of this campaign, such as Github’s open source tinyPortMapper, which supports Linux / Windows / MacOS hosts, Android phones / tablets, routers, Raspberry Pi devices, etc. For example, the TCP and UDP traffic received by the local port 1234 is forwarded to the port 443 of the destination IP.
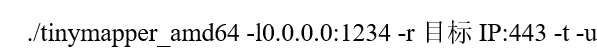
Figure 3-1 How tinyPortMapper is used –
When the hard-coded address is the real C2 server, the target port is 443, and the domain name and VPS are scattered abroad, with no obvious characteristics.
4.Connection traceability
4.1 Highly homologous to the Torii family
Through code comparison, Antiy CERT found that the Trojan family had a lot of homology with the Trojan horse in the second stage of the Torii botnet, and it could be confirmed that they belong to the same Trojan family. But there are relatively more standard code implementations and upgrades, a new version of the Torii family.
Table 4-1 Homology of the Trojan Horse Family and Torii ‑
| Homology | This Trojan family | The Torii family |
| Means of adversarial analysis | 1. character XOR encryption, key: 0xfffabfacb; 2. sleep first after execution; Randomization of child process names. | 1. character XOR encryption, key: 0xfebceade; 2. sleep first after execution; Randomization of child process names. |
| Instruction functions are basically the same | 0x5b77, get heartbeat or ping | 0x5b77, get heartbeat or ping |
| 0x73bf for heartbeat or ping | 0x73bf for heartbeat or ping | |
| 0xa16d, get the time-out value | 0xa16d, get the time-out value | |
| 0xa863, download file from C2, flag rwxr-xr-x, and execute | 0xa863, download file from C2, flag rwxr-xr-x, and execute | |
| 0xae35, execute a given shell command, The result returns to C2 | 0xae35, executes the given shell command, and the result returns C2 | |
| 0xbb32, download the file from C2, Md5 verifies and saves | 0xbb32, download file from C2, MD5 check and save | |
| 0xc221, download file from given URL and save | 0xc221, download file from given URL and save | |
| 0xdeb7, delete the specified file | 0xdeb7, delete the specified file | |
| 0xe04b, searching for the specified file and returning the size | 0xe04b, searching for the specified file and returning the size | |
| 0xebf0 for heartbeat or ping | 0xebf0 for heartbeat or ping | |
| 0xf28c, read the contents of the specified offset of the file and send it to C2 | 0xf28c, read the contents of the specified offset of the file and send it to C2 | |
| 0xb76e, meaningless | ||
| 0xf76f, switch the new C2 address | ||
| C2 Address | Hard coding, each sample contains 1 address, can be an attacker self-registered domain name, can also be a springboard server |
4.2 The homology and difference with the remote control family of lotus
The domestic Netlab laboratory’s research report [4] shows that: The two-headed dragon family and the MacOS remote control organized by the Lotus group are remarkably similar from the establishment of the C2 session, the online package structure, the encryption and decryption algorithm, and even the function pairs of instructions. The two-headed dragon family can be referred to as the sea lotus MAC remote control on Linux platform implementation version.
Earlier reports showed that [2], there were similarities in the reuse of sensitive commands, traffic construction and persistence between the two families, and the report speculated that the two families might be the same attacker.
Antiy CERT further analysis found that although there are individual similarities between the two-headed dragons and the Torii family, the overall differences are much more than coincidence. the following table lists two-headed dragons, Torii and another known Linux remote control Buni family. Important differences between the three are shown in Table 42. ‑
Table 4-2 Differences between Torii Family and Diplodocus ‑
| Points of difference | Two-headed dragon family (sea lotus) | The Torii family | Buni Family (Sea Lotus) |
| Encryption and decryption algorithm for sensitive characters: There are no identical encryption and decryption algorithms | Aes algorithm, cyclic shift algorithm | Multi-byte round-robin exclusive-or algorithm | Single-byte round-robin exclusive-or algorithm |
| Corresponding relationship of instruction functions: No same instruction function corresponding | Article 12: 0x138e3e6, 0x208307A 0x5cca727, 0x17B1CC4 0x25360ea, 0x18320e0 0x2e25992, 0x2CD9070 0x12b3629, 0x1B25503 0x1532e65, 0x25D5082 | Article 11: 0xbb32, 0xE04B 0xebf0, 0xF28C 0xc221, 0xDEB7 0xa16d, 0xA863 0xae35, 0x5B77 0x73bf | Article 7: 0x48b8, 0x5C37 0x5c7c, 0x7221 0xb616, 0x1CE3 |
| Encryption algorithm for communication traffic: There are no identical encryption algorithms | Zlib Compression after AES Encryption | Md5 verification after AES-128 encryption; Or put in reverse order after RC4 encryption | Gzip Compression after XOR Encryption |
| Network assets: No identical network assets overlap | News.th * * * .net Blog.edu * * * .com Cdn.mir * * * .net Status.sub * * * .net More. | Jd – * * * .com Kjtzgz.szl * * * .org Update.firm * * * .com More. Or IoT springboard | Zabbix * * * .com More. Or IoT springboard |
From the perspective of overall functional design, code implementation and asset support, the local similarity of Torii, Double-headed Dragon and Buni indicates that they may come from the same attacker, But the three cannot be divided into the same malicious code family, but should belong to three different remote control tools.
4.3 Connection with the assets of the Lotus Group
The Torii family’s active payload distribution server 185.174 in February 2020. * * *. * * *, which was bound to the known domain name svena * * .com from 2017 to 2018, And a highly suspicious domain name hosti * * * .xyz that can be linked to multiple historical assets of sea lotus.
Table 4-3 Asset Correlation between the Organization and the Lotus Group 1 ‑
| Torii family assets | Historical binding relationship | Historical binding relationship | Linking the known assets of Hailian Lotus |
| 185.174.* * *. * * Property: Payload Distribution Server | Svena * * .com, the known domain name of sea lotus | ||
| Hosti * * * .xyz | 185.174.* * *. * * | Mariala * * * .club | |
| 185.174.* * *. * * | Loucest * * * .club | ||
| Annette * * * .club | |||
| Ganmo * * * .com | |||
| Abigails * * * .com | |||
| Barbara * * * .com | |||
The Torii family C2 domain name zhi * * * .com, which was active in February 2022, was first resolved to the dynamic IP address 188.166. * * *. * * *. * *, which was mentioned in the Kaspersky PhantomLance Activity Report [5]. Further analysis found that it is not a private IP of Hytera Lotus, However, since 2018, Hytera has preferred to temporarily point a large number of domain name assets such as Denes Remote Control, KerrDown Downloader, Phantom Lance Android Trojan and theft during the Covid19 pandemic to the IP.
Table 4-4 Asset Correlation between the Organization and the Lotus Group 2 ‑
| Torii family assets | Historical binding relationship | Linking the known assets of Hailian Lotus |
| Zhi * * * .com Nature: C2 domain name | 188.166. * * *. * * | Udt.sophi * * * .com, Denes remote control |
| E.browser * * * .com, KerrDown Downloader | ||
| Elizongha * * * .com, PhantomLance Android Trojan | ||
| Georgiath * * * .com, PhantomLance Android Trojan | ||
| Dictionari * * * .com, Cobalt Strike remote control | ||
| Social.ceri * * * .com, Remy Remote Control | ||
| Aidanpain * * * .com | ||
| Others |
To sum up, the relationship between Torii and the early network assets of Hailanhua, the high homology between the codes of the two-headed dragon family organized by Hailanhua and the MAC remote control family of Hailanhua, and the similarity in design between Torii and the two-headed dragon family. Moreover, the Torii family recently attacked China’s Internet of Things (IoT) equipment as a springboard through similar attacks organized by Hailotus in recent years to control the network and office equipment of important government and enterprise units in China. There are reasons to believe that the Torii family is probably the third mature remote control tool for Linux or IoT platforms in addition to the two-headed dragon family and the Buni family.
5.ATT&CK Mapping from the Perspective of Threat Framework
This series of attacks involves 17 technical points in 10 phases of ATT & CK framework, and the specific behavior is described in Table 5-1.
Table 5-1 Description of technical behavior of recent Torri attacks ‑
| ATT&CK phase | Specific behavior | Notes |
| Reconnaissance | Active scanning | Scan for IOT devices that are exposed to the public network and have specified vulnerabilities |
| Resource development | Access to infrastructure | Register the C2 domain name, purchase and build the C2 server |
| Intrusion into infrastructure | Intrusion into a server or IOT device as a springboard | |
| Initial access | Make use of public-facing applications | Exploit application services that are exposed in the public network and have vulnerabilities |
| Use of external remote services | Password blasting for remote services exposed in the public network | |
| Execution | Using command and script interpreters | Use shell script to install subsequent trojan horse after obtaining permission |
| Persistence | Use automatic startup to perform booting or logging | Implement boot-time with / etc / init |
| Utilization of planned tasks / jobs | Using crontab to schedule tasks for automatic execution | |
| Defensive evasion | Circumventing the debugger | Process name randomization evades debugger attach |
| Counterfeit | The manual file name is copied into a normal system file | |
| Findings | Discovery of account | Access to system account information |
| Discovery of system information | Get the system version information | |
| Discovery system network configuration | Access to system network information | |
| Collection | To compress / encrypt the collected data | The collected data is encrypted by exclusive OR and then AES |
| Command and control | Encoded data | The collected data is encrypted before it is communicated |
| Standard non-application layer protocols are used | Communication using TCP protocol | |
| Data seeps out | The C2 channel is used for backtransmission | The remote control uses the traditional C2 channel communication |
Mapping the technical points involved in the threat behavior to the ATT & CK framework is shown in Figure 5-1.
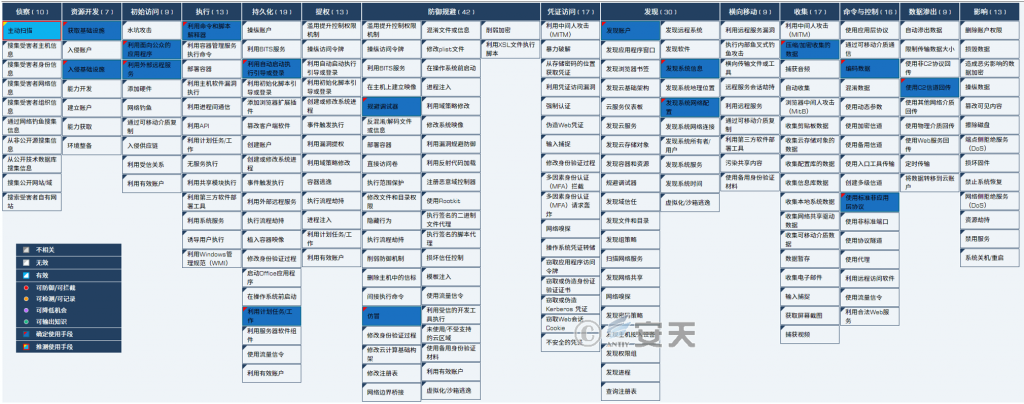
Figure 5-1 Mapping of Recent Torri Attack Activities to ATT&CK
Appendix I: Reference
[1] Torii botnet – not another Mirai variant
Https: / / blog.avast.com / new-torii-botnet-threat-research
[2] Two-headed dragon (Rota Jakiro), a backdoor trojan that has been lurking for at least three years
Https: / / blog.netlab.360.com / health _ rotajakiro _ backdoor _ cn /
[3] Hacker group “sea lotus” battle weapon “Buni” newly revealed, target Linux platform
Https: / / mp.weixin.qq.com / s / 1WtaS7htgiUGhty _ ovERxA
[4] “Double-headed dragon” from the sea lotus group?
Https: / / blog.netlab.360.com / rotajakiro _ vs _ oceanlotus _ cn /
[5] Hiding in plain sight: Phantomlance walks into a market
Https: / / securelist.com / apt-phantomlance / 96772 /
Appendix II: About Antiy
Antiy is committed to enhancing the network security defense capabilities of its customers and effectively responding to security threats. Through more than 20 years of independent research and development, Antiy has developed technological leadership in areas such as threat detection engines, advanced threat countermeasures, and large-scale threat automation analysis.
Antiy has developed IEP (Intelligent Endpoint Protection System) security product family for PC, server and other system environments, as well as UWP (Unified Workload Protect) security products for cloud hosts, container and other system environments, providing system security capabilities including endpoint antivirus, endpoint protection (EPP), endpoint detection and response (EDR), and Cloud Workload Protection Platform (CWPP) , etc. Antiy has established a closed-loop product system of threat countermeasures based on its threat intelligence and threat detection capabilities, achieving perception, retardation, blocking and presentation of the advanced threats through products such as the Persistent Threat Detection System (PTD), Persistent Threat Analysis System (PTA), Attack Capture System (ACS), and TDS. For web and business security scenarios, Antiy has launched the PTF Next-generation Web Application and API Protection System (WAAP) and SCS Code Security Detection System to help customers shift their security capabilities to the left in the DevOps process. At the same time, it has developed four major kinds of security service: network attack and defense logic deduction, in-depth threat hunting, security threat inspection, and regular security operations. Through the Threat Confrontation Operation Platform (XDR), multiple security products and services are integrated to effectively support the upgrade of comprehensive threat confrontation capabilities.
Antiy provides comprehensive security solutions for clients with high security requirements, including network and information authorities, military forces, ministries, confidential industries, and critical information infrastructure. Antiy has participated in the security work of major national political and social events since 2005 and has won honors such as the Outstanding Contribution Award and Advanced Security Group. Since 2015, Antiy’s products and services have provided security support for major spaceflight missions including manned spaceflight, lunar exploration, and space station docking, as well as significant missions such as the maiden flight of large aircraft, escort of main force ships, and Antarctic scientific research. We have received several thank-you letters from relevant departments.
Antiy is a core enabler of the global fundamental security supply chain. Nearly a hundred of the world’s leading security and IT enterprises have chosen Antiy as their partner of detection capability. At present, Antiy’s threat detection engine provides security detection capabilities for over 1.3 million network devices and over 3 billion smart terminal devices worldwide, which has become a “national-level” engine. As of now, Antiy has filed 1,877 patents in the field of cybersecurity and obtained 936 patents. It has been awarded the title of National Intellectual Property Advantage Enterprise and the 17th (2015) China Patent Excellence Award.
Antiy is an important enterprise node in China emergency response system and has provided early warning and comprehensive emergency response in major security threats and virus outbreaks such as “Code Red”, “Dvldr”, “Heartbleed”, “Bash Shellcode” and “WannaCry”. Antiy conducts continuous monitoring and in-depth analysis against dozens of advanced cyberspce threat actors (APT groups) such as “Equation”, “White Elephant”, “Lotus” and “Greenspot” and their attack actions, assisting customers to form effective protection when the enemy situation is accurately predicted.


