Antiy AVL SDK Anti-Virus Engine Upgrade Announcement (20251213)
Based on the principles of transparency, accessibility, usability, verifiability and perceptibility of security capabilities, Antiy releases weekly updates of the AVL SDK anti-virus engine and the full set of capabilities to the public every week.
Statistical period: December 6, 2025 ~ December 12, 2025
Antiy AVL SDK anti-virus engine released a total of 84 virus database updates this week, with an average of 12 updates per day, adding 41 new detectable malware families, 7,923 new detectable malicious code variants, and 23,912 new detection rules.
1.Weekly Update
The following table shows the TOP5 newly detectable malicious code families:
| Number | Virus Name | Virus Description |
| 1 | Trojan/Win32.Sysdoz[Ransom] | This family is a type of Trojan. After the sample is executed, it first creates a specific mutex name to prevent repeated running, and then scans the entire disk to encrypt files. The encryption algorithm used is RSA and AES. The file extension of the encrypted files will be changed to “.sysdoz”, and a ransom note named “README.TXT” will be generated at the same time. This sample demands ransom from the victim through the Tor network. |
| 2 | Trojan/Win64.Stealka[PSW] | This family is a type of Trojan, mainly spreading through phishing emails, malicious download links or software carriers. After infecting a user’s computer, it will hide itself and steal sensitive information such as account passwords, bank card information, etc., thereby endangering the privacy security of the user. |
| 3 | Trojan/MSIL.YaLeak | This family is a type of Trojan, mainly spreading through network downloads. It has characteristics such as independent spread and strong concealment. It will attempt to hide itself and steal users’ sensitive information, thereby damaging system security and stability. |
| 4 | Trojan/JS.MagnitudeEK[Exploit] | This family is a type of Trojan that spreads and infects through exploiting system vulnerabilities. The virus disguises itself as normal software or hides in cracked programs or pirated software to trick users into downloading and executing it, stealing users’ sensitive information, including bank accounts, passwords, personal identity information, and other important data. |
| 5 | Trojan/MacOS.Komplex | This family is a Trojan virus targeting the MacOS system. It enters the victim’s computer system by deceiving the user or carrying other malicious software. Once infected, it runs in the background and hides to steal sensitive information, monitors the user’s activities and sends data to a remote server. |
(According to the HASH number of family samples within the period)
For more related content, please visit www.virusview.net (the Computer Virus Encyclopedia).
2. Full Detection Capabilities
As of 24:00 on December 12, 2025, the AVL SDK anti-virus engine can detect 18,400,282 malware variants of 57,919 malware families distributed in 8 basic categories, with a total of 41,303,666 detection rules.
The detection capabilities and the number of rules classified by malicious code are as follows:
| Type | Detectable Malicious Code (Types) | Detection rules (Items) |
| Infectious viruses | 59,102 | 6,947,279 |
| Worms | 313,170 | 4,003,612 |
| Trojans | 13,371,768 | 24,847,000 |
| Hacking tools | 454,713 | 349,374 |
| Risk tools | 1,201,812 | 2,207,222 |
| Rogue software | 3,007,604 | 2,947,994 |
| Junk files | 11 | 1,104 |
| Test programs (for self-test) | 24 | 81 |
| Total | 18,408,204 | 41,303,666 |
Preprocessing Capabilities (partial) :
There are 31 types of shells that can be unpacked (accurate to the type), and 132 packages that can be disassembled, including all common packages and self-extracting packages.
Supporting Knowledge Output Capabilities:
For malware payloads, the AVL SDK and the accompanying malware knowledge base can output 533 key behavior mapping tags, covering 139 categories of ATT&CK tactical tags, with a coverage rate of 64.29%, basically covering all the statically detectable tags in the ATT&CK framework.
3. Be on Guard Against These Virus Families This Week
Recently, Antiy Labs detected an active ransomware sample named Trojan/Win32.Sysdoz[Ransom] on the Windows platform. This ransomware was captured in December 2025. After execution of this family of samples, it first creates a specific mutex name to prevent duplicate runs, then traverses the entire disk to encrypt files. The encryption algorithms used are RSA and AES. The file extensions of the encrypted files will be changed to “.sysdoz”, and a ransom document named “README.TXT” will also be generated. This sample demands ransom from the victims through the Tor network. As of now, no effective tool has been found to decrypt the files encrypted by this ransomware.

3.1 Overview of the Sysdoz Family
| Organization name | Sysdoz |
| Appearance time | December, 2025 |
| Encryption system | Windows |
| Extended name | .sysdoz |
| Technical methods | Encryption and obfuscation, encrypted data |
| Ransom letter | 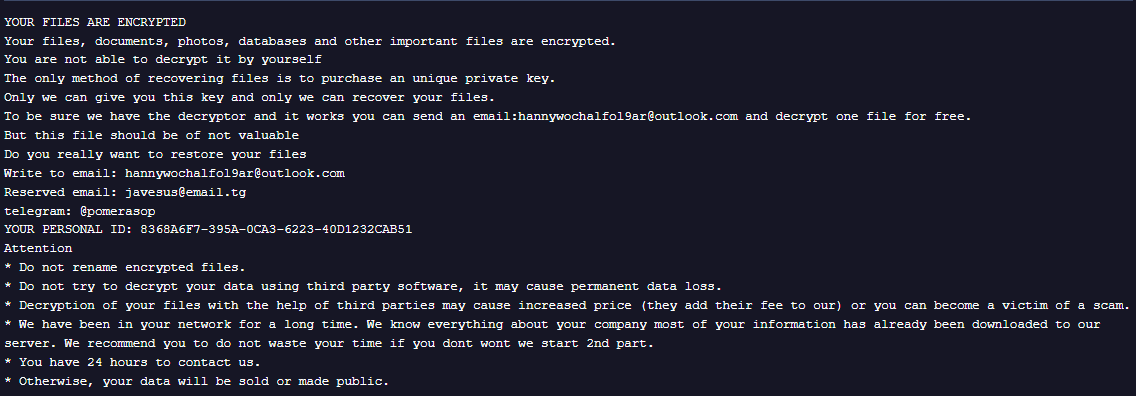 |
Recommendations for Protection
For this ransomware, Antiy recommends the following protective measures:
(1) Install terminal anti-virus software: It is recommended to use host anti-virus and protection products such as Antiy Intelligent Endpoint Protection System (IEP) that use the AVL SDK engine. It is recommended that users of Antiy IEP enable the ransomware defense tool module (enabled by default).
(2) Enhance password strength: Avoid using weak passwords. It is recommended to use 16-character or longer passwords, including combinations of uppercase and lowercase letters, numbers, and symbols. At the same time, avoid using the same password on multiple servers.
(3) Regularly change passwords: Change system passwords regularly to avoid password leaks that may lead to system intrusions;
(4) Timely update patches: It is recommended to enable the automatic update function to install system patches. System patches should be updated in a timely manner for vulnerable parts such as servers, databases, and middleware.
(5) Close high-risk ports: Adopt the minimization principle to external services and close unused high-risk ports such as 3389, 445, 139, and 135.
(6) Email security: Handle suspicious emails carefully to avoid downloading unknown attachments or clicking on unfamiliar links.
(7) Disable PowerShell: If you are not using the PowerShell command-line tool, it is recommended to disable it.
(8) Regular data backup: Regularly back up important files, and the backed-up data should be isolated from the host.
Antiy Emergency Response Service
Antiy continuously empowers users to build an effective network attack security protection system and achieve effective security value.
National service hotline: 400-840-9234
Service support email: support@antiy.cn
Be Vigilant Against New Threats, Fortify Data Defenses!
Appendix: Introduction to Antiy AVL SDK Anti-Virus Engine
Antiy AVL SDK anti-virus engine is a threat detection capability middleware developed by Antiy for all architectures and system platforms. By embedding the AVL SDK, Antiy products and ecosystem partners’ products can acquire virus and malicious code detection capabilities, and receive continuous updates through the virus database.
For eight malicious code categories including infectious viruses, worms, Trojans, hacking tools, gray software, risky software, junk files, and test files, it accurately identifies and detects over 50,000 families and 18 million malicious code variants. The detection capability fully covers all known malicious codes and strictly adheres to the CARO convention. The output is structured and named in sections by classification, environment, and family, and based on the behavioral capabilities of malicious samples, it outputs nearly a hundred types of malicious behavior tags for typical malicious behaviors such as encryption ransomware, data theft, remote control, botnet programs, and mining. Antiy Engine can recognize over 300 file formats and conduct in-depth preprocessing on compilable executable formats such as PE and ELF. It also performs recursive unpacking of various packages (including self-extracting archives), and conduct structural analysis of compound documents such as OFFICE and ACAD files that may contain embedded scripts or vulnerability-prone formats. This ensures high robustness against malicious code. Antiy Engine also comes with a trusted file signature library, supporting the product to implement security policies based on blacklist and whitelist controls, significantly enhancing the difficulty for attackers.
Antiy’s detection capabilities can be fully deployed locally. Antiy automatically analyzes and processes over 2 million new file objects on average every day and releases a virus database update every two hours. It also provides support services such as cloud detection, cloud analysis, and computer virus encyclopedia.
Antiy AVL SDK is available in various versions such as traditional PC hosts, smart terminals, network traffic, IT application innovation systems, industrial systems, and unmanned systems. It provides threat detection capabilities for scenarios including host system and workload security, network traffic security, business flow security, email and file service security, etc. It fully supports various architectures such as X86, ARM, MIPS (including Cavium), RISC, and PowerPC, supports a variety of mainstream operating systems including domestic operating systems, Linux, and Windows, as well as real-time industrial operating systems like Vxwork. It also supports high-speed detection in backbone network scenarios.
Antiy AVL SDK empowers over 100 industry partners. In addition to Antiy’s own product deployment, Antiy Engine has cumulatively covered more than 4 billion nodes (including mobile terminals, secure and controllable PC endpoints, cloud-native nodes, network devices, network security devices, etc.), providing inherent security detection capabilities for mobile phones and smart terminals. The main partners using Antiy Engine include mobile phone enterprises such as Huawei, Xiaomi, Honor, VIVO and OPPO, large Internet enterprises such as Ant Financial, and several listed cybersecurity companies. Partner products using Antiy Engine have won internationally renowned evaluation awards such as AV-TEST and NSS Labs. The “L Tomahawk” logo of AVL SDK has become a symbol of reliable anti-virus capabilities.
All of Antiy’s products, including but not limited to IEP security protection system product family, Unified Workload Protect, Persistent Threat Detection System (PTD), Persistent Threat Analysis System (PTA), Attack Capture System, Qingzhu Zhiyu WAF, etc., all use Antiy anti-virus engine.
The AVL SDK anti-virus engine has been under development since 2001 and has undergone significant version upgrades and iterations. It has successively received support from key national initiatives, including: the Ministry of Science and Technology’s Innovation Fund for Technology-based Firms (2004), the Ministry of Science and Technology’s National High-Tech R&D Program (863 Program) (2006), the National Development and Reform Commission’s Information Security Special Project (2008), and the Ministry of Industry and Information Technology’s Engineering Special Project (2019). The mobile version of AVL SDK won the 2014 AV-TEST Best Protection Award for Mobile Devices. Products powered by the AVL SDK, Antiy PTD and PTA, won first place in both the first and second National Cybersecurity Technology Challenge competitions hosted by the National Computer Network Emergency Response Technical Team/Coordination Center of China (CNCERT/CC).
