“Operation Chart Hunt”: An Analysis of Data Theft Targeting NFT Artists
The original report is in Chinese, and this version is an AI-translated edition.
1.Overview
Since April this year, Antiy CERT has monitored multiple theft activities targeting non-fungible token (NFT) [1] artists, with multiple victims currently. Based on attack methods, C2 addresses and other features, they are linked to large-scale theft operations initiated by the same attack group. Since the attackers’ main target is NFT artworks, Antiy named this activity “Operation Chart Hunt”.
The attackers posed as employees of mobile game development company PlayMe Studio, NFT project “Cyberpunk Ape Executive”, and other companies, sending job recruitment information through art creation social platforms such as ArtStation, Pixiv, and DeviantArt. Each attack message contained a link to a download page where victims could download a compressed file. The compressed file contained not only several sample images but also a stealing Trojan disguised as an image. By hiding the extension, it could easily be mistaken for an image and executed upon click.
Once executed, the stealing Trojan automatically collects computer system information, browser data, e-wallets, NFT managers, password managers, and other software data, then encrypts and transmits this data back to the attacker’s server. If social media platform accounts and passwords are stored in the browser, the attackers will also use the stolen information to log in to the social media platform and continue to post phishing messages to users on other platforms, further expanding the scope of victims. This attack campaign has been ongoing for over a month. During this period, the attackers have continuously changed their shell protection technology while retaining the core functional payload to evade detection by antivirus engines and security software.
With the rise of the next-generation internet “metaverse,” the market for NFTs—identity symbols within the metaverse—has also seen rapid growth. However, as NFTs gain wider recognition, they have also become a new target for attackers. NFTs are a relatively new type of digital asset. Similar to mainstream digital assets like Ether (ETH) and Bitcoin (BTC), they are stored as data on the blockchain and in NFT-compatible wallets. Therefore, attackers can steal the account and password stored in cryptocurrency wallet clients or browsers to open a victim’s digital wallet and steal the NFT artworks. Furthermore, attackers can steal user accounts and passwords through forged phishing websites or attacks on NFT trading platforms. Because NFTs utilize digital technologies such as blockchain, once stolen, there is currently no way to recover them other than immediately locking and prohibiting trading.
Antiy CERT continues to follow up and analyze such incidents. It has been verified that Antiy Intelligent Endpoint Protection System (IEP) can effectively detect and eliminate this stealing Trojan.
2.ATT&CK Mapping Diagram Corresponding to the Incident
The distribution of technical features corresponding to this event is as follows:
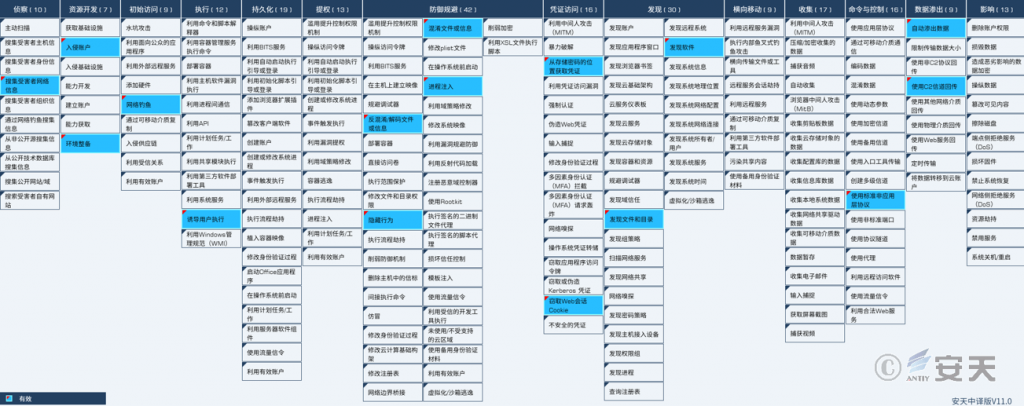
Figure 2-1 Mapping of technical characteristics to ATT&CK
The specific ATT&CK technical behavior description table is as follows:
Table 2 ‑1 ATT&CK technical behavior description table
| ATT&CK stages/categories | Specific behavior | Notes |
| Reconnaissance | Collect victim’s network information | Collect target information |
| Resource development | Hack accounts | Compromised accounts used for further dissemination |
| Resource development | Environmental preparation | Upload the attack payload to the network disk |
| Initial access | Phishing | Phishing |
| Execute | Induce users to execute | Induce users to execute |
| Defense evasion | Deobfuscate/decode files or information | Decrypte the attack payload |
| Defense evasion | Hidden Behavior | Hidden Behavior |
| Defense evasion | Obfuscate files or information | Encrypt attack payload |
| Defense evasion | Process injection | Process injection |
| Credential access | Get the credentials from where the password is stored | Get the key from the password manager |
| Credential access | Steal web session cookies | Steal web session cookies |
| Discover | Discover files and directories | Discover files and directories |
| Discover | Discovery software | Discover target software installed on the system |
| Command and control | Use standard non-application layer protocols | Use TCP protocol |
| Data exfiltration | Automatic exfiltration of data | Automatic exfiltration of data |
| Data exfiltration | Use C2 channel for backhaul | Use C2 channel for backhaul |
3.Protection Recommendations
To effectively defend against this type of malicious code and improve security protection, Antiy recommends that enterprises take the following protective measures:
3.1 Improve Host Security Protection Capabilities
- Install terminal protection system: Install anti-virus software. It is recommended to install Antiy Intelligent Endpoint Protection System.
- Strengthen password strength: Avoid using weak passwords. It is recommended to use passwords that are 16 characters or longer, including a combination of uppercase and lowercase letters, numbers, and symbols. Also, avoid using the same password on multiple servers.
- Deploy an Intrusion Detection System (IDS): Deploy traffic monitoring software or equipment to facilitate the discovery and tracing of malicious code. Antiy Persistent Threat Detection System (PTD) uses network traffic as the detection and analysis object, and can accurately detect a large amount of known malicious code and network attack activities, effectively discovering suspicious network behavior, assets, and various unknown threats;
3.2 Improve Cybersecurity Awareness
- Avoid opening content from unknown sources, including links, files, images, and text messages.
- It is recommended to execute suspicious files in a sandbox environment and only execute them on the host when safety is ensured. The Antiy Persistent Threat Analysis System (PTA) uses a combination of deep static analysis and sandbox dynamic loading and execution to effectively detect, analyze and identify various known and unknown threats.
3.3 Initiate Emergency Response Promptly When Attacked
- Contact the emergency response team: If you are attacked by malware, it is recommended to isolate the attacked host in a timely manner and protect the site while waiting for security engineers to investigate the computer; Antiy 24/7 service hotline: 400-840-9234.
It has been verified that Antiy Intelligent Endpoint Protection System (IEP) can effectively detect and kill this data-stealing Trojan.
Figure 3-1 Antiy IEP provides effective protection for user terminals
4.Attack Process
The attacker sent phishing messages to NFT artists on various platforms, asking them to download encrypted compressed packages under the pretext of examples, and hid the data-stealing Trojan disguised as an image in it, inducing the victim to click on it and execute it.
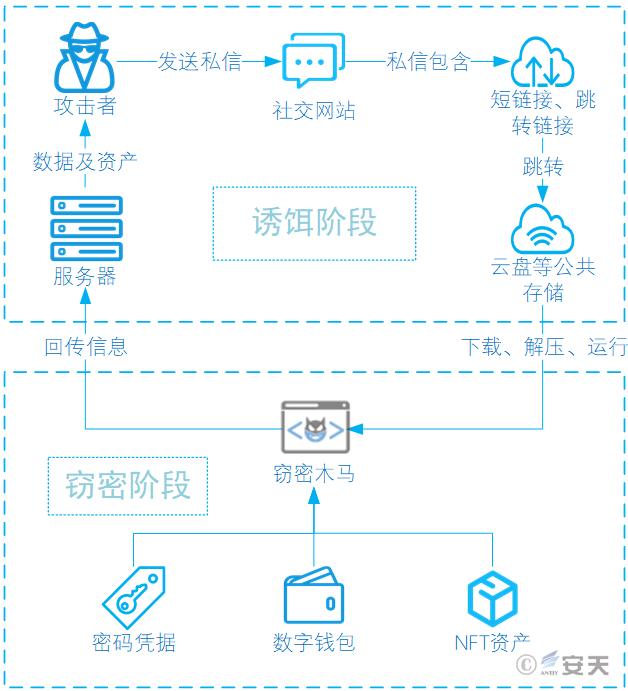
Figure 4-1 Attack flowchart
4.1 Disguised Mobile Game Development Company PlayMe Studio Staff
Attackers masqueraded as mobile game development company PlayMe Studio staff recruited and invited NFT artists to create characters for their mobile games.
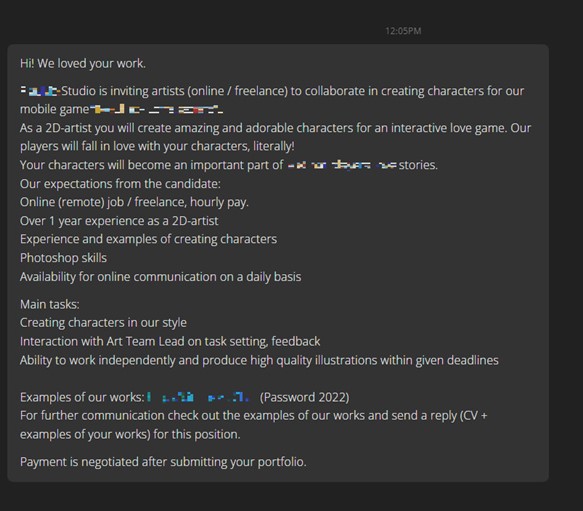
Figure 4-2 Disguised as mobile game development company PlayMe Studio to send recruitment information
The attacker sent a link to the victim, claiming it was a sample of their work. The link led to a download page on the file-sharing website MediaFire, where the download content was an encrypted compressed file.
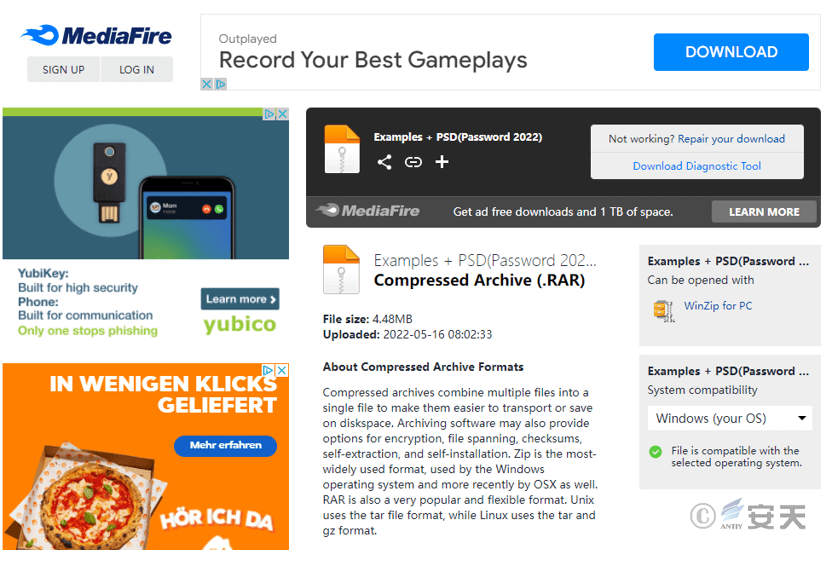
Figure 4-3 The link points to the MediaFire download page.
The contents of the compressed file include several PNG images as examples and two stealing Trojans disguised as PNG images and PSD (Photoshop-specific format) files respectively.
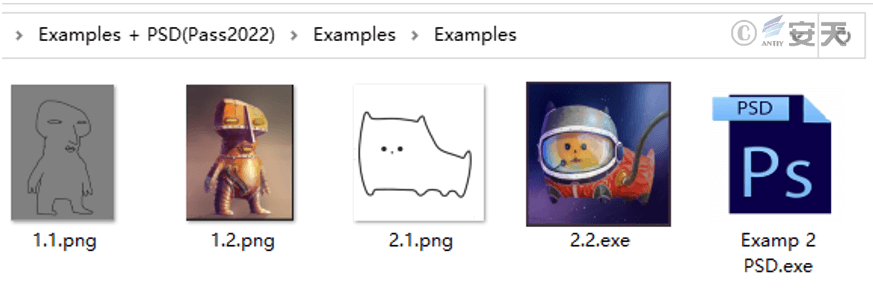
Figure 4-4 File contents in the compressed package
4.2 Disguised as a Staff Member of the NFT Project Disguised “Cyberpunk Ape Executive”
The attackers disguised themselves as staff members of the NFT project “Cyberpunk Ape Executive” and proposed cooperation to NFT artists and design a set of new characters.
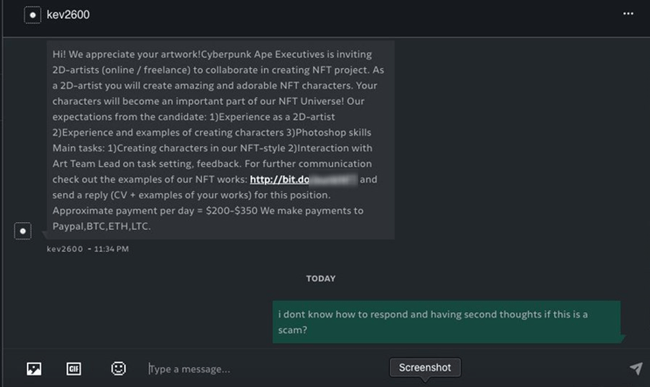
Figures 4-5 Disguised as mobile game development company PlayMe Studio to send cooperation information
The attacker also sent a short link to the victim under the pretext of a work example. The short link redirected to a MEGA download page. The download content was an encrypted compressed package containing multiple NFT works of the “Cyberpunk Ape Executive” project and a stealing Trojan disguised as a GIF image.
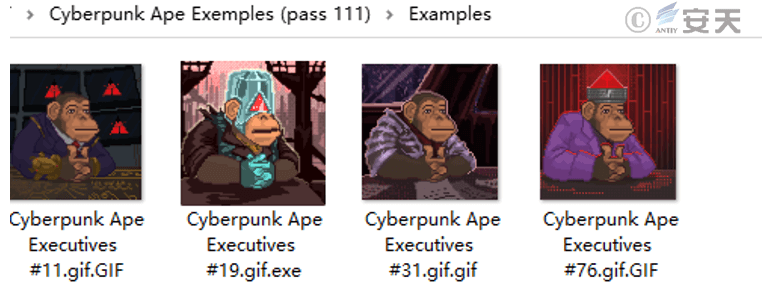
Figures 4 – 6 File contents in the compressed package
Over the past month, attackers have been constantly changing their packer protection techniques while retaining the core functional payload, in an effort to evade detection by antivirus engines and security software. Antivirus engine detection results show that the detection rate of newly emerged samples is generally lower than that of older samples.
5.Sample Analysis
5.1 Sample Tags
Table 5‑1 Binary executable file
| Virus name | Trojan[Spy]/Win32. Stealer |
| Original file name | Cyberpunk Ape Executives #19.gif.exe |
| MD5 | C9403AC2AEEB66BDDBD5D181B84D61F5 |
| Processor architecture | Intel 386 or later, and compatibles |
| File size | 2.10 MB ( 2,202,624 bytes ) |
| File format | BinExecute/Microsoft.EXE[:X86] |
| Timestamp | 2022-05-04 17:51:47 UTC |
| Digital signature | None |
| Packer type | UPX |
| Compiled language | Golang |
| VT first upload time | 2022-05-05 01:01:00 UTC |
| VT test results | 36/69 |
5.2 Sample Analysis
After the sample is executed, the payload and shellcode are decrypted in memory.
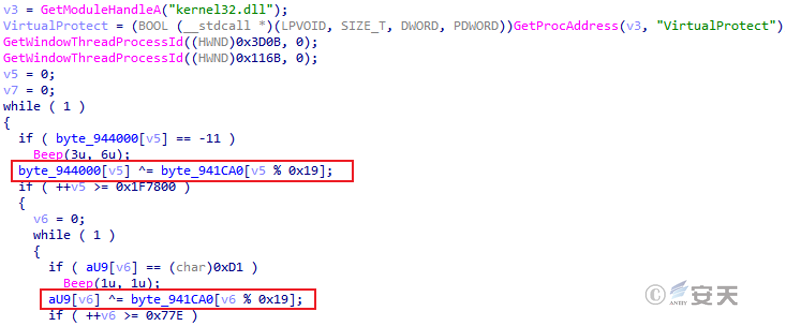
Figure 5-1 Decrypted payload and Shellcode
The Shellcode function is to create a RegSvcs.exe process and inject the decrypted payload into the process.
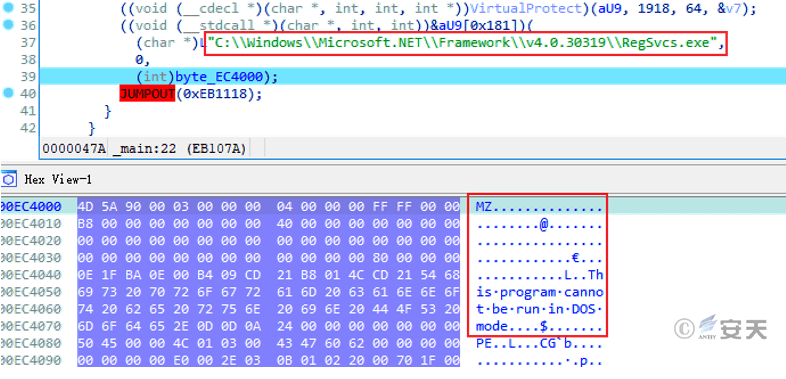
Figure 5-2 Hollowing out the malicious payload injected into RegSvcs.exe
The malicious payload is a data-stealing Trojan written in Go language and compressed using the UPX shell. After execution, it will automatically collect the computer’s system information, browser data, e-wallet, NFT manager, password manager and other software data.
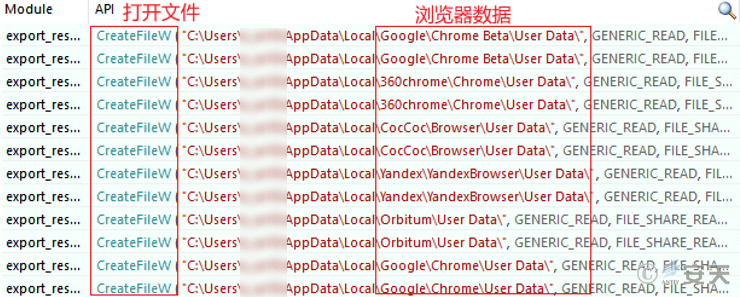
Figure 5-3 Collect data
Some of the software that suffered data theft are shown in the table below, including several browser plug-ins and digital wallet clients used to manage NFT artworks.
Table 5‑2 Some software that has suffered data theft
| Browser | 360chrome | Brave | Chrome | Chrome Beta |
| Chromium | CocCoc | Comodo Dragon | Edge | |
| Firefox | Maxthon | Maxthon | Opera | |
| Orbitum | QQBrowser | Vivaldi | Vivaldi | |
| Yandex | ||||
| Browser plug-ins | Binance | CerbyMask | CLV | Coin98 |
| Coinbase | Crust | Finnie | Goby | |
| Guarda | Hashpack | Hiro | ICONex | |
| Infinity | Jaxx Liberty | Kardia Chain | Keplr | |
| Liquality | Maiar DeFi | Math Wallet | Meta | |
| MetaMask | MEW CX | MOBOX | Monsta | |
| Nabox | Nami | Nash | Oasis | |
| ONTO | Phantom | PIP | polkadot{.js} | |
| Rabby | Ronin | Sender | Slope | |
| Solflare | Solong | StarMask | TerraStation | |
| TronLink | WaykiMax | Wombat | XDEFI | |
| Yoroi | Zecrey | ZilPay | Authenticator | |
| E-wallet | 42-coin | Argentum | Armory | atomic |
| Bitcoin | bytecoin | Coinomi | com.liberty.jaxx | |
| Daedalus Mainnet | DashCore | Dogecoin | Electrum | |
| Ethereum | Exodus | Guarda | Litecoin | |
| Monero | polkadot-apps | Quarkcoin | RaptoreumCore | |
| Raven | TerracoinCore | TokenPocket | Zecwallet Lite | |
| Other | FileZilla | Minecraft | Discord | Discord PTB |
| Discord Canary | Steam | Telegram Desktop |
The stealing Trojan encrypts the data and sends it back to the attacker’s server 45.142.122.179:7777.
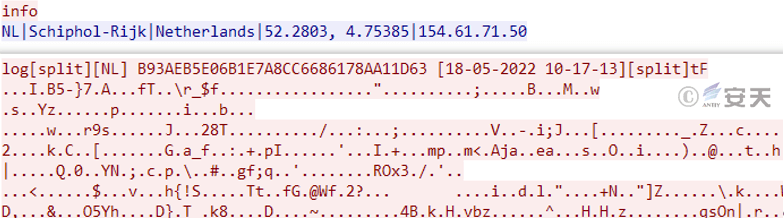
Figure 5-4 Return data
6.Summarize
In recent years, NFT transaction volume has steadily increased, and the NFT market has become increasingly popular. However, NFTs are still in their early stages of development, and many issues remain to be addressed. For example, due to the use of digital technologies such as blockchain, once an NFT is stolen, there is currently no way to recover it other than immediately locking and prohibiting trading. In fact, NFT holders are increasingly being targeted by attackers, and users should remain vigilant to avoid negligence that could allow criminals to exploit them.
Recent changes in the samples used by the attackers indicate they are employing various packer protection techniques to evade detection by antivirus engines and security software. Furthermore, the attackers are using stolen accounts and passwords to log into social media platforms and continue to distribute phishing messages to users on other platforms, thereby expanding their reach. This suggests that this theft activity will continue for some time to come. Users should remain vigilant against such attacks and avoid opening unidentified web links or downloading and executing suspicious files to avoid potential loss of digital assets.
Antiy CERT continues to follow up and analyze such incidents, focusing on the technical changes and characteristics of stealing Trojans, proposing corresponding solutions, and deploying corresponding defense capabilities into security products. Antiy IEP not only provides basic functions such as virus detection and active defense, but also provides enhanced capabilities such as terminal control and network control, which can effectively defend against such threats and ensure the security of user data.
7.IoCs
| 9B472A7F4E7B7DE1D5CE9049F400EFBB |
| D2233AA3AC1490968F62A9C9D55E9D36 |
| A592073C9AA063756605EF0EAF0AC289 |
| BDD239862D7F615C5EB709EF5C5E282F |
| EF47843068F3005F3ACD454C9BEE744F |
| 02D9EEE4BE3E1A41037222E3F43662AB |
| 667710059ECCD9C23880AACDFD0DB5ED |
| 260F44E2632DDA4C511F3B4DFEB58AD8 |
| FD4B860F4504C6A92B80E42AFA8BD525 |
| 1A08486FDF53F0F6A1A2781045570E73 |
| CD5E45337B22986033EBE4553C242FAF |
| 70161EB7087936D92D9762A8A5F99FF1 |
| 01C77CDD4DB48A2FDB976A8D79343D5C |
| 75D03DE5C50EA9E54654A229CFBC5827 |
| 3CAEEB9E025BFFF2215D84CD25E26187 |
| DA0F3222B92E10A24546FA7B266F2A0B |
| F1F83A9CE9A0227DDBC8FBF31B16589B |
| A818170717263831D6E42AC54DD07183 |
| 9A3439E9A4DC5962C9EC4411BD30AB16 |
| E05E73FB5D9DF18317DA096C65F5554E |
| 4330BDA7F122DBC0A4917AE48A4F3457 |
| FC1982DB2F536F0D4B7C2B50E4A385A1 |
| ADB3E6C596FC36B8D89AFFE0CE68614E |
| 498E68AC36E7A7CA8BF032E3549861E9 |
| AC74EA4EE583202166C1EED9A5381A9A |
| 61EB4ABCB5D7224EA7A17AB24A628EAC |
| 674543B35C33EE2343E09F1672F90F3C |
| C9403AC2AEEB66BDDBD5D181B84D61F5 |
| 5D5A9401C57AE158076D8FAB2418B174 |
| 93BB6CC0EF8C7FB729B0BF0D67C96989 |
| 154182A094041880D0757B65804FE6CC |
| 50EE952A73A2612084D266D46E59F9D6 |
| 22BF1AABA120FD55BA1D9C3D316DBF30 |
| 41AE1344A5D3BB23117A81047A593BD2 |
| 8925177864A9112A42B3117750C07781 |
| CF997C7D4BB2023A28AFB81BC5B43529 |
| F0DF194AC8E5100B9C05A8B7C97CF634 |
| 81A966F3211871E76BE12C05279C23AD |
| 035B2F18376C3067F7789160C2A9EBD4 |
| C4FFCDF45DBFF50DAC01947063B8D4FE |
| 4773C61E1AF41892874B559C9A6F597F |
| 45.142.122.179:7777 |
Appendix 1: References
- NFT (Non-Fungible Token)
https://baike.baidu.com/item/NFT/56358612
Appendix 2: About Antiy
Antiy is committed to enhancing the network security defense capabilities of its customers and effectively responding to security threats. Through more than 20 years of independent research and development, Antiy has developed technological leadership in areas such as threat detection engines, advanced threat countermeasures, and large-scale threat automation analysis.
Antiy has developed IEP (Intelligent Endpoint Protection System) security product family for PC, server and other system environments, as well as UWP (Unified Workload Protect) security products for cloud hosts, container and other system environments, providing system security capabilities including endpoint antivirus, endpoint protection (EPP), endpoint detection and response (EDR), and Cloud Workload Protection Platform (CWPP) , etc. Antiy has established a closed-loop product system of threat countermeasures based on its threat intelligence and threat detection capabilities, achieving perception, retardation, blocking and presentation of the advanced threats through products such as the Persistent Threat Detection System (PTD), Persistent Threat Analysis System (PTA), Attack Capture System (ACS), and TDS. For web and business security scenarios, Antiy has launched the PTF Next-generation Web Application and API Protection System (WAAP) and SCS Code Security Detection System to help customers shift their security capabilities to the left in the DevOps process. At the same time, it has developed four major kinds of security service: network attack and defense logic deduction, in-depth threat hunting, security threat inspection, and regular security operations. Through the Threat Confrontation Operation Platform (XDR), multiple security products and services are integrated to effectively support the upgrade of comprehensive threat confrontation capabilities.
Antiy provides comprehensive security solutions for clients with high security requirements, including network and information authorities, military forces, ministries, confidential industries, and critical information infrastructure. Antiy has participated in the security work of major national political and social events since 2005 and has won honors such as the Outstanding Contribution Award and Advanced Security Group. Since 2015, Antiy’s products and services have provided security support for major spaceflight missions including manned spaceflight, lunar exploration, and space station docking, as well as significant missions such as the maiden flight of large aircraft, escort of main force ships, and Antarctic scientific research. We have received several thank-you letters from relevant departments.
Antiy is a core enabler of the global fundamental security supply chain. Nearly a hundred of the world’s leading security and IT enterprises have chosen Antiy as their partner of detection capability. At present, Antiy’s threat detection engine provides security detection capabilities for over 1.3 million network devices and over 3 billion smart terminal devices worldwide, which has become a “national-level” engine. As of now, Antiy has filed 1,877 patents in the field of cybersecurity and obtained 936 patents. It has been awarded the title of National Intellectual Property Advantage Enterprise and the 17th (2015) China Patent Excellence Award.
Antiy is an important enterprise node in China emergency response system and has provided early warning and comprehensive emergency response in major security threats and virus outbreaks such as “Code Red”, “Dvldr”, “Heartbleed”, “Bash Shellcode” and “WannaCry”. Antiy conducts continuous monitoring and in-depth analysis against dozens of advanced cyberspce threat actors (APT groups) such as “Equation”, “White Elephant”, “Lotus” and “Greenspot” and their attack actions, assisting customers to form effective protection when the enemy situation is accurately predicted.


