Antiy Conducted a Correlation and Attribution Analysis on the 0day Ransomware Attack on Chanjet, and Provided Product Solution
The original report is in Chinese, and this version is an AI-translated edition.
The 0day vulnerability of Chanjet + software is used by the attacking organizations to carry out extortion attacks, which causes great social impact. Antiy actively follows up and supports the work of the competent department, and provides technical support in event and sample analysis, vulnerability mechanism recurrence and other work. According to the detailed association analysis of the event, the CERT named it “Magic Flute Organization” according to the attack method, tool information and the string “mdzz” in the domain name used, and provided the product solution.
1.Overview
Recently, the 0day vulnerability of Chanjet + software was used by the “Magic Flute” hacker organization to carry out blackmail attacks, causing greater social impact. Antiy actively follows up and supports the work of the competent department, provides technical support for events, sample analysis and recovery of vulnerability mechanism, and reports relevant product vulnerabilities. At the same time, we will assist customers in checking software assets, and test the effectiveness of AVL SDK anti-virus engine, IEP cloud host protection, IEP endpoint protection, and Qingzhu WAF against threats at the first time. Quickly deploy rules and upgrade capabilities to help customers take preventive measures.
Antiy CERT uses the string “mdzz” in the domain name for the history of the attack organization, naming the attack group “Magic Flute Organization.” Antiy CERT uses the TID threat intelligence platform to conduct comprehensive research and judgment. This attack is connected in parallel with attacks such as the launch of mining virus in 2019, the launch of RAT Trojan horse using Eternal Blue vulnerability, and the violent attack based on MSSQL in 2020. And provides a comprehensive solution including cloud host protection, endpoint protection, application firewall and other products.
The attacker takes advantage of any file upload vulnerability and uploads the back door to the Chanjet Web service back end specific path. When the back door receives the HTTP request of “/ Load.aspx” path, the AES algorithm is used to decrypt the remote code in the request content and load it for execution, and the Web service port of Chanjet + can be accessed remotely without authorization. To realize the attack purpose of encrypted blackmail. According to the encrypted file suffix, ransom amount, ransom note and other related information, it is inferred that the ransomware used by the attacker belongs to the Tellyouthepass ransomware family. The ransomware uses “AES + RSA” encryption algorithm, adds the suffix of “.locked” after the original file to be encrypted, and creates a ransom note named “READ _ ME.html” under the desktop and all paths containing the encrypted file. A ransom of 0.2 BTC was demanded from the victim.
An analysis of the IoC of the incident by the Antiy CERT using the Antiy Threat Intelligence Integrated Analysis Platform uncovered the organization’s historical activities as well as more IoCs used for this event. Combined with the attacking method, attacking technology, tool information and attacking purpose of the organization, it is presumed that the organization is a black organization from the country. In historical activities, the group mainly mines attacks to seek money for the purpose of attacking, mainly using Gh0st remote control to control the target, and good at using all kinds of hacking tools, Antiy named the organization “Magic Flute.” As a result of online related information tracing show, as there have been attackers selling some domestic enterprises SaaS service attack entrance information. Therefore, in this attack, there may be cooperation between the upstream and the downstream, and it is not excluded that the “Magic Flute” hacker organization may have learned / purchased the vulnerability and utilization mode of Chanjet T + from other attackers or attack organizations. As well as the existence of vulnerability of the host list and other information, and according to this launch blackmail program for attack.
The verified ransomware protection module of the Antiy EPP, without an upgrade, It can still effectively prevent the encryption of the Tellyouthepass ransomware launched by the attacker, and the cloud host security system (CWPP) of Antiy IEP can detect threats from the dimensions of assets and vulnerabilities. It can effectively reinforce servers, cloud hosts and containers, and improve the threat awareness of SaaS-based software. The user can upgrade to the latest version of the rule base to detect and prevent corresponding threats; the WAF application has certain broad-spectrum capability to intercept any file uploading vulnerability and malicious shellcode loading. Users can upgrade to the latest version of the rule base, even if the Chanjet software is not upgraded to the latest patch, by deploying Antiy Qingzhu Firewall at the front end of the server, relevant vulnerabilities can be intercepted.
2.ATT&CK Mapping Map of Event
The ATT&CK mapping map corresponding to this attack event is sorted by the SMS CERT, as shown in the figure below:

Figure 2-1 Mapping of Technical Features to ATT&CK
The technical points used by the attacker in this incident are shown in the following table:
Table 2-1 ATT&CK Technical Behavior Description Table
| ATT&CK stages / categories | Specific behavior | Notes |
| Resource development | Access to infrastructure | Gets the C2 server |
| Environmental preparation | Build C2 environment | |
| Initial access | Use of external remote services | Take advantage of the public Web service |
| Execution | Implement by exploit host computer software vulnerability | Exploit vulnerabilities to execute |
| Right to Submission | Taking advantage of loopholes to grant rights | Taking advantage of loopholes to grant rights |
| Defensive evasion | Anti-obfuscate / decode files or information | Decryption payload |
| Concealment | Back-office execution | |
| Confusion of documents or information | Encryption payload | |
| Findings | Find files and directories | Find the file to be encrypted |
| Impact | Data encryption with adverse effects | To encrypt the data |
3.Analysis of vulnerability mechanism
Chanjet + is an Internet-based business management software to help enterprises improve office efficiency. By repeating the attack link, it is confirmed that the attacker takes advantage of any file upload vulnerability existing in Chang Jitong +. The vulnerability allows an unauthenticated remote attacker to execute arbitrary code by constructing a specific request to upload a malicious file (such as a WebShell) to the target system. The scope of influence of the vulnerability is Chanjet + < = v17.0.
The cause of the vulnerability is that the Upload .aspx file is insufficient to verify the content uploaded by the user, and the attacker can use this method to bypass the authority authentication directly, thus realizing arbitrary file upload. Antiy CERT has reproduced the vulnerability, the specific use of the details are temporarily not public.
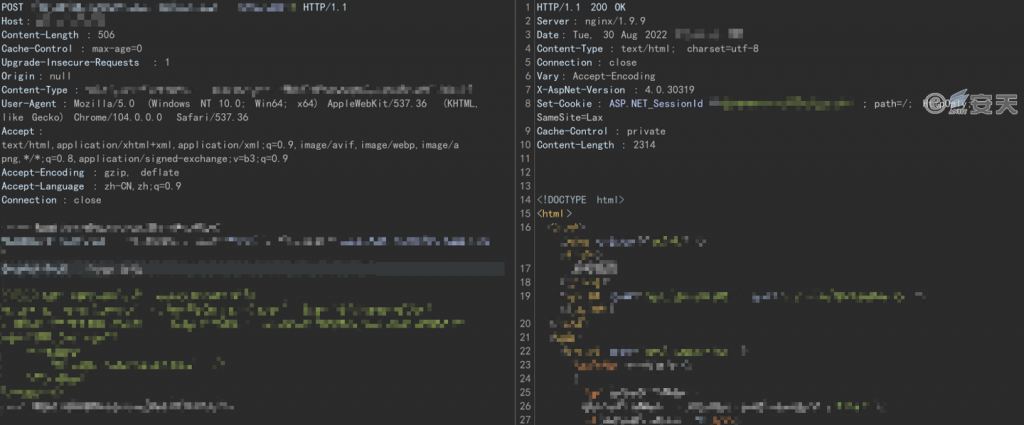
Figure 3-1 Vulnerability recurrence
4.Sample analysis
4.1 Sample labels
Table 4-1 Binary executable file ‑
| Virus name | Trojan [Backdoor] / Win32.loader |
| Original file name | App _ Web _ load.aspx.cdcab7d2.dll |
| Md5 | 45625d6092a287284cd71af690c5c393 |
| Processor architecture | Intel 386 or later, and compatibles |
| File size | 5.50 KB (5632 bytes) |
| File format | Binexecute / Microsoft.EXE [: X86] |
| Time stamp | 2022-08-27 14: 51: 15 UTC |
| Digital signature | None |
| Shell type | None |
| Compiled Language | Asp.net |
| Vt First Upload Time | 2022-08-29 13: 23: 16 UTC |
| Vt test result | 13 / 68 |
4.2 Detailed analysis
Listens to the HTTP request path “/ Load.aspx,” and passes the corresponding request to the Load.aspx module for processing.
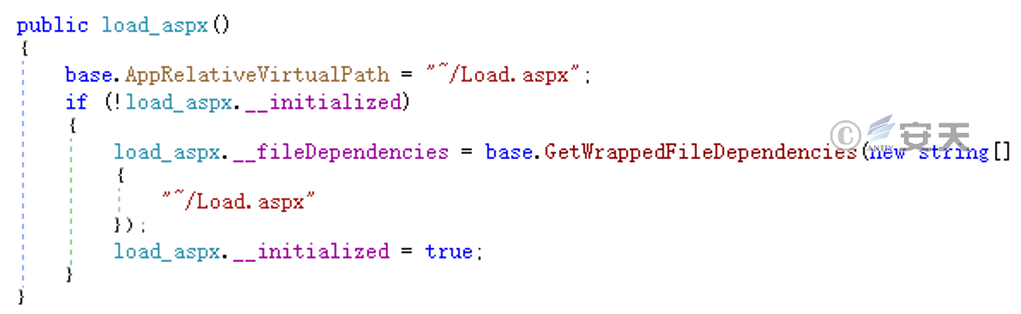
Figure 4-1 Loading the Load.aspx Module
The corresponding xml configuration file configures itself as a Load.aspx virtual path to process the above request.
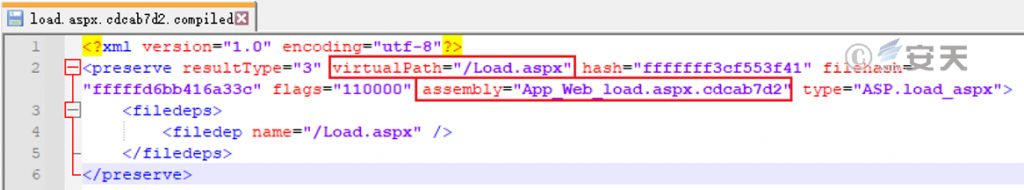
Figure 4-2 Configuration file
The handler decrypts the payload using the AES algorithm and loads it, creates an instance of a class with the class name “U,” and executes the code in the request.
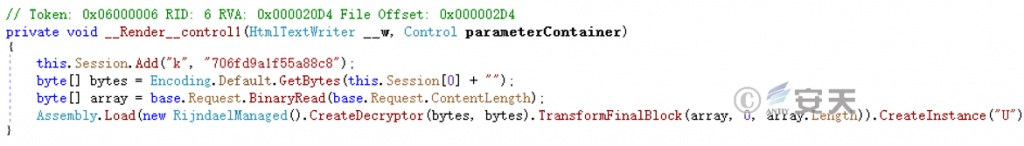
Figure 4-3 Decrypt the payload and loads execution
5.Correlation analysis
According to the attack domain name lllw0.com [3] disclosed in the tracking intrusion log of Friends, Antiy analyzed the IoC of the event based on the TID threat intelligence comprehensive analysis platform. Discover the organization’s historical activities as well as more IoCs used for this event. Combined with the attacking method, attacking technique, tool information and attacking purpose of the “Magic Flute” organization, it is inferred that the organization is a black organization from China. With the earliest C2 analysis currently linked, the organisation is likely to start its activities as early as 2017. In its historical activities, the group mainly used mining attacks for the purpose of seeking money, mainly used Gh0st remote control to control the target, and was good at using all kinds of hacking tools. In this attack activity, “magic flute” organization may know from somewhere the flaw of certain home-made financial software, use the past experience and resources to continue to launch the attack to put blackmail program to seek money.
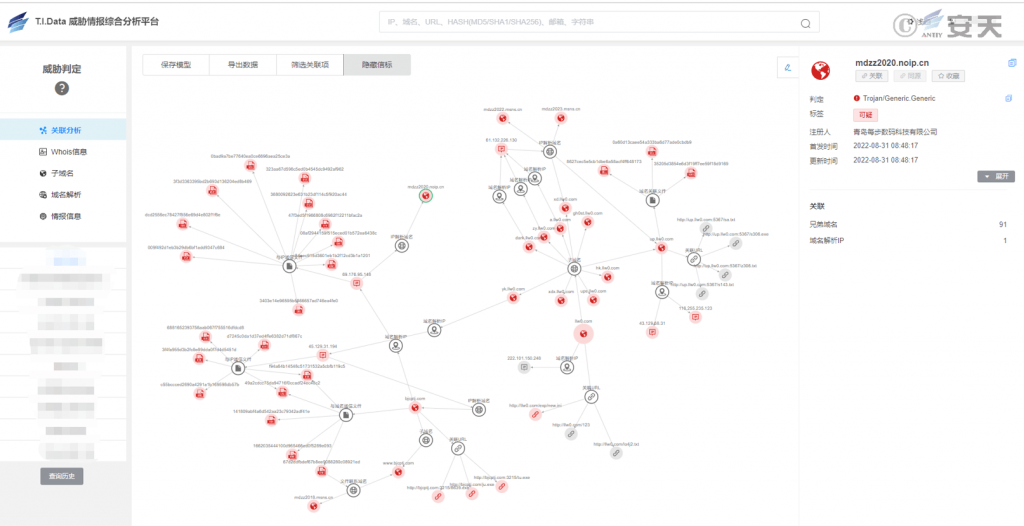
Figure 5-1 TID Threat Intelligence Comprehensive Analysis Platform ‑
The timeline of historical attacks of the organization based on association analysis is as follows:
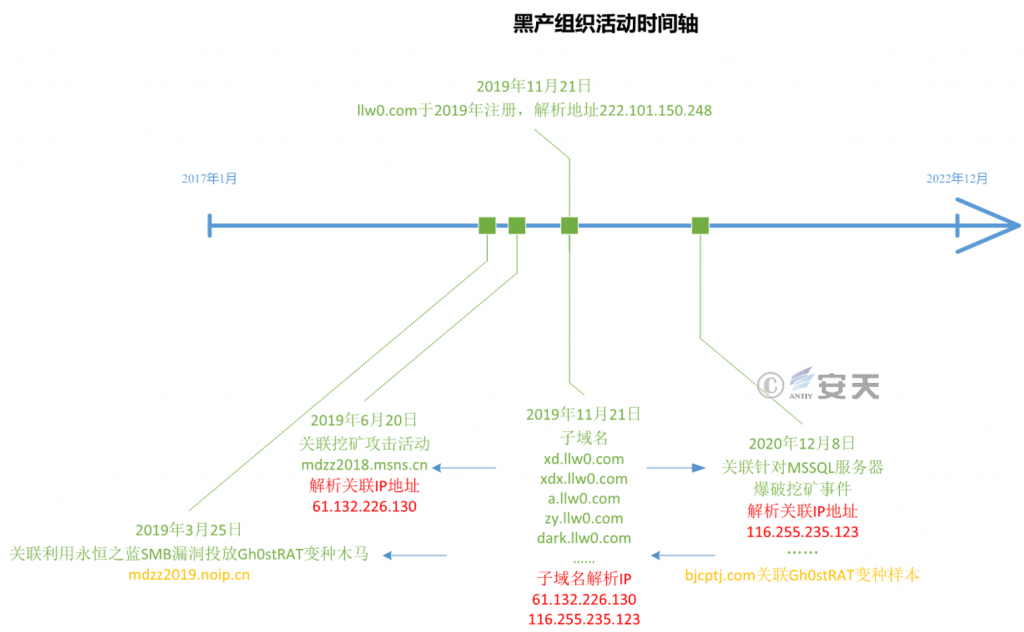
Figure 5-2 Timeline of the group’s historical attack activities
5.1 This blackmail incident domain name lllw0.com
The domain name llw0.com used for sample propagation was registered in 2019. the current resolution address is 222.101.150.248, and the IP is a virtual host according to the analysis of the domain name resolution.
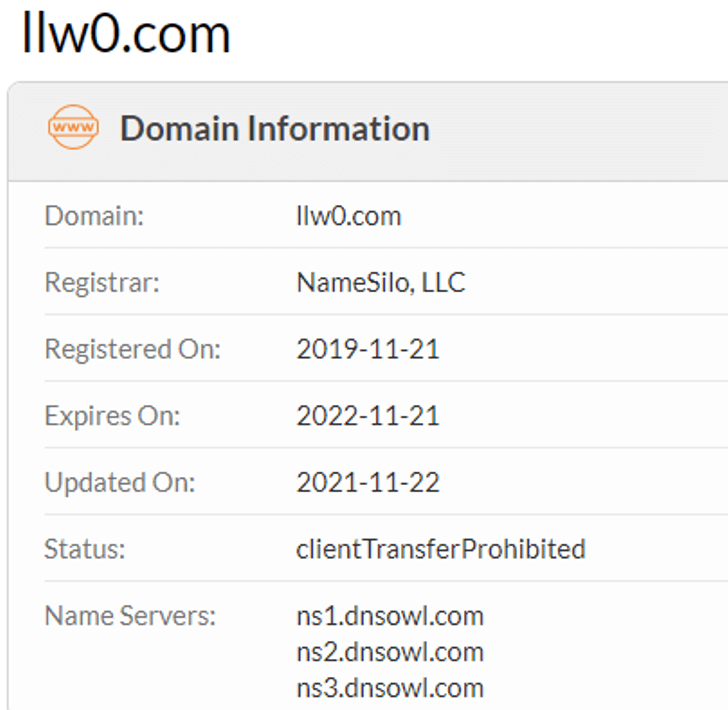
Figure 5-3 Llw0.com domain name registration information
This domain carries a large number of malicious files, mainly including Gh0st remote control Trojan horse, mining Trojan, ransomware and right-raising tools. According to the file name, the group may have used the log4j vulnerability to attack.
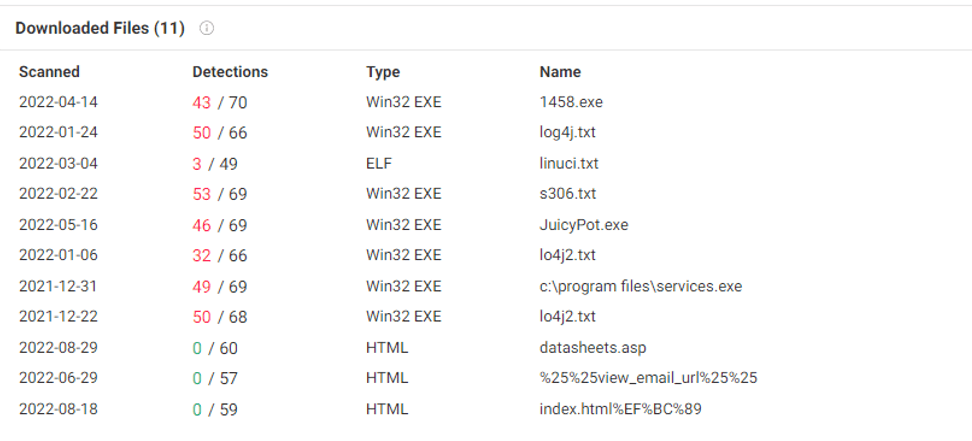
Figure 5-4 Domain name association information for lllw0.com
This domain has a large number of sub-domain names, of which the domain names xd.llw0.com and up.llw0.com have been resolved to two IP43.129.68.31 and 51.81.145.78, and two servers have directly attached with exploit payload (CVE-2017-0213) for download.
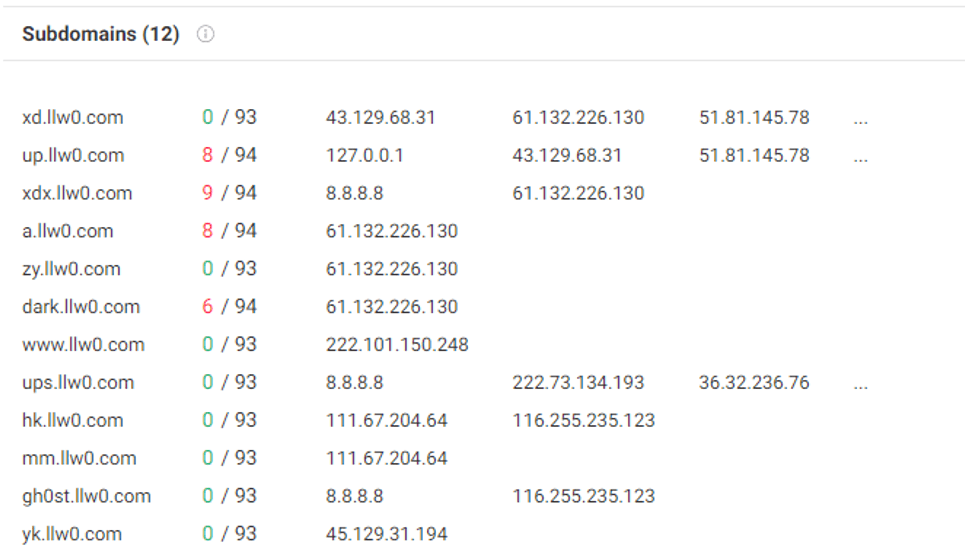
Figure 5-5 Llw0.com subdomain information ‑
5.2 Linked mining attacks in 2019
Multiple llw0 .com subdomain histories have resolved to 61.132.226.130, and the server is owned by the attacker. The mdzz2022.msns .cn and mdzz2023.msns .cn have also been resolved to this IP, and several Gh0st remote control Trojans communicate with two domain names, so the two domain names of mdzz are also likely to belong to this organization.
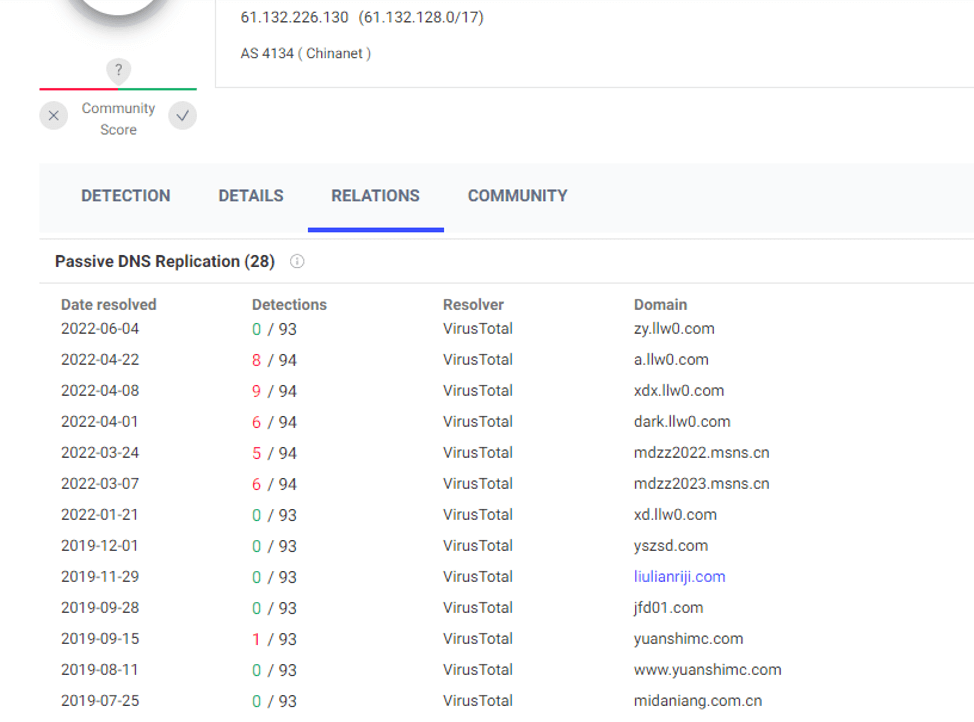
Figure 5-6 61.132.226.130 Related Information
In addition, when analyzing the two mdzz sub-domain names, it was found that its brother domain name mdzz2018.msns.cn appeared in relevant reports, and the attacks disclosed in the reports were also mining incidents. The domain related malicious code is also a large number of mining Trojan horse and Gh0st remote control, so the above mdzz related domain is likely to be the organization’s C2 assets.
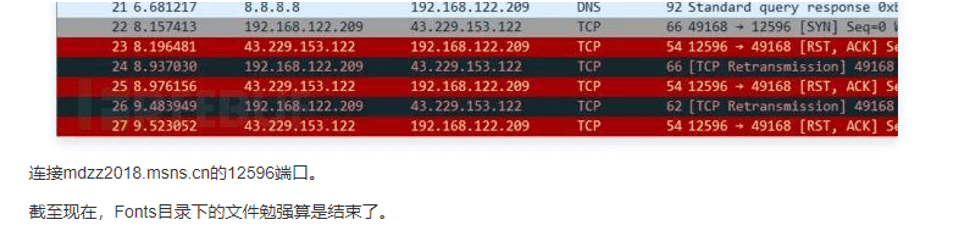
Figure 5-7 Public report mentions that the domain name mdzz2018. msns .cn is related to mining attacks
5.3 Related 2019 Using Eternal Blue SMB Vulnerability to Launch Gh0stRAT Mutant Trojan
Up.llw0.com subdomain was resolved to 61.183.237.30 in July 2020, and mdzz2020.noip.cn was resolved to 61.183.237.30 in August of the same year. Mdz2020.noip.cn related files are also mostly remote control Trojans, combined with the last section of MDZ.2020.noip.cn domain name features, MDZ.2020.noip.cn is likely to be the same attack organization assets.
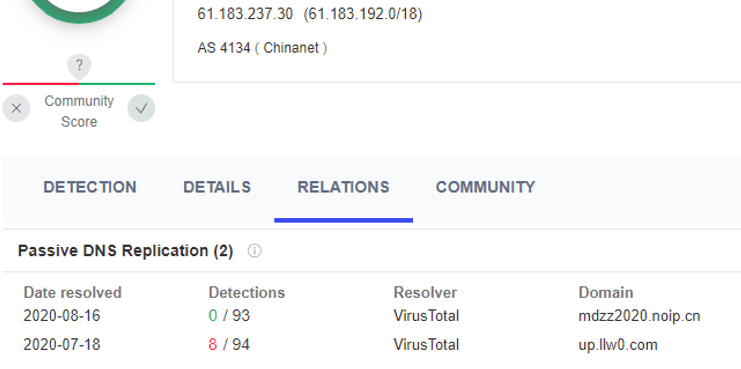
Figure 5-8 Resolution domain name of 61.183.237.30 IP
Also analyzing the domain name of mdzz2020.noip.cn, we found that its brother domain name mdzz2019.noip.cn, which was disclosed by foreign security agencies in the 2019 analysis report, is the C2 address of the remote control of the variant Gh0st.
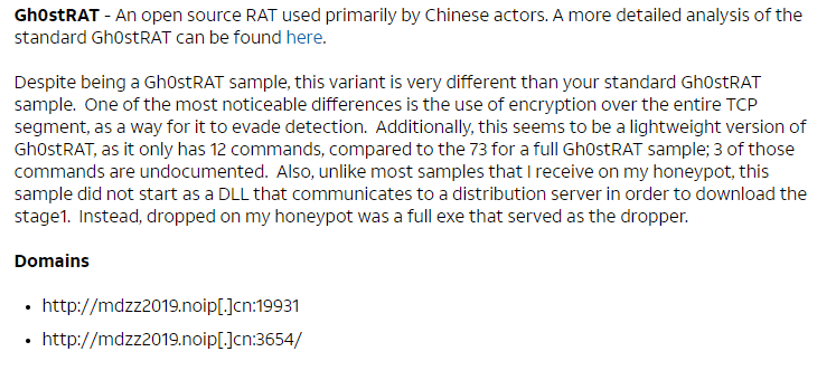
Figure 5-9 mdzz2019.noip.cn was disclosed to be C2 of variant Gh0st remote control
5.4 Associated with mine excavation events of MSSQL server blasting in 2020
Several llw0.com subdomains have also been resolved to 116.255.235.123, and a large number of related malicious codes communicate with the IP, and the address is owned by the attacker.
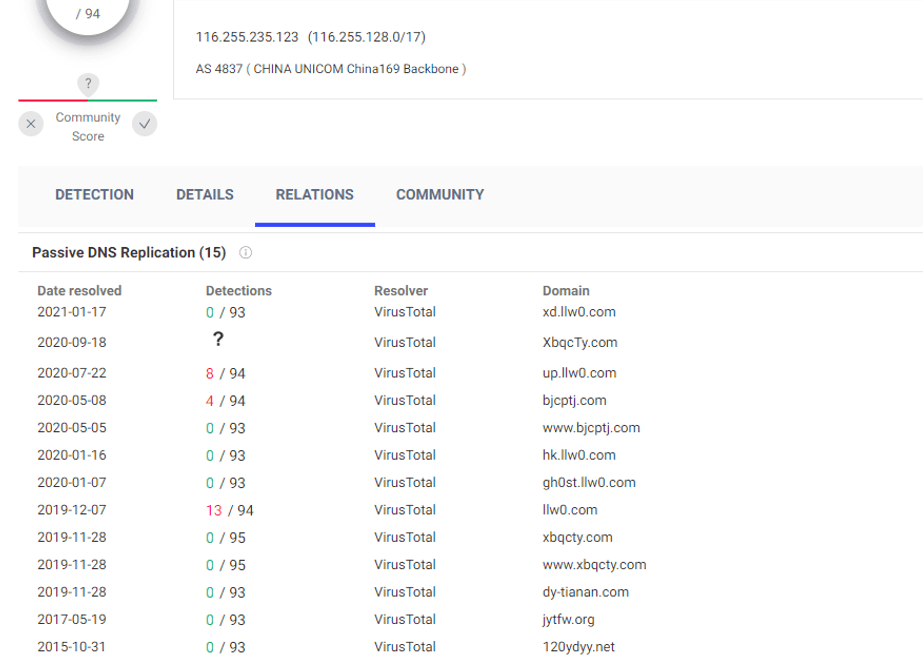
Figure 5-10 116.255.235.123 IP association information
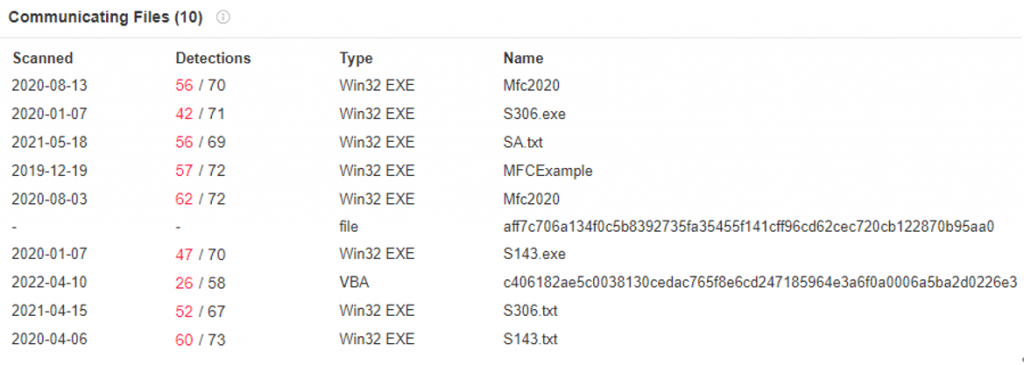
Figure 5-11 Malware of IP communication with 116.255.235.123
The IP resolves the domain name bjcptj.com in 2020 and the domain name is registered in 2021. In the domain name on the mount, with the domain name communication related malicious files many, most for the backdoor and the right tool.
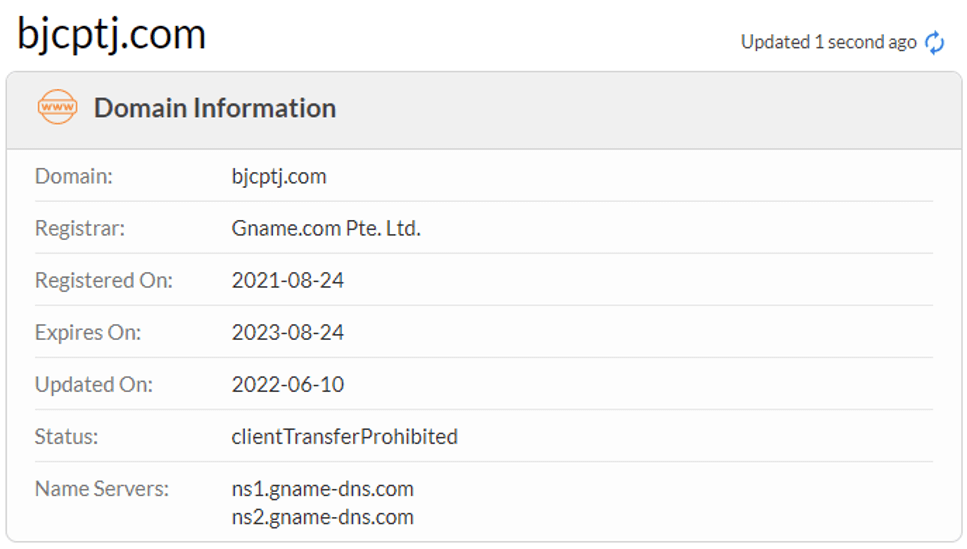
Figure 5-12 bjcptj.com domain name registration information
The domain name has been disclosed by the domestic security team in 2020, is aimed at MS SQL server blasting drop mining trojan C2.
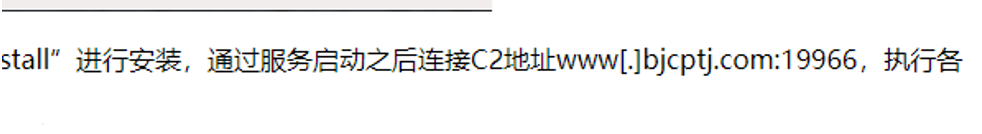
Figure 5-13 Public report disclosing that the domain name is related to a mining event ‑
6.Ransomware at a glance
Table 6-1 Overview of ransomware
| Time of occurrence | 2019 |
| Encryption algorithm | Aes + RSA |
| Encryption system | Windows, Linux |
| How to name encrypted files | Original file name +. Locked |
| Contact information | Contact the attacker via the email in the ransom note (service @ sunshinegirls.space) |
| Encrypted file type | Encrypt files in specified formats (specific formats include * .docx, * .doc, * .docm, * .pdf, * .xlsx, etc.) |
| Currency and amount of blackmail | 0.2 BTC (currently equivalent to RMB 27,439) |
| Whether it is targeted | Yes |
| Whether it can be declassified | No |
| Whether internal network propagation or not | No |
| Ransom note interface |  |
By looking up the Bitcoin address left by the attacker in the ransom note, it is possible that there are already compromised businesses that have paid the hacker a ransom.
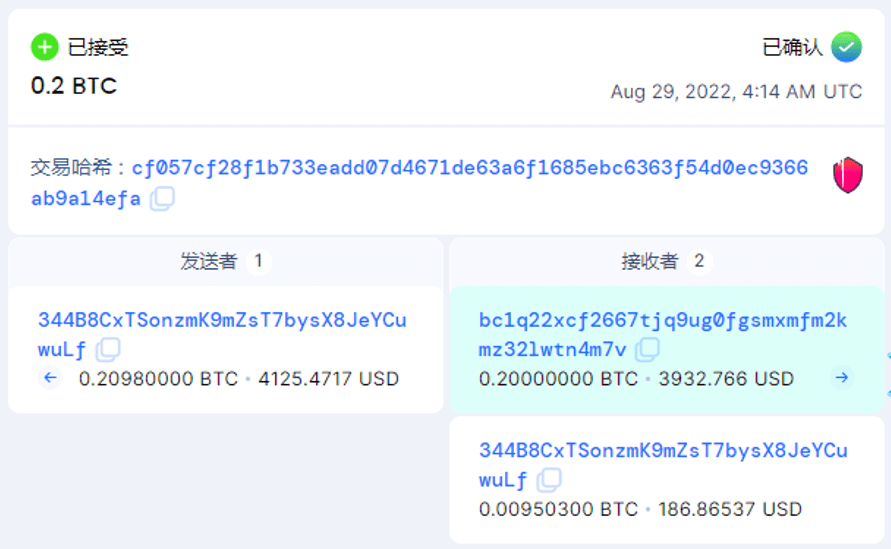
Figure 6-1 A ransom of 0.2btc has been paid by a victim
7.Corresponding measures and protection suggestions
7.1 Affected equipment
- The affected host shall be disconnected first to avoid expansion of the influence;
- If the local data file is not backed up, it is recommended to contact technical personnel to find out whether there is any backed up file;
- If the customer uses its own cloud server, the customer manager can first back up the image of the affected equipment through the management background, and then contact the technical staff to find out whether there is any backup file;
- Check whether the SQL database file is encrypted, if not, please back up as soon as possible;
- Check whether the backup files and mdf database files in zip format under the directory of “Chanjet\ TPlusStd\ DBServer\ data” are encrypted. if they are not encrypted, account creation can be redeployed, backup can be restored or database files can be restored;
- If both zip backup and database files are encrypted, you can find out whether there are other backup files;
- If that size of the partially encrypt file is 1K, it is possible that the encryption is not successful, in this case, it is possible to check whether the original file exist.
7.2 Unaffected equipment
- Check whether the automatic backup function is enabled for the current equipment, and if so, dump the backup files through mobile media, NAS, network disk and other methods;
- The official patch has been updated, please install the official bug patch in time, download the link below.
Https: / / www.chanjetvip.com / product / goods
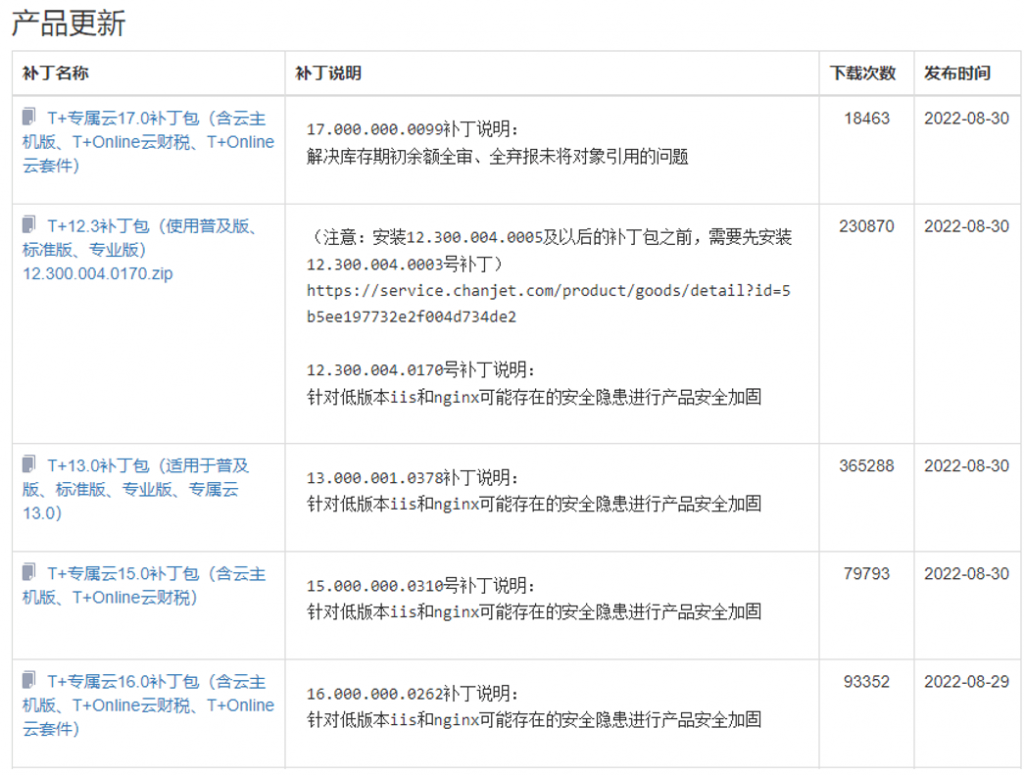
Figure 7-1 Chang Jitong T + official hole patch
8.Product protection
8.1 Atria’s terminal defense system
The Antiy IEP terminal defense system provides management personnel with unified management of intranet Windows, Linux and domestic terminals, and can display detailed information of threatening security events. Including asset information, document information, behavior event information, disposal result, etc. Security operation and maintenance personnel can use the management center to realize centralized viewing, analysis and handling of security events related to ransomware without terminal operation, which greatly improves the response speed of such events. And continuously improve the efficiency of safe operation and maintenance.
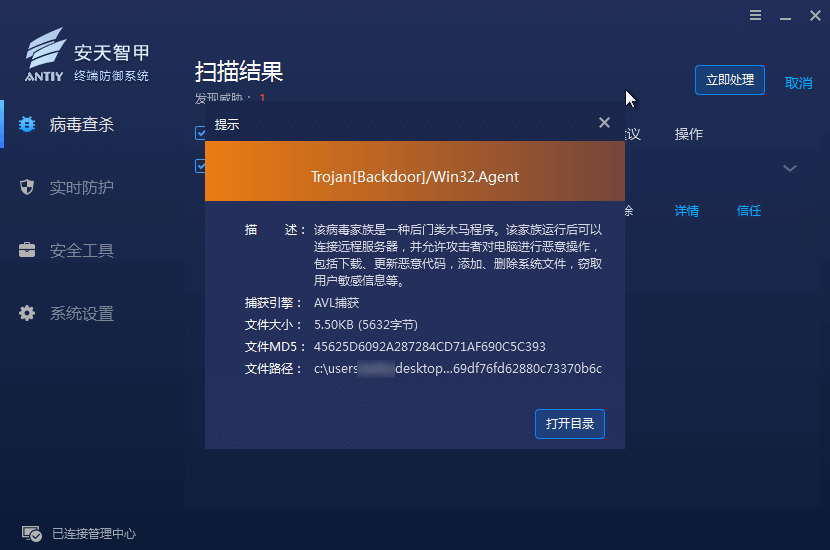
Figure 8-1 Antiy IEP Terminal Defense System – Scan Log
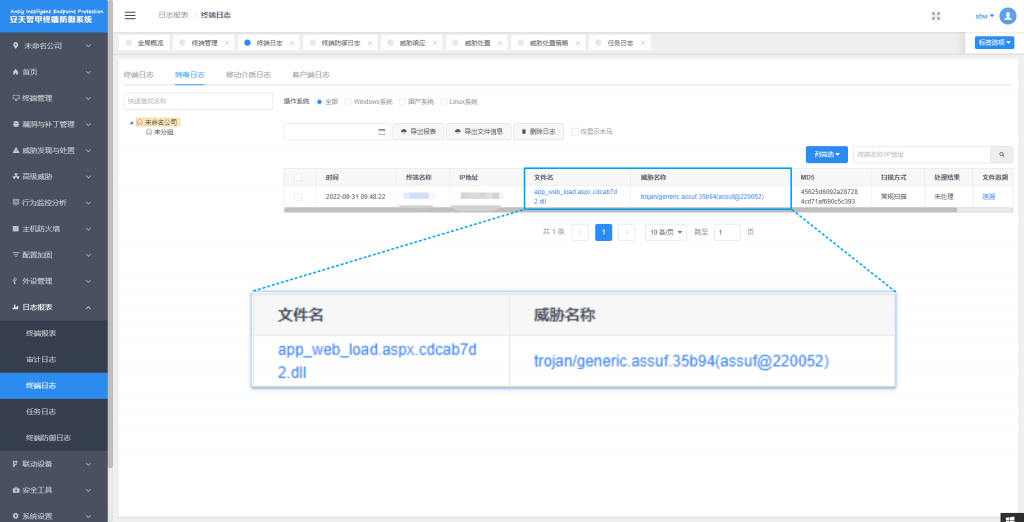
Figure 8-2 Antiy IEP Terminal Defense System – Terminal Log
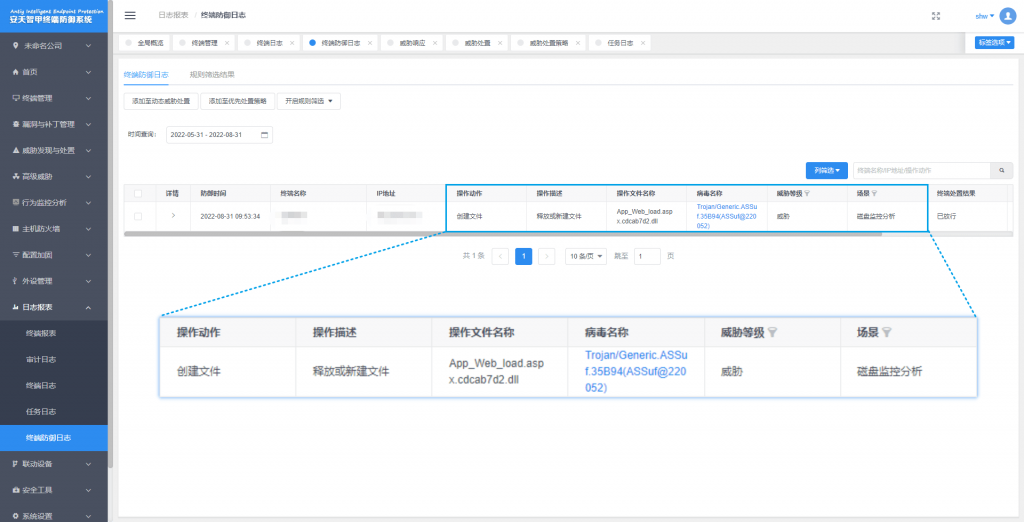
Figure 8-3 Antiy IEP Terminal Defense System – File Release Defense Log
8.2 Safety system of cloud host computer of Antiy IEP
The ATZ cloud host security system can scan the software application information (software name, version information and host view) through the asset inventory function and the vulnerability detection function to detect the information related to the 0day vulnerability (risk level). Vulnerability name, vulnerability type, risk characteristics, etc.).
Antiy IEP cloud host security system web interface – Asset Center – Windows host – All software applications – Asset View, where you can view information related to Chanjet + software.
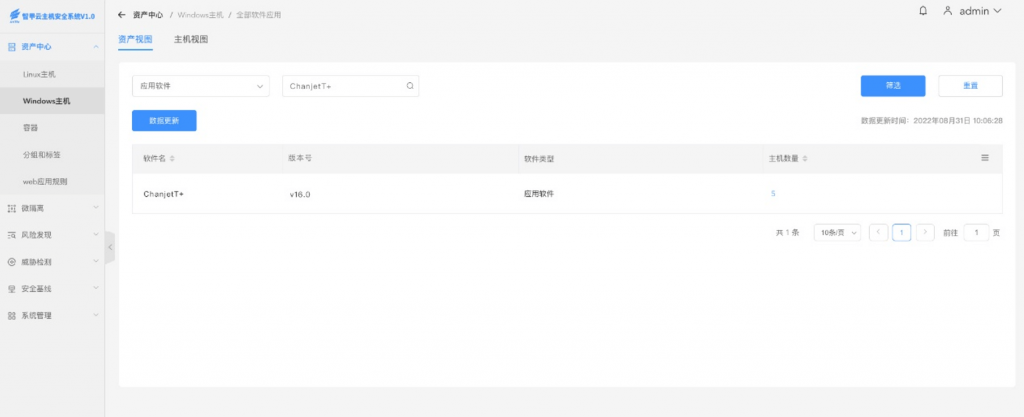
Figure 8-4 Asset Counting
Atis A cloud host security system web interface – risk discovery – vulnerability detection – risk view, you can view the information related to the 0day vulnerability.
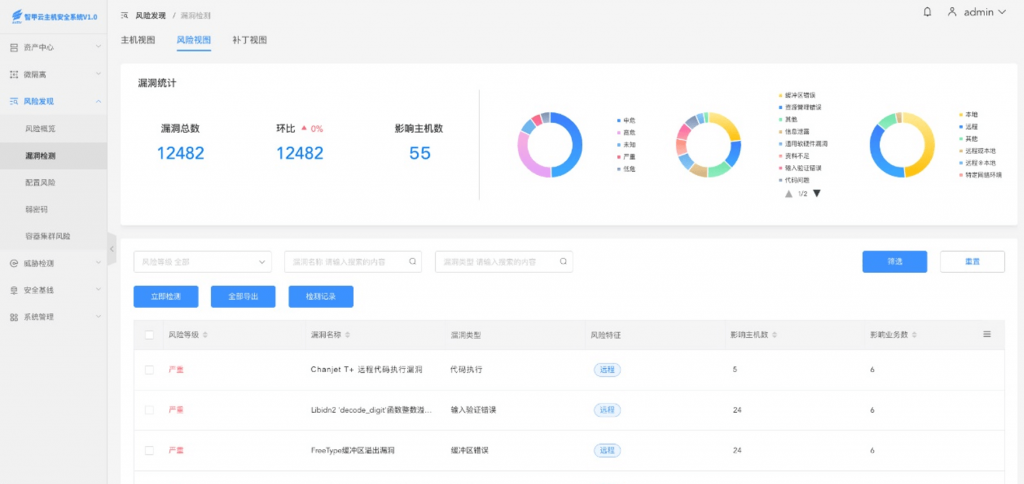
Figure 8-5 Vulnerability detection
8.3 Antiy Qingzhu WAF
The next generation Web application protection system of Antiy takes active defense as the security concept, overcomes the inherent deficiency of the traditional WAF passive protection, and starts from the security of users. Through the dynamic transformation and encapsulation of the key business and data of the user website, the security enhancement and reinforcement of the client running environment can not only effectively protect the vulnerability against attack, but also combine with the real-time man-machine identification technology. To effectively deal with the security threats associated with robots and upper-level services that are becoming more and more serious on the Internet.
8.3.1 Real-time upgrade of feature database
The feature database supports real-time upgrade online and manual upgrade offline. Through the online real-time upgrade function, the user’s characteristic database can be updated in time.
For users with network access restrictions, the WAF feature database may be upgraded by manual upgrade. For high-risk vulnerabilities, the WAF team will send an alert notice to users in a timely manner, and users can download the upgrade package and manually upgrade the vulnerabilities.
Figure 8-6 Manual uploading of upgrade package ‑
8.3.2 File upload protection
If the feature library cannot be upgraded, you can use WAF’s File Upload feature to intercept attacks.
The file uploading function of the WAF can check the file type, size and WebShell characteristics of the uploading. in the attack phase, the uploading environment of the user is basically only used for uploading pictures. The attack can be intercepted by setting up a whitelist of uploaded file types.
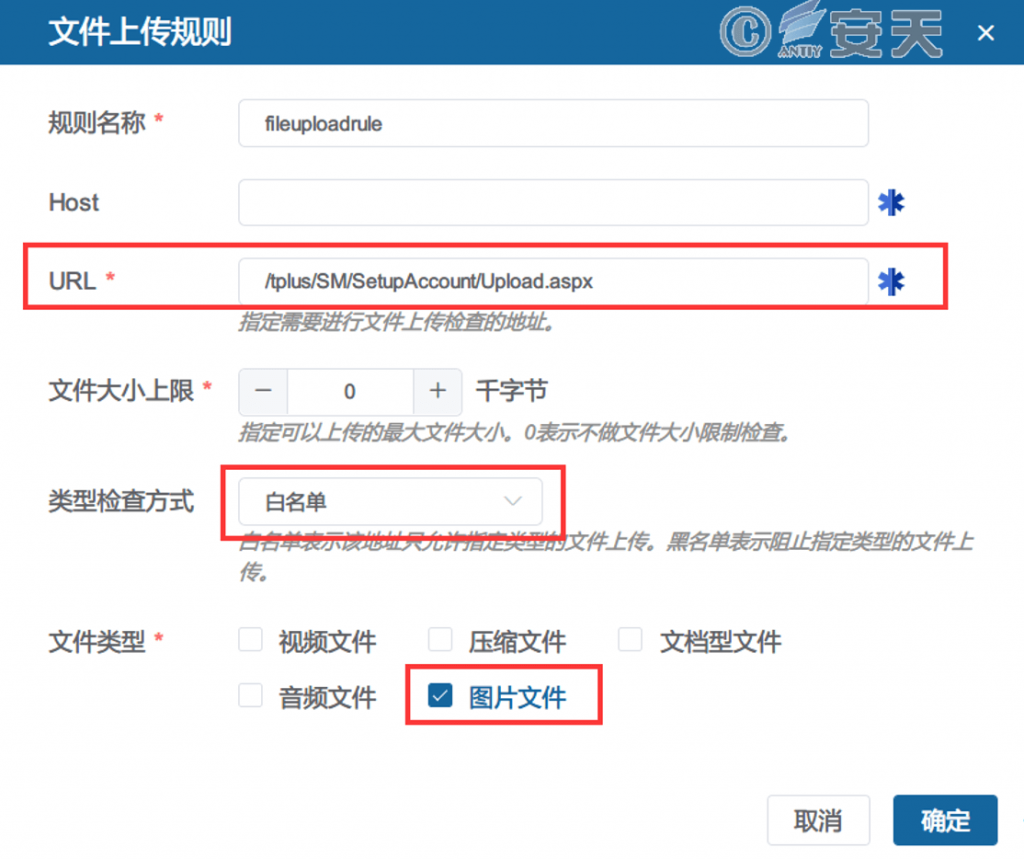
Figure 8-7 Set the white list of uploaded file types ‑
- Url: / tplus / SM / SetupAccount / Upload.aspx
- Type check method: White list
- File type: Picture file
8.3.3 URL access control
If a malicious file may have been populate because that feature library has not been upgraded or a file upload policy has not been effectively set, the threat can be mitigate by intercepting the upload path of shellcode.
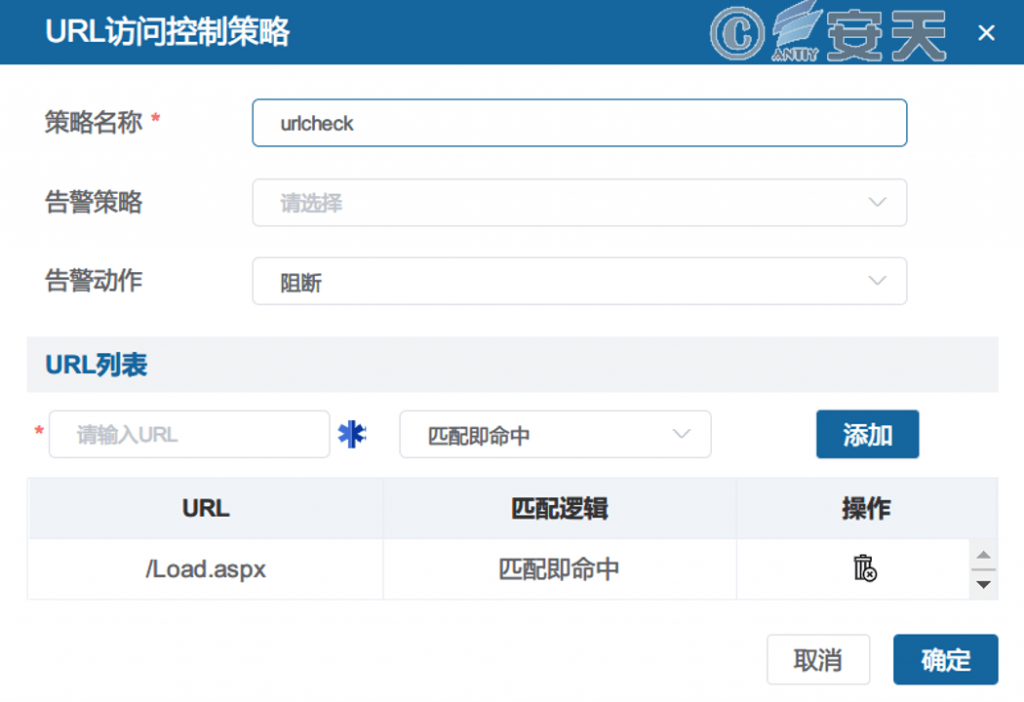
Figure 8-8 Upload path for intercepting shellcode ‑
9.IoCs
| 45625d6092a287284cd71af690c5c393 |
| 966a5a6b8054827e1462aa91ad2f7c |
| Bc1q22xcf2667tjq9ug0fgsmxmfmm2kmz32lwtn4m7v |
| Xd.llw0.com |
| Up.llw0.com |
| Xdx.lllw0.com |
| A.llw0.com |
| Zy.llw0.com |
| Dark.llw0.com |
| Mm.llw0.com |
| Hk.llw0.com |
| Yk.llw0.com |
| Ups.llw0.com |
| Gh0st.llw0.com |
| Mdzz2018.msns.cn |
| Mdzz2019.msns.cn |
| Mdzz2020.msns.cn |
| Mdzz2021.msns.cn |
| Mdzz2022.msns.cn |
| Mdzz2023.msns.cn |
| Mdz2019.noip.cn |
| Mdz2020.noip.cn |
| Bjcptj.com |
| 43.129.68.31 |
| 51.81.145.78 |
| 116.255.235.123 |
Appendix I: Reference
- Network security risk prompt about serious security vulnerability of Chang Jitong T + software resulting in hidden danger of blackmail attack
https: / / mp.weixin.qq.com / s / Y4sd7vwOGhe0S3XM5wgWw
- Antipyretic armour effectively protects the tellyouthepass ransomware
https: / / www.antiy.cn / research / notice & report / frontier _ tech / 2020243.html
https: / / mp.weixin.qq.com / s / Fw3IRSUbf1gS5EruR5Gjxw
- Note down a strange event found in emergency response
Https: / / cloud.tencent.com / developer / article / 1449219
- Watch out for BasedMiner Trojan horse blasting SQL weak password intrusion mining
https: / / s.tencent.com / research / report / 1052.html
- The odd case of a Gh0stRAT variant
https: / / cybersecurity.att.com / blogs / labs-research / the-odd-case-of-a-gh0strat-variant
Appendix II: About Antiy
Antiy is committed to enhancing the network security defense capabilities of its customers and effectively responding to security threats. Through more than 20 years of independent research and development, Antiy has developed technological leadership in areas such as threat detection engines, advanced threat countermeasures, and large-scale threat automation analysis.
Antiy has developed IEP (Intelligent Endpoint Protection System) security product family for PC, server and other system environments, as well as UWP (Unified Workload Protect) security products for cloud hosts, container and other system environments, providing system security capabilities including endpoint antivirus, endpoint protection (EPP), endpoint detection and response (EDR), and Cloud Workload Protection Platform (CWPP) , etc. Antiy has established a closed-loop product system of threat countermeasures based on its threat intelligence and threat detection capabilities, achieving perception, retardation, blocking and presentation of the advanced threats through products such as the Persistent Threat Detection System (PTD), Persistent Threat Analysis System (PTA), Attack Capture System (ACS), and TDS. For web and business security scenarios, Antiy has launched the PTF Next-generation Web Application and API Protection System (WAAP) and SCS Code Security Detection System to help customers shift their security capabilities to the left in the DevOps process. At the same time, it has developed four major kinds of security service: network attack and defense logic deduction, in-depth threat hunting, security threat inspection, and regular security operations. Through the Threat Confrontation Operation Platform (XDR), multiple security products and services are integrated to effectively support the upgrade of comprehensive threat confrontation capabilities.
Antiy provides comprehensive security solutions for clients with high security requirements, including network and information authorities, military forces, ministries, confidential industries, and critical information infrastructure. Antiy has participated in the security work of major national political and social events since 2005 and has won honors such as the Outstanding Contribution Award and Advanced Security Group. Since 2015, Antiy’s products and services have provided security support for major spaceflight missions including manned spaceflight, lunar exploration, and space station docking, as well as significant missions such as the maiden flight of large aircraft, escort of main force ships, and Antarctic scientific research. We have received several thank-you letters from relevant departments.
Antiy is a core enabler of the global fundamental security supply chain. Nearly a hundred of the world’s leading security and IT enterprises have chosen Antiy as their partner of detection capability. At present, Antiy’s threat detection engine provides security detection capabilities for over 1.3 million network devices and over 3 billion smart terminal devices worldwide, which has become a “national-level” engine. As of now, Antiy has filed 1,877 patents in the field of cybersecurity and obtained 936 patents. It has been awarded the title of National Intellectual Property Advantage Enterprise and the 17th (2015) China Patent Excellence Award.
Antiy is an important enterprise node in China emergency response system and has provided early warning and comprehensive emergency response in major security threats and virus outbreaks such as “Code Red”, “Dvldr”, “Heartbleed”, “Bash Shellcode” and “WannaCry”. Antiy conducts continuous monitoring and in-depth analysis against dozens of advanced cyberspce threat actors (APT groups) such as “Equation”, “White Elephant”, “Lotus” and “Greenspot” and their attack actions, assisting customers to form effective protection when the enemy situation is accurately predicted.


