Delete Such Files Immediately! Avoid Falling into the “SwimSnake” Trap
The original report is in Chinese, and this version is an AI-translated edition.
1.Overview
The “SwimSnake” cybercriminal group, also known as “Silver Fox” or “Valley Thief” by other security firms, primarily targets domestic users with attack and fraud campaigns. Antiy discovered and analyzed early activities of the SwimSnake group in the second half of 2022. These included disguising themselves as popular software download sites, poisoning search engine results through SEO manipulation, and mass-sending phishing emails for distribution. During payload execution, they frequently employed a “white and black” approach and further spread via instant messaging apps (WeChat, WeCom, etc.). Its main way of making profits is to defraud by creating groups through instant messaging software. At the same time, it also develops the ability to steal secrets from infected hosts and may engage in other activities such as data sales. The malicious files it spreads are characterized by a large number of variants and rapid iterations of anti-detection technologies. The attack targets involve a large number of individual users and multiple industry fields, posing a wide and serious threat.
The “SwimSnake” group likely operates under a Fraud-as-a-Service (FaaS) cybercrime model, commoditizing and offering attack methods, tools, and infrastructure for sale or lease to other criminals. This significantly lowers the barrier to entry for conducting cyber fraud.
The “SwimSnake” remote access Trojan is currently very rampant. Antiy CERT has been closely monitoring it. To help users promptly identify and prevent the “SwimSnake” remote access Trojan, this report focuses on the typical phenomena after infection and how to identify and prevent them.
Antiy Intelligent Endpoint Protection System (IEP) features enhanced download protection and supports control over the entry points of browsers, instant messaging software, and email clients. It can detect receiving and downloading behaviors, preventing malicious codes from easily landing on local disks or starting up. This ensures that the vast majority of malicious files are intercepted before loading and execution.
Detailed introduction to enhanced download protection: “IEP EDR’s “Enhanced Download Protection”: Halting the SwimSnake (Silver Fox) Threat.
2.Primary Phenomena, Identification and Hazards Following Infection with “SwimSnake”
The “SwimSnake” attack group mainly spreads malicious software through SEO poisoning by search engines and sending files via instant messaging software. Therefore, there are mainly two scenarios in which users are vulnerable to “SwimSnake” threats in their daily work and life:
- The first scenario: The victim, through search engines, finds phishing websites disguised as common software, downloads malicious software from them, installs and executes it, and then gets infected.
- The second scenario is when a victim has already been infected with the “SwimSnake” Trojan. After obtaining the system control authority, the “SwimSnake” group controls the victim’s host during idle time. Once it detects that a chat software is online, it will use the chat software’s group-creating function to create a group. After creating the group, it will spread false sensitive topics within the group to deploy the Trojan.
2.1 Hazards After Infection
After being infected with a Trojan, attackers usually carry out further spread and fraud. One way is to use the victim’s communication software group to spread the “SwimSnake” Trojan to control more hosts. The other way is to spread QR codes or phishing links to conduct phishing. If a member of the group clicks on the first situation, they themselves become a spreader of the “SwimSnake”. If they click on the phishing link, they may be defrauded and suffer financial losses.
In addition, attackers may also adopt more direct fraud methods: they can control the victim’s WeChat through remote access Trojans and disguise themselves as the victim to defraud their friends. Or control the victim’s WeChat to delete one of their friends, and then add another attacker’s WeChat ID with the same profile picture as that friend, thereby disguising themselves as a friend and defrauding the victim.
2.1.1 Spread the “SwimSnake” Trojan to Control More Hosts
Through WeChat chat records, it can be found that the victim spread the file “Information on Internally Disciplined Personnel in Q3 2025_“. This file is actually a sample related to the “SwimSnake” remote access Trojan. After execution, the attacker can use the remote access Trojan to remotely control the victim’s computer.
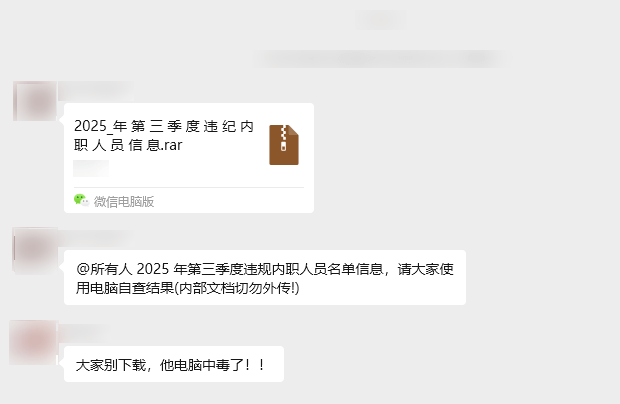
Figure 2‑1 Send Samples Related to the “SwimSnake” Trojan
- Common phishing tricks and file names
Some common phishing tactics are shown in the following table.
| Phishing Tactics | Examples |
| The attacker forges a file subject (such as personnel list, enterprise list, etc.) and sends a file with a name related to that subject (such as a compressed package or executable program, etc.). | 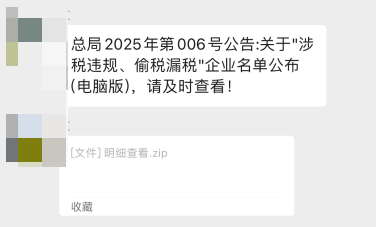 |
| Attackers may also not send text but directly send malicious files. | 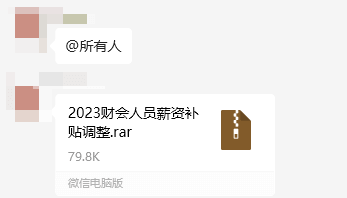 |
- Some common types and examples of malicious file names are shown in the following table.
| File Name Type | Examples |
| Name Format: [Date] _* Personnel List [May contain a long string of characters] | List of Internally Disciplined Personnel in Q2 2025 (11).txt.exedj List of Internally Disciplined Personnel in Q2 2025 adjia…(6).exehd Regarding List of Personnel Violating Rules and Discipline (202509) dsabr… (14).exeds List of Internally Disciplined Personnel in Q3 2025 nirotetmeoNFIWETQ (2).exe2025.09.10_ Personnel List nmcxnbnmcbskkdwjhejn511 (400).exe |
| Related to keywords such as “view” and “consult” | View Details.zipQuery Details.exeView After Unzipping.zipPlease Compress Before Viewing.zipView After Unzipping.zip |
| Disguised as policy documents or notice documents of the government or enterprises | Adjustment of Salary Subsidies for Financial and Accounting Staff.rarTax Adjustment for Taxpayers (Effective July).exeNotice on National Taxation and Enterprise Subsidy Policies.zipCompany-Wide Personnel Restructuring.rarDetails Regarding 2025 Employee Salary Adjustment.exe |
2.1.2 Spread QR Codes or Phishing Links to Carry out Phishing and Fraud
Attackers gain control of the victim’s WeChat account, mass-invite users to groups or, if the victim is already in a group, send a PDF phishing file accompanied by instructions and a phishing link.
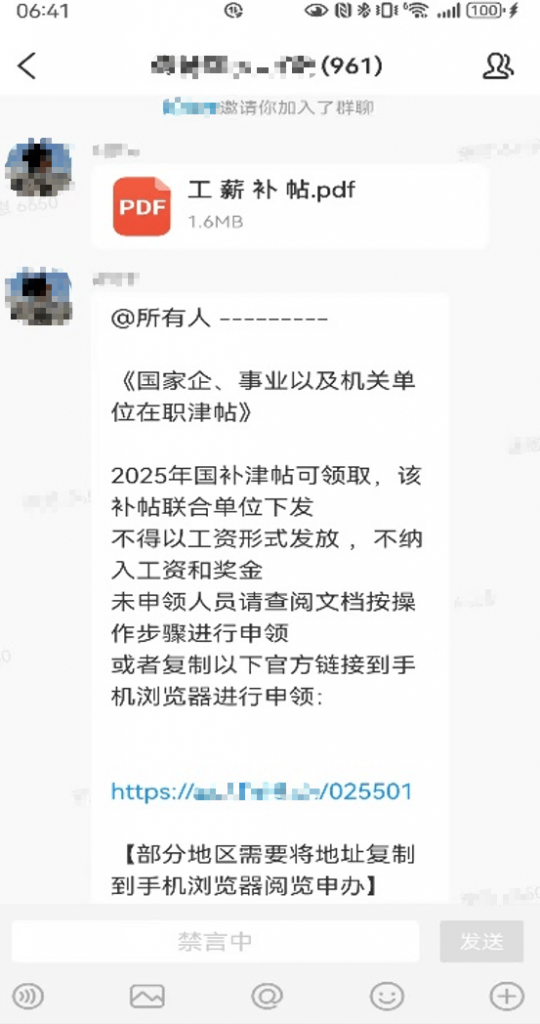
Figure 2‑2 Phishing Using Phishing Links
- Common phishing tactics
| Phishing Tactics | Examples |
| The attacker sent a PDF document file along with instructions and links to phishing websites, luring users to visit the phishing websites. | 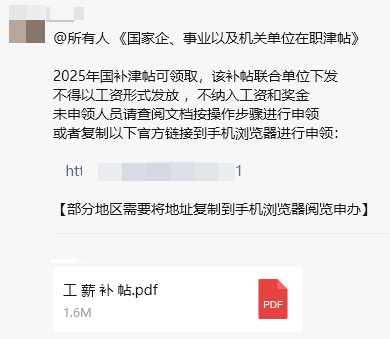 |
| The attacker sent a picture containing instructions and an Alipay QR code, asking users to scan the code with Alipay and visit their phishing website. |  |
| The attacker sends a WeChat QR code, instructing the user to scan it with WeChat and visit a phishing website. | 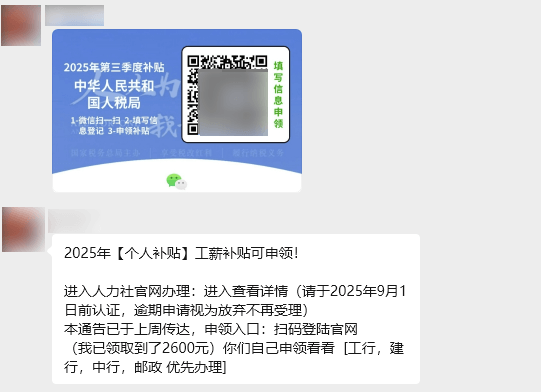 |
- Analysis of typical phishing websites imitating national “subsidies”
After analysis, Antiy CERT found that the “SwimSnake” group would initially verify on all pages whether the identity information entered by the victims had any format errors. On each page, it would induce the victims to fill in their own identity information, such as name, ID number, bank card number, bank card balance, bank card password and mobile phone number, etc. After all the information of the victim has been entered, if the information is filled in correctly, the “SwimSnake” group will directly withdraw or transfer money to the victim’s bank card, and then a fraud incident will occur.
After opening the phishing file, it was found that there was a phishing link inside. This link was consistent with the one in the instructions. Therefore, users who were phished would be redirected to the same phishing website if they clicked on the link in the instructions or clicked the “Log in to Official Processing” button after opening the phishing file.

Figure 2‑3 Phishing File Reports Phishing Website Links
This phishing website can only be opened using the mobile client. By default, the browser of the PC client does not support opening. The homepage on the phishing website was forged as the “Statement on 2025 Individual Subsidies” issued by the Ministry of Human Resources and Social Security of the People’s Republic of China. After clicking “Apply Now”, it redirects to the stage of entering real names and ID numbers, aiming to induce victims to enter their real names and ID numbers.
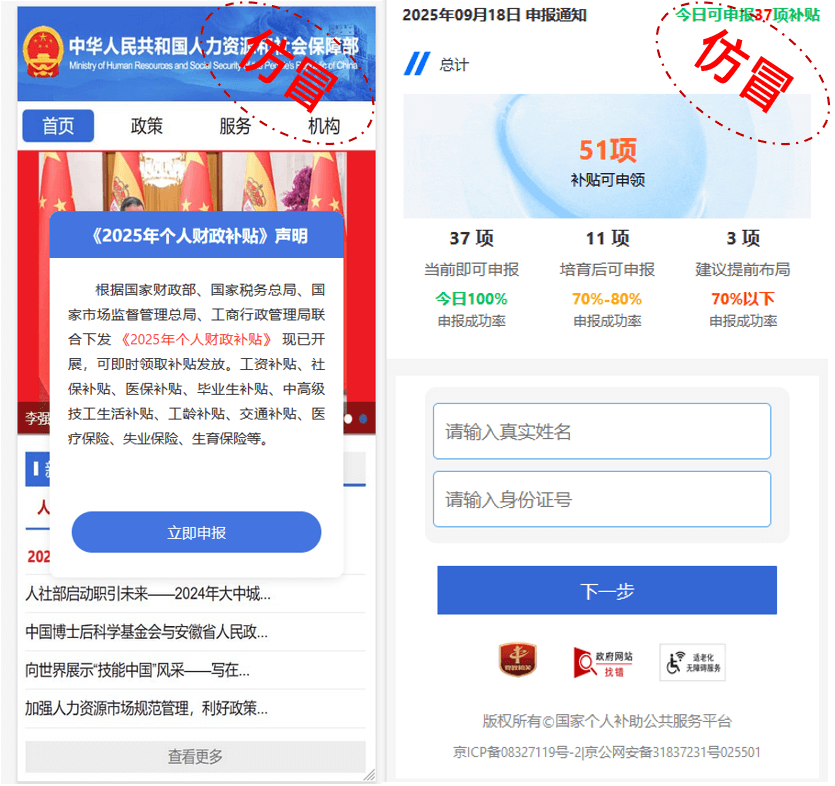
Figure 2‑4 Phishing Site Home Page and Counterfeit Declaration Page
After entering the bank card information, it jumps to the page for verifying the individual’s identity. After clicking “Next”, it jumps to the page for verifying the identity, luring the victim to enter the account balance of the real bank card.
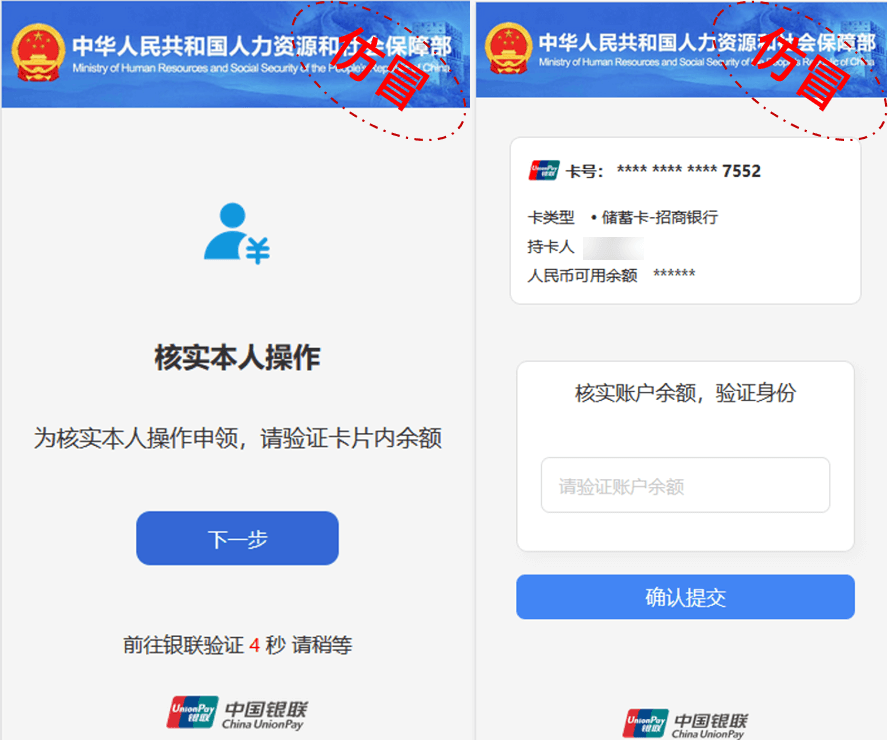
Figure 2‑5 Verify the User ‘s Operation and Induce the User to Enter the Balance of the Bank Account
Then, the user is asked to verify the bank password, thereby tricking the user into entering the real bank card password. After the victim submits, a submitted page will be displayed to deceive the user into believing it to be true.
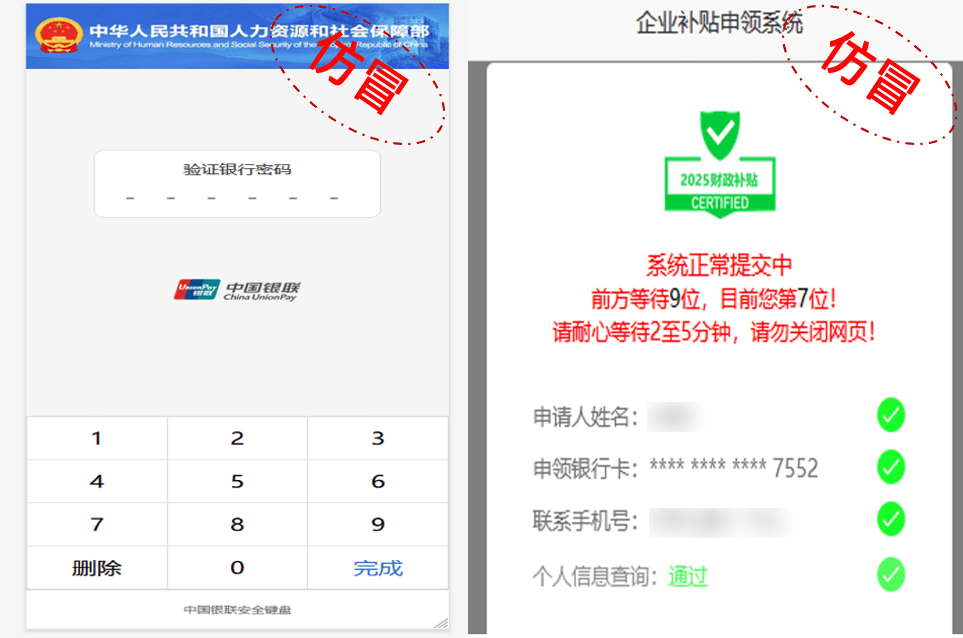
Figure 2‑6 Verify Bank Card Password
If the information submitted by the user is inaccurate, the user will eventually be informed that the submission was not approved, that the ID number is incorrect, etc., and be required to return and re-enter.
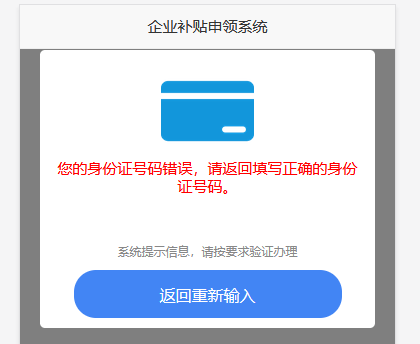
Figure 2‑7 Error Submission Will Require Re-Entry.
3.Defense Strategy for “SwimSnake (Silver Fox)” Cybercriminal Group
3.1 Source Prevention: Blocking Entry Points for Malicious Transmission
- Standardize software downloads and identify counterfeit websites
Only download software from the official website and legitimate app stores. Refuse to download software from non-official channels such as “cracked versions” and “internal versions”.
Carefully check the domain name and be vigilant against counterfeit ones that contain garbled characters or substitution characters (such as changing “o” to “0”).
Download the file to check if it has a formal and valid digital signature and is consistent with the software developer.
Enable the “Safe Browsing Mode” of your browser and the “Web Protection” function of your antivirus software to automatically block phishing websites.
Please refer to the “How to Crack Down on Fake WPS Download Sites: A Special Report on the “SwimSnake (Silver Fox)” Cybercriminal Group’s Mass Impersonation of Popular Apps” released by Antiy for the identification and prevention of phishing websites.
- Identify malicious files spread by instant messaging software and refuse to operate blindly
Be vigilant against files with names containing “Personnel List”, “Subsidy Adjustment”, “Tax Notice”, “Professional Title Evaluation”, “Project Application”, “Heating Subsidy”, and with garbled characters or overly long characters (such as “List of Internally Disciplined Personnel in 2025 XXXXX.exe”). When seeing.exe or.rar files sent by strangers or non-administrators, verify them first before handling them.
When receiving suspicious files, first scan them with the “right-click scan” function of antivirus software, or use online virus analysis platforms such as Antiy File Analysis Service (https://fenxi.antiy.cn/#/entirety/upload) for detection. Do not double-click to execute unknown executable files.
- Install anti-virus software
It is recommended to install Antiy terminal protection products. Antiy Intelligent Endpoint Protection System (IEP) features enhanced download protection and supports control over the entry points of browsers, instant messaging software, and email clients. It can detect receiving and downloading behaviors, preventing malicious codes from easily landing on local disks or starting up, and blocking the vast majority of malicious files before loading and execution.
3.2 Process Interception: Preventing Proliferation and Fraud
- Manage group chats and prevent malicious proliferation
WeChat and WeCom users: Group owners or administrators can click the three dots in the top-right corner of a group chat to access group settings. Tap “Group Management” to enable the “Group Chat Invitation Confirmation” feature. This blocks attackers from arbitrarily adding members to spread malicious code and enables regular cleanup of unfamiliar accounts.
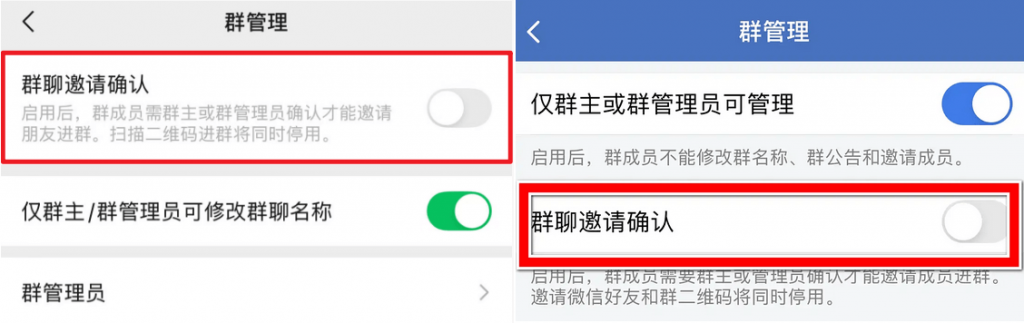
Figure 3‑1 Enable Group Chat Invitation Confirmation Function
- Identify phishing content and do not disclose sensitive information
Upon receiving information such as “Subsidy Application” and “Identity Verification”, first verify through official channels and refuse requests like “open short links in your mobile browser” or “scan QR codes to fill in information”.
If you see phishing websites inducing you to fill in sensitive information such as “bank card password” or “account balance”, close them directly. Do not disclose your ID card number or bank card number to non-official channels.
3.3 Post-Infection Handling: Emergency Operations After Infection
➢ Disconnection to stop losses: Immediately disconnect your computer from the network, exit the chat software, and change your account and password on another device.
➢ Remove viruses: Restart your computer and enter “Safe Mode”. Use antivirus software to perform a full disk scan and delete abnormal processes and malicious files. Users can download and use the “SwimSnake” special troubleshooting tool and the Antiy System Security Analysis Tool (ATool) from the Antiy Vertical Response Platform (https://vs2.antiy.cn) for detection and removal.
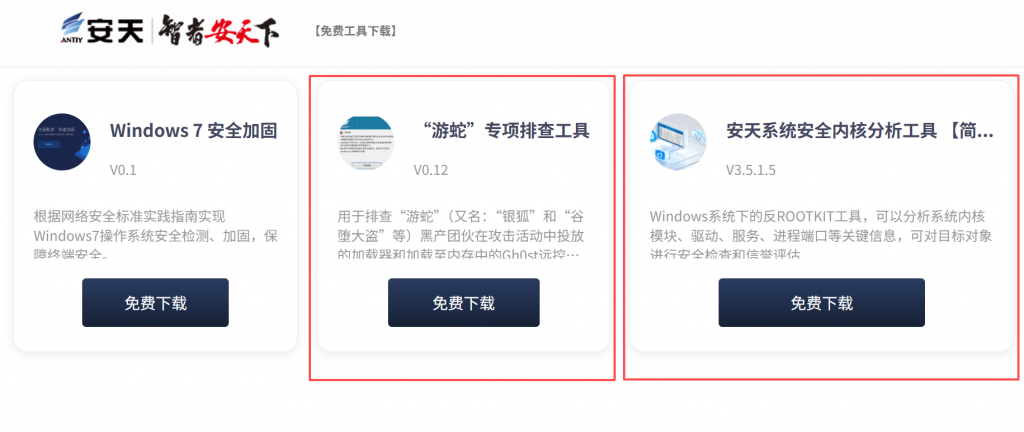
Figure 3‑2 Download Tools in the Antiy Vertical Response Platform
➢ Verify security: Freeze bank cards with filled information and check if there are any abnormal transactions. Notify the contacts in your address book to be vigilant against malicious information and avoid being reinfected.
➢ Preserve evidence: Save malicious files, abnormal screenshots, antivirus logs, etc. You can contact Antiy Emergency Response Team (cert@antiy.cn) for handling. When necessary, redo the system to clean up other malicious codes dropped by attackers.
List of Historical Analysis Reports on SwimSnake by Antiy
[1] Analysis of the Attack Activity of Delivering Remote Access Trojans Through the Fake Chinese Version of Telegram Website [R/OL].(2022-10-24)
https://www.antiy.cn/research/notice&report/research_report/20221024.html
[2] Analysis of Attack Activities Using Cloud Note Platforms to Deliver Remote Access Trojans [R/OL].(2023-03-24)
https://www.antiy.cn/research/notice&report/research_report/20230324.html
[3] Analysis of a Cybercrime Group Using Cloud Notes Platform to Deliver Remote Access Trojans [R/OL].(2023-03-30)
https://www.antiy.cn/research/notice&report/research_report/20230330.html
[4] Analysis of the Large-Scale Attack Activities Launched by the “SwimSnake” Cybercrime Group Against Domestic Users [R/OL].(2023-05-18)
https://www.antiy.cn/research/notice&report/research_report/20230518.html
[5] Analysis of Recent Phishing Attacks by the “SwimSnake” Cybercrime Group [R/OL].(2023-07-11)
https://www.antiy.cn/research/notice&report/research_report/TrojanControl_Analysis.html
[6] Activity Analysis of Malicious Code Spread by the SwimSnake Cybercrime Group Using WeChat [R/OL].(2023-08-22)
https://www.antiy.cn/research/notice&report/research_report/SnakeTrojans_Analysis.html
[7] Special Analysis Report on the SwimSnake Cybercrime Group [R/OL].(2023-10-12)
https://www.antiy.cn/research/notice&report/research_report/SwimSnakeTrojans_Analysis.html
[8] Analysis of the New Round of Attacks by the “SwimSnake” Cybercrime Group Against Financial Personnel and E-Commerce Customer Service [R/OL].(2023-11-11)
https://www.antiy.cn/research/notice&report/research_report/SwimSnake_Analysis.html
[9] Analysis of Recent Attacks by the “SwimSnake” Cybercrime Group [R/OL].(2024-04-07)
https://www.antiy.cn/research/notice&report/research_report/SwimSnake_Analysis_202404.html
[10] Analysis of the “SwimSnake” Cybercrime Group’s Phishing Attack Activities Using Malicious Documents [R/OL].(2024-06-21)
https://www.antiy.cn/research/notice&report/research_report/SwimSnake_Analysis_202406.html
[11] Phishing Download Website Spreads the Threat of “SwimSnake”, Malicious Installer Contains Remote Access Trojan [R/OL].(2024-12-20)
https://www.antiy.cn/research/notice&report/research_report/SwimSnake_Analysis_202412.html
[12] “SwimSnake” Cybercriminal Operations Rampant! Launch Special Inspection and Handling Immediately! [R/OL].(2025-04-23)
https://www.antiy.cn/research/notice&report/research_report/SwimSnake_Analysis_202504.html
[13] The SwimSnake Cybercriminal Group Distributes Remote Access Trojans by Leveraging Counterfeit WPS Office Download Sites [R/OL].(2025-05-15)
https://www.antiy.cn/research/notice&report/research_report/SwimSnake_Analysis_202505.html
[14] SwimSnake (Silver Fox) Cybercrime Group’s Latest Variant Attack Campaign [R/OL].(2025-08-17)
https://www.antiy.cn/research/notice&report/research_report/SwimSnake_Analysis_202508.html
[15] Continuous Tracking of the Dissemination and Tactics of the SwimSnake (Silver Fox) Cybercrime Group: Analysis of the Attack Methods of the Counterfeit Finalshell Management Software [R/OL].(2025-09-19)
https://www.antiy.cn/research/notice&report/research_report/SwimSnake_Analysis_202509.html
[16] How to Crack Down on Fake WPS Download Sites: A Special Report on the “SwimSnake (Silver Fox) [R/OL].(2025-10-10)
https://www.antiy.cn/research/notice&report/research_report/SwimSnake_Analysis_202510.html


